Resilient Time-Varying Output Formation Tracking of Linear Multi-Agent Systems Against Unbounded FDI Sensor Attacks and Unreliable Digraphs
Abstract
One salient feature of cooperative formation tracking is its distributed nature that relies on localized control and information sharing over a sparse communication network. That is, a distributed control manner could be prone to malicious attacks and unreliable communication that deteriorate the formation tracking performance or even destabilize the whole multi-agent system. This paper studies a safe and reliable time-varying output formation tracking problem of linear multi-agent systems, where an attacker adversely injects any unbounded time-varying signals (false data injection (FDI) attacks), while an interruption of communication channels between the agents is caused by an unreliable network. Both characteristics improve the practical relevance of the problem to be addressed, which poses some technical challenges to the distributed algorithm design and stability analysis. To mitigate the adverse effect, a novel resilient distributed control architecture is established to guarantee time-varying output formation tracking exponentially. The key features of the proposed framework are threefold: 1) an observer-based identifier is integrated to compensate for adverse effects; 2) a reliable distributed algorithm is proposed to deal with time-varying topologies caused by unreliable communication; and 3) in contrast to the existing remedies that deal with attacks as bounded disturbances/faults with known knowledge, we propose resilience strategies to handle unknown and unbounded attacks for exponential convergence of dynamic formation tracking errors, whereas most of existing results achieve uniformly ultimately boundedness (UUB) results. Numerical simulations are given to show the effectiveness of the proposed design.
Index Terms:
Dynamic output formation tracking, Heterogeneous linear multi-agent system, Unbounded attacks, Unreliable digraphs, Resilient distributed control, Global exponential convergence.I Introduction
Formation control of the multi-agent system has attracted considerable attention in recent years due to its potential applications such as cooperative localization [1], surveillance [2] and moving target enclosing [3]. The main objective of formation control is to present distributed control protocols via neighboring interactions such that the states of all agents can form a desired configuration. In addition to time-invariant formation control, the formation of a team of agents in many practical applications (target enclosing or source seeking) often changes, and is required to track a desired reference. Thus, a time-varying formation tracking problem arises where the agent team can maintain a time-varying formation and meanwhile, track a reference. Based on neighboring interactions, time-varying formation tracking is investigated for homogeneous multi-agent systems with single-/double-integrator [1], high-order linear [5, 4] and nonholonomic [3] dynamics. In practice, each agent has different dynamics and dimensions. That is, the exiting approaches in [1, 2, 3, 5, 4] cannot be directly applied for heterogeneous systems. Recently, formation tracking of heterogeneous systems is studied in [7, 8, 6] via an output regulation scheme.
Notice that all aforementioned works relied on the availability of the local healthy sensors of each agent of the team associated with a reliable communication network. However, the multi-agent systems involving the communication and collaboration between connected agents, are prone to malicious cyber-attacks such as the DoS attacks, deception attacks (FDI attacks or replay attacks), and disclosure attacks [9, 10, 11, 13, 12, 14, 16, 15]. In this paper, we focus on these FDI attacks on the sensors by injecting any false signals to manipulate sensor measurements. Moreover, each agent can communicate via an unreliable network. Note that both characteristics may severely affect the performance of the system, prohibit the accomplishment of system-level objectives, and even destabilize the whole multi-agent system. In light of a wide application of distributed control schemes in a cyber-physical system (safety-critical), and inspired by the studies of security issues in many existing works [9, 10, 11, 13, 12, 14, 16, 15], it is desirable to see if the distributed formation tracking algorithm can provide certain resilience against FDI attacks over unreliable communication. Hence, the objective of this paper is to address a safe and reliable time-varying output formation tracking problem of heterogeneous linear multi-agents to provide certain resilience against unbounded FDI attacks and unreliable communication. So far, this problem is still open, and to the best of our knowledge, few efforts are made on this issue.
This paper investigates resilient time-varying output formation tracking problems of heterogeneous linear multi-agent system in the presence of unbounded FDI attacks and unreliable networks. The resilient distributed estimator-based control algorithms without requiring any attack information, are proposed to deal with the problem over directed topologies caused by unreliable communications. The previous works in [13, 12, 14, 15] studied secure consensus only for homogeneous multi-agent system under DoS attacks. The designs in [9, 10, 11] and [18, 19, 17, 20, 21] to deal with the sensor/actuator attacks or faults highly depended on some assumptions that those attacks or faults either satisfy some special structures or are upper bounded with known knowledge. Those aforementioned works do not consider malicious FDI attacks that are rational, unknown and unbounded. As compared to those works, the main contributions of this paper can be summarized as follows.
-
•
A resilient distributed estimator-based control framework is developed for heterogeneous linear multi-agent systems with sensor attacks and unreliable digraphs. A reliable distributed leader estimator is firstly proposed to reconstruct the leader’s state for each agent over unreliable communication. Further, a novel resilient distributed output feedback control algorithm is designed to achieve global exponential convergence of the proposed algorithm such that the output of each follower can not only maintain the prescribed time-varying formation, but also track the output of the leader’s trajectory.
-
•
In contrast to works in [9, 10, 11] in which resilient function calculation and consensus were investigated under the constraints on the number of malicious agents or certain special structure attacks, those requirements are not required in this work. Instead, we only suppose that information interaction over the unreliable communication is allowed to be switching between a graph set containing a directed spanning tree and a paralyzed graph set (in Assumption 1), which is less mild than the fixed undirected or directed graphs in [5, 4, 7, 8, 6, 9, 10, 11].
-
•
Compared with existing works in [18, 19, 17, 20, 21] to handle attacks or faults as disturbances that have to be bounded with a prior knowledge, the malicious FDI sensor attacks in this work are intelligent, unknown and unbounded, which are practical and reasonable. The proposed scheme does not require any attack information. Moreover, a global exponential convergence can be achieved under attacks, while only the uniformly ultimate boundedness (UUB) result is obtained in [19, 20, 21].
-
•
The novel resilient distributed output feedback control architecture enables the global exponential stability of the system for time-varying output containment-formation tracking with multiple leaders. Local sufficient conditions and design procedures are presented via the Lyapunov analysis.
The rest of this paper is organized below. The preliminaries and problem formulation are provided in Section II. The resilient time-varying output formation tracking results are proposed in Section III with the global exponential convergence analysis. The design is further extended for resilient time-varying output containment-formation tracking with multiple leaders in Section IV. Examples and numerical simulation results are given in Section V, followed by the conclusion in Section VI.
II Preliminaries and Problem Formulation
II-A Mathematical Preliminaries
Notation: let , and be the sets of the real numbers, real -dimensional vectors and real matrices, respectively. Let be the set of all positive real numbers and denote the set of all positive natural numbers. Let 0 (1) be the vector with all zeros (ones) with proper dimensions, respectively. Denote col and diag as a column vector with all entries and a diagonal matrix with all entries , , respectively. and are the Kronecker product and Euclidean norm, respectively. Given a real matrix , let be positive definite. Let , be its minimum and maximum eigenvalues, respectively. Besides, represents the maximum singular value of a matrix .
Graph Theory: Let be a graph and be the set of vertices. The set of edges is denoted as . is the neighborhood set of vertex . For a directed graph , means that the information of node is accessible to node , but not conversely. The matrix denotes the adjacency matrix of , where if , else . The matrix is called the Laplacian matrix of , where and , . The digraph is said to contain a spanning tree if there exists a node from which there are directed paths to all other nodes. For a general directed graph, is not necessarily symmetric. Let be a directed graph of a leader-follower network, where , , and the node is associated with the leader. Then, is the neighbor set of node . Clearly, is a subgraph of , where is obtained from by removing all the edges between the node and the nodes in . Define the Laplacian matrix of as , where is a diagonal matrix with its -th diagonal element being , (, if , and , otherwise), and is an information exchange matrix.
Lemma 1
[25] Suppose that the graph contains a directed spanning tree with the leader as the root, then is a non-singular and positive definite matrix. Further, there exists a diagonal matrix such that is symmetric and positive definite, where .
II-B Heterogeneous Linear Multi-Agent Systems
Consider a multi-agent system consisting of followers governed by the following heterogeneous linear dynamics:
| (1) |
where denotes the state of agent , denotes the control input to agent , is its output, and , , are constant system matrices.
The dynamics of the leader are described by
| (2) |
where is the leader’s state, is its measurable output, and are constant matrices.
For this leader-follower system, suppose that the pair is stabilizable and is detectable. Moreover, the following linear matrix equation has a solution for each agent
| (3) |
To specify the desired time-varying output formation tracking, a time-varying vector is introduced, where each is generated by
| (4) |
and the pair satisfies
| (5) |
Remark 1
As compared to homogeneous multi-agent systems with identical dynamics and/or time-invariant formation in [1, 2, 3, 5, 4], it can be seen from (1)-(4) that the linear dynamics of each agent can be heterogeneous in the aspects of both parameters and dimensions, and the desired formation is time-varying. In an output formation tracking of multi-robot systems, the position is usually required to form the desired formation, while its velocity and orientation do not need to keep a strict formation. Then, the output of each robot can be the position only.
Remark 2
The linear matrix equation (3) is regarded as the regulated equation that has been widely studied in many existing output regulation literature (e.g., see [22, 23, 24]). Similarly, a new format of time-varying output formation shape is considered in (4) that satisfies the matrix equation (5) to facilitate the subsequently control development and system convergence analysis. It is noted that does not require to be detectable, and when is designed, is the solution of (5).
II-C Unreliable Communication Network
In a large-scale cyber-physical system, the wireless communication may not be always reliable due to the physical uncertainties such as failures, quantization errors, and packet losses in a digital communication. Hence, we study an unreliable network where all agents’ communication links are time-varying and switching. Let represent a piecewise constant switching signal used to describe the switching among topologies and indicates its cardinality. Suppose that there exists a sequence with for a dwell time and so that during , for and this graph is time-invariant [12].
Suppose that is divided into two subsets and , i.e., , where is used to index the set of graphs that contain a directed spanning tree with the leader being the root, while indexes the set of graphs that are allowed to be disconnected. Then, we denote and as the total activation time when and , respectively, during , [12].
Assumption 1
The topologies contain a directed spanning tree with the leader being the root, while are allowed to be disconnected. There exist positive constants and such that for .
Remark 3
Assumption 1 implies that there are certain topologies that do not contain any directed spanning trees or even can be paralyzed under unreliable communication networks, which is mild in practice. In order to guarantee the information sharing, it supposes that a proportion of communication can work normally for an information exchange among agents.
II-D Malicious FDI Attack Model
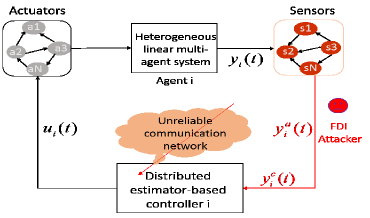
In this part, we describe the model of unknown and unbounded FDI attacks on the sensors of agents as shown in Fig. 1.
Definition 1
(FDI Sensor Attacks) This attack refers at time , an adversary injects any time-varying signals into the measurement channel and thereby, modifying into adversely with a mapping , i.e.,
| (6) |
where denotes the nominal output measurement in (1), represents the disrupted signal that is injected into the sensors of agent and denotes the corrupted measurements of agent . If agent is under attacks, , otherwise, .
Assumption 2
The FDI attack signals are unknown and unbounded, while their time derivatives are assumed to be upper bounded but with certain unknown constants.
Remark 4
The adversary’s injections can be unbounded time-varying signals, which aim to manipulate or even destabilize the whole agent team’s behaviors. The slow-varying signals may not be easily detected. Hence, this assumption is more practical and reasonable in real-world applications.
II-E Main Objective
This work aims to achieve the resilient time-varying output formation tracking of linear multi-agent systems under FDI attacks and unreliable digraphs. We will develop a distributed estimator-based controller with corrupted individual output information and neighbor-based group output information. The control of agent is supposed to have the structure as depicted in Fig. 1. In the next section, we will specify the design procedure.
Problem 1
(Resilient Time-Varying Output Formation Tracking) Consider a leader-follower agent network consisting of (1)-(2). This multi-agent system is subject to malicious FDI attacks in (6) and communicates over unreliable digraphs . Design a resilient distributed algorithm so that all agents achieve safe and reliable time-varying output formation tracking exponentially, i.e.,
| (7) |
Remark 5
In contrast to many related existing works, solving Problem 1 is more challenging at least from the following aspects: 1) Adverse effects: as illustrated in Fig. 1, the unknown malicious FDI attackers can inject and manipulate the measured sensor data to destabilize the whole multi-agent network. Since the output of each agent is under FDI sensor attacks, only the uncompromised measurements will be available for a resilient distributed design; 2) Communication network: the unreliable communication makes topologies frequently switching rather than the fixed undirected or directed graphs in [5, 4, 7, 8, 6]. The underlying Laplacian matrices of each digraph are not necessarily positive definite; (3) Output time-varying formation tracking: many formation tracking algorithms in the existing works (e.g., [5, 4, 7, 8, 6]) require the full states of either the homogeneous or heterogeneous leader-follower system, which may not be available in practice. On the contrary, we adopt each agent’s corrupted outputs to develop a distributed observer-based controller; and (4) Design requirement: propose a novel resilient algorithm to deal with the adverse impacts of FDI attacks and unreliable communication. Due to the aforementioned aspects, the existing designs in [5, 4, 7, 8, 6] cannot be directly applied. A resilient distributed control framework is shown in Fig. 2.
III Exponential Distributed Stabilization for Resilient Time-Varying Output Formation Tracking
In this section, we will design a resilient distributed mechanism with an estimator-based control framework. To begin with, a distributed leader estimator is given to estimate and reconstruct the leader’s state for each follower over an unreliable communication network. Then, a resilient distributed output feedback controller is proposed to achieve time-varying output formation tracking. The procedure is given to design the estimator and controller gains.
III-A Reliable Distributed Leader Estimator Design
Denote an estimated state named as to estimate the leader’s state . Then, a consensus tracking error is defined as
| (8) |
In light of (8), a reliable distributed leader estimator using only output information is designed with a constant gain matrix ,
| (9) |
Denote the tracking error and its collective form is given by . Then, combing (8) and (9) gives rise to the following closed-loop error system
| (10) |
Next, the following lemma is provided to establish a symmetric and positive definite matrix for directed graphs.
Lemma 2
Under Assumption 1, there exist positive definite diagonal matrices for each , so that .
Proof:
For notational convenience, denote
| (11) |
where , are defined in Lemma 2, and further, let
| (12) |
where denotes the average of , , and moreover, it is not difficult to derive , .
Theorem 1
Suppose that Assumption 1 holds. If the distributed leader estimator is designed as (9) with , , then all the estimated states of the distributed estimator can globally exponentially converge to the leader’s state, provided that the scalars and satisfy
| (13) |
where , , , , and are the solutions of an optimization problem:
| (14) |
| (15) |
where and are symmetric positive definite matrices.
Proof:
we construct the following piecewise Lyapunov functional candidate for the closed-loop error system in (10) as
| (16) |
Next, the proof includes the following steps:
Step (i). we consider the case with . Taking the time derivative of (16) along (10) with yields
| (17) | ||||
Step (ii). consider the case with . Similarly, the time derivative of (16) along (10) with the fact that yields
| (19) |
Step (iii). synthesizing Steps (i)-(ii) into one, it is obtained from (18) and (19) that for any , we can have
| (20) |
Since , it further has for any ,
| (21) |
Suppose that there is no jump in the state at the switching instant, i.e., . Further, using (16) gives rise to
| (22) |
III-B Resilient Distributed Control against FDI Sensor Attacks
In this subsection, we propose a novel resilient mechanism to achieve exponential output formation tracking in the presence of FDI sensor attacks in (6). Under sensor attacks, the output is corrupted and only the corrupted can be measured. To deal with these FDI sensor attacks, a novel resilient distributed output feedback controller is developed as
| (27) | ||||
| (28) |
where are controller and observer gain matrices to be determined later, represents the observed state of the observer, is the estimate of the leader’s state designed in (8) and (9), is the time-varying formation vector defined in (4), and denotes the measurable error term described by
| (29) |
where is an estimation of the uncorrupted output measurement , and is an estimation of unknown sensor attacks , which is updated through the following design:
| (30) |
where is a gain matrix with appropriate dimensions and denotes a compensation signal to be determined later.
Next, we denote two estimated errors:
| (31) |
To achieve the main objective of this paper, we need to analyze the global exponential convergence of and . Denote as an augmented error variable. Further, it follows from (32)-(33) that we can derive the following closed-loop error system described by
| (34) |
| (35) |
Before presenting the convergence of , the following assumption is made to facilitate stability analysis.
Assumption 3
The pair is observable.
Proposition 1
Proof:
according to (35), we can obtain that
Then, it is observed that the matrix pair is observable if and only if , which is equivalent to the following expression
| (37) |
where the second equation is guaranteed according to the Cayley-Hamilton theorem with and .
Based on Assumption 3, we have
| (38) |
Thus, and can be chosen such that is Hurwitz. That is, (36) is obtained, and the proof is completed. ∎
Next, we present the global exponential convergence of in the closed-loop error system (34).
Proposition 2
Suppose that Assumptions 1-3 hold. For leader -follower multi-agent systems in (1)-(4) subject to sensor attacks in (6), the global exponential convergence of and can be guaranteed under the proposed resilient distributed controller in (27)-(30), provided that is designed as
| (39) |
where is to be determined later, denotes the estimate of , is the th element of , and is an integrable function such that for certain scalar , i.e., with a scalar .
Proof:
Consider the following Lyapunov functional candidate
| (40) |
where can be selected such that in (36) holds with , , and denotes the estimated error.
Then, the time derivative of along the trajectories of the closed-loop error system (34) is described by
| (41) |
Let represent the th element of the vector . Since , we have
| (42) |
Next, we are ready to present the resilient time-varying output formation tracking result, which is summarized below.
Theorem 2
Consider the heterogeneous leader-follower multi -agent system (1)-(4) subject to FDI sensor attacks and unreliable digraphs. Suppose that Assumptions 1-3 hold. Under the proposed resilient algorithm in (27)-(30), the time-varying output formation tracking can be achieved exponentially, provided that the observer gain matrices , are selected such that in (35) is Hurwitz, the controller gain matrix is chosen such that is Hurwitz, and are designed as
| (44) |
where and are the solution of the well-known regulated equations in (3) and (5), respectively.
Proof:
define a formation transformation coordinate as
| (45) |
Then, the time derivative of is described as
| (46) |
It follows from Theorem 1 that exponentially converges to zero and from Proposition 2 that exponentially converges to zero. Moreover, is selected so that is Hurwitz. Thus, it is concluded from (48) that can converge to zero exponentially, i.e., exponentially.
Denote the time-varying output formation tracking error as
| (49) |
Due to the fact that and , then we can have . Since exponentially, it is concluded that exponentially. Hence, the global exponential time-varying output formation tracking is achieved for the heterogeneous linear multi-agent systems in the presence of FDI sensor attacks and unreliable digraphs. ∎
IV Resilient Time-Varying Formation-Containment Tracking with Multiple Leaders
Consider a linear multi-agent network consisted of followers and leaders with their dynamics described by
| (50) |
where and are the sets of the followers and leaders, respectively, and and are the state and output of the th leader, respectively.
In the networked agent team, the leaders do not have incoming edges and the followers have the relative neighboring information. The well-informed and unwell-informed followers are defined.
Definition 2
[5] A follower is called the well-informed one if it has incoming edges from all leaders, and the uniformed follower if it has no incoming edges from any leaders.
Definition 3
[28] A set can be said to be convex if holds for any and . Then, the convex hull of a finite set of points is the minimal convex set containing all points in , i.e., . That is, is the convex combination of .
Problem 2
The multi-agent system (50) subject to unreliable digraphs and unknown and unbounded sensor attacks in (6) is said to achieve resilient time-varying formation-containment tracking if there exist a scalar , that satisfies such that for any initial states, the closed-loop system is globally stable and the output formation-containment tracking satisfies
| (51) |
Similar to Assumption 1, we make another assumption.
Assumption 4
For each uninformed follower in , there exists at least one well-informed follower that has a directed path to it, while are allowed to be disconnected. There exist scalars , so that for all .
Remark 6
Remark 7
As compared to the existing works, solving Problem 2 is much more challenging at least from threefold. Firstly, the linear multi-agent system with multiple leaders has different dynamics and system dimensions. Secondly, unlike many existing works requiring the prefect communication network, the digraphs caused by unreliable communication are allowed to be disconnected in Assumption 4. Thirdly, the presence of unknown and unbounded sensor attacks leads to the fact that only corrupted output measurements are available for distributed designs.
Similar to Section III, we propose a novel distributed estimator-based control architecture to solve Problem 2.
Reliable Distributed Leader Estimator Design: propose a novel reliable distributed leader estimator for each follower using the output information only, which is described by
| (52) |
where denotes an estimated containment tracking error as
| (53) |
Denote , where represents the information exchange matrix with and , . Then, combing (52) and (53) yields the following error system
| (54) |
Next, the following lemmas are provided to establish symmetric and positive definite matrices for directed topologies.
Lemma 3
and are positive define for by Assumption 4.
Lemma 4
There exist some positive definite diagonal matrices so that for , where .
Theorem 3
Suppose that Assumption 4 holds. If the distributed leader estimator is designed as (52) with , , then the estimated states globally exponentially converge to the convex combination of the leaders’ states, provided that the scalars and satisfy
| (57) |
where , , , , and are solutions of minimizing subject to and , where and are symmetric positive definite.
Proof:
the proof is similar to Theorem 1, and is omitted. ∎
Remark 8
Next, we are ready to present the resilient time-varying output containment-formation tracking result as follows.
Theorem 4
Consider the heterogeneous leader-follower multi -agent system in (50) subject to unreliable digraphs and unknown and unbounded FDI sensor attacks. Suppose that Assumptions 2-4 hold. Under a resilient distributed output feedback controller
| (58) |
where and are developed in (28) and (52), respectively, then, the time-varying output containment-formation tracking can be achieved, provided that the gain matrices , are selected so that in (35) is Hurwitz, is chosen so that is Hurwitz, and are given in (44).
Proof:
denote a containment-formation tracking error as
| (59) |
Similar to (46)-(49), we can have . Then, from Theorem 3 and Proposition 2, can be chosen so that converges to zero exponentially. The time-varying output containment-formation tracking error is
| (60) | ||||
where is the convex combination of .
Due to the fact that and , then we can obtain . Since exponentially, exponentially. Hence, the global exponential time-varying output containment-formation tracking is achieved for multi-agent follower-leader systems under FDI sensor attacks and unreliable communication digraphs. ∎
V Numerical Simulation
In this section, the simulation results are presented to show the effectiveness of the proposed resilient distributed algorithms for heterogeneous linear multi-agent systems.
V-A System description
Consider a multi-agent system consisting of six agents with the following heterogeneous linear dynamics
| (61) |
| (62) |
where the nonidentical parameters are chosen as , , , , , and , respectively. In addition, the leader dynamics are described by
| (63) |
Based on (61)-(63), it is not hard to verify that the pair is stabilizable and is detectable. Moreover, Assumption 3 is satisfied. The solution to the regulated equation in (3) is
Next, the time-varying output formation shape is described by , which yields the studied system in (4) with
| (64) |
Let . Then, the solution to the matrix equation in (5) is
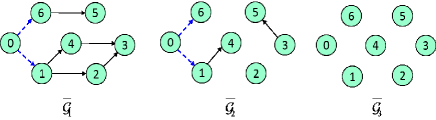
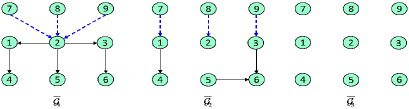
The unreliable directed communication topologies between the leader and the six followers are shown in Fig. 3, where only has a directed spanning tree. It can be verified that Assumption 1 is satisfied. Besides, the linear multi-agent system suffers from unknown and unbounded FDI sensor attacks, i.e., Next, the control objective is to achieve resilient time-varying output formation tracking for multi-agent systems under FDI sensor attacks and unreliable digraphs.
V-B Algorithm design and result
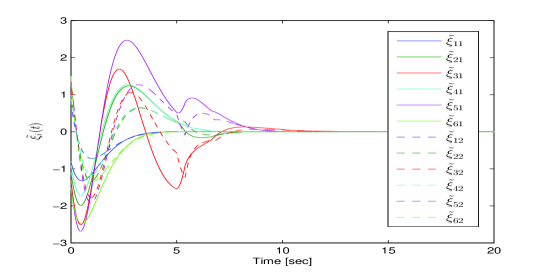
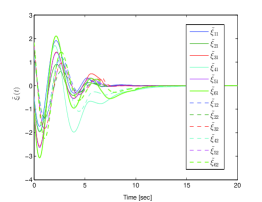
The proposed distributed leader estimator in (9) is performed under unreliable digraphs. We select the leader’s initial states as , and the initial estimated states as . Based on certain calculations, one has that , , . Further, the estimator gain matrix can be designed as by solving this optimization problem in (14)-(15), given and . The parameters , and are selected to satisfy (13) in Theorem 1. Then, the proposed reliable distributed leader estimator in (9) is performed, and the simulation result is depicted in Fig. 5. As can be observed, the leader’s state can be estimated for each follower exponentially.
The proposed resilient distributed control algorithms are performed against unbounded sensor attacks and unreliable digraphs.
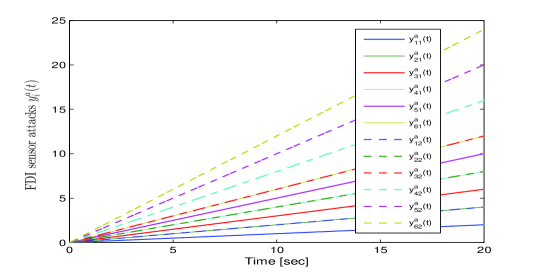
Case 1: Resilient Output Formation Tracking with FDI Sensor Attacks and Unreliable Digraphs
In this part, these FDI sensor attacks are modeled by shown in Fig. 4. As can be seen, Assumption 2 is verified. According to Theorem 2, the controller gain matrices are: , , , , , ; , , , , , ; and , , , , , . By Proposition 1, the observer gain matrices are: , , , , , ; and , , , . The initial states and are randomly specified.
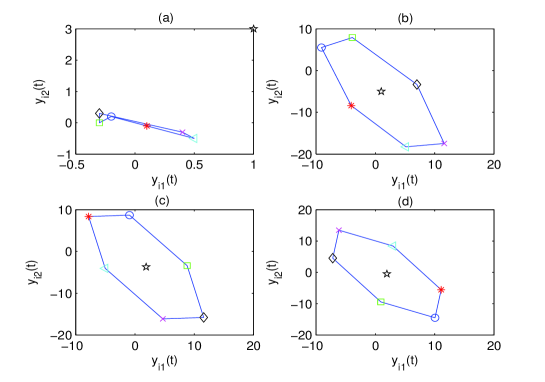
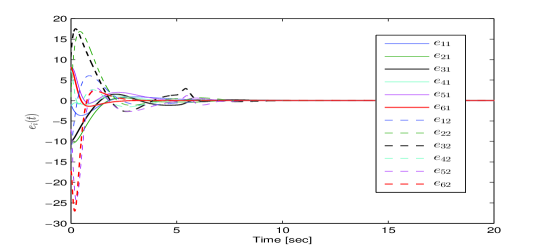
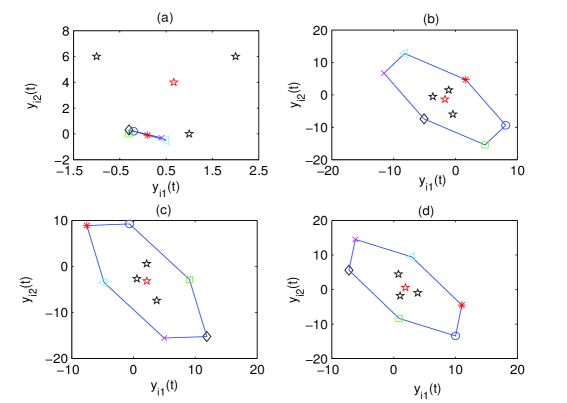
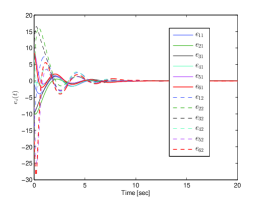
Next, the proposed resilient algorithm in (27)-(30) with (39) is performed, and the simulation results are shown in Figs. 5-7. Fig. 5 shows the leader-follower estimated error under unreliable digraphs. The output trajectories of all agents are shown in Fig. 6 for four different instants (t=0s, 8s, 15s, 20s). It can be seen in the presence of the FDI sensor attacks and unreliable communication, the six followers can rotate around the leader (black pentagram) that locates in the center of the time-varying formation. Moreover, Fig. 7 depicts the trajectories of output formation tracking errors . From those figures, it is concluded that the time-varying output formation can be achieved under the FDI attacks and unreliable digraphs.
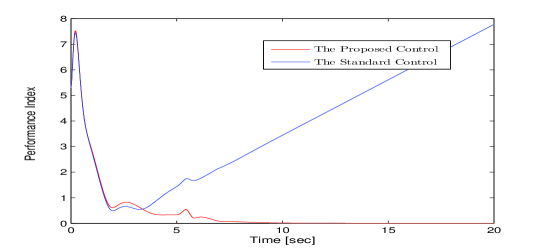
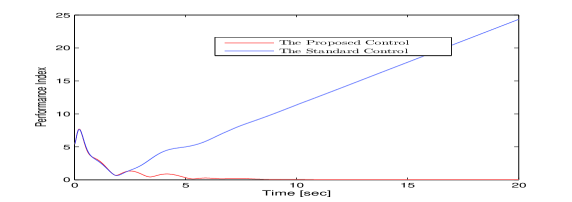
To show the resilient performance of the proposed algorithm, we compare our approach with the standard method, i.e., (27)-(30) without in (30) and in (39). The performance index is: , which is the average tracking error. The performance comparisons between the standard and the proposed resilient approaches are presented as depicted in Fig. 8. As can be observed, the proposed control method enables the zero-error tracking resilience against sensor attacks and unreliable digraphs, while the tracking error diverges under the standard method.
Case 2: Resilient Output Containment-Formation Tracking with FDI Sensor Attacks and Unreliable Digraphs
The dynamics of the three leaders are described by , , where , are the state and output of the th leader, respectively. We select these three leaders’ initial states as , , . These unbounded FDI sensor attacks and the initial estimated states are given the same as those in Case 1. The unreliable digraphs between the leaders and the followers are provided in Fig. 9. The simulation results are depicted in Figs. 10-11. The state snapshots of three leaders, six followers and the convex combination of leaders are depicted in Fig. 10 for four different instants (t=0s, t=8s, t=15s and t=20s). It can be observed that 1) the states of the six followers can form a parallel hexagon, while rotating around the states of the three leaders; and 2) the states of these three leaders are time-varying and their convex combination can lie in the center of the parallel hexagon. That is, the desired time-varying output containment-formation tracking with multiple leaders has been achieved under FDI sensor attacks and unreliable digraphs. Fig. 11(a)-(c) shows the simulated results for , , and performance comparison, respectively.
VI Conclusion
In this paper, we investigated the resilient time-varying output formation tracking problem of a heterogeneous linear multi-agent system under the unknown and unbounded FDI sensor attacks and unreliable digraphs. The new resilient distributed estimator-based control algorithms have been proposed to guarantee time-varying output formation tracking. Then, the proposed distributed design is extended to achieve time-varying output containment-formation tracking in the presence of FDI attacks and unreliable digraphs.
References
- [1] Z. Han, K. Guo, L. Xie, Z. Lin, “Integrated relative localization and leader-follower formation control,” Automatica, 64(1): 20–34, 2019.
- [2] S. Du, X. Sun, M. Cao, W. Wang, “Pursuing an evader through cooperative relaying in agent surveillance networks,” Automatica, 83(9): 155–161, 2017.
- [3] R. Zheng, Y. Liu, D. Sun, “Enclosing a target by nonholonomic mobile robots with bearing-only measurements,” Automatica, 53: 400–407, 2015.
- [4] X. Dong, G. Hu, “Time-varying formation control for general linear multi-agent systems with switching directed topologies,” Automatica, 73(1): 47–55, 2016.
- [5] X. Dong, G. Hu, “Time-varying formation tracking for linear multi-agent systems with multiple leaders,” IEEE Trans. Autom. Control, 62(2): 3658–3664, 2017.
- [6] Y. Hua, X. Dong, G. Hu, Q. Li, Z. Ren, “Distributed time-varying output formation tracking for heterogeneous linear multi-agent systems with a nonautonomous leader of unknown input,” IEEE Trans. Autom. Control, 62(10): 4292–4299, 2019.
- [7] W. Jiang, G. Wen, Z. Peng, T. Huang, A. Rahmani, “Fully distributed formation-containment control of heterogeneous linear multi-agent systems,” IEEE Trans. Autom. Control, 64(9): 3889–3896, 2019.
- [8] Y. Wang, X. Liu, J. Xiao, Y. Shen, “Output formation-containment of interacted heterogeneous linear systems by distributed hybrid active control,” Automatica, 93(1): 26–32, 2018.
- [9] S. Sundaram, C. N. Hadjicostis, “Distributed function calculation via linear iterative strategies in the presence of malicious agents,” IEEE Trans. on Automatic Control, 56(7), 1495–1508, 2011.
- [10] F. Pasqualetti, A. Bicchi, F. Bullo, “Consensus computation in unreliable networks: a system theoretic approach,” IEEE Trans. on Automatic Control, 57(1), 90–104, 2012.
- [11] T. Yucelen, W. M. Haddad, E. M. Feron, “Adaptive control architectures for mitigating sensor attacks in cyber-physical systems,” in IEEE. American control conference, pp. 1165-–1170, 2016.
- [12] Z. Feng, G. Hu, G. Wen, “Distributed consensus tracking for multi-agent systems under two types of attacks,” Int. J. Robust. Nonlinear Control, 26(5) : 896–918, 2015.
- [13] Z. Feng, G. Wen, G. Hu, “Distributed secure control for multi-agent systems under strategic attacks,” IEEE Trans. Cybern., 47(5): 1273–1284, 2017.
- [14] Z. Feng, G. Hu, “Secure cooperative event-triggered control of linear multi-agent systems under DoS attacks,” IEEE Trans. Contr. Syst. Tech., 28(3): 741–752 2020.
- [15] D. Zhang, L. Liu, G. Feng, “Consensus of heterogeneous linear multi-agent systems subject to aperiodic sampled-data and DoS attack,” IEEE Trans. Cybern., 49(4): 1501–1511, 2019.
- [16] B. Chen, D. W. Ho, G. Hu, L. Yu, “Secure fusion estimation for bandwidth constrained cyber-physical systems under replay attacks,” IEEE Trans. Cybern., 48(6): 1862–1876, 2018.
- [17] C. Deng, W. Che, P. Shi, “Cooperative fault-tolerant output regulation for multi-agent systems by distributed learning control approach,” IEEE Trans. Neural Netw. Learn. Syst., 31(11): 4831–4841, 2020.
- [18] Z. Feng, G. Hu, “Connectivity-preserving flocking for networked Lagrange systems with time-varying actuator faults,” Automatica, 109(1): 1–10, 2019.
- [19] C. Chen, F. L. Lewis, S. Xie, H. Modares, Z. Liu, S. Zuo, “Resilient adaptive and controls of multi-agent systems under sensor and actuator faults,” Automatica, 102: 19–26, 2019.
- [20] H. Modares, B. Kiumarsi, F. L. Lewis, F. Ferrese, A. Davoudi, “Resilient and robust synchronization of multi-agent systems under attacks on sensors and actuators,” IEEE Trans. Cybern., 47(7): 1706–1718, 2020.
- [21] S. Zuo, F. L. Lewis, A. Davoudi, “Resilient output containment of heterogeneous cooperative and adversarial multi-group systems,” IEEE Trans. Autom. Control, 65(7): 3104–3111, 2020.
- [22] Y. Su, J. Huang, “Cooperative output regulation of linear multi-agent systems,” IEEE Trans. Autom. Control, 57(4): 1062–1066, 2012.
- [23] Z. Li, M. Chen, Z. Ding, “Distributed adaptive controllers for cooperative output regulation of heterogeneous agents over directed graphs” Automatica, 68(1): 179–183, 2016.
- [24] H. Cai, F. L. Lewis, G. Hu, J. Huang, “The adaptive distributed observer approach to the cooperative output regulation of linear multi-agent systems,” Automatica, 75(1): 299-–305, 2017.
- [25] Z. Feng, G. Hu, W. Ren, W. E. Dixon, J. Mei, “Distributed coordination of multiple Euler-Lagrange systems,” IEEE Trans. Control Netw. Syst., 5(1): 55–66, 2018.
- [26] Z. Li, Z. Duan. Cooperative control of multi-agent systems: a consensus region approach. CRC Press, 2014.
- [27] F. L. Lewis, D. M. Dawson, C. T. Abdallah. Robot manipulator control: theory and practice. CRC Press, 2003.
- [28] R. T. Rockafellar. Convex analysis. Princeton Press, NJ, USA, 2015.