Safeguarding UAV Networks Through Integrated Sensing, Jamming, and Communications
Abstract
This paper proposes an integrated sensing, jamming, and communications (ISJC) framework for securing unmanned aerial vehicle (UAV)-enabled wireless networks. The proposed framework advocates the dual use of artificial noise transmitted by an information UAV for simultaneous jamming and sensing of an eavesdropping UAV. Based on the information sensed in the previous time slot, an optimization problem for online resource allocation design is formulated to maximize the number of securely served users in the current time slot, while taking into account a tracking performance constraint and quality-of-service (QoS) requirements regarding the leakage information rate to the eavesdropper and the downlink data rate to the legitimate users. A channel correlation-based algorithm is proposed to obtain a suboptimal solution for the design problem. Simulation results demonstrate the security benefits of integrating sensing into UAV communication systems.
Index Terms— UAV, physical layer security, extended Kalman filter, resource allocation.
1 Introduction
Compared with traditional terrestrial networks, UAV-enabled wireless networks [1] have the potential to cover a larger area with a higher data rate, thanks to their high flexibility and mobility as well as the line-of-sight (LoS) dominated propagation channels to the ground terminals. It is expected that UAV-enabled wireless networks will play a key role in supplementing future cellular networks by providing communication services to rural and hot spot areas [2]. However, UAV communications are highly susceptible to eavesdropping as the associated leakage channels are also LoS dominated [3].
Therefore, the exchange of confidential information in UAV wireless networks has to be safeguarded. Numerous works studied secure resource allocation design for UAV-enabled wireless communication systems assuming the availability of perfect channel state information (CSI) of the eavesdropper channels [4, 5, 6]. For the case of imperfect CSI, the authors of[7, 8] proposed robust and secure resource allocation schemes to enhance the physical layer security (PLS) of UAV communications. However, all these works [4, 5, 6, 7, 8] assumed static eavesdroppers and did not develop specific sensing schemes for the eavesdropper channels. In practice, if the eavesdropper has high-maneuverability, such as an eavesdropping UAV (E-UAV), guaranteeing communication security is very challenging and it is necessary to integrate leakage channel sensing/tracking into the system design. The general concept of sensing-aided PLS has been discussed in the recent article [9], but a corresponding practical scheme has not been reported. The authors in [10] studied PLS in dual-functional radar-communication (DFRC) systems, where the multi-user interference is designed to be constructive at the legitimate users, while disrupting the eavesdropper. A jamming-based PLS enhancing scheme has been proposed for DFRC systems in [11]. However, this scheme does not sense the eavesdropper channel.
In this paper, we propose an integrated sensing, jamming, and communications (ISJC) framework to guarantee PLS in UAV-enabled wireless networks. In particular, an information UAV (I-UAV) transmits confidential information to legitimate ground users (GUs) and jams the E-UAV with artificial noises (AN) to facilitate secure communications. At the same time, the I-UAV tracks the location and velocity of the E-UAV by reusing the reflected AN. Based on the sensing information obtained in the previous time slot, a channel correlation-based online resource allocation algorithm is developed to determine the user scheduling and precoding policy for the current time slot. Our simulation results demonstrate the benefits of integrating sensing, jamming, and communications for safeguard UAV networks.
2 System Model
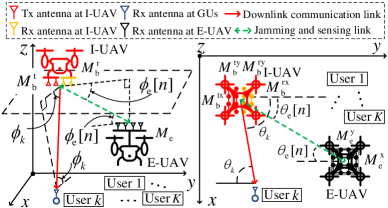
We consider a downlink UAV communication system where a hovering I-UAV111Mobile I-UAVs can further enhance PLS and will be considered in our future work. serves as a base station broadcasting independent confidential data streams to legitimate single-antenna GUs in the presence of a flying E-UAV, cf. Fig. 1. The I-UAV is equipped with two uniform planar arrays (UPAs) for 3-dimensional (3D) transmit (Tx) and receive (Rx) beamforming, respectively, comprising ( rows and columns) and ( rows and columns) antennas, respectively. The E-UAV is equipped with a Rx UPA, comprising ( rows and columns) antennas. The total service time is divided into equal-length time slots with a slot duration of , i.e., . The locations of the I-UAV and GUs are denoted as and , , respectively, where is the transpose operation. The E-UAV flies along a given trajectory, , designed for intercepting the legitimate information transmission with velocity , . The state of the E-UAV, , is unknown to the I-UAV. In contrast, the locations of both the I-UAV and GUs are known to the E-UAV. The time slot structure of the proposed ISJC scheme is illustrated in Fig. 2, where represents all observable parameters at E-UAV. At the beginning of time slot , I-UAV first predicts the state of E-UAV based on the state estimates in time slot , i.e., . Based on the predicted state, I-UAV designs the resource allocation policy for time slot and broadcasts the information and the AN accordingly. Exploiting the echoes from E-UAV, I-UAV takes the new measurement and estimates the new state of E-UAV , which is used as the input of the predictor for time slot . Note that the considered system is inherently causal, where the resource allocation design in time slot is based on new measurements and new state estimates in time slot .

The received signal at GU in time slot is given by
| (1) |
where is a time instant within time slot , denotes the transmitted information signal for GU , is the AN, and denotes the background noise at GU with power . Here, denotes the circularly symmetric complex Gaussian (CSCG) distribution with mean and variance . indicates that GU is selected for communication in time slot , otherwise, . Vectors and denote the precoding vectors for GU and AN, respectively. Vector is the channel vector between I-UAV and GU , where is the steering vector of a UPA of size [12]. Constant represents the channel gain at a reference distance and denotes the distance between I-UAV and GU , where denotes the -norm of a vector. Note that as this is the first work on ISJC in UAV networks, we assume that all links are LoS-dominated to facilitate the presentation. Angles and denote the azimuth angle of departure (AOD) and the elevation AOD from I-UAV to GU , respectively, cf. Fig. 1.
As the precoding policy of I-UAV is unknown to E-UAV, we assume that E-UAV performs maximum ratio combining (MRC) to maximize its received signal power. Assuming the azimuth and elevation angles-of-arrival (AoAs) are perfectly known at the E-UAV, the post-processed signal at E-UAV in time slot is
| (2) |
where represents the MRC gain and is the noise at E-UAV. Vector denotes the effective channel between I-UAV and E-UAV, where is the corresponding distance and and denote the azimuth and elevation AODs from I-UAV to E-UAV, respectively. Due to the unknown location of E-UAV, , , , and are a prior unknown and have to be estimated by I-UAV.
Based on (2), the achievable data rate of GU is given by
| (3) |
When E-UAV intercepts the information of GU , as a worst case, we assume it can mitigate the inter-user interference of the other GUs and is only impaired by the AN. Thus, the leakage information rate associated with GU in time slot is given by
| (4) |
In practice, the signal transmitted by I-UAV is partially received by the Rx antennas of E-UAV and is partially reflected by its body. The I-UAV is assumed to operate in the full-duplex mode, which allows it to transmit and receive signals simultaneously, while the received signal may suffer residual self-interference[13]. The corresponding echo received at I-UAV in time slot is given by
| (5) |
where the round-trip channel matrix is given by
| (6) |
Here, variables and denote the round-trip time delay and Doppler shifts, respectively, denotes the reflection coefficient of E-UAV in time slot , and is the radar cross-section of E-UAV [14]. Vector captures both the background noise and the residual self-interference [13] at I-UAV, where denotes an identical matrix. Note that clutter, such as the reflected signals of the GUs and the ground itself, is omitted here as it can be substantially suppressed by clutter suppression techniques [14] owing to its distinctive reflection angles and Doppler frequencies compared to the echoes from E-UAV [14]. Besides, we assume that the AOA is identical to the corresponding AOD at I-UAV in (6), which is reasonable when assuming a point target model [15] and reciprocal propagation.
3 E-UAV Tracking
3.1 Estimation Model of E-UAV
Based on the echoes in (2), different estimation methods can be used to estimate , , , and [16]. One possible approach to estimate these parameters is the matched filter (MF) principle by exploiting the AN [16]:
| (7) | |||
Note that we exploit the AN rather than the user signals for sensing as using user signals would require the I-UAV to beamform the information-bearing signals towards the E-UAV, which increases the risk of information leakage. Instead, using AN for both sensing and jamming is a win-win strategy for secrecy applications. Analyzing the estimation variances associated with (7) is a challenging task. According to [15, 16], assuming the independence of the AN and the user signals, i.e., , , the estimation variances of , , , and can be modeled by , , , and , respectively, where the MF output signal-to-noise ratio (SNR) is given by
| (8) |
Parameters are determined by the specific adopted estimation methods [15] and is the MF gain, which is proportional to the number of transmit symbols in a time slot.
3.2 Measurement Model for E-UAV
The measurement model characterizes the relationship between the observable parameters and the hidden state, which is the key for inferring the state of E-UAV. In particular, considering the positions of both I-UAV and E-UAV in Fig. 1, the measurement models associated with , , , and are given by
| (9) |
respectively, where is the carrier frequency and is the light speed. , , , , and denote measurement noises with variances , , , , and , respectively. Using trigonometric identities and assuming , we have , , and .
Let collect all observable parameters. Then, the measurement model can be rewritten as
| (10) |
where and represents the Gaussian distribution with mean and covariance matrix . The main diagonal entries of the measurement covariance matrix are given by , , , , and , respectively, and the only two non-zero off-diagonal entries are . The non-linear function represents the measurement functions defined by (3.2).
3.3 State Evolution Model of E-UAV
Assuming a constant velocity movement model [15], the state evolution model of E-UAV is given by
| (11) |
where is the state transition matrix. All main diagonal entries of are one and the only three non-zero off-diagonal entries are . Vector is the state evolution noise vector and is the state evolution covariance matrix, which is assumed to be known by I-UAV from long-term measurements.
3.4 Tracking E-UAV via EKF
Due to the non-linearity of the measurement model in (10), we adopt an extended Kalman filter (EKF) [17] to track E-UAV. In time slot , we assume that I-UAV has the estimates of E-UAV’s state in the previous time slot, , with the corresponding covariance matrix . I-UAV predicts the state of E-UAV in time slot by , where the prediction covariance matrix is given by
| (12) |
According to the predicted state, one can predict the effective channel between I-UAV and E-UAV in time slot as follows,
| (13) |
where , , and are the predicted distance, azimuth AOD, and elevation AOD, respectively. Due to the prediction uncertainty in (12), the channel prediction in (13) is also inaccurate. However, analyzing the prediction variance of is a challenging task due to complicated mapping function between and . To facilitate robust resource allocation design, we assume holds for the channel prediction error , where and parameters can be obtained via Monte Carlo simulation [18].
To update the state of E-UAV in time slot , we linearize the measurement model in (10) around the predicted state, i.e.,
| (14) |
where denotes the Jacobian matrix for with respect to (w.r.t.) for the predicted state, i.e., . Now, the state of E-UAV in time slot is estimated as follows,
| (15) |
and the corresponding posterior covariance matrix is
| (16) |
where the Kalman gain matrix is given by
| (17) |
Note that the trace of characterizes the posterior mean square error (MSE) for tracking the state of E-UAV.
4 Online Resource Allocation Design
4.1 Problem Formulation
In time slot , , the resource allocation design is formulated as the following optimization problem:
| (18) | ||||
| s.t.C1: | ||||
| C2: | ||||
| C3: | ||||
| C4: |
where . The objective function represents the number of GUs that can be served securely. In (18), in C1 is the maximum transmit power, in C2 the minimum data rate for the selected GUs, and in C4 is the maximum tolerable tracking MSE for the location and velocity of E-UAV. in C3 is the maximum allowable leakage rate associated with the selected GUs in the presence of channel prediction uncertainty. Note that in (17) depends on the MF output SNR in (8) and thus in (16) depends on the values of , , and , which are unknown at the time of resource allocation design. Thus, instead of using the posterior covariance matrix , its predicted value, , is adopted in C4. Substituting (17) into (16) and employing the matrix inversion lemma, is given by
| (19) |
where is the predicted measurement covariance matrix, which can be obtained based on the predicted state of the E-UAV . Note that the prediction uncertainty is taken into account in C4 via , see (19).
4.2 Proposed Solution
Now, introducing six auxiliary variables , , to bound the main diagonal entries of , i.e., , C4 in (18) becomes . The problem in (18) is then equivalently transformed as follows
| (20) |
where is the -th column of the identity matrix.
One obstacle for solving (20) is the binary variable . Conventional approaches to handle binary variables, such as the big-M formulation and successive convex approximation [19], require iterative algorithms, whose computational complexity and delay might not be affordable for online resource allocation design. Fortunately, for given user scheduling variables, the problem in (20) becomes a feasibility problem which can be solved optimally by the commonly-used S-procedure [20] and semidefinite relaxation (SDR) approach [21]. Hence, we propose a channel correlation-based user scheduling strategy. Without loss of generality, all GUs are indexed in descending order of the correlation coefficients between and , . In general, the higher the channel correlation, the higher the risk of information leakage. Then, we first select all GUs for service, i.e., , . If the resulting problem in (20) is infeasible, we de-select GUs one-by-one in descending order of their channel correlations until (20) becomes feasible. If all GUs are de-selected and the problem in (20) is still infeasible, the I-UAV transmits only AN for jamming and sensing adopting maximum ratio transmission, i.e., , , and . The details of the resulting algorithm are omitted here due to space limitation.
5 Simulation Results
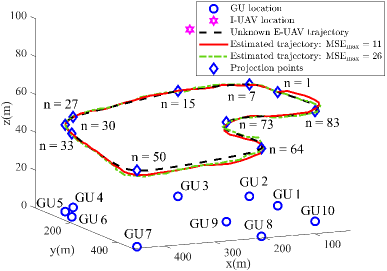
In this section, we evaluate the performance of the proposed ISJC scheme via simulations. The main simulation parameters are as follows: , s, , dBm, bit/s/Hz, bit/s/Hz, , dBm, dBm, dB, , and . Note that a higher implies that a poorer tracking performance is tolerable by the considered system. Thus, we consider . The locations of I-UAV and the GUs and the unknown trajectory of E-UAV are illustrated in Fig. 3. The modeling parameters, including , , , , and , are initialized numerically assuming random walks of the I-UAV and E-UAV, respectively.
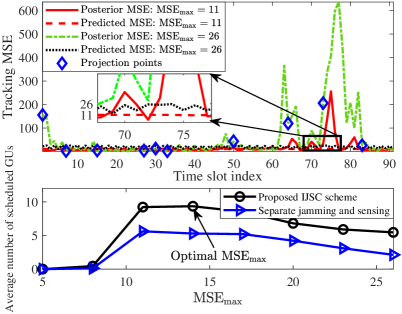
The estimated trajectory of E-UAV is shown in Fig. 3. The corresponding posterior tracking MSE, , in each time slot is shown in the upper half of Fig. 4. We observe that a smaller leads to a lower tracking MSE and a more accurate trajectory estimation. In fact, a smaller imposes a more stringent tracking MSE constraint for resource allocation design and thus more power and spatial degrees of freedom are allocated for sensing. To provide more insights, we define “projection points” on the unknown trajectory for which E-UAV has the smallest 3D distance w.r.t. the GUs, respectively. Comparing Fig. 3 and Fig. 4, we observe a high tracking MSE around some projection points, such as and , where E-UAV changes directions, since the constant velocity model assumption for the EKF is less accurate in those points. Note that in Fig. 4, the posterior tracking MSE in some time slots is higher than while the predicted MSE is guaranteed to be smaller than . In fact, only limits the predicted tracking MSE for resource allocation design while the actual tracking MSE, which is not accessible to the I-UAV at the time of resource allocation design, might be much higher due to the state evolution model mismatch and the measurement uncertainty in (10). Furthermore, the average number of scheduled GUs versus is shown in the lower half of Fig. 4. The performance of a baseline separate jamming and sensing scheme, where a dedicated sub-slot is used for sensing and the remaining time is used for communications and jamming, is also illustrated for comparison. We can observe a higher number of scheduled GUs for the proposed scheme compared to the benchmark scheme. This is because the dual use of AN in the proposed scheme preserves the system resources and provides more flexibility for resource allocation design. This underlines the advantage of integrating sensing, jamming, and communications for improving secrecy performance. It can be further observed that both a small and a large result in a small number of securely served GUs for both schemes. For a small , more resources are needed for sensing, and thus, fewer GUs can be scheduled. This implies that enhancing the tracking performance is not always beneficial for communications as it requires more system resources. Increasing relaxes the tracking performance constraint C4 in (18) and thus results in a larger objective value. However, a too large in a given time slot leads to unreliable eavesdropper channel prediction in the next time slot, and thus, a lower jamming efficiency. Hence, the number of securely served GUs is ultimately limited by the channel prediction uncertainty in the large regime. In fact, choosing properly is critical for maximizing the secrecy communication performance. For example, for the considered scenario, is optimal for the proposed scheme.
6 Conclusions
In this paper, we proposed a novel ISJC framework and an online resource allocation design for securing UAV-enabled downlink communications. The dual use of AN enables the I-UAV to concurrently jam the E-UAV and sense the corresponding channels efficiently. Through simulations, we demonstrated that integrating sensing, jamming, and communications improves the secrecy performance, while choosing a suitable value for the tolerable tracking MSE is critical for balancing tracking and secrecy performance.
References
- [1] Qingqing Wu, Jie Xu, Yong Zeng, Derrick Wing Kwan Ng, Naofal Al-Dhahir, Robert Schober, and A. Lee Swindlehurst, “A comprehensive overview on 5G-and-Beyond networks with UAVs: From communications to sensing and intelligence,” IEEE J. Select. Areas Commun., vol. 39, no. 10, pp. 2912–2945, Oct. 2021.
- [2] Zhiqiang Wei, Yuanxin Cai, Zhuo Sun, Derrick Wing Kwan Ng, Jinhong Yuan, Mingyu Zhou, and Lixin Sun, “Sum-rate maximization for IRS-assisted UAV OFDMA communication systems,” IEEE Trans. Wireless Commun., vol. 20, no. 4, pp. 2530–2550, Apr. 2021.
- [3] Qingqing Wu, Weidong Mei, and Rui Zhang, “Safeguarding wireless network with UAVs: A physical layer security perspective,” IEEE Wireless Commun., vol. 26, no. 5, pp. 12–18, Oct. 2019.
- [4] Qian Wang, Zhi Chen, Weidong Mei, and Jun Fang, “Improving physical layer security using UAV-enabled mobile relaying,” IEEE Wireless Commun. Lett., vol. 6, no. 3, pp. 310–313, Jun. 2017.
- [5] Guangchi Zhang, Qingqing Wu, Miao Cui, and Rui Zhang, “Securing UAV communications via joint trajectory and power control,” IEEE Trans. Wireless Commun., vol. 18, no. 2, pp. 1376–1389, Feb. 2019.
- [6] Xiaobo Zhou, Qingqing Wu, Shihao Yan, Feng Shu, and Jun Li, “UAV-enabled secure communications: Joint trajectory and transmit power optimization,” IEEE Trans. Veh. Technol., vol. 68, no. 4, pp. 4069–4073, Apr. 2019.
- [7] Yuanxin Cai, Zhiqiang Wei, Ruide Li, Derrick Wing Kwan Ng, and Jinhong Yuan, “Joint trajectory and resource allocation design for energy-efficient secure UAV communication systems,” IEEE Trans. Commun., vol. 68, no. 7, pp. 4536–4553, Jul. 2020.
- [8] Miao Cui, Guangchi Zhang, Qingqing Wu, and Derrick Wing Kwan Ng, “Robust trajectory and transmit power design for secure UAV communications,” IEEE Trans. Veh. Technol., vol. 67, no. 9, pp. 9042–9046, Sep. 2018.
- [9] Zhongxiang Wei, Fan Liu, Christos Masouros, Nanchi Su, and Athina P Petropulu, “Towards multi-functional 6G wireless networks: Integrating sensing, communication and security,” arXiv preprint arXiv:2107.07735, 2021.
- [10] Nanchi Su, Fan Liu, Zhongxiang Wei, Ya-Feng Liu, and Christos Masouros, “Secure dual-functional radar-communication transmission: Exploiting interference for resilience against target eavesdropping,” arXiv preprint arXiv:2107.04747, 2021.
- [11] Nanchi Su, Fan Liu, and Christos Masouros, “Secure radar-communication systems with malicious targets: Integrating radar, communications and jamming functionalities,” IEEE Trans. Wireless Commun., vol. 20, no. 1, pp. 83–95, 2021.
- [12] Harry L Van Trees, Optimum Array Processing: Part IV of Detection, Estimation and Modulation Theory, John Wiley & Sons, 2004.
- [13] Yan Sun, Derrick Wing Kwan Ng, Jun Zhu, and Robert Schober, “Robust and secure resource allocation for full-duplex MISO multicarrier NOMA systems,” IEEE Trans. Commun., vol. 66, no. 9, pp. 4119–4137, Sep. 2018.
- [14] Merrill I Skolnik, Introduction to Radar, McGraw-hill New York, NY, USA, 1962.
- [15] Fan Liu, Weijie Yuan, Christos Masouros, and Jinhong Yuan, “Radar-assisted predictive beamforming for vehicular links: Communication served by sensing,” IEEE Trans. Wireless Commun., vol. 19, no. 11, pp. 7704–7719, Nov. 2020.
- [16] Steven M Kay, Fundamentals of Statistical Signal Processing: Estimation Theory, Prentice-Hall, Inc., 1993.
- [17] Brian DO Anderson and John B Moore, Optimal Filtering, Courier Corporation, 2012.
- [18] George Fishman, Monte Carlo: Concepts, Algorithms, and Applications, Springer Science & Business Media, 2013.
- [19] Zhiqiang Wei, Derrick Wing Kwan Ng, Jinhong Yuan, and Hui-Ming Wang, “Optimal resource allocation for power-efficient MC-NOMA with imperfect channel state information,” IEEE Trans. Commun., vol. 65, no. 9, pp. 3944–3961, Sep. 2017.
- [20] S Boyd and L Vandenberghe, Convex Optimization, Cambridge University Press, 2004.
- [21] Zhi-Quan Luo, Wing-Kin Ma, Anthony Man-Cho So, Yinyu Ye, and Shuzhong Zhang, “Semidefinite relaxation of quadratic optimization problems,” IEEE Signal Process. Mag., vol. 27, no. 3, pp. 20–34, May 2010.