Simultaneous Mode, Input and State Set-Valued Observers with Applications to Resilient Estimation against Sparse Attacks
Abstract
A simultaneous mode, input and state set-valued observer is proposed for hidden mode switched linear systems with bounded-norm noise and unknown input signals. The observer consists of two constituents: (i) a bank of mode-matched observers and (ii) a mode estimator. Each mode-matched observer recursively outputs the mode-matched sets of compatible states and unknown inputs, while the mode estimator eliminates incompatible modes, using a residual-based criterion. Then, the estimated sets of states and unknown inputs are the union of the mode-matched estimates over all compatible modes. Moreover, sufficient conditions to guarantee the elimination of all false modes are provided and the effectiveness of our approach is exhibited using an illustrative example.
I Introduction
Potential vulnerability of Cyber-Physical Systems (CPS) to adversarial attacks and henceforth their security, are emerging as an important and critical issue. Given that attackers are often strategic, there are many potential avenues through which they can cause harm, steal information/power, etc. Recent incidents of attacks on CPS, e.g., the Maroochy water system and Ukrainian power grid, [1, 2], highlight a need for new resilient estimation and control designs.
In particular, an adversary’s ability to inject counterfeit data into sensor and actuator signals (false data injection) or to compromise an unknown subset of vulnerable sensors and actuators (e.g., [3, 4, 5, 6, 7, 8, 9]) in order to mislead the system operator has been a subject of considerable interest in recent years. This problem can be considered in a more general framework of hidden mode switched linear systems with unknown inputs and also has applications in urban transportation systems [6], aircraft tracking and fault detection [10], etc.
Literature review. The filtering problem of hidden mode systems without unknown inputs have been extensively studied (see, e.g., [11, 12] and references therein). More recently, an extension to consider unknown inputs has been proposed in [6] for stochastic systems. However, these methods mainly focus on obtaining point estimates, i.e., the most likely or best single estimates, and do not directly apply to bounded-error models, i.e., uncertain dynamic systems with set-valued uncertainties (e.g., bounded-norm noise), where the sets of all modes, states and unknown inputs that are compatible with sensor observations are desired.
On the other hand, set-membership or set-valued state observers (e.g., [13, 14, 15]) are capable of estimating the set of compatible states and are preferable to stochastic estimation when hard accuracy bounds are important, e.g., to guarantee safety. Moreover, a recent extension to also compute the set of unknown input signals in addition to the states has been introduced in [16]. However, these approaches do not apply to hidden mode systems that we consider in this paper.
In the context of resilient estimation against sparse false data injection attacks, numerous approaches were proposed (e.g., [3, 4, 5, 6, 7, 8, 9]), but they all only obtain point estimates, as opposed to set-valued estimate s. Moreover, only sensor attacks have been considered, although actuator attacks are also a source of concern in CPS security. On the other hand, our prior work in [16, 17] design a fixed-order set-valued observer that simultaneously outputs sets of compatible state and input estimates despite data injection attacks for linear time-invariant and linear parameter-varying systems, without considering the hidden modes, i.e., with the assumption that the subset of attacked sensors and actuators is known.
To consider hidden modes, a common approach is to construct residual signals, especially for fault detection [18], where a threshold based on the residual signal is used to distinguish between consistent and inconsistent modes. Using this idea, [19] presents a robust control inspired resilient state estimator for models with bounded-norm noise that consists of local estimators, residual detectors and a global fusion detector. However, in their setting, only sensors are attacked, while the existence of the observers are assumed with no observer design approach nor performance guarantees.
Contributions. The goal of this paper is to simultaneously consider state and unknown input estimation as well as mode detection for hidden mode switched linear systems with bounded-norm noise and unknown inputs. To address this, we propose a multiple-model approach that leverages the optimally designed set-valued state and input observers in our previous work [16] to obtain a bank of mode-matched set-valued observers in combination with a novel mode observer based on elimination. Our mode elimination approach uses the upper bound of the norm of to-be-designed residual signals to remove inconsistent modes from the bank of observers. In particular, we provide a tractable method to calculate an upper bound signal for the residual’s norm and prove that the upper bound signal is a convergent sequence. Moreover, we provide sufficient conditions to guarantee that all false modes will be eventually eliminated.
Notation. denotes the -dimensional Euclidean space and nonnegative integers. For a vector and a matrix , , and and denote their induced -norm and non-trivial least singular value, respectively.
II Problem Statement
Consider a hidden mode switched linear system with bounded-norm noise and unknown inputs (i.e., a hybrid system with linear and noisy system dynamics in each mode, and the mode and some inputs are not known/measured):
| (3) |
where is the continuous system state and is the hidden discrete state or mode. For each (fixed) mode , is the known input, the unknown but sparse input or attack signal, i.e., every vector has precisely nonzero elements where is a known parameter, is the output, whereas and are process and measurement 2-norm bounded disturbances with known parameters and as their 2-norm bounds respectively. The matrices , , , , and are known and no prior ‘useful’ knowledge or assumption of the dynamics of , except sparsity is assumed.
More precisely, and represent the different hypothesis for each mode , about the sparsity pattern of the unknown inputs, which in the context of sparse attacks corresponds to which actuators and sensors are attacked or not attacked. In other words, we assume that and for some input matrices and , where and are the number of vulnerable actuator and sensor signals respectively. Note that and , where () is the number of attacked actuator (sensor) signals and clearly cannot exceed the number of vulnerable actuator (sensor) signals, which in turn cannot exceed the total number of actuators (sensors). Furthermore, we assume that the total number of unknown inputs/attacks in each mode is known and equals (sparsity assumption). Moreover, the index matrix () represents the sub-vector of that indicates signal magnitude attacks on the actuators (sensors).
Note that the approach in our paper can be easily extended to handle mode-dependent , , , , , , and but is omitted to simplify the notation. Moreover, throughout the paper, we assume, without loss of generality, that for each possible mode , the system is strongly detectable [16, Definition 1], since this is a necessary and sufficient condition for obtaining meaningful set-valued state and input estimates when the mode is known.
Using the modeling framework above, the simultaneous state, unknown input and hidden mode estimation problem is threefold and can be stated as follows:
Problem 1.
Given a switched linear hidden mode discrete-time bounded-error system with unknown inputs (3),
-
1.
Design a bank of mode-matched observers that for each mode optimally finds the set estimates of compatible states and unknown inputs in the minimum -norm sense, i.e., with minimum average power amplification, conditional on the mode being true.
-
2.
Develop a mode observer via elimination and the corresponding criterion to eliminate false modes.
-
3.
Find sufficient conditions for eliminating all false modes.
III Proposed Observer Design
In this section, we propose a multiple-model approach for simultaneous mode, state and unknown input estimation for (3), where the goal of the observer is to find compatible set estimates , and for unknown inputs, states and modes at time step , respectively.
III-A Overview of Multiple-Model Approach
The multiple-model design approach consists of three components: (i) designing a bank of mode-matched set-valued observers, (ii) designing a mode observer for eliminating incompatible modes using residual detectors, and (iii) a global fusion observer that outputs the desired set-valued mode, input and state estimates.
III-A1 Mode-Matched Set-Valued Observer
First, we design a bank of mode-matched observers, which consists of simultaneous state and input set-valued observers based on the optimal fixed-order observer design in [16], which we briefly summarize here. For each mode-matched observer corresponding to mode , following the approach in [16, Section 3.1], we consider set-valued fixed-order estimates of the form:
| (4) | ||||
| (5) |
where their centroids are obtained with the following three-step recursive observer that is optimal in -norm sense:
Unknown Input Estimation:
| (9) |
Time Update:
| (12) |
Measurement Update:
| (13) |
where , and are observer gain matrices that are chosen in the following theorem from [16] to minimize the “volume” of the set of compatible states and unknown inputs, quantified by the radii and .
Theorem 1.
[16, Lemma 2 & Theorem 4] Suppose the system is strongly detectable, and . Then, for each mode , there exists a stable and optimal (in -norm sense) observer with gain , where the input and state estimation errors, and , are bounded for all (i.e., the set-valued estimates are bounded with radii ), and the observer gains and the set estimates are given in [16, Theorem 2 & Algorithm 1].
III-A2 Mode Estimation Observer
To estimate the set of compatible modes, we consider an elimination approach that compares residual signals against some thresholds. Specifically, we will eliminate a specific mode , if , where the residual signal is defined as follows and the thresholds will be derived in Section III-B.
Definition 1 (Residuals).
For each mode at time step , the residual signal is defined as:
III-A3 Global Fusion Observer
Then, combining the outputs of both components above, our proposed global fusion observer will provide mode, unknown input and state set-valued estimates at each time step as:
The multiple-model approach is summarized in Algorithm 1.
III-B Mode Elimination Approach
The idea is simple. If the residual signal of a particular mode exceeds its upper bound conditioned on this mode being true, we can conclusively rule it out as incompatible. To do so, for each mode , we first compute an upper bound () for the 2-norm of its corresponding residual at time , conditioned on being the true mode. Then, comparing the 2-norm of residual signal in Definition 1 with , we can eliminate mode if the residual’s 2-norm is strictly greater than the upper bound. This can be formalized using the following proposition and theorem.
Proposition 1.
Consider mode at time step , its residual signal (as defined in Definition 1) and the unknown true mode . Then,
where is the true mode’s residual signal (i.e., ), and is the residual error.
Proof.
This follows directly from plugging the above expressions into the right hand side term of Definition 1. ∎
Theorem 2.
Consider mode and its residual signal at time step . Assume that is any signal that satisfies , where is defined in Proposition 1. Then, mode is not the true mode, i.e., can be eliminated at time , if
Proof.
To use contradiction, suppose is the true mode. By uniqueness of the true mode , so and by Proposition 1, and hence , which contradicts with the assumption. ∎
III-C Tractable Computation of Thresholds
Theorem 2 provides a sufficient condition for mode elimination at each time step. To apply this sufficient condition, we need to compute an upper bound for , i.e., our signal ( cf. Theorem 3) and show that it is bounded in the following lemmas.
Lemma 1.
Consider any mode with the unknown true mode being . Then, at time step , we have
| (14) |
where ,
with , , , and .
Proof.
Lemma 2.
For each mode at time step , there exists a generic finite valued upper bound for .
Proof.
Consider the following optimization problem for by leveraging Lemma 1:
| (16) | ||||
The objective 2-norm function is continuous and the constraint set is an intersection of level sets of lower dimensional norm functions, which is closed and bounded , so is compact. Hence, by Weierstrass Theorem [20, Proposition 2.1.1], the objective function attains its maxima on the constraint set and so a finite-valued upper bound exists. ∎
Clearly in Lemma 2 is the tightest possible residual norm’s upper bound and potentially can eliminate the most possible number of modes, so is the best choice if we can calculate it. But, notice that although it was straight forward to show that a finite-valued exists, but since the optimization problem in Lemma 2 is a norm maximization (not minimization) over the intersection of level sets of lower dimensional norm functions, i.e., a non-concave maximization over intersection of quadratic constraints, it is an NP-hard problem [21]. To tackle with this complexity, we provide an over-approximation for in the following Theorem 3, which we call .
Theorem 3.
Consider mode . At time step , let
where is a vertex of the following hypercube:
i.e.,
Then, is an over-approximation for in Lemma 2.
Proof.
Consider the optimization problem
| (17) | |||
Comparing (16) and (17), the two problems have the same objective functions, while since , the constraint set for (16) is a subset of the one for (17). Hence . Also, it is easy to see that , using triangle and sub-multiplicative inequalities. Moreover, (17) is a maximization of a convex objective function over a convex constraint (hypercube ). By a famous result [22, Corollary 32.2.1], in such a problem, the objective function attains its maxima on some of the extreme points of the constraint set, which in this case are the vertices of the hypercube . ∎
It can be easily seen as a corollary of Theorem 3 that:
Corollary 1.
.
Theorem 3 enables us to obtain an upper bound for , by enumerating the objective function in (17) at vertices of the hypercube and choosing the largest value as . Moreover, we can easily calculate ; then, the upper bound is chosen as the minimum of the two as .
Remark 1.
Although simulation results indicate that especially in earlier time steps, may have smaller values than , but if we only consider as the over-approximation and do not use , then we will face two difficulties. First, as time increases, the number of required enumerations (i.e., the number of hypercube’s vertices which is ) increases with an exponential rate. Second and more importantly, as Lemma 3 will indicate later, goes to infinity as time increases, so it will be unlikely to eliminate any mode when the time step is large, i.e., asymptotically speaking, will be useless. In contrast, again by Lemma 3, converges to some steady-state value, so it can be always used as an over-approximation for in the mode elimination process.
IV Mode Detectability
In addition to the nice properties regarding the stability and boundedness of the mode-matched set estimates of state and input obtained from [16], we now provide some sufficient conditions for the system dynamics, which guarantee that regardless of the observations, after some large enough time steps, all the false (i.e., not true) modes can be eliminated, when applying Algorithm 1. To do so, first, we define the concept of mode detectability as well as some assumptions for deriving our sufficient conditions for mode detectability.
Definition 2 (Mode Detectability).
System (3) is called mode detectable if there exists a natural number , such that for all time steps , all false modes are eliminated.
Assumption 1.
There exist known such that and , i.e., there exist known bounds for the whole observation/measurement and state spaces, respectively.
Assumption 2.
The unknown input/attack signal has an unlimited energy, i.e., , where .
Note that Assumption 2 is not restrictive because otherwise, the unknown input/attack signal must vanish asymptotically, which means that the true mode (with no unknown inputs) can be inferred asymptotically.
In order to derive the desired sufficient conditions for mode detectability in Theorem 4, we first present the following Lemmas 3–5. For the sake of clarity, the proofs of these results are given in the Appendix.
Lemma 3.
Lemma 4.
Suppose that Assumption 1 holds. Consider two different modes and their corresponding upper bounds for their residuals’ norms, and , at time step . At least one of the two modes will be eliminated if
| (20) |
where .
Lemma 5.
Consider any mode with the unknown true mode being . Then, at time step , we have
where ,
Theorem 4 (Sufficient Conditions for Mode Detectability).
V Simulation Example
We consider a system that has been used as a benchmark for many state and input filters/observers (e.g.,[6]):
The unknown inputs used in this example are as given in Figure 2, while the initial state estimate and noise signals have bounds , and . We assume possible attacks on the actuator and four of five sensors, i.e., and . Moreover, we assume that there are attacks, so we should consider modes. Table I indicates different modes, their attack location(s) and the matrix for each mode , where, as can be observed, the second set of sufficient conditions in Theorem 4 holds, i.e., for all , so we expect that after some large enough time, all the false modes be eliminated, i.e., at most one (true) mode remains at each time step, which can be seen in Figure 2, where the number of eliminated modes at each time step is exhibited.
| Mode | Attack location(s) | |
|---|---|---|
| Actuator & Sensors 1,2,3 | [0.2518 -0.1068 -0.2409 -0.5862 0.7236]⊤ | |
| Actuator & Sensors 1,2,4 | [0.0080 0.7604 -0.1522 -0.5862 -0.6313]⊤ | |
| Actuator & Sensors 1,3,4 | [-0.5357 0.7289 0.1984 -0.3774 0.0009]⊤ | |
| Actuator & Sensors 2,3,4 | [0.7092 -0.5570 -0.1797 -0.3295 0.2143]⊤ | |
| Sensors 1,2,3,4 | [0.1679 -0.5682 0.5198 -0.4883 0.3747]⊤ |
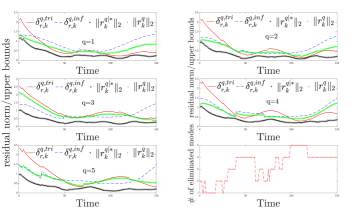
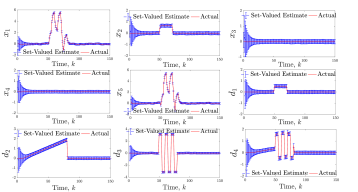
Moreover, for each specific mode , the signals and are depicted in Figure 2. As can be seen, up to some large enough time, at different time intervals for different modes, one of the upper bounds may be tighter than the other, or vice-versa, so it is reasonable that we consider a minimum of them as the computed upper bound in our mode elimination algorithm. Furthermore, for all modes, is eventually convergent while diverges, as we proved in Lemma 3. So, after some large enough time, can be used as our upper-bound, while becomes useless. The corresponding set-valued estimates are provided in Figure 2.
VI Conclusion
We proposed a residual-based approach for hidden mode switched linear systems with bounded-norm noise and unknown attack signals . The proposed approach at each time step, removes the inconsistent modes and their corresponding observers from a bank of estimators, which includes mode-matched observers . Each mode-matched observer, conditioned on its corresponding mode being true, simultaneously finds bounded sets of states and unknown inputs that include the true state and inputs. Our mode elimination criterion required a bounded upper bound for the residual’s norm, for which we proved its existence and computed it by over-approximating the value function of a non-concave NP-hard norm-maximization problem by expanding its constraint set and converting it into a convex maximization over a convex set with finite number of extreme points. Such a problem can be solved by enumerating the objective function on the extreme points of the constraint set and comparing the corresponding values. Moreover, we proved the convergence of the upper bound signal and derived sufficient conditions for eventually eliminating all false modes using our mode elimination algorithm. Finally, we demonstrated the effectiveness of our observer using an illustrative example.
References
- [1] A.A. Cárdenas, S. Amin, and S. Sastry. Research challenges for the security of control systems. In Proceedings of the 3rd Conference on Hot Topics in Security, HOTSEC’08, pages 6:1–6:6, 2008.
- [2] K. Zetter. Inside the cunning, unprecedented hack of Ukraine’s power grid. Wired Magazine, 2016.
- [3] H. Fawzi, P. Tabuada, and S. Diggavi. Secure estimation and control for cyber-physical systems under adversarial attacks. IEEE Transactions on Automatic control, 59(6):1454–1467, 2014.
- [4] F. Pasqualetti, F. Dörfler, and F. Bullo. Attack detection and identification in cyber-physical systems. IEEE Transactions on Automatic Control, 58(11):2715–2729, November 2013.
- [5] M. Pajic, J. Weimer, N. Bezzo, O. Sokolsky, G.J Pappas, and I. Lee. Design and implementation of attack-resilient cyberphysical systems: With a focus on attack-resilient state estimators. IEEE Control Systems Magazine, 37(2):66–81, 2017.
- [6] S.Z. Yong, M. Zhu, and E. Frazzoli. Switching and data injection attacks on stochastic cyber-physical systems: Modeling, resilient estimation, and attack mitigation. ACM Transactions on Cyber-Physical Systems, 2(2):9, 2018.
- [7] M.S Chong, M. Wakaiki, and J.P Hespanha. Observability of linear systems under adversarial attacks. In 2015 American Control Conference (ACC), pages 2439–2444. IEEE, 2015.
- [8] Y. Shoukry and P. Tabuada. Event-triggered state observers for sparse sensor noise/attacks. IEEE Transactions on Automatic Control, 61(8):2079–2091, 2016.
- [9] Y. Mo and E. Garone. Secure dynamic state estimation via local estimators. In 2016 IEEE 55th Conference on Decision and Control (CDC), pages 5073–5078. IEEE, 2016.
- [10] W. Liu and I. Hwang. Robust estimation and fault detection and isolation algorithms for stochastic linear hybrid systems with unknown fault input. IET Control Theory Applications, 5(12):1353–1368, 2011.
- [11] Y. Bar-Shalom, T. Kirubarajan, and X.R. Li. Estimation with Applications to Tracking and Navigation. John Wiley & Sons, Inc., New York, NY, USA, 2002.
- [12] E. Mazor, A. Averbuch, Y. Bar-Shalom, and J. Dayan. Interacting multiple model methods in target tracking: a survey. IEEE Transactions on Aerospace and Electronic Systems, 34(1):103–123, Jan 1998.
- [13] M.A Dahleh and I.J Diaz-Bobillo. Control of uncertain systems: a linear programming approach. Prentice-Hall, Inc., 1994.
- [14] J.S. Shamma and K. Tu. Set-valued observers and optimal disturbance rejection. IEEE Trans. on Automatic Control, 44(2):253–264, 1999.
- [15] F. Blanchini and M. Sznaier. A convex optimization approach to synthesizing bounded complexity filters. IEEE Transactions on Automatic Control, 57(1):216–221, 2012.
- [16] S.Z. Yong. Simultaneous input and state set-valued observers with applications to attack-resilient estimation. In 2018 Annual American Control Conference (ACC), pages 5167–5174. IEEE, 2018.
- [17] M. Khajenejad and S.Z. Yong. Simultaneous input and state set-valued -observers for linear parameter-varying systems. In American Control Conference, pages 4521–4526, July 2019.
- [18] R.J. Patton, P.M. Frank, and R.N. Clark. Issues of fault diagnosis for dynamic systems. Springer Science & Business Media, 2013.
- [19] Y. Nakahira and Y. Mo. Attack-resilient , , and state estimator. arXiv preprint arXiv:1803.07053, 2018.
- [20] D.P. Bertsekas, A. Nedich, A.E Ozdaglar, et al. Convex analysis and optimization. 2003.
- [21] H.L. Bodlaender, P. Gritzmann, V. Klee, and J. Van Leeuwen. Computational complexity of norm-maximization. Combinatorica, 10(2):203–225, 1990.
- [22] R.T. Rockafellar. Convex analysis. Princeton university press, 2015.
- [23] J.F. Grcar. A matrix lower bound. Linear Algebra and its Applications, 433(1):203–220, 2010.
Appendix: Proofs
Proof of Lemma 3.
To show (18), we first find a lower bound for . Then, we show that the lower bound diverges and so does . Define , where is defined in Corollary 1. Now consider
where is the least non-trivial singular value of matrix , the first equality holds since is a linear operator, the second equality is a special case of a matrix lower bound [23] when 2-norms are considered, the inequality holds since by Corollary 1, so is a feasible point for the minimization in the third statement and the last equality holds by Theorem 3. So far we have shown that is a lower bound for . Next, we will prove that is unbounded. First, it is trivial that is unbounded by its definition in Corollary 1. Second, consider the block matrix in Lemma 1. By the strong detectability assumption, matrix is stable [16, Theorem 3 and Appendix C], so all the block matrices of , except three of them which are constant matrices with respect to time, converge to zero matrices when time goes to infinity. Hence converges to an infinite dimensional sparse matrix, with only three non-zero finite dimensional constant blocks and so the limit matrix has a finite rank and clearly has a bounded minimum non-trivial singular value. Henceforth, is unbounded, since the product of the bounded and non-zero and unbounded is unbounded. As for (19), the first equality holds by definition of ( cf. Theorem 3) and (18), the first inequality holds since by triangle and sub-multiplicative inequalities and the last equality, i.e., convergence of , follows from strong detectability assumption which implies the stability of [16, Theorem 3].∎
Proof of Lemma 4.
Suppose, for contradiction, that none of and are eliminated. Then
where the equality holds by Definition 1, the first inequality holds by triangle inequality and the last inequality holds by the assumption that none of and can be eliminated, as well as the boundedness assumption for the measurement space. This last inequality contradicts with the inequality in the lemma, thus the result holds. ∎
Proof of Theorem 4.
To show that (i) is sufficient for asymptotic mode detectability, consider Lemma 4 with as the upper bound. It suffices to show , such that (20) holds for Notice that by Definition 1, . Plugging this into (20), we need to show such that:
| (21) | |||
A sufficient condition to satisfy (21) is that such that , (21) holds for all . Equivalently, it suffices
By expanding the constraint set, it is sufficient to require that such that:
Now, by matrix lower bound theorem [23] and similar argument as in the proof of Lemma 3, it is sufficient to be satisfied that
| (22) |
(22) provides us a time-dependent sufficient condition for mode detectability. In order to find a time-independent sufficient condition, notice that is an upper bound for the right hand side of (22), since the latter’s denominator is smaller than the former’s and the numerator of the latter is an upper bound signal for the former’s by triangle and sub-multiplicative inequalities. So a sufficient condition for (22) is
| (23) |
Then, for the above to hold, it suffices that
which is equivalent to (i) by (19). As for the sufficiency of (ii), notice that by Theorems 2 and 3, Lemma 1 and Definition 2, for mode detectability, it suffices that for any specific mode , the true mode and large enough ,
with given in (17). Since is unknown, a sufficient condition to satisfy the above equality is
So it suffices that , such that:
Again by matrix lower bound theorem, a sufficient condition for the above inequality to hold is that , such that:
| (24) | ||||
Finally, since and
then a sufficient condition for (24) is that
| (25) |
Now suppose that (otherwise the matrix in the denominator of (25) is zero and it never holds). Asymptotically speaking, the right hand side of (25) converges to , since converges to and the least singular value in the denominator either diverges or converges to some steady value . So we set equal to any real number strictly grater than . By unlimited energy assumption for attack signal, after some large enough time step , the monotone increasing function , exceeds and so the system will be mode detectable. ∎