hidelinks
Reputation-Driven Asynchronous Federated Learning for Enhanced Trajectory Prediction with Blockchain
Abstract
Federated learning combined with blockchain empowers secure data sharing in autonomous driving applications. Nevertheless, with the increasing granularity and complexity of vehicle-generated data, the lack of data quality audits raises concerns about multi-party mistrust in trajectory prediction tasks. In response, this paper proposes an asynchronous federated learning data sharing method based on an interpretable reputation quantization mechanism utilizing graph neural network tools. Data providers share data structures under differential privacy constraints to ensure security while reducing redundant data. We implement deep reinforcement learning to categorize vehicles by reputation level, which optimizes the aggregation efficiency of federated learning. Experimental results demonstrate that the proposed data sharing scheme not only reinforces the security of the trajectory prediction task but also enhances prediction accuracy.
Index Terms:
Trajectory prediction, data sharing, graph convolutional network, asynchronous federated learning, differential privacy, deep reinforcement learning.I Introduction
The rapid advancements in emerging computational and communication technologies within the 5G network have revolutionized the operational paradigms of modern vehicular services and applications, thereby enhancing the overall driving experience[1]. Autonomous vehicles represent intricate systems that amalgamate various technologies, including perception algorithms[2], path planning[3], control theory[4], and vehicle positioning[5]. Among the crucial research domains in autonomous vehicles, trajectory prediction[6] stands out as it plays an essential role in the decision-making processes of intelligent vehicles. A precise and dependable vehicle trajectory prediction algorithm holds the capability to anticipate potential traffic accidents, thus safeguarding overall vehicular safety by enabling timely preventive measures.
Currently, trajectory prediction in the context of autonomous vehicles is mainly driven by neural network approaches. Recurrent neural networks (RNNs) are leading the way. Researchers have made extensive efforts to develop vehicle trajectory prediction models based on historical trajectory data and environmental information. For instance, GRIP[7] optimizes convolutional layers with graph operations, treating the driving scenario as a graph model. In this way, the interactions between the vehicles are represented as the interrelationships between the nodes of this graph model. The method[8] introduces a novel framework based on spectral clustering, enabling simultaneous prediction of vehicle trajectories and driving behavior. While these studies yield promising results, we must recognize that trajectory prediction faces significant challenges in the real world, especially in traditional telematics environments. In these cases, owners of trajectory data face a vexing problem of data silos. This issue emphasizes the necessity for creative solutions, and federated learning (FL) is a promising method for addressing it.
FL presents a viable strategy for preserving data privacy in distributed settings[9]. It achieves edge intelligence by imparting knowledge gleaned from decentralized data sources while upholding stringent privacy standards. Moreover, when coupled with the inherent features of blockchain technology[10], such as tamper resistance, anonymity, and traceability, it establishes a robust foundation for efficient and reliable data sharing among participants. Even in situations where trust among participants is limited, users are required to transmit model parameters to a central server for aggregation. This not only facilitates parallel learning to enhance the global model but also ensures data integrity, maintains anonymity, and provides traceability. Nonetheless, as autonomous driving continues to advance rapidly and the data generated by vehicles becomes increasingly complex, the task of trajectory prediction still confronts several pressing challenges that require resolution:
-
1.
Lack of complete trust in multiple parties. Many current data sharing schemes with central administrators pose an increased risk of data leakage. Administrators must manage large volumes of aggregated data from multiple parties, including unknown or raw sources.
-
2.
Uncertainty in participant data quality. Due to vehicle mobility and unreliable communications, the data sharing environment is highly fluid, with new unverified data being created constantly. When data providers share malicious or redundant data, it can significantly bias the entire prediction process.
-
3.
Extensive prediction delays. In the context of updating dynamic vehicle data, addressing aggregation challenges caused by delays in heterogeneous vehicle data is crucial. The conventional approach, which relies solely on federated learning-enabled blockchain technology, requires coordination among Roadside Units (RSUs) at each timestamp before uniformly uploading data for global aggregation.
To systemically address these limitations, we introduce a novel trajectory prediction approach RAFLTP based on graph neural networks to address the aforementioned challenges. We design an asynchronous FL strategy based on reputation evaluation to quantify vehicle reputation through interactions between vehicles. Furthermore, data providers release data structures under the constraints of differential privacy. Due to the excellent performance of deep reinforcement learning (DRL) in dealing with dynamic stochastic decision problems, many studies use DRL to improve the performance and efficiency of FL. For instance, deep Q-learning network (DQN) and FL are applied jointly to address challenges in edge computing, including task offloading [11], caching, and communication issues [12]. Additionally, deep deterministic policy gradient (DDPG) is employed to select device nodes with high data quality for improved model aggregation and reduced communication costs [13, 14]. Moreover, proximal policy optimization (PPO) is utilized to determine the optimal task scheduling strategy [15]. It is worth noting that both DQN and PPO are more adept at solving discrete action space problems. Due to its excellent stability and efficiency [16], PPO is our primary choice for achieving the vehicle grouping task to minimize the FL cost. The contributions of this paper can be summarized as follows.
-
•
We present an interpretable reputation-based framework for secure data sharing in trajectory prediction tasks. We design a reputation reward mechanism that replaces the traditional loss function with reputation values computed from vehicle trajectory data, driving the method components to cooperate and promoting federated learning to train more instructive global models.
-
•
We propose a reputation-driven asynchronous FL scheme adapted to dynamic and heterogeneous vehicle networks. This scheme is complemented by a reputation-enhanced PPO algorithm that groups vehicle trajectory models based on reputation values to reduce the FL cost. High-reputation vehicle clusters, characterized by high data quality and similar trajectory graph models, are prioritized for deep global federated learning aggregation.
-
•
We introduce differential privacy techniques to enhance the privacy and security of shared trajectory graph models and vehicle reputation values while preserving the graph structure and interactions among vehicles.
-
•
Extensive experiments are conducted on two large-scale vehicle trajectory datasets, namely NGSIM and ApolloScape, with different real-world scenarios, comparing our approach with other related models. The results demonstrate that our data sharing scheme effectively ensures data security, enhances trajectory prediction accuracy, and adapts well to various traffic scenarios. Moreover, comprehensive ablation studies confirm the effectiveness of our method components.
The rest of the paper is organized as follows. Section II presents related work. Section III gives the problem definition. Sections IV and V elaborate on the proposed model. Section VI presents an extensive experiment evaluation. Section VII concludes the paper.
II RELATED WORK
Trajectory prediction spans multiple domains, incorporating statistics[17], signal processing[18], and control systems engineering[4]. Contemporary trajectory prediction techniques often rely on data-driven approaches, particularly deep learning methods. CS-LSTM[19] and Social-STGCNN[20] combine neural networks and graph-based models to handle vehicle interactions. Some deep learning methods[21, 22, 23] have been employed for trajectory prediction. However, they primarily focus on local road interactions. In contrast, graph-based methods such as GRIP[7] and certain traffic density prediction techniques are capable of accommodating interactions without geographical constraints, ensuring a comprehensive view. Spectral[8] simulates the entire world, allowing graph models to capture diverse temporal correlations. Real-world traffic scenarios often face data silos, contrasting with the Internet of Vehicles (IoV)[24], an emerging paradigm that promotes high-quality services by enabling vehicles to share road-related information within in-vehicle networks. Data sharing[25] is integral to enhancing driving experiences and Internet of Thing (IoT) services, with data quality hinging on vehicle reputation[26], considering the potential for incorrect or irrelevant information stemming from defective sensors, corrupted firmware, or selfish motives. Therefore, developing a mechanism for quantifying vehicle reputation based on inter-vehicle interactions is pivotal[27].
Trust management systems in vehicular networks enable vehicles to assess information trustworthiness and provide network operators with a basis for incentives or penalties[28]. Centralized trust systems often struggle to meet stringent quality of service (QoS) requirements due to short decision times and central server reliance[29]. Distributed trust systems, where vehicles or roadside units manage trust locally, reduce network infrastructure interactions but face challenges due to variable vehicle capabilities and network dynamics[30]. Some studies involve roadside units in trust management[31], but RSUs can be half-trusted, leading to inconsistent services[32]. Various schemes exist, including trust calculation upon data reception and joint privacy-reputation consideration[33]. These approaches require vehicles to manage trust values, which may be inaccurate due to limited observations or failures[34]. Blockchain technology, known for its security features, has gained attention for vehicular data sharing[35]. Combining AI and blockchain enhances resource sharing under 5G conditions. Despite efforts like the Bayesian inference model on a public blockchain[26], creating a decentralized, reliable, and consistent vehicular trust management system remains challenging.
FL[36] offers privacy-preserving edge intelligence in distributed scenarios, allowing users to maintain their data while sharing model parameters with a server for collaborative global model learning. Traditional synchronous FL results in high communication costs and idle times[37, 38]. To improve efficiency, an asynchronous mini-batch algorithm was proposed, addressing optimization problems with multiple processors[39]. However, existing FL methods like Stochastic Gradient Descent (SGD) or Deep Neural Networks (DNN) may risk exposing sensitive data. Most data sharing schemes involve large amounts of aggregated data, including fresh, malicious, or redundant data[40]. Differential privacy[41], unlike prior models such as k-anonymity[42] and l-diversity[43], offers reliable privacy guarantees, defending against various privacy attacks. A machine learning differential privacy[44] has been proposed that releases data structures under the constraints of differential privacy rather than directly disclosing queries and answers.
III SYSTEM MODEL
In this paper, based on the inefficiency and poor security of current trajectory prediction methods, we propose a new asynchronous FL model for trajectory prediction, which effectively addresses the problems of inefficient training and privacy leakage in existing methods.
III-A Formulation of Trajectory Prediction
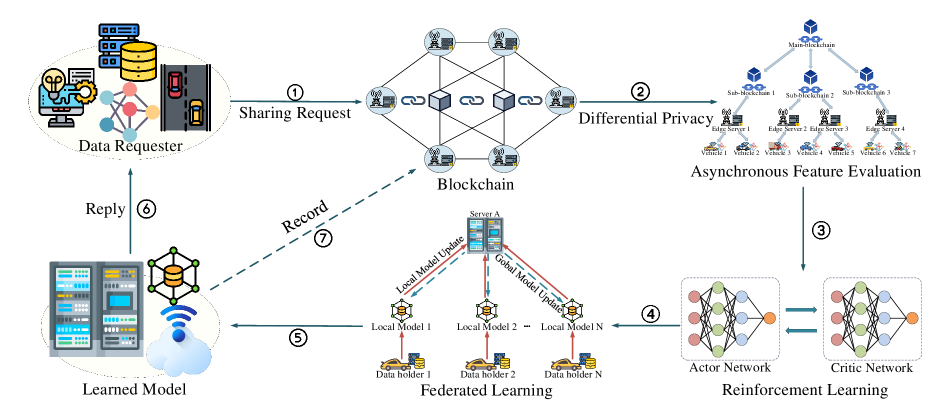
To begin with, we propose integrating the task of trajectory prediction into a practical scenario of distributed data sharing that involves multiple participants. Each participant has their own data and is willing to share it to realize the collaborative task, but we cannot exclude the existence of malicious sharers who try to interfere with the trajectory prediction task. In addition, the vehicular network comprises vehicles, RSUs, and Macro Base Stations (MBSs), primarily utilizing vehicle-to-vehicle (V2V) and vehicle-to-RSU (V2R) communication. RSUs are equipped with Mobile Edge Computing (MEC) servers, providing computational and storage capabilities. The proposed data sharing architecture comprises a permissioned blockchain module and a FL module, illustrated in Fig. 1. The permissioned blockchain handles retrieval and data-sharing transactions. We utilize the permissioned blockchain solely for retrieving relevant data and managing data accessibility, without recording the raw data.
We consider vehicle participants and a joint dataset . For any vehicle that participates in the request for data sharing, its local dataset , which contains the historical trajectory of all observations at time step observations at time step :
| (1) |
where are the coordinates of all observations at time and is the number of observations. We employ a coordinate system based on the measured relative values of the self-vehicle with reference to [45]. And the output , which predicts the future positions of all observations from time step to :
| (2) |
where is the predicted range.

III-B Our Proposed Architecture And Workflow
To improve computational and storage efficiency while facing limited resources, and to ensure secure and robust vehicle interactions, we implement a graph-based approach for model training and data sharing. Initially, vehicles must undergo authentication to become legitimate nodes in the permissioned blockchain, obtaining certificates for participating in V2V data sharing, and enabling them to download the global model locally for training purposes. Subsequently, vehicles transmit data sharing requests to nearby super nodes (such as MBS and RSU) for processing. Upon verifying their public keys, the super nodes commence the collection of weighted graph models perturbed with differential privacy noise from vehicles within the community for federated learning training. Participating vehicles compute reputation values based on the original data to assess the quality of their trajectory data. These values are recorded as shared transactions and in the local models of other participating vehicles within each vehicle’s local Directed Acyclic Graph (DAG). To mitigate the global aggregation latency and optimize the aggregation results, we use the PPO algorithm to group vehicles based on the reputation evaluation mechanism. Therefore, the high-quality vehicle clusters receive priority in deep aggregation. The super nodes collaborate to train the global model through asynchronous FL and broadcast the results to all committee nodes, which are charged with driving the consensus process for the permissioned blockchain. The committee nodes collect the transactions into blocks and verify the blocks to further add them to the permissioned blockchain. The vehicles optimize their local models by integrating the global model, thereby achieving increased accuracy in predicting trajectories. Fig. 2 shows the working mechanism of our scheme.
IV Reputation-Based Hybrid Blockchain For Data Sharing
Considering resource constraints and privacy concerns of vehicle users, we propose a data sharing scheme, which involves the collaborative learning of a federated graph neural network model across decentralized parties to share well-trained model parameters instead of raw data.
IV-A Graph-Based Trajectory Modeling
Our approach transforms object trajectories into weighted graphs for interaction modeling. Referring to the trajectory prediction model GRIP++[45], each object trajectory is organized as a 3D array, computed for improved speed to enhance prediction accuracy. We use undirected graphs to depict the interactions between objects. The input data is processed by graph convolution network (GCN). Graph operations handle spatial interactions and temporal convolution captures time-based features. Both the encoder and decoder used for the trajectory prediction model are two-layer GRU (Gated Recurrent Unit) networks. Based on this, is converted into a weighted graph of vehicle trajectories. The set of nodes is defined as , with denoting the total number of objects observed in the scene. Each node contains its own weights . The weights are determined based on the similarity of trajectories between vehicles, including direction, speed, and tilt angle, as described in the following subsection. Subsequently, is serialized into ordered vectors that are then mapped onto linear vectors. These maps are combined to form a global vehicle network graph . For the overall graph , the number of representative vertices is denoted as . Afterwards, the size of the normalization property of the vertices will be and the size of the normalization property of the edges will be . Eventually, the normalized vector .
After that, we use cosine similarity as a distance function to compare vehicle matrices sequentially in temporal order, and confidence levels above 80% will fail validation, as well as new weighted graphs added in future moments with confidence levels above a preset threshold will fail validation. By using weighted graphs and the PPO algorithm, the set of vehicles is divided into high and low reputation groups. Through this differential privacy federation learning mechanism, instead of sharing local vehicle model parameters, the shared graph neural network model is used to retrieve and compare confidence levels thus filtering out the series of graphs with high trustworthiness as well as low similarity, which prevents the model parameters from leaking the vehicle trajectory information and improves the efficiency of the next global aggregation.
IV-B Differential Privacy-Enhanced Data Sharing
Our objective is to develop a secure mechanism for data sharing in trajectory prediction scenarios that intelligently facilitates data sharing among distributed multi-users while effectively safeguarding data privacy. Our approach involves considering parties or data holders, along with a joint data set . For each party , there exists a local data set in . All parties unanimously agree to share data without compromising confidential information. Let represent requests for data sharing. Requesters submit queries , and we provide computed results rather than raw data to fulfill sharing requirements. Finally, the trained global model is returned to the committee node. Recipients can leverage the received global aggregation model to respond to data sharing requests locally.
Considering the large size and sensitivity of the data, inspired by previous work[46], we utilize the blockchain for data retrieval, while the actual data remains stored on local vehicles. We combine graph neural networks and differential privacy for quality verification. Using a graph representation of the raw data improves computational and storage efficiency under resource constraints, preserving more structural and contextual information for validation while also preventing privacy leakage. Once new data providers join, their uniqueness (vehicle ID) is recorded on the blockchain, alongside an overview of their data, including trajectory data, vehicle types, and data sizes. All data profiles from multiple participants are recorded as transactions and verified by blockchain nodes using Merkle trees[47]. Each data sharing event is also stored as a transaction on the blockchain. All participants (denoted as ) are selected through multi-party searches in the blockchain and are divided into communities based on their reputation values. These communities consist of members with similar data quality. Given the limited communication resources of IoT devices, the retrieval process should also consider the matrix cosine similarity between the two participants. When a user submits a request to share data with a nearby node , all nodes within the identical community as broadcast this request to other vehicles that are observing the target during that timestamp to commence the retrieval process. The process is recursively executed until all trajectory graphs for that timestamp have been executed. At the end of the retrieval process, we will procure a collection of vehicles that pertain to the request. These vehicles exhibit structural stability, the absence of anomalous data, and minimized redundancy in trajectory graphs within the community, addressing the constraints posed by limited communication resources. To ensure privacy protection for the shared model, we employ differential privacy for each local model using the Laplace mechanism. Here, we add calibrated noise with sensitivity to the local data to train , expressed as:
| (3) |
where denotes the privacy budget. Subsequently, participant transmits the model as a blockchain transaction broadcast to other participants for federated learning. Upon receiving , participant trains a new local data model based on the received and its local data, and subsequently broadcasts to other participants. This iterative process continues among participants. Finally, a global model is generated, given by .

IV-C Trajectory Similarity-Based Reputation-Aware Data Sharing
The use of Mean Absolute Error (MAE) as an evaluation metric may not be practical in real-world trajectory prediction scenarios. We employ a novel evaluation metric: the reputation value derived from trajectory similarity among vehicles. The locally collected vehicle data is spatially correlated and exhibits a spatial extent. Incorporating trajectory similarity into reputation calculations when sharing data between vehicles enables location awareness and enhances data relevance. The more similar the trajectories, the more relevant the shared data from the data provider, resulting in improved quality, accuracy, and reliability of the shared data. Trajectory coefficients of a vehicle are represented as velocity, position, orientation. The weights of each coefficient in are , , and , and . The similarity between two trajectory segments, and , of vehicles and , can be expressed as . This is calculated using the Eq.(4),
| (4) |
The normalized dissimilarity for and , denoted as , is used to calculate this similarity, as Eq.(5),
| (5) | ||||
We assert that relies on the disparity in velocity, position, and orientation of the two trajectory segments. The velocity difference between the two segments of the trajectory is given by
| (6) |
where and are the velocities of vehicles and during their trajectory segments, respectively. and are the average velocities of these two vehicles. The position shows the variance in the position between the trajectory segments. The number of sampled points for and during the time window are denoted as and , respectively. The set of sampled points in temporal order are and . We employ the Longest Common Sequence (LCS) method to measure the similarity of trajectory segments. For trajectory segments and , the LCS is described as , where . Therefore, the equation for the difference in position between the trajectory segment position is provided as follows:
| (7) |
where is the number of points in the LCS of the trajectory segments and . The directory difference between the two trajectory segments is the angle between the two trajectory segments. Here, we employ as the angle between the trajectories and to represent the direction. More precisely,
| (8) |
1) Local Opinions for Subjective Logic
In the case of two vehicles, the reputation between and can be formally described as a local opinion vector , where , , and denote trust, distrust, and uncertainty, respectively. , and ,,. Here,
| (9) |
where represents the number of negative events, and represents the number of positive events. The uncertainty of the local opinion vector depends on the quality of communication between vehicles and , and the communication quality is the probability of successful transmission of packets of data sharing requests during communication. According to , the reputation value denotes the expected belief of in providing true relevant data to , which can be expressed as
| (10) |
The constant is assigned by the vehicle and measures how much uncertainty affects the reputation of the vehicle. It is recommended to initially set to 0.5.
2) Combine Local Opinions With Suggested Opinions
Subjective opinions of neighboring vehicles should be taken into account when considering the requesting vehicle. We combine the subjective opinions of different recommenders into a single opinion, named according to the weight of each opinion. These opinions are combined to form the following common opinion , as follows,
| (11) |
where represents the set of neighboring vehicles that interact with . The data requestor has a local opinion after receiving the shared data from the data provider. In order to avoid spoofing, this local opinion should still be taken into account when forming the final opinion. The final opinion formation for , where , and are calculated as
| (12) |
So the final reputation of to is
| (13) |
Reputation values are incorporated into the DAG as training model parameters. The DAG comprises nodes of both data sharing events and training model parameters, which are connected by edge connections established through approval relationships between transactions. These connections facilitate nodes to be connected to each other. Vehicles store DAGs locally and update asynchronously to achieve consistency with other vehicles. Each vehicle disperses its own latest DAG, which includes transactions and approval relationships, to neighboring vehicles. This scheme propagates updated DAGs and maintains loose consistency among vehicles, resulting in lower computational intensity and increased global robustness. The specific process is shown in Fig. 3.
IV-D Consensus: Proof of Reputation(PoR)
By transforming the data sharing problem into a model sharing problem, the privacy of data holders is enhanced. Moreover, the data model of the graph neural network efficiently provides essential information for new sharing requests, as well as better-preserved vehicle trajectory features during data fusion. However, the use of prevailing consensus mechanisms like Proof-of-Work (PoW) in data sharing may lead to high computational and communication costs. To resolve this matter, implementing the FL Authorised Consensus Proof of Reputation (PoR) protocol is suggested. PoR combines vehicle reputation values with the consensus process, enhancing node computational resources. When data sharing requests occur, consensus committee members are chosen by retrieving the relevant blockchain nodes. The committee oversees the consensus process and acquires knowledge of the data model of the requested data. Asynchronous FL seeks to develop a worldwide information model , which delivers an effective response (Req) to inquiries concerning data sharing, thereby achieving the intended objective.
Sending consensus messages to only the committee nodes can lower communication overhead. However, reducing the number of nodes increases the challenge of reaching agreement. We offer reputation proof for consensus in data sharing to balance security and overhead. We choose committee leaders based on their reputation scores. As each committee node trains a local data model, it is imperative to verify and measure the quality of the model during the consensus process. Prediction accuracy is deemed essential to evaluate the performance of the trained local models. More precisely, we train the model as a regression task each time during trajectory prediction training. The total loss can be calculated as
| Loss | (14) |
where is the future time step, and and are the predicted position and ground truth at time step , respectively.
For each committee node, a trained global model and a local model are obtained after asynchronous training. The committee executes the consensus process, during which committee node sends its trained model to the next committee node while responding to a data sharing request. The transmission is recorded as a model transaction along with its corresponding loss (). has a pair of public and private keys (, ) to encrypt and sign the message. then sends the encrypted message to the other committee nodes. All model transactions are then collected and stored locally as potential blocks by the committee node . As part of the training procedure, validates all transactions it receives by computing the loss defined in Eq.14. , the loss of , is calculated through the following equation:
| (15) |
where represents a weight parameter indicating the contribution of to the global model and represents the loss of the local training model , determined by the size of the training data of and other participants .
IV-E Trajectory Prediction
Using the aforementioned approach, we achieve effective interpretable federal learning for the trajectory prediction task. Specifically, by characterizing the vehicle trajectory data as a normalized weighted graph, the important private parameters are preserved. Preventing data redundancy, we achieve the elimination of vehicles with high similarity in the set of neighboring nodes using a multi-party query approach while protecting privacy. We are well aware that the quality of vehicle improvement data directly affects the results of parameter fusion in the federal learning model, so we introduce a reputation mechanism to solve this problem well by using the reputation values calculated from the private track data of the vehicles that are not eliminated and submit them to the reviewer for further grouping. The grouping method will be further described in section V.

V Enhanced Asynchronous Federated Learning with PPO Clustering Algorithm Based on Vehicle Reputation
In this subsection, we tackle the challenges of insufficient heterogeneous model aggregation and significant global model update delays in FL by incorporating the proposed reputation evaluation mechanism to design an interpretable asynchronous FL mechanism that utilizes the enhanced PPO algorithm.
V-A Graph Asynchronous Federated Learning for Trajectory Prediction
In IoV, the computational power and dynamic communication conditions of each vehicle result in different learning times. As a result, the slowest participant determines the running time of each learning iteration, while the other participants must wait to keep in sync. Existing work on trajectory prediction using FL essentially uses the synchronous federated algorithm FedAvg[48], which improves data security for multi-client model training. However, synchronous FL leads to increased communication costs and longer waiting times for idle nodes. For tasks with spatial timing dependencies, it can cause training difficulties leading to untimely global aggregation. Several studies have investigated asynchronous learning mechanisms to improve the learning performance[39, 49]. However, implementing these mechanisms for trajectory prediction may lead to suboptimal node selection, as their lack of interpretability can introduce biases in vehicle evaluations. Therefore, this paper proposes a method to predict trajectories via asynchronous FL. It utilizes the proposed reputation evaluation mechanism to group nodes with the PPO algorithm, enabling the asynchronous training of trusted vehicle clusters.
With the filtering and reputation value calculations of the previous section, we obtained a set of vehicles with unique features. Local aggregation on each vehicle is performed asynchronously within the range to enhance the quality of the locally trained model. The vehicles preserve and update the DAG locally to achieve asynchronous consistency with the other vehicle nodes. Asynchronous consensus enables vehicles to reach an agreement based on historical states rather than the current state. Vehicle sends updates to its local and then transmits the updates to nearby vehicles using a gossip scheme to achieve synchronization. Each vehicle randomly scatters its latest to neighboring vehicles. The gossip scheme propagates the DAG updates and maintains loose consistency between vehicles. This approach is less computationally intensive and globally robust. While asynchronous FL has improved aggregation efficiency, the issue of vehicle grouping remains unresolved. Limitations arise from exclusively conducting asynchronous local aggregation on nearby local vehicles to obtain a global model, as it fails to adapt to dynamic traffic conditions and thus cannot effectively optimize local prediction models. Therefore, as illustrated in Fig. 4, we employ the PPO algorithm with an innovative reward feedback mechanism driven by reputation evaluation. This mechanism prioritizes the deep aggregation of high-reputation vehicles, leading to a superior global aggregation model.
V-B Reputation-Based PPO Vehicle Clustering Algorithm
We aim to minimize execution time and enhance model accuracy by precisely categorizing the vehicle nodes according to their reputation values. During the global aggregation phase, the disparate computational resources and fluctuating communication conditions among different vehicles hinder the attainment of efficient execution. Therefore, we propose an approach where participating vehicles within a specific timestamp are selected based on reputation values until each grouping contains no more than vehicles. This approach prioritizes the aggregation of trajectory graphs with high reputation representing high data quality and improves the global aggregation.
Unlike conventional reinforcement learning, which evaluates the performance of an agent in a specific slot primarily based on accuracy loss alone, we consider the characteristics of the data during node clustering. For this purpose, we introduce the Reputation of Learning (RoL) to describe the high or low reputation value of vehicle in the aggregation process of slot as follows,
| (16) |
where represents the completed combined model in slot , and represents the training data of vehicle . Furthermore, we define the local learning time cost of vehicle in slot and the communication cost of vehicle as follows,
| (17) |
where denotes the necessary CPU cycles to train model per iteration. Thus, the function of time consumption is
| (18) |
In this way, the total cost of FL in time slot can be given by the following equation:
| (19) |
where in the time step is an indicator vector for vehicle selection, with indicating activation and indicating the opposite. We formulate the combinatorial optimization problem using a Markov Decision Process, which we denote as . The task of node selection can be expressed in the following way:
| (20a) | ||||
| s.t. | (20b) | |||
| (20c) | ||||
where the constraint Eq.20c ensures that the distance between the selected participating vehicles and the computed centroid cannot exceed a finite distance . We use PPO to solve the problem Eq.20a. The fundamental principle involves updating the system policy with a value function.
We utilize PPO to ascertain the optimal resolution for vehicle reputation categorization in asynchronous FL. PPO operates on a well-defined Markov decision process . At each time slot in FL, the system state is represented by . Here, denotes the wireless data rate between vehicles, represents the available computing resources of the vehicles, indicates the reputation of the vehicles, and signifies the selection state of the vehicles. The action taken at time slot , denoted by , corresponds to a vehicle selection decision and can be framed as a 0-1 problem. Specifically, when vehicle is selected as a node with a high reputation value, otherwise . Our improvement is mainly in the reward function. Specifically, we customize the reward function to add 1 to the reward value for choosing a vehicle with a high reputation value, subtract 1 from the reward value for choosing a low reputation value, subtract 10 from the reward value for choosing a low reputation value for 5 consecutive times, and end the round; if the number of vehicles chosen with a high reputation value reaches the threshold, then 20 points are rewarded; and end the round. The system assesses the impact of an action using a reward function called . At iteration , the agent carrying out the task of selecting the vehicle reputation takes action while in state . Subsequently, the action is appraised via the established reward function in the ensuing manner:
| (21) | ||||
The reward function assesses the standing of taking action at time interval . The overall cumulative reward can be presented as:
| (22) |
where is the reward discount factor.
For the PPO algorithm, the objective is to determine the value of lambda that maximizes reputation accumulation, as shown in the following Eq.23.
| (23) |
Through algorithm 1, the corresponding groups with high and low reputations can be obtained. Next, the vehicle feature parameters of each group are combined, followed by global fusion, with priority given to the high reputation group for deep aggregation.
| Attributes | ApolloScape | NGSIM |
|---|---|---|
| Frequency of sample | 2 Hz (downsampled) | 5 Hz |
| Total number of vehicles | 5156 | 11 779 |
| Total frames | 5593 (downsampled) | 30 476 |
| Train len/pred len | 3 s/3 s | 3 s/5 s |
VI EXPERIMENTS
In this section, we initially present the renowned datasets used in the experiment, followed by the description of evaluation metrics. Subsequently, we explicate the impact of adjusting diverse model components on the prediction effect and compare the current approach to previous ones. We investigate the impact of various iterations of the model on convergence and the influence of varying quantities of bad nodes on model forecasts. We run our scheme on a desktop running Ubuntu 20.04 with 2.30GHz Intel(R) Xeon(R) E5-2686 v4 CPU, 64GB Memory, and a NVIDIA 3090 Ti Graphics Card.

VI-A Datasets
We evaluated our proposed method RAFLTP on well-known real-world datasets: NGSIM[51, 50], and ApolloScape Trajectory dataset[52], as shown in Fig. 5. The basic info is listed in Table I. NGSIM contains two road segment datasets, US-101 and I-80. Referring to the method[53, 54, 19] for data segmentation of the training set and testing set, a quarter of each of the three road condition data is selected as the test set. Each trajectory is segmented into 8 s, the first 3 s are used as training data, and the last 5 s are used as training labels. The ApolloScape Trajectory dataset was gathered in an urban area during rush hour by a vehicle called the Apollo acquisition car. The data primarily comprises vehicle trajectories that are based on object detection and tracking algorithms. During the initial phase, we adopt GRIP++[45] to select 20 of the sequences for validation purposes, while the remaining 80 is utilized as the training set.
VI-B Metrics
This subsection highlights several established metrics that demonstrate the validity and merits of the proposed methodology. Specifically, we adopt the Root Mean Square Error (RMSE), Average Displacement Error (ADE), and Final Displacement Error (FDE) to evaluate the performance with reference to Social-GAN[55].

VI-C Ablation study
To demonstrate the advantage of the proposed approach, several subsequent ablation experiments were performed in this subsection.


VI-C1 The influence of different components
To test the effectiveness of the various components in our framework, we conducted ablation experiments on the ApolloScape Trajectory dataset consisting of five variants: basic encoder–decoder network (GRU based), w/o RL, w/o differential privacy, w/o Asynchronous FL (AFL), priority aggregation of low reputation vehicles (Low-R) and our complete methodology. From Fig. 6, it is evident that the basic encoder-decoder network exhibits the highest error, primarily due to its limited consideration of vehicle interactions. However, with the incorporation of GRIP-based model enhancements under our proposed method, the ADE shows a substantial reduction. Furthermore, we observe that the impact of our method on ADE is most pronounced when the reputation-based PPO module is absent. This underscores the significance of our reputation-based PPO node grouping approach in trajectory prediction. By dynamically aggregating data from high-quality vehicle data providers using learnable weights, we effectively enhance prediction accuracy.
Additionally, the influence of the differential privacy module is apparent, as it enforces constraints to filter out abnormal and redundant data, resulting in more robust and secure model aggregation. It’s noteworthy that the absence of FL leads to lower prediction accuracy compared to the full model. This emphasizes the effectiveness of reputation-based grouping aggregation in alleviating the challenges associated with heterogeneous data fusion and enhancing trajectory prediction accuracy. Moreover, if we choose to prioritize the aggregation of vehicles with low reputation values, it will rather reduce the trajectory prediction accuracy.
VI-C2 The influence of DRL Methods
We compare the learning results of the PPO algorithm and the DQN algorithm in the NGSIM and ApolloScape datasets. All algorithms take the same number of network layers, neurons, and training parameters. Fig. 7 and Fig. 8 demonstrate that the PPO algorithm is more stable and adaptable to changes in both datasets, converging quickly after positive feedback. Additionally, it was found through testing that the training time of the PPO algorithm is 34.5% faster than that of the DQN algorithm.


VI-C3 The influence of bad nodes
To analyze the impact of bad nodes on different modules within the overall framework, we examined how different components of the proposed solution affect the ADE under different amounts of bad nodes. We randomly selected a certain number of data providers at each iteration and manipulated their data to introduce anomalies. As shown in Fig. 9 and Fig. 10, an increase in the number of bad nodes significantly degrades performance. Interestingly, in Fig. 9, the w/o differential privacy leads to different effects of ADE with different amounts of bad nodes. Surprisingly, a higher number of bad nodes results in a lower ADE. This can be attributed to the reinforcement learning-based grouping of vehicles according to their reputation scores, which directs low-quality data providers to a shallow aggregation group and subsequently improves prediction accuracy.
In Fig. 10, we can clearly observe the importance of the differential privacy module in safeguarding the model from bad nodes. The number of bad nodes has no discernible effect on the ADE of trajectory prediction, confirming the efficiency of the differential privacy module in constraining the data structures shared by the data providers. This effectively limits the impact of anomalous data nodes and redundant nodes on prediction accuracy.


VI-C4 Frequency of aggregation
To explore the impact of different local and global aggregation frequencies on prediction accuracy and the influence of invoking the differential privacy module at different frequencies, we designed different combinations of aggregation and invocation frequencies. As depicted in Fig. 11, higher local and global aggregation frequencies lead to faster convergence and improved prediction accuracy. Similarly, Fig. 12 shows that higher invocation frequencies of the differential privacy module also lead to improved prediction accuracy. Taken together, these results underscore the effectiveness of our proposed solution in improving prediction accuracy.
VI-C5 Impact of Private Budget
To explore the impact of differential privacy hyperparameters on prediction accuracy while striking a balance between data utility and privacy, we investigate privacy budget from 0.1 to 1.0 across different datasets. As shown in Fig. 13, in the ApolloScape dataset, significantly affects data utility due to excessive noise, with stability observed from 0.3 onwards. However, excessively large values of compromise privacy protection. Therefore, 0.3 strikes a good balance between data privacy and utility. In the NGSIM dataset, due to the increase in the number of vehicles, maintaining a balance between privacy budget and utility requires .


VI-C6 Impact of Reputation Quantization Mechanism
To demonstrate the superiority of our proposed interpretable reputation reward mechanism as a quantitative metric for optimizing federated learning, we conducted ablation experiments on the NGSIM dataset. Specifically, we replaced our AFL algorithm with the traditional synchronous FL (SFL) scheme FedAVG [48] and used RMSE as the trajectory prediction loss for uploading local parameters to the server for vehicle grouping. As depicted in Fig. 14, the traditional SFL scheme yielded inferior prediction results compared to the AFL scheme. In dynamic trajectory prediction scenarios, waiting for inefficient vehicle nodes to complete local model aggregation inevitably leads to suboptimal global model outcomes. Additionally, substituting RMSE for reputation values for reinforcement learning-based vehicle grouping resulted in a reduction in trajectory prediction accuracy. This is because loss functions provide an incomplete assessment of the impact of vehicle nodes on both local and global aspects. In dynamic traffic environments, vehicles continuously influence each other, leading to unavoidable biases in trajectory prediction. Discarding vehicle nodes solely based on significant biases and rewarding vehicles that consistently exhibit smooth and straight trajectories would be unfair. In contrast, our proposed vehicle reputation quantification mechanism focuses on the quality of vehicle data and the similarity of local trajectories. It facilitates deep aggregation of clusters of vehicles with high-quality data and similar trajectory model structure, thereby yielding a global model with enhanced guidance value.





VI-D Comparison analysis
With regard to the latest findings in DGInet[56], we have compared our model with seven baseline methods consisting of state-of-the-art trajectory prediction methods:
-
1.
Encoder–Decoder[8]: This approach employs an enc-dec architecture based on LSTM.
-
2.
CS-LSTM[19]: This approach combines CNN and LSTM to extract spatio-temporal features.
-
3.
TraPHic[57]: This approach employs spatial attention pooling in combination with CNNs and LSTMs to predict the trajectory.
-
4.
Social-GAN[55]: It employs the encoder-decoder architecture as a generator and subsequently trains an additional encoder to serve as a discriminator for trajectory prediction.
-
5.
GRIP[7]: This method uses graph convolution for trajectory prediction. The resulting features from the enc-dec network facilitate trajectory prediction.
-
6.
Spectral[8]: The approach forecasts both paths and actions and utilizes an additional network founded on spectral clustering to adapt the LSTM-based enc-dec network.
-
7.
DGInet[56]: This approach combines a semi-global graph mechanism with a convolutional graph network based on M-products for predicting trajectories.
In Table II, we compare the ADE and FDE of our predicted trajectory with the previous methods. Unfortunately, our solution did not achieve state-of-the-art results. However, compared to the GRIP method, we managed to reduce the ADE by 11.2% and the FDE by 10.2% on the ApolloScape dataset, surpassing even the Spectral result. It’s important to note that our approaches, like GRIP and DGInet, predict trajectories for all vehicles in a traffic scenario, as opposed to Spectral, which predicts only a single vehicle’s trajectory. Fortunately, our approach, which enhances the security and robustness of data sharing among vehicles in a distributed trajectory prediction scenario, aligns more closely with real-world traffic situations and stands out as a unique contribution.
| Method | ApolloScape (3s) | NGSIM (5s) | ||
|---|---|---|---|---|
| ADE | FDE | ADE | FDE | |
| Enc-Dec(LSTM) | 2.24 | 8.25 | 6.86 | 10.02 |
| CS-LSTM | 2.14 | 11.69 | 7.25 | 10.05 |
| TraPHic | 1.28 | 11.67 | 5.63 | 9.91 |
| Social-GAN | 3.98 | 6.75 | 5.65 | 10.29 |
| GRIP | 1.25 | 2.34 | 1.61 | 3.16 |
| Spectral | 1.12 | 2.05 | 0.40 | 1.08 |
| RAFLTP (Ours) | 1.11 | 2.01 | 0.98 | 2.04 |
| DGInet | 0.99 | 1.74 | 0.37 | 1.01 |
VI-E Visualization of Prediction Results
In Fig. 15, we use the NGSIM datasets to show several prediction results under different traffic conditions, where the circled vehicles are those that GRIP++ tries to predict, the purple solid line is the observed history, the red solid line is the future ground truth, the blue dashed line is the prediction result of our model (5 seconds), the green dashed line is the GRIP++ prediction (5 seconds). The range from -90 to 90 feet is the observation range. After observing the 3-second historical trajectories, our model predicts the trajectories over the 5-second horizon in the future. As can be seen in Fig. 15, in various scenarios, when feeding the model with identical historical trajectories, our proposed model (blue dashed line) shows a closer match with the actual trajectories represented by the red solid line compared to GRIP++ (green dashed line), especially at the endpoints of the dashed lines. This further substantiates the superior predictive performance of our approach over GRIP++.
VI-F Computation time
The computational efficiency of the algorithm is a critical performance metric for autonomous vehicles. The computation time of our proposed approach is reported in Table III, implemented using PyTorch. We evaluate the prediction time for 1000 vehicles with batch sizes of 128 and 1, respectively. Our trajectory prediction model is an enhancement based on GRIP++. Although our computational time exhibits a delay compared to the GRIP++ model, it remains acceptable compared to other methods. Despite the latency incurred by our approach, it provides data privacy protection and higher prediction accuracy in return. Notably, our proposed PPO method for grouping vehicles operates on the server. The pre-trained PPO grouping model is deployed on the server, requiring only periodic experience replay[58] and asynchronous updates, without impacting the prediction efficiency of the vehicles themselves.
| Scheme | Predicted # | Times (s) batch size 128 | Times (s) batch size 1 |
|---|---|---|---|
| CS-LSTM | 1000 | 0.29 | 35.13 |
| GRIP | 1000 | 0.05 | 6.33 |
| GRIP++ | 1000 | 0.02 | 1.62 |
| Spectral | 1000 | 1.10 | 120.20 |
| DGInet | 1000 | 0.07 | 6.42 |
| RAFLTP (Ours) | 1000 | 0.38 | 5.278 |
VII CONCLUSION
This paper presents an innovative framework to address the distributed trajectory prediction problem. Within this framework, we leverage graph neural network tools and propose an asynchronous federated learning-based data sharing approach with an interpretable reputation quantization mechanism. Data providers share data structures under differential privacy constraints to ensure security. We implement PPO to categorize vehicles based on reputation levels, thereby optimizing the efficiency of FL aggregation. Experimental results demonstrate that the proposed data sharing scheme is more tolerant of bad nodes, enhances the security of the distributed trajectory prediction task, and significantly improves prediction accuracy. In future research, we plan to focus on integration with 6G networks and further enhancing efficiency.
References
- [1] K. Yu, L. Lin, M. Alazab, L. Tan, and B. Gu, “Deep Learning-Based Traffic Safety Solution for a Mixture of Autonomous and Manual Vehicles in a 5G-Enabled Intelligent Transportation System,” IEEE Trans. Intell. Transport. Syst., vol. 22, no. 7, pp. 4337–4347, Jul. 2021.
- [2] Z. Xiao, J. Shu, H. Jiang, G. Min, H. Chen, and Z. Han, “Perception Task Offloading With Collaborative Computation for Autonomous Driving,” IEEE J. Select. Areas Commun., vol. 41, no. 2, pp. 457–473, Feb. 2023.
- [3] J. Wang, X. Yuan, Z. Liu, W. Tan, X. Zhang, and Y. Wang, “Adaptive dynamic path planning method for autonomous vehicle under various road friction and speeds,” IEEE Transactions on Intelligent Transportation Systems, vol. 24, no. 10, pp. 10 977–10 987, 2023.
- [4] Z. Peng, Y. Jiang, and J. Wang, “Event-Triggered Dynamic Surface Control of an Underactuated Autonomous Surface Vehicle for Target Enclosing,” IEEE Trans. Ind. Electron., vol. 68, no. 4, pp. 3402–3412, Apr. 2021.
- [5] H. Xu, W. Liu, M. Jin, and Y. Tian, “Positioning and contour extraction of autonomous vehicles based on enhanced doa estimation by large-scale arrays,” IEEE Internet of Things Journal, vol. 10, no. 13, pp. 11 792–11 803, 2023.
- [6] Y. Huang, J. Du, Z. Yang, Z. Zhou, L. Zhang, and H. Chen, “A Survey on Trajectory-Prediction Methods for Autonomous Driving,” IEEE Trans. Intell. Veh., vol. 7, no. 3, pp. 652–674, Sep. 2022.
- [7] X. Li, X. Ying, and M. C. Chuah, “GRIP: Graph-based Interaction-aware Trajectory Prediction,” in 2019 IEEE Intelligent Transportation Systems Conference (ITSC). Auckland, New Zealand: IEEE, Oct. 2019, pp. 3960–3966.
- [8] R. Chandra, T. Guan, S. Panuganti, T. Mittal, U. Bhattacharya, A. Bera, and D. Manocha, “Forecasting trajectory and behavior of road-agents using spectral clustering in graph-lstms,” IEEE Robotics and Automation Letters, vol. 5, no. 3, pp. 4882–4890, 2020.
- [9] Q. Li, Z. Wen, Z. Wu, S. Hu, N. Wang, Y. Li, X. Liu, and B. He, “A Survey on Federated Learning Systems: Vision, Hype and Reality for Data Privacy and Protection,” IEEE Trans. Knowl. Data Eng., vol. 35, no. 4, pp. 3347–3366, Apr. 2023.
- [10] Z. Peng, J. Xu, X. Chu, S. Gao, Y. Yao, R. Gu, and Y. Tang, “VFChain: Enabling Verifiable and Auditable Federated Learning via Blockchain Systems,” IEEE Trans. Netw. Sci. Eng., vol. 9, no. 1, pp. 173–186, Jan. 2022.
- [11] S. Shen, Y. Han, X. Wang, and Y. Wang, “Computation offloading with multiple agents in edge-computing–supported iot,” ACM Trans. Sen. Netw., vol. 16, no. 1, dec 2019. [Online]. Available: https://doi.org/10.1145/3372025
- [12] X. Wang, R. Li, C. Wang, X. Li, T. Taleb, and V. C. M. Leung, “Attention-weighted federated deep reinforcement learning for device-to-device assisted heterogeneous collaborative edge caching,” IEEE Journal on Selected Areas in Communications, vol. 39, no. 1, pp. 154–169, 2021.
- [13] P. Zhang, C. Wang, C. Jiang, and Z. Han, “Deep reinforcement learning assisted federated learning algorithm for data management of iiot,” IEEE Transactions on Industrial Informatics, vol. 17, no. 12, pp. 8475–8484, 2021.
- [14] M. Zhou, Y. Yu, and X. Qu, “Development of an efficient driving strategy for connected and automated vehicles at signalized intersections: A reinforcement learning approach,” IEEE Transactions on Intelligent Transportation Systems, vol. 21, no. 1, pp. 433–443, 2020.
- [15] T. M. Ho, K.-K. Nguyen, and M. Cheriet, “Federated deep reinforcement learning for task scheduling in heterogeneous autonomous robotic system,” IEEE Transactions on Automation Science and Engineering, vol. 21, no. 1, pp. 528–540, 2024.
- [16] J. Schulman, F. Wolski, P. Dhariwal, A. Radford, and O. Klimov, “Proximal policy optimization algorithms,” 2017.
- [17] D. Yuan, X. Chang, P.-Y. Huang, Q. Liu, and Z. He, “Self-supervised deep correlation tracking,” IEEE Transactions on Image Processing, vol. 30, pp. 976–985, 2021.
- [18] Y. Wang, W. Yang, D. Li, and J. Q. Zhang, “An rfs time-frequency model for decomposing chirp modes with dynamic cross, appearance, and disappearance,” IEEE Transactions on Aerospace and Electronic Systems, vol. 59, no. 4, pp. 4525–4539, 2023.
- [19] N. Deo and M. M. Trivedi, “Convolutional social pooling for vehicle trajectory prediction,” in 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition Workshops (CVPRW), 2018, pp. 1549–15 498.
- [20] A. Mohamed, K. Qian, M. Elhoseiny, and C. Claudel, “Social-stgcnn: A social spatio-temporal graph convolutional neural network for human trajectory prediction,” in 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), 2020, pp. 14 412–14 420.
- [21] A. Monti, A. Bertugli, S. Calderara, and R. Cucchiara, “Dag-net: Double attentive graph neural network for trajectory forecasting,” 2020.
- [22] Y. Ma, X. Zhu, S. Zhang, R. Yang, W. Wang, and D. Manocha, “Trafficpredict: Trajectory prediction for heterogeneous traffic-agents,” 2019.
- [23] F.-C. Chou, T.-H. Lin, H. Cui, V. Radosavljevic, T. Nguyen, T.-K. Huang, M. Niedoba, J. Schneider, and N. Djuric, “Predicting motion of vulnerable road users using high-definition maps and efficient convnets,” 2020.
- [24] Z. Lv, J. Lloret, and H. Song, “Guest editorial software defined internet of vehicles,” IEEE Transactions on Intelligent Transportation Systems, vol. 22, no. 6, pp. 3504–3510, 2021.
- [25] J. Contreras-Castillo, S. Zeadally, and J. A. Guerrero-Ibañez, “Internet of vehicles: Architecture, protocols, and security,” IEEE Internet of Things Journal, vol. 5, no. 5, pp. 3701–3709, 2018.
- [26] Z. Yang, K. Yang, L. Lei, K. Zheng, and V. C. M. Leung, “Blockchain-based decentralized trust management in vehicular networks,” IEEE Internet of Things Journal, vol. 6, no. 2, pp. 1495–1505, 2019.
- [27] E. M. Ghourab, M. Azab, and N. Ezzeldin, “Blockchain-guided dynamic best-relay selection for trustworthy vehicular communication,” IEEE Transactions on Intelligent Transportation Systems, vol. 23, no. 8, pp. 13 678–13 693, 2022.
- [28] M. K. Jabbar and H. Trabelsi, “A novelty of hypergraph clustering model (hgcm) for urban scenario in vanet,” IEEE Access, vol. 10, pp. 66 672–66 693, 2022.
- [29] C. Lai, K. Zhang, N. Cheng, H. Li, and X. Shen, “Sirc: A secure incentive scheme for reliable cooperative downloading in highway vanets,” IEEE Transactions on Intelligent Transportation Systems, vol. 18, no. 6, pp. 1559–1574, 2017.
- [30] X. Huang, R. Yu, J. Kang, and Y. Zhang, “Distributed reputation management for secure and efficient vehicular edge computing and networks,” IEEE Access, vol. 5, pp. 25 408–25 420, 2017.
- [31] J. Oluoch, “A distributed reputation scheme for situation awareness in vehicular ad hoc networks (vanets),” in 2016 IEEE International Multi-Disciplinary Conference on Cognitive Methods in Situation Awareness and Decision Support (CogSIMA), 2016, pp. 63–67.
- [32] J. Ni, A. Zhang, X. Lin, and X. S. Shen, “Security, privacy, and fairness in fog-based vehicular crowdsensing,” IEEE Communications Magazine, vol. 55, no. 6, pp. 146–152, 2017.
- [33] M. Raya, P. Papadimitratos, V. D. Gligor, and J.-P. Hubaux, “On data-centric trust establishment in ephemeral ad hoc networks,” in IEEE INFOCOM 2008 - The 27th Conference on Computer Communications, 2008, pp. 1238–1246.
- [34] Z. Li and C. T. Chigan, “On joint privacy and reputation assurance for vehicular ad hoc networks,” IEEE Transactions on Mobile Computing, vol. 13, no. 10, pp. 2334–2344, 2014.
- [35] M. B. Mollah, J. Zhao, D. Niyato, Y. L. Guan, C. Yuen, S. Sun, K.-Y. Lam, and L. H. Koh, “Blockchain for the internet of vehicles towards intelligent transportation systems: A survey,” IEEE Internet of Things Journal, vol. 8, no. 6, pp. 4157–4185, 2021.
- [36] J. Konečný, H. B. McMahan, F. X. Yu, P. Richtárik, A. T. Suresh, and D. Bacon, “Federated learning: Strategies for improving communication efficiency,” 2017.
- [37] S. Samarakoon, M. Bennis, W. Saad, and M. Debbah, “Federated learning for ultra-reliable low-latency v2v communications,” in 2018 IEEE Global Communications Conference (GLOBECOM), 2018, pp. 1–7.
- [38] M. Han, K. Xu, S. Ma, A. Li, and H. Jiang, “Federated learning-based trajectory prediction model with privacy preserving for intelligent vehicle,” Int J of Intelligent Sys, vol. 37, no. 12, pp. 10 861–10 879, Dec. 2022.
- [39] H. R. Feyzmahdavian, A. Aytekin, and M. Johansson, “An asynchronous mini-batch algorithm for regularized stochastic optimization,” IEEE Transactions on Automatic Control, vol. 61, no. 12, pp. 3740–3754, 2016.
- [40] L. T. Phong, Y. Aono, T. Hayashi, L. Wang, and S. Moriai, “Privacy-preserving deep learning via additively homomorphic encryption,” IEEE Transactions on Information Forensics and Security, vol. 13, no. 5, pp. 1333–1345, 2018.
- [41] C. Dwork, “Differential privacy,” in Proceedings of the 33rd International Conference on Automata, Languages and Programming - Volume Part II, ser. ICALP’06. Berlin, Heidelberg: Springer-Verlag, 2006, p. 1–12. [Online]. Available: https://doi.org/10.1007/11787006_1
- [42] L. T. Phong, Y. Aono, T. Hayashi, L. Wang, and S. Moriai, “Privacy-preserving deep learning via additively homomorphic encryption,” IEEE Transactions on Information Forensics and Security, vol. 13, no. 5, pp. 1333–1345, 2018.
- [43] A. Machanavajjhala, J. Gehrke, D. Kifer, and M. Venkitasubramaniam, “L-diversity: privacy beyond k-anonymity,” in 22nd International Conference on Data Engineering (ICDE’06), 2006, pp. 24–24.
- [44] T. Zhu, G. Li, W. Zhou, and P. S. Yu, “Differentially private data publishing and analysis: A survey,” IEEE Transactions on Knowledge and Data Engineering, vol. 29, no. 8, pp. 1619–1638, 2017.
- [45] X. Li, X. Ying, and M. C. Chuah, “Grip++: Enhanced graph-based interaction-aware trajectory prediction for autonomous driving,” 2020.
- [46] P. Maymounkov and D. Mazières, “Kademlia: A Peer-to-Peer Information System Based on the XOR Metric,” in Peer-to-Peer Systems, G. Goos, J. Hartmanis, J. Van Leeuwen, P. Druschel, F. Kaashoek, and A. Rowstron, Eds. Berlin, Heidelberg: Springer Berlin Heidelberg, 2002, vol. 2429, pp. 53–65.
- [47] A. Kosba, A. Miller, E. Shi, Z. Wen, and C. Papamanthou, “Hawk: The blockchain model of cryptography and privacy-preserving smart contracts,” in 2016 IEEE Symposium on Security and Privacy (SP), 2016, pp. 839–858.
- [48] H. B. McMahan, E. Moore, D. Ramage, S. Hampson, and B. A. y Arcas, “Communication-efficient learning of deep networks from decentralized data,” in International Conference on Artificial Intelligence and Statistics, 2016. [Online]. Available: https://api.semanticscholar.org/CorpusID:14955348
- [49] S. Ko, K. Lee, H. Cho, Y. Hwang, and H. Jang, “Asynchronous federated learning with directed acyclic graph-based blockchain in edge computing: Overview, design, and challenges,” Expert Systems with Applications, vol. 223, p. 119896, 2023.
- [50] J. Halkias and J. Colyar, “Us highway 101 dataset,” Federal Highway Administration (FHWA), Tech. Rep. FHWA-HRT-07-030, 2007.
- [51] ——, “Us highway 80 dataset,” Federal Highway Administration (FHWA), Tech. Rep. FHWA-HRT-07-030, 2007.
- [52] X. Huang, P. Wang, X. Cheng, D. Zhou, Q. Geng, and R. Yang, “The apolloscape open dataset for autonomous driving and its application,” IEEE Transactions on Pattern Analysis and Machine Intelligence, vol. 42, no. 10, pp. 2702–2719, 2020.
- [53] N. Deo, A. Rangesh, and M. M. Trivedi, “How Would Surround Vehicles Move? A Unified Framework for Maneuver Classification and Motion Prediction,” IEEE Trans. Intell. Veh., vol. 3, no. 2, pp. 129–140, Jun. 2018.
- [54] N. Deo and M. M. Trivedi, “Multi-Modal Trajectory Prediction of Surrounding Vehicles with Maneuver based LSTMs,” in 2018 IEEE Intelligent Vehicles Symposium (IV). Changshu: IEEE, Jun. 2018, pp. 1179–1184.
- [55] A. Gupta, J. Johnson, L. Fei-Fei, S. Savarese, and A. Alahi, “Social gan: Socially acceptable trajectories with generative adversarial networks,” in 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition, 2018, pp. 2255–2264.
- [56] J. An, W. Liu, Q. Liu, L. Guo, P. Ren, and T. Li, “DGInet: Dynamic graph and interaction-aware convolutional network for vehicle trajectory prediction,” Neural Networks, vol. 151, pp. 336–348, Jul. 2022.
- [57] R. Chandra, U. Bhattacharya, A. Bera, and D. Manocha, “Traphic: Trajectory prediction in dense and heterogeneous traffic using weighted interactions,” in Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), June 2019.
- [58] X. Liang, Y. Ma, Y. Feng, and Z. Liu, “Ptr-ppo: Proximal policy optimization with prioritized trajectory replay,” 2021.