The Algorithm for Solving Quantum Linear Systems of Equations With Coherent Superposition and Its Extended Applications
Abstract
Many quantum algorithms for attacking symmetric cryptography involve the rank problem of quantum linear equations. In this paper, we first propose two quantum algorithms for solving quantum linear systems of equations with coherent superposition and construct their specific quantum circuits. Unlike previous related works, our quantum algorithms are universal. Specifically, the two quantum algorithms can both compute the rank and general solution by one measurement. The difference between them is whether the data register containing the quantum coefficient matrix can be disentangled with other registers and keep the data qubits unchanged. On this basis, we apply the two quantum algorithms as a subroutine to parallel Simon’s algorithm (with multiple periods), Grover Meets Simon algorithm, and Alg-PolyQ2 algorithm, respectively. Afterwards, we construct a quantum classifier within Grover Meets Simon algorithm and the test oracle within Alg-PolyQ2 algorithm in detail, including their respective quantum circuits. To our knowledge, no such specific analysis has been done before. We rigorously analyze the success probability of those algorithms to ensure that the success probability based on the proposed quantum algorithms will not be lower than that of those original algorithms. Finally, we discuss the lower bound of the number of CNOT gates for solving quantum linear systems of equations with coherent superposition, and our quantum algorithms reach the optimum in terms of minimizing the number of CNOT gates. Furthermore, our analysis indicates that the proposed algorithms are mainly suitable for conducting attacks against lightweight symmetric ciphers, within the effective working time of an ion trap quantum computer.
Keywords: quantum linear systems of equations; parallel Simon’s algorithm; Grover Meets Simon algorithm; Alg-PolyQ2 algorithm; quantum circuits; ion trap quantum computer
1 Introduction
Quantum computing fully utilizes the advantages of parallel computing by exploiting quantum phenomena such as quantum superposition and entanglement, which allows for simultaneous processing of multiple computable states, enhancing efficiency and speed. The unique capabilities of quantum computers allow them to outperform classical computers in some computational tasks. They can solve some problems that are difficult for traditional computers in polynomial time, which significantly impacts the security of many cryptographic schemes nowadays. The well-known quantum algorithm proposed by Shor [1] allows solving factorization and discrete logarithm problems in polynomial time and can achieve an exponential acceleration effect. Since the security of almost all public key schemes in the current classical cryptosystem relies on this computational assumption that those problems are intractable, Shor’s algorithm seriously threatens the security of public key cryptography. The quantum algorithm proposed by Grover [2, 3] can achieve quadratic acceleration compared to the classical exhaustive search. People thought that this was the only threat to symmetric cryptography. However, with many cryptanalyses relying on Simon’s algorithm [4, 5, 6, 7], people changed their minds. Nowadays, the impact of many quantum attacks in symmetric cryptography is still not so clear, and possible potential threats continue to be explored.
The quantum algorithm with exponential speedup proposed by Simon [8] is the enlightenment of many quantum algorithms, and it is of great significance in symmetric cryptanalysis. However, [9] pointed out that only a problem with a promise can obtain the exponential speedup in advance, and any quantum algorithm with unlimited Boolean functions can only provide higher polynomial speedup over classical deterministic algorithms. Simon’s algorithm is often used in cryptanalysis of symmetric cryptography and attacks certain constructions of cipher modes often involved in symmetric cryptography. Kuwakado and Morii first used it to break the 3-round Feistel scheme [4] and then proved that the Even-Mansour construction [10] was insecure with superposition query. Santoli and Schaffiner extended their results and proposed a quantum forgery attack on the CBC-MAC scheme [11]. In [5], Kaplan et al. used Simon’s algorithm to attack various symmetric cryptosystems, such as CBC-MAC, PMAC, GMAC, GCM, OCB, etc. At the same time, it was applied to many constructions, such as LRW Construction. Simon’s algorithm was also applied in the sliding attack [12] to achieve an exponential acceleration effect. Leander et al. [13] combined the quantum algorithm of Grover and Simon to attack FX-Construction for the first time in a cryptographic setting, thereby destroying this construction with whitened keys. In [7], Bonnetain et al. proposed the Alg-PolyQ2 algorithm to attack FX-Construction, greatly reducing the query complexity compared to Grover Meets Simon algorithm.
The problem of solving linear equations must be involved in the process of using Simon’s algorithm. Solving linear systems of equations is the central issue of scientific computing, and the solutions of linear equations in the quantum era need further research. In the quantum setting, Harrow et al. [14] proposed a quantum algorithm to solve non-homogeneous linear systems of equations with a sparse Hamiltonian coefficient matrix, reducing the time complexity of the classical algorithm from to . Based on the idea of HHL algorithm and quantum simulation algorithm [15], Childs et al. [16] proposed a new algorithm to avoid the limitation of HHL algorithm phase estimation and exponentially improve the dependence on accuracy. Then, Wossnig et al. [17] proposed a new algorithm using the quantum singular value estimation algorithm (QSVE) in [18] to break through the sparse matrix assumption in HHL algorithm and further improve the algorithm for solving quantum linear systems of equations. Subasi et al. [19] proposed two quantum algorithms based on adiabatic quantum computing to solve linear equations, further reducing the time complexity.
In the field of cryptography, we often need the accurate solution of linear equations, and solving linear equations is a subroutine in many cryptanalytic algorithms. For cryptanalysis in public-key cryptosystems, the intermediate process of some classical information set decoding schemes often needs to use the Gaussian elimination algorithm to transform the matrix. Perriello [20] and Esser [21] respectively constructed quantum circuits for the information set decoding problem in code-based cryptanalysis algorithms and gave an implementation for solving a system of full-rank quantum linear equations with coherent superposition in the corresponding process. Regarding the cryptanalysis of symmetric cryptosystems, many quantum algorithms for attacking symmetric ciphers involve the problem of quantum linear equations, especially in the process of using Simon’s algorithm. Simon’s algorithm serves as a subroutine in various quantum cryptanalysis algorithms. It needs to solve the problem of quantum linear equations in the quantum setting. In [12], it proposed the method of judging whether the quantum linear equations is full rank, which is of great help to many algorithms based on the quantum linear systems of equations. In [7], it gave two algorithms for asymmetric search of a shift using Simon’s algorithm under the Q1 and Q2 models, which involves the rank problem of quantum linear equations. Many cryptographic protocols are also designed based on quantum linear equations, such as quantum key distribution [22], quantum authentication [23] and quantum secret sharing [24], etc. It can be seen that solving quantum linear systems of equations is a significant research problem in cryptography.
Our contributions In this paper, we define quantum linear equations with coherent superposition and propose two quantum algorithms for solving quantum linear equations with coherent superposition in the quantum setting, which are developed from the algorithm in [25]. Then, we modify and extend this original algorithm to obtain different versions and apply them to different quantum symmetric attack algorithms as a subroutine. In more detail, our main contributions are as follows:
-
1.
We propose two quantum algorithms, differing in whether the data register containing the quantum coefficient matrix can be disentangled with other registers and keep the data qubits unchanged. Algorithm 2 is the case where the data register is entangled with other registers, but it can reduce quantum resources. Algorithm 3 requires that the data register is disentangle with other registers (the data qubits unchanged before and after performing) and adds about qubits to store the general solution. Different from the previous quantum algorithms for solving linear equations, the algorithms we propose are universal for solving quantum linear equations with coherent superposition in the quantum setting, which is the same as the effect of using Gaussian elimination to solve any classical linear equations in a classical computer. Our method is similar to the one given by Bonnetain et al. in [25] to solve the quantum circuit of Boolean linear equations, but we can compute the rank and general solution in any case under the condition of unchanged complexity algorithm in the quantum setting, and give a detailed circuit construction. After performing quantum gates, we can obtain the rank, general solution, and upper triangular matrix by one measurement, and the register containing the solutions can also be used in the subsequent circuits of other quantum algorithms, which makes our method more general.
-
2.
We give three applications involving quantum linear equations as a subroutine, respectively parallel Simon’s algorithm [8] (with multiple periods), Grover Meets Simon algorithm [13], and Alg-PolyQ2 algorithm [7]. First, applying Algorithm 2 to parallel Simon’s algorithm (with multiple periods) can solve the problem by one measurement with the original success probability unchanged (or even higher, close to 1). Similarly, We reconstruct the classifier (in Grover Meets Simon algorithm) as a new quantum classifier by applying Algorithm 2, including its detailed quantum circuit. Afterwards, we construct a detailed circuit of the test oracle (in Alg-PolyQ2 algorithm) combined with Algorithm 3 (which can compute the rank, even though the original article does not specifically introduce how to compute the rank). Moreover, we also construct the specific quantum circuits of the three applications. The solutions to these problems can be obtained by one measurement using the proposed algorithms. Finally, we discuss the optimality of our algorithms and their applicability to lightweight cryptographic attacks during the effective working time of an ion trap quantum computer.
Outline Section 2 introduces some knowledge of linear algebra and the basic principles of quantum computing and quantum circuits. Section 3 gives the specific definition of quantum linear equations with coherent superposition and proposes two quantum algorithms, including their circuit constructions. Section 4 applies the proposed quantum algorithms in some quantum symmetric attack cryptographic algorithms and constructs their specific quantum circuits. Section 5 discusses the lower bound of quantum gate resources for quantum linear equations and the applications of some lightweight ciphers in an ion trap quantum computer, then summarizes the whole article.
2 Preliminaries
In this section, we briefly recall some notations and results about linear equations over binary fields and quantum circuits.
2.1 Gaussian Elimination over Binary Fields
Among the classical algorithms for solving linear equations, the most common one is the Gaussian elimination algorithm. Here, we introduce Gaussian elimination algorithm over binary fields.
Definition 1.
(Linear Equations over Binary Fields) Let be a matrix, and its elements , then is called a matrix over binary fields. Given a matrix and a constant vector , find a vector such that . When , it is called a homogeneous linear system of equations; when , it is called a non-homogeneous linear system of equations.
Definition 2.
(Row Echelon Form over Binary Fields) Given a matrix over binary fields, is called row echelon form over binary fields if the following conditions are satisfied:
-
1.
The first non-zero element of each row is 1, and its column index strictly increases with the increase of the row index (the column index must not be smaller than the row index).
-
2.
All elements below the first non-zero element of the non-zero row are zero.
-
3.
Any rows consisting of all zeros appear below the rows with non-zero elements.
It can be written in the following form:
Definition 3.
(Row Reduced Form Matrix) Given a row echelon matrix over binary fields, if the first non-zero elements of its non-zero rows are all 1, and the rest elements in the column where the first element 1 of its non-zero row is located are all 0, the matrix is called a row reduced form matrix.
Theorem 1.
If the rank of the coefficient matrix is equal to the rank of the coefficient augmented matrix over binary fields, i.e., , then this linear system of equations must have a set of solutions.
Proof.
Let is the rank of , is the rank of , is the number of unknown variables, then , .
If , then the last column in the augmented matrix must be a linear combination of the first columns, i.e., there is a set of solutions to the linear system of equations, and the theorem holds.
If , i.e., , then the rank of is equal to the rank of add the dimension of the subspace spanned by the column vector in , so is not in the subspace spanned by the column vectors of , i.e., cannot be linearly represented by the column vectors of , then the linear system of equations has no solution.
Therefore, when , the linear system of equations must have a set of solutions. ∎
Theorem 2.
If there are basic solution vectors of the homogeneous linear system of equations over binary fields, has a zero solution and non-zero solutions. Then, x has non-zero solutions for non-homogeneous linear system of equations .
2.2 Quantum Circuit
We briefly introduce the relevant knowledge of quantum circuits. A circuit composed of multiple quantum gates with certain logic functions is called a quantum circuit. It is applied to a series of operations of a group of qubits and can be used to describe the change of the quantum state in the two-dimensional Hilbert space. Each quantum logic gate can be represented by a unitary matrix.
A single qubit has two quantum ground states ,. If the quantum state is in a state other than the ground state and can be represented linearly by and , then the state is called a superposition state . The probability amplitudes and are complex numbers and satisfy .
When given qubits, the computational basis has vectors. After applying a series of quantum gates to the initial state, the original quantum superposition state is changed. Finally, we measure the quantum system and get some -qubit vectors on the computational ground state to obtain our desired results.
In quantum circuits, the unitary operators in the Hilbert space are all reversible, and it may be necessary to use auxiliary qubits to achieve our desired goal. Typically, we can perform some computations, copy the results to an output register using Controlled-NOT (CNOT) gates, and uncompute (performing the same operation backwards) to restore the initial state of the auxiliary qubits. That is, if there is a computational operation , then the uncomputing operation is a hermitian conjugate transpose operator . Since arbitrary quantum gates can be represented by single-qubit quantum gates and CNOT gates, we focus on these quantum gates. We first show single-qubit quantum gates in Figure 1.

In quantum circuits, multi-qubit gates are often used. Common multi-qubit gates include CNOT gates, Toffoli gates, SWAP gates, and Fredkin gates. The XOR gate in the classical circuit can be implemented by the CNOT gate in the quantum logic gates. Similarly, the Toffoli gate can implement the "AND" operation in quantum computing, and it can also be regarded as a double-controlled CNOT gate. The Fredkin gate can be viewed as a controlled SWAP gate. They are shown in Figure 2.

In an ion-trap quantum computer, CNOT gates can only operate serially. Even though different CNOT gates involve different qubits, they cannot operate in parallel [26]. Therefore, the number of CNOT gates significantly affects the running time of quantum algorithms. When considering the computational complexity of quantum algorithms, we focus on the number of CNOT gates. Since CNOT gates are very critical in quantum computers, in order to calculate the number of CNOT gates in the subsequent article, we decompose a Toffoli gate into single-qubit quantum gates and CNOT gates.
Shende and Markov confirmed [27] that no matter whether the auxiliary system is used or not, at least 6 CNOT gates are needed to implement the Toffoli gate decomposition. A Toffoli gate can be decomposed into six CNOT gates, seven T gates, two H gates, and one S gate. The quantum circuit is as Figure 3.

In [28], seven CNOT gates can be used to implement the decomposition of Fredkin gates. A Fredkin gate can be decomposed into seven CNOT gates, seven T gates, two H gates, and three S gates. The quantum circuit is Figure 4.

3 Algorithms for Solving Quantum Linear Systems of Equations
In quantum linear equations, there is no need to distinguish column pivots and full pivots (because the pivot can only be 1, there is no statement of selecting the largest pivot, and it does not involve precision issues). Only the precise general algorithm needs to be considered, and we analyze it based on the ideas of Gaussian elimination and Gaussian-Jordan elimination.
We divided the section into three subsections. In section 3.1, we first translate the classical Gaussian-Jordan elimination algorithm over binary fields to the equivalent quantum algorithm, so as to analyze the number of quantum gates required. In section 3.2, we propose a quantum algorithm using the quantum data register itself as a storage register, and the number of quantum gates for solving the quantum linear equations with coherent superposition can be polynomially reduced. In section 3.3, we propose another quantum algorithm using a quantum auxiliary register as a storage register. Although the number of auxiliary qubits for solving the quantum linear equations with coherent superposition increases, this method can be disentangled with other registers and keep the quantum data register unchanged.
Definition 4.
(Quantum linear equations with coherent superposition) We define a quantum state matrix to be the tensor product of , i.e. . After Hadamard transformation , denote , then
If measured, will collapse to a certain classical matrix over binary fields. It can be written as:
, i.e., is 0 or 1.
Given a quantum state constant vector , it can be written as:
If there is a quantum state variable vector that collapses to , such that , then is called the solution of this quantum linear equations with coherent superposition .
3.1 Quantum Gaussian-Jordan elimination for general solution and rank
Theorem 3.
(Quantum Turing completeness theorem [29]) A quantum computer can theoretically solve any problem that a classical computer can solve, and it can outperform classical computers in terms of speed when tackling certain problems.
According to Theorem 3, we first translate the classical Gaussian-Jordan elimination Algorithm 4 in the Appendix to the equivalent quantum algorithm, as shown in Algorithm 1.
Note: denotes the NOT gate; denotes the Hadamard gate; denotes ; denotes ; indicates that when , . represents all elements (the quantum state of 0 or 1) in the -th row. indicates the auxiliary qubits in the process of finding the pivot (when , perform ; when , perform ; when , perform steps 8-10), indicates the auxiliary qubits that are used to judge whether it is the pivot column for each column of each row, indicates the auxiliary qubits that are used to construct the coefficients of the basic solution system, and indicate the auxiliary qubits that need to be used in the row addition and solution process respectively.
Brief description of Algorithm 1: If , add zero quantum states below the original augmented matrix for Gaussian elimination transformation and a all-zero matrix for storing the basic solution system and special solution. First traverse by row, then traverse by column, and use Toffoli gates to find the pivot in each row. If is the first element with 1 in the -th row, mark it as the pivot with a CNOT gate and store it in auxiliary qubits ; use the -th row to eliminate the row where the element is 1 (except the pivot) in the pivot column. Using as control qubits, exchange the elements of the -th row and the -th row such that the pivot is on the main diagonal. After traversing all the rows and columns, if a column is the pivot column, then the data qubit is 1; otherwise, is 0. Continue to traverse by column, if the -th column is the column where the pivot is located, then use the Toffoli gates to XOR to (), and store it in the special solution; otherwise, use the Toffoli gates to XOR to () and assign to 1, then store them in the basic solution system. Then the coefficient before each vector in the basic solution system is obtained to be 0 or 1 by using the Hadamard transformation. By measuring, .
We analyze the number of quantum gates needed by quantum Gaussian-Jordan elimination algorithm for solving quantum linear equations. Steps 8-10 need CNOT gates, step 19 needs CNOT gates, step 24 needs CNOT gates, the total number of CNOT gates is ; steps 8-10 need Toffoli gates, step 12 needs Toffoli gates, step 13 needs Toffoli gates, step 16 needs Toffoli gates, step 18 needs Toffoli gates, step 23 needs Toffoli gates, the total number of Toffoli gates is ; step 14 needs Fredkin gates. Therefore, the number of CNOT gates required is ; the number of Toffoli gates required is ; the number of Fredkin gates required is .
3.2 Quantum algorithm for general solution and rank
In this section, we propose a quantum algorithm that given m n-qubit vectors as input, computes the rank of its span and general solutions. The algorithm can polynomially reduce the number of quantum gates compared with Algorithm 1.
This algorithm needs to add zero quantum states as auxiliary qubits above the original quantum state matrix to form a quantum state matrix, which does not change the rank and solution of the original quantum linear system of equations. We can use the original matrix only as the quantum storage register to complete the process of solving the general solution and rank with this quantum algorithm. We use the symbols and (which can be regarded as auxiliary qubits). indicates whether the -th row in the original quantum state matrix is added to the -th row of the all-zero matrix; indicates whether the -th column is the pivot column or the free variable column after adding the zero quantum states as auxiliary qubits.
When , the matrix added above the original matrix is used to store the quantum state matrix after being transformed into an upper triangle; matrix below the original matrix is stored in the same register as the original matrix. According to Theorem 1, considering the case where there are solutions, we analyze from the coefficient augmented matrix (ignoring the amplitude here), then the coefficient augmented matrix can be transformed into the form as in formula (1).
| (1) |
When , only need to add quantum states above the original matrix to store the quantum state matrix transformed into the upper triangle, and its coefficient augmented matrix is transformed into the form as in formula (2).
| (2) |
In the above two formulas, in the original matrix corresponds to in the new matrix, ; in the original matrix corresponds to in the new matrix, . Initialize and , set all to 0 and all to 1. The detailed quantum algorithm is as shown in Algorithm 2.
Brief description of Algorithm 2: add zero quantum states above the original matrix, when , the zero quantum states need to be added to the original matrix register; when , there is no need to add the zero quantum states. After traversing all the rows and columns, store the basic solution system and special solution in the original matrix register. The first qubits store the basic solution system, and qubits store the special solution. Use the intermediate variables (initialized to 0) and (initialized to 1) for marking. Traverse the elements of the -th column, if () is the first element with 1 in the -th column, then update the value of to 1, the value of to 0, and add the -th row to the -th row to achieve swapping with Toffoli gates; continue to find the element () of the -th to the -th row and the )-th to the -th row, remains unchanged and is still 0, is still 0 after updating; use the -th row to eliminate the row where the element in the -th column is 1 with Toffoli gates. Judge by the updated value of , if the value of is 1, then this column is the column where the free variable is located. Add this column to the -th column of the register where the original matrix is located, i.e., the -th row to the -th row of the -th column of the new matrix, and assign to 1; if the value of is 0, then this column is the column where the pivot is located, and the is the special solution corresponding to the -th row. This special solution is added to the -th element of the -th row of the new matrix. The -th to -th rows of the new matrix correspond to the solutions respectively, and the auxiliary qubits are subjected to Hadamard transformation, so that the coefficient of the basic solution system is 0 or 1, then add its row to the auxiliary qubits .
Note: " to " can be omitted in step 12, but it does not affect the order of magnitude of the number of quantum gates. Symbol description is the same as Algorithm 1.
Its quantum circuit is as shown in Figure 5:


We analyze the number of quantum gates needed by the quantum algorithm Algorithm 2 for solving the quantum linear equations. Step 10 needs CNOT gates, step 14 needs CNOT gates, step 20 needs CNOT gates, the total number of CNOT gates is ; step 7 needs Toffoli gates, step 8 needs Toffoli gates, step 11 needs Toffoli gates, step 13 needs Toffoli gates, step 15 needs Toffoli gates, step 19 needs Toffoli gates, the total number of Toffoli gates is . Therefore, the number of CNOT gates required is ; the number of Toffoli gates required is .
More visually, we do not write other registers. when , is operated, and will become the following form after Algorithm 2:
where indicates that the all-zero quantum state matrix is added below the original matrix , indicates that all-zero vector is added below the constant vector . is a special solution vector, is a basic solution system.
When , is operated, and will become the following form after Algorithm 2:
where indicates that the all-zero quantum state matrix is added below the basic solution system , indicates that the all-zero vector is added below the special solution vector . is an upper triangular quantum state matrix, a special solution vector.
Its universal quantum circuit is as shown in Figure 6.

Note that and are operated respectively when and . means unitary transformation, and the registers are entangled with eacn other after . "" means not to undergo this unitary transformation. In Algorithm 2, for each column, step 7 can be represented by , step 8 can be represented by , steps 6-8 can be represented by , judging whether the row is added and whether the column is the pivot column; steps 9-11 can be represented by , eliminating the rest elements with 1 in the pivot column; steps 12-15 can be represented by , judging whether the colum is a free variable column or a pivot column and operating respectively. Steps 5-15 can be represented by , storing the general solution; steps 16-21 can be represented by , obtaining the final solution (by last measurement).
This quantum algorithm cannot disentangle the data register containing or with other auxiliary registers since the data register is used as control qubits, and the unitary operation is performed. But auxiliary qubits can be saved, and they can be directly used in the circuits of some quantum algorithms for solving linear equations. For example, it can be directly applied to the circuit of parallel Simon’s algorithm (in section 4). However, in the case where we need to obtain the solutions of the quantum linear equations by one measurement at last, the data register can be used as a single input and output, and the data register is disentangled with other auxiliary registers at this time.
3.3 Quantum algorithm for general solution and rank (Another Version)
We propose another algorithm that uses an auxiliary register as a storage register. This algorithm needs to add zero quantum states as auxiliary qubits above and below the original quantum state matrix to form a quantum state matrix, which does not change the rank and solution of the original quantum linear equations. Similarly, the symbols and are also given. The difference from Algorithm 2 is that we use the zero quantum states added below as the storage register for storing the general solution. It can completely disentangle the original quantum coefficient matrix register with other registers and keep data qubits unchanged. According to Theorem 1, considering the case where there are solutions, we analyze from coefficient augmented matrix (ignoring the amplitude), the transformation form is as shown in formula (3), where and of the original matrix correspond to and , respectively.
| (3) |
The matrix added above the original matrix is used to store the quantum state matrix after the upper triangle; the matrix added below the original matrix is used to store the general solution. The first quantum qubits store the basic solution system, and the latter quantum qubits store the special solution. The detailed quantum algorithm is as shown in Algorithm 3.
Note: Same as Algorithm 2, " to " can be omitted in step 5, but it does not affect the order of magnitude of the number of quantum gates. Symbol description is the same as Algorithm 1.
Its quantum circuit is as shown in Figure 7:

Brief description of Algorithm 3: The whole process is similar to Algorithm 2, the difference is that not only adding zero quantum states above the original matrix, but also adding zero quantum states below the original matrix for storing the general solution. Similarly, the -th to the -th rows of the new matrix correspond to the solutions respectively, and the auxiliary qubits are subjected to Hadamard transformation such that the coefficients of the basic solution system is 0 or 1, then add its row to the auxiliary qubits .
We analyze that Algorithm 3 and Algorithm 2 need the same number of quantum gates for solving quantum linear equations.
Vividly, will become the following form after Algorithm 3:
Each row of the quantum state matrix is a register. Here, represents the quantum coefficient matrix, represents the quantum constant vector, represents the all-zero quantum state matrix, represents the quantum upper triangular matrix and the elements of the pivot column are zero except for the pivot, represents the quantum basic solution system, and represents the quantum special solution vector. Its universal quantum circuit is shown in Figure 8.

Unlike Figure 6, there is an additional -qubit auxiliary register for storing the general solution. This is used to disentangle the data register where the original matrix is located with other registers and keep data qubits unchanged, so as to facilitate subsequent applications.
Remark In summary, we compare Algorithm 2 and Algorithm 3. If we need to measure the final result, we do not need to add a third register, i.e., we do not need to add the zero quantum states below the original matrix for storing the general solution. Directly use algorithm 2 to measure the data register, then we can get a matrix that stores the basic solution system and special solution. Compared with Algorithm 3, qubits are saved. If the solutions of quantum linear equations need to be measured at last, the basic solution system and special solution can be directly output in the data register, and they can be disentangled with other auxiliary qubits (not add the registers containing and ); if there is no solution, it can also be judged by the quantum storage register. It is as shown in following Figure 9.

The unitary operators in Figure 9 correspond to in Figure 6. Auxiliary registers’ inputs are the same as outputs and they are disentangled with the data registers.
Due to the nature of quantum entanglement, different registers cannot be measured simultaneously. Therefore, we must store the general solution in the auxiliary register. If we do not need to measure the final result, we need to use the auxiliary register for subsequent other applications. At this time, it is necessary to apply Algorithm 3, which can reverse the first two registers, and only keep the general solution in the auxiliary register added, as shown in Figure 10.

4 Application
In this section, we apply Algorithm 2 and Algorithm 3 as a subroutine to parallel Simon’s algorithm [8] (with multiple periods), Grover Meets Simon algorithm [13], and Alg-PolyQ2 Algorithm [7]. The desired results can be obtained by one measurement at last.
4.1 Application to parallel Simon’s Algorithm
The goal of Simon’s algorithm [8] is to solve the periodic problem of hidden subgroups, which can be described as the following problem:
Simon’s Problem: Suppose there is a quantum oracle with a computable function : , and it satisfies the promise: , such that , we have . The goal is to find the period .
Simon’s algorithm can be performed by the following steps:
-
1.
Prepare the initial state, and perform the Hadamard transform on the first register. The following quantum states can be obtained:
-
2.
Perform a quantum query on the function , mapping to the quantum state:
-
3.
Perform the Hadamard transform on the first register, and the following quantum states can be obtained:
Suppose there is some , for each , then , and the amplitude of this configuration is:
(4) -
4.
The amplitude satisfying is 0. Therefore, it will randomly and uniformly collapse after measuring the first register, and we can obtain a value of y, which must satisfy .
Repeat the above algorithm times to get linearly independent values of , then can be obtained by solving the following classical linear equations:
| (5) |
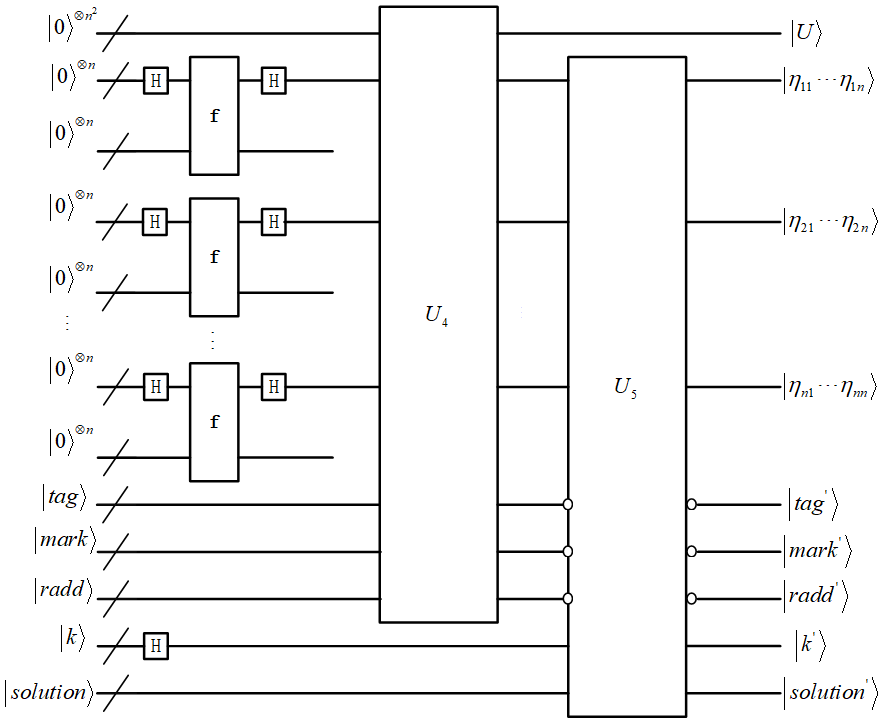
Now we apply Algorithm 2 in section 3 to parallel Simon’s algorithm. Since Simon’s algorithm is probabilistic, we parallel Simon’s algorithms and finally obtain the period with high probability by one measurement. The quantum circuit that applies Algorithm 2 for solving the quantum linear equations to parallel Simon’s algorithm is as shown in Figure 11.
Next, we compute the probability that we can obtain the solution by one measurement.
In Figure 11, there are a total of Simon’s algorithms in parallel, and the quantum states obtained by the first register of each Simon’s algorithm are stored together in of Algorithm 2 (since it is a homogeneous quantum linear system of equations, there is no need to use coefficient augmented matrix, i.e., is a matrix here).
Lemma 1.
Suppose is an -dimensional subspace, randomly select at uniform , then the probability that is linearly independent is at least 0.288.
Proof.
For the first register in each Simon’s algorithm of the parallel Simon’s algorithm, the probability that is
where is a subgroup over binary fields and is the coset representation, , then . If the set of Eqs.(5) has only one nontrivial solution, according to Theorem 2, when we query times, we can get linearly independent vectors to obtain the only non-zero solution, i.e., the period , and the probability at this time is
According to Euler’s pentagon theorem, . ∎
Thereby, we know that Simon’s algorithm is a probabilistic algorithm, and the promise of Simon’s problem is not always fully satisfied in cryptanalysis. In order to improve the success probability of Simon’s algorithm as much as possible, we need to increase the number of queries. Next, a theorem is given to weigh the relationship between the parallel number of Simon’s queries and the success probability of Simon’s algorithm. This theorem can be found similarly in [5]:
Theorem 4.
Given , s is a period of f, , such that the input satisfies . Define
| (6) |
If , after performing m Simon’s algorithms in parallel, the success probability of outputing the period is at least . When choosing , it can ensure that is far enough away from 1 in eq.(6), so as to ensure that the success probability of Simon’s algorithm is as large as possible.
From Lemma 1, we can see that the upper bound of is . According to Theorem 4, we only need to ensure that the number of parallel Simon’s algorithm is , measure the register once at last, then the solution (period ) to the problem can be obtained with a probability close to 1.
Simon’s quantum algorithm can also be applied to the case where the Boolean function F has two or more periods, i.e., there are multiple non-zero solutions to the quantum linear system of equations.
Simon’s Problem with multiple periods: Suppose there is a quantum oracle with a computable function : . It satisfies the promise: there exist linearly independent vectors , such that , we have . The goal is to find the periods .
Perform steps 1-3 of Simon’s algorithm, then the amplitude of the resulting quantum state is
| (7) |
Since the amplitude of satisfying is 0, there are m blocks (totally equations), and we can divide them into k groups to obtain :
| (8) |
Lemma 2.
Suppose is an -dimensional subspace, randomly select at uniform, then the probability that is linearly independent is at least 0.288.
Proof.
Let be the event that , same as the proof of Lemma 1, for the first register in each Simon’s algorithm of the parallel Simon’s algorithm, the probability satisfying is
where is a subgroup over binary fields and is the coset representation, , then . According to Theorem 2, if we query times, we can get linearly independent vectors to obtain non-zero solutions, the probability at this time is
Similarly, . ∎
Unlike the original Simon’s algorithm, which only has a non-zero period, the last measured register is the data register where is located (shown in 9), rather than the register. This is because, if we measure the solution register , it will only collapse to one of the solutions (period ), but we can get the basic solution system and special solutions by measuring the register where is located, so as to obtain all solutions (periods ).
Similarly, according to Theorem 4, as long as the number of parallel Simon’s algorithm is guaranteed , then the solution (all periods ) to the problem can be obtained with a probability close to 1 by measuring register.
4.2 Application to Grover Meets Simon Algorithm
The Grover Meets Simon algorithm [13] performs a quantum search, uses Simon’s algorithm to identify the correct guess, and can attack the FX-construction. It solves the problem of searching for a periodic function, which can be described as the following problem:
Grover Meets Simon Problem: Suppose there is a quantum oracle with a computable function : , unique , such that , we have . The goal is to find and period .
Simon’s promise: Since some function values may have more than two preimages, the function is not a mapping of . Suppose that is a vector in the linear space of periodic function , choose , so that span a linear space of with high probability (at least ). At this time, under the assumption that is a random periodic function whose period is , the probability that any function value has only two preimages is at least .
We analyze the Grover Meets Simon algorithm in more detail, reconstruct the classifier in the original algorithm from the view of quantum, and while ensuring the high probability of solving and period , Algorithm 2 for solving linear equations in section 3 is applied to Grover Meets Simon algorithm as a subroutine. Moreover, we construct the specific quantum circuit of Grover Meets Simon algorithm.
Here we first show the universal quantum circuit of Grover Meets Simon algorithm:

In fact, the quantum algorithm is a parallel Simon’s algorithm with control qubits and works on the input , the steps are as follows:
-
1.
Prepare the initial state .
-
2.
Perform Hadamard transform on the first qubits, the result is
-
3.
Perform a unitary transformation , the result is
-
4.
Perform Hadamard transform on the qubit, the result is
Assume that measure the last qubits of in step 4, then these qubits will collapse to
for some fixed .
An arbitrary -qubit state from is entangled with . Therefore, after measuring , collapses into a superposition state.
If and are the only two preimages of , then is called a proper state. And collapses to the superposition
| (9) |
it can be seen from eq.(9) that has a non-vanishing amplitude if and only if .
Here, we reconstruct the classifier (in Grover Meets Simon algorithm) as a new quantum classifier , then we give its description and quantum circuit construction based on Algorithm 2 (in fact, this quantum construction can also be applied to the oracle construction in other quantum algorithms):
-
1.
Based on the quantum state , we apply Algorithm 2 to construct the specific quantum circuit of Grover Meets Simon algorithm. Use the second register as control qubits to perform , and store the value in the fourth register. We can obtain the following result (other auxiliary qubits are not listed, the same below):
where is the basic solution system of quantum linear equations .
-
2.
Use the second and the fourth register as control qubits to perform and store the value in the fifth register. We can obtain the following result
where when , i.e. , the value of is ; otherwise, the value of will be multiple or only zero. According to Theorem 2, only when , the coefficient matrix has a unique non-zero solution, so that find according to .
-
3.
Randomly select plaintext pairs , prepare the quantum uniform superposition state in the sixth register, and perform inverse transformation . We can obtain the following result
At this time, there is entanglement between the second register and the fifth register.
-
4.
Suppose that there is a quantum oracle , which can calculate the function , ,
Base on calling the oracle, define the unitary operator :
where , Enc corresponds to FX-construction Enc, is a random permutation in a secure block cipher [13]. When for all , then .
-
5.
Add the auxiliary qubit and perform Hadamard transformation, then perform Grover iteration times , return the result by measuring the first and fifth register.
Next, the quantum classifier in Figure 12 can be constructed, and the detailed quantum circuit of the Figure 12 is as shown in Figure 13.

Where, the framed part in Figure 13 is the quantum classifier construction of in Figure 12, and is the unitary operator . The iteration operator is , where .
The analysis of the success probability is given in [13], and we summarize it as the following theorem:
Theorem 5.
By choosing such that the probability that contains at least proper states is at least , and randomly select plaintext pairs to make the classifier output 1, the probability of getting is at least . Based on the Quantum Amplitude Amplification Theorem proposed by Brassard, Hoyer, Mosca and Tapp [30], choose the number of Grover iterations , then the probability of getting a good state is at least .
Based on Algorithm 2, we can guarantee the same success probability as the above theorem, or even higher (by choosing the number of parallel Simon’s algorithms).
4.3 Application to Asymmetric Search of a Shift
We introduce a problem that can be viewed as a general combination of Simon’s problem and Grover’s problem, which can be solved by a corresponding combination of algorithmic ideas and can reduce query complexity of attacking the FX-construction compared with Grover Meets Simon algorithm. First, we introduce a periodic asymmetric search problem described as follows:
Asymmetric Search Problem of a Period : Suppose , are two functions. is a family of functions on , written as , unique , such that , we have . The goal is to find and .
Simon’s promise: Suppose is a period of the function , , such that the input satisfies . Assume
| (10) |
We analyze Alg-PolyQ2 algorithm in detail, apply Algorithm 3 for solving linear equations in section 3 as a subroutine to Alg-PolyQ2 algorithm [7], and while ensuring the high probability of solving and period , we construct the circuit of the test oracle and the specific circuit of the entire algorithm.
We show the universal quantum circuit of Alg-PolyQ2 algorithm about the test oracle:

Where is unitary operator ; the framed part in Figure 14 is an iterative operator .
Compared with Grover Meets Simon algorithm, this algorithm has two improvements: the first improvement is to reduce the query to , from the exponential level to the polynomial level; the second improvement is that for each , if we get the superposition state and can be queried, then we can obtain whether has a period without repeatedly querying .
Here, we apply Algorithm 3 as a subroutine to this quantum algorithm and give the specific construction of the test oracle. We can obtain and period by the last measurement. The whole algorithm is as follows:
-
1.
Prepare the initial state .
-
2.
Perform the Hadamard transform on the first qubits, the result is
where b is initialized to 0.
-
3.
Query times and obtain the following quantum states:
-
4.
Similarly, query times and obtain the following quantum states:
-
5.
Perform the Hadamard transform on the first qubits, the result is
-
6.
Since it is necessary to ensure that the register where is located is disentangled before and after the test oracle, we apply Algorithm 3 and use the first register as control qubits to perform , store the calculated value of the rank in the fourth register, and store the calculated value of the period in the fifth register. We can obtain the following results (ignore the amplitude, other auxiliary qubits are not listed, the same below):
-
7.
Use the fourth register as control qubits (n CNOT gates) and store the value in the third register. The following result is:
Here, when , ; when , .
-
8.
Perform the inverse transformation to obtain the following result:
-
9.
Suppose that there is a quantum oracle , which can calculate the function , ,
By calling the oracle, one can perform the unitary operator :
where , Enc corresponds to FX-construction Enc [7].
-
10.
Perform Hadamard transform on the first qubits to uncompute, and query again such that becomes .
-
11.
Add the auxiliary qubit and perform Hadamard transformation, then perform Grover iteration, return the result by measuring the second and third register.
-
12.
If the hidden shift is also required, the instance of parallel Simon’s algorithm in section 4.1 needs to be applied to obtain the result by measuring the fifth register.
Next, the test oracle in Figure 14 can be constructed, and a detailed quantum circuit based on Grover iterations is shown as in Figure 15.

Where we give the specific test oracle construction, is initialized to 0, and the framed part in Figure 15 is the test oracle. Before and after applying the test, the register where should be disentangled.
Similarly, the analysis of the success probability is given in [7], and we summarize it as the following theorem:
Theorem 6.
The Alg-PolyQ2 algorithm can query times and times to find with probability , the error produced in each iteration is bounded by the maximum on of , the error probability that Simon’s algorithm returns is a periodic function, but is actually not a periodic function is .
Based on Algorithm 3, we can also guarantee the same success probability as the above theorem, or even higher (by choosing the number of parallel Simon’s algorithms).
5 Discussion and Conclusion
5.1 Discussion
In this paper, we propose two quantum algorithms 2 and 3 for solving quantum linear equations with coherent superposition. The main difference is that Algorithm 2 stores the general solution directly in the data register containing the quantum coefficient matrix, and this register is entangled with the solution register. While Algorithm 3 has an additional qubits auxiliary register for storing the general solution, and the data register containing quantum coefficient matrix is disentangled before and after input (the data qubits remains unchanged). Therefore, we can select distinct quantum algorithms to apply based on various quantum application scenarios, ensuring the feasibility in different quantum settings.
The number of quantum gates of the proposed quantum algorithms for solving quantum linear systems of equations with coherent superposition is . We guess that the lower bound of the number of quantum gates in solving quantum linear systems of equations with coherent superposition at least , which also shows that our quantum algorithms have reached the optimum. Next,we will give a brief proof.
Proof.
(Sketch) We know that solving linear equations in a classical computer is a P problem. Based on the quantum Turing completeness Theorem 3, we can transform this problem into solving quantum linear equations in polynomial time, and we call it the Q problem. Simon’s problem is a BQP problem. Therefore, the problem of solving quantum linear systems of equations can be reduced to Simon’s problem. Then, the lower bound of the number of quantum gates for solving the problem of quantum linear systems of equations will not be lower than the quantum gates required by parallel Simon’s algorithm.
Similarly, we assume that is a function that can solve the problem of quantum linear equations. There must be an Oracle machine , such that can solve the parallel Simon’s problem. At this time, we cook reduce the parallel Simon’s problem to solve the problem of quantum linear equations. Then, the lower bound of the number of quantum gates required by parallel Simon’s algorithm will not be lower than the number of quantum gates for solving the problems of quantum linear equations.
To sum up, the lower bound of the number of quantum gates for solving the problem of quantum linear equations should be the same as the number of quantum gates required by parallel Simon’s algorithm. However, the number of quantum gates required by parallel Simon’s algorithms is at least , so the lower bound of the number of quantum gates for solving the problem of quantum linear systems of equations is at least .
The main idea of our algorithms is still based on Gaussian-Jordan elimination, which needs to traverse the elements of each row and column and perform transformation operations (this process requires Toffoli gates). If the lower bound of the required number of quantum gates is , it means that only the row traversal or column traversal is performed, and the entire algorithm process cannot be completed. Therefore, the number of quantum gates of a quantum algorithm for solving a quantum linear system of equations is at least . ∎
The CNOT gate can be seen as the key to quantum computers, and multiple CNOT gates in an ion trap quantum computer cannot be operated in parallel, but they can only be performed in series. We briefly discuss the applicability of our quantum algorithms based on ion trap computers. An ion trap quantum computer’s effective working time (i.e., decoherence time) is no more than seconds, currently 600 seconds [31]. And it can only handle CNOT gates of the order of in one error-correction period [32]. The time of performing a CNOT gate in an ion trap quantum computer is about [26]. Our algorithms give a specific construction for solving quantum linear equations with coherent superposition. If there are quantum linear equations with coherent superposition, the number of CNOT gates reaches after decomposing Toffoli gates into CNOT gates based on section 3. Parallel computation of multiple quantum computers still faces many technical and implementation challenges. To complete the attack within a meaningful time, our algorithms should be mainly applied to many attacks against lightweight symmetric cipher constructions (e.g., the Three-round Feistel scheme, Even-Mansour Construction [4], FX Construction [13], and so on). It can be applied to the detailed construction of the black box that needs to solve the rank of quantum linear equations, such as DESX [33] (a 64-bit state, two 64-bit whitening keys, and a 56-bit internal key), PRINCE [34], and PRIDE [35] (one 64-bit state, two 64-bit whitening keys, and one 64-bit internal key).
5.2 Conclusion
We first give the definition of quantum linear equations with coherent superposition in detail, then we propose two quantum algorithms for solving quantum linear equations with coherent superposition, and construct their specific quantum circuits. This is a work that has never been done before. According to the quantum Turing completeness Theorem 3, a quantum computer can theoretically simulate the calculation process of any classical Turing machine. Therefore, we analyze the number of quantum gates simulating the classical Gaussian-Jordan elimination is about . However, the number of quantum gates of applying Algorithm 2 and Algorithm 3 can be reduced to , then we prove that it reaches optimality. Moreover, our quantum algorithms can be applied in different quantum settings. All solutions of the quantum linear systems of equations in the quantum setting can be obtained by measuring the storage register (may be a data register or auxiliary register) once.
We also apply the proposed algorithms to parallel Simon’s algorithm [8] (including with multiple periods), Grover Meets Simon algorithm [13] and Alg-PolyQ2 algorithm [7], under the condition of satisfying the same success probability (even higher by choosing the number of parallel Simon’s algorithms), the solutions of the problem can be obtained by one measurement. In addition, based on the proposed quantum algorithms, we reconstruct the classifier black box (in Grover Meets Simon algorithm) as a new quantum classifier and construct the test oracle (the original article does not introduce how to compute the rank in Alg-PolyQ2 algorithm, we can apply Algorithm 3 to compute the rank), then construct their quantum circuits in detail, including specific quantum circuits of the three algorithms. Finally, we discuss our algorithms are applicable to lightweight cryptographic attacks during the effective working time of an ion trap quantum computer.
FUNDING
This work was supported by Beijing Natural Science Foundation (Grant No.4234084).
References
- [1] Peter W Shor. Algorithms for quantum computation: discrete logarithms and factoring. In Proceedings 35th annual symposium on foundations of computer science, pages 124–134. Ieee, 1994.
- [2] Lov K Grover. A fast quantum mechanical algorithm for database search. In Proceedings of the twenty-eighth annual ACM symposium on Theory of computing, pages 212–219, 1996.
- [3] Lov K Grover. Quantum mechanics helps in searching for a needle in a haystack. Physical review letters, 79(2):325, 1997.
- [4] Hidenori Kuwakado and Masakatu Morii. Quantum distinguisher between the 3-round feistel cipher and the random permutation. In 2010 IEEE International Symposium on Information Theory, pages 2682–2685. IEEE, 2010.
- [5] Marc Kaplan, Gaëtan Leurent, Anthony Leverrier, and María Naya-Plasencia. Breaking symmetric cryptosystems using quantum period finding. In Advances in Cryptology–CRYPTO 2016: 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, August 14-18, 2016, Proceedings, Part II 36, pages 207–237. Springer, 2016.
- [6] Xavier Bonnetain. Quantum key-recovery on full aez. In Selected Areas in Cryptography–SAC 2017: 24th International Conference, Ottawa, ON, Canada, August 16-18, 2017, Revised Selected Papers 24, pages 394–406. Springer, 2018.
- [7] Xavier Bonnetain, Akinori Hosoyamada, María Naya-Plasencia, Yu Sasaki, and André Schrottenloher. Quantum attacks without superposition queries: the offline simon’s algorithm. In Advances in Cryptology–ASIACRYPT 2019: 25th International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, December 8–12, 2019, Proceedings, Part I, pages 552–583. Springer, 2019.
- [8] Daniel R Simon. On the power of quantum computation. SIAM journal on computing, 26(5):1474–1483, 1997.
- [9] Robert Beals, Harry Buhrman, Richard Cleve, Michele Mosca, and Ronald De Wolf. Quantum lower bounds by polynomials. Journal of the ACM (JACM), 48(4):778–797, 2001.
- [10] Hidenori Kuwakado and Masakatu Morii. Security on the quantum-type even-mansour cipher. In 2012 International Symposium on Information Theory and its Applications, pages 312–316. IEEE, 2012.
- [11] THOMAS SANTOLI and CHRISTIAN SCHAFFNER. Using simon’s algorithm to attack symmetric-key cryptographic primitives. Quantum Information and Computation, 17(1&2):0065–0078, 2017.
- [12] Xavier Bonnetain, María Naya-Plasencia, and André Schrottenloher. On quantum slide attacks. In Selected Areas in Cryptography–SAC 2019: 26th International Conference, Waterloo, ON, Canada, August 12–16, 2019, Revised Selected Papers, pages 492–519. Springer, 2020.
- [13] Gregor Leander and Alexander May. Grover meets simon–quantumly attacking the fx-construction. In Advances in Cryptology–ASIACRYPT 2017: 23rd International Conference on the Theory and Applications of Cryptology and Information Security, Hong Kong, China, December 3-7, 2017, Proceedings, Part II 23, pages 161–178. Springer, 2017.
- [14] Aram W Harrow, Avinatan Hassidim, and Seth Lloyd. Quantum algorithm for linear systems of equations. Physical review letters, 103(15):150502, 2009.
- [15] Dominic W Berry, Andrew M Childs, Richard Cleve, Robin Kothari, and Rolando D Somma. Exponential improvement in precision for simulating sparse hamiltonians. In Proceedings of the forty-sixth annual ACM symposium on Theory of computing, pages 283–292, 2014.
- [16] Andrew M Childs, Robin Kothari, and Rolando D Somma. Quantum algorithm for systems of linear equations with exponentially improved dependence on precision. SIAM Journal on Computing, 46(6):1920–1950, 2017.
- [17] Leonard Wossnig, Zhikuan Zhao, and Anupam Prakash. Quantum linear system algorithm for dense matrices. Physical review letters, 120(5):050502, 2018.
- [18] Iordanis Kerenidis and Anupam Prakash. Quantum recommendation systems. In Christos H. Papadimitriou, editor, 8th Innovations in Theoretical Computer Science Conference, ITCS 2017, January 9-11, 2017, Berkeley, CA, USA, volume 67 of LIPIcs, pages 49:1–49:21. Schloss Dagstuhl - Leibniz-Zentrum für Informatik, 2017.
- [19] Yiğit Subaşı, Rolando D Somma, and Davide Orsucci. Quantum algorithms for systems of linear equations inspired by adiabatic quantum computing. Physical review letters, 122(6):060504, 2019.
- [20] Simone Perriello, Alessandro Barenghi, and Gerardo Pelosi. A complete quantum circuit to solve the information set decoding problem. In 2021 IEEE International Conference on Quantum Computing and Engineering (QCE), pages 366–377. IEEE, 2021.
- [21] Andre Esser, Sergi Ramos-Calderer, Emanuele Bellini, José I. Latorre, and Marc Manzano. An optimized quantum implementation of ISD on scalable quantum resources. CoRR, abs/2112.06157, 2021.
- [22] Charles H Bennett and Gilles Brassard. Quantum cryptography: Public key distribution and coin tossing. Theoretical Computer Science, 560:7–11, 2014.
- [23] Marcos Curty and David J Santos. Quantum authentication of classical messages. Physical Review A, 64(6):062309, 2001.
- [24] Chuan Wang, Fu-Guo Deng, Yan-Song Li, Xiao-Shu Liu, and Gui Lu Long. Quantum secure direct communication with high-dimension quantum superdense coding. Physical Review A, 71(4):044305, 2005.
- [25] Xavier Bonnetain and Samuel Jaques. Quantum period finding against symmetric primitives in practice. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2022(1):1–27, 2021.
- [26] Li Yang and Rui-Rui Zhou. On the post-quantum security of encrypted key exchange protocols. arXiv preprint arXiv:1305.5640, 2013.
- [27] Vivek V Shende and Igor L Markov. On the cnot-cost of toffoli gates. Quantum Information & Computation, 9(5):461–486, 2009.
- [28] Amit Saha and Om Khanna. Intermediate-qudit assisted improved quantum algorithm for string matching with an advanced decomposition of fredkin gate. CoRR, abs/2304.03050, 2023.
- [29] Michael A Nielsen and Isaac L Chuang. Quantum computation and quantum information. Cambridge university press, 2010.
- [30] Gilles Brassard, Peter Hoyer, Michele Mosca, and Alain Tapp. Quantum amplitude amplification and estimation. Contemporary Mathematics, 305:53–74, 2002.
- [31] Ye Wang, Mark Um, Junhua Zhang, Shuoming An, Ming Lyu, Jing-Ning Zhang, L-M Duan, Dahyun Yum, and Kihwan Kim. Single-qubit quantum memory exceeding ten-minute coherence time. Nature Photonics, 11(10):646–650, 2017.
- [32] Biyao Yang and Li Yang. Effect on ion-trap quantum computers from the quantum nature of the driving field. Science China Information Sciences, 63:1–15, 2020.
- [33] Joe Kilian and Phillip Rogaway. How to protect des against exhaustive key search. In Advances in Cryptology—CRYPTO’96: 16th Annual International Cryptology Conference Santa Barbara, California, USA August 18–22, 1996 Proceedings 16, pages 252–267. Springer, 1996.
- [34] Julia Borghoff, Anne Canteaut, Tim Güneysu, Elif Bilge Kavun, Miroslav Knezevic, Lars R Knudsen, Gregor Leander, Ventzislav Nikov, Christof Paar, Christian Rechberger, et al. Prince–a low-latency block cipher for pervasive computing applications. In Advances in Cryptology–ASIACRYPT 2012: 18th International Conference on the Theory and Application of Cryptology and Information Security, Beijing, China, December 2-6, 2012. Proceedings 18, pages 208–225. Springer, 2012.
- [35] Martin R Albrecht, Benedikt Driessen, Elif Bilge Kavun, Gregor Leander, Christof Paar, and Tolga Yalçın. Block ciphers–focus on the linear layer (feat. pride). In Advances in Cryptology–CRYPTO 2014: 34th Annual Cryptology Conference, Santa Barbara, CA, USA, August 17-21, 2014, Proceedings, Part I 34, pages 57–76. Springer, 2014.
Appendix
Gaussian-Jordan Elimination over Binary Fields
We first give a lemma about the relationship between the rank of the matrix and the number of the basic solution vectors, so as to understand the Gaussian-Jordan elimination algorithm over binary fields.
Lemma 3.
(Rank of matrix over binary fields) Given a matrix over binary fields, then its rank equals the number of unknown variables minus the number of the basic solution vectors.
Proof.
Let be the rank of , and be the number of basic solution vectors.
equals the dimension of the column space of , i.e., the maximum number of linearly independent column vectors of . The matrix has columns in total, and the number of free vector columns is , so the rank of is equal to , the number of basic solution vectors (consists of free vector columns) is . Therefore, the rank of the matrix is equal to the number of unknown variables minus the number of basic solution vectors , i.e., . ∎
According to Lemma 3, we can know that given a matrix over binary fields, when , the number of basis vectors of the solution is , then its coefficient augmented matrix must be transformed into the following form through Gaussian-Jordan elimination method and row-column transformation:
The -th to -th columns are the columns where the free variables are located, then the basic solution system of the linear equations is:
The special solution of the linear equations is . We can obtain the general solution is , where .
Since the above form has undergone a column transformation, the order of the variable vectors corresponding to the special solution and the basic solution system is not sequential. When the general solution is given, the order of the variable vectors still needs to be adjusted. Algorithm 4 gives the method for solving the general solution of the linear equations without column transformation, and the order of the variable vectors does not change at this time.
The row echelon matrix is the middle matrix form of the elimination step in the Gaussian elimination method, which is also a critical step. The row reduced form matrix is the final matrix form after the Gauss-Jordan elimination operation. Based on the two forms, after performing elementary transformations on augmented matrices, we give a Gaussian-Jordan elimination algorithm 4 for the general solutions of linear equations over binary fields.
Brief description of Algorithm 4: Initialization the list, including Pivot, , and base solution system list. If , use the all-zero elements to complement the list into a matrix; if , the matrix remains unchanged. First traverse by row and then traverse by column, if is the first element with 1 in the -th row, mark it as the pivot and store the column index in the list Pivot. Use the -th row to eliminate the row where the element 1 is located in the -th column. Swap the -th row and the -th row so that all pivots are on the main diagonal. After traversing all the rows and columns, at this time, Pivot stores the index of the columns where all the pivots are located in row order. Afterwards, continue to traverse by column, if is in the list Pivot, it means that there is a pivot element in this column, then traverse by row, find the pivot, swap the -th row and the -th row such that the pivot is on the main diagonal, and store the special solution corresponding to in the list at this time, otherwise add zero to the list . If is not in the list Pivot, add the elements in this column to the list in reverse order, and assign the -th element in to 1. Finally, we can obtain the general solution , and the rank is the length of the list Pivot.
A Proof of Theorem 4
Proof.
Given a lemma in [5], as follows:
Lemma 4.
For , consider function , Where, . For , satisfy
| (11) |
Where, means 1 when , otherwise 0.
Now we start to prove Theorem 4. If there are Simon’s algorithms in parallel, vectors can be obtained. Under the promise that the Simon’s algorithm is satisfied, these vectors and are orthogonally spanned into a dimensional linear space. However, if the spanned space is less than n-1 dimensional, then can still be efficiently recovered by testing all vectors that are orthogonal to the subspace. Therefore, the probability of not recovering correctly is , as follows:
Thus, the probability that cannot be recovered correctly, that is, the failure probability is
Therefore, the success probability of recovering the correct period by Simon’s algorithms in parallel is at least . ∎