Securing Communications with
Friendly Unmanned Aerial Vehicle Jammers
Abstract
In this paper, we analyze the impact of a friendly unmanned aerial vehicle (UAV) jammer on UAV communications in the presence of multiple eavesdroppers. We first present channel components determined by the line-of-sight (LoS) probability between the friendly UAV jammer and the ground device, and introduce different channel fadings for LoS and non-line-of-sight (NLoS) links. We then derive the secrecy transmission probability satisfying both constraints of legitimate and wiretap channels. We also analyze the secrecy transmission probability in the presence of randomly distributed multiple friendly UAV jammers. Finally, we show the existence of the optimal UAV jammer location, and the impact of the density of eavesdroppers, the transmission power of the UAV jammer, and the density of UAV jammers on the optimal location.
Index Terms:
Unmanned aerial vehicle, physical layer security, line-of-sight probability, secrecy transmission probabilityI Introduction
As an UAV communication has several advantages such as the LoS environment and their flexible mobility, many researchers have studied the use of UAVs as a communication device [1]. Specifically, by using the relation between the LoS probability and the distance-dependent path loss, the optimal positioning of UAVs has been mainly studied. When the UAV height increases, the link between the UAV and the ground device forms the better link due to increasing LoS signal, while the link distance increases. Hence, several works optimized the UAV height to improve the communication performance [2, 3].
In UAV communications, the secrecy is also an important issue due to the broadcast nature of wireless channels. To overcome this, the physical layer security has recently emerged as an effective approach for communication secrecy [4, 5]. Different from terrestrial communications, in UAV communications, the UAV and the ground devices form LoS links with higher probability, so malicious eavesdroppers as well as legitimate receivers can receive the signal from the transmitting UAV with higher power. Hence, the works in [6, 7] provided the optimal deployment and trajectory of UAVs, which improve the effect of the jamming signal to the eavesdroppers, while reducing the effect of the interfering signal to the receivers. Specifically, the optimal UAV height and the transmit power were presented to minimize the secrecy outage probability in [6]. The intercept probability and the ergodic secrecy rate were presented by considering the effect of the UAV height and the transmit power in [7]. However, the works in [6, 7] did not consider the friendly jammer which can reduce the eavesdropping probability.
Recently, the friendly jammer has been considered in [8, 9, 10, 11] to improve the secrecy performance. For the case of the friendly terrestrial jammer, the optimal secrecy guard zone radius was presented to maximize secrecy throughput in [8]. Different from terrestrial communications, the UAV and the ground devices form LoS links with higher probability in UAV communications. Hence, the friendly UAV jammer can generally give stronger jamming signals to eavesdroppers than a terrestrial jammer by having LoS links to eavesdroppers. Furthermore, the friendly UAV jammer can also be readily located to maximize the jamming efficiency as it has on-demand mobility. Therefore, in recent works such as [9, 10, 11], the friendly UAV jammer has also been considered. Specifically, the secrecy energy efficiency was presented to analyze the effect of the transmission power and the density ratio of transmitters to eavesdroppers in [9]. The optimal UAV height and the secrecy guard zone size were presented to maximize the secrecy transmission capacity in [10]. The optimal deployment and transmission power of the friendly UAV jammer were provided to maximize the intercept probability security region in [11]. However, the works in [9, 10] focused on the effect of the density ratio of friendly UAV jammers to eavesdroppers instead of the specific location of the friendly UAV jammer. The optimal location of a friendly UAV jammer was presented in [11], but the channel fading for the air-to-ground (A2G) channel was not considered. In addition, the work in [11] did not show the effect of the eavesdropper density on the optimal location of the friendly UAV jammer.
In this paper, we present the effect of a friendly UAV jammer on the secrecy transmission probability. We consider channel fadings and components, affected by horizontal and vertical distances between the friendly UAV jammer and the ground devices including eavesdroppers. The main contributions of this paper can be summarized as follows:
-
•
we consider realistic channel model, determined by the LoS probability between a friendly UAV jammer and a ground device;
-
•
we derive the secrecy transmission probability considering different channel fadings for LoS and NLoS links;
-
•
we also analyze the secrecy transmission probability by considering multiple UAV jammers, randomly distributed in the network; and
-
•
we finally show the optimal location of the friendly UAV jammer that maximizes the secrecy transmission probability according to the eavesdropper density and the transmission power of the friendly UAV jammer.
II System Model
In this section, we describe the UAV network and the channel model, affected by horizontal and vertical distances between the friendly UAV jammer and ground devices.
II-A Network Description
We consider the UAV network with a transmitter (Tx), a legitimate receiver (Rx), a friendly UAV jammer (Jammer), and multiple eavesdroppers (Eves) as shown in Fig. 1. On the ground, the Tx and the Rx are located at and , respectively. Eves are randomly distributed by a Poisson point process (PPP) with density , where is the location of an arbitrary Eve [12]. Each Eve decodes the received signal from the Tx independently, i.e., we consider non-colluding Eves. The Jammer is placed in an adjustable location . In this network, we assume the Tx and the Jammer do not know the locations of Eves. We also assume the legitimate channel (between Tx and Rx in the presence of Jammer) and the wiretap channel (between Tx and Eves in the presence of Jammer) are independent.111If the eavesdroppers are more than half-wavelength away from the legitimate users, the legitimate users experience independent channels to eavesdroppers [13].
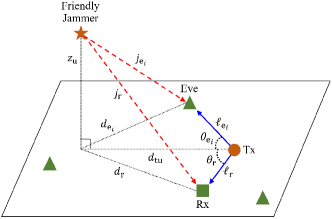
Based on , , , and , we define the signal-to-interference-plus-noise ratio (SINR) of the legitimate channel or the wiretap channel as
| (1) |
where is the link distance between the Tx and the Rx or the Eve , is the link distance between the Jammer and the Rx or the Eve , and are the transmission power of the Tx and the Jammer, respectively, and is the noise power. Here, and are channel fading gains, and and are path loss exponents, where the subscript represents the transmission from the Tx to the Rx or the Eve , and the subscript represents the transmission from the Jammer to the Rx or the Eve .222Note that the instantaneous channel state information (CSI), which is generally difficult to obtain especially for eavesdropping links, is not required in this work. Only the location of Tx and Rx as well as the densities of eavesdroppers and Jammers are needed to determine the location of Jammer. In (1), for convenience, we introduce and , where is horizontal distance between the Jammer and the Rx or the Eve , which can be expressed as
| (2) |
where is the horizontal distance between the Jammer and the Tx, and is the included angle between and as shown in Fig. 1.
II-B Channel Model
Since all the devices except for the Jammer are located on the ground, there can be two types of channels, which are the ground-to-ground (G2G) channel and the A2G channel. The G2G channel between ground devices is commonly modeled as the NLoS environment with the Rayleigh fading due to a lot of obstacles. On the other hand, the A2G channel between the Jammer and the ground device (e.g., the interference link to Rx and the jamming link to Eve) can have the LoS or NLoS environment according to the existence of obstacles. In this subsection, we introduce channel components and provide the model of the A2G channel.
II-B1 Channel component
On UAV communications, channel components such as the LoS probability and the path loss exponent are affected by the horizontal distance and the vertical distance between a Jammer and a Rx or a Eve . First, when the heights of ground devices are sufficiently small, the LoS probability, , , is given by [14]333The LoS probability is also defined in [15], but it is determined by the ratio of the vertical and horizontal link distances, not by the absolute distances. On the other hand, the one in [14] is affected by the absolute positions of the Tx and Rx, and it can be applicable for more general cases.
| (3) |
where is the Q-function, and , , and are environment parameters, determined by the building density and height. We then define the NLoS probability as . Note that the LoS probability can be applicable in various environments (e.g., urban, suburban, and dense urban) by adjusting the environment parameters. In addition, the path loss exponent is determined by when the A2G channel is in the LoS environment. Otherwise, .
II-B2 Air-to-Ground (A2G) channel
In the A2G channel, as the received signal power at the ground device is affected by the combination of the LoS and NLoS signals [16], we consider that the channel fading is the Nakagami- fading with mean for the LoS environment and the Rayleigh fading with mean for the NLoS environment. Therefore, the distribution of channel fading gains, , , can be expressed as
| (4) |
where is the Nakagami- fading parameter and is the gamma function.
III Secrecy Transmission Probability Analysis
In this section, for given and , we analyze the secrecy transmission probability , which is the probability that a Tx reliably transmits signals to a Rx, while all the Eves fail to eavesdrop, and is defined as [8]
| (5) |
where and are target SINRs of the legitimate channel and the wiretap channel, respectively.
Lemma 1
The secrecy transmission probability can be presented as
| (6) |
where and are given by
| (7) | |||
| (8) |
In (8), , which is presented from (7) by substituting from , , and to , , and , respectively.444For given , even though the eavesdropping probability cannot be obtained in a closed-form, we can calculate it efficiently using the numerical integral method.
Proof:
For given , , , and , we can obtain the secrecy transmission probability as
| (9) |
where is the successful transmission probability, is the eavesdropping probability, and (a) is obtained due to the independence between the legitimate channel and the wiretap channel. In (9), can be obtained as [2]
| (10) |
where is the successful transmission probability in the environment of the interference link , given by
| (11) | |||
| (12) |
Here, (a) is from the cumulative distribution function (CDF) of the exponential distribution. In (11), by [17, eq. (3.326)], the integral term can be expressed as
| (13) |
where , , , and . By using (13) in (11) and the definite integral in (12), is presented as (7).
From Lemma 1, we can know that and decrease with . Using this result, the impact of on is shown and discussed in the numerical results.
Corollary 1
For given , , and , the optimal value of that maximizes is .
Proof:
For convenience, we introduce and represent as functions of , , and as
| (15) |
In (15), for given , , and , we obtain the first derivative of with respect to as
| (16) |
In (16), for , , , and . In addition, from (3), we obtain , , and for positive , , and . Hence, the stationary values of are obtained when . Furthermore, we readily know that is greater than because is smaller than and is smaller than . Therefore, the optimal value of that maximizes is . ∎
From Corollary 1, we can see that the Jammer needs to be located along the line from the Rx to the Tx. Hence, in Section V, we analyze instead of .
We now present the asymptotic secrecy transmission probability when the Jammer is located near to the Tx.
Corollary 2
As the Jammer approaches to the Tx, the asymptotic secrecy transmission probability can be given by
| (17) |
where is given in (7).
Proof:
In (8), as (i.e., when the Jammer approaches to the Tx with the height ), the eavesdropping probability can be given by
| (18) |
In (18), when is small, approaches to zero and can be represented as
| (19) |
Using the following result [17, eq. (3.326)]
| (20) |
with , , , and , in (19) can be presented in a closed-form. Finally, we can obtain the asymptotic expression of as (17). ∎
From Corollary 2, we can readily see the effect of the network parameters (e.g., main link distance and transmission power of Tx) on the secrecy transmission probability.
IV Secrecy Transmission Probability Analysis With Multiple UAV Jammers
In this section, we now consider multiple UAV jammers, which are randomly distributed by a PPP with density at the height . The channel components and fading gains between the typical Jammer and the ground device are the same as the single Jammer case. From the secrecy transmission probability in (6), we obtain the secrecy transmission probability for multiple UAV jammers in the following corollary.
Corollary 3
In the presence of multiple UAV jammers, the secrecy transmission probability is given by
| (21) |
where is the successful transmission probability of the interference limited environment (i.e., in (11) and (12)) and is the horizontal distance between the Jammer and the Rx. In (21), is obtained from by replacing , , and with , , and , respectively. Here, is the environment of the jamming link and is the horizontal distance between the Jammer and the Eve.
Proof:
In a similar way to the Corollary 2, we provide the asymptotic analysis of the secrecy transmission probability for multiple UAV jammers. Specifically, in (21), when goes zero, and approach to zero and the secrecy transmission probability can be represented as
| (23) |
where the integral term is represented as [17, eq. (3.241)]
| (24) |
with (or ), , , , and . By using (24) in (23) and , can be expressed as
| (25) |
In (25), when , by substituting , is given by
| (26) |
Using the following result [17, eq. (3.322)]
| (27) |
with and , in (26) can be presented in closed-form as
| (28) |
where is the error function. From this result, we can see the effect of on the secrecy transmission probability.
V Numerical Results
In this section, we evaluate the secrecy transmission probability depending on the location and the transmission power of the Jammer. Unless otherwise specified, the values of simulation parameters are , , , , , , , , , , , and .
Figure 2 presents the secrecy transmission probability as a function of the horizontal distance between the Jammer and the Tx with for different values of the Eve density and the Jammer height . From Fig. 2, we can see that first increases with up to a certain value of , and then decreases. This is because for small , the decrease in the LoS probability of the interference link to the receiver is greater than that of the jamming link to the Eve with , who mainly affects the eavesdropping probability. On the other hand, for large , as increases, the Eve with can be located closer to the Tx than the Rx, so decreases with . We can also see that as increases, the optimal value of decreases to make the jamming link stronger as there exist more Eves. From this, we can find out that as the density of Eves increases, the Jammer needs to be located nearer to the Tx. In Fig. 2, we can additionally see the impact of on according to . Specifically, for small , decreases with since decreases with more than . On the other hand, for large , increases with since becomes similar for different , but still decreases with . Hence, the optimal value of increases with , which means the Jammer needs to be located further from the Tx as increases. Furthermore, we can know that the asymptotic analysis almost matches the analytic analysis as the Jammer approaches to the Tx (i.e., as for ).
Figure 3 presents the secrecy transmission probability as functions of the Jammer height and the horizontal distance between the Tx and the Jammer with . The symbols mean the optimal Jammer locations, and , for each Eve density . From Fig. 3, we can see that first decrease with up to a certain value of , and then increase. This is because, for small (e.g., ), since there exist less eavesdroppers, the Jammer needs to be located at the low height to reduce the LoS probability of interference link to the Rx. However, for relatively high (e.g., ), the Jammer needs to be located closer to the Tx, especially by reducing the horizontal distance for giving stronger jamming signal to Eves, although it also gives larger interference to the Rx. Additionally, when is much higher (e.g., ), since there exist many Eves, the Jammer needs to give much stronger jamming signal to Eves. Hence, the Jammer is located at the high height to increase the LoS probability of the jamming link.
Figure 4 presents the secrecy transmission probability as a function of the height of UAV jammers for different values of the UAV jammer density and the transmission power of the UAV jammer. Here, we use and . From Fig. 4, we can see that first increases with up to a certain value of , and then decreases. This is because for small , the increase in the LoS probability of the jamming link is greater than that of the interference link. On the other hand, for large , the LoS probability of the interference link keeps increasing, while the distance-dependent path loss of the eavesdropping link decreases. Therefore, decreases with when large . We can also see that as increases, the optimal value of decreases to give weaker LoS probability (i.e., weaker signal) on the interference link to the Rx. Furthermore, the optimal value of increases as increases. From these results, we can know that when the effect of UAV jammers is strong enough by using the larger transmit power, the UAV jammers need to be located at the low height to reduce the LoS probability of the interfering signal at the Rx or located at the high height to decrease the distance-dependent path loss of the interference link.
VI Conclusion
This paper derives and analyzes the secrecy transmission probability of UAV communications considering the realistic channel models affected by the communication link. Using the derived expression, we show the effect of a UAV friendly jammer on network parameters. Specifically, as the UAV height increases, the distance-dependent path loss decreases, but the LoS probability for jamming signal increases. From this relation, we show that there can exists an optimal UAV height, which decreases as the density of UAV jammers increases for the multiple Jammer case. We also provide that as the Eve density increases or the Jammer height becomes lower, the optimal horizontal distance between the Jammer and the transmitter decreases to make the jamming link stronger. The outcomes of this work can provide insights on the optimal deployment of the friendly UAV jammer that prevents eavesdropping while reducing the interference to the receiver.
References
- [1] Y. Zeng, R. Zhang, and T. J. Lim, “Wireless communications with unmanned aerial vehicles: opportunities and challenges,” IEEE Commun. Mag., vol. 54, no. 5, pp. 36–42, May 2016.
- [2] M. Kim and J. Lee, “Impact of an interfering node on unmanned aerial vehicle communications,” IEEE Trans. Veh. Technol., vol. 68, no. 12, pp. 12 150–12 163, Dec. 2019.
- [3] D. Kim, J. Lee, and T. Q. S. Quek, “Multi-layer unmanned aerial vehicle networks: Modeling and performance analysis,” IEEE Trans. Wireless Commun., vol. 19, no. 1, pp. 325–339, Jan. 2020.
- [4] A. D. Wyner, “The wire-tap channel,” Bell syst. Tech. J., vol. 54, no. 8, pp. 1355–1387, 1975.
- [5] G. Chen, J. P. Coon, and M. D. Renzo, “Secrecy outage analysis for downlink transmissions in the presence of randomly located eavesdroppers,” IEEE Trans. Inf. Forensics Security, vol. 12, no. 5, pp. 1195–1206, May 2017.
- [6] C. Liu, J. Lee, and T. Q. S. Quek, “Safeguarding UAV communications against full-duplex active eavesdropper,” IEEE Trans. Wireless Commun., vol. 18, no. 6, pp. 2919–2931, Jun. 2019.
- [7] T. Bao, H. Yang, and M. O. Hasna, “Secrecy performance analysis of UAV-assisted relaying communication systems,” IEEE Trans. Veh. Technol., vol. 69, no. 1, pp. 1122–1126, Jan. 2020.
- [8] X. Xu, B. He, W. Yang, X. Zhou, and Y. Cai, “Secure transmission design for cognitive radio networks with poisson distributed eavesdroppers,” IEEE Trans. Inf. Forensics Security, vol. 11, no. 2, pp. 373–387, Feb. 2016.
- [9] X. Qi, B. Li, Z. Chu, K. Huang, H. Chen, and Z. Fei, “Secrecy energy efficiency performance in communication networks with mobile sinks,” Physical Communication, Jul. 2018.
- [10] J. Yao and J. Xu, “Secrecy transmission in large-scale UAV-enabled wireless networks,” IEEE Trans. Commun., vol. 67, no. 11, pp. 7656–7671, Nov. 2019.
- [11] Y. Zhou, P. L. Yeoh, H. Chen, Y. Li, R. Schober, L. Zhuo, and B. Vucetic, “Improving physical layer security via a UAV friendly jammer for unknown eavesdropper location,” IEEE Trans. Veh. Technol., vol. 67, no. 11, pp. 11 280–11 284, Nov. 2018.
- [12] M. Haenggi and R. K. Ganti, “Interference in large wireless networks,” Foundations and Trends in Networking, vol. 3, no. 2, pp. 127–248, 2009.
- [13] D. Tse and P. Viswanath, Fundamentals of wireless communication. Cambridge, U.K.: Cambridge university press, 2005.
- [14] Z. Yang, L. Zhou, G. Zhao, and S. Zhou, “Blockage modeling for inter-layer UAVs communications in urban environments,” in Proc. IEEE Int. Conf. Telecommun. (ICT), St. Malo, France, Jun. 2018, pp. 307–311.
- [15] A. Al-Hourani, S. Kandeepan, and S. Lardner, “Optimal LAP altitude for maximum coverage,” IEEE Wireless Commun. Lett., vol. 3, no. 6, pp. 569–572, Dec. 2014.
- [16] S. Shimamoto et al., “Channel characterization and performance evaluation of mobile communication employing stratospheric platforms,” IEICE Trans. Commun., vol. 89, no. 3, pp. 937–944, Mar. 2006.
- [17] I. S. Gradshteyn and I. M. Ryzhik, Table of Integrals, Series, and Products, 7th ed. San Diego, CA: Academic Press, 2007.