Secure Communication for Spatially Correlated Massive MIMO with Low-Resolution DACs
Abstract
In this paper, the performance of a secure massive multiple-input multiple-output (MIMO) system adopting low-resolution digital-to-analog converters (DACs) is analyzed over spatially correlated wireless channels. A tight lower bound for the achievable secrecy rate is derived with artificial noise (AN) transmitted in the null space of the user channels. Using the analytical results, the impact of spatial correlation on the secrecy rate is explicitly evaluated in the presence of low-resolution DACs. The analytical observations reveal that using low-resolution DACs can be beneficial to the secrecy performance compared with ideal DACs, when the channels are strongly correlated and optimal power allocation is not employed.
Index Terms:
Physical layer security, massive MIMO, spatial correlation, digital-to-analog converters (DACs)I Introduction
Physical layer security (PLS) has become an emerging technology for securing wireless communication without relying upon traditional cryptographic mechanisms. Compared to conventional upper-layer cryptographic schemes, PLS has the advantages of low computational complexity and low resource consumption [1]. Massive multiple-input multiple-output (MIMO) systems provide another disruptive technology for fifth generation (5G) cellular communications, and have shown great potential in improving spectral and energy efficiency. The use of large-scale antenna arrays in massive MIMO provides a large excess of redundant spatial degrees of freedom (DoF), which can be exploited to achieve secure physical layer transmission. This idea has been attracting increasing research interest in the past few years [2], [3].
Massive MIMO transmission requires a very high power consumption if high-resolution digital-to-analog converters (DACs) are employed in the RF chains for each antenna. At the transmitter, power expenditure is dominated by power amplifiers (PAs), which are usually required to operate within a high linearity regime to avoid distortion. A practical solution to the above challenge is to use low-resolution DACs, which relaxes the requirement of linearity and allows the amplifiers to operate closer to saturation, thus increasing the efficiency of PAs [4], [5]. In [6], both finite-bit DACs at base station (BS) and finite-bit analog-to-digital converters (ADCs) at user side were analyzed in the massive MIMO downlink. The work was then extended in [7] by considering spatially correlated channels. Further in [8], a constant envelope precoding technique was devised for the multiuser MIMO with one-bit DACs.
The effect of hardware impairments (HWIs) on spectral efficiency of massive MIMO systems has been studied in [9]. Regarding the secrecy performance, the authors in [10] analyzed the effects of HWIs on secrecy rate, where ideal converters with infinite resolution were considered. Secure communication in a massive MIMO system with low-resolution DACs was investigated in [11], which revealed that low-resolution DACs can achieve superior secrecy rate under certain conditions, e.g., at low SNR or with a large power allocation factor.
Most of the existing works on low-resolution DACs transmissions have focused on the assumption of independent identically distributed (i.i.d.) channels for massive MIMO. However, in practice, the limited space between the BS antennas as well as the rich scattering propagation environment can result in spatial correlation. The impact of correlated Rayleigh fading channels on optimal multiuser loading was analyzed in [6] by applying asymptotic random matrix theory. How spatial correlation impacts secure massive MIMO communication with low-resolution DACs is still an open problem.
In this paper, we focus on secure transmission in the massive MIMO downlink when low-resolution DACs are employed. A tight lower bound for the ergodic secrecy rate is derived that explicitly characterizes the impact of channel correlation on the secrecy rate for typical correlated channels. An optimal power allocation strategy is proposed, which suggests that more power should be allocated to AN when strong channel correlation is present. It is revealed that using low-resolution DACs can improve the secrecy performance for a fixed power allocation factor under strong spatially correlated channels.
Notation: , , and represent the conjugate, transpose, conjugate transpose and trace of matrix , respectively. is the expectation operator. denotes a diagonal matrix that retains only the diagonal elements of the input matrix, and represents a diagonal matrix with the input vector as its diagonal entries.
II System Model
The secure massive MIMO system under investigation comprises one -antenna BS, single-antenna legitimate users, and one -antenna passive eavesdropper. The channel matrices are modeled based on the Kronecker channel model as shown in [12]. To make the problem more tractable, we consider the system with a common correlation matrix at the BS. Specifically, the channel between the BS and the users is modeled as , where the elements of are i.i.d. Gaussian random variables with zero mean and unit variance, the diagonal matrix characterizes the large-scale fading with its th diagonal element given by , and is the transmit covariance matrix satisfying . Similarly, the channel matrix between the BS and the eavesdropper is , where contains i.i.d. Rayleigh fading channel coefficients following . The diagonal matrix represents the large-scale fading at the eavesdropper with identical diagonal entries .
The BS desires to transmit the symbols to the legitimate users with using a linear precoding matrix . The eavesdropper’s channel state information (CSI) is assumed unknown to the BS, and AN is injected to ensure confidential communication. The AN vector is precoded by an AN shaping matrix . Denote by the total transmit power. The power allocation factor aims to strike a balance between the transmit signal and the AN. The unquantized downlink transmit signal vector is then expressed as
| (1) |
where and .
The precoded signal is transmitted after DAC quantization, which is denoted by . Establishing the non-linear quantization model of a finite-bit DAC is challenging. We follow a popular way of charactering the quantizer by a linear function applying the simple additive quantization noise model. The quantized signal vector can accordingly be decomposed as
| (2) |
where the quantization noise is assumed to be uncorrelated with the input signal , and
| (3) |
The value of the distortion factor depends on the DAC resolution; for example, it can be chosen as in [5] for DAC resolutions of less than 5 bits, or as for scenarios with higher precision, where represents the number of quantization bits. From (1) and (3), the covariance matrix of the quantization noise equals
| (4) |
Given the CSI of the legitimate channels, the matrix is designed to lie in the null space of the channel matrix , i.e., , which (ideally) makes the AN “invisible” to the legitimate users [13]. Using (1) and (2), the signals received at the users and the eavesdropper are expressed as
| (5) |
| (6) |
where and respectively represent the additive noise terms at the users and at the eavesdropper.
III Achievable Ergodic Secrecy Rate Analysis
In this section, we derive a tight lower bound for the ergodic secrecy rate of the secure multiuser massive MIMO downlink and analyze the impact of spatial correlation on the secrecy rate in the presence of low-resolution DACs.
III-A Lower Bound on the Achievable Ergodic Secrecy Rate
We adopt linear matched filter (MF) precoding for data transmission, i.e., . The received signal at the th user according to (5) is expressed as
| (7) |
Then, under the assumption of Gaussian distributed interference, a lower bound on the ergodic rate for the th user can be calculated as
| (8) |
| (9) |
where , denotes the th row of , and is the th column of . Note that the numerator of is the power of the desired signal component for the th user, and the denominator represents the power from inter-user interference, quantization noise from the low-resolution DACs, AN leakage, and thermal noise.
Lemma 1
A lower bound on the achievable rate (8) of user is given by
| (10) |
where , and is the average SNR.
Proof:
Please refer to Appendix A. ∎
To guarantee secure communication in the worst case, we assume that the eavesdropper has perfect CSI of all legitimate users and can remove all the interference from the legitimate users [2], [3], [10], [11]. According to (6), the ergodic rate of the eavesdropper is expressed as
| (11) |
where is defined as
| (12) |
Furthermore, we assume that is negligibly small corresponding to the worst case, and consequently, is independent of the path-loss of the eavesdropper [2], [3], [10], [11]. A tight upper bound for is derived in the following lemma.
Lemma 2
For , an upper bound on the eavesdropping rate is given by
| (13) |
where , , , , , and .
Proof:
Please refer to Appendix B. ∎
Applying Lemma 1 and Lemma 2, a lower bound on the ergodic secrecy rate of the th user is obtained in Theorem 1.
Theorem 1
For , the achievable ergodic secrecy rate for the th user is lower bounded by
| (14) |
where , and and are given in (10) and (13), respectively.
If no spatial correlation is present, i.e., , then (14) reduces to
| (15) |
As expected, increases with and .
III-B Optimal Power Allocation Strategy for AN
Here we investigate the impact of the power allocation factor on the ergodic secrecy rate in (14) under spatially correlated channels. Assume in (13), which is reasonable in massive MIMO equipped with a large number of antennas. The derivative of w.r.t. is calculated as
| (16) |
where , , and . Since for small and for large , the optimal power allocation factor that achieves the highest secrecy rate is obtained by setting . A closed-form expression for can be founded as follows:
| (17) |
where the parameters , , and are given by
| (18) |
| (19) |
| (20) |
and , , and .
Assuming , we can simplify the above expressions to evaluate the impact of spatial correlation on for different DAC resolutions. Comparing the value of for the special case of an i.i.d. channel, i.e., with a fully correlated channel, i.e., for a Hermitian Toeplitz correlation matrix, we can easily observe that decreases when increases from to . The relationship between and the design parameters, including the DAC resolution and channel correlation coefficient, is verified in Section IV through numerical results.
III-C Impact of Spatial Correlation
We first analyze the impact of the antenna ratio under the correlated channel condition when AN is injected. In (14), decreases with respect to . Considering the special case of , and , by setting , the maximum number of eavesdropper antennas that still allows for a positive secrecy rate can be obtained from the following proposition.
Proposition 1
If a positive secrecy rate can be achieved, then the maximum antenna ratio is obtained as
| (21) |
Remark 1
By direct inspection of (21), the maximum number of eavesdropper antennas that can be tolerated for secure transmission decreases with and the spatial correlation level because Eve can wiretap more information under strongly correlated channels. For the special case of and , we have , which indicates that is independent of the large-scale fading factor with infinite-resolution DACs.
To extract clear insights, we further consider a representative exponential correlation model [14]
| (22) |
where denotes the correlation coefficient. The exponential model is widely adopted in literature and is applicable to analysis for a massive MIMO system with uniform planar array (UPA) scenarios [15].
Proposition 2
The secrecy rate gap for different DAC resolutions decreases with the correlation coefficient .
Proof:
exists under the exponential correlation model in (22). From (14), we have . The first term is given by
| (23) |
where , , and . The expression of is shown in (24), on the top of the next page.
| (24) |
Assuming for typical massive MIMO systems, (24) can be simplified as
| (25) |
Focusing on the impact of , we observe that and decreases with , while and increases with . Therefore, is an increasing function of , which completes the proof. ∎
Remark 2
From (23) and (25), it shows that and is a monotonically increasing function in terms of the level of spatial correlation . It implies that the eavesdropper’s capacity degrades faster than does at large . Thus, we conclude that there exists a threshold of correlation coefficient, i.e., , where lower-resolution DACs achieve a higher secrecy rate for . The value of is obtained from the solution of by focusing on the impact of spatial correlation. Note that the higher the correlation the lower the effective dimension (d.o.f.), in the extreme case of , the users and Eve are separated only in the angle of arrival domain, which only has dimension 1 instead of . Therefore, quantization noise from lower-resolution DACs could compensate for AN to improve secrecy rate under spatially correlated channel.
IV Numerical Results
In this section, the analytical results are validated through Monte-Carlo simulation. We consider a system with , , and in all simulations. The large-scale fading is modeled as , where denotes the path loss exponent, (m) and (m) are, respectively, the reference distance and the distance between the BS and the th user. The expected values in (14) were evaluated by averaging over 1000 random channel realizations.

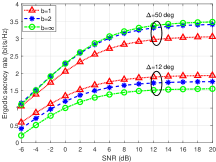
Fig. 1 shows the ergodic secrecy rate versus the average SNR under different DAC resolutions and spatial correlations. The derived lower bound on the secrecy rate is fairly accurate and tight for the entire range of SNR. In addition, it is observed that the secrecy rate is decreasing as increases.
Fig. 2 plots the ergodic secrecy rate as a function of the power allocation factor . The optimal power allocation factor largely depends on . Specifically, It is observed that decreases with . The information signal leakage grows when the spatial correlation is strong. Thus, more power should be allocated for AN to ensure secure communication.
In Fig. 3 (a) we show the ergodic secrecy rate versus with different DAC resolutions for = 10 dB. We choose a fixed power allocation factor due to the difficulties in optimizing theoretically. The secrecy rate loss due to low-resolution DACs decreases with as predicted in Remark 2. Interestingly, although the channel correlation has a detrimental effect on the secrecy rate, the use of 1-bit DACs can improve the secrecy rate when the spatial correlation coefficient is large. This is because the additional quantization noise serves to increase the level of AN, which is beneficial for spatially colored channels if the AN level has not already been optimized. Finally, Fig. 3 (b) presents the secrecy rate versus assuming the optimal power allocation in (17) is chosen. The secrecy rate gaps are bit/s/Hz at and bit/s/Hz at , respectively. If optimal power allocation is adopted, then using infinite-resolution DACs can always achieve a higher secrecy rate. In this case, quantization noise from lower-resolution DACs does not compensate for the AN anymore. However, we observe that the secrecy rate loss due to low-resolution DACs decreases with channel correlation coefficient, regardless of the value of .
For comparison, Fig. 4 plots the Monte-Carlo simulation by using the spatial correlation model in [9], denoted by , where is the large scale fading coefficient, is the actual angle-of-arrival and is the azimuth angular spread. We consider scattering clusters and , . It is observed that transitioning from larger to smaller angular spread ( to ) significantly reduces the secrecy rate of the th user for different DAC resolutions. However, the lower resolution DAC is always beneficial for secrecy rate with a fixed under highly correlated channels as expected.



V Conclusion
This paper has characterized the performance of AN-based secure transmission in a massive MIMO downlink system with low-resolution DACs under spatially correlated channels. In particular, it is shown that optimal secrecy performance can be obtained by increasing the amount of power dedicated to artificial noise when the channel correlation increases. Furthermore, the use of low-resolution DACs has been shown to be beneficial to the secrecy performance for a fixed power allocation factor when the channels possess strong spatial correlation. Interesting future extension of this paper includes studying the impact of different spatial correlation matrices at both transmitter and the eavesdropper.
Appendix A
Consider MF precoding satisfying , which leads to . First, we directly obtain
| (26) |
where we have used in [16, Lemma 4]. Then, the inter-user interference is calculated as
| (27) |
For large and , converges to
| (28) |
where we use the definition of and , and the fact that and due to the strong law of large numbers. Further, we obtain the component of the quantization noise as
| (29) |
Regarding the AN power, it follows that
| (30) |
since . Finally, by substituting (26), (27), (29), (30) and the definition of and into (8), and according to the Continuous Mapping Theorem, we complete the proof.
Appendix B
By applying Jensen’s inequality, the capacity of the eavesdropper can be upper bounded as
| (31) |
Let us first focus on the term and by substituting (28) into (12) yields
| (32) |
where and . It is obvious that , because forms a complete orthogonal basis. Eigendecompose such that to decorrelate matrix as , where is the diagonal matrix of the eigenvalues of and the columns of consist of the corresponding eigenvectors. Since is unitary, the statistics of are identical to those of . Thereby, the distributions of and are the same as
| (33) |
and
| (34) |
where is the th row of , and are th column of and , respectively. Following the same approach in [17], may be accurately approximated as a single scaled Wishart matrix , where we define and . Equating the first two moments of those matrices with and leads to
| (35) |
and
| (36) |
where we use and . By exploiting the independence of the elements in , we can further obtain with , where we use the property for a Wishart matrix with [4]. Substituting this result and into (31) completes the proof.
References
- [1] F. Oggier and B. Hassibi, “The secrecy capacity of the MIMO wiretap channel,” IEEE Trans. Inf. Theory, vol. 57, no. 8, pp. 4961–4972, Jul. 2011.
- [2] J. Zhu, R. Schober, and V. K. Bhargava, “Secure transmission in multicell massive MIMO systems,” IEEE Trans. Wireless Commun., vol. 13, no. 9, pp. 4766–4781, Sep. 2014.
- [3] J. Zhu, R. Schober, and V. K. Bhargava, “Linear precoding of data and artificial noise in secure massive MIMO systems,” IEEE Trans. Wireless Commun., vol. 15, no. 3, pp. 2245–2261, Mar. 2016.
- [4] A. K. Saxena, I. Fijalkow, and A. L. Swindlehurst, “Analysis of one-bit quantized precoding for the multiuser massive MIMO downlink,” IEEE Trans. Signal Process., vol. 65, no. 17, pp. 4624–4634, Sep. 2017.
- [5] Y. Li, C. Tao, A. Lee Swindlehurst, A. Mezghani, and L. Liu, “Downlink achievable rate analysis in massive MIMO systems with one-bit DACs,” IEEE Commun. Lett., vol. 21, no. 7, pp. 1669–1672, Jul. 2017.
- [6] J. Xu, W. Xu, and F. Gong, “On performance of quantized transceiver in multiuser massive MIMO downlinks,” IEEE Wireless Commun. Lett., vol. 6, no. 5, pp. 562–565, Jun. 2017.
- [7] J. Xu, W. Xu, F. Gong, H. Zhang, and X. You, “Optimal multiuser loading in quantized massive MIMO under spatially correlated channels,” IEEE Trans. Veh. Technol., vol. 68, no. 2, pp. 1459–1471, Feb. 2019.
- [8] H. Jedda, A. Mezghani, A. L. Swindlehurst, and J. A. Nossek, “Quantized constant envelope precoding with PSK and QAM signaling,” IEEE Trans. Wireless Commun., vol. 17, no. 12, pp. 8022–8034, Dec. 2018.
- [9] E. Björnson, J. Hoydis, and L. Sanguinetti, “Massive MIMO networks: Spectral, energy, and hardware efficiency,” Found. Trends Signal Process., vol. 11, nos. 3–4, pp. 154–655, 2017.
- [10] J. Zhu, D. W. K. Ng, N. Wang, R. Schober, and V. K. Bhargava, “Analysis and design of secure massive MIMO systems in the presence of hardware impairments,” IEEE Trans. Wireless Commun., vol. 16, no. 3, pp. 2001–2016, Mar. 2017.
- [11] J. Xu, W. Xu, J. Zhu, D. W. K. Ng, and A. Lee Swindlehurst, “Secure massive MIMO communication with low-resolution DACs,” IEEE Trans. Commun., vol. 67, no. 5, pp. 3265–3278, May 2019.
- [12] D.-S. Shiu, G. J. Foschini, M. J. Gans, and J. M. Kahn, “Fading correlation and its effect on the capacity of multielement antenna systems,” IEEE Trans. Commun., vol. 48, no. 3, pp. 502–513, Mar. 2000.
- [13] S. Goel and R. Negi, “Guaranteeing secrecy using artificial noise,” IEEE Trans. Wireless Commun., vol. 7, no. 6, pp. 2180–2189, Jun. 2008.
- [14] S. L. Loyka, “Channel capacity of MIMO architecture using the exponential correlation matrix,” IEEE Commun. Lett., vol. 5, no. 9, pp. 369–371, Sep. 2001.
- [15] H. Lim, Y. Jang, and D. Yoon, “Bounds for eigenvalues of spatial correlation matrices with the exponential model in MIMO systems,” IEEE Trans. Wireless Commun., vol. 16, no. 2, pp. 1196–1204, Feb. 2017.
- [16] J. Hoydis, S. ten Brink, and M. Debbah, “Massive MIMO in the UL/DL of cellular networks: How many antennas do we need?” IEEE J. Sel. Areas Commun., vol. 31, no. 2, pp. 160–171, Feb. 2013.
- [17] Q. T. Zhang and D. P. Liu, “A simple capacity formula for correlated diversity Rician channels,” IEEE Commun. Lett., vol. 6, no. 11, pp. 481–483, Nov. 2002.