Rate compatible reconciliation for continuous-variable quantum key distribution using Raptor-like LDPC codes
Abstract
In the practical continuous-variable quantum key distribution (CV-QKD) system, the postprocessing process, particularly the error correction part, significantly impacts the system performance. Multi-edge type low-density parity-check (MET-LDPC) codes are suitable for CV-QKD systems because of their Shannon-limit-approaching performance at a low signal-to-noise ratio (SNR). However, the process of designing a low-rate MET-LDPC code with good performance is extremely complicated. Thus, we introduce Raptor-like LDPC (RL-LDPC) codes into the CV-QKD system, exhibiting both the rate compatible property of the Raptor code and capacity-approaching performance of MET-LDPC codes. Moreover, this technique can significantly reduce the cost of constructing a new matrix. We design the RL-LDPC matrix with a code rate of 0.02 and easily and effectively adjust this rate from 0.016 to 0.034. Simulation results show that we can achieve more than 98% reconciliation efficiency in a range of code rate variation using only one RL-LDPC code that can support high-speed decoding with an SNR less than -16.45 dB. This code allows the system to maintain a high key extraction rate under various SNRs, paving the way for practical applications of CV-QKD systems with different transmission distances.
I Introduction
Quantum key distribution (QKD) pirandola2019advances ; RevModPhys.92.025002 ; diamanti2016practical enables two spatially separated parties—named Alice and Bob—for extracting a symmetrical string of secret keys using the fundamental properties of quantum mechanics. Currently, there are two mainstream schemes for QKD research, namely, discrete-variable QKD (DV-QKD)bennett2014quantum ; gisin2002quantum ; scarani2009security and continuous-variable QKD (CV-QKD) grosshans2002continuous ; grosshans2003quantum ; braunstein2005quantum ; weedbrook2012gaussian . In DV-QKD systems, the polarization or phase of a single-photon state is encoded by key information, whereas in CV-QKD systems, the amplitude and phase quadrature of quantum states are encoded. The CV-QKD system offers good application prospects for the implementation of classical telecom components, thus attracting considerable research attention. Research activities have primarily focused on extending the transmission distance and improving secret key rate between two parties in the CV-QKD systemsjouguet2013experimental ; Zhang_2019 ; zhang2020PRL ; GUO2021 .
A typical CV-QKD system consists of two phases. First, Alice prepares a quantum state and transmits it to Bob through a quantum channel; Bob uses a homodyne or heterodyne detector to measure the raw data. Second, both parties extract the secret key by performing postprocessing through a classical channel. In postprocessing, the information reconciliation step, particularly the performance of error correction, will limit the transmission distance and secret key rate of the system. Currently, commonly used reconciliation methods are slice reconciliation PhysRevA.90.042329 and multidimensional reconciliation leverrier2008multidimensional ; jouguet2011long . The slice reconciliation method is more suitable for short-distance transmission systems and can extract multiple bits of information from a single pulse. The multidimensional reconciliation method provides an effective way to correct low signal-to-noise ratio (SNR) Gaussian continuous variables using classical error correction codes zhaoshenmei ; baizengliang . Increased reconciliation efficiency, which can be achieved using near-Shannon-limit error correction codes with low rates in the information reconciliation step, is a technical challenge in extending transmission distance and improving secret key rate of CV-QKD systems milicevic2018quasi ; zhou2019 .
Multi-edge type low-density parity-check (MET-LDPC) codes richardson2002multi exhibiting low rates combined with the reverse multidimensional reconciliation scheme can achieve excellent correction performance in the CV-QKD system. The SNR of an optical quantum channel is low in such a long-distance transmission, thus requiring a low code rate and long code block length. For example, when the SNR is less than -15 dB, the code rate is less than 0.02 and the block length has an order of leverrier2009unconditional . However, designing a parity-check matrix with good performance is complex, and it is extremely complicated to design all matrices for different SNRs wang2017efficient . Therefore, to improve the reconciliation efficiency, the system must change the modulation variance at Alice’s side to ensure the receiving variables achieve the target SNR. The frame error rate and postprocessing speed must also be considered in the practical application of the CV-QKD system 9057665 ; li2020high . Multiple interactions and decoding steps of Alice and Bob in the information reconciliation step will increase system delay. This paper focuses on a method achieving good error correction performance that can be flexibly implemented in different scenarios in the practical system.
Further, we introduce Raptor-like LDPC (RL-LDPC) codes 6744572 into the CV-QKD system. These codes possess a rateless Raptor code property as well as good error correction performance of MET-LDPC codes under a low SNR. The raptor-like structure is important for providing rate compatibility and obtaining capacity-approaching performance, particularly at low code rates 7045568 ; LIU20151582 . The generator matrix of the Raptor codes is randomly generated; thus, it is impossible to remove all short cycles in the matrix, and the error correction performance is unstable. Unlike the Raptor codes 1638543 ; zhou2019 , the structure of each additional parity bit is explicitly designed through density evolution in the RL-LDPC codes. Currently, the RL-LDPC code is mainly used in wireless broadcast communications. We simply design a RL-LDPC code with a rate of 0.02 and adjust this code rate. Numerical results show good performance of the RL-LDPC codes, which are designed to meet the requirements of the practical CV-QKD system in real-time and realize high-speed processing in different application scenarios.
The remaining of this paper is organized as follows: In Sec. II, the structure of RL-LDPC codes is briefly introduced and its application to the postprocessing of the CV-QKD system is provided. In Sec. III, we describe the construction of low-rate RL-LDPC codes and realize rate compatibility. In Sec. IV, several simulations are performed to show the good performance of the RL-LDPC codes. Finally, the conclusions of this paper are summarized in Sec. V.
II Postprocessing using RL-LDPC codes
In this section, we introduce the RL-LDPC codes into the CV-QKD system. First, we provide additional details about the RL-LDPC codes. As the name implies, such codes are special LDPC codes with the structure of the Raptor code. Raptor codes are the first rateless codes with linear time encoding and decoding, and they have been used in several applications with large data transmissions. The RL-LDPC codes retain the characteristics of Raptor codes to some extent.
II.1 Base matrix structure of RL-LDPC codes
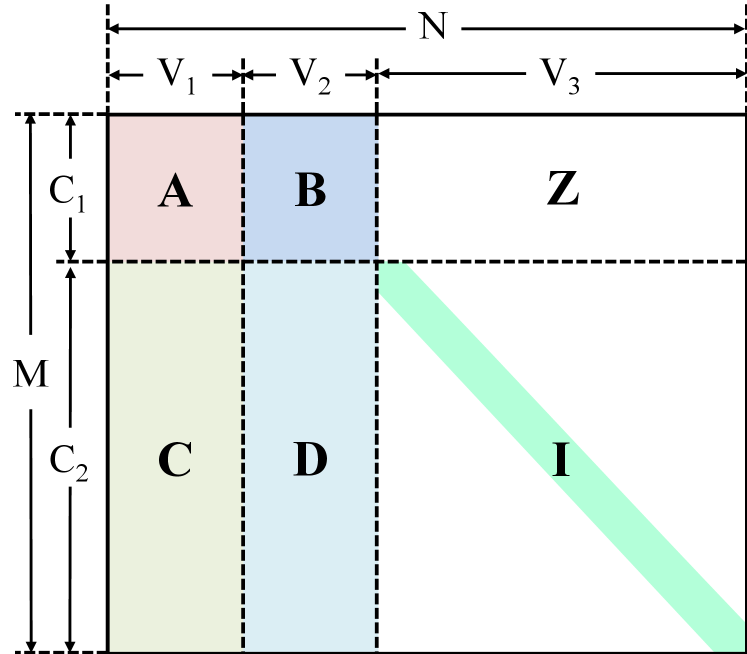
Generally, the Raptor codes include two parts: linear precoder (such as LDPC codes) and Luby transform (LT) codes. Its Tanner graph is concatenated with LDPC and LT code Tanner graphs and can be transformed into a parity-check matrix, similar to the structure in Figure 1. This figure shows the base parity-check matrix structure of the RL-LDPC codes. As we can see that the base parity-check matrix with a size of is constructed using different size submatrices, different colors represent different types of edges. , , , and are four sparse subparity-check matrices, and their sizes are , , , and , respectively. is a zero matrix with a size of , and is an identity matrix with a size of . It can be seen from this figure that the sizes of matrices , , , and are related. Hence, their sizes can be adjusted based on their degree distributions, or the two submatrices can be merged into one. If submatrices and are considered as precoding matrices and and as generator matrices of LT codes, the structure shown in Figure 1 will represent the parity-check matrix of Raptor codes. The RL-LDPC codes can be regarded as special MET-LDPC codes, which consist of different types of edges.
In this paper, we design low-rate LDPC codes based on the long-distance CV-QKD system structure. This structure not only maintains the capacity-approaching performance of MET-LDPC codes but also exhibits the rate compatibility of Raptor codes.
II.2 Procedure of postprocessing
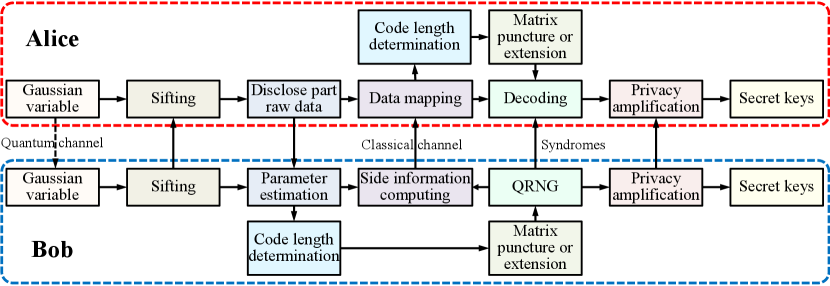
Here, we introduce RL-LDPC codes into the CV-QKD system and explain its operation in postprocessing. The schematic of postprocessing is shown in Figure 2. First, Alice prepares Gaussian-modulated coherent states and transmits them to Bob, who measures one of the quadratures using a homodyne detector. After Bob measures the quantum states received from Alice through a quantum channel, both parties start extracting the secret keys through a public channel, which is assumed to be noiseless and error-free.
Postprocessing mainly includes four steps, namely, base sifting, parameter estimation Leverrier2010Finite ; jouguet2012analysis , information reconciliation grosshans2003virtual ; van2004reconciliation , and privacy amplification bennett1995generalized . Base sifting implies that Bob transmits his selected measurement base to Alice, and then Alice retains the relevant data. Next, Bob determines quantum channel parameters and estimates the secret key rate using the parameter estimation step. The optimal code rate can be calculated using the current SNR and target reconciliation efficiency and can be used to determine the size of the RL-LDPC parity-check matrix needed in the information reconciliation step. According to the optimal code rate, Alice and Bob puncture or extend the base parity-check matrix. Owing to a long transmission distance in this work, we adopt the reverse multidimensional reconciliation scheme. Here, Bob uses a quantum random number generator to generate the initial secret keys to calculate the side information to be transmitted to Alice. Alice determines the size of the matrix of the RL-LDPC code based on the length of the received-side information and then corrects the errors after data mapping. Both parties can hold a set of common sequences when Alice successfully decodes the information. Following the above steps, Eve may have collected sufficient information during her observations of the quantum and classical channels. Hence, privacy amplification is an indispensable step to extract final secret keys from common sequences between Alice and Bob.
Considering the finite-size effects, the secret key rate of the CV-QKD system using one-way reverse reconciliation is expressed as Leverrier2010Finite ; pirandola2019advances ; zhang2020PRL
| (1) |
where is the proportion of the number of key extraction in the total number of data exchanged by Alice and Bob, is the reconciliation efficiency, and is the classical mutual information shared between Alice and Bob. is the reconciliation frame error rate. is the maximum of the Holevo information that Eve can obtain from the information of Bob. is the finite-size offset factor. Because of the imperfect reconciliation scheme, the secret key rate is reduced and the range of the protocol is limited. To achieve a high secret key rate, high reconciliation efficiency is needed under low SNRs, and should be as low as possible.
III Design of low-rate RL-LDPC codes
In this section, we show the construction of a low-rate RL-LDPC code. In the information reconciliation step of the CV-QKD system, the MET-LDPC codes are combined with multidimensional reconciliation owing to their capacity-approaching performance, particularly in the low code rate regime. First, we construct a base matrix of the RL-LDPC code with a rate of 0.02 based on the degree distribution of MET-LDPC codes.
Usually, parity-check matrices are used to represent MET-LDPC codes. The rows of matrices represent check nodes, and the columns represent variable nodes. Here, let be a multi-edge degree, and let denote (vector) variables. Each element of indicates the number of edges of type incident to a node. The sum of these elements in is referred to as the degree of . We use to denote . Two multivariate polynomials are used to determine the degree distribution of the MET-LDPC codes; they are as defined
| (2) |
where coefficient () is the proportion of variable nodes (check nodes) of the multi-edge degree . In eq.(2), and are called the degree distributions of variable and check nodes, respectively. The rate of MET-LDPC codes is expressed as
| (3) |
For an unpunctured ensemble, the sum of is 1 and the sum of is . Here, the codeword length of the MET-LDPC codes is , and () is the number of variables (check) nodes with edge type . The threshold of a code is defined as the maximum standard deviation of the noise channel that can be corrected when the code length is infinite and the maximum number of iterations is sufficiently large. The threshold can be estimated using the density evolution method. Table 1 presents the degree distributions for the MET-LDPC code rates of 0.05 and 0.02 wang2017efficient . The two MET-LDPC codes exhibit excellent error correction performance and are usually used in long-distance CV-QKD systems. The degree distributions possess three edge types, and the multinomial () can be partitioned into three (two) multinomials.
| Code rate | Degree distribution | Threshold |
| 0.05 | 3.674 | |
| 0.02 | 5.91 |
Next, we consider the MET-LDPC code in Table 1 as an example to design a RL-LDPC code, as shown in Figure 1. The code length is . For convenience, we consider the submatrices and as one matrix, denoted by , and and as one matrix, denoted by . The base matrix of the RL-LDPC code can be obtained by concatenating the submatrices , , and . In this MET-LDPC code, there are large numbers of variable nodes with degrees of 1, which are represented by the degree distribution and , corresponding exactly to the identity matrix , with a size of . Thus, we only need to design and according to the multinomials. Ref. richardson2002multi shows that the concatenation of a high-rate code and a large number of single parity-check codes can achieve a threshold close to the Shannon limit. The submatrix comprising edge type-1 can be represented by the degree distribution and . This matrix of size can also be expressed using the following polynomials according to its row and column weights:
| (4) |
The above equation shows that there are 22500 columns with a weight of 2, 17500 columns with a weight of 3, 10625 rows with a weight of 3, and 9375 rows with a weight of 7 in matrix . Similarly, the submatrix comprising edge type-2 can be represented as
| (5) |
The random construction method PEG2005 can be employed to construct the parity-check matrices using the parameters of the above two matrices. Finally, we must concatenate the submatrices simply to achieve the base matrix with a code rate of 0.02. To obtain a high secret key rate in the long-distance CV-QKD system, high reconciliation efficiency under a low SNR is required. Reconciliation efficiency is a significant parameter for evaluating the performance of the information reconciliation step. In the CV-QKD system, reconciliation efficiency can be expressed as
| (6) |
where is the code rate, which equals , is the Shannon capacity, and at SNR of the additive white Gaussian noise (AWGN) channel. From eq.(6), we know that one code with a fixed rate cannot maintain high reconciliation efficiency under different SNRs.
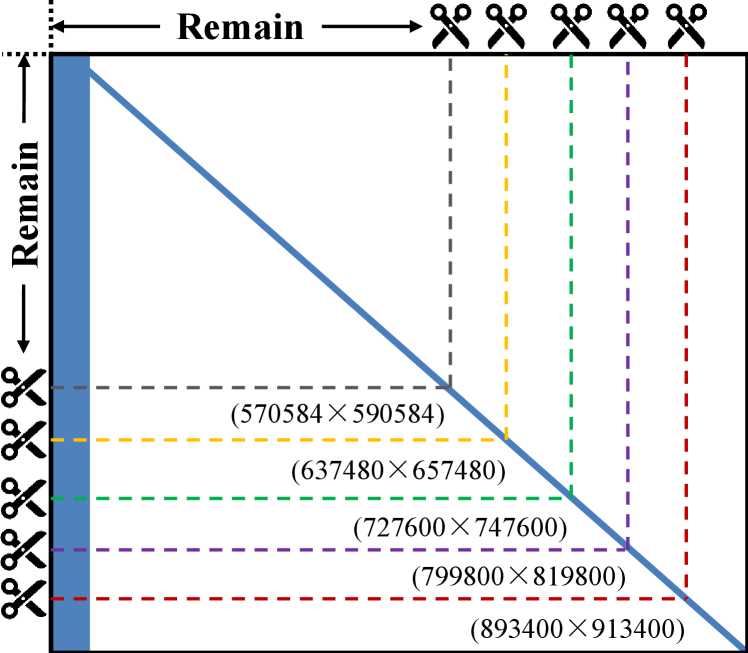
The introduced RL-LDPC codes exhibit rate compatibility similar to the Raptor codes. Figure 3 shows the method for generating different code rates using the designed base matrix. The same length of the base matrix is cut from the right and bottom sides, and the upper left corner of the base matrix is retained. The dotted lines represent the boundary of the target matrices. Assume that the punctured length is ; then, the code rate of the target matrix is modified by
| (7) |
Although rate compatibility can be easily achieved, the error correction performance of the target matrix is still a challenge. The code rate of the target matrix gradually increases as the base matrix is cut continuously, and its degree distribution also changes. The selection of the degree distribution is an important factor affecting the code performance; thus, the design of the submatrix must satisfy certain rules. In other words, after it is cut, the degree distribution will be changed according to a higher code rate than 0.02. In this work, we selected the code of rate as 0.05 in Table 1 for reference. Let denote the check node degree distribution of submatrix in reference codes. When the code rate of the target matrix gradually increases, must satisfy
| (8) |
where denotes the check node degree distribution of submatrix in target codes and is the rate of reference codes.
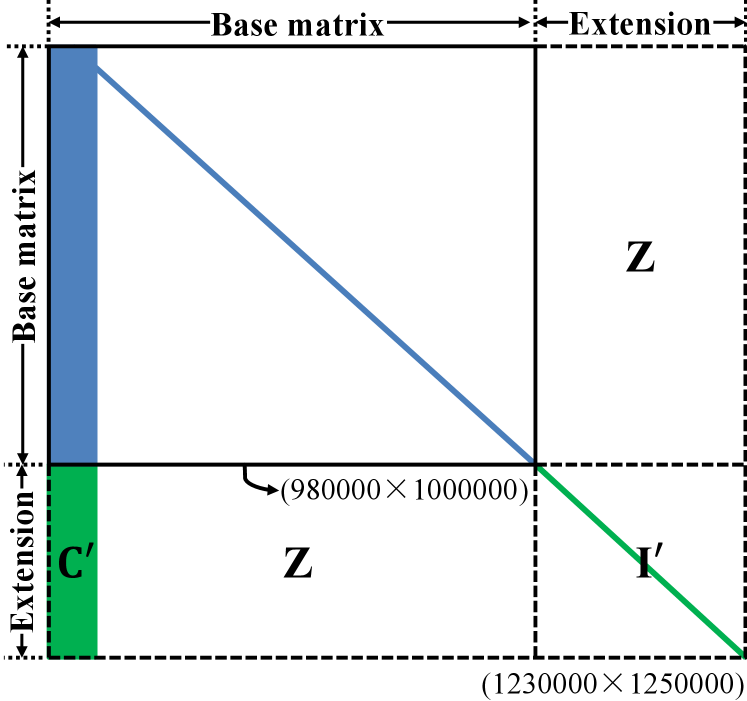
However, it can be seen from eq.(7) that puncture can only increase the code rate of the designed base matrix. When the SNR reduces, the error correction performance will deteriorate; thus, it is necessary to determine a way to reduce the code rate of the designed base matrix. Fortunately, we can simply reduce the code rate of the RL-LDPC codes and maintain promising performance. Figure 4 shows the schematic diagram of extending the base matrix. We must only fill in some data on the right and bottom sides of the designed base matrix. More simply, only the extended matrix needs to be designed here. Assume the extended length is ; the code rate of the target matrix is modified by
| (9) |
In theory, will change with an increase in according to eq.(8). A lower rate code than 0.02 should be selected as a reference, and denotes its degree distribution. At the time of writing this paper, no degree distribution of code rate less than 0.02 for long-distance CV-QKD systems has been reported and the focus of this paper is not to design it. Thus, we use to construct matrix . The code rate of the extended matrix is 0.016. Using the above simple steps, we can achieve matrices with code rates between 0.016 and 0.034 based on the designed RL-LDPC code.
IV Simulation results
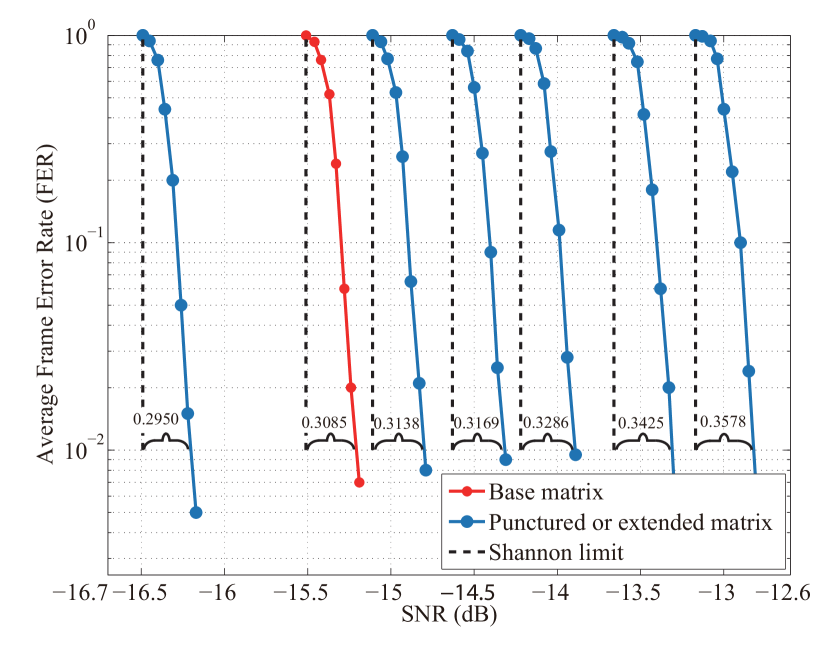
In this section, we show the performance of the low rate RL-LDPC code in CV-QKD system. First, we simulate a Gaussian variable with different SNRs in the AWGN channel. Then, the error correction performance is analyzed based on the log-likelihood ratio belief propagation (LLR-BP) using multidimensional reconciliation. Here, we adopt an eight-dimensional reconciliation because it shows the highest performance compared with other dimensions (details for Appendix. A.1). Figure 5 shows the of the designed RL-LDPC code. From this figure, we can observe that with increasing , when , the gap from the Shannon limit becomes larger, which implies that the error correction performance is worse. We can conclude that the performance of the smallest two submatrices tends to decrease further because when the size of the matrix becomes smaller, the length of the code becomes shorter as well as the degree distribution of the matrix changes. The error correction performance of the extended matrix with a code rate of 0.016 is slightly better than that of the base matrix, mainly because of the long code length of the former.
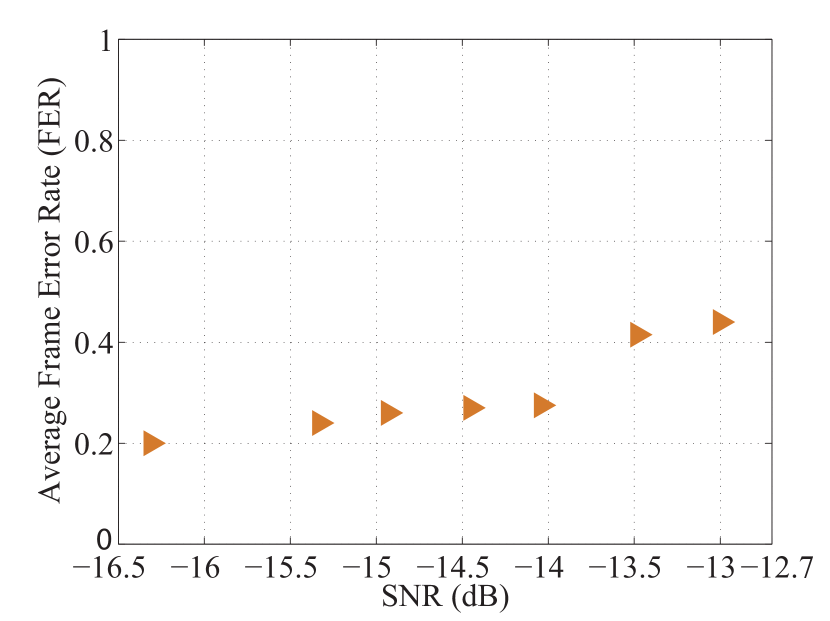
Figure 6 shows the performance of the RL-LDPC code at reconciliation efficiency . Here, the LLR-BP decoding algorithm is employed using an eight-dimensional reconciliation method. Although the SNR fluctuates significantly, the decoding success rate of the RL-LDPC codes can still be kept stable. These codes can significantly reduce the complexity of constructing a matrix while maintaining the performance.
| Code rate | 0.016 | 0.02 | 0.02 | 0.0304 | ||
| Block length | 657,480 | |||||
|
4,187,300 | 3,337,500 | 3,337,500 | 2,181,429 | ||
|
32 | 64 | 64 | 96 | ||
| 98% | 98% | 96% | 95% | |||
| 0.75 | 0.76 | 0.453 | 0.375 | |||
| Max iterations | 400 | 400 | 200 | 200 | ||
|
8.14 | 8.17 | 16.41 | 16.47 |
The decoding latency of the RL-LDPC code on the GPU platform is tested to meet the real-time processing requirements of the CV-QKD system. We use the parallel decoding method of ref. wang2018high00 on a single NVIDIA TITAN Xp GPU. Table 2 presents the test results for fore codes. The number of codewords refers to the number of code blocks decoded in parallel using the same block length and code rate. By reducing the maximum iterations, both the decoding speed and can be improved. The lower the SNR, the higher the required reconciliation efficiency. Therefore, low-rate codes need more iterations to be decoded. In comparison, the maximum iterations of high-rate code can be appropriately reduced to improve the decoding speed. For a submatrix with a code rate of 0.0304, the total number of edges is one-third less than that of the base matrix. Although more codewords can be processed simultaneously, the decoding speed cannot improve significantly. Thus, the decoding speed is linearly related to the number of iterations when the GPU memory is fully utilized.
.
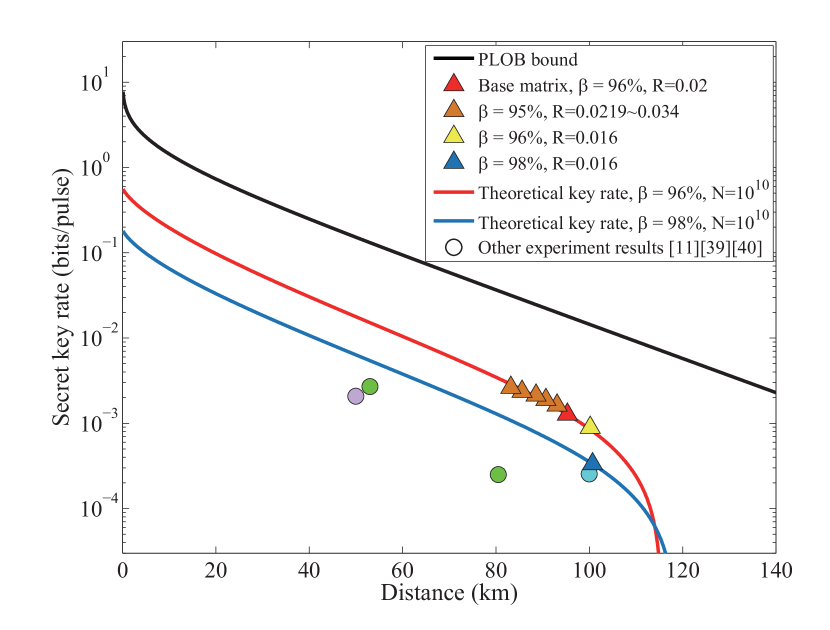
In Ref. zhou2019 , it is shown that the optimal modulation variance can further improve the secret key rate. Our work also allows the system to maintain the optimal modulation variance without sacrificing the target SNR. According to eq.(1), the tradeoff between and is considered to obtain high secret key rate. Furthermore, we can use all the data to estimate the channel parameter and extract the secret keys Wang2019 .
Figure 7 shows the finite-size secret key rate of the designed RL-LDPC codes with the transmission distance. The eight triangles are the simulation results of seven designed matrices under different . Here, we consider that the selection of and will maximize the results, and the block length is . The yellow and blue triangles represent the extended matrix with a code rate of 0.016 at and , respectively. Notably, the secret key rate can be extracted at high speed when the SNR is as low as 0.0226 (-16.45 dB). Although a high reconciliation efficiency is suitable for long distances, the low can significantly improve the secret key rate. The system repetition rate is not considered in this simulation result. Other experimental results jouguet2013experimental ; wang201525 ; huang2016long with the standard loss of a single-mode optical cable are also shown in Figure 7. Here, we also compared the key rate with the PLOB bound pirandola2017fundamental , i.e., the fundamental limit of repeaterless quantum communications. The RL-LDPC codes offer the advantages of practical applications in the CV-QKD system.
V Conclusion
The practical application of the CV-QKD system is increasingly urgent and requires high -performance postprocessing, particularly in terms of reconciliation efficiency, frame error rate, and processing speed. Error correction steps are the key to restrict the above factors. This paper introduces RL-LDPC codes into the CV-QKD system. These codes exhibit the rateless property of Raptor codes as well as good error correction performance of MET-LDPC codes under a low SNR. We design the RL-LDPC matrix with a code rate of 0.02 and randomly select six target rates as reference. The seven designed matrices show positive performance and can meet the system requirements. Furthermore, our work allows the system to operate under the optimal modulation variance to improve the secret key rate. Our work can promote the application of the CV-QKD system in a practical environment.
In our work, we do not consider designing a matrix in the lower-triangular form to reduce encoding complexity because the improvement in encoding is not significant on the GPU platform. If the application is considered in a small integrated system, such as a field-programmable gate array platform, the lower-triangular form will be a good choice. Using quasi-cyclic codes to construct the RL-LDPC matrix can reduce memory usage and decoder implementation complexity.
VI Acknowledgments
This work was supported by the Key Program of National Natural Science Foundation of China (Grant No. 61531003), the National Natural Science Foundation of China (Grant No. 62001041), and the Fund of State Key Laboratory of Information Photonics and Optical Communications.
References
- (1) S. Pirandola, U. L. Andersen, L. Banchi, M. Berta, D. Bunandar, R. Colbeck, D. Englund, T. Gehring, C. Lupo, C. Ottaviani, J. L. Pereira, M. Razavi, J. S. Shaari, M. Tomamichel, V. C. Usenko, G. Vallone, P. Villoresi, and P. Wallden, Adv. Opt. Photon. 12, 1012 (2020).
- (2) F. Xu, X. Ma, Q. Zhang, H.-K. Lo, and J.-W. Pan, Rev. Mod. Phys. 92, 025002 (2020).
- (3) E. Diamanti, H.-K. Lo, B. Qi, and Z. Yuan, npj Quantum Inform. 2, 16025 (2016).
- (4) C. H. Bennett and G. Brassard, Proc. of IEEE Int. Conf. on Comp., Syst. and Signal Proc., Bangalore, India pp 175–179 (1984).
- (5) N. Gisin, G. Ribordy, W. Tittel, and H. Zbinden, Rev. Mod. Phys. 74, 145 (2002).
- (6) V. Scarani, H. Bechmann-Pasquinucci, N. J. Cerf, M. Duˇsek, N. L¨utkenhaus, and M. Peev, Rev. Mod. Phys. 81, 1301 (2009).
- (7) F. Grosshans and P. Grangier, Phys. Rev. Lett. 88, 057902 (2002).
- (8) F. Grosshans, G. Van Assche, J. Wenger, R. Brouri, N. J. Cerf, and P. Grangier, Nature 421, 238 (2003).
- (9) S. L. Braunstein and P. Van Loock, Rev. Mod. Phys. 77, 513 (2005).
- (10) C. Weedbrook, S. Pirandola, R. García-Patrón, N. J. Cerf, T. C. Ralph, J. H. Shapiro, and S. Lloyd, Rev. Mod. Phys. 84, 621 (2012).
- (11) P. Jouguet, S. Kunz-Jacques, A. Leverrier, P. Grangier, and E. Diamanti, Nat. Photonics 7, 378 (2013).
- (12) Y. Zhang, Z. Li, Z. Chen, C. Weedbrook, Y. Zhao, X. Wang, Y. Huang, C. Xu, X. Zhang, Z. Wang, M. Li, X. Zhang, Z. Zheng, B. Chu, X. Gao, N. Meng, W. Cai, Z. Wang, G. Wang, S. Yu, and H. Guo, Quantum Sci. Technol. 4, 035006 (2019).
- (13) Y. Zhang, Z. Chen, S. Pirandola, X. Wang, C. Zhou, B. Chu, Y. Zhao, B. Xu, S. Yu, and H. Guo, Phys. Rev. Lett. 125, 010502 (2020).
- (14) H. Guo, Z. Li, S. Yu, and Y. Zhang, Fundamental Research 1, 96-98 (2021).
- (15) P. Jouguet, D. Elkouss, and S. Kunz-Jacques, Phys. Rev. A 90, 042329 (2014).
- (16) A. Leverrier, R. Alléaume, J. Boutros, G. Zémor, and P. Grangier, Phys. Rev. A 77, 042325 (2008).
- (17) P. Jouguet, S. Kunz-Jacques, and A. Leverrier, Phys. Rev. A 84, 062317 (2011).
- (18) S. M. Zhao, Z. G. Shen, H. Xiao, and L. Wang, Sci. China-Phys. Mech. Astron. 61, 090323 (2018).
- (19) Z. L. Bai, X. Y. Wang, S. S. Yang, and Y. M. Li, Sci. China-Phys. Mech. Astron. 59, 614201 (2016).
- (20) M. Milicevic, C. Feng, L. M. Zhang, and P. G. Gulak, npj Quantum Inform. 4, 21 (2018).
- (21) C. Zhou, X. Wang, Y. Zhang, Z. Zhang, S. Yu, and H. Guo, Phys. Rev. Applied 12, 054013 (2019).
- (22) T. Richardson, R. Urbanke,et al., Workshop honoring Prof. Bob McEliece on his 60th birthday, California Institute of Technology, Pasadena, California pp 24–25 (2002).
- (23) A. Leverrier and P. Grangier, Phys. Rev. Lett. 102, 180504 (2009).
- (24) X. Wang, Y. Zhang, S. Yu, B. Xu, Z. Li, and H. Guo, Quantum Inf. Comput. 17, 1123 (2017).
- (25) S. Yang, Z. Lu, and Y. Li, J. Lightwave Technol. 38, 3935 (2020).
- (26) Y. Li, X. Zhang, Y. Li, B. Xu, L. Ma, J. Yang, and W. Huang, Sci Rep 10, 1 (2020).
- (27) S. I. Park, Y. Wu, H. M. Kim, N. Hur, and J. Kim, IEEE Trans. Broadcast. 60, 239 (2014).
- (28) T. Chen, K. Vakilinia, D. Divsalar, and R. D. Wesel, IEEE Trans. Commun. 63, 1522 (2015).
- (29) J. Liu and R. C. de Lamare, AEU-Int. J. Electron. Commun. 69, 1582 (2015).
- (30) A. Shokrollahi, IEEE Trans. Inf. Theory 52, 2551 (2006).
- (31) A. Leverrier, F. Grosshans, and P. Grangier, Phys. Rev. A 81, 062343 (2010).
- (32) P. Jouguet, S. Kunz-Jacques, E. Diamanti, and A. Leverrier, Phys. Rev. A 86, 032309 (2012).
- (33) F. Grosshans, N. J. Cerf, J. Wenger, R. Tualle-Brouri, and P. Grangier, Quantum Inf. Comput. 3, 535 (2003).
- (34) G. Van Assche, J. Cardinal, and N. J. Cerf, IEEE Trans. Inf. Theory 50, 394 (2004).
- (35) C. H. Bennett, G. Brassard, C. Crépeau, and U. M. Maurer, IEEE Trans. Inf. Theory 41, 1915 (1995).
- (36) X.-Y. Hu, E. Eleftheriou, and D.-M. Arnold, IEEE Trans. Inf. Theory 51, 386 (2005).
- (37) X. Wang, Y. Zhang, S. Yu, and H. Guo, Sci. Rep. 8, 10543 (2018).
- (38) X. Wang, Y. Zhang, S. Yu, and H. Guo, Quantum Inf. Process. 18, 264 (2019).
- (39) C. Wang, D. Huang, P. Huang, D. Lin, J. Peng, and G. Zeng, Sci. Rep. 5, 14607 (2015).
- (40) D. Huang, P. Huang, D. Lin, and G. Zeng, Sci. Rep. 6, 19201 (2016).
- (41) S. Pirandola, R. Laurenza, C. Ottaviani, and L. Banchi, Nat. Commun. 8, 15043 (2017).
Appendix A
A.1 Multidimensional reconcliaition method
The central idea of multidimensional reconciliation is to reformulate the attenuated Gaussian physical channel into a virtual Binary input AWGN (BI-AWGN) channel. Here, we consider an eight-dimensional reconciliation as an example to introduce the multidimensional reverse reconciliation method. After the quantum transmission and sifting steps, Alice and Bob share correlated Gaussian sequences. The detailed analysis of a set of data is presented. First, they combine eight continuous-variable sequences into an eight-dimensional vector. Let and corresponding to the correlated Gaussian vectors of Alice and Bob, respectively; then, with , where is multidimensional noise variance. Then, Alice and Bob normalize their Gaussian variables and to and , respectively, where and . The vectors and are uniformly distributed on the unit sphere of . Bob randomly generates a binary sequence , and maps it to the unit sphere:
| (10) |
Next, Bob calculates the mapping function with using the following formula:
| (11) |
where is the coordinate of the vector under the orthonormal basis and it can be expressed as . is the orthogonal matrix of size and has been provided in the Appendix of Ref. leverrier2008multidimensional .
Then, Bob transmits the function to Alice through a public classical authenticated channel. Alice operates the same data mapping on x to map the Gaussian variables to , which is the noisy version of .
After the above steps, the virtual BI-AWGN channel with binary input and continuous -variable output is established. Then, Alice uses the RL-LDPC codes to recover from .