Performance Optimization in RSMA-assisted Uplink xURLLC IIoT Networks with Statistical QoS Provisioning
Abstract
Industry 5.0 and beyond networks have driven the emergence of numerous mission-critical applications, prompting contemplation of the neXt-generation ultra-reliable low-latency communication (xURLLC). To guarantee low-latency requirements, xURLLC heavily relies on short-blocklength packets with sporadic arrival traffic. As a disruptive multi-access technique, rate-splitting multiple access (RSMA) has emerged as a promising avenue to enhance quality of service (QoS) and flexibly manage interference for next-generation communication networks. In this paper, we investigate an innovative RSMA-assisted uplink xURLLC industrial internet-of-things (IIoT) (RSMA-xURLLC-IIoT) network. To unveil reliable insights into the statistical QoS provisioning (SQP) for our proposed network with sporadic arrival traffic, we leverage stochastic network calculus (SNC) to develop a dependable theoretical framework. Building upon this theoretical framework, we formulate the SQP-driven short-packet size maximization problem and the SQP-driven transmit power minimization problem, aiming to guarantee the SQP performance to latency, decoding, and reliability while maximizing the short-packet size and minimizing the transmit power, respectively. By exploiting Monte-Carlo methods, we have thoroughly validated the dependability of the developed theoretical framework. Moreover, through extensive comparison analysis with state-of-the-art multi-access techniques, including non-orthogonal multiple access (NOMA) and orthogonal multiple access (OMA), we have demonstrated the superior performance gains achieved by the proposed RSMA-xURLLC-IIoT networks.
Index Terms:
next-generation ultra-reliable and low-latency communications (xURLLC), stochastic network calculus, rate-splitting multiple access (RSMA), industrial internet-of-things.I Introduction
With the rapid evolution of mobile wireless network technologies, there has been a proliferation of numerous high-stack control and mission-critical emergent industrial applications, such as metaverse, robot control, and industrial automation [1, 2]. These industrial applications have sparked unprecedented stringent quality of service (QoS) requirements, encompassing flexible interference management, robust multi-access, impeccable reliability, and resilient low latency, prompting people’s envisioning for neXt-generation ultra-reliable and low-latency communications (xURLLC) [1, 3, 4, 5, 6]. xURLLC stands as a pivotal cornerstone within the wireless IIoT ecosystems, the heightened anticipation regarding xURLLC has accelerated the development and customized standardization of Industry 5.0 and beyond networks [7, 2, 1].
In IIoT scenarios requiring precision critical to mission success, base station (BS) and IIoT devices are typically deployed within confined environments. These IIoT devices transmit short-packet data, awakened periodically by internal events and sporadically triggered by external events, via the uplink to BS [8]. The BS seamlessly forwards these data to the data fusion center (DFC), where actionable insights are promptly derived and executed. Effectively meeting xURLLC’s low-latency requirements imperatives necessitates the organization of extensive short-packet data transmissions within dynamic wireless networks [5, 4, 3]. However, under Shannon regimes, the decoding error probability (DEP) associated with long blocklength channel codes virtually approaches zero [9, 10, 3], rendering the maximum achievable rate (MAR) inadequate for characterizing xURLLC’s short-packet data transmissions. To address this theoretical limitation, finite blocklength coding (FBC) theory has been advanced, revealing MARs for short-packet data transmissions and elucidating the intricate tradeoff between DEP and target latency [9, 10, 3, 4]. This tradeoff is influenced not only by blocklength but also by factors such as transmit power, inter-user interference, and transmission rate. Therefore, to guarantee xURLLC’s QoS requirements, there arises an urgent need for robust multi-access techniques that provide more flexible interference management, higher spectrum efficiency (SE), and broader coverage.
Rate-splitting multiple access (RSMA), positioned as a candidate technique for next-generation wireless networks, has garnered widespread attention owing to its flexible interference management, effective resource sharing, and superior SE [11, 12, 13]. In uplink RSMA scenarios, users split their transmitted messages into multiple streams, allocating suitable transmit power to each stream based on specific power allocation schemes [14]. At the BS receiver, successive interference cancellation (SIC) is performed to decode each stream in designated orders, subsequently combining and reconstructing these streams. Through message splitting, RSMA facilitates flexible management of inter-user interference in the uplink without resorting to time sharing among users to achieve capacity [11, 12, 13]. Remarkably, non-orthogonal multiple access (NOMA) falls within the subset of RSMA, with the distinction that NOMA does not involve the splitting of users’ messages. RSMA’s message splitting mechanism naturally aligns with core services (e.g., xURLLC) with sporadic access request behavior.
I-A Motivations and Challenges
Although RSMA has demonstrated promise in enhancing the QoS in next-generation wireless networks, recent research has predominantly concentrated on downlink multi-antenna and multi-access scenarios under Shannon regimes with long blocklengths [15, 16, 17]. Studies reveal that uplink RSMA can realize the optimal rate region of a -user Gaussian Multiple Access Channel (MAC) by exploiting up to virtual point-to-point Gaussian channels generated through message splitting, thereby providing superior reliability, sum-throughput, and lower latency compared to non-orthogonal multiple access (NOMA) [18] and orthogonal multiple access (OMA) [14]. Furthermore, most studies on uplink RSMA are conducted under Shannon regimes with long blocklengths [19, 20, 21], while the exploration of RSMA-assisted xURLLC under FBL regimes is still in its infancy, accompanied by various challenges.
On the one hand, the stringent low-latency demands of IIoT devices necessitate xURLLC to operate under FBL regimes, underscoring the need to investigate the DEP and total throughput of uplink RSMA-assisted xURLLC networks. However, RSMA’s flexible interference management, involving message splitting and combining, potentially introduces complexity to networks and poses challenges for seamless xURLLC integration [5, 12, 11]. On the other hand, previous research endeavors on xURLLC have predominantly focused on deterministic QoS provisioning (DQP) mechanisms, which are insufficient for analyzing the QoS requirements of extreme and rare events [4, 1, 3, 22, 2, 23]. Specifically, xURLLC demands reliability, sub-1 ms latency, statistical QoS provisioning (SQP), and relies on short-blocklength packets with sporadic arrival traffic, presenting unparalleled challenges to the existing Industrial Internet [4, 1]. Moreover, given the highly time-varying nature of wireless fading channels, DQP fails to accurately capture the queueing behavior of xURLLC traffic [4, 3, 22]. This deviates from the fundamental design principles mandated by xURLLC, which involve analyzing the tail distribution of stringent QoS, underscores the need for a paradigm shift. Consequently, a thorough understanding of statistical metrics associated with rare and extreme events, known as the tail distribution, is essential to accommodate xURLLC’s stringent QoS requirements [4, 3, 22].
Although embracing the SQP mechanism for xURLLC appears more feasible, there is a dearth of relevant studies in this area, leaving the underlying principles enigmatic [2, 1, 3, 4, 23, 22]. Currently, SQP theory championed by stochastic network calculus (SNC), has gained extensive traction [24, 25, 26]. SNC has evolved into a prominent methodology providing dependable theoretical insights into the SQP performance of latency-sensitive services [4, 3, 22]. Nevertheless, current endeavors fall short of providing sufficient guidance for xURLLC’s SQP, and existing state-of-the-art solutions for xURLLC operate independently, lacking direct compatibility and seamless integration [27, 28, 29, 30, 31, 32]. Therefore, tailoring an innovative RSMA-assisted transmission framework for xURLLC looms large.
I-B Related Work
State-of-the-art research endeavors have extensively focused on uplink RSMA under Shannon regimes with long blocklengths [19, 20, 21, 33], and relatively little research has focused on uplink RSMA under FBL regimes [34], let alone considering the SQP-based tail analysis for uplink RSMA-assisted xURLLC networks. The authors in [19] have investigated a two-user uplink cooperative RSMA (C-RSMA) scheme, which jointly optimizes beamforming and device transmit power. In [20], authors have tackled the optimization problem of maximizing the minimum SE of uplink RSMA-assisted user-centric massive MIMO networks. To enhance SE and user fairness, the authors in [21] have proposed a novel C-RSMA scheme for uplink user cooperation. Additionally, the authors in [33] have studied the optimization problems of power allocation and decoding order, and have proposed a low-complexity user-pair-based resource allocation algorithm to minimize the maximum latency. To study the impact of target rate and blocklength on the DEP and throughput performance, the authors in [34] have investigated the performance of uplink RSMA under FBL regimes.
xURLLC underscores extreme and rare events such as 99.9999% reliability and sub-1 ms latency [1, 35]. Currently, some relevant studies have explored the statistical QoS provisioning for xURLLC [4, 3, 22, 36, 37, 38]. In [4], we have proposed a NOMA-assisted uplink xURLLC network and analyzed the tail distributions of latency, age-of-information (AoI), and reliability of xURLLC leveraging SNC theory. To explore xURLLC’s fundamentals and performance tradeoffs, we have developed an xURLLC-enabled massive MIMO network and proposed a theoretical framework for statistical QoS provisioning analysis for xURLLC by leveraging and promoting SNC theory [3]. In [22], the authors have proposed a 360∘ virtual reality (VR) streaming architecture with statistical QoS provisioning by developing an SNC-based SQP theoretical framework from delay and rate perspectives. To fulfill QoS guarantees for URLLC slicing, the authors in [36] have proposed an SNC-based URLLC slicing allocation scheme, which effectively ensures the QoS violation probability remains consistently lower than the target value over the long term with a certain probability. To investigate the violation probability of end-to-end (E2E) latency for target services in IIoT, the authors in [37] have introduced an SNC-based cascaded theorem to evaluate the service capability of xURLLC networks and studied the service processes across various wireless fading channels.
I-C Main Contributions
To effectively overcome the aforementioned challenges, we have developed an innovative RSMA-assisted uplink xURLLC IIoT (RSMA-xURLLC-IIoT) network architecture under FBL regimes and imperfect channel-state-information (CSI) scenarios. To accurately capture the queueing behavior of sporadic xURLLC traffic, we have proposed an SNC-based SQP (SNC-SQP) theoretical framework to analyze the tail distribution of xURLLC’s QoS requirements. Building upon this theoretical framework, we have formulated two SQP-driven optimization problems tailored for the developed RSMA-xURLLC-IIoT network architecture and proposed a low-complexity algorithm to tackle them. Extensive simulations demonstrate the dependability of the proposed theoretical framework, and comprehensive comparisons validate the superior performance of our developed RSMA-xURLLC-IIoT network architecture. The primary contributions of this paper are summarized as follows:
-
•
We have developed an innovative RSMA-xURLLC-IIoT network architecture, which seamlessly bridges the integration gaps between RSMA and xURLLC under FBL regimes and imperfect CSI scenarios, providing flexible interference management, robust multi-access, impeccable reliability, and resilient low latency.
-
•
Leveraging SNC theory, we have proposed a dependable SNC-SQP theoretical framework. In particular, a novel terminology named statistical delay violation probability (SDVP) is introduced to access the SQP performance of xURLLC’s delay. Subsequently, we derive a closed-form upper-bounded expression for SDVP termed UB-SDVP to quantify SDVP accurately. Additionally, we have derived various closed-form expressions for the probability density functions (PDFs) of wireless channels involved in our developed RSMA-xURLLC-IIoT network architecture.
-
•
Building upon the proposed theoretical framework, we have delved into two critical optimization problems. The first one addresses the SQP-driven short-packet size maximization problem, which holds extraordinary significance for the IIoT since it guarantees not only the execution of complex machine instructions but also the accomplishment of coherent mission-critical tasks. The second problem deals with the SQP-driven transmit power minimization, which is also of great importance, particularly with the application prospect of massive xURLLC networks and battery-constrained IIoT devices. Then, we have proposed a low-complexity three-step sequential optimization algorithm (TSOO) for their efficient resolutions.
-
•
Extensive simulations have reliably demonstrated the effectiveness of our developed RSMA-xURLLC-IIoT network architecture. Comprehensive comparisons with results from Monte-Carlo methods rigorously validate the dependability of the proposed SNC-SQP theoretical framework. Furthermore, through comparisons with prevalent NOMA and OMA, we have further substantiated the remarkable performance gains achieved by our developed network architecture.
The remainder of this paper is organized as follows. In Sec. II, the RSMA-xURLLC IIoT network architecture is investigated. In Sec. III, the SNC-SQP theoretical framework is developed. In Sec. IV, two optimal SQP-driven optimization problems are formulated and addressed, followed by the performance evaluation and comparisons. Finally, a conclusion of this paper is given.
II RSMA-Assisted Uplink xURLLC IIoT Networks Architecture
As illustrated in Fig. 1, we consider an RSMA-assisted uplink IIoT network architecture accessed with multiple IIoT devices, where single-antenna IIoT devices simultaneously transmit short-packet data to a base station (BS) equipped with a single antenna. These IIoT devices are randomly grouped into pairs, each pair comprising two IIoT devices. The available spectrum is evenly divided into orthogonal subchannels, with each assigned to an IIoT device pair. Without loss of generality, we focus on a specific IIoT device pair designated as 111To facilitate the analysis of the SQP performance for the developed RSMA-xURLLC-IIoT network architecture, without loss of generality, this paper considers the single-antenna setup, which is consistent with the most prevailing uplink RSMA-assisted IIoT systems [34, 33, 21, 27]. While the multi-antenna setup enhances the performance of our developed RSMA-xURLLC-IIoT network architecture, it leads to the increased complexity of IIoT system design, which is also beyond the scope of this article. However, it is worth noting that the network architecture considered in this paper can be reasonably extended to multi-antenna scenarios, with recent references expected to provide valuable insights into this aspect[19, 20, 28, 3]..

II-A RSMA for Uplink xURLLC with Imperfect CSI
At the transmitter side, the message from IIoT device- at time slot is represented as . Following RSMA principles [12, 11], the message from IIoT device- is split into two components, denoted as . The message can be first encoded into the stream , where . These streams are mapped into finite-length codewords and transmitted over wireless fading channels. The received signal at the BS can be given as follows:
| (1) | ||||
where is the uplink transmit power of , represents the channel coefficient of IIoT device-, and is the Additive White Gaussian Noise. and denote the large-scale fading coefficient and small-scale fading coefficient, respectively.
In realistic industrial scenarios, channel estimation is essential since IIoT devices do not have perfect prior knowledge of channel states, and the actual channel coefficient can not be perfectly known. We consider each IIoT device- transmits a known orthogonal pilot sequence of length to the BS at the beginning of each time slot. As a result, the BS can obtain the minimum mean squared error (MMSE) channel estimation for IIoT device-. Given the obtained , the can be given as
| (2) |
where , with , and denotes the actual signal-noise-ratio (SNR) of IIoT device- during the training phase, which is constant and known at both transmitter and receiver. The channel estimation is Gaussian distributed as with . Then, the actual SNR can be given as follows:
| (3) |
where operators and represent the real part and phase of the complex number, respectively. The term follows a Gaussian distribution with variance , and the term of estimation error becomes quite small after sufficient pilot training, i.e., , which can be reasonably neglected in (3). In this case, the distribution of can be approximated as , where , , and denotes the average SNR of stream . If , then ; otherwise, . The blocklength used for short-packet communications and channel estimation is typically extremely limited. We consider that the blocklength of each time slot is , then only channel uses (CUs) available for short-packet data transmission.
At the receiver side, we consider that the streams are decoded in the order of 222The decoding order can be categorized into six cases, including (1) , (2) , (3) , (4) , (5) , (6) . Without loss of generality, we select the decoding order (3) in this paper.. Accordingly, is first decoded by treating and as noise. Then, the SINR of is represented as
| (4) |
If is decoded successfully, it can be reconstructed into , and then removed from the received signal . Secondly, is decoded by treating as noise. Thus, the SINR of can be expressed as
| (5) |
If is decoded successfully, it can also be reconstructed into , and removed from . Using a message combiner, the estimated message of IIoT device- is . Finally, the SINR of can be given as follows:
| (6) |
If is decoded successfully, it can be reconstructed into .
II-B Short-packet Data Communications Model
III SNC-Based SQP Theoretical Framework
In this section, we develop a dependable SNC-SQP theoretical framework. In particular, we introduce a novel terminology termed SDVP to characterize the tail distribution of delays. We derive the closed-form expressions for the PDFs of , , and , and subsequently induced the closed-form expression of UB-SDVP.
III-A Statistical Delay Violation Probability
To facilitate system-level analysis, we consider a statistical QoS-driven queueing system that employs the first-come-first-serve (FCFS) policy [3, 22, 26]. The cumulative arrival, service, and departure processes of within the time interval are given as , , and , respectively. Here, and represent the amount of short-packet data generated by and transmitted over wireless channels at time slot , respectively, while indicates the amount of short-packet data of that is successfully received at time slot . Then, to facilitate the analysis of SQP performance, we introduce a succinct and novel operator by leveraging moment generating function (MGF)-based SNC theory, which is termed min-deconvolution as follows:
Definition 1.
(min-deconvolution ): The min-deconvolution between and for stream can be given as follows:
| (8) |
where the parameter denotes the statistical QoS exponent of . and refer to the MGF of and inverse-MGF of , respectively 333 In SNC theory [3, 26], is exploited to characterize the decay rate of the queue length for statistical QoS-driven queueing systems. A larger corresponds to having stricter statistical QoS requirements. Conversely, a smaller implies looser statistical QoS requirements [3, 26]. Given a random process , the MGF of is denoted as , and the inverse-MGF of is [chen2023statistical, 26]..
Based on the operator min-deconvolution, we have the following Theorem 1:
Theorem 1.
Given and , the SDVP of can be expressed as follows:
| (9) |
where and denote the actual delay and target delay of , respectively.
Proof.
The proof of Theorem 1 is given in Appendix A. ∎
III-B The Closed-Form Expression of UB-SDVP
The promotion of MGF-SNC theory in Theorem 1 provides a crucial theoretical foundation for further deriving the closed-form expression of UB-SDVP for the developed RSMA-xURLLC-IIoT network architecture. We consider , , and have independent and identically distributed (i.i.d.) increments. Then, the MGF and the inverse-MGF of and can be respectively expressed as follows:
| (10a) | |||
| (10b) | |||
Combining Definition 1 with (10a) and (10b), we can derive the closed-form expression of UB-SDVP, as stated in Theorem 2.
Theorem 2.
Given the target delay , the SDVP of can be upper bounded by
| (11) |
where denotes the stability condition, and .
Proof.
According to Definition 1, the min-deconvolution between and can be expressed by (12), where . Substituting (10a) and (10b) into (12), respectively, we can derive the inequality (a). Based on inequality (a), equality (b) can be further deduced by taking variable replacement, i.e., . Inequality (c) can be derived by scaling the upper bound of the summation sign in (b) from to . Finally, according to the relevant properties of the geometric series, when the stability condition holds, equality (d) can be easily derived.
| (12) | ||||
So the proof of Theorem 2 can be concluded. ∎
Theorem 2 refers that further derivation of the inverse-MGF of the service process increment (i.e., ) and the MGF of the arrival increment (i.e., ) is essential to determine the closed-form expression for UB-SDVP. In this case, we consider the arrival process follows a Poisson distribution, as follows:
| (13) |
where denotes the average arrival rate of .
The inverse-MGF depends on , which varies from time slots, thus can be given by
| (14) |
where denotes the expectation operator of . From (14), the expression of p.d.f. for is indispensable for determining , which motivates Lemma 1 as follows:
Lemma 1.
Given the transmit power , the PDF of can be given as follows:
| (15) | ||||
where and .
Proof.
The proof of Lemma 1 is given in Appendix B. ∎
Combining Theorem 1, Theorem 2, and Lemma 1, the closed-form expression of UB-SDVP can be finally derived.
IV Problem Formulation And Solutions
In this section, building upon the proposed SNC-SQP theoretical framework, we delve into two critical optimization problems within our developed RSMA-xURLLC-IIoT network architecture:
-
•
The SQP-driven short-packet size maximization problem, the study of which is of extraordinary significance for IIoT networks since it guarantees not only the execution of complex machine instructions but also the accomplishment of coherent mission-critical tasks.
-
•
The SQP-driven transmit power minimization problem, which is also of great importance, particularly with the application prospect of massive xURLLC networks and battery-constrained IIoT devices.
Significantly, in both optimization problems, we jointly optimize the rate-allocation ratio, transmit power, and information bit number with the aim of maximizing short-packet size and minimizing transmit power for RSMA-xURLLC while guaranteeing the SQP performance, respectively.
IV-A The SQP-driven Short-packet Size Maximization Problem
Given the statistical QoS requirements , where denotes the threshold od SDVP, indicates the threshold of target delay, and represents the threshold of decoding error probability. As a result, the SQP-driven short-packet size maximization problem can be formulated as
| (16a) | ||||
| (16b) | ||||
| (16c) | ||||
| (16d) | ||||
| (16e) | ||||
| (16f) | ||||
where and , and (16a) defines the objective function and optimization variables; (16b) imposes a limit of on the SDVP of , where is the SDVP threshold; (16c) indicates the constraint on the decoding error probability of , with as the decoding error probability threshold; (16d) restricts the transmit power of IIoT device- to a maximum value of ; (16e) specifies the constraint on the short-packet size of IIoT device-. Finally, (16f) defines the range of values for the rate-splitting ratio.
IV-B The SQP-driven Transmit Power Minimization Problem
Given , the SQP-driven transmit power minimization problem can be formulated as
| (17a) | ||||
| (17b) | ||||
The intertwined co-channel interference [12, 11] and the highly-varying wireless fading channels [3, 4] in RSMA-xURLLC-IIoT network architecture render the analytical expression for SDVP in (16b) is inaccessible [26, 22]. Additionally, the closed-form expression for the decoding error probability of short-packet data transmission becomes exceedingly complex in FBL regimes [22]. As a result, and become exceedingly intractable and cannot be tackled analytically. Fortunately, by leveraging the proposed SNC-SQP theoretical framework, the inaccessible SDVP can be converted into the manageable UB-SDVP, which not only provides insightful theoretical guidance but also guarantees relatively conservative information bit transmission and power allocation schemes. Consequently, (16b) in and can be reformulated as follows:
| (18a) | |||
| (18b) | |||
where (18a) imposes a limit of on the UB-SDVP for stream , and represents the stability condition of UB-SDVP.
IV-C Proposed Solutions
Due to the complex constraints, solving and remains non-trivial. Therefore, we focus on exploring the intrinsic properties of and .
Corollary 1.
Proof.
The detailed proof of Corollary 1 can be found in Appendix C. ∎
From Corollary 1, can be easily determined by the one-dimensional search method. According to the properties of the convex function, we can easily determine through stochastic gradient descent (SGD) method444Due to space limitations, we have omitted detailed descriptions of one-dimensional search method and SGD method here since they are the fundamental content of optimization theory..
Corollary 2.
The decoding error probability given by is strictly decreasing with respect to , and strictly increasing with respect to .
Proof.
According to (7), we can obtain as follows:
From [3, Theorems 5], is a monotonically decreasing function with respect to . Moreover, it can be easily obtained that , thus .
Next, we prove the monotonic increasing property of with respect to . The partial derivative of in can be given by
| (19) |
The partial derivative of with respect to can be derived as follows:
| (20) |
In addition, we also investigate the intrinsic properties of UB-SDVP as follows:
Corollary 3.
The UB-SDVP given by (18a) is strictly decreasing with respect to transmit power , and strictly increasing with respect to the information bit number (i.e., the short-packet size) .
Proof.
The partial derivative of in can be given as follows:
| (21) |
It can be easily obtained that . Next, we examine the monotonicity of as follows:
| (22) |
Thus, is strictly decreasing with . And the partial derivative of in can be given as follows:
| (23) |
From Corollary 2 and Corollary 3, Theorem 3 can be derived as follows:
Theorem 3.
For , the optimal transmit power is determined as , and the optimal rate-allocation ratio is , where and represent the optimal short-packet sizes for and , respectively. As for , the optimal short-packet size is determined as , and the optimal rate-splitting ratio is .
Proof.
According to Corollary 2 and Corollary 3, the transmit power should be as high as possible to maximize the short-packet size. Therefore, we have . We denote that the optimal short-packet sizes for and are and , respectively. Based on (7), we have , thus, . Furthermore, we have to minimize the transmit power of short-packet communications, and we can obtain that since . ∎


Following RSMA principles [12, 11], is immune to interference, experiences co-channel interference from , and is affected by co-channel interference from both and . Based on the distinct characteristics of streams, we propose leveraging sequential optimization techniques to effectively solve and [39]. Specifically, we decompose and into three subproblems that need to be tackled sequentially. For Subproblem I, we focus on maximizing(or minimizing) the short-packet size (or transmit power) of stream . For Subproblem II and Subproblem III, we concentrate on maximizing (or minimizing) the short-packet size (or transmit power) of streams and , respectively.
It can be easily observed that if these three subproblems are optimized sequentially in the reverse decoding order, i.e., , and can be successfully decoupled into three independent subproblems [39]. For each subproblem, if and , it indicates that the short-packet size (or transmit power ) is too small (or large) and needs to be increase (or reduced); if or , it indicates that the short-packet size (or ) is too large (or small) and needs to be reduced (or increased). In this case, we propose a low-complexity algorithm termed the three-step sequential optimization algorithm (TSSO) to effectively tackle and . The detailed descriptions of TSSO are outlined in Algorithm 1.
IV-D Computational Complexity Analysis
Algorithm 1 primarily involves the one-dimensional search method and SGD algorithm. The complexity of the one-dimensional search method can be represented as , where and denote the step-length factor and step-length threshold, respectively. The complexity of the SGD method can be denoted as , where and indicate the step-length factor and convergence accuracy, respectively. As a result, the complexity of Algorithm 1 is , where is the number of iterations for Step i, .
V Performance Evaluation
In this section, extensive simulations are conducted to demonstrate the effectiveness of the proposed RSMA-xURLLC. The BS service radius is m, with each subcarrier operating at a bandwidth of MHz and a time-slot length of ms. Thus, the maximum available blocklength is CUs. The lengths of the orthogonal pilot sequence is set to CUs. The average arrival rate is kbps. The maximum uplink transmit power for each stream of IIoT devices is , the minimum short-packet size is bits, and the maximum short-packet size is bits. The noise power level is at dBm/Hz, and the path-loss factor is . Shadow fading is modeled as a lognormal distribution with a standard variance of dB and small-scale fading follows a Rayleigh fading distribution. The parameters involved in Algorithm 1 are as follows: , , , .
V-A Convergence Analysis
In Fig. 3 and Fig. 3, we showcase the superior convergence performance exhibited by the proposed TSSO in tackling and , respectively. Fig. 3 reveals that the upper and lower bounds associated with short-packet sizes of streams , , and rapidly converge as the number of iterations increases. Specifically, the short-packet sizes of streams , , and converge after , , and iterations, respectively. Similarly, it can be observed from Fig. 3 that the upper and lower bounds of the required transmit power for streams , , and also converge rapidly with increasing iterations. In particular, the transmit power of streams , , and converge after , , and iterations, respectively. Henceforth, the proposed TSSO algorithm demonstrates exceptional convergence performance, culminating in stable solutions within several iterations. Significantly, stream requires the highest transmit power but it can only accommodate the smallest short-packet size. Following closely is stream , while stream demands the lowest transmit power while supporting the largest short-packet data size. These distinctions primarily stem from the distinctive co-channel interference characteristics inherent to streams , , and themselves. Notably, experiences interference from both streams and simultaneously.
V-B Validation of SNC-SQP Theoretical Framework
As illustrated in Fig. 4, we substantiate the dependability of the developed SNC-SQP theoretical framework for capturing the SQP performance. We employ Monte Carlo methods to stochastically generate channels, meticulously evaluating the actual SDVP, yielding Sim-SDVP. Subsequently, we conduct a comprehensive comparative analysis by juxtaposing the UB-SDVP with the Sim-SDVP. The precisely calculated slopes of Sim-SDVP and UB-SDVP on the - axis for , , and reveal near-identical slopes within the logarithmic domain. This compellingly demonstrates the accuracy of the developed SNC-based SQP theoretical framework in capturing the SQP performance of our developed RSMA-xURLLC-IIoT network architecture. Moreover, the observable horizontal gap between UB-SDVP and Sim-SDVP primarily arises from the fact that our theoretical framework is grounded in -algebra theory [24, 26, 25], which can effectively utilize arrival processes and the distribution of fading channels to elucidate the queuing system of our developed RSMA-xURLLC-IIoT network architecture. These numerical results undeniably validate the feasibility of our theoretical framework in converting unavailable SDVP into manageable UB-SDVP, providing profound theoretical guidance for SQP-driven optimization problems. Additionally, the developed RSMA-xURLLC-IIoT network architecture incorporates the statistical QoS provisioning mechanism, which provides a more flexible and QoS-guaranteed short-packet size maximization scheme and transmit power allocation scheme, in contrast to traditional deterministic QoS provisioning mechanisms.

V-C Comprehensive Performance Comparison
To comprehensively evaluate the effectiveness of our developed RSMA-xURLLC-IIoT network architecture, we conduct an exhaustive performance comparison with state-of-the-art multi-access techniques exploited in current IIoT networks, including NOMA and OMA [4, 12, 11].
As shown in Fig. 5, the relationship between the maximum short-packet size and target delay is investigated. We have carefully examined the sequential optimization process of streams , , and conducted by our proposed TSSO algorithm, the performance of the proposed schemes across varied scenarios, and comparisons with NOMA and OMA. It can be easily seen that as the target delay increases, the maximum short-packet size supported by the developed RSMA-xURLLC-IIoT network architecture improves as the target delay becomes relaxed. Moreover, it can be observed that increasing the allocated blocklength or relaxing the SDVP threshold contributes to enhancing the maximum short-packet size. With CUs and , the developed RSMA-xURLLC-IIoT network architecture outperforms NOMA and OMA schemes by margins of and , respectively.

As depicted in Fig. 6, the relationship between minimum transmit power and target latency is explored. It is readily apparent that when the target delay is relatively relaxed, the minimum transmit power required to guarantee the expected QoS requirements rapidly decreases. It demonstrates that the minimum required transmit power of our network architecture is sensitive to the target delay. Furthermore, increasing the allocated blocklength and relaxing the SDVP threshold effectively reduce the required minimum transmit power. Under CUs and , compared to NOMA and OMA schemes, the developed RSMA-xURLLC-IIoT network architecture achieves performance improvements in terms of power consumption of and , respectively.




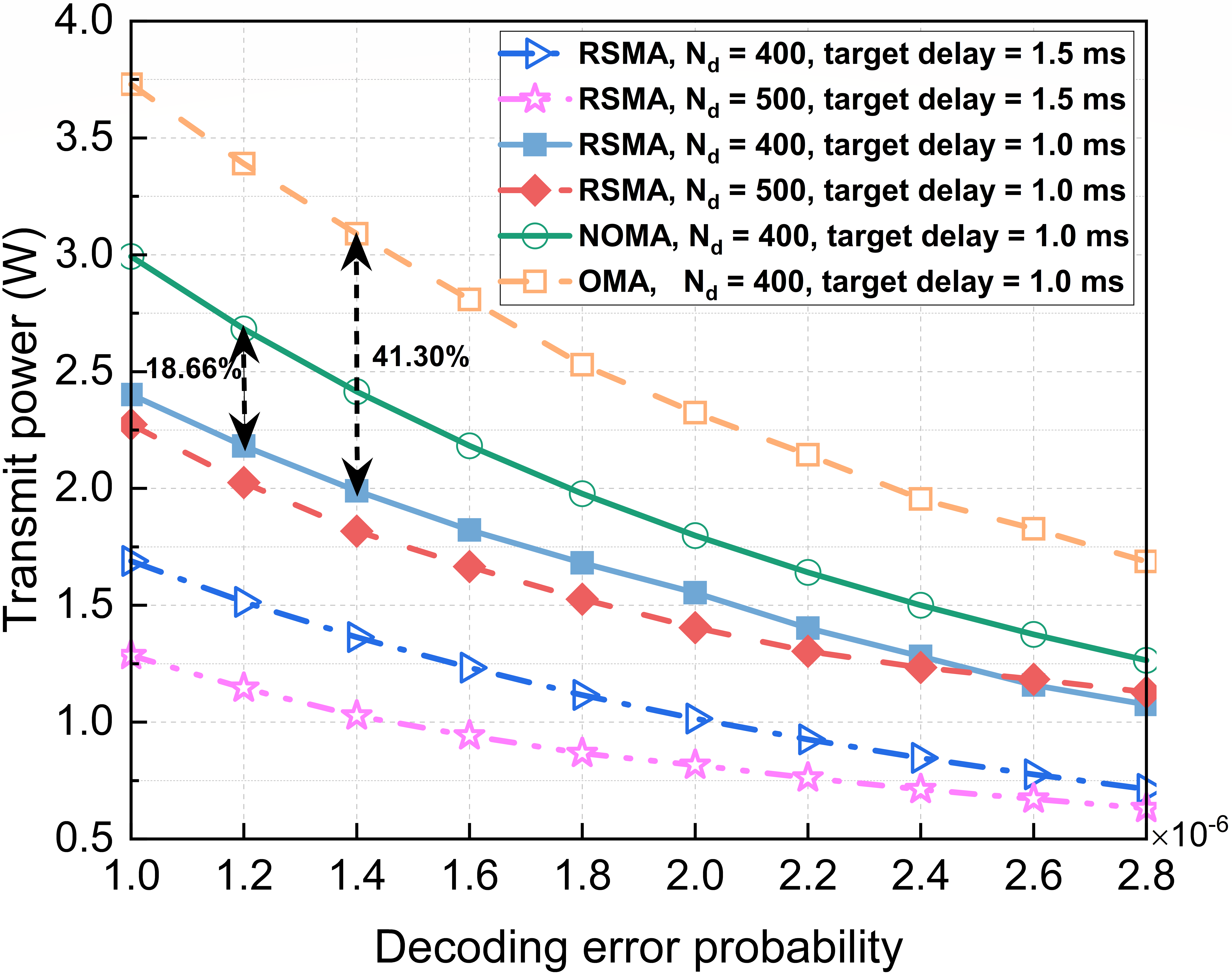
In Fig. 7, we investigate the relationship between the maximum short-packet size and the reliability of xURLLC compared to NOMA and OMA schemes across various scenarios. It can be observed that as the SDVP threshold and DEP threshold become more relaxed, the short-packet size supported by our proposed RSMA-xURLLC-IIoT network architecture can be significantly enhanced, which is extremely favorable for accomplishing diverse and complex mission-critical tasks in IIoT networks. Remarkably, supports the largest short-packet size, followed by , and finally . These distinctions primarily arise from the flexible interference management strategy of the developed RSMA-xURLLC-IIoT network architecture, which splits into and through rate splitting. As a result, , decoded first, experiences the most severe interference, including co-channel interference from and . Subsequent decoding of only experiences co-channel interference from . In contrast, the last decoded remains free from co-channel interference. It ultimately results in distinct co-channel interference characteristics for , , and . Despite more complex interference management in our proposed RSMA-xURLLC-IIoT network architecture, numerical results consistently underscore the remarkable performance advantages. In Fig. 7 (a) and Fig. 7 (b), we provide details of the sequential optimization process performed by the proposed TSSO. Numerical results distinctly demonstrate that, under different SDVP thresholds, our developed RSMA-xURLLC-IIoT network architecture can achieve and performance gains in terms of augmenting short-packet size compared to NOMA and OMA schemes, respectively. Moreover, as depicted in Fig. 7 (b), we further emphasize that under varying DEP thresholds, our developed RSMA-xURLLC-IIoT network architecture realizes performance enhancements of and when compared with NOMA and OMA schemes, respectively.
As depicted in Fig. 8, we have presented the minimum transmit power required by our developed RSMA-xURLLC-IIoT network architecture compared to NOMA and OMA schemes across various scenarios. It can be observed that as the SDVP threshold and DEP threshold become more lenient, the transmit power required to guarantee the expected SQP performance decreases significantly. Fig. 8 (a) shows that for varying SDVP thresholds, our developed RSMA-xURLLC-IIoT network architecture is capable of conserving and of the transmit power in terms of improving the power consumption for short-packet transmissions when compared to NOMA and OMA schemes, respectively. As depicted in Fig. 8 (b), with different DEP thresholds, our developed RSMA-xURLLC-IIoT network architecture outperforms NOMA and OMA schemes by achieving and performance improvements in terms of power consumption for short-packet transmission, respectively.
In Fig. 7 and Fig. 8, the fact-filled comparative analyses against NOMA and OMA schemes highlight that our developed RSMA-xURLLC-IIoT network architecture not only facilitates larger short-packet sizes but also achieves superior energy efficiency. This primarily stems from the fact that our developed network architecture empowers multiple access with the potential for concurrent non-orthogonal interference management by partially treating interference as noise while partially decoding it, thereby maximizing interference management optimally. In contrast, NOMA and OMA schemes exhibit disadvantages from two critical perspectives. On the one hand, the NOMA scheme essentially epitomizes an extreme interference management paradigm, which treats interference fully as noise and completely decodes interference [4, 12, 11]. This severely limits the flexible concurrent non-orthogonal interference management empowerment for multi-access IIoT networks, which in turn leads to poor spectral efficiency and more radio resource overhead. On the other hand, although the OMA scheme can facilitate interference-free multiple access through orthogonal resource allocation, it results in diminished spectrum efficiency. From Fig. 7 and Fig. 8, it can be observed that this deficiency becomes particularly pronounced for xURLLC services with stringent SQP requirements. Therefore, the orthogonal resource allocation in the OMA scheme is unsuitable for multi-access IIoT networks, which intuitively indicates that the OMA scheme can only support relatively small short packets and requires more transmit power to fulfill the expected SQP performance.
VI Conclusion And Future Outlook
In this paper, we have embarked on a pioneering exploration of xURLLC in Industrial 5.0 and beyond networks by investigating an innovative RSMA-xURLLC-IIoT network architecture. Leveraging SNC theory, we have proposed the SNC-SQP theoretical framework, which is precision-engineered to unveil dependable insights into the SQP analysis for our developed RSMA-xURLLC-IIoT network architecture. Building upon this theoretical framework, we have formulated two SQP-driven optimization problems that hold immense significance in massive-access IIoT networks. To engineer efficient resolution, we have harnessed sequential optimization techniques to propose a low-complexity TTSO algorithm. Through Monte-Carlo methods, we have thoroughly verified the dependability of the proposed SNC-SQP theoretical framework. Additionally, through extensive comparison analyses with prevalent NOMA and OMA schemes, we have further corroborated the superior performance gains achievable by our developed RSMA-xURLLC-IIoT network architecture.
For future endeavors, we have deeply contemplated four intimately intertwined perspectives. Firstly, we intend to expand our proposed system model to encompass massive MIMO scenarios, aiming to further elevate network performance [40]. Secondly, recognizing age-of-information (AoI) as another critical metric in mission-critical IIoT networks, we plan to incorporate the SQP analysis of AoI for xURLLC traffic into our forthcoming research. Moreover, under FBL regimes, the transmission of machine instructions entails potential security risks [4]. Therefore, the tailored physical layer security mechanisms crafted for our developed RSMA-xURLLC-IIoT network architecture are paramount to guarantee the privacy, stability, and integrity of data [41]. Henceforth, another significant facet of our future work entails drafting relevant security metrics for xURLLC, such as false alarm probability and missed detection probability, to combat malicious attacks and data breaches [42]. In essence, our proposed SNC-SQP theoretical framework requires further refinement, necessitating the inclusion of additional QoS indicators into the formulated SQP-driven optimization problems, along with corresponding algorithm enhancements.
Appendix A Proof of Theorem 1
| (A-1) |
According to Chernoff’s bound for (A-1) [26, 25], for any random process , the inequality holds for . By substituting it into A-1, we can immediately derive that
| (A-2) | ||||
Based on the definition of MGF, the right-hand side of (A-2) satisfies
| (A-3) | ||||
| (A-4) |
Appendix B Proof of Lemma 1
According to (6), stream is immune to co-channel interference, thus , and the closed-form expression of PDF for can be expressed as follows:
| (B-1) |
Based on (7), stream experiences co-channel interference from stream . The c.d.f. of can be given as follows:
| (B-2) | ||||
Taking the derivative of (B-2) with respect to , yields:
| (B-3) | ||||
| (B-4) | ||||
where and . So the proof of Lemma 1 is concluded.
Appendix C Proof of Corollary 1
We first prove the convexity property of the stability condition (18b). The stability condition (18b) can be rewritten as follows
| (C-1) | ||||
where the independent property between and is utilized, and the variable substitution is exploited. According to the definition of convex functions, we can obtain that and , where , the following inequality must hold:
| (C-2) | ||||
According to Hölder’s inequality, we can derive that
| (C-3) | ||||
where the inequality (a) in (C-3) holds due to the fact that
| (C-4) |
As a result, we define the function . and , the second-order derivation . Since and , it follows that reaches a local maximum for . Thus, , and (C-4) holds. Therefore, we show that the stability condition is convex.
Secondly, we prove the convexity property of the UB-SDVP (18a). According to the convexity property of stability condition, in the feasible domain , it follows that is a concave and positive function. Hence, its reciprocal is convex, i.e., [43]. According to the definition of convex function, and , we have
| (C-5) | ||||
By multiplying both the left and right sides of the inequality (C-5) by , we derive that
| (C-6) | ||||
By using Hölder’s inequality, we can derive that
| (C-7) | ||||
Due to the fact that . Then, the following inequality applies to the right side of (C-6), and we can derive that
| (C-8) | ||||
References
- [1] J. Park et al., “Extreme ultra-reliable and low-latency communication,” Nat. Electron., vol. 5, no. 3, pp. 133–141, Mar. 2022.
- [2] C. She et al., “A tutorial on ultrareliable and low-latency communications in 6G: Integrating domain knowledge into deep learning,” Proc. IEEE, vol. 109, no. 3, pp. 204–246, Mar. 2021.
- [3] Y. Chen et al., “Statistical QoS provisioning analysis and performance optimization in xURLLC-enabled massive MU-MIMO networks: A stochastic network calculus perspective,” IEEE Trans. Wireless Commun., pp. 1–1, 2024.
- [4] Y. Chen et al., “When xURLLC meets NOMA: A stochastic network calculus perspective,” IEEE Commun. Mag., Jul. 2023.
- [5] Y. Chen et al., “Enhancing xURLLC with RSMA-assisted massive-MIMO networks: Performance analysis and optimization,” arXiv preprint arXiv:2402.16027, 2024.
- [6] Y. Liu et al., “Deep reinforcement learning-based grant-free NOMA optimization for mURLLC,” IEEE Trans. Commun., vol. 71, no. 3, pp. 1475–1490, 2023.
- [7] W. Xian et al., “Advanced manufacturing in industry 5.0: A survey of key enabling technologies and future trends,” IEEE Trans. Ind. Informat., 2023.
- [8] M. Khoshnevisan et al., “5G industrial networks with CoMP for URLLC and time sensitive network architecture,” IEEE J. Sel. Areas Commun., vol. 37, no. 4, pp. 947–959, 2019.
- [9] Y. Polyanskiy et al., “Channel coding rate in the finite blocklength regime,” IEEE Trans. Inf. Theory, vol. 56, no. 5, pp. 2307–2359, May 2010.
- [10] W. Yang et al., “Quasi-static multiple-antenna fading channels at finite blocklength,” IEEE Trans. Inf. Theory, vol. 60, no. 7, pp. 4232–4265, Jul. 2014.
- [11] Y. Mao et al., “Rate-splitting multiple access: Fundamentals, survey, and future research trends,” IEEE Commun. Surv. Tutorials, 2022.
- [12] B. Clerckx et al., “A primer on rate-splitting multiple access: Tutorial, myths, and frequently asked questions,” IEEE J. Sel. Areas Commun., 2023.
- [13] A. Mishra et al., “Rate-splitting multiple access for 6G—part i: Principles, applications and future works,” IEEE Commun. Lett., vol. 26, no. 10, pp. 2232–2236, 2022.
- [14] B. Rimoldi and R. Urbanke, “A rate-splitting approach to the gaussian multiple-access channel,” IEEE Trans. Inf. Theory, vol. 42, no. 2, pp. 364–375, 1996.
- [15] H. Li et al., “Synergizing beyond diagonal reconfigurable intelligent surface and rate-splitting multiple access,” IEEE Trans. Wireless Commun., 2024.
- [16] O. Dizdar and S. Wang, “Rate-splitting multiple access for semantic-aware networks: an age of incorrect information perspective,” IEEE Wireless Commun. Lett., 2024.
- [17] H. Lei et al., “On secure mmWave RSMA systems,” IEEE Internet Things J., 2024.
- [18] L. Qin et al., “Joint transmission and resource optimization in NOMA-assisted IoVT with mobile edge computing,” IEEE Trans. Veh. Technol., pp. 1–16, 2024.
- [19] S. Khisa et al., “Power allocation and beamforming design for uplink rate-splitting multiple access with user cooperation,” IEEE Trans. Veh. Technol., 2024.
- [20] M. Sarker and A. O. Fapojuwo, “Uplink power allocation for RSMA-aided user-centric cell-free massive MIMO systems,” in 2023 IEEE 97th Vehicular Technology Conference (VTC2023-Spring). IEEE, 2023, pp. 1–5.
- [21] O. Abbasi et al., “Transmission scheme, detection and power allocation for uplink user cooperation with NOMA and RSMA,” IEEE Trans. Wireless Commun., vol. 22, no. 1, pp. 471–485, 2023.
- [22] Y. Chen et al., “Streaming 360-degree VR video with statistical QoS provisioning in mmWave networks from delay and rate perspectives,” arXiv preprint arXiv:2305.07935, 2023.
- [23] M. Bennis et al., “Ultrareliable and low-latency wireless communication: Tail, risk, and scale,” Proc. IEEE, vol. 106, no. 10, pp. 1834–1853, Oct. 2018.
- [24] H. Al-Zubaidy et al., “Network-layer performance analysis of multihop fading channels,” IEEE/ACM Trans. Networking, vol. 24, no. 1, pp. 204–217, Feb. 2014.
- [25] M. Fidler, “Survey of deterministic and stochastic service curve models in the network calculus,” IEEE Commun. Surv. Tutorials, vol. 12, no. 1, pp. 59–86, First Quarter 2010.
- [26] M. Fidler and A. Rizk, “A guide to the stochastic network calculus,” IEEE Commun. Surv. Tutorials, vol. 17, no. 1, pp. 92–105, Firstquarter 2014.
- [27] S. K. Singh et al., “RSMA for hybrid RIS-UAV-aided Full-Duplex communications with finite blocklength codes under imperfect SIC,” IEEE Trans. Wireless Commun., 2023.
- [28] X. Ou et al., “Resource allocation in MU-MISO rate-splitting multiple access with SIC errors for URLLC services,” IEEE Trans. Commun., 2022.
- [29] Y. Wang et al., “Flexible rate-splitting multiple access with finite blocklength,” IEEE J. Sel. Areas Commun., vol. 41, no. 5, pp. 1398–1412, 2023.
- [30] S. Kurma et al., “URLLC-based cooperative industrial IoT networks with nonlinear energy harvesting,” IEEE Trans. Ind. Informat., vol. 19, no. 2, pp. 2078–2088, 2022.
- [31] I. Muhammad et al., “Mission effective capacity—a novel dependability metric: A study case of multiconnectivity-enabled URLLC for IIoT,” IEEE Trans. Ind. Informat., vol. 18, no. 6, pp. 4180–4188, 2021.
- [32] S.-Y. Lien and D.-J. Deng, “Intelligent session management for URLLC in 5G open radio access network: A deep reinforcement learning approach,” IEEE Trans. Ind. Informat., vol. 19, no. 2, pp. 1844–1853, 2022.
- [33] J. Hu et al., “Low-complexity resource allocation for uplink RSMA in future 6G wireless networks,” IEEE Wireless Commun. Lett., vol. 13, no. 2, pp. 565–569, 2024.
- [34] J. Xu et al., “Rate-splitting multiple access for short-packet uplink communications: A finite blocklength analysis,” IEEE Commun. Lett., vol. 27, no. 2, pp. 517–521, 2023.
- [35] O. L. A. López et al., “Statistical tools and methodologies for ultrareliable low-latency communication—a tutorial,” Proc. IEEE, vol. 111, no. 11, pp. 1502–1543, 2023.
- [36] O. Adamuz-Hinojosa et al., “A stochastic network calculus (SNC)-based model for planning B5G uRLLC RAN slices,” IEEE Trans. Wireless Commun., vol. 22, no. 2, pp. 1250–1265, 2023.
- [37] P. Cui et al., “End-to-end delay performance analysis of industrial internet of things: A stochastic network calculus perspective,” IEEE Internet Things J., vol. 11, no. 3, pp. 5374–5387, 2024.
- [38] C. Wu et al., “Cross-layer optimization for statistical QoS provision in C-RAN with finite-length coding,” IEEE Trans. Commun., pp. 1–1, 2024.
- [39] X. Du et al., “Sequential optimization and reliability assessment method for efficient probabilistic design,” J. Mech. Des., vol. 126, no. 2, pp. 225–233, 2004.
- [40] G. Zheng et al., “Joint hybrid precoding and rate allocation for RSMA in near-field and far-field massive MIMO communications,” IEEE Wireless Commun. Lett., pp. 1–1, 2024.
- [41] L. Qin et al., “Energy-efficient blockchain-enabled user-centric mobile edge computing,” IEEE Trans. Cogn. Commun. Netw., pp. 1–1, 2024.
- [42] H. Forssell et al., “Physical layer authentication in mission-critical MTC networks: A security and delay performance analysis,” IEEE J. Sel. Areas Commun., vol. 37, no. 4, pp. 795–808, 2019.
- [43] S. P. Boyd and L. Vandenberghe, Convex optimization. Cambridge university press, 2004.