Percolation on complex networks: Theory and application
Abstract
In the last two decades, network science has blossomed and influenced various fields, such as statistical physics, computer science, biology and sociology, from the perspective of the heterogeneous interaction patterns of components composing the complex systems. As a paradigm for random and semi-random connectivity, percolation model plays a key role in the development of network science and its applications. On the one hand, the concepts and analytical methods, such as the emergence of the giant cluster, the finite-size scaling, and the mean-field method, which are intimately related to the percolation theory, are employed to quantify and solve some core problems of networks. On the other hand, the insights into the percolation theory also facilitate the understanding of networked systems, such as robustness, epidemic spreading, vital node identification, and community detection. Meanwhile, network science also brings some new issues to the percolation theory itself, such as percolation of strong heterogeneous systems, topological transition of networks beyond pairwise interactions, and emergence of a giant cluster with mutual connections. So far, the percolation theory has already percolated into the researches of structure analysis and dynamic modeling in network science. Understanding the percolation theory should help the study of many fields in network science, including the still opening questions in the frontiers of networks, such as networks beyond pairwise interactions, temporal networks, and network of networks. The intention of this paper is to offer an overview of these applications, as well as the basic theory of percolation transition on network systems.
keywords:
Percolation , Complex Network , Network Structure , Network Dynamics , Phase Transition and Critical Phenomena1 Introduction
In contrast to many other modern research fields, the network problem is often easy to define by abstracting from everyday life [1, 2]. For examples, how many people an epidemic can infect in a social contact network, whether a communication network can maintain its function after an intentional attack, which node has the largest impact in a social network, and so on [3, 4, 5, 6]. The key point of these problems with network involved can be summarized as a cluster forming process within a chosen fraction of nodes, those might be infected people, preserved nodes after an intentional attack, or individuals with the same opinion. In principle, these processes are easy to define, however, not so easy to solve.
Fortunately, in statistical physics, a profound theoretical system, called percolation theory, just touches this problem, i.e., the behaviors of a networked system when some of nodes or links are not available [7]. Indeed, when the network science was just a new rising topic, the percolation theory has already been widely used for explaining empirical results, and solving models [2]. Now, after more than twenty years’ development of network science, the percolation theory, including conceptions, analytical methods, and algorithms, can be found almost in all the research fields of network science.
It is known that the classical percolation in statistical physics only considers regular lattices, therefore, with these applications to complex networks, the percolation theory itself also has been enriched and developed. In recent hot areas of network science, such as higher-order networks [8, 9] and networks beyond pairwise interactions [10], models and methods of percolation have still been widely touched. This is obviously because the connection property must always be a key point to understand network structure and dynamics.
Due to importance of the percolation theory in the study of complex networks, almost all the review articles about networks have the relevant sections to introduce distinguishable developments and applications of percolation theory on complex networks, however, a systematic comparison and summary specifically from the perspective of percolation is still absent. This review article aims to fill this gap, and comb the scattered discussions on the network percolation and its applications, which can facilitate a wide area of sciences, ranging from physics and computer science to biology and sociology, as well as various branches of probability theory in mathematics.
1.1 Classical percolation
Percolation now usually refers to a class of models that describe geometric features of random media. In statistical physics, percolation theory is often accompanied by scaling law, fractal, self-organization criticality, and renormalization, which are all of immense importance theoretically in many diverse fields of physics [7]. Therefore, percolation has long served as a basic ideal model for demonstrating phase transition and critical phenomena. However, quite apart from the role percolation theory now plays, it originates from an honest applied problem in the study of gelation in the 1940s [11, 12, 13]. To be a mathematical subject, it first starts from Broadbent and Hammersley’s paper in 1957 [14], in which its name, and the geometrical and probabilistic concepts were introduced.
The study of percolation then becomes popularized in the physics community, and many of the open problems have been proposed and solved [15, 16, 17, 18, 19, 20, 21]. Now, the percolation theory has also been found to be of a broad range of applications to diverse problems. The applications in network science that this article focuses on are one of the typical representatives. This is also benefited from the development of computational technology, as the simulation plays a crucial role in the study of percolation [22].
In the following, we will firstly give a brief introduction to the percolation model, as well as some physical concepts and quantities involved.
1.1.1 Percolation process in random media
Imagine a large porous stone immersed in water. Does the water come into the core of the stone? If so, there must be some paths formed by the pores running through the stone. However, as a whole, the connection of any two adjacent pores is probabilistic, supposing the probability is . The problem thus reduces to whether there exist such paths for a given probability . This actually is a typical example of percolation problems. The connection of two adjacent pores, in the terminology of percolation, is called occupying the corresponding bond between the two pores, and hence is the occupied probability. Obviously, if is large enough, the core of the porous stone can be wetted. In that case, the connected pores are able to form a cluster that penetrates the stone. Accordingly, percolation theory is mainly concerned with the existence of such a cluster and its structure with respect to the occupied probability .
The above process is just a special case of the percolation process. The same question can also be proposed for many other systems constituted by random medium. Another typical example is the forest fire model. Suppose a burning tree can only ignite the trees in the adjacent sites, the destructiveness of the forest fire depends on the density of the trees, i.e., the probability of finding a tree on a site. This is also obviously a percolation process – when the adjacent trees form a cluster that can penetrate the entire forest, the fire could raze almost the entire forest; otherwise, the fire is constrained in a small area. Furthermore, similar regulations can also be applied to model the spreading of epidemics among individuals, where infected individuals can infect their neighbors probabilistically.
Although the soaking of porous stone, the forest fire and the spreading of epidemics seemingly belong to separated fields, the three are now converging in an intriguing manner. That is, is there a cluster of connected sites through the system? As is quite typical, it is actually easier to examine such an infinite cluster in an infinite system than just large ones. With the increasing of the probability , there must be a critical , called percolation threshold or critical point, below which such a cluster cannot be found. For a more detailed understanding of this criticality, the percolation model needs to be defined explicitly. That is what we are going to talk about.
1.1.2 Percolation model on lattices
To facilitate presentation, we consider a two-dimensional lattice here as shown in Fig.1 (a). Mathematically, each bond is occupied with probability or unoccupied with probability . Then, the occupied bonds connect the sites into clusters. This model is called bond percolation, which can be used to model the process of the soaking of porous stone and the spreading of epidemics. For the forest fire model, one often uses a slightly different percolation model, the so-called site percolation model. For this model, we occupy each site with probability rather than bonds as shown in Fig.1 (b). In general, the bond percolation is considered less general than the site percolation due to the fact that the bond percolation can be reformulated as a site percolation on a different lattice, but not vice versa.

The percolation theory mainly focuses on the emergence of the infinite cluster with the increasing of probability . To characterize this phenomenon, one often adopts the size of the giant cluster, which is defined as
| (1) |
Here, is the size of the system (site number), and is the number of sites in the largest cluster. As shown in Fig.1, with the increasing of , there must be a critical point , above which a non-zero can be found. This figures out the percolation transition of the system with respect to the control parameter , and is the corresponding order parameter.
In addition, there is another commonly used order parameter called wrapping probability, which is defined as the probability that a cluster wraps around the periodic boundary conditions on a regular lattice. For large systems, this probability is equal to the probability that the system percolates. This parameter is usually used to estimate the position of the percolation threshold, since it is a size-independent parameter at the critical point. Specifically, cluster wrapping can be defined in a number of different ways, such as wrapping around one direction, wrapping around one direction but not the other, and wrapping around both directions. This probability, however, cannot be well defined in network systems without spatial constraints, so that the size of the giant cluster is the preferred order parameter in network science.
To describe the features of finite clusters, the distribution of cluster sizes is also used, where is the number of the clusters with size . Sometimes, the normalized cluster number is also used to feature the cluster size distribution. It is obvious that , where is the average cluster size.
It must be pointed out that the average size is not the mean cluster size commonly used in percolation theory, which is defined as . It is not hard to know that is the probability that a randomly chosen site belongs to a cluster with size . Thus, the mean cluster size actually is the average size of the cluster that a randomly chosen site belongs to. Together with the characteristic length and the characteristic size , above which the clusters are exponentially scarce, these statistics are often used to describe and characterize the percolation transition [7]. The critical behaviors of these parameters will be briefly introduced in the next section.
Besides, there exist several other variants of percolation. For example, one could drop the assumption of independence of occupation, so that the occupation of a site or a bond could depend on the state of other sites or bonds. This type of percolation is often called dependent percolation, which is widely used in network science to model the spreading dynamics and the cascading process [3, 5, 6, 8, 23]. Such models will also be discussed in subsequent parts of this paper.
1.1.3 Percolation transition
The prerequisite for the study of critical phenomena is determining the percolation threshold . Figure 1 indicates that the site percolation and the bond percolation have different critical points. In fact, the threshold of bond percolation on square lattice can be solved exactly by the duality transformation or real-space renormalization [24, 7, 25, 26, 27], that is . However, there is no exact solution for site percolation on square lattice. Through Monte Carlo simulation, a good estimate of the critical point can be obtained, such as in Ref.[28], and in Ref.[29]. In Tab.1, we list the percolation thresholds for some typical systems.
| Network | Site | Bond |
|---|---|---|
| square lattice | [28], [29] | |
| triangular lattice | [30] | |
| honeycomb lattice | [31], [32], [33] | [30] |
| simple cubic | [29], [34], [35], [36], [37] | [34], [38], [39] |
| hypercubic | [40], [41], [42], [43], [35], [44] | [40], [41], [38], [45], [44] |
| hypercubic | [40], [35], [44] | [40], [38], [44] |
| hypercubic | [40], [35], [44] | [46], [40], [44] |
| hypercubic | [40], [35], [44] | [46], [40], [44] |
| Bethe lattice | ||
| ER network | [47, 48] | [47, 48] |
| SF network | [48] | [48] |
| tree-like network | [48] | [48] |
In the subcritical regime (), all clusters are finite and the size distribution has a tail which decays exponentially; in the supercritical regime (), an infinite cluster can be found in the system, and the size distribution of other finite clusters has a tail which decays slower than exponential. Near the critical point, some asymptotic behaviors can be found, referred to as critical phenomena. In the percolation theory, these behaviors are characterized by the critical exponents [7],
| (2) | ||||
| (3) | ||||
| (4) | ||||
| (5) | ||||
| (6) |
with relations
| (7) | ||||
| (8) |
Here, , , , , and are the so-called critical exponents, which determine the universal class of the percolation transition. Besides, at the critical point the characteristic length and size also have a relation
| (9) |
The exponent is often called fractal dimension [7, 49], characterizing the structure of the infinite cluster at the critical point. Assuming the dimension of the system is , there is another relation between critical exponents, called hyperscaling,
| (10) |
Note that this relation is also universal, and independent of the topological structure of the system. The phase transition theory points out that there is an upper critical dimension (for percolation ), above which the critical exponents become the same as that in mean-field theory [50, 51]. So this hyperscaling relation holds only for . It is also worth mentioning that the geometric structure of high-dimensional percolation clusters cannot be fully accounted for by the counterparts of random networks, though both of them have the mean-field nature [52].
In addition, the critical behavior below is different from the mean-field approximation which is valid away from the phase transition. For these systems, the renormalization group theory has made remarkable predictions about the behavior of the percolation near and at the threshold [53, 54]. In the renormalization group theory, there is also a lower critical dimension (for percolation ), below which there is no phase transition.
Furthermore, the universality principle states that the value of is determined by the local structure of the system, whereas the behavior of clusters that is observed near is independent of the local structure (lattice type and percolation type). In this sense, percolation is believed to be a substrate-dependent but model-independent process, and therefore, the critical exponents of the transition are only determined by the geometry of the system, and identical for the bond and site percolation. The critical exponents are thus more natural to be considered than the threshold , and there is no need to deal with the site and bond percolation, individually.
To end this subsection, it must be pointed out that the critical exponent is distinguishable for the site and bond percolation on scaling-free (SF) networks [55]. This is a special case derived from the vanished percolation threshold, which has no effect on the other properties discussed above.
1.2 Networks
This paper mainly focuses on the percolation theory on networks and its applications. So, in this section we will provide an overview of some simple and general properties and models of networks.
1.2.1 Network representation
In network science, the elements of a system and the connections between them are no longer known as site and bond. Instead, they are often called node and link, or vertex and edge, respectively. The number of links a node has is called degree, labeled .
To exactly represent the connection pattern of a network, one often uses a matrix , called adjacent matrix, where is the number of nodes in the network. In this way, the element of is one when there is a link from node to node , and zero when there is no link. For undirected networks, it must have , thus is a symmetric matrix. For weighted networks, the element can further be any non-zero value to represent the corresponding link weight.
1.2.2 Statistical properties
Instead of studying a special network with a given adjacent matrix, the network science is more on discovering the common nature of a class of networks, i.e., a network ensemble. For that, networks are often featured by the degree distribution , which provides the probability that a randomly selected node in the network has degree .
A typical network ensemble is the one with Poisson degree distribution
| (11) |
where means the average over all the nodes. This just is the ensemble of the known Erdős–Rényi (ER) random networks/graphs [47], and can be simply realized by randomly connecting a given number of links among a set of nodes, or connecting each pairs of nodes with a given probability. Quite obviously, the generation of ER networks is actually a percolation process. Only when the system percolates (), the giant cluster can be found. Specifically, when almost surely each cluster has size , at , the largest cluster has a size of order , and at , there exists a single giant cluster of size of order and all other clusters have a size of order . Since such systems have no spatial constraint, the critical phenomena in this ensemble just recover the mean-field solution.
Besides, distinguishing from the degree distribution, there is another kind of commonly used networks, which represents a deeper organizing principle of real networks called the SF property [2]. In mathematical terms, the SF property translates into a power-law function of the form
| (12) |
For a real network, there must also be an upper bound of degree, called degree cutoff .
The main difference between an ER and a SF network comes in the tail of the degree distribution. For ER networks, most nodes have comparable degrees and hence the degree cutoff is in the order of the average degree. In contrast, nodes with very large degrees are expected in SF networks, called hubs of the networks. Indeed, the degrees of hubs grow with the network size, and thus can grow quite large. This indicates that SF networks have strong heterogeneity, and hence the percolation transition bears a strong dependence upon the degree distribution. Beyond this, there are many other measurements to further subdivide the network ensembles, such as clustering, correlation, and community. In recent years, temporal networks, multiplex networks, and high-order networks have also received a lot of attention. Because of space limitation and the focus of this paper, the details will not be included here and brief discussions will be given in this article when necessary. Further details on these can also be found in Refs.[3, 5, 6, 1, 2].
1.2.3 Network models
After a review of the fundamental properties of complex networks, we explore the mathematical modeling of network ensembles, and mainly focus on the configuration model and the hidden parameter model [1, 2]. In principle, the two models can generate any network ensembles with a meaningful degree distribution. In fact, these two models are usually only used to realize SF property, since there exist easy-implemented models for Poisson degree distribution (ER networks) and small-world (SW) networks [1, 2]. Note that the SF network also has an easy-implemented model, Barabási–Albert (BA) model [56], nevertheless, the generated SF network has its own structural features and limitations rather than a network with programmable and tunable SF properties.
From random graph theory [47], there are two ways to generate a network with Poisson degree distribution. One is randomly connecting nodes until the excepted number of links is met, and the other is connecting each pair of nodes with a given probability. For a given average degree, networks implemented by the former method must be a subset of those by the later one. In spite of this, the two methods will become equivalent in the thermodynamic limitation ().
The SW network grows out of a regular network, such as the triangle lattice and the square lattice, by randomly rewiring a small fraction of links [57, 58, 59, 60]. Since there is no spatial constraint for the rewired link, the average distance of nodes becomes much smaller than that of the underlying regular network. This is why it is called small-world. In turn, the regular backbone of the SW network usually leads to a high clustering, namely, the neighbors of a node are also connected. This is another characteristic of the SW network. For this type of networks, the degree distribution is often not the concern, and one often uses the backbone network and the rewiring probability to define a SW network ensemble.
The configuration model can help us build a network with a pre-defined degree distribution [61, 62, 1, 2]. The algorithm consists of two steps. First, assigning degrees to each node drawn randomly from the pre-defined degree distribution, represented as stubs. Then, two stubs are selected randomly and connected. Repeating this procedure until all stubs are paired up. If there is nothing in this procedure to forbid self- and multi-connections, the obtained network is probably not a simple graph as usually studied in network science. While rejecting such connections could add much more overhead to the program’s execution time.

Indeed, one of the effective methods to generate random networks by the configuration model without self- and multi-connections can be as follows. First, connecting the stubs in any fast and easy-to-implement ways (the details are dependent on the specific degree distribution), and recording the self- and multi-connections. Then, rewiring a fraction of links of the obtained network, and the self- and multi-connections must be included. Note that the rewiring leading to self- or multi-connections is forbidden.
A schematic diagram of the rewiring procedure is shown in Fig.2. For the degree distribution with the maximum degree larger than , this method could be much more effective than the original one, which may not even complete the network. This is because there must be some degree correlation in the network with [63, 64], randomly connecting stubs with self- and multi-connection forbidden is a very inefficient procedure. Of course, the efficiency of the algorithm also depends on the implementing way and the detailed property of the network, thus this just is a general discussion and not always the case.
By the way, the rewiring operation as shown in Fig.2 is often called degree preserving randomization, which can randomize the connections of a network without changing the degree distribution. With this operation, one can eliminate other properties from the network, for example, clustering, and assure that a certain network feature is predicted by its degree distribution alone. If the network is large enough and all the degrees are much smaller than the network size , the degree preserving randomization could turn the network to be locally tree-like.
Note that the correlation derived from the degree distribution cannot be undone by this randomization procedure. A typical example is a network with . Consequently, when we study networks with hubs, i.e., SF networks, the configuration model and the degree preserving randomization must be carefully dealt with. In turn, with some constraints, this rewiring operation can also “randomize” the network into the one with a given high-order property [65, 66].
There is another model, hidden parameter model, to generate networks with a pre-defined degree distribution [67, 68, 69, 70, 71]. In this model, each node is assigned a hidden parameter , chosen from a pre-defined distribution . Then, we connect each node pair with probability . The expected number of links is thus . For SF networks, we can set , and the obtained network has the degree distribution .
The SF networks generated by the configuration model and the hidden parameter model also have their own properties, thus are not exactly equivalent, at least for small systems. First of all, the boundaries of degrees must be given for the configuration model to normalize the degree distribution. However, the boundaries of degrees are not needed for the hidden parameter model, in which a degree cutoff occurs naturally at , thus known as the natural cutoff of the SF network [72, 73, 74, 75, 76]. This cutoff can be also found in the configuration model, if the upper boundary used to normalize the degree distribution is larger than . Then, the hidden parameter model generates no self- and multi-connections, since only a single connection would occur between each node pair. Another is that the degree distribution of the SF network generated by the hidden parameter model has negative deviations for small degrees, while the one generated by the configuration model almost perfectly matches the pre-defined degree distribution. In addition, setting the total number of links is not allowed in the configuration model, since it is fixed by the pre-defined degree distribution. Rather, the hidden parameter model allows controlling the link number, accurately. Finally, what need to be pointed out is that both the networks generated by the configuration model and by the hidden parameter model are only a possible realization of the pre-defined degree distribution. To check the property induced by a certain degree distribution, the ensemble average must be done.
In recent years many works have also been devoted to the so-called multiplex networks (or multilayer networks, interdependent networks) [8, 9]. In this network ensemble, links are divided into different layers to represent different types of connections between nodes. To generate such a network ensemble, one can first generate several networks using the methods mentioned above, and then bundle nodes from different networks together to form the layered connections. It can also be interpreted as inserting some inter-connections between nodes in different networks (layers), which represent the dependence relations between them. The bundling of nodes (or inter-connection) could be one-to-one, one-to-many, or with some other rules, that depending on the inter-correlation between layers. Of course, there are many other network models with different properties, one can find them in special books and reviews about complex networks.
1.3 Outline of the report
This paper contains six sections. In the next section, we start by reviewing the basic properties of the percolation process on networks, including the model definition, the analytical methods, and the corresponding discussions. Section 3 reviews some typical percolation models on networks, mainly focusing on the phase transition and the critical phenomena. The percolation model is by nature featuring the cluster forming process in random media. Therefore, the percolation theory including conceptions, theoretical methods, and algorithms, is widely used in network structure analysis. This is the main content of Sec.4. Moreover, the percolation process is often used to model and analyze network dynamics, which will be reviewed in Sec.5. Finally, we summarize and prospect to this paper in Sec.6.
In addition, the main notations used in this paper are listed in Tab.2 for readability.
| Notation | Meaning |
|---|---|
| system dimension | |
| fractal dimension | |
| generating function of degree distribution | |
| generating function of excess-degree distribution | |
| Hamiltonian of Potts model | |
| generating function of | |
| generating function of | |
| fraction of infected individuals in all degree- nodes at time step | |
| node degree | |
| degree cutoff of a network | |
| average degree | |
| -th moment of degree distribution | |
| Hashimoto or non-backtracking matrix of graph | |
| node number of a network | |
| occupied probability | |
| percolation threshold | |
| degree distribution | |
| distribution of the cluster sizes | |
| excess-degree distribution | |
| probability that link belongs to the giant cluster | |
| fraction of removed individuals in all degree- nodes at time step | |
| probability that a link belongs to the giant cluster | |
| probability that a node belongs to the giant cluster | |
| cluster size | |
| probability that node belongs to the giant cluster | |
| fraction of susceptible individuals in all degree- nodes at time step | |
| characteristic size | |
| partition function of Potts model | |
| rescaled partition function of Potts model | |
| partition function of the branching from node of Potts model | |
| critical exponent for the giant cluster; infection rate | |
| critical exponent for the mean cluster size | |
| Kronecker delta function | |
| Riemann zeta function | |
| Hurwitz zeta function | |
| probability that a neighbor of a degree- node is infected | |
| ratio of and | |
| exponent of SF degree distribution, | |
| recovery rate | |
| critical exponent for the characteristic length | |
| characteristic length | |
| size distribution of the cluster that a randomly chosen node belongs to | |
| size distribution of the cluster at the end of a link | |
| critical exponent for the characteristic size | |
| Fisher exponent | |
| Lerch’s transcendent | |
| mean cluster size |
2 Classical percolation on networks
In statistical physics, the percolation model is often displayed on regular lattices. However, the regular topological structure is not always the case in reality. In this section, we will review the basic properties of the classical percolation on heterogeneous network systems, mainly focusing on analytic methods, critical phenomena, and Monte Carlo algorithms of the classical percolation. It should be pointed out that there are a lot of theoretical studies of percolation transition on networks from the perspective of random graphs, one can refer to Refs.[77, 78, 47, 79, 80, 81, 82] and the relevant references to learn more. Here we mainly focus on the network percolation from the perspective of statistical physics and network science.
2.1 Problem description
As a lattice model, the percolation model can be easily extended to networked systems, namely, nodes or links are randomly designated either occupied (with probability ) or unoccupied (with probability ). For convenience, in network science one usually removes each node or link with probability to realize the percolation model. The parameters and the corresponding problems can be defined on the preserved network as that on regular lattices. As a result, there is no need to repeat the arguments. Here we will concentrate on the relationships between the classical percolation model and some typical issues of network science, such as network robustness, and epidemics spreading on network.
For site percolation, the network science often translates the unoccupied nodes as failed/removed ones. In this way, the percolation process is just the performance of the network under random nodal failures. If the giant cluster remains after the percolation process, the resulted network can be thought of as a whole, and still functional. Thus the percolation threshold can be used to evaluate the robustness of the network [83, 84, 85, 72, 86]. A large threshold indicates that only a small amount of failed nodes can disconnect the network, so its robustness is poor, and vice versa. Furthermore, if the unoccupied nodes are chosen with preference, this model can further explain the robustness of networks under intentional attacks. A remarkable knowledge of this model is the finding of the strong robustness of SF networks under random failures, and extremely fragile for intentional attacks [85]. A specific discussion on this problem can be found in Sec.4.
In network science, bond percolation often refers to the spreading process [23]. The connection between the spreading of epidemic and percolation is in fact one of the original motivations for the percolation model itself [16, 7, 17, 25]. For this process, the occupation of a link means a successful infection between the two connected nodes. That is, the occupied probability reflects the infectiousness of the epidemic. However, different from the mapping between site percolation and models for network robustness, the link occupied probability is not simply equivalent to the infectious probability, but an integrated probability of transmission of the disease between two individuals [87]. In this way, the emergence of the giant cluster corresponds to the outbreak of an epidemic, so that the percolation threshold can also be used to evaluate the infectiousness of the epidemic. An epidemic with smaller percolation threshold has a stronger infectious ability. Specific discussion on this problem can be found in Sec.5.
The basic mechanisms of the network percolation and their extensions can be further applied in various fields of network science from structure analysis to dynamics modeling, which this article explores next.
2.2 Analytic method based on branching process
Although the percolation model is easy to define, the exact solutions are absent for most systems. If the network topology is restricted to be tree-like, like that of Bethe lattice, there is a mean-field method based on the branching process for solving the percolation model. Here we introduce the framework of this method, including the solutions for the size of the giant cluster and the distribution of finite clusters [48, 87, 1].
2.2.1 Behaviors of the giant cluster
The percolation process is tantamount to dilute links and thus changes the degree distribution . So, for convenience and generality, the occupation of nodes or links will not be considered in the following discussion. After obtaining the result, we can revise it by considering the diluting effect of the percolation on the degree distribution .
When a network percolates, there must be an infinite cluster, in which the branching process is endless. Specifically, when arriving at a node by following a link, the node must have some other links (at least one) to ensure the continuity of branching. In terms of this, assuming a link belongs (connects) to the giant cluster with probability , we have a self-consistent equation
| (13) |
where is the probability that the node reached by following a link has degree , known as the excess-degree distribution, and is the corresponding generating function. The term in the square brackets just means that at least one excess link is needed to keep branching.
After obtaining from Eq.(13), the order parameter , i.e., the probability that a randomly chosen node belongs to the giant cluster (the infinite cluster), can be expressed as
| (14) |
where is the generating function of the degree distribution. The right hand side of this equation means that at least one of the neighbors must belong to the giant cluster. From the perspective of branching, this equation can also be interpreted as the start point of the branching process, while Eq.(13) is the intermediate process. In the infinite cluster any nodes can be the start point, so is an average probability, as well as the parameter .
Furthermore, for the percolation with occupied probability , we only need to replace the generating functions in Eqs.(13) and (14) with those of the diluted network. Next, let us calculate the degree distribution of the diluted network. Regardless of the type of the percolation (site percolation or bond percolation), the diluting ratio of links is , i.e., each link is preserved with probability . So the generating functions and of the diluted networks can be written as
| (15) | ||||
| (16) |
Then, inserting them into Eqs.(13) and (14), we have [48, 87]
| (17) | ||||
| (18) |
Before continuing to consider the details of these two equations, we must point out that the order parameter here is the size respected to the diluted network. For bond percolation, the dilution is only for links, so the diluted network has the same size as the original network and is also the size respecting to the original network. However, for site percolation the diluted network consists of only occupied nodes (fraction respected to the original network). As a result, Eq.(18) should be revised for site percolation, that is
| (19) |

In general, one can solve Eq.(17) first, and then insert into Eq.(18) or (19) to get the order parameter for the bond percolation and the site percolation, respectively. From Eqs.(17)-(19), we can also find that the two types of percolation models give the same probability , but different giant clusters. For mathematical tractability, sometimes one just uses to represent the meaning of for site percolation in Eqs.(17) and (19), that is
| (20) | ||||
| (21) |
These two equations are fully equivalent to Eqs.(17) and (19).
Although the mean-field approximation is used in the above discussion, i.e., all the nodes have the same probability and all the links have the same probability , Eqs.(17)-(21) can give an exact solution for the percolation on tree-like networks, see Fig.3 as an example. A comparison between the mean-field prediction and the numerical simulation on some real-world networks can also be found in Ref.[88].
Following the idea of branching, the microstructure of the giant cluster in random networks [89], such as degree distribution, and degree correlations, as well as that of temporal networks [90], can also be obtained. For networks with loops, different links could lead to the same nodes in the branching process. In other words, the branching processes starting from different links are no longer independent of each other, thus all the equations (13)-(21) are not valid. That is why the above method is only applicable to the tree-like structure.
2.2.2 Behaviors of finite clusters
Besides the giant cluster, the percolation theory also concerns the behaviors of finite clusters, such as mean cluster size, and cluster size distribution. Next, along with the idea of the branching process used above, we will further show how to obtain the information of finite clusters in percolation model.
As discussed in Ref.[48], it is more convenient to study the distribution rather than or , which means the probability distribution of the size of the cluster that a randomly chosen node belongs to. One can further define as the size distribution of the cluster at the end of a link. Accordingly, the generating functions have the forms and . For convenience, the occupation of links and nodes is not taken into account in the following. When necessary, one can use the revised generating functions Eqs.(15) and (16) to get the corresponding results.
Note that a zero size has no physical senses, so , while can be non-zero corresponding a node with degree one. Since and only contain the finite clusters, and the giant cluster is excluded (if there is one), we have and , where and are defined as that for Eqs.(13) and (14). Below the critical point, and , so and .
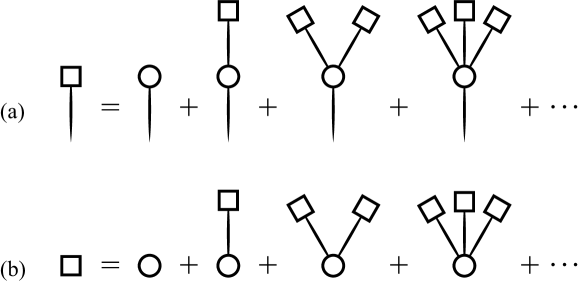
As the schematic in Fig.4, the cluster size distributions and are dependent on both the degree/excess-degree distribution and the branching size at the end of a link. Thus, Fig.4 can be translated as the equations
| (22) | ||||
| (23) |
Note that there is one more factor on the right hand sides of the two equations for the contribution of the root node. Using the relations and , these two equations just recover Eqs.(13) and (14) when .
In principle, we can solve Eqs.(22) and (23) together to find , and then use
| (24) |
to find the cluster size distribution. However, usually no closed form can be found for . Instead, we can substitute Eqs.(22) and (23) into Eq.(24), then do a change of variables via Cauchy formula, and finally get
| (25) |
With this, the cluster size can be obtained directly from , therefore avoiding solve Eqs.(22) and (23) [91, 92, 93]. As , the result must have the form , where is the Fisher exponent.
Furthermore, the mean cluster size can also be obtained from Eqs.(22) and (23). From the definition, the mean cluster size can be represented as
| (26) |
In the last equation the differential of Eq.(22) is used. We can further employ Eq.(23) to replace the term , and yield
| (27) |
It is obvious that is divergent when
| (28) |
This is the Molloy–Reed criterion found in random graph theory [77], above which () the giant cluster exists.
In addition, the discussion of finite clusters based on generating functions and can also work without the help of generating functions and , so it is not limited to uncorrelated tree-like networks, see Sec.3.4 for an example of the percolation on growing networks.
2.3 Potts model formulation
The Potts model is a generalization of the Ising model with more than two components [94], and related to a number of other outstanding problems in lattice systems [24], including percolation model. Although the Potts model is also unsolved for an arbitrary network, the connection between the Potts model and the percolation model has made it possible to explore the network percolation from the known information on the Potts model. This section will provide the mapping between Potts model and percolation model, as well as some discussions.
2.3.1 Fortuin-Kasteleyn cluster representation
It is known that the limit of the -state Potts model without external field corresponds to the percolation problem, which is thus applied to the study of percolation on networks [95, 96, 16, 24]. To consider the percolation on a network , we introduce a -state Potts model with the Hamiltonian
| (29) |
where is the spin state of node , and the sums and are over all the links and nodes of the network, respectively. is the Kronecker delta function, i.e., if and , respectively. Here, the ferromagnetic interaction is used , and the magnetic field is applied to the spin . Then, the partition function can be written as
| (30) |
where , , and the sum is over all the spin configurations of the system. We can further expand the products and use the subnetworks of to represent the terms in the expansion, which is often called Fortuin–Kasteleyn cluster representation [97].
Next, we give a brief derivation for the Fortuin–Kasteleyn cluster representation. For arguments , , the product is equivalent to the sum of all the possible polynomials formed by , , so that , where is a subset of , and the sum is over all the possible cases. By this formula, the product in Eq.(30) can be represented by the sum of the subnetworks of , that is
| (31) |
where is the number of links in subnetwork . Note that the term gives nonzero value only when the nodes in the same clusters are in the same states (any of the states ). This can further simplify the partition function to be
| (32) |
Here, the product is over all the clusters formed by the links in subnetwork , and is the number of nodes in cluster . The sum over spin in Eq.(30) has now been replaced by a sum over subnetwork , this is just the Fortuin–Kasteleyn cluster representation of the partition function of Potts model.
Let , the partition function Eq.(32) can be rescaled as
| (33) |
where is the total number of links in . If is interpreted as the occupied probability of links, the term is just the probability of a percolation configuration with occupied links. Thus, Eq.(33) bridges the Potts model and the percolation model.
From Eq.(33), we can write the free energy per node as
| (34) |
For convenience, we further define
| (35) |
For the sum in this equation is over all the finite clusters, then the size of the percolating cluster is
| (36) |
and the mean cluster size is
| (37) |
By the above two equations, the percolation property can then be extracted from the Potts model.
The product in Eq.(33) is over all the clusters. It thus can be rewritten in another form of
| (38) |
where the product is over the size of the clusters, and is the number of clusters with size . By this formula, function can also be expressed as
| (39) |
Here, is the cluster size distribution. This is just the generating function with , which can be used to study the cluster size distribution.
Specifically, once the Hamiltonian (Eq.(29)) of a network is known, all the percolation parameters can be obtained by the above equations. However, for most network models, it is difficult to simplify the sum over links in Eq.(29). A solvable case is the hidden parameter model, for which the pre-defined connection probability is given for each pair of nodes. Thus, the sum over links can be translated as a weighed (connection probability) sum over all the node pairs. With this technique, the Potts model formulation has been used in solving the percolation on SF networks [98, 99], on correlated hypergraphs [100], and in generalized canonical random network ensembles [101].
2.3.2 Relation with the mean-field equations
Through the so-called recurrence relation, the mean-field equations for tree-like networks can be recovered by the Potts model formulation [102]. For this purpose, the partition function can be represented as an integration of a root, labeled node , and the branchings from it, that is
| (40) |
Here, is the partition function of the branching from node , and the product runs over all the root’s nearest neighbors (nodes in the first shell of node ). Due to the symmetry, in the second term of Eq.(40) can be any state excluding . Obviously, this formulation is only for the tree-like networks, if not, the product must include some double counting.
Different from Eq.(30), the partition function equation (40) represents the effective state of the root node. In this way, the free energy per nodes is , then we have
| (41) |
To study the percolation model, we assume here that describes the state for and , thus it is irrelevant to the differentials and . For convenience, we further rescale by , i.e., . Then, by Eq.(36), we can find the order parameter of the percolation transition
| (42) |
From this equation, the physical meaning of becomes clear, that is the probability that the branching from node is not the giant cluster.
To obtain the order parameter, we need to further find . Comparing Eqs.(40) and (30), we have
| (43) |
where the sums and run over the nodes and the links in the branching from node , respectively. Note that the interaction between node and the root is also included in this partition function. Furthermore, it is not hard to find that satisfies the following recurrence relation
| (44) |
Here, the product is over all the neighbors of node except the root (nodes in the second shell of node ), and is the partition function for the subnetwork branching from node .
For infinite system, the recursive relation Eq.(44) holds for any two adjacent shells. If , it can be rewritten as
| (45) |
While for , Eq.(44) reduces to
| (46) |
Then, we can find the recursive equation for ,
| (47) |
For and , it reduces to
| (48) |
where .
From the view of mean-field theory, the probabilities for different nodes can all be replaced by an average probability . Then, Eqs.(42) and (48) become
| (49) | ||||
| (50) |
These are just the mean-field equations (17) and (18) found in Sec.2.2 with . By this equation, we bridge the Potts model formulation of the percolation model with that of the mean-field method based on the branching process [102]. Note that the tree-like structure is also required here.
2.4 Message passing method
In recent years, there has been a growing interest in the analysis of the percolation problem on real networks. These systems all have finite sizes and are featured by the adjacency matrix rather than the degree distribution. As a consequence, the above mean-field method does not work in this case. Instead, the most common method to estimate the percolation threshold on these networks is the so-called message passing method [103, 104, 105, 106, 107, 108, 109, 110, 111, 112, 113]. Note that the percolation threshold (transition) is theoretically defined in the thermodynamic limit (), here we assume that the system is large enough to observe a percolation transition. Next, we will go to the details of this method.
Different from the above mean-field method, the message passing method allows each node has its own probability to express whether it is a part of the giant cluster. From this perspective, the size of the giant cluster can be written as
| (51) |
Similar to Eqs.(20) and (21), we can also express as
| (52) | ||||
| (53) |
where is the probability that the link leads to the giant cluster, and is the set of neighbors of node . Furthermore, by evaluating the logarithm of the above two equations, we can turn the products into sums,
| (54) | ||||
| (55) |
Here is the adjacency matrix of the network, i.e., if there is a link , otherwise .
Let and , Eq.(55) becomes equivalent to the vectorial equation
| (56) |
where is a matrix ( is the number of links). From Eq.(55), we can find that only when and , the entry is non-zero. In other words, the two links must be head to tail, and excluding the case of backtracking. This matrix is known as the Hashimoto or non-backtracking matrix of graphs [114, 115]. Mathematically, , where is the Kronecker delta function if , and , otherwise.
When , all trend to zero. Then, expanding Eq.(55) around the critical point, we obtain an eigenvalue equation of matrix ,
| (57) |
According to the Perron-Frobenius theorem, only the largest eigenvalue of matrix can give a meaningful eigenvector (with all elements non-negative). Therefore, it gives a lower bound for the site percolation threshold on an infinite graph [103]. Considering the effects of triangles, this framework can also be used to establish a tighter lower bound of the bond percolation threshold on clustered networks [116].
The above discussion is for site percolation, it can be easily extended to bond percolation, that is
| (58) | ||||
| (59) |
Further discussion of the two equations can be done like that of the site percolation.
2.5 Phase transition and critical phenomena
Due to the heterogeneous structure, the classical percolation on networks demonstrates many interesting phenomena. In this subsection we will review the findings on tree-like network ensembles, for which the percolation problem can be solved exactly by the methods reviewed in the above subsections.
2.5.1 Percolation threshold
To discuss the critical phenomena, we first need to determine the critical point. For tree-like networks, it is easy to know from Eqs.(17)-(21) that only a non-zero can lead to a non-zero . Thus the percolation threshold can be found by analyzing the non-trivial solution of Eq.(17), and the site and bond percolations have the same critical point. For this purpose, we can construct a function
| (60) |
The solution of Eq.(17) corresponds to the crossing point of and -axis. Since is continuous with and , we can draw a qualitative curve of as shown in Fig.5. It is easy to find that the critical point corresponds to the tangency of and -axis with , so we have
| (61) |
Thus, the percolation threshold can be written as
| (62) |
This is a general form for any tree-like networks. Using the expression of the generating function , it can be rewritten as
| (63) |
For , this equation reduces to Eq.(28), i.e., the Molloy–Reed criterion [77]. Note that this is an approximate expression for tree-like infinite networks. A general case for finite systems is the one found by message passing method, see the last subsection.

For ER networks, node degrees obey the Poisson distribution , so that
| (64) | ||||
| (65) |
This allows the percolation threshold has a simple form . Besides, due to the Poisson degree distribution, ER networks can have a closed solution of percolation threshold for many network percolation models. For comparison, we list the percolation thresholds of ER networks for different models in Tab.3.
| Model | Threshold |
|---|---|
| Classical percolation | [48] |
| Biconnected cluster | [117] |
| Core percolation | [118] |
| Greedy articulation point removal | [119] |
| Two interdependent networks | [120, 121] |
| Single networks with dependence links | [122] |
| Classical percolation | [47] |
| Clique percolation | [123, 124] |
| Growing network | [125] |
A more interesting case is the SF network with , for which is divergent, indicating a vanished percolation threshold. Employing the Hurwitz zeta function , the percolation threshold of SF networks can be represented as
| (66) |
One can find that for , this formula gives a percolation threshold larger than when , indicating there is no percolation transition. This is due to the absence of the spanning cluster in such SF networks [78]. The typical value can be obtained by , where is the Riemann zeta function. This problem can be overcome by simply setting . Furthermore, the Hurwitz zeta function is divergent for . Thus a vanished percolation threshold can be found for SF networks with .
The zero percolation threshold is not unique to SF networks, and a general class of self-similar and hierarchical networks can also have zero percolation threshold [126, 127, 128]. This property can be derived from the hierarchy of nested subgraphs in self-similar networks and real-space renormalization group technique, and does not require the assumption that networks are tree-like. In addition, by embedding SF networks into physical dimensions, a non-zero percolation threshold can also be reconstructed [129]. This is mainly because the spatial constraint induces a high clustering and dilutes the global connections.
2.5.2 Scaling behaviors
Varied percolation thresholds in different networks are excepted, since it is not universal, whereas things get interesting in that the heterogeneous structures could produce a different universal property of percolation transition, i.e., the critical exponent. Indeed, we can expand the analytical results (see Sec.2.2) around the critical point to find the critical exponents. It is also worth pointing out that the critical exponents derived from the results obtained in Sec.2.2 are still the sense of mean-field solutions, although they might be different from the regular mean-field nature.
For a few cases that have a closed form of the generating functions and , such as ER networks and RR networks, they give the critical exponents above the critical dimension (the mean-field critical exponents), since these systems have no spatial constraint. Mathematically, for these networks, the degree distribution only affects the coefficients of the expansion series around the percolation threshold, then yields the same leading order. For the calculation of these cases, one can refer to Refs.[48, 87, 91, 92] for details.
A special case is SF networks, which have strong heterogeneity. Although there is also no spatial constraint, it shows a -dependent critical behavior ( is the exponent of the degree distribution ). Even for a vanished percolation threshold (), the critical behavior is also well defined. The critical exponents can be also derived from the results obtained in Sec.2.2, but bear a strong heterogeneity of the degree distribution.
Although the generating functions and have no closed form for SF networks, they can be represented by the Lerch’s transcendent ,
| (67) | ||||
| (68) |
where . To find the critical behaviors of the percolation on SF networks, we need further to know the series expansion of and at the critical point , which corresponds to , see Sec.2.5.1. However, has a singularity at , which is dependent on . This is the mathematical origin of the specific critical behaviors of SF networks.
From Ref.[130], for and , the Lerch’s transcendent can be expanded as
| (69) |
Let , we also have
| (70) |
Then, we can further write as a series of ,
| (71) |
where is the signed Stirling numbers of the first kind. With this equation, we can find the leading terms of the generating functions and for , i.e., the asymptotic series to the percolation threshold. Then, substituting into the corresponding equations in Sec.2.2, the -dependent critical exponents can be obtained, which are summarized in Tab.4. We can find that the case of is just a mirror copy of the case of .
| 1 | 1 |
In essence, a strong heterogeneity just means a broad degree distribution. Therefore, when the emergence of hubs in SF networks is suppressed (large ), the regular mean-field exponents as that found in ER networks are excepted. Cohen et al. pointed out that the regular mean-field results can be found when [131].
Moreover, Radicchi and Castellano pointed out that the site percolation on SF networks gives a different critical exponent for [55]. This comes from the singularity of Eq.(19), which has the leading term . For , the system has a non-trivial , and the leading term reduces to , which gives the same critical exponent as that of the bond percolation. However, for , it can be rewritten as , where . This leads to .
It is also worth noting that with the Potts model formulation, Lee et al. shows for [98, 99], which is contradict with that listed in Tab.4 [131]. By this, the validity of the treatments used in the two works requires further study. Besides, Cohen et al. pointed out that due to the vanished threshold for , the exponent is calculated at a small but fixed occupied probability [131].
With the framework shown above, many other features about the percolation transition on SF networks were also studied, such as the fractal dimensions of percolating networks [132], the giant cluster in the large-network limit [133], branching trees [134], statistical ensemble [135, 136, 137], width of percolation transition [138], the upper critical dimension [139], and the cluster forming in SF networks with exponent less than two [140] or one [141].
Although the above discussions are concentrated on the degree distributions of networks, we must point out that the spatial constraint still plays a key role in the nature of percolation transition. By embedding networks in a physical dimension, the network percolation can also exhibit a range of phase behaviors, as well as reconstructing the universality class of physical dimensions, depending on the dominant structure properties, such as spatial constraint, small-world, fractal, and hierarchy [142, 143, 144, 145, 146]. In Refs.[58, 60, 147, 148], Newman and the coauthors also developed a method to study the percolation transition on SW networks, suggesting that the SW network resembles more a random network in infinite dimension.
2.6 On clustered and correlated networks
Real world networks are commonly clustered and correlated rather than a tree-like random structure [2]. Some works also contributed to the percolation of clustered and correlated networks. Note that the clustering and the correlation discussed here are local, i.e., they are the properties of adjacent nodes.
2.6.1 Networks with low clustering
As a starting point, we first review the method proposed by Berchenko et al. to find the approximate solution of the percolation model for networks with low clustering [149]. Network science often employs the clustering coefficient to feature how well connected the neighborhood of a node is [150, 57, 1, 2]. If the neighbors are fully connected, the clustering coefficient is , while a value close to means that there are hardly any connections in the neighborhood. Indeed, as the definition of the clustering coefficient, it also represents the connection probability of a node’s two neighbors. In the branching process one can exclude the backward links from the excess degrees, see Fig.6 (a). Therefore, the effective excess-degree of a node with degree can be expressed as
| (72) |
For , this reduces to the tree-like structure . This equation has no physical meaning for , since it is only an approximate treatment for low clustering. With Eq.(72), the generating function of the excess degrees can be revised as
| (73) | |||||
where is that with no thought of clusterings. With this revised generating function, we can solve the percolation model on networks with low clustering, which gives the critical point [149]
| (74) |
This indicates that for a given degree distribution, the clustering leads to a larger percolation threshold. This mainly because for a fixed number of links, the clustering structure reinforces the core of the network with the price of diluting the global connections [151, 152, 153, 154]. However, the clustering cannot restore a finite percolation threshold for SF networks with [155], since the divergence of only depends on the degree distribution in this approximation.
It is important to notice that Eq.(74) works only for networks with low clusterings. Strong clustering could induce the core-periphery structure [156, 157], in which the core and periphery might percolate at different critical points [158, 159, 160], and the above approximate treatment is not applicable. In this perspective, the clustered networks are often characterized as a robust system [161, 162, 163].
2.6.2 Networks with high clustering
For high clustering, the triangles formed by adjacent nodes could share links, which cannot be directly reflected by the clustering coefficient, Eq.(72) thus overcounts the excess links. Of course, one can further use the polynomials of the clustering coefficient to estimate these high-order clustering structures [65]. However, to completely eliminate the overcounting, the history of the branching process has to be considered, which is beyond the compass of the mean-field method. In addition, this problem in a sense relates to the minimum spanning tree of networks [164, 165, 166], which is also a problem without a unified solution.
If the triangles or other non-tree-like motifs do not share links with each other, there is another framework to solve the corresponding percolation problem [152, 153, 167, 168]. Beyond the degree distribution, this approach requires to know the distribution of all other motifs that a node has, see Fig.6 (b). Taking the triangle structure as an example, when the number of triangles that a node has is known, one can treat the triangle as a special link in the branching process. Then, the network can percolate by means of not only single links but also triangles. Under this premise, the clustered networks can also be regarded as tree-like, and the processing method provided above can thus be used. In principle, this method can be applied to networks with any motifs. However, it is a tedious work to classify diverse clustered structures and get the corresponding distribution. In addition, this approach can be well summarized as mapping the clustered network into a tree-like hyper-network [169].
The general thought in dealing with this problem, namely, recognizing a certain connection structure as an individual (link or node), is also used in the so-called clique percolation [170]. In this percolation problem, the -clique, a complete subnetwork with nodes, is treated as a node, and two -cliques sharing nodes are considered to be connected. This percolation model is usually used as an algorithm for the detection of communities with overlap [171]. For percolation transition, the main finding is the seemingly discontinuous transition, which essentially is a continuous one [124]. The details will be discussed in Sec.4.3.

Another application of this framework is the solution of the percolation model on SW networks [147, 148], which typically show a highly clustering effect. In Refs.[147, 148] the authors treated the finite percolation clusters extracted from the underlying lattice of the SW network as effective nodes, then the system is just a set of effective nodes connected by the shortcuts, which are links added between randomly selected pairs of nodes in the underlying lattice [57, 59]. As the setting of SW networks, the shortcuts are sparse, so near or below the percolation threshold the reduced network demonstrates a tree-like structure composed of effective nodes and shortcuts, see Fig.7. Consequently, the formulation of the self-consistent equation as Eq.(23) can be used to solve the model, too. Based on this treatment, they found that the shortcuts not only modify the percolation threshold but also the universality class.
Since the clusterings are naturally excluded in the non-backtracking matrix, with some techniques the message passing method can also be used to find the percolation threshold of clustered networks, see the references listed in Sec.2.4 for details.
2.6.3 Correlated networks
Along with clusterings, real networks generally show a structure with degree correlation rather than random connections. For such networks, the branching process cannot be simply described by the excess-degree distribution. Instead, a joint degree-degree distribution is used to figure out the degree correlation of the two nodes at two ends of a link [172, 173].
Theoretical results show that a finite amount of random mixing of the connections in SF networks with is sufficient to give a divergent , and thus leads to a vanished percolation threshold [172]. Moreover, the assortative correlation makes networks more robust, while the disassortative correlation makes networks fragile even with a divergent second moment of degree distribution. However, in the spatially constrained ER networks, degree correlations favor or do not favor percolation depending on the connectivity rules [174].
The Monte Carlo simulations on the exponential random network show that the disassortative correlation has no effect on the critical phenomena so that the percolation transition on disassortative networks belongs to the same universality class as on uncorrelated networks [175]. While assortative correlation is relevant, percolation transition shows continuously varying critical exponents [175]. Recently, Mizutaka et al. proposed a maximally disassortative network model, which realizes a maximally negative degree-degree correlation [176]. Both the analytical and simulation results suggest this maximally disassortative network can also give new critical exponents for SF networks with .
Goltsev et al. further summarized three conditions [173]: (i) The largest eigenvalue of the branching matrix is finite if is finite, or if ; (ii) The second largest eigenvalues of the branching matrix is finite; (iii) The sequence of entries of the eigenvector associated with the largest eigenvalue converges to a nonzero value. When these conditions are fulfilled, the critical exponents are completely determined by the asymptotic behavior of the degree distribution at large degrees, thus the percolation transition on a correlated network belongs to the same universality class as the percolation on an uncorrelated network. If at least one of the three conditions is not fulfilled, the critical exponent becomes model-dependent and hence non-universal [177, 178, 179]. Furthermore, by the technique that dividing nodes into different types with hyper-links, the site and bond percolations on clustered and correlated networks can also be solved [180, 181, 108].
2.7 On directed networks
The percolation transition can be also defined on directed networks. The difference is that the giant cluster of directed networks can be further specified as [48]: (i) the giant strongly connected cluster (GSCC), in which each node is reachable from others; (ii) the giant in-cluster (GIC), from which GSCC are reachable but those are not reachable from GSCC; (iii) the giant out-cluster (GOC), from which GSCC are not reachable but those are reachable from GSCC; (iv) the giant weakly connected cluster (GWCC), in which each pair of nodes are reachable without regard to the direction of links. A schematic of these giant clusters is shown in Fig.8.

The mean-field method reviewed in Sec.2.2 can also be extended to directed networks [182, 183, 184, 185, 186, 187, 188, 189]. For this, we define and as the probabilities that a directed link leads to GSCC and comes from GSCC, respectively. Thus, similar to Eq.(13), we have two self-consistent equations,
| (75) | ||||
| (76) |
where is the probability that a node has in-degree and out-degree , and
| (77) | ||||
| (78) |
are the generating functions of the excess-degree distribution following and against the link direction, respectively. Note that a directed network has an identical average in-degree and average out-degree .
When Eqs.(75) and (76) only have the trivial solution , there is thus no GSCC in the system. Otherwise, the giant cluster can be expressed by and according to their definitions,
| (79) | ||||
| (80) | ||||
| (81) |
where
| (82) |
is the generating function of the degree distribution. Similar as that for undirected networks, let in Eqs.(75) and (76), we have the criterion of percolation transition,
| (83) | ||||
| (84) |
The two equations are equivalent, that is
| (85) |
This is the condition that the GSCC exists in a directed network. Considering the dilution of the initial node or link removal as that for undirected networks (see Sec.2.2), one can also find the percolation threshold from Eq.(85),
| (86) |
where . If there is no correlation between in-degrees and out-degrees, i.e., , Eq.(86) reduces to . This indicates that in contrast to undirected networks, a non-zero percolation threshold can exist in directed SF networks with and [183]. Here, and are the in-degree and out-degree distribution exponents, respectively.
From the asymptotic expansion of Eqs.(75)-(81), the critical exponents can also be obtained [183]. In general, the GIC and GOC can give different critical exponents , which are dependent on the in-degree and out-degree distributions. As the definition, GSCC is the intersection of GIC and GOC. Therefore, it behaves as the smaller one of GIC and GOC. For directed SF networks, the critical exponents can be also written in the form of undirected SF networks, see Tab.4, but with an effective , which is dependent on the existence of correlations and on the degree distribution exponents and [183].
The above discussion can also be generalized to the cases with the bidirectional links and the degree correlations [184, 190]. The result shows that the percolation threshold can be generally expressed as a function of the maximum eigenvalue of the connectivity matrices. In particular, for networks with no degree correlations, bidirectional links act as a catalyst for percolation, favoring the emergence of the GSCC, and for SF networks, only an infinitesimal fraction of bidirectional links is needed. The interface links, i.e., the ones joining GIC/GOC and GSCC, can also be investigated analytically in this framework [185]. In addition, the GWCC of a directed network can be obtained by mapping it into an undirected network. It should be noted that the GWCC could emerge at a smaller than that of GSCC, which is dependent on the degree correlations of the in-degrees and the out-degrees. This indicates that the directed network may have the GWCC and, simultaneously, may not have the GSCC.
2.8 Algorithm for network percolation
For most network systems, the percolation model cannot be solved exactly. In consequence, the simulation algorithm becomes very important to estimate the critical point and to study the critical phenomena. However, due to the diversity of network connections, the algorithms for classical percolation on regular lattices cannot be transplanted into network percolation directly. One needs to store the connection information of the network, while this is not necessary for that on regular lattices [191]. Hence, the simulation of the network percolation requires more memory than of the classical percolation on physical dimensions.
In general, we can first construct the percolation configuration following the percolation rule, then use the classical algorithm of graph searching to identify the connections of the configuration, including the breadth-first searching and the depth-first searching. For a given configuration with links, these searching algorithms take time to find all the clusters. This is the minimal overhead for scanning an unknown structure. If the data structure of the network does not allow to directly scan the neighbors of nodes, such as the adjacency matrix, the time complexity will be higher. This two-step algorithm, i.e., constructing the configuration first and then identifying the clusters, does not have a specific requirement for percolation rules and network structures, and thus is universally applicable.
To be more effective, the percolation algorithm should be a creative blend of configuration constructing and cluster identifying, not a process with two standalone steps. In other words, while constructing the percolation configuration, we must simultaneously update the cluster information. The detailed techniques are dependent on the percolation model and the network model. Here, we only introduce the algorithm proposed by Newman and Ziff for the classical percolation on networks [28, 192], which is applicable to any given networks. Other algorithms will be reviewed when necessary.
The Newman-Ziff algorithm employs an exquisite data structure [28, 192], with which the nodes/links can be occupied one by one, and the cluster size information can be updated concurrently, which improves greatly the efficiency for checking the percolation properties of a system under a sequence of occupied probability . In this algorithm, each cluster is stored as a separate tree with a single root node. Each node is allocated a pointer either to the root of the cluster or to another node in the cluster, such that by following a pointer chain we can travel from any node to the root of the cluster. The root nodes can be identified by the fact that they have a null pointer. To be more efficient, we can also use the pointer of the root to store the size of the cluster.
Taking bond percolation as an example, this percolation algorithm can be summarized as follows [28, 192]:
-
1.
Initially each node is its own root, and contains a record of its own size, which is .
-
2.
Links of the network are occupied in random order. When a link is occupied, two nodes are joined together. Follow the pointer chains from the two nodes separately until we reach the root nodes of the clusters to which they belong.
-
(a)
If the two roots are the same node, we do nothing further.
-
(b)
If the two roots are different, we examine the cluster sizes stored in them, and add a pointer from the root of the smaller cluster to the root of the larger, thereby making the smaller tree a subtree of the larger one. If the two have the same size, we may choose whichever tree we like to be the subtree of the other. We also update the size of the larger cluster by adding the size of the smaller one to it.
-
(a)
Step is repeated until the expected number of occupied links is reached. The cluster size can be obtained from the pointer of the root, thus it allows us to evaluate the observable quantities of interest. In addition, to improve the efficiency of the algorithm, we can compress the pointer chain as much as possible. For site percolation, the algorithm is similar, see Refs.[28, 192] for details.
3 Network-specific percolation models
In the previous section, we reviewed the studies of the classical percolation model on networked systems. As a framework to evaluate the system performance, the emergence of the giant cluster with respect to some control parameters is widely used in network science [3, 5, 6, 1, 86, 8, 2]. However, the cluster forming rule is diversiform rather than a probabilistic occupation as that in the classical percolation. They usually contain some recursive/iterative processes or with a broad sense of occupation in the cluster forming. Thus, these derivative models are often categorized into a family called dependent percolation. Typical examples include -core percolation, clique percolation, core percolation, explosive percolation, percolation on interdependent/multiplex networks, etc. In this section we will give a brief introduction of the theoretical findings of these models.
In Tab.5, we list the key rules and the types of the percolation transitions for different models.
| Model | Rule | Type |
| -core percolation [193] | Removing all the nodes with degrees less than , iteratively. | continuous for , hybrid for |
| Threshold model [194, 195] | Removing all the nodes with iteratively, where and are the current and the initial degrees of node , respectively | continuous for small , discontinuous for large [195] |
| Bootstrap percolation [196] | Removed nodes will be iteratively recovered when they have at least neighbors. | discontinuous, hybrid [196] |
| Core percolation [118] | Removing nodes of degree along with its neighbor, iteratively. | continuous for undirected networks, discontinuous for directed networks [118] |
| Greedy articulation points removal [119] | Removing all the articulation nodes iteratively, where the articulation node is the one whose removal disconnects the network. | hybrid [118] |
| Percolation on interdependent networks [120, 121] | Removing all the failed nodes iteratively, where the failed node is the one does not belong to the giant cluster, or has a failed dependent partner in other layers. | hybrid [120, 121] |
| Network observability [197] | The initial observable (occupied) node makes both the node and all of its neighbors observable (occupied). | continuous [197] |
| -hop percolation [198] | The nodes no farther than away from the initial removed nodes will also be removed. | continuous [198] |
| History-dependent percolation [199] | Removing all the links between different clusters of the last generation. | continuous for finite generations, hybrid for infinite generation [199, 200] |
| Explosive percolation [201, 202, 203, 204, 205, 21] | At each time step, more than one potential links are arbitrarily chosen. The one that suppresses the emergence of a giant cluster is inserted eventually, and other potential links are discarded. | continuous with unusual finite size behavior [206] |
| Growing network [125] | At each time step, a new node is inserted into the system, then two nodes are chosen randomly from all the existing nodes and joined by a link with probability . | infinite order [125] |
| -component | The nodes in the same cluster must connect to each other by at least independent paths. | continuous for [117] |
| Limit path percolation [207] | After link/node removal, two nodes are considered as connected, if the new shortest path between them is shorter than , where is the shortest path before removal. | continuous [207] |
| Clique percolation [170, 124] | This model considers the percolation of connected cliques in a network, and two cliques are regarded as adjacent, if they share some nodes. | continuous [124, 208] |
| Color-avoiding percolation [209, 210] | Two nodes are considered as color-avoiding connected, only if they are always connected for the removal of any colored links/nodes. | continuous [209, 210] |
3.1 k-core percolation
-core percolation is one of the typical representatives of the dependent percolation on networks[211, 212, 213, 193]. For a given network -core is the subnetwork in which nodes have at least links connecting with other nodes in this subnetwork. So, as a percolation model, it mainly studies the emergence of the giant -core when a fraction nodes are removed, i.e., occupying each node with probability [193]. The case recovers the classical percolation. While the formed cluster has a structure similar to the so-called bicomponent/biconnectivity, which is a meaningful concept of network robustness [117]. For , -core percolation transition becomes discontinuous. In this subsection we will review the theoretical researches of -core percolation, as well as some related percolation models. -core percolation and its variants are often used as algorithms to provide the structure information of networks [214], some of which will be included in Sec.4.
3.1.1 Model and phase transition characteristics
We can iteratively remove nodes with degrees smaller than to obtain the -core of a network. Note that even without the initial node removal, -core may be absent in networks, dependent on the network topology. An extreme case is the tree-like network, for which there cannot exist any finite -cores with . This is not difficult to be understood from the pruning process of -core percolation. In any finite and tree-like networks, there must be some nodes with degree , located at the periphery of the network. The removal of these nodes must introduce some new periphery nodes with degree . In this way the pruning process will destroy the whole network. However, this does nothing to the theoretical analysis of -core percolation transition on tree-like networks, since an infinite spanning tree does not have periphery nodes, and all the degrees are larger than or equal to . This also means that there are no finite -core clusters () in tree-like networks, thus the -core, if exists, is just the giant cluster, and can be used to feature the percolation transition.
As the model setting, if a node is in the -core, it must have at least links connecting to other nodes in the -core. By this, similar to Eqs.(17) and (19), we can write the self-consistent equations for -core percolation on tree-like networks as [193],
| (87) | ||||
| (88) | ||||
| (89) | ||||
| (90) |
where is the size of the -core, and is the probability that a node reached by following a randomly chosen link belongs to the -core. Here, to avoid confusion we use to represent the degree distribution. The sum is over the nodes with preserved neighbors, and the sum is for the degree distribution. Note that the sum in Eq.(89) begins with , since the link used to reach the node has already provided a link for the -core. For both the two cases and , Eq.(90) reduces to that of the classical percolation equation (20), so -core percolation and -core percolation have the same threshold equation (62). For the threshold of the -core percolation becomes distinguishable for .

To get the critical point, one can also define a function as that for classical percolation, see Sec.2.5.1. The critical point thus corresponds to the tangency of and -axis. However, since function has more than one extreme point for , the tangency point gives a non-zero , labeled , which indicates that the percolation transition is discontinuous, see the schematic shown in Fig.9.
Although there is no closed form for the solution of Eqs.(88) and (90), the asymptotic expansion shows that the scaling behaviors can also be observed near the critical point, that is
| (91) |
In consequence, the emergence of a -core is a unique hybrid phase transition with a jump emergence of the -core as a first-order phase transition but also with a critical singularity as the second-order phase transition. This result is first found in Bethe lattice with respectively for and [215], where the model is called bootstrap percolation. Note that the bootstrap percolation now often refers to another percolation model related to -core percolation, and we will give the details later. It is worth noting that this result indicates that -core percolation belongs to a different universality class from that of -core percolation (the classical percolation), although they have the same percolation threshold [216]. This finding is also confirmed by the Monte Carlo simulation on ER networks [217].
For SF networks that bear a strong heterogeneous degree distribution, a ratio for and for is found [218], where is the exponent of the degree distribution of SF networks. This suggests that the -core percolation could reconstitute the normal mean-field nature like that on ER networks when , while for the classical percolation the criterion is [131, 98]. Numerical results also reveal that the fluctuations of the order parameter and mean avalanche size diverge in different ways for [219]. The main focus of this review is network systems, however, we need to point out that the mean-field hybrid nature of the -core percolation can only survive in high dimensions [220, 221, 222, 223].
More generally, Dorogovtsev et al. showed that if the second moment of the degree distribution of a network is finite, -core percolation has a hybrid nature, and there is no principal difference between different tree-like networks [193, 224, 225]. A dramatic difference takes place if the second moment of the degree distribution diverges, i.e., the SF networks with exponent , for which an infinite order transition is observed. Besides, -core percolation was also analyzed for clustered networks [226, 227] and for biased initial node removal [228]. Moreover, -core percolation is also studied as models of the jamming transition [229, 230], granular gas [231], evolution [232], and nervous system [233]. Furthermore, the inducing mechanism has been found that can bridge the classical percolation and -core percolation for a general , which always causes a discontinuous percolation transition [234].
In network science, the pruning process of -core percolation has also attracted a lot of attention [235, 236, 237, 238, 239], which is used to analyze network structures [211, 240, 241, 242, 243, 244, 245]. It often refers to -core/-shell decomposition [214], and the nodes belong to -core, but not -core, are named -shell.
3.1.2 Variants and related models
Focusing on the pruning process, one can adjust the criterion to observe the emergence of other core structures of networks. Meanwhile, the corresponding percolation transitions can be also defined. Although some of them are not initially motivated by -core percolation, here we review these studies roughly attributed to variants and related models of the -core percolation.
Heterogeneous -core percolation
In the pruning process of -core percolation, if different thresholds are allowed for different nodes, the model becomes a sophisticated one known as heterogeneous -core percolation [246, 247, 248, 249, 250]. Specifically, after the initial node removal, some of nodes need subtrees to survive from the pruning process, some of nodes need subtrees, and so forth.
A representative example of the heterogeneous -core is the binary mixture that nodes have a threshold of either or distributed randomly through the network with probabilities and , respectively. With the framework figured by Eqs.(88) and (90), one can easily express the size of the heterogeneous -core as a linear combination of those for the two thresholds [246, 247, 248, 249, 250], each of which takes the form as the right hand side of Eq.(88) or Eq.(90).

The transition nature of the heterogeneous -core percolation obviously depends on the probabilities assigned to different thresholds, as well as the values of thresholds. Although the cases and behave similarly in -core percolation, the percolation transitions of and are much different. For , there is a crossover of the continuous and the hybrid percolation transitions [247], i.e., in the phase diagram the lines for the two types of phase transitions match at a tricritical point, see Fig.10 (a). In contrast, the case demonstrates a complex phase diagram: the line for the hybrid transition ends at a point that is out of the line of the continuous transition, see Fig.10 (b). This means that a double percolation transition can be observed in the system for some appropriate probabilities [248], namely, first showing the continuous transition, and later the discontinuous hybrid transition. In general, the tricritical point never occurs for the case , whereas in the case it is presented only for [249]. It is also worth pointing out that the case can also map onto a model of glasses on the Bethe lattice [251], which suggests the same universality class.
More generally, the ternary mixture [252] and the generalized case [250] were also investigated to show new types of critical phenomena. Through the analytic calculations and the numerical simulations on ER networks, Chae et al. concluded that the heterogeneous -core percolation can be featured by the series of continuous transitions with order parameter exponents , discontinuous hybrid transitions with or , and three kinds of multiple transitions [250].
Cascading failure model
A special case of the heterogeneous -core percolation is the one with threshold for nodes with degree , where [194, 253, 254, 255, 256, 257, 258, 195, 259, 260]. In other words, if a node can be preserved from the pruning process, must be satisfied for any stages, where and are the current and the initial degree of node , respectively. This node removal process is usually used to model the spreading of failures on networks, hence its name cascading failure model, sometimes also referred to as threshold model.
The simulation results suggest the existence of the crossover of the continuous percolation transition and the discontinuous percolation transition [195]. However, more detailed checking of the critical phenomena as that of heterogeneous -core percolation is still lacking. More often, the emergence of the giant cluster in this model is studied as a criterion for network robustness rather than a characterization for phase transition. We will review these works in the later sections.
In addition, there are two caveats to this model. First, many works on this cascading failure model focus on the clusters formed by failed nodes, not those of preserved nodes [194, 253, 256, 257, 258, 261, 259]. Second, there is another model in network science called cascading failure model which focuses on the overload failures, see Ref.[262] and subsequent references for details.
Bootstrap percolation
Along with the -core percolation, there is an important and well-known model, called bootstrap percolation. In the early literature the bootstrap percolation just refers to the model of -core percolation introduced above, such as Refs.[215, 263, 246]. Now, the bootstrap percolation is generally referring to an activation process, which starts with a fraction of active seeds (occupied nodes) and other nodes (unoccupied) will be activated (occupied) when they have at least activated neighbors. A theoretical analysis for this model like Eqs.(88) and (90) can be found in Refs.[196, 264, 265]. This model and its variants are often used to describe the spreading dynamics in network science. A typical example is the cascading failure model reviewed previously.
Although the bootstrap percolation is an activation process beginning from a sparsely activated network, while the -core percolation is a pruning process beginning from the whole network, a corresponding relation between them can also be established [248]. For comparison, we construct a heterogeneous -core percolation with . Threshold is randomly assigned to a fraction of nodes corresponding to the seeds in bootstrap percolation, and other nodes have threshold . By this mapping, the heterogeneous -core percolation can demonstrate very similar critical phenomena as the bootstrap percolation, i.e., a double percolation transition [196, 248]. However, this model cannot completely recover the bootstrap percolation [248]. This is because all the clusters in the bootstrap percolation must grow from the seeds, while for heterogeneous -core percolation nodes can also survive from the pruning process by forming a compact cluster. Moreover, Di Muro et al. also pointed out that the heterogeneous bootstrap percolation is the complement of the heterogeneous k-core percolation for complex networks with any degree distribution in the thermodynamic limit, as long as the thresholds of the nodes in both processes complement each other [264].
Due to the correlation of bootstrap percolation and -core percolation, many works for -core percolation also contributed to bootstrap percolation. For systems in physical dimensions and the Bethe lattice, one can also refer to Refs.[266, 267, 268, 269, 270, 271, 272]. In network science, bootstrap-like processes are often used to model the cascading dynamics [3, 6, 23, 273, 1, 86], such as the spreading of information, opinion, and disease. Instead of the critical phenomena, these researches are focusing on the dynamical characteristics and their relations with the problems in real life. For this reason, there is no need to lump them into a clear category (bootstrap percolation or heterogeneous -core percolation). Some of these studies will be reviewed in the later sections.
Core percolation
The core of a network is defined as the subnetwork after a greedy leaf removal (GLR) procedure. Here, the leaf of a network refers to the node of degree . The GLR procedure is just iteratively removing nodes of degree along with its neighbor. Note that the nodes with degree only have one neighbor. Apparently, the GLR procedure is more destructive than the pruning process of -core percolation, and finite clusters cannot exist in tree-like networks. As the -core percolation, the core percolation model is also used to identify the core structure of networks, which could dominate the dynamical properties of complex networks [274].

Considering the branching process, the infinite cluster (core) of a tree-like network can also be obtained exactly [118]. For that, nodes are divided into four categories, see Fig.11: (i) removable: nodes that can become isolated without directly removing themselves, i.e., all neighbors are removable; (ii) removable: nodes that can become a neighbor of a leaf, i.e., at least one neighbor is removable; (iii) removable: nodes that can become leaves but are neither nor removable; (iv) non-removable: nodes that cannot be removed and hence belong to the core. The rule for removable nodes can be ignored because it is not useful to determine the size of the core. Denoting (or ) as the probability that a random neighbor of a random node in a network is removable (or removable), two self-consistent equations can be derived,
| (92) | ||||
| (93) |
where is the generating function of the excess-degree distribution. From the two equations, it can be found that satisfies . With this, we can find the solutions of and . For tree-like networks, if the core exists, it must have infinite size (a giant cluster). Hence, the size of the giant cluster, i.e., the normalized core size, can be expressed as
| (94) |
where is the generating function of degree distribution. This approach can also be generalized for directed networks with given in- and out-degree distributions [118].
The theoretical results show that, for undirected networks, if the core percolation occurs, then it is always continuous, while for directed networks, it becomes discontinuous with a hyperscaling when the in- and out-degree distributions are different [118]. For ER networks the percolation threshold can be solved theoretically [275], and the core of purely SF networks never percolates for any degree exponents larger than . While for the SF networks generated by the static model with only for large [276], the core develops when the average degree is larger than a threshold value, which is actually similar to ER networks.
The leaf removal procedure of the core percolation can also be generalized as that nodes of degree smaller than , together with their nearest neighbors and all incident links are progressively removed from a random network [277]. With this pruning process, the percolation transition can also be well defined, which can be seen as either a generalized core percolation or a generalized -core percolation. Similar to the ordinary -core percolation, this model also shows a discontinuous phase transition for .
Greedy articulation points removal
The articulation points of a network are the nodes whose removal disconnects the network, such as nodes , , and in Fig.11. Those nodes play an important role in keeping the connectivity of real-world networks, such as infrastructure networks, protein interaction networks and terrorist communication networks. Tian et al. proposed a greedy articulation point removal (GAPR) process to study the organizational principles of complex networks [119].
In each iterative step of GAPR, all the articulation points are removed from the network and their sub-clusters disconnected from the giant cluster are also removed. After that new articulation points emerge. This removal process is repeated until there is no articulation point left in the network. Note that at each step all the articulation points are removed simultaneously and the size of the giant cluster in the final network is studied as a key quantity.

It is obvious that if the network is sparse, the giant cluster will finally be destroyed with the proceeding of GAPR. For a dense network, a giant cluster, in which all the nodes connect to each other with at least two paths, can be obtained. Note that this cluster is not equivalent to the -core, or the biconnected cluster (BCC) [278, 279, 117, 218, 216], or the one obtained by GLR. A comparative sketch of the -core, the BBC, the cluster preserved after the GLR, and the one after the GAPR is shown in Fig.12.
Next, we briefly cover the relations between these clusters. For convenience, let , , , and be the subnetworks after applying the pruning rules of -core, BBC, GLR, and GAPR, respectively. For -core, one only needs to recursively remove the nodes with degree , thus some tree-like structures might exist in -core. The nodes in a BCC must connect each other with more than one independent paths. This further requires removing the nodes and links that do not belong to any loops from the -core, therefore, . For GLR, when we remove the nodes with degree , their root nodes will also be removed, thus we also have .
However, the relation of and is network dependent. The case shown in Fig.12 gives an example that . Considering a network configuration that two triangles are connected by a degree- node, we can also have . But both and are larger than . This is because all the nodes and links that do not belong to and are certainly not in , whereas the articulation points excluded from might contribute to or , see Fig.12. In summary, for a given network, we have the relation .
An additional consequence of the above relation is that the emergence of the giant cluster after GAPR needs a denser initial configuration than that after GLR. For ER networks, it has been found that the critical point of the percolation induced by GAPR is [119], which is obviously larger than the one induced by GLR (core percolation) [118], see Tab.3 for the percolation thresholds of some models on ER networks. This percolation is also proved to be a hybrid percolation transition with critical exponent . Note that the core percolation is always continuous for undirected networks. Besides, if one only does a finite iteration of the GAPR, the percolation transition can also be observed, and will have the same nature of the ordinary percolation. This finding has the same manner of the so-called history-dependent percolation on multiplex networks [199].
There is also a variation of GAPR: iteratively remove the most destructive articulation point that will cause the most nodes disconnected from the giant cluster of the current network. This is called articulation point targeted attack strategy [119]. Given a limited “budget” (that is, the number of nodes to be removed), this strategy is very efficient in reducing the giant cluster, compared with strategies based on other node centrality measures, such as degree [84, 85] and collective influence [280].
The statistical properties of articulation points, i.e., the probability that a random node in a network is an articulation point, has been also derived in Ref.[281]. It has been found that high-degree nodes are more likely to be articulation points than low-degree nodes. Articulation point is related to another concept of “bridge”, which is a link whose removal disconnects the network and increases the number of connected clusters [282]. Both articulation point and bridge can be used to qualify the importance of a bridge structure in damaging a network and provide useful ideas to destroy a network efficiently.
Color-avoiding percolation
In the color-avoiding percolation, the nodes in the percolating cluster also need more than one path that connect with each other. The details are as follows. First, each link is assigned a color chosen from . If there exists a path between two nodes after the removal of all the links of color , the two nodes are called -avoiding connected. Then, if two nodes are -avoiding connected for all the color , we say that the two nodes are color-avoiding connected. Thus, the color-avoiding percolation studies the behaviors of the giant cluster, in which all the nodes are color-avoiding connected. The color avoiding can also be generalized as the case where arbitrary sets of colors are avoided. Furthermore, colors can also be assigned on nodes, that is the setting when the model was first proposed [283].
Different from the previous percolation models, the color-avoiding connected clusters cannot be simply acquired from a single pruning process. Instead, one can find -avoiding connected clusters for all the color , then the intersections of these clusters are just the color-avoiding connected clusters, see Fig.13 for a schematic of a three-color case. Due to this intersection process, the connectivity of a color-avoiding cluster could access through some nodes/links outside the color-avoiding cluster.
In Ref.[284], it is suggested that the complexity of finding the color-avoiding cluster highly depends on the exact definition, using a strong version the problem is NP-hard, while using a weaker notion makes it possible to find the components in polynomial time. In spite of this, there are some special structures that surely do not contribute to the color-avoiding connected clusters. The first is the bridge link, whose removal disconnects the network. The second is the nodes that all their links have identical colors. A typical example for these two structures is the nodes of degree and their links, i.e., the leaves of the network.
Besides, the size of , i.e., the number of colors , also has significant restrictions on the structural features of the color-avoiding connected clusters. First, a small generally results in a large frequency for each color, thus the emergence of color-avoiding clusters for small requires a dense connection. Second, the size of the color-avoiding connected cluster has a lower bound, which increases with the color number . All these suggest that the color-avoiding connected cluster must have a relatively dense and complex structure, containing many loops.

If there is only one color , the model reduces to a classical percolation with respect to the fraction of colored links/nodes. For , the critical behaviors have a rich, multifaceted nature, depending on the network topology, the number of avoided colors and the color frequencies [283, 209, 210, 284]. If all the colors have identical probabilities, the results on ER networks show that the critical exponent is dependent on the number of colors, i.e., . This is identical for both node and link coloring. Varying the color frequencies, fractal exponents can also be observed. However, topological constraints of SF networks are so strong that the corresponding critical behaviors are independent of the number of the colors (only dependent on the exponent ), but still dependent on the existence of the colors and therefore different from standard percolation. Due to the vanished percolation threshold, the breaking of the universality class of the site percolation and the bond percolation can also be observed for . In Ref.[285] a generic analytic theory that describes how structure and sizes of all connected components in the network are affected by simple and color-dependent bond percolation was also established.
3.2 Percolation on interdependent/multiplex networks
The hybrid percolation transition is not unique to the -core percolation [20, 21, 286, 287, 288, 289, 290, 291]. In the last decade a major concern in network science, the interdependent networks or multilayer networks [8, 9], also involves a dependent percolation, for which both abrupt change and critical exponents can be found at the critical point [120, 121, 292]. For convenience, the following discussions are given by means of interdependent networks [120], see Fig.14 for an example of the interdependent networks.
This model considers the iterative percolation process between different network layers. If a node does not belong to the giant cluster of one layer, its dependent nodes in other layers are also no longer eligible to be considered in the percolation of their layers, and vice versa. Obviously, one must check the percolation process of each layer interactively to obtain a steady giant cluster, referred to as the mutual giant cluster. Thus, this model checks the emergence of the mutual giant cluster after an initial node removal.

3.2.1 Model and phase transition characteristics

To provide a direct and precise description for this percolation model, the dependence link is used to connect dependent nodes in different network layers, see Fig.14. Specifically, a dependence link between node and node means that if node is removed, node will also be removed, and vice versa. The node removal process caused by dependence links is often called dependence process. Correspondingly, all the finite percolation clusters in each layer will also be removed from the system, which is called percolation process. Thus, after an initial node removal (fraction ), the removal of nodes caused by the percolation process and the dependence process will occur alternately until no more nodes can be removed, see Fig.15. The remained nodes (if any) form the mutual giant cluster, in which nodes are reachable through each layer. Note that if we do not remove the finite clusters from the system, the finite mutual clusters can also be well defined in the steady state [293, 199].
The above pruning process to find the mutual giant cluster was first proposed in Ref.[120], in which the dependence links are assigned randomly between two network layers, labeled and (see Fig.14). Assuming both the two network layers have tree-like structures, we can express the size of the mutual giant cluster as
| (95) |
Here, () represents the probability that a randomly chosen link in network layer () leads to the mutual giant cluster. By analogy with that of classical percolation equations (15) and (16), we can know that the right hand side of Eq.(95) just describes the final state of the pruning process, i.e., all the preserved nodes must be reachable in both layers. Similarly, and must satisfy
| (96) | ||||
| (97) |
The above three equations (95)-(97) were first used to analyze the percolation on the networks with dependence links by Son et al. [294, 295]. Considering the iterative process of the pruning process, this model can also be solved. That is the analytical method when this model was proposed [120, 121], which is equivalent to the method listed above [296, 297].
From Eqs.(96) and (97), we can also find the critical point of the system as we do for the classical percolation. The solution of shows a similar behavior as -core percolation illustrated in Fig.9, indicating a discontinuous transition. The value of is significantly larger than that of classical percolation. For example, two interdependent ER networks give , while for single ER networks. This also means that is the minimum degree to observe a mutual giant cluster in two interdependent ER networks. Even for SF network layers with , the mutual giant cluster can emerge at a non-vanished . Further study have showed that this discontinuous transition is also a hybrid transition with exponent [121, 292], which is the same as the -core percolation with .
Parshani et al. also pointed out that the number of iterations in the cascading process of interdependent networks diverges when [121], and thus can be used to identify the transition point in numerical simulations. This is mainly because there is a plateau in the collapse of the system, and the plateau regime increases with the system size. Zhou et al. found that during the collapse there is also a random branching process at criticality, i.e., a continuous percolation transition. This simultaneously continuous phase transition is just the origin of the observed long plateau regime in the cascading failures and its dependence on system size [298]. This result coincides with the one found in Ref.[199], in which the percolation transition is defined in each iteration, called generation. Theoretical analysis indicates that for any finite generation, the system demonstrates a continuous percolation transition. Monte Carlo simulations on ER networks further suggest that all these continuous transitions belong to the same universality class. Specifically, SF networks with exponent have a vanished critical point for any finite generations. For infinite generation, it just recovers the percolation transition on interdependent networks, i.e., it has a nature of hyper transition. Hu et al. further pointed that in two-dimensional systems the infinite generation still presents a continuous transition, but with a different universality class [200].
By decreasing the coupled strength (the fraction of nodes that have dependence links), this discontinuous percolation transition can also reduce to the continuous transition [121]. An exception is the coupled lattices, for which the networks abruptly collapse for any finite [299]. But this does not always mean the continuous percolation cannot exist in interdependent spatially embedded networks. If the dependence links establishing the interdependence between two lattices are not random but have a typical length , the percolation transition will be continuous for (lattice units), and discontinuous for larger [300]. For , the percolation threshold increases linearly with from at and reaches a maximum, for , and then gradually decreases to for . This is mainly because the spatial embedding induces a similar structure in different network layers, and thus breaks the cascading picture of interdependence [294]. This model has also been generalized to high dimensions [301]. The simulation results show that the value decreases with dimension, and for lattices with dimension larger than or equal to , the continuous percolation transition disappears. This suggests that a high degree of freedom (high dimension) decreases the structural similarity of the spatially embedded networks under random node or link dilution, thus reconstructs the cascading picture.
It should be noted that the model, based on which the authors claimed that percolation transitions are not always sharpened by making networks interdependent [294], is a bond percolation model on the interdependent square lattice with typical length , and not the one discussed above. Thus their findings do not contradict that of Ref.[300], which considers the site percolation with different typical lengths. Grassberger also studied the bond percolation model with typical length in high dimension lattices [293]. The simulation results have showed that there is an upper critical dimension , below which the percolation transition is always continuous, and at least for – not in the universality class of ordinary percolation. This suggests that although the similar structure induced by spatial embedding breaks the cascading picture of interdependence, it indeed changes the nature of the branching process in the continuous percolation transition. The bond percolation has also been studied on multiplex networks, and reported a multiple percolation phase transition [302]. Here, the multiple percolation transition refers to more than one transition in a percolation process, also is reported in other related percolation models [303, 304, 305, 306, 307, 308].
In Ref.[293], an efficient and implementable algorithm has also been proposed, based on which some other critical behaviors of the percolation on interdependent networks have been rechecked, numerically. The result suggests that for the model of Ref.[300] there exists such a above which the transition seems to be discontinuous, but a strong evidence that this is related to very large finite-size corrections was also found. Moreover, this work also provided some evidences that the cluster statistics of independent ER networks can be exactly described by mean-field theory, while the cascade process cannot. For interdependent lattices with dimension a discontinuous transition was observed as ER networks, but a nontrivial distribution of finite clusters also exists at the transition point.
3.2.2 Algorithms for reducing time complexity
For facilitating the studies on non-tree-like networks, some efficient algorithms have been developed to find the mutual giant cluster. Tracing the largest cluster during the whole pruning process, the algorithm proposed by Schneider et al. can achieve time complexity [312]. Nevertheless, this processing is too loose to study the critical phenomena, since an initially large cluster could be taken over by a cluster that had started smaller after the pruning process, especially near the critical point. Apart from the critical phenomena or limited to tree-like networks, this algorithm might be a good choice to avoid brute-force searching.
Although the finite mutual clusters are ignored in the original definition of this percolation model [120, 121], all mutual clusters must be taken into count for providing a more reliable simulation. A viable way to define such clusters can be found in Refs.[293, 199], in which the percolation transition can be defined in each generation. Based on a fully dynamic graph algorithm [279], Hwang et al. proposed an efficient algorithm designed to proceed as links are deleted, whose time complexity is approximately for random networks [313]. With this algorithm, large scale simulations for ER and -dimensional interdependent networks have been carried out, which verifies the exponents for the order parameter and its fluctuations numerically, as well as the finite avalanches [314]. Stippinger et al. later generalized this algorithm to efficiently simulate interdependent networks with healing [315].
Besides, Grassberger proposed an easily implemented algorithm to find all the mutual clusters by mapping the problem onto a solid-on-solid model [293]. This method is simply done by alternately performing Leath-like processes on different network layers [316], each is referred to as a “wave” from the starting node. Waves are confined to the nodes that have the same “height” as the starting node. All the nodes’ heights are initially set as , and after the spreading of a wave, the heights of the involved nodes increase by . Do the searching process for all the possible starting nodes, a landscape of node heights can be obtained, from which the mutual giant cluster and the distribution of mutual cluster sizes can be found. With some techniques this algorithm can also simulate the percolation process on interdependent networks, effectively. In Ref.[315], it is also pointed out that compared to the algorithm of Ref.[293] their algorithm is generally intended for fast updates at the cost of higher memory use.
3.2.3 Variants and related models
With the growing trend of multiplex networks, this percolation model has also been employed frequently to figure out the robustness of multiplex networks [8, 317, 296, 318, 9], which can be generally classified into three categories, single networks with dependence links, networks of networks, and multiplex networks with general and special dependence. Most of these studies demonstrate a hybrid transition as shown above, and a crossover between the continuous and discontinuous percolation transition can also be found in some of them. Besides, the correlation between different network layers can also be represented by interconnections, in which the percolation transition can be also observed [319].
More importantly, these works show the robustness of multiplex networks in various environments, and are meaningful for understanding the structures and the robustness of multiplex networks. More results will be reviewed later when we turn our thoughts to the applications of percolation model. Of course, one can find more information in the special papers and books on multiplex networks [8, 317, 296, 318, 9].
3.3 Explosive percolation
The explosive percolation was proposed by Achlioptas et al. in 2009 [201], hence this type of percolation process is named as Achlioptas process. In general, Achlioptas process is a competitive process that can be realized by many rules, and the key is suppressing the emergence of a giant cluster. There is a specialized review article for this issue [206], here we only give a brief introduction of the main findings.
3.3.1 Achlioptas process

As we know, ER networks can be generated by randomly inserting links into a set of nodes one by one. The Achlioptas process is just a variation of this process [201]. Assuming there are initially nodes and no links, at each time step, potential links are arbitrarily chosen, each of which is supposed to bridge two distinct clusters with size and , respectively. (The two nodes can belong to the same cluster with no impact on the following process). Then, according to a function , the potential link with the smallest is inserted eventually, and other potential links are discarded, see Fig.16 (b) as an example. Repeating this process until the expected number of links is met. Such a selection mechanism is often called the best-of- rule or the min-cluster- rule [202], and the function represents the competitive rule.
In order to suppress the emergence of the giant cluster, the competitive rule must be of positive correlation with and . Two commonly used ones are the product rule and the sum rule . For , this model reduces to the ER network model, which percolates when links have been inserted, i.e., . For , the emergence of a giant cluster will be suppressed, resulting in an explosive percolation. A comparison of the two cases is shown in Fig.16 (a). One can find that the explosive percolation shows a sharper transition with a larger threshold.
Since Ref.[201], many other generalized Achlioptas processes have been proposed and investigated. A typical example is the -node (-vertex) model. In this model nodes are chosen randomly at each step, and two of them are connected according to a selection criteria, for example, the size difference [320]. The original Achlioptas process just corresponds to , and the case with different selection criteria is used in many studies [204, 321, 322].
Besides, there are some other models can realize the Achlioptas process, such as BFW model [323, 324, 325, 326, 327, 328, 329, 330], dCDGM model [203, 331, 332, 333, 334, 335, 336, 337], Hamiltonian model [205], diffusion-limited cluster aggregation model [338, 339], spanning cluster-avoiding model [340, 341], and hybrid model [342, 343, 344]. One can find a contrast analysis of these models in Ref.[345]. Most of these models can be generalized to any networks by constraining the potential links in a given configuration. One can refer to Ref.[206] for more information.
3.3.2 Phase transition characteristics
For a deep understanding of the explosive percolation, one can consider a complete network with size [202, 321]. In each step , all the unconnected node pairs provide potential links, i.e., . In this case, up to new links are added, only connect isolated nodes to result in clusters with size such that the maximum cluster size remains for the first steps. Each of the subsequent links connects clusters of size to clusters of size keeping the maximum cluster size until step . As an analogy, in step , the remaining two clusters of size join. The jump of the largest cluster is thus clearer, indicating a discontinuous transition [324, 346]. In general, one can connect a link chosen from all the possible positions at each step, thus the jump of the largest cluster is excepted in any network configurations. By the way, such successive jumps of the largest cluster are named microtransition cascades [330], which is probably used to warn signals anticipating phase transitions in complex systems.
A small will relax the suppression for the emergence of the giant cluster, thus the jump of the largest cluster is blurred. Although a sharp transition might also be observed as shown in Fig.16, Riordan et al. pointed out that any rule based on picking a fixed number of random nodes gives a continuous transition [324]. They also suggested a lower end of the range: Whenever as , the Achlioptas process exhibits explosive percolation. The findings of da Costa et al. show that the Achlioptas process is irreversible, which also indirectly suggests a continuous transition [203]. However, these findings do not mean that the Achlioptas process behaves exactly like a continuous percolation. The discontinuities can also be observed in the Achlioptas process [320]. The double humped distribution of the sizes of the largest cluster and the hysteresis, which are both recognized as the sign of discontinuous transition, can be also found in finite systems [347, 348]. These works also reported a finite-size behavior with non-analytic scaling functions, and demonstrated that the explosive percolation transitions are indeed continuous but with some unusual scaling properties [203, 349, 350, 325, 347, 351, 352, 345]. Riordan et al. also pointed out that the fluctuation of the order parameter in explosive percolation does not disappear in the thermodynamic limit [322].
3.4 Percolation transition during the growth of networks
In contrast to the network models with a fixed size, such as the configuration model and ER network model, there is a family of network models with growing size featuring the growing property of real networks [3, 4, 353]. A typical example is the famous BA networks [56]. However, there is always only one single cluster in the growing process, thus the system always percolates. To observe a percolation transition in the growth of a network, it must be allowed that new nodes enter the system without connecting to the existing nodes. In this way, the network could contain isolated nodes and finite clusters.
Instead of looking at the network configuration, one can solve the growing network model by checking the evolution process via the master equation. The key point is featuring the increment and decrement of the parameters in one time step, which might vary from model to model [354, 125, 355].
3.4.1 Growing random network
A simple rule to achieve a percolation transition in network growing is the one proposed in Ref.[125], called growing random network. This model begins with no node, and at each time step a new node is inserted into the system, then two nodes are chosen randomly from all the existing nodes and joined by a link with probability .
At time step , there are nodes in the system. Let be the degree distribution at time step , then a rate equation for the evolution of the degree distribution can be established,
| (98) |
The two terms on the right hand side of this equation correspond to the expected increment and decrement of nodes with degree in one time step, respectively. For , , and Eq.(98) reduces to a recursion formula . Note that Eq.(98) holds only for , and for it is specialized as
| (99) |
which gives for . Consequently, the degree distribution has a closed form for ,
| (100) |
Obviously, the degree distribution decreases with the increase of . In fact, the power-law degree distribution can also be produced in this model by introducing preferential attachment [355, 356].
From Eq.(100), the generating functions are also available, those are and . Substituting into the Molloy-Reed criterion Eq.(28), we can find the percolation threshold . This result is for an uncorrelated tree-like network with degree distribution Eq.(100), whereas the growing random network has degree correlation. Specifically, earlier nodes are sure to form a core, in which there is a higher average degree. This indicates that the giant cluster forms more readily than in a network whose links are uniformly distributed.
To find the percolation threshold of the growing random network, we need to examine the cluster size distribution [125]. Let be the normalized cluster number at time step , i.e., the ratio of the number of clusters with size to the total number of nodes, then a rate equation for the evolution of can be expressed as
| (101) | ||||
| (102) |
Note that can be interpreted as the size of the cluster that a randomly chosen node belongs to. Therefore, is the increment of clusters with size by combining two small clusters in one time step, while for the increment just is the newly added node; is the decrement of clusters with size in one time step by combining two clusters that at least one of them has size .
For , , then Eqs.(101) and (102) can be simplified to
| (103) | ||||
| (104) |
Although the two equations cannot give a closed form of , we can find a recursive function for the generating function by multiplying both sides of Eqs.(103) and (104) by and then summing over . The result reads
| (105) |
where is used. Now, we have
| (106) |
Note that the mean cluster size , then the critical behavior of can be derived from Eq.(106). In the supercritical phase, the giant cluster exists, thus , Eq.(106) gives the mean cluster size . For the subcritical phase, all the clusters have finite sizes, i.e., , then can be solved by letting in Eq.(106), that is
| (107) |
For a physical meaning, is required here, which gives the percolation threshold . This threshold is smaller than that for the configuration network with the same degree distribution, confirming that the growing mechanism facilitates the forming of the giant cluster, theoretically [125].
As just described, the critical behavior of can be summarized as
| (108) |
This means that the mean cluster size jumps discontinuously at the percolation threshold, whereas diverges for the standard percolation.
Moreover, compared with the static network, the existence of the core makes the size of the giant cluster increases more slowly in the supercritical phase. The simulation results imply that the size of the giant cluster obeys with , and suggest an infinite order phase transition [125, 357, 358, 359], like the Berezinskii-Kosterlitz-Thouless phase transition in the condensed matter [360, 361]. In addition, such a phase transition was also found on the substrate formed by XY spin configurations [362]. Some simulation verification for these findings and the fractal geometry can be found in Refs.[363, 364]. In a growing network with a renormalization group treatment, Dorogovtsev also found that the critical behavior of percolation on growing networks differs from that in uncorrelated networks [365].
3.4.2 Variants and related models
Similar results can also be found in a general model with preferential attachment [355], i.e., the link between nodes and is inserted with a probability proportional to , where () is the degree of node (), and is a positive constant which plays the role of additional attractiveness of node for new links [366]. The power-law form of the cluster size distribution in standard percolation has a decay for large sizes both above and below the percolation threshold. However, in the growing network the power-law form can be observed in the entire phase without the giant cluster. This indicates that the system is in the critical state for the entire phase.
Instead of connecting nodes randomly, other typical mechanisms for generating networks can also be incorporated into the growing network model, such as BA network model [367] and the explosive percolation model [368, 333, 369, 308]. In these models, when a new node enters the system, with probability links are inserted following the given rule, otherwise, do nothing. When the rule of BA network model is applied, the percolation transition is still of infinite order [367]. This mainly because the rule of BA network model does not break the picture of the forming of the giant cluster, which is the crucial factor for the nature of infinite order transition [355].
Conversely, the Achlioptas process induces a suppression effect against the growth of the large clusters. Thus, when the Achlioptas process is used, the percolation of growing network can revert to a nature of the second order transition with scaling behaviors depending on the specific rules [333, 369]. It should be pointed out that if there are not enough potential nodes/links in the Achlioptas process, the growth mechanism will still dominate the nature of the percolation transition, hence an infinite order transition [368]; rather, if the Achlioptas process is done with global information, the growth of large clusters can be completely suppressed, so that the continuous percolation transition will change to a discontinuous one [370, 308].
Besides, the infinite order transition can occur even in the hierarchical networks with small-world effects [142, 371, 144, 372]. For the growing network without percolating state [373], the preferentially growing network [374], and the growing directed network [375, 376], the power-law distribution of cluster sizes can be also observed. The percolation transition of growing networks has also been studied by diluting links or nodes in a generated network [377]. The dense structures were also found to undergo phase transitions in the growth of networks[378, 379].
4 Applications to network structural analysis
The previous section mainly reviews the typical percolation models on complex networks, focusing on the phase transition and the critical phenomena. In fact, the percolation theory, including conceptions, theoretical methods, and algorithms, has a broader range of applications in the study of network structures and dynamics. This is mainly because the percolation model is by nature for featuring the cluster forming process in random media, while network science is exploring the properties of various topological structures and the correlation with dynamics. In this section we will review the applications to network structural analysis. We should point out that some of these problems are not firstly motivated by percolation, however, a good interpretation can be given from the perspective of percolation.
4.1 Hierarchical structure of networks
Hierarchical structure is one of the important characteristics of real networks [3, 5, 6, 1, 2], which can be generally identified by either a branching process or a pruning process. For tree-like networks, the analytical method for network percolation is often employed to find theoretical results, while for non-tree-like networks percolation process can also be used as an algorithm to identify hierarchical structures.
4.1.1 Tree-like networks
As shown in Fig.17, the hierarchical structure of a tree-like network can be figured out by a spanning tree. For a large enough network with tree-like structures, any node can be seen as the root of the spanning tree. Then the direct neighbors of this node are the first shell of the network, and the neighbors’ neighbors belong to the second shell, and so on. This is just the branching process we discussed in Sec.2.2. Thus, the generating function can be also employed to study this shell structure [48].

Since the root node is arbitrarily chosen, the sub-branchings from it can be described by the generating function . Here, an refers to an outgoing link from the root node. Following these outgoing links, we can find the nodes in the first shell of the network. As the explanation for Fig.4, the generating function can be used to represent the state of the node at the end of a randomly chosen link, where also refers to the outgoing link from this node. Therefore, replacing in with , we will obtain the sub-branchings from the nodes in the first shell . Similarly, the sub-branchings from the second shell can be represented by . In general, the sub-branchings coming from the -th shell can be written as
| (109) |
With this iteration relation, Shao et al. found that the distribution of node numbers in these shells follows a power law for a broad class of complex networks [380]. This branching process can also be used to realize the configuration model [381], i.e., connecting nodes with given degrees shell by shell.
Note that loops are forbidden here, so there must be a one-to-one correspondence between the parameter and the sub-branching. Consequently, the exponent for the power of in Eq.(109) is just the total number of sub-branchings from the -th shell. In other words, the derivative of Eq.(109) with respect to at must equal to the average number of nodes in the -th shell,
| (110) |
where is the average number of nodes in the -th shell, and is just the average degree of the network. From Eq.(110), we can also find
| (111) |
This indicates that the growth rate of the node number with shells is a constant . For an infinite network, the shell must be endless, so the node number cannot decrease with the increasing of shells, i.e.,
| (112) |
This is the existence condition of the giant cluster in a tree-like network, namely, percolation threshold, see Sec.2.2.
For a finite network, the number of shells must be finite. Next, we will show how to estimate . Using Eq.(111), the number of nodes in the -th shell can be written as
| (113) |
Summing over all the shells, we obtain the network size
| (114) |
This yields
| (115) |
Real networks usually have and , thus can be approximately represented as
| (116) |
This result can be seen as an approximation of the average distance or the diameter of real networks [382, 383], which indicates that . This is just the small-world effect of random networks.
The above derivations depend on a finite (when ). However, SF networks with give a divergent moment , where is the lower boundary of degrees and is the natural cutoff of degrees. Substituting into Eq.(116), we can find a size-independent , indicating that SF networks are ultrasmall.
Actually, the diameter of SF networks increases with the system size in the form of [70, 384, 385]. To find this, the degree distribution of the nodes in each shell must be checked, separately. In general, an outgoing link is more likely to lead to a node with large degree, which can be seen from the expression of the excess-degree distribution . For finite networks, this means that earlier shells will bag almost all the nodes with large degrees, so that the small degree nodes are located in the periphery of the hierarchical structure. This effect is more notable when networks have strong heterogeneity like SF networks. This mainly indicates that the degree cutoff of nodes in each shell decreases with the growth of shells. With this, the form can be found in [70, 384, 385, 381, 386].
4.1.2 k-shell structure
As pointed above, the hierarchical structure shown in Fig.17 has an arbitrary root. In network science, there is another hierarchical structure with deterministic shells, i.e., -shell structure [193]. For a given network, the -shell refers to the nodes that belong to the -core but not belong to the -core, see Fig.18.

For tree-like networks, one can use Eqs.(88) and (90) to obtain the -core size for any , the size of -shell is thus . In general, the pruning process of -core percolation is just used as an algorithm to identify the -shell structure, called -core/-shell decomposition. The related discussions are far away from the percolation transition. So we will not go into details on this topic here, and one can refer to the specialized review on this topic for details [214].
4.2 Network robustness
In network science, percolation process has already become a paradigm for studying the network robustness. Specifically, one often removes a fraction of nodes from a given network, then checks the existence of the giant cluster. If the giant cluster remains, the resulted network is still considered functional. Thus the percolation threshold can be used to evaluate the robustness of the network. A large threshold indicates that only a small amount of failed nodes can disconnect the network, so its robustness is poor, and vice versa. With different node removal methods, the percolation model can further explain the robustness of networks under various failure mechanisms, some of which are also used to model network dynamics. Here, we review the main findings of the network robustness based on the percolation model from two aspects, single networks and multiplex networks.
4.2.1 Single networks
As mentioned above, the percolation threshold of SF networks is much smaller than that of ER networks with the same link density, especially for SF networks with which have a vanished percolation threshold [83, 84, 85, 72, 86]. This suggests that SF networks are more robust than ER networks. More generally, for networks with the same average degree, the broader the degree distribution, the more robust the network is [387].
For a given link density, the clustering structure compacts node clusters with the price of diluting global connections. Therefore, the corresponding percolation threshold is smaller than that of tree-like networks, indicating that the networks with clustering are fragile [151, 152, 153, 154]. However, highly clustered networks are often characterized as a resilient system [161, 162, 163]. In fact, the two are reconcilable, since strong clustering could induce the so-called core-periphery structure [156, 157], for which the percolation model shows a double transition [158].
More generally, the loop structure, including clustering, is a meaningful concept for network robustness, captured by the connection between a pair of nodes through at least two disjointed paths, termed biconnectivity. Since a pair of biconnected nodes in networks can communicate under the removal of one route, biconnectivity can play a significant role in network robustness [388, 117, 218, 216], as well as other high order connectivity. Some of studies on this topic in terms of the percolation transition can be found in Sec.3.1. Moreover, the resilience of networks with community structure has also been studied by the percolation model, which shows a behavior similar to the spin system under an external field [389].
In addition, the degree correlation can also influence the percolation process on networks, see Sec.2.6. Generally speaking, increasing the assortativity of a network makes the network more robust against nodes removal [390, 172]. In fact, the clustering structure and the degree correlation are inseparable for real networks. Even for network models, it is impossible to adjust the clustering structure arbitrarily without inducing any degree correlation, and vice versa. Therefore, the robustness of real networks, even of some network models, cannot be evaluated by their clustering coefficients or assortative coefficients, individually.
If the hub nodes are preferred to be removed initially, i.e., intentional attack, the percolation model can also be used to study the robustness of networks under targeted attack. A simple implementation approach is to remove a fraction of the nodes with the highest degrees [72], which reports that SF networks, known to be resilient to random removal, are sensitive to intentional attack. More generally, the intentional attacks are commonly realized by removing nodes with probability proportional to [391], where refers to degree. When , nodes with larger degrees are more vulnerable under the intentional attacks, while for , nodes with larger degrees are defended and so have a lower probability to fail. The case just represents the random removal of nodes. This mechanism can also be developed to study the robustness of networks under intentional link attack [392].
For , SF networks become extremely fragile [85], and the percolation threshold will be larger than that of ER networks with the same link density [85] or even equal to [393]. At criticality, the topology of the network depends on the details of the removal strategy, implying that different strategies may lead to different kinds of percolation transitions [391, 392]. An optimal attack is also directly related to optimal graph partitioning and immunization of epidemics [394]. Different structures can also emerge from these pruning processes [395, 396, 397]. Moreover, by mapping the intentional attack to a normal percolation problem, this robustness model can also be solved [398]. Further research also shows that an onion-like structure could be a nearly optimal structure against simultaneous random and targeted high degree node attacks [399, 400, 401].
There is also a special percolation model for the case , called degree-ordered percolation [402], where nodes are occupied in degree-descending order (or alternatively, removed in degree-ascending order). The mean-field results on SF networks suggest that the critical exponents depend on the heterogeneity of the network, and do not belong to the universality class of the standard percolation [403].
Besides, the localized attack, meaning that an attack on a node can destroy the node together with its neighbors within a range, has also been introduced into the percolation model to show the robustness of networks under attacks [404, 387, 405, 228, 406, 407, 408]. When the intentional attacks are dependent on spatial distances, the spatial networks are more fragile than expected [409]. Moreover, the finite-size scaling analysis suggests that for some of the intentional attack strategies, the critical exponents seem to deviate from the mean field, but the evidence is not conclusive [410].
The percolation model is a random process, and the corresponding theory only characterizes the results on average. Nevertheless, two different realizations with the same magnitude of removal could result in very different giant clusters. For the study of the robustness of real networks, the fluctuations of different percolation realizations become extremely important. Bianconi introduced a message-passing algorithm able to predict the fluctuations in a single network, and an analytic prediction of the expected fluctuations in ensembles of sparse networks [411, 412]. The following works also contributed to the stability of the giant cluster [413], the large deviation of percolation [414, 415], and the largest biconnected cluster for random graphs [216]. The results mainly showed that the large-deviation approach to percolation can provide a more accurate characterization of system robustness.
As shown in Sec.2.7, the percolation transition can also be well defined on directed networks, so that with similar consideration the robustness of directed networks can also be studied in the framework of percolation transition. It mainly demonstrates that the GWCC is more vulnerable, and the directed network may have the GWCC and, simultaneously, may not have the GSCC [182, 183, 184, 190, 185, 186, 187, 188, 189].
In addition, if the communication of nodes in the network is effective only if the shortest path between nodes and after removal is shorter than , where is the shortest path before removal, a much smaller failure of the network can lead to an effective network breakdown. This problem was also studied in a percolation form called limited path percolation [207, 416]. Note that this mechanism was also used to feature the entanglement percolation in quantum complex networks [417].
4.2.2 Multiplex networks
In recent years, multiplex network has become a research hotspot. The consideration of multiplex network naturally introduces the interaction between different network layers, thus constructs a cascading picture, which changes the nature of percolation transition, see Sec.3.2. Consequently, the robustness of multiplex networks under the framework of percolation transition has its own characteristics, or even in a completely opposite manner as the single network.
Topological structure
As shown in Sec.3.2, multiplex networks are more fragile than single networks due to the cascading failures induced by the interdependence between nodes from different network layers. More interestingly, the effects of the topology structure on the robustness of the network are also very different from those of the single network.
In Refs.[122, 120], researchers found that a network with a broader degree distribution results in a larger , which is opposite to ordinary networks. As we know, the hub nodes have a dominant role in the robustness of a network. However, when the node dependence is involved, a hub node could depend on a small degree node, which is quite vulnerable during the iterated removal process triggered by the initial node removal. Moreover, a broader degree distribution with the same average degree implies that there are more small degree nodes. Therefore, the advantage of a broad degree distribution for the ordinary network becomes a disadvantage for the network with dependence links. For this reason, the assortativity and high clustering structures will also make such networks fragile [418, 419]. These features are in consonance with the robustness of single networks under intentional attack [395, 391, 392, 396, 397, 404]. For directed networks, the in-degree and out-degree correlations could increase the robustness of interdependent networks with heterogeneous degree distributions, but decrease the robustness of interdependent networks with homogeneous degree distributions and with strong coupling strengths [420].
Inter similarity
In contrast to single networks, the multiplex networks are difficult to defend by strategies such as protecting the large degree nodes (intentional attack with ) that have been found useful to significantly improve the robustness of single networks [398, 421, 422]. This is mainly because the dependence partners could have very different degrees, and defend strategies based on degrees cannot protect the two nodes at the same time. By this consideration, the system will obviously become robust, when the dependence partners have identical degrees [423, 424]. Such correlations between dependent partners are called inter similarity of different network layers.
Parshani et al. introduced two parameters to evaluate the level of inter similarity between networks: the inter degree-degree correlation and the inter clustering coefficient. The simulation results demonstrated that the inter-similar multiplex networks are significantly more robust to random failures than a randomly interdependent system [425]. Theoretically, Hu et al. developed an approach to analyze the robustness of multiplex networks with inter similarity [426]. In their model, there are some probabilities that the dependence nodes of two adjacent nodes in one network are also connected. The studies showed that this inter similarity can improve the robustness of the interdependent networks and change the critical behaviors of the percolation transition. In addition, a similar work has also been done on this problem [427]. The inter-similarity of dependence partners is also studied in single networks. The results show that the local dependence, i.e., dependence partners are adjacent, can result in a robust network [428].
Dependence relations
The dependence links were proposed to reflect the dependence relationships in reality, but not all the nodes in a networked system have such dependence. In this way, the percolation on networks with weak dependence has been studied [121, 422, 429]. In this model, instead of each node having a dependence partner, only a fraction of nodes have dependence links. When , the multiplex networks reduce to some single networks, while , the fully dependence model discussed above is covered. Thus the system becomes robust with the decreasing of .
Besides, without reducing the number of dependence links, the dependence can also be adjusted by the so-called dependence/coupling strength [430, 431, 432]. When a node loses its dependence partner in the pruning process, each of its links is removed from the network with a probability . With this mechanism, heterogeneous dependence can be realized by assigning different dependence links with different dependence strength, and the results demonstrate that the heterogeneous dependence strength makes the system more robust [431]. In addition, Liu et al. proposed a model that integrates interdependent networks and single networks with dependence links [433]. They found that when most of the dependence links are inner- or inter-ones, the coupled network system is fragile and shows a discontinuous percolation transition. However, when the two types of dependence links have nearly the same number, the system is robust and shows a continuous percolation transition.
The one-to-one dependence in the original model is also generalized to multiplex dependence or group dependence. Obviously, the multiplex/group dependence makes the spreading of failures easier, so that the vulnerability of interdependent network under various dependence mechanisms is demonstrated [122, 434, 435, 436]. Wang et al. further showed that a larger dependence group did not always make the network fragile, which is also dependent on the grouping mode and the cascading rules in the group [437, 438]. Li et al. also pointed out that the asymmetric dependence can break the cascading picture between dependence partners, thus results in a robust network [439].
Network of networks
Considering the real situation that more than two networks are connected by the dependence links, Gao et al. extended the model of the interdependent networks into the model of a network of networks [440, 441, 442, 443, 444, 445, 446]. In this model, each network is composed of a set of nodes and connectivity links, then the dependence links connect them to form a larger network. The common factors that influence the network robustness, such as clustering [447], and targeted attack [448], have also been explored in the network of networks. Liu et al. proposed a “weak” interdependence mechanism capturing the differences of networks, where network layers at different positions within the multiplex system experience distinct percolation transitions [306].
In general, the robustness of network of networks decreases with the increasing of network layers. Due to the cascading failures caused by the dependence of networks, the percolation transition of a network of networks could be discontinuous and even a single node failure may lead to an abrupt collapse of the system [440, 441, 442]. Based on a network model composed of spatially embedded networks, Shekhtman et al. showed the extreme sensitivity of coupled spatial networks and emphasized the susceptibility of these networks to sudden collapse [449]. In real life, infrastructural networks are governed and operated separately, and interactions are only allowed within well-defined boundaries. Therefore, for different situations, the percolation on network of networks may be very different. For example, Radicchi et al. introduced a model of percolation where the condition that makes a node functional is that the node is functioning in at least two network layers of the system, and found that the addition of a new layer of interdependent nodes to a preexisting multiplex network will improve its robustness [450].
In addition, the network of networks is also studied as interacting networks [319, 451, 452], in which the connections between the network layers are ordinary links. A system of this kind is therefore equivalent to a single modular network, for which the system can be easily separated into isolated modules, and different modules might percolate at different thresholds [453, 454, 455, 389]. It should mention that there are some special reviews on the resilience of network of networks [456, 457]. One can refer to those for more details.
4.3 Community detection
Community structures are the subsets of nodes within a network that have a high density of within-group connections but a lower density of between-group connections. Traditional community detection methods are usually deterministic and used for finding separated communities, whereas most of the actual networks are made of highly overlapping cohesive groups of nodes. To identify the overlapping communities in large real networks, Derényi and co-workers have proposed a dependent percolation model, called clique percolation [170, 171].
A clique is a fully connected subset of nodes of a network; such a subset with nodes is often called a -clique. In their model, two -cliques are regarded as adjacent, if they share () nodes. With this connection rule, a node can belong to more than one clique cluster, see Fig.19. Then, by identifying these clique clusters as communities, the overlapping communities are thus detected.
This method also has a clear limitation. That is the network must have a large number of cliques, so it may fail to give meaningful community structures for networks with just a few cliques. For more discussions on this problem, one can refer to Ref.[458].

Aside from the analysis of network structure, clique percolation transition itself provides a set of very interesting problems. As classical percolation in ER networks, -clique percolation considers the behaviors of clusters formed by connected -cliques for a different connection probability of links. The simulation results in Ref.[170] indicate that the fraction of nodes in the largest -clique cluster makes a discontinuous percolation transition with increasing connection probability ; however, the fraction of -cliques in the largest -clique cluster demonstrates a continuous percolation transition. Bollobás and Riordan gave a rigorous mathematical result of the critical point for a more general percolation model, in which two -cliques are regarded as adjacent if they share or more nodes [123]. The Monte Carlo simulation indicates that for different and , this general clique percolation model could demonstrate rich critical phenomena [459].
In Ref.[124], Li et al. proved theoretically that the fraction of nodes in the giant clique cluster for makes a step-function-like phase transition in the thermodynamic limit and a continuous phase transition for . More interestingly, they showed that the order parameter at the critical point is neither nor , but a constant depending on and . In addition, the fraction of cliques in the giant clique cluster always makes a continuous phase transition as the classical percolation. Through analysis of the clique cluster number distribution, they found that there is no essential distinction between the two processes measured by and , and the different behaviors are mainly caused by the quantitative relation between the total numbers of cliques and nodes. Besides, the clique percolation has also been studied in two-dimensional systems [208]. The finite-size scaling analysis shows that, in contrast to the clique percolation on an ER network where the critical exponents are parameter dependent, the two-dimensional clique percolation simply shares the same critical exponents with traditional site or bond percolation, independent of the clique percolation parameters [208].
4.4 Vital nodes identification
The heterogeneity of complex networks shows up in the different roles that nodes play in the structure resilience and the dynamical behaviors. The vital nodes identification classifies nodes based on their roles played in network structure or dynamics [245]. As a model of cluster forming, percolation model has also been employed to identify vital nodes.
In Ref.[460], Piraveenan et al. proposed a centrality measure based on the percolation state of networks, called percolation centrality. In this method, percolation state of node is denoted as . Specifically, indicates that node is in the fully percolated state, and for a non-percolated state, while a partially percolated state corresponds to . Accordingly, the percolation centrality of a node in a network with size is defined as
| (117) |
where is the number of shortest paths between nodes and , and is that pass through node . With this, nodes in large clusters are considered to be more important. If all nodes are in the same cluster, , so that the percolation centrality reduces to the well-known betweenness centrality. From this perspective, percolation centrality is just a betweenness centrality with weighting based on percolated state.
In percolation process, if a node’s removal breaks down the network into many small clusters, the nodes must be very important for the network structure. From this basis, Morone and Makse proposed a method to find the superspreaders in network spreading, in which the influence of a node is the size of the largest cluster after removing this node [280]. Accordingly, the influence maximization problem is to find the minimal set of nodes which, if removed, would turn the network into the non-percolating state. Such an operation is often called optimal percolation. The method is also used to find the influential nodes in brain networks [461] and multiplex networks [462].
Due to the inherent relation with spreading dynamics, bond percolation is also used to identify the optimal combination of a given number of influential spreaders [463]. This method needs first to perform a bond percolation on the network, i.e., randomly removing some links. In the resulting network, the largest degree nodes in the top- largest clusters are selected and one score is assigned. With different realizations, the average score of each node can be obtained, and the ones with large scores are suggested to be the influential spreaders. Furthermore, Hu et al. offered an analogy of the correlation length in percolation transition to explain the local length scale in spreading dynamics, which could also be used to measure a node’s or a group of nodes’ global influence [464].
In addition, percolation process is also employed as a criterion of the node ranking algorithm [245]. In this criterion, the size of the giant cluster after a node’s removal is assumed to be the structural importance of the node, such that the smaller the obtained giant cluster is the more important the node is. For a node ranking, one can remove nodes from the network one by one in the order of the ranking, then the average size of the giant clusters for each stage can be expressed as
| (118) |
Here, is the number of nodes in the network, and is the size of the giant cluster when the -th node has been removed. Obviously, a good node ranking will give a small . From Eq.(118), if the network is large enough, is approximately the area surrounded by function and the horizontal axis.
4.5 Network observability
In Ref.[197], a fundamental problem in network science, namely, the determination of the state of the system from limited measurements, was abstracted as a percolation model, called network observability transition. In this model the initial node occupation is understood as placing a sensor device on the corresponding node, making both the node and all of its neighbors observable. Then, network observability transition focuses on the emergence of the giant cluster formed by observable nodes.
Obviously, the threshold of such percolation must be smaller than that of the classical percolation. By generating function technique, this model can also be solved theoretically. The percolation threshold depends dominantly on the average degree and the variance of degree distribution. The transition occurs earlier in denser and more heterogeneous networks, meaning that only a small amount of sensor devices can observe the key structure of such networks. However, Allard et al. further found a nontrivial coexistence of an observable and of a nonobservable extensive cluster in this percolation model [465]. This suggests that monitoring a macroscopic portion of a network does not prevent a macroscopic event to occur or be unknown to the observer. Further studies also showed that both the negative degree correlation and the betweenness-based sensor placement can make networks more observable [466, 467], and were applied to many real networks [468, 469]. In Ref.[469], a discontinuous observability transition was found in synthetic multiplex networks.
There is another percolation model called -hop percolation [198], following a very similar percolation rule. In this model when a node is removed all the nodes in the -hop distance, i.e., the nodes no farther than away from this node, will also be removed, therefore it can cause more damage than the normal robustness model based on the classical percolation. For the study of networks robustness, such a removal rule is often named localized attack [404, 387, 405, 228, 406, 407, 408].
5 Applications to network dynamics
The origin and development of percolation are inextricably bound up with the spreading process, therefore it is completely natural that in network science the percolation mechanism has been widely used to embody the spreading dynamics. In this section we will first review some typical models of spreading dynamics and their relations with the percolation transition. Besides, the percolation theory has also been borrowed to analyzing the cluster forming of individuals in the dynamics that the node or individual group plays a key role in the evolution of systems, such as the cascading process, traffic jam, and cooperation evolution. These works will also be reviewed in this section.
5.1 Epidemic spreading on networks
The modeling of epidemics is a very active field of research across different disciplines [470], and complex networks provide a powerful framework to describe the contact structure among individuals [471]. As mentioned in Sec.2.1, the epidemic spreading on networks is closely related to percolation process. When the spanning cluster does not exist or the susceptible individuals are isolated into small clusters, infectious diseases will be constrained to some small areas and a global outbreak is impossible. Similarly, when some individuals are immunized to the disease, i.e., recovered from the disease, being quarantined or get vaccinated, the susceptible individuals can be also separated as small isolated clusters and thus the disease cannot spread across the network. From this perspective, regardless of the specifics, the outbreak of the epidemics corresponds to a percolation transition among connected individuals, and there is a direct correlation between the percolation threshold and the epidemic threshold.
In this section, we introduce the framework of epidemic modeling in complex networks from a percolation perspective, although most of them are not inspired by percolation theory initially. Due to the focus of this article, we will not deeply explore various models and the corresponding analytic methods. For details, one can refer to the special reviews [472, 473, 23].
It should be noted that the spreading of epidemics is a dynamic process, while the percolation process results in a static configuration. Because of this, one often employs the master equation to feature the system state during the spreading process, instead of considering the static configuration of the system. Nevertheless, we will find that the results obtained by the master equation directly reflect the nature of percolation transition. With some mathematical techniques, some spreading models can also be exactly mapped to a percolation process [87, 23].
Generally, the epidemic model assumes that the individuals can be categorized as different classes depending on the stage of the disease in the population, such as susceptible (, those who have not got infected), infectious (, those who have been infected and are contagious), and recovered (, those who have recovered from the disease or death) [23]. Based on this classification, three epidemiological models, susceptible–infected (SI), susceptible–infected–susceptible (SIS) and susceptible–infected–recovered (SIR) are usually used to study the dynamics of disease evolution.
The simplest one is the SI model in which individuals can only exist in two discrete states, namely, and . The probability that an node gets infected by any given neighbor in an infinitesimal time interval is , where is the infection rate of the epidemic. The SIS model considers that individuals change stochastically through a reversible process: , where the infection rate is described as in the model, but infected individuals may recover and become susceptible again with a recovery rate . In the SIR model, infected individuals are removed permanently from the network with a rate and labeled as the state corresponding to immune or death. There is a second version of SIS/SIR model, where infected individuals remain in state for time steps, and then become either in SIR model or again in SIS model [474].
5.1.1 SI model
As the setting of SI model, even for a very small infection rate , all the individuals will be finally infected. Therefore, the epidemic threshold is meaningless for SI model, and the interest of research is the effect of the heterogeneity of degree distributions on the spreading velocity [475].
Let be the fraction of infections in nodes with degree at time step , then the growth of per time step can be expressed as , where is the fraction of susceptible in nodes with degree , and is the probability that a neighbor of a node of degree is infected. Note that cannot decrease with time for this model, so the rate equation reads
| (119) |
For uncorrelated networks, is independent of . Considering that an infected node at least has an infected neighbor, from which the disease has been transmitted, we have
| (120) |
In the early epidemic stages, is small, then one can neglect the second term of the right hand side of Eq.(119), which is in an order of . Together with Eq.(120), we have
| (121) | ||||
| (122) |
where . For a uniform initial condition , the two differential equations have solution
| (123) |
with the outbreak’s time scale
| (124) |
The average prevalence can also be obtained,
| (125) |
These results indicate that the prevalence shows an exponential growth in the early stages, and larger degree nodes display larger prevalence levels. By the way, the spreading dynamics on the networks with small-world effects also reported a power-law growth with a tunable exponent [476, 477], which has already been observed in the epidemic data of COVID-19 [478, 479, 480, 481]. Such growth patterns are often referred to the sub-exponential growth dynamics in the phenomenological models [482].
Equation (124) implies that the outbreak’s time scale of an epidemic is related to the heterogeneity of the degree distribution as measured by . A strong heterogeneity corresponds to a large , and thus the time scale of outbreak is very small, which signals a very fast spreading of the infection. The physical reason is that once the disease has occupied the hubs, it can spread very fast among the network following a “cascade” of decreasing degree classes [475, 483].
Note that the percolation threshold corresponds to [72]. When the infection rate , the outbreak’s time scale becomes . This means that an epidemic with an infection rate larger than the percolation threshold can quickly spread far and wide. Moreover, a special case is SF networks with an exponent , for which any infected rates will lead to a rapid spreading due to the vanished percolation threshold.
5.1.2 SIR model
The above discussion can be easily extended to the SIR model. To describe the transition from state to state, an extra term defining the rate at which infected individuals of degree recover and permanently removed must be added into Eq.(119) [484],
| (126) | ||||
| (127) | ||||
| (128) |
where is defined as the density of removed individuals of degree and . With the initial conditions , , and , the solution of Eq.(127) can be written as
| (129) |
Here, considering the uncorrelated networks, i.e., , reads
| (130) |
In the last equality we have utilized the integral of Eq.(128).
Different from SI model, for , the infections vanish and the individuals are either in state or in state , depending on the infection rate and the recovery rate . We can use to find the steady state, that is
| (131) |
Together with Eq.(129), we find a self-consistent equation for ,
| (132) |
Solving this equation, we can find , and thus all other parameters for the steady state can be found.
It is easy to find that if
| (133) |
Eq.(132) only has a solution , indicating the epidemic cannot break out. This yields the epidemic threshold
| (134) |
above which the epidemic incidence attains a finite value. Note that is just the percolation threshold of the network. This suggests that there is a tight correspondence between the emergence of the giant cluster in the bond percolation and the outbreak of epidemic in the system.
Similar to SI model, Eq.(134) also suggests that a high level of connectivity heterogeneity (large ) facilitates the spreading of epidemics. When diverges (SF networks with ), an epidemic with any non-zero infection rate can break out in the system [475, 483, 485]. This is analogous to those concerning the network resilience under random damages, which can be studied by the standard percolation on networks.
The above discussion focuses the steady state of spreading process. The time evolution of SIR model can be solved by other approaches, such as the effective degree-based method [486] and the pair-based mean-field method [487, 488]. The extended degree-based method is used to derive an expression for the basic reproduction ratio [486], and also provides an excellent agreement with numerical simulations for both the temporal evolution and the final outbreak size [489]. The threshold condition derived from the effective degree-based method turns out to be equal to the one obtained by percolation theory. The pair-based method was proven to be an exact deterministic description of the infection probability time course for each individual in the tree-like network [490]. For networks with loops, a precise closures can be also derived according to the detailed loop structure [491]. At the same time, the pair-based approach can be easily extended to models with heterogeneous infection and recovery rates [487].
The correspondence between the steady properties of SIR model and the bond percolation is also studied in Refs.[1, 87, 492, 493]. Considering the second version of SIR model with a uniform infection time , i.e., infected nodes will recover after being infected for time steps. For continuous-time dynamics, the transmissibility , defining the probability that the disease will be transmitted from an infected node to a susceptible neighbor before recovery takes place, can be computed as
| (135) |
With this relation, we can exactly map the steady state of an SIR model to a bond percolation with occupied probability . Then, from the critical transmissibility
| (136) |
one can find the critical infection rate for a given , that is
| (137) |
For discrete time, particularly computer simulations, the transmissibility , thus
| (138) |
These results also show that different combinations of and could result in the same spreading result, related to the percolation cluster under occupied probability [87].
5.1.3 SIS model
Based on the degree-based mean-field theory [494], the complete evolution equation for the SIS model on a network with arbitrary degree distribution can be written as
| (139) |
The creation term considers the density of susceptible nodes with degree that can get the infection from a neighboring individual [495]. For uncorrected networks, is used in Ref.[494], which is different from Eq.(120). This is because the infected nodes can recover to be a susceptible, and all the excess-degree of an infected node at the end of a link could lead to a node in state . However, we think that around or above the epidemic threshold, on average an infected individual is very unlikely to recover before the individuals infected by it transmit the disease to others. Thus, we still use Eq.(120) to represent here. It must be pointed out that both the two choices are an approximation for , and do not affect the basic conclusion.
With the limit, the system can reach the stationarity state, i.e., . This yields
| (140) |
This equation shows that the larger the degree of a node, the higher its probability to be infected. Substituting Eq.(120) into Eq.(140), a self-consistent equation can be found
| (141) |
This equation always has a trivial solution , and the nontrivial solution exists only for
| (142) |
Thus, the epidemic threshold reads
| (143) |
This result is the same as that found in SIR model, the qualitative analysis is not repeated here. Note that for SF networks with , neither assortativity nor disassortativity can reconstruct a non-vanished epidemic threshold for SIS model [496].
For the version that infected nodes remain in state for time steps, and then become again, the epidemic threshold of SIS model can be also derived by the branching process in percolation theory [474]. In SIS model, it has been found that there exist dynamic correlations coming from that if one node is infected, its neighbors are likely to be infected, which has been neglected by the degree-based mean-field theory. To account for this, effective degree approach [489, 497] and the combination of degree-based mean-field theory and effective degree approach [498] have been proposed to obtain accurate expressions for the average prevalence and the epidemic threshold.
5.1.4 Immunization
Not only the epidemic model itself but also the immunization strategy for suppressing the spreading is related to percolation process. The simplest immunization strategy is the random one, which chooses immune individuals randomly from a population. After immunization, the infected individuals cannot transmit disease to the immune individuals. Thus it is equivalent to a spreading process on a diluted network. If there is no giant cluster in the diluted network, the epidemic will not break out, regardless of infection rate. The corresponding immunization ratio is called immunization threshold. A detailed discussion for this problem is the same as that for the network robustness, and thus immunization can be treated as a percolation process.
The introduction of a fraction of immune individuals chosen randomly is equivalent to dilute nodes with probability . According to Eqs.(15) and (16), the immunization process results in [499]. Thus, the epidemic threshold is rescaled as
| (144) |
This generally covers the common sense that the more immune individuals, the larger the epidemic threshold. However, for SF networks with , is divergent, implying that random immunization cannot bring the epidemic into healthy region except for the case . From Eq.(144), we can also find that if , even if Eq.(144) does not make sense. This indicates that when the fraction of unimmunized individuals is below the percolation threshold , the epidemic cannot break out [499]. This is mainly because below this threshold the susceptible individuals are segregated in smaller regions by immune individuals.
Obviously, whoever the immune individuals are, they can suppress the infection locally. However, an apparent inadequacy of random immunization strategies is that it gives the same importance to both high-connected nodes (with the largest infection potential) and low-connected nodes, and thus is unable to find the critical individuals to make them immune for the eradication of infection. Targeted immunization is referred as the immunization of most highly connected individuals (potentially the largest spreaders), i.e., a fraction of the individuals with the highest degrees is immunized [470]. The equivalent diluted result depends on the details of the targeted immunization, which is very similar to the intentional attack in the study of network robustness (see Sec.4.2).
In Ref.[499], the authors showed that the immunization threshold takes the form for SF networks with , where is the minimum degree. This clearly highlights that the targeted immunization program is extremely convenient, with an immunization threshold that is exponentially small in a wide range of infection rates. Based on the global knowledge of network, the nodes with the highest recalculated degree or betweenness centrality are selected for immunization during the selection procedure [500]. Schneider et al. sought to minimize a properly defined size for the connected cluster of susceptible individuals, which is found to be more effective than the methods based on immunizing the highest-betweenness links or nodes [501]. Similarly, seeking to fragment the network into connected clusters of approximately the same size, “equal graph partitioning” strategy can achieve the same degree of immunization as targeted immunization by fewer immunization doses [502].
An efficient targeted immunization requires global information about the network, which makes it to be impractical in many real situations. Acquaintance immunization can make immune a small fraction of random acquaintances of randomly selected nodes [503]. In this way, the highly connected nodes are more likely to be chosen and immunized, and the process prevents epidemics with a small finite immunization threshold and without requiring global knowledge of the network. In acquaintance immunization, a random fraction of nodes is chosen and then selects their random neighbors, i.e., acquaintances. The acquaintances, rather than the originally chosen nodes, are the ones immunized. The fraction may be larger than , for a node might be queried more than once, on average, while the fraction of nodes immunized is always less than or equal to . The critical threshold for a complete immunization can be solved analytically based on a branching process on a network as that in percolation model.
If more local information is available, the acquaintance immunization strategy can be further improved in efficiency. For example, allowing initial selected node to have knowledge of the degrees of its nearest neighbors, immunizing the neighboring nodes with the largest degree is smart for efficiency [504]. Similarly, if the information within a distance of initial selected node is available, one can consider the immunization of the nodes with the highest degrees within that scope.
5.2 Cascading process on networks
It has been widely recognized that there are interdependencies or hidden interactions among the nodes in a networked system, which allows the viruses, information, opinion or failures to propagate from node to node via a certain topology. Although the specific scenarios might be different, most models present an iterative process: each individual in a population must decide a state between two or more alternatives and their decisions are made based on the options of their neighbors rather than relying on their own information about the problem, thus after an initial state setting the state flipping of individuals will occur recursively until no node meets the flipping criterion. This type of processes is often called cascading process.
With a given amount of excitation sources, the emergence of a giant cluster formed by individuals with identical states is just a dependent percolation process. Most of the models reviewed in Sec.4 belong to this category, i.e., the system evolves in generations. Here we mainly concentrate on another model widely used for the cascading process, called threshold model.
Threshold model was first proposed by Watts for the study of cascading failures in networks [194]. In this model, there are two states for nodes, namely, functional and failed, to be more generic, we use state and state instead. At each time step, the binary decision rule with externalities is outlined as follows: each node in state observes the current states (either or ) of all its neighbors, and adopts state if at least a threshold fraction of its neighbors are in state , else remains unchanged. No transition from state back to state is possible. With a small fraction of seed nodes (state ) in a population which is initially set as state , the system evolves at successive time steps with all nodes updating their states according to the threshold rule above.
In a sufficiently large random network with sparse connections and only a few seeds, it can be assumed that the network is locally tree-like, hence, no node has more than one neighbor in state . Under this condition, only the nodes with degrees have the potential to flip their states to be , called vulnerable nodes. If the vulnerable nodes percolate in the system, the global cascades can be triggered by the initial seeds; otherwise, the propagation of cascades will be limited by the stable nodes and global cascade is impossible.
That is to say, this dynamic problem can be mapped to a static percolation problem, which can be solved by the generating function approach, see Sec.2.2. According to percolation threshold of random networks and denoting the probability that a node with degree is vulnerable as , the largest vulnerable cluster percolates when
| (145) |
With the above analysis, we know that for , otherwise . For large thresholds , Eq.(145) has no solution, meaning that the vulnerable nodes cannot percolate and there is no global cascade in the system. For small thresholds , Eq.(145) has two solutions resulting in two phase transitions. Below the smaller critical point, the network is composed of some small clusters and the propagation of cascades is thus constrained by these segregated clusters. Above the larger critical point, the network becomes dense enough, so that the propagation of cascades is blocked by the local stability of nodes. In summary, the global cascades can only occur in the network with a structure lying between the two phase transition points. Moreover, the transition of the cascade upon the average degree is continuous at the smaller critical point and discontinuous at the larger critical point.
The above discussion is based on that the seeds are scarce. Gleeson and Cahalane further studied the effects of seed size on the cascading process [253]. Their method is based on a level-to-level update process, the final cascade size (rescaled by the system size) of active nodes (state ) is given by
| (146) |
where is seed size, and gives the probability that the node with degree and active neighbors meets the excitation condition. In addition, is the probability that a link leads to an active node, which satisfies the recursion relation
| (147) |
With these equations, the cascade size can be solved. The results show that the cascade transition at low may in fact be discontinuous in certain parameter regimes, and the seed size as low as has dramatic effects on the location of cascade transition points, that is
| (148) |
Obviously, this result reduces to Eq.(145) found in Ref.[194] by letting , for which and .
This analysis method is also valid for large seed , which has been also extended to analyze networks with community structures and degree-degree correlations [256, 505]. For networks with clusterings [258], it turns out that for large and small values of clustering reduces the size of cascades, while the converse occurs for intermediate values of the average degree. In Ref.[195], Liu et al. showed that using the seed size as the control parameter, the crossover of the continuous and discontinuous phase transitions can be found.
Watts’s threshold model can be seen as a particular instance of a more generalized model of contagion [506], and has been used to study the effects of network properties that may influence the spreading process, such as boolean networks [507], SW networks [254], multiple layers [261], temporal networks [508] where the associated bursty activity of individuals may either facilitate [509] or hinder [510] the spreading process.
5.3 Traffic and transportation
As travel demand increases in modern cities, traffic congestion becomes more frequent. As a result, the study on the dynamical transition from free flow to congestion in traffic flow has attracted much attention. To understand the traffic transition in a network scale (representing a city or an urban region), the percolation model has also been applied to the urban traffic network.
With percolation theory, the typical question of how the traffic in the network collapses from a global efficient state to isolated local flows in small clusters is clearly demonstrated, which might be useful for improving transportation efficiency, reducing traffic delay, and facilitating emergency evacuation. Percolation theory also provides useful tools for urban planning. Traffic network connectivity under disasters, such as earthquake or rain, has also been investigated by percolation theory.
5.3.1 Percolation in urban traffic networks
Li et al. considered the percolation process in Beijing road traffic network, and identified bottleneck roads that connect different functional clusters [511]. The velocity data of -min segment records measured in a central region of Beijing is used to construct the road network, where nodes represent the intersections and links represent the road segments between two intersections. For each road, the velocity varies with time during a day. A dynamic functional traffic network can be constructed by the links with velocity higher than a given threshold . With a small threshold , a giant cluster of functional network can extend to almost the full scale of the road network. As increases, the size of the giant component decreases, and the second-largest cluster becomes maximal at a threshold , which signifies the percolation transition from the connected phase to the fragmented phase of the functional traffic network. The critical value can be seen as an indicator of the efficiency of global traffic. Obviously, an efficient traffic system will have a higher .
In a static network, bottleneck links are identified usually based on structural connectivity information. Traffic, as a dynamical non-equilibrium system, evolves with time and shows varying during the day. The bottleneck links of global traffic will also evolve accordingly and appear in different locations in different hours. By investigating the functional cluster at percolation criticality, Li et al. identified some bottleneck links that play a critical role in bridging different functional clusters of traffic [511]. With the congestion of these links, the giant cluster will disintegrate and result in some small clusters. Conversely, improvement of these critical bottleneck roads can significantly increase the threshold of the traffic network, thus benefit the global traffic. This kind of improvement of is higher than that by increasing the velocity of a random link or the link with the highest path-based betweenness. This proves the uniqueness of the bottleneck links found by percolation theory.
Zeng et al. further identified two modes of percolation behaviors in Beijing and Shenzhen traffic network [512]. To investigate the differences of the dynamic traffic network in rush hours and nonrush hours, they performed a percolation analysis by calculating the size of the functional clusters. At criticality, a well-defined Fisher exponent as that in percolation theory can be observed. With this, Zeng et al. found that the disintegration transition of urban traffic can be characterized by two sets of exponents. During rush hours on workdays, the critical exponent is in general smaller than that during nonrush hours or days off. During workday rush hours, is close to the theoretical result of the two dimensional lattice (), while during other periods, it is close to the mean-filed value for high dimensional systems ().
This phenomenon can be understood as follows. The urban traffic network can be generally seen as a system embedded in two dimensions with some long-range connections corresponding to urban highways. During nonrush hours, all the roads are in the free flow state, the system is thus a two dimensional lattice with long-range connections. In contrast, during rush hours, the highways become congested and the urban traffic network reduces to a two dimensional system. With the aid of traffic management methods, the traffic system can be tuned to the desired class by adjusting the amount of effective long-range connections. Using the corresponding signal control or road pricing on urban highways, this mechanism can help to create a significantly better traffic system.
The above investigations are based on the analysis of the empirical traffic data. Obviously, the percolation properties vary with traffic parameters, such as the level of traffic load and the detailed behaviors of drivers. Such analysis can also be performed by modeling simulations. Wang et al. studied the traffic percolation properties on a traffic system based on an agent-based model [513]. Using the traffic model in Ref.[514], the level of traffic demand and routing preference can be tuned to verify their impacts on the percolation property. It has been widely proved that the traffic will undergo a phase transition from the free state to the congested state with the increase of traffic load in the network. In Ref.[513], the functional network is constructed by the free state nodes with load lower than a threshold. The emergence of the giant cluster indicates the percolation transition and the formation of global traffic flow. It is also found that the threshold of the traffic percolation shows a sharp minimum value at the traffic transition threshold, indicating that the global flow can be maintained with minimal number of local flows. The value of is also influenced by the routing choice. In the giant percolation cluster, optimal paths will accumulate to a high level. This can provide a possible routing choice to mitigate traffic congestion.
In the modern urban traffic system, different transportation modes have been widely constructed, including bus, metro, and road networks, which can be represented as a multiplex network. In such a system, a fraction of node failures in one layer can trigger a cascade of failures that propagate in the multiplex network, see Sec.3.2. Baggag et al. studied the resilience and robustness of multi-modal transportation networks using percolation theory [515]. In this study, percolation is used to investigate the impact of link failures in the multiplex transportation network. By calculating the size of the mutually connected giant cluster under random or targeted failures, the robustness of multiplex transportation networks can be evaluated. The four cities studied in Ref.[515] behave similarly in terms of coverage degradation under random failure, with Paris network being the most robust.
5.3.2 Percolation in connected vehicle networks
Connected Vehicles (CV) technology is the leading edge of intelligent traffic systems [516], and has great potential to mitigate traffic congestion through the creation of a CV network [517]. Once the vehicle cloud network is formed, travel information such as speed, density, and signal timing can be retrieved from the network. This information would help the driver’s decision-making and eventually enhance the mobility of CV in terms of travel time. In an urban traffic system, the benefits of the corresponding applications will depend on the CVs’ communication range and the market penetration, which can be featured by the percolation model.
The study of CV network was pioneered by the analysis of network connectivity for wireless sensor networks and ad-hoc networks. Ammari and Das studied the sensing-converge and network-connectivity in wireless sensor networks using percolation theory [518]. A probabilistic approach is created to compute the covered area fraction at percolation threshold. Under various scenarios, the critical percolation density and radius of the covered components are identified. Similarly, Khanjary et al. conducted percolation studies in the two-dimensional fixed-orientation directional sensor network [519]. The critical density of the nodes can be analytically computed from the percolation theory framework.
Jin et al. first assessed the connectivity of Vehicular Ad-hoc NETwork (VANET) through a percolation framework [520]. The relationship among network connectivity, vehicle density and communication range was analyzed. When vehicle density or communication range is big enough, VANET will show a jump of network connectivity, corresponding to the percolation transition. Given vehicle density, the minimum communication range can be calculated to achieve good network connectivity. As a large transmission range can cause serious collisions in wireless links, the percolation analysis can help to determine the tradeoff and guide the deployment of VANETs in real world.
Talebpour et al. investigated the effect of CV information availability on the stability of traffic flow through continuum percolation theory [521]. The impact of CV density and communication range on the connectivity of the network is determined by percolation properties. The results show that as the communication range increases, the traffic flow system becomes more stable.
Mostafizi et al. investigated the impacts of CV network on the mobility of traffic systems at varying levels of market penetration and communication range [522]. When more CVs are present, the network tends to be more connected. When the percentage of CV decreases, there exists a percolation threshold where the giant cluster breaks apart. It has been found that the percolation transition is a function of both market penetration and communication range. The emergence of mobility benefits is highly related to the percolation transition in CV network. Only when the system reaches the percolation threshold, the benefits of reducing mean travel time begin to appear. Below the threshold, although small clusters can form in the network, they will not create a significant impact on the mean travel time due to the scarce information available from the CV network.
5.3.3 Percolation in urban traffic planning
The analysis of the inter-relations between traffic flows and urban street networks can provide a meaningful tool for urban planning processes. From this perspective, Serok et al. identified functional spatio-temporal street clusters of London and Tel Aviv using network percolation analysis [523]. The dynamics of these clusters and their spatial stability over time are analyzed, which can help to develop new, adaptive, decision-making tools for urban and transportation planners. Traditionally, urban planning is a long-term and static process. The application of traffic percolation will enable planners to keep their role in the flexible and dynamic urban system.
Behnisch et al. studied the settlement connectivity in Germany using the percolation concept [524]. The percolation is introduced to quantify the connectivity of buildings. They found that at a critical distance of m the buildings settlement network in Germany will undergo a transition from isolated clusters to a country-spanning building cluster. This rather short critical distance indicates that the landscape is already overbuilt in Germany. For urban planning, limiting urban sprawl and further land consumption is crucial. The application of percolation can provide a useful monitoring tool for settlement and landscape degradation.
Transport accessibility is an important issue for industrial relocation and the related sustainable development of economics. Jiang et al. studied the impact of transportation accessibility on industry relocation pattern of China’s Yangtze River Economic Belt using percolation theory [525]. In the network, the nodes are cities, and the links are defined according to the Yangtze River’s waterways and the highways in the Yangtze River Economic Belt. Their results proved the existence of percolation transitions during the process of industry relocation, and identified the bottlenecks for industry relocation as cities located in border regions.
Piovani et al. studied the relation of urban retail location distribution and road network properties in London from percolation theory. Road network and retail location are two interwoven factors in an urban ecosystem. The emergence of clustering in retail centers depends greatly on road network [526]. Piovani et al. compared the road network’s hierarchical percolation structure with the retail location distribution. To evaluate the road network, the subgraph is constructed by the road segments with length below a threshold, and the transition is defined at the threshold that generates the maximal entropy configuration. The results show that clusters of the road network and retail location are very similar in spatial characteristics.
5.3.4 Percolation in post-disaster traffic networks
Post-disaster traffic networks are very important since they offer access to affected areas, sustain evacuation and medical operations after a disaster. If a disaster is very severe and many roads are malfunctioned, the traffic network could collapse into isolated subnetworks, and there will be no route connecting some locations. Therefore, the connectivity of post-disaster traffic networks also provide an important index for the assessment of vulnerability, robustness, and resilience of the road system.
Zhou et al. studied the connectivity of post-earthquake road networks using percolation theory [527]. To assess the road network, they proposed the concepts of “global connectivity” and “local connectivity”. Global connectivity measures the extent to which the whole network is connected, and local connectivity measures the distances between each node to its neighbors. Specifically, the global connectivity is quantified by the percolation threshold, the size of the giant subnetwork, and average sizes of small subnetworks, while local connectivity is quantified by the number of neighbors. In particular, Zhou et al. proposed an integrated percolation model combining localized attacks and random failures to capture the feature of earthquake-impacted [527]. Namely, the impact of the earthquake on the inner network is modeled as a localized attack (where node disruption is dominant), while it is modeled as random link disruption in the outer network. The model can be used to assess the connectivity of road networks impacted by different magnitudes of earthquakes.
Extreme weather, such as torrential rain and hurricane, could greatly influence urban traffic system. Although the traffic flows under extreme weather have been widely studied, little work has been done to understand whether and how the destruction of local roads can degrade the global traffic. Guo et al. studied the impact of torrential rain on traffic percolation properties in Beijing and Wuhan [528]. In Beijing, whose street layout is more symmetrical, the dysfunctional roads are scattered uniformly. However, for Wuhan with a river valley, the dysfunctional roads appear in a cluster way and partially along the riverbank. Interestingly, the percolation threshold of traffic network is stable against weather perturbation, even if some roads are significantly influenced. This is mainly because extreme weather (torrential rain) will not only damage road conditions in the supply end, but also reduce the traffic demand correspondingly.
5.4 Evolutionary game
Evolutionary game theory offers a powerful mathematical framework to study the emergence of cooperation among selfish individuals. When the contact network of individuals is taken into account, i.e., the spacial evolutionary game, the focus of the research just translates to the emergence of the clusters formed by adjacent cooperators. Therefore, the percolation theory is also employed to explore the spacial evolutionary game.
In Ref.[529], Yang et al. studied the cooperation percolation in spatial prisoner’s dilemma game. Their model is defined on a two-dimensional square lattice. Initially, with probability a node is occupied by a cooperator and with probability a node is occupied by a defector. At each time step, each individual plays the prisoner’s dilemma game with its four nearest neighbors. Specifically, if both players cooperate, then both get the payoff . If one cooperates while the other defects, the defector gets while the cooperator gets nothing. If both defect, no gains for both of them. After the games, individuals update their strategies asynchronously in a random sequential order. A randomly selected player compares its payoff with its nearest neighbors and changes strategy by following the one (including itself) with the highest payoff.
They found that the percolation transition can be well-defined by the control parameter , the phase diagram can be divided into several regions based on whether the cooperator cluster can percolate. With the analysis of finite size scaling, they claimed that the region belongs to the universality class of the classical percolation in two dimensions, whereas region is subject to that of invasion percolation with trapping. However, an exhaustive simulation revealed that all these regions belong to the universality class of the classical percolation in two dimensions [530]. In Ref.[530], the authors also studied the model on the triangular lattice and the hexagonal lattice, and concluded that the observed percolation transitions on various two-dimensional lattices belonged to the universality class of the standard percolations.
In Ref.[531] the percolation transition was also observed in the Stag Hunt game and the Snowdrift game. More interestingly, they found a double transition in ER networks. With the increase of , the giant cooperator cluster increases continuously from zero above a critical point, then at a second critical point the giant cooperator cluster jumps from a low value to a very high value. These rich phenomena highlight the role of the social contact in the emergence of the cooperation.
In Ref.[532] Lin et al. also found a scaling feature in the evolutionary game on the interaction graph extracted from percolation process. The power-law distribution of cooperator clusters like that in percolation model was also observed in fractal hierarchical networks [533]. Besides, an interaction graph at the percolation threshold has also been proved to be an optimal population density for public cooperation [534, 535]. Peng and Li suggested that this is due to the fractal structure formed at the percolation threshold [536], which constructs an asymmetric barrier that the defection strategy is almost impossible to cross, but the cooperation strategy has a not too small chance. In the system with mobile individuals, the geometric percolation of the contact network (i.e., irrespective of the strategy) also enhances cooperation [537].
6 Discussion and outlook
Percolation describes the patterns of connections under a random or semi-random connection mechanism, while network science focuses on the non-trivial topological features inspired largely by the empirical study of real-world networks. In this sense, although the proposal of percolation model predates the rise of the research of complex networks by about fifty years, it inherently provides a framework for the studies of complex networks. So it is no surprise that the application of percolation theory in network science has achieved fruitful results.
First of all, the study of percolation process on a non-trivial topology, including strong heterogeneity, high clustering, assortativity or disassortativity, modular, hierarchical structures and so on, has brought new power to percolation theory, especially for the fractal and non-physical dimension systems. For examples, the heavy-tailed degree distribution of the SF network induces a special mean-field nature of percolation transition (see Sec.2.5.2), and the percolation in the growing network demonstrates an infinite order transition like that found in the Berezinskii-Kosterlitz-Thouless phase transition in condensed matter (see Sec.3.4). In recent years, we have also witnessed a wide range of discussion on the explosive percolation and the hybrid percolation transition on network systems (see Sec.3). Besides, quite a number of pruning rules used in the identification of special network structures are also defined in terms of percolation process, such as -core percolation (see Sec.3.1), clique percolation (see Sec.4.3), and core percolation (see Sec.3.1). These percolation models also attracted a lot of studies on the system with physical dimensions, and enriched the research of the percolation theory [20, 21].
In addition to providing theoretical supports for the findings from empirical researches, the ideas and conceptions of percolation theory furnish a quantitative analysis approach to the methodology of network science. A typical representative is the giant cluster, which has already been widely used to evaluate the state of a network. For the study of network resilience, if a giant cluster exists, the network is considered functional, otherwise the network is paralyzed. In this way, the percolation threshold can be used to quantify the robustness of networks (see Sec.4.2). Similarly, if the infections form a giant cluster, it can be concluded that the epidemic breaks out, so that an epidemic with a smaller percolation threshold is more infectious (see Sec.5). Even for the problems that seemed to be irrelative to percolation process, the percolation analysis can offer a good interpretation for their findings, such as the evolution of traffic state of an urban network, and the emergence of the cooperation clusters (see Sec.5). Although almost all of these studies are not originally motivated by the percolation process and the evolution rules might be far away from the standard percolation, the emergence of the giant cluster is employed as a picture of the inherent problem. Because of this, some of the modeling of network dynamics just take the form of percolation process, such as the cascading failures, and the spreading of information/opinion/epidemics (see Sec.5).
The classical percolation in physical dimensions often refers to regular systems, such that the percolation results are totally random, and the focus is more on the statistic characteristic of the clusters. However, the important characteristic of empirical networks, i.e., strong heterogeneity, can bring determinacy into the percolation configuration. For example, the hubs of a SF network almost always belong to the giant cluster of different realizations. Once the hubs are destroyed, the network will be disintegrated. From this perspective, the percolation results in part reflect the connective features of networks, and thus can be used as an algorithm for identifying the special subsets of networks. Some typical examples have been reviewed in Sec.4, including -core decomposition, community detection, vital node identification, and so on.
In summary, the percolation theory has already percolated into many research aspects of network science, ranging from structure analysis to dynamics modeling. Loosely speaking, one would hardly evade conceptions, analytic methods, and algorithms of percolation in the studies of complex networks. For this reason, almost all the review articles on the network science spill some ink on the corresponding percolation problems, such as network structures and dynamics [5, 3, 6, 538], multiplex networks [8, 445, 317, 457, 446], spatial networks [539], epidemic process [23, 473], explosive transition [206], community detection [458, 540], -core [214], and vital nodes identification [245]. Besides, the significant findings of network percolation are also included in the articles on recent advances of percolation transition [21, 20].
By tracing the progress of percolation on networks and its applications, in this paper we briefly review the percolation on complex networks from models, theoretical methods, to applications for network problems. Overall, the studies of percolation on networks yield a rich harvest from theory to applications. Meanwhile, many challenges still remain. First, real networks have a rich mixture of properties, such as degree correlation, clustering, modularity, heterogeneity, small world, and spatial constraint. For these complex structures, only some approximate theory can be applied to simplify the structural models, while whether these structures can separately or collectively change the nature of the percolation transition or not remains an open question. Moreover, the mixture pattern often refers to the high-order structure of networks. This is a new research hotspot of network science in recent years, for which the percolation theory also plays an important role [541, 542, 543, 544, 545, 546, 10].
Furthermore, as a random process, the percolation result of a given network can differ from realization to realization, while the network identification often requires a deterministic result. How to solve this conflict when employing percolation process to analyze network structure? Are there some ways to take advantage of the fluctuation of percolation results to give more information on network structures? Moreover, it is known that the percolation clusters in the subcritical phase are dominated by local connections, and the global connections for the supercritical phase. In this way, is there a unified algorithm based on percolation process for identifying network structures in different scales? To answer these questions, more researches should also be done to explore the percolation process on networks.
Acknowledgments
We would like to thank Pan Zhang, Manuel S. Mariani, and Xu Na for useful discussions and comments. The research was supported by the National Natural Science Foundation of China under Grant Nos.11622538, 61673150, 61773148, and 12072340. L.L. also acknowledges Zhejiang Provincial Natural Science Foundation of China under Grant No.LR16A050001, and the Science Strength Promotion Programme of UESTC.
References
- [1] M. E. J. Newman, Networks: An Introduction, Oxford University Press, 2010.
- [2] A.-L. Barabási, Network science, Cambridge university press, 2016.
-
[3]
R. Albert, A.-L. Barabási,
Statistical
mechanics of complex networks, Rev. Mod. Phys. 74 (2002) 47–97.
doi:10.1103/RevModPhys.74.47.
URL https://link.aps.org/doi/10.1103/RevModPhys.74.47 - [4] S. N. Dorogovtsev, J. F. F. Mendes, Evolution of networks, Adv. Phys. 51 (2002) 1079–1187. doi:10.1080/00018730110112519.
-
[5]
S. Boccaletti, V. Latora, Y. Moreno, M. Chavez, D.-U. Hwang,
Complex
networks: Structure and dynamics, Phys. Rep. 424 (2006) 175 – 308.
doi:https://doi.org/10.1016/j.physrep.2005.10.009.
URL http://www.sciencedirect.com/science/article/pii/S037015730500462X -
[6]
S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Critical phenomena
in complex networks, Rev. Mod. Phys. 80 (2008) 1275–1335.
doi:10.1103/RevModPhys.80.1275.
URL https://link.aps.org/doi/10.1103/RevModPhys.80.1275 - [7] D. Stauffer, A. Aharony, Introduction to percolation theory, 2nd Edition, Taylor & Francis, London, 1991.
-
[8]
S. Boccaletti, G. Bianconi, R. Criado, C. I. del Genio, J. Gómez-Gardeñes,
M. Romance, I. Sendiña-Nadal, Z. Wang, M. Zanin,
The
structure and dynamics of multilayer networks, Phys. Rep. 544 (2014) 1 –
122.
doi:https://doi.org/10.1016/j.physrep.2014.07.001.
URL http://www.sciencedirect.com/science/article/pii/S0370157314002105 - [9] G. Bianconi, Multilayer Networks: Structure and Function, Oxford University Press, 2018.
- [10] F. Battiston, G. Cencetti, I. Iacopini, V. Latora, M. Lucas, A. Patania, J.-G. Young, G. Petri, Networks beyond pairwise interactions: Structure and dynamics, Phys. Rep. 874 (2020) 1–92. doi:10.1016/j.physrep.2020.05.004.
- [11] P. J. Flory, Molecular size distribution in three dimensional polymers. i. gelation, J. Am. Chem. Soc. 63 (1941) 3083. doi:10.1021/ja01856a063.
- [12] P. J. Flory, Molecular size distribution in three dimensional polymers. ii. trifunctional branching units, J. Am. Chem. Soc. 63 (1941) 3096. doi:10.1021/ja01856a063.
- [13] P. J. Flory, Molecular size distribution in three dimensional polymers. iii. tetrafunctional branching units, J. Am. Chem. Soc. 63 (1941) 3091. doi:10.1021/ja01856a063.
- [14] S. R. Broadbent, J. M. Hammersley, Percolation processes: I. crystals and mazes, Math. Proc. Cambridge Philos. Soc. 53 (1957) 629––641. doi:10.1017/S0305004100032680.
-
[15]
D. Stauffer,
Scaling
theory of percolation clusters, Phys. Rep. 54 (1979) 1 – 74.
doi:https://doi.org/10.1016/0370-1573(79)90060-7.
URL http://www.sciencedirect.com/science/article/pii/0370157379900607 - [16] J. W. Essam, Percolation theory, Rep. Prog. Phys. 43 (1980) 833–912. doi:10.1088/0034-4885/43/7/001.
-
[17]
M. B. Isichenko,
Percolation,
statistical topography, and transport in random media, Rev. Mod. Phys. 64
(1992) 961–1043.
doi:10.1103/RevModPhys.64.961.
URL https://link.aps.org/doi/10.1103/RevModPhys.64.961 -
[18]
M. Sahimi, Flow
phenomena in rocks: from continuum models to fractals, percolation, cellular
automata, and simulated annealing, Rev. Mod. Phys. 65 (1993) 1393–1534.
doi:10.1103/RevModPhys.65.1393.
URL https://link.aps.org/doi/10.1103/RevModPhys.65.1393 -
[19]
T. Nakayama, K. Yakubo, R. L. Orbach,
Dynamical
properties of fractal networks: Scaling, numerical simulations, and physical
realizations, Rev. Mod. Phys. 66 (1994) 381–443.
doi:10.1103/RevModPhys.66.381.
URL https://link.aps.org/doi/10.1103/RevModPhys.66.381 -
[20]
N. Araújo, P. Grassberger, B. Kahng, K. Schrenk, R. Ziff,
Recent advances and open
challenges in percolation, Eur. Phys. J. Spec. Top. 223 (2014) 2307–2321.
doi:10.1140/epjst/e2014-02266-y.
URL https://doi.org/10.1140/epjst/e2014-02266-y -
[21]
A. A. Saberi,
Recent
advances in percolation theory and its applications, Phys. Rep. 578 (2015) 1
– 32.
doi:https://doi.org/10.1016/j.physrep.2015.03.003.
URL http://www.sciencedirect.com/science/article/pii/S0370157315002008 - [22] J. M. Hammersley, Origins of percolation theory, Annals of the Israel Physcial Society 5 (1983) 47–57.
-
[23]
R. Pastor-Satorras, C. Castellano, P. Van Mieghem, A. Vespignani,
Epidemic processes
in complex networks, Rev. Mod. Phys. 87 (2015) 925–979.
doi:10.1103/RevModPhys.87.925.
URL https://link.aps.org/doi/10.1103/RevModPhys.87.925 -
[24]
F. Y. Wu, The potts
model, Rev. Mod. Phys. 54 (1982) 235–268.
doi:10.1103/RevModPhys.54.235.
URL https://link.aps.org/doi/10.1103/RevModPhys.54.235 - [25] K. Christensen, N. R. Moloney, Complexity and Criticality, Imperial College Press, 2005.
-
[26]
R. M. Ziff, C. R. Scullard,
Exact bond percolation
thresholds in two dimensions, J. Phys. A: Math. Gen. 39 (2006) 15083.
URL http://stacks.iop.org/0305-4470/39/i=49/a=003 -
[27]
M. Ohzeki, Duality
with real-space renormalization and its application to bond percolation,
Phys. Rev. E 87 (2013) 012137.
doi:10.1103/PhysRevE.87.012137.
URL https://link.aps.org/doi/10.1103/PhysRevE.87.012137 -
[28]
M. E. J. Newman, R. M. Ziff,
Efficient monte
carlo algorithm and high-precision results for percolation, Phys. Rev. Lett.
85 (2000) 4104–4107.
doi:10.1103/PhysRevLett.85.4104.
URL https://link.aps.org/doi/10.1103/PhysRevLett.85.4104 -
[29]
Y. Deng, H. W. J. Blöte,
Monte carlo study
of the site-percolation model in two and three dimensions, Phys. Rev. E 72
(2005) 016126.
doi:10.1103/PhysRevE.72.016126.
URL https://link.aps.org/doi/10.1103/PhysRevE.72.016126 - [30] M. F. Sykes, J. W. Essam, Exact critical percolation probabilities for site and bond problems in two dimensions, J. Math. Phys. 5 (8) (1964) 1117–1127. doi:10.1063/1.1704215.
- [31] J. L. Jacobsen, High-precision percolation thresholds and potts-model critical manifolds from graph polynomials, J. Phys. A: Math. Theor. 47 (13) (2014) 135001. doi:10.1088/1751-8113/47/13/135001.
- [32] X. Feng, Y. Deng, H. W. J. Blöte, Percolation transitions in two dimensions, Phys. Rev. E 78 (3) (sep 2008). doi:10.1103/physreve.78.031136.
-
[33]
R. M. Ziff, H. Gu,
Universal
condition for critical percolation thresholds of kagomé-like lattices,
Phys. Rev. E 79 (2009) 020102.
doi:10.1103/PhysRevE.79.020102.
URL https://link.aps.org/doi/10.1103/PhysRevE.79.020102 - [34] J. Wang, Z. Zhou, W. Zhang, T. M. Garoni, Y. Deng, Bond and site percolation in three dimensions, Phys. Rev. E 87 (5) (2013) 052107. doi:10.1103/physreve.87.052107.
- [35] Z. Koza, J. Poła, From discrete to continuous percolation in dimensions 3 to 7, J. Stat. Mech. 2016 (10) (2016) 103206. doi:10.1088/1742-5468/2016/10/103206.
- [36] J. Škvor, I. Nezbeda, Percolation threshold parameters of fluids, Phys. Rev. E 79 (4) (2009) 041141. doi:10.1103/physreve.79.041141.
- [37] X. Xu, J. Wang, J.-P. Lv, Y. Deng, Simultaneous analysis of three-dimensional percolation models, Front. Phys. 9 (1) (2013) 113–119. doi:10.1007/s11467-013-0403-z.
- [38] S. M. Dammer, H. Hinrichsen, Spreading with immunization in high dimensions, J. Stat. Mech. 2004 (07) (2004) P07011. doi:10.1088/1742-5468/2004/07/p07011.
- [39] C. D. Lorenz, R. M. Ziff, Precise determination of the bond percolation thresholds and finite-size scaling corrections for the sc, fcc, and bcc lattices, Phys. Rev. E 57 (1) (1998) 230–236. doi:10.1103/physreve.57.230.
- [40] P. Grassberger, Critical percolation in high dimensions, Phys. Rev. E 67 (3) (2003) 036101. doi:10.1103/physreve.67.036101.
- [41] G. Paul, R. M. Ziff, H. E. Stanley, Percolation threshold, fisher exponent, and shortest path exponent for four and five dimensions, Phys. Rev. E 64 (2) (2001) 026115. doi:10.1103/physreve.64.026115.
- [42] H. Ballesteros, L. Fernández, V. Martín-Mayor, A. Muñoz^Sudupe, G. Parisi, J. Ruiz-Lorenzo, Measures of critical exponents in the four-dimensional site percolation, Phys. Lett. B 400 (3-4) (1997) 346–351. doi:10.1016/s0370-2693(97)00337-7.
- [43] M. Kotwica, P. Gronek, K. Malarz, Efficient space virtualization for the hoshen-kopelman algorithm, Int. J. Mod. Phys. C 30 (08) (2019) 1950055. doi:10.1142/s0129183119500554.
- [44] S. Mertens, C. Moore, Percolation thresholds and fisher exponents in hypercubic lattices, Phys. Rev. E 98 (2) (2018) 022120. doi:10.1103/physreve.98.022120.
- [45] Z. Xun, R. M. Ziff, Precise bond percolation thresholds on several four-dimensional lattices, Phys. Rev. Research 2 (1) (2020) 013067. doi:10.1103/physrevresearch.2.013067.
- [46] J. Adler, Y. Meir, A. Aharony, A. B. Harris, Series study of percolation moments in general dimension, Phys. Rev. B 41 (13) (1990) 9183–9206. doi:10.1103/physrevb.41.9183.
- [47] B. Bollobás, Random graphs, Cambridge University Press, 2001.
-
[48]
M. E. J. Newman, S. H. Strogatz, D. J. Watts,
Random graphs with
arbitrary degree distributions and their applications, Phys. Rev. E 64
(2001) 026118.
doi:10.1103/PhysRevE.64.026118.
URL https://link.aps.org/doi/10.1103/PhysRevE.64.026118 - [49] A. Bunde, S. Havlin, Fractals and disordered systems, Springer Science & Business Media, 2012.
- [50] H. E. Stanley, Phase transitions and critical phenomena, Clarendon Press, Oxford, 1971.
- [51] S.-K. Ma, Modern theory of critical phenomena, Routledge, 2018.
-
[52]
W. Huang, P. Hou, J. Wang, R. M. Ziff, Y. Deng,
Critical
percolation clusters in seven dimensions and on a complete graph, Phys. Rev.
E 97 (2018) 022107.
doi:10.1103/PhysRevE.97.022107.
URL https://link.aps.org/doi/10.1103/PhysRevE.97.022107 -
[53]
A. Pelissetto, E. Vicari,
Critical
phenomena and renormalization-group theory, Phys. Rep. 368 (2002) 549 –
727.
doi:https://doi.org/10.1016/S0370-1573(02)00219-3.
URL http://www.sciencedirect.com/science/article/pii/S0370157302002193 - [54] J. Zinn-Justin, et al., Phase transitions and renormalization group, Oxford University Press on Demand, 2007.
- [55] F. Radicchi, C. Castellano, Breaking of the site-bond percolation universality in networks, Nat. Commun. 6 (2015) 10196. doi:10.1038/ncomms10196.
- [56] A.-L. Barabási, R. Albert, Emergence of scaling in random networks, Science 286 (1999) 509–512. doi:10.1126/science.286.5439.509.
- [57] D. J. Watts, S. H. Strogatz, Collective dynamics of ‘small-world’networks, Nature 393 (1998) 440. doi:10.1038/30918.
-
[58]
M. Newman, D. Watts,
Renormalization
group analysis of the small-world network model, Phys. Lett. A 263 (1999)
341 – 346.
doi:https://doi.org/10.1016/S0375-9601(99)00757-4.
URL http://www.sciencedirect.com/science/article/pii/S0375960199007574 -
[59]
M. E. J. Newman, Models of the
small world, J. Stat. Phys. 101 (2000) 819–841.
doi:10.1023/A:1026485807148.
URL https://doi.org/10.1023/A:1026485807148 -
[60]
M. E. J. Newman, C. Moore, D. J. Watts,
Mean-field
solution of the small-world network model, Phys. Rev. Lett. 84 (2000)
3201–3204.
doi:10.1103/PhysRevLett.84.3201.
URL https://link.aps.org/doi/10.1103/PhysRevLett.84.3201 - [61] E. A. Bender, E. R. Canfield, The asymptotic number of labeled graphs with given degree sequences, J. Comb. Theory A 24 (1978) 296–307.
- [62] B. Bollobás, A probabilistic proof of an asymptotic formula for the number of labelled regular graphs, Eur. J. Combin. 1 (1980) 311–316.
-
[63]
Z. Burda, A. Krzywicki,
Uncorrelated
random networks, Phys. Rev. E 67 (2003) 046118.
doi:10.1103/PhysRevE.67.046118.
URL https://link.aps.org/doi/10.1103/PhysRevE.67.046118 -
[64]
M. Boguñá, R. Pastor-Satorras, A. Vespignani,
Cut-offs and finite size
effects in scale-free networks, Eur. Phys. J. B 38 (2004) 205–209.
doi:10.1140/epjb/e2004-00038-8.
URL https://doi.org/10.1140/epjb/e2004-00038-8 -
[65]
E. Volz, Random
networks with tunable degree distribution and clustering, Phys. Rev. E 70
(2004) 056115.
doi:10.1103/PhysRevE.70.056115.
URL https://link.aps.org/doi/10.1103/PhysRevE.70.056115 -
[66]
M. Ángeles Serrano, M. Boguñá,
Tuning clustering
in random networks with arbitrary degree distributions, Phys. Rev. E 72
(2005) 036133.
doi:10.1103/PhysRevE.72.036133.
URL https://link.aps.org/doi/10.1103/PhysRevE.72.036133 -
[67]
K.-I. Goh, B. Kahng, D. Kim,
Universal
behavior of load distribution in scale-free networks, Phys. Rev. Lett. 87
(2001) 278701.
doi:10.1103/PhysRevLett.87.278701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.87.278701 -
[68]
G. Caldarelli, A. Capocci, P. De Los Rios, M. A. Muñoz,
Scale-free
networks from varying vertex intrinsic fitness, Phys. Rev. Lett. 89 (2002)
258702.
doi:10.1103/PhysRevLett.89.258702.
URL https://link.aps.org/doi/10.1103/PhysRevLett.89.258702 -
[69]
B. Söderberg,
General formalism
for inhomogeneous random graphs, Phys. Rev. E 66 (2002) 066121.
doi:10.1103/PhysRevE.66.066121.
URL https://link.aps.org/doi/10.1103/PhysRevE.66.066121 -
[70]
F. Chung, L. Lu, The average
distances in random graphs with given expected degrees, Proc. Natl. Acad.
Sci. U.S.A. 99 (2002) 15879–15882.
doi:10.1073/pnas.252631999.
URL https://www.pnas.org/content/99/25/15879 -
[71]
M. Boguñá, R. Pastor-Satorras,
Class of
correlated random networks with hidden variables, Phys. Rev. E 68 (2003)
036112.
doi:10.1103/PhysRevE.68.036112.
URL https://link.aps.org/doi/10.1103/PhysRevE.68.036112 -
[72]
R. Cohen, K. Erez, D. ben Avraham, S. Havlin,
Breakdown of the
internet under intentional attack, Phys. Rev. Lett. 86 (2001) 3682–3685.
doi:10.1103/PhysRevLett.86.3682.
URL https://link.aps.org/doi/10.1103/PhysRevLett.86.3682 -
[73]
H. Hong, M. Ha, H. Park,
Finite-size
scaling in complex networks, Phys. Rev. Lett. 98 (2007) 258701.
doi:10.1103/PhysRevLett.98.258701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.98.258701 -
[74]
B. Waclaw, L. Bogacz, W. Janke,
Approaching the
thermodynamic limit in equilibrated scale-free networks, Phys. Rev. E 78
(2008) 061125.
doi:10.1103/PhysRevE.78.061125.
URL https://link.aps.org/doi/10.1103/PhysRevE.78.061125 -
[75]
C. Castellano, R. Pastor-Satorras,
Routes to
thermodynamic limit on scale-free networks, Phys. Rev. Lett. 100 (2008)
148701.
doi:10.1103/PhysRevLett.100.148701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.100.148701 -
[76]
Y. Baek, D. Kim, M. Ha, H. Jeong,
Fundamental
structural constraint of random scale-free networks, Phys. Rev. Lett. 109
(2012) 118701.
doi:10.1103/PhysRevLett.109.118701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.109.118701 - [77] M. Molloy, B. Reed, A critical point for random graphs with a given degree sequence, Random Struct. Alg. 6 (1995) 161–180.
-
[78]
W. Aiello, F. Chung, L. Lu,
A random graph model
for power law graphs, Exp. Math. 10 (2001) 53–66.
doi:10.1080/10586458.2001.10504428.
URL https://doi.org/10.1080/10586458.2001.10504428 - [79] F. Chung, L. Lu, Connected components in random graphs with given expected degree sequences, Ann. Comb. 6 (2002) 125–145.
- [80] S. Janson, M. J. Luczak, A new approach to the giant component problem, Random Struct. Alg. 34 (2009) 197–216.
- [81] B. Bollobas, O. Riordan, Asymptotic normality of the size of the giant component in a random hypergraph, Random Struct. Alg. 41 (2012) 441–450.
- [82] H. Hatami, M. Molloy, The scaling window for a random graph with a given degree sequence, Random Struct. Alg. 41 (2012) 99–123.
-
[83]
D. S. Callaway, M. E. J. Newman, S. H. Strogatz, D. J. Watts,
Network
robustness and fragility: Percolation on random graphs, Phys. Rev. Lett. 85
(2000) 5468–5471.
doi:10.1103/PhysRevLett.85.5468.
URL https://link.aps.org/doi/10.1103/PhysRevLett.85.5468 -
[84]
R. Cohen, K. Erez, D. ben Avraham, S. Havlin,
Resilience of the
internet to random breakdowns, Phys. Rev. Lett. 85 (2000) 4626–4628.
doi:10.1103/PhysRevLett.85.4626.
URL https://link.aps.org/doi/10.1103/PhysRevLett.85.4626 - [85] R. Albert, H. Jeong, A.-L. Barabási, Error and attack tolerance of complex networks, Nature 406 (2000) 378. doi:10.1038/35019019.
- [86] R. Cohen, S. Havlin, Complex networks: structure, robustness and function, Cambridge university press, 2010.
-
[87]
M. E. J. Newman,
Spread of epidemic
disease on networks, Phys. Rev. E 66 (2002) 016128.
doi:10.1103/PhysRevE.66.016128.
URL https://link.aps.org/doi/10.1103/PhysRevE.66.016128 -
[88]
J. P. Gleeson, S. Melnik, J. A. Ward, M. A. Porter, P. J. Mucha,
Accuracy of
mean-field theory for dynamics on real-world networks, Phys. Rev. E 85
(2012) 026106.
doi:10.1103/PhysRevE.85.026106.
URL https://link.aps.org/doi/10.1103/PhysRevE.85.026106 -
[89]
I. Tishby, O. Biham, E. Katzav, R. Kühn,
Revealing the
microstructure of the giant component in random graph ensembles, Phys. Rev.
E 97 (2018) 042318.
doi:10.1103/PhysRevE.97.042318.
URL https://link.aps.org/doi/10.1103/PhysRevE.97.042318 -
[90]
M. Starnini, R. Pastor-Satorras,
Temporal
percolation in activity-driven networks, Phys. Rev. E 89 (2014) 032807.
doi:10.1103/PhysRevE.89.032807.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.032807 -
[91]
M. E. J. Newman,
Component sizes in
networks with arbitrary degree distributions, Phys. Rev. E 76 (2007) 045101.
doi:10.1103/PhysRevE.76.045101.
URL https://link.aps.org/doi/10.1103/PhysRevE.76.045101 -
[92]
I. Kryven, General
expression for the component size distribution in infinite configuration
networks, Phys. Rev. E 95 (2017) 052303.
doi:10.1103/PhysRevE.95.052303.
URL https://link.aps.org/doi/10.1103/PhysRevE.95.052303 -
[93]
I. Kryven, Finite
connected components in infinite directed and multiplex networks with
arbitrary degree distributions, Phys. Rev. E 96 (2017) 052304.
doi:10.1103/PhysRevE.96.052304.
URL https://link.aps.org/doi/10.1103/PhysRevE.96.052304 - [94] R. B. Potts, Some generalized order-disorder transformations, Math. Proc. Cambridge Philos. Soc. 48 (1952) 106–109. doi:10.1017/S0305004100027419.
- [95] M. J. Stephen, Percolation problems and the potts model, Phys. Lett. A 56 (1976) 149–150.
- [96] F. Y. Wu, Percolation and the potts model, J. Stat. Phys. 18 (1978) 115–123.
- [97] P. W. Kasteleyn, C. M. Fortuin, Phase transitions in lattice systems with random local properties, J. Phys. Soc. JPN 26 (1969) 11.
-
[98]
D.-S. Lee, K.-I. Goh, B. Kahng, D. Kim,
Evolution
of scale-free random graphs: Potts model formulation, Nucl. Phys. B 696
(2004) 351 – 380.
doi:https://doi.org/10.1016/j.nuclphysb.2004.06.029.
URL http://www.sciencedirect.com/science/article/pii/S0550321304004298 - [99] D.-S. Lee, K.-I. Goh, B. Kahng, D. Kim, Scale-free random graphs and potts model, Pramana-J Phys 64 (2005) 1149–1159.
-
[100]
S. Bradde, G. Bianconi,
The
percolation transition in correlated hypergraphs, J. Stat. Mech. 2009 (2009)
P07028.
doi:10.1088/1742-5468/2009/07/p07028.
URL https://doi.org/10.1088%2F1742-5468%2F2009%2F07%2Fp07028 - [101] S. Bradde, G. Bianconi, Percolation transition and distribution of connected components in generalized random network ensembles, J. Phys. A: Math. Theor. 42 (2009) 195007. doi:10.1088/1751-8113/42/19/195007.
- [102] S. Dorogovtsev, A. Goltsev, J. F. F. Mendes, Potts model on complex networks, Eur. Phys. J. B 38 (2004) 177–182. doi:10.1140/epjb/e2004-00019-y.
-
[103]
B. Karrer, M. E. J. Newman, L. Zdeborová,
Percolation on
sparse networks, Phys. Rev. Lett. 113 (2014) 208702.
doi:10.1103/PhysRevLett.113.208702.
URL https://link.aps.org/doi/10.1103/PhysRevLett.113.208702 -
[104]
M. E. J. Newman, T. Martin,
Equitable random
graphs, Phys. Rev. E 90 (2014) 052824.
doi:10.1103/PhysRevE.90.052824.
URL https://link.aps.org/doi/10.1103/PhysRevE.90.052824 -
[105]
K. E. Hamilton, L. P. Pryadko,
Tight lower
bound for percolation threshold on an infinite graph, Phys. Rev. Lett. 113
(2014) 208701.
doi:10.1103/PhysRevLett.113.208701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.113.208701 -
[106]
F. Radicchi,
Predicting
percolation thresholds in networks, Phys. Rev. E 91 (2015) 010801.
doi:10.1103/PhysRevE.91.010801.
URL https://link.aps.org/doi/10.1103/PhysRevE.91.010801 - [107] F. Radicchi, Percolation in real interdependent networks, Nat. Phys. 11 (2015) 597–602. doi:10.1038/nphys3374.
-
[108]
A. Allard, L. Hébert-Dufresne, J.-G. Young, L. J. Dubé,
General and exact
approach to percolation on random graphs, Phys. Rev. E 92 (2015) 062807.
doi:10.1103/PhysRevE.92.062807.
URL https://link.aps.org/doi/10.1103/PhysRevE.92.062807 -
[109]
F. Radicchi, C. Castellano,
Beyond the locally
treelike approximation for percolation on real networks, Phys. Rev. E 93
(2016) 030302.
doi:10.1103/PhysRevE.93.030302.
URL https://link.aps.org/doi/10.1103/PhysRevE.93.030302 -
[110]
R. Kühn,
Disentangling
giant component and finite cluster contributions in sparse random matrix
spectra, Phys. Rev. E 93 (2016) 042110.
doi:10.1103/PhysRevE.93.042110.
URL https://link.aps.org/doi/10.1103/PhysRevE.93.042110 -
[111]
G. Timár, R. A. da Costa, S. N. Dorogovtsev, J. F. F. Mendes,
Nonbacktracking
expansion of finite graphs, Phys. Rev. E 95 (2017) 042322.
doi:10.1103/PhysRevE.95.042322.
URL https://link.aps.org/doi/10.1103/PhysRevE.95.042322 -
[112]
G. Bianconi, F. Radicchi,
Percolation in
real multiplex networks, Phys. Rev. E 94 (2016) 060301.
doi:10.1103/PhysRevE.94.060301.
URL https://link.aps.org/doi/10.1103/PhysRevE.94.060301 -
[113]
G. Bianconi, Epidemic
spreading and bond percolation on multilayer networks, J. Stat. Mech. 2017
(2017) 034001.
doi:10.1088/1742-5468/aa5fd8.
URL https://doi.org/10.1088%2F1742-5468%2Faa5fd8 -
[114]
K. ichiro Hashimoto,
Zeta
functions of finite graphs and representations of p-adic groups, in:
K. Hashimoto, Y. Namikawa (Eds.), Automorphic Forms and Geometry of
Arithmetic Varieties, Vol. 15 of Advanced Studies in Pure Mathematics,
Academic Press, 1989, pp. 211 – 280.
doi:https://doi.org/10.1016/B978-0-12-330580-0.50015-X.
URL http://www.sciencedirect.com/science/article/pii/B978012330580050015X - [115] F. Krzakala, C. Moore, E. Mossel, J. Neeman, A. Sly, L. Zdeborova, P. Zhang, Spectral redemption in clustering sparse networks, Proc. Natl. Acad. Sci. U.S.A. 110 (52) (2013) 20935–20940. doi:10.1073/pnas.1312486110.
-
[116]
P. Zhang, Spectral
estimation of the percolation transition in clustered networks, Phys. Rev. E
96 (2017) 042303.
doi:10.1103/PhysRevE.96.042303.
URL https://link.aps.org/doi/10.1103/PhysRevE.96.042303 -
[117]
M. E. J. Newman, G. Ghoshal,
Bicomponents
and the robustness of networks to failure, Phys. Rev. Lett. 100 (2008)
138701.
doi:10.1103/PhysRevLett.100.138701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.100.138701 -
[118]
Y.-Y. Liu, E. Csóka, H. Zhou, M. Pósfai,
Core
percolation on complex networks, Phys. Rev. Lett. 109 (2012) 205703.
doi:10.1103/PhysRevLett.109.205703.
URL https://link.aps.org/doi/10.1103/PhysRevLett.109.205703 - [119] L. Tian, A. Bashan, D.-N. Shi, Y.-Y. Liu, Articulation points in complex networks, Nat. Commun. 8 (2017) 14223. doi:10.1038/ncomms14223.
- [120] S. V. Buldyrev, R. Parshani, G. Paul, H. E. Stanley, S. Havlin, Catastrophic cascade of failures in interdependent networks, Nature 464 (2010) 1025. doi:10.1038/nature08932.
-
[121]
R. Parshani, S. V. Buldyrev, S. Havlin,
Interdependent
networks: Reducing the coupling strength leads to a change from a first to
second order percolation transition, Phys. Rev. Lett. 105 (2010) 048701.
doi:10.1103/PhysRevLett.105.048701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.105.048701 -
[122]
R. Parshani, S. V. Buldyrev, S. Havlin,
Critical effect of dependency
groups on the function of networks, Proc. Natl. Acad. Sci. U.S.A. 108 (2011)
1007–1010.
doi:10.1073/pnas.1008404108.
URL https://www.pnas.org/content/108/3/1007 -
[123]
B. Bollobás, O. Riordan, Clique
percolation, Random Struct. Alg. 35 (2009) 294–322.
doi:10.1002/rsa.20270.
URL http://dx.doi.org/10.1002/rsa.20270 -
[124]
M. Li, Y. Deng, B.-H. Wang,
Clique percolation
in random graphs, Phys. Rev. E 92 (2015) 042116.
doi:10.1103/PhysRevE.92.042116.
URL https://link.aps.org/doi/10.1103/PhysRevE.92.042116 - [125] D. S. Callaway, J. E. Hopcroft, J. M. Kleinberg, M. E. J. Newman, S. H. Strogatz, Are randomly grown graphs really random?, Phys. Rev. E 64 (2001) 041902. doi:10.1103/physreve.64.041902.
-
[126]
S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Pseudofractal
scale-free web, Phys. Rev. E 65 (2002) 066122.
doi:10.1103/PhysRevE.65.066122.
URL https://link.aps.org/doi/10.1103/PhysRevE.65.066122 - [127] M. A. Serrano, D. Krioukov, M. Boguñá, Percolation in self-similar networks, Phys. Rev. Lett. 106 (2011) 048701. doi:10.1103/PhysRevLett.106.048701.
-
[128]
D. M. Auto, A. A. Moreira, H. J. Herrmann, J. S. Andrade,
Finite-size
effects for percolation on apollonian networks, Phys. Rev. E 78 (2008)
066112.
doi:10.1103/PhysRevE.78.066112.
URL https://link.aps.org/doi/10.1103/PhysRevE.78.066112 -
[129]
C. P. Warren, L. M. Sander, I. M. Sokolov,
Geography in a
scale-free network model, Phys. Rev. E 66 (2002) 056105.
doi:10.1103/PhysRevE.66.056105.
URL https://link.aps.org/doi/10.1103/PhysRevE.66.056105 -
[130]
H. Bateman,
Higher
Transcendental Functions, Vol. I, McGraw-Hill Book Company, New York, 1953.
URL https://resolver.caltech.edu/CaltechAUTHORS:20140123-104529738 -
[131]
R. Cohen, D. ben Avraham, S. Havlin,
Percolation
critical exponents in scale-free networks, Phys. Rev. E 66 (2002) 036113.
doi:10.1103/PhysRevE.66.036113.
URL https://link.aps.org/doi/10.1103/PhysRevE.66.036113 - [132] R. Cohen, S. Havlin, Fractal dimensions of percolating networks, Physica A 336 (2004) 6–13. doi:10.1016/j.physa.2004.01.005.
- [133] A. Janssen, J. S. van Leeuwaarden, Giant component sizes in scale-free networks with power-law degrees and cutoffs, Europhys. Lett. 112 (2016) 68001. doi:10.1209/0295-5075/112/68001.
-
[134]
D.-S. Lee, J. S. Kim, B. Kahng, D. Kim,
Scale-free random
branching trees in supercritical phase, J. Phys. A: Math. Theor. 40 (2007)
7139–7149.
doi:10.1088/1751-8113/40/26/002.
URL https://doi.org/10.1088%2F1751-8113%2F40%2F26%2F002 -
[135]
Z. Burda, J. D. Correia, A. Krzywicki,
Statistical
ensemble of scale-free random graphs, Phys. Rev. E 64 (2001) 046118.
doi:10.1103/PhysRevE.64.046118.
URL https://link.aps.org/doi/10.1103/PhysRevE.64.046118 -
[136]
A. V. Goltsev, S. N. Dorogovtsev, J. F. F. Mendes,
Critical phenomena
in networks, Phys. Rev. E 67 (2003) 026123.
doi:10.1103/PhysRevE.67.026123.
URL https://link.aps.org/doi/10.1103/PhysRevE.67.026123 - [137] Z. Burda, J. Jurkiewicz, A. Krzywicki, Statistical mechanics of random graphs, Physica A 344 (2004) 56–61.
-
[138]
T. Kalisky, R. Cohen,
Width of
percolation transition in complex networks, Phys. Rev. E 73 (2006) 035101.
doi:10.1103/PhysRevE.73.035101.
URL https://link.aps.org/doi/10.1103/PhysRevE.73.035101 -
[139]
Z. Wu, C. Lagorio, L. A. Braunstein, R. Cohen, S. Havlin, H. E. Stanley,
Numerical
evaluation of the upper critical dimension of percolation in scale-free
networks, Phys. Rev. E 75 (2007) 066110.
doi:10.1103/PhysRevE.75.066110.
URL https://link.aps.org/doi/10.1103/PhysRevE.75.066110 -
[140]
H. Seyed-allaei, G. Bianconi, M. Marsili,
Scale-free
networks with an exponent less than two, Phys. Rev. E 73 (2006) 046113.
doi:10.1103/PhysRevE.73.046113.
URL https://link.aps.org/doi/10.1103/PhysRevE.73.046113 -
[141]
G. Timár, S. N. Dorogovtsev, J. F. F. Mendes,
Scale-free
networks with exponent one, Phys. Rev. E 94 (2016) 022302.
doi:10.1103/PhysRevE.94.022302.
URL https://link.aps.org/doi/10.1103/PhysRevE.94.022302 - [142] S. Boettcher, J. L. Cook, R. M. Ziff, Patchy percolation on a hierarchical network with small-world bonds, Phys. Rev. E 80 (2009) 041115. doi:10.1103/PhysRevE.80.041115.
- [143] H. D. Rozenfeld, C. Song, H. A. Makse, Small-world to fractal transition in complex networks: A renormalization group approach, Phys. Rev. Lett. 104 (2010) 025701. doi:10.1103/physrevlett.104.025701.
- [144] T. Hasegawa, M. Sato, K. Nemoto, Generating-function approach for bond percolation in hierarchical networks, Phys. Rev. E 82 (2010) 046101. doi:10.1103/PhysRevE.82.046101.
- [145] D. Li, G. Li, K. Kosmidis, H. E. Stanley, A. Bunde, S. Havlin, Percolation of spatially constraint networks, Europhys. Lett. 93 (2011) 68004. doi:10.1209/0295-5075/93/68004.
- [146] T. Hasegawa, T. Nogawa, Absence of the nonpercolating phase for percolation on the nonplanar hanoi network, Phys. Rev. E 87 (2013) 032810. doi:10.1103/PhysRevE.87.032810.
-
[147]
C. Moore, M. E. J. Newman,
Exact solution of
site and bond percolation on small-world networks, Phys. Rev. E 62 (2000)
7059–7064.
doi:10.1103/PhysRevE.62.7059.
URL https://link.aps.org/doi/10.1103/PhysRevE.62.7059 -
[148]
M. E. J. Newman, I. Jensen, R. M. Ziff,
Percolation and
epidemics in a two-dimensional small world, Phys. Rev. E 65 (2002) 021904.
doi:10.1103/PhysRevE.65.021904.
URL https://link.aps.org/doi/10.1103/PhysRevE.65.021904 -
[149]
Y. Berchenko, Y. Artzy-Randrup, M. Teicher, L. Stone,
Emergence and
size of the giant component in clustered random graphs with a given degree
distribution, Phys. Rev. Lett. 102 (2009) 138701.
doi:10.1103/PhysRevLett.102.138701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.102.138701 - [150] S. Wasserman, K. Faust, Social network analysis: Methods and applications, Cambridge University Press, 1994.
-
[151]
I. Z. Kiss, D. M. Green,
Comment on
“properties of highly clustered networks”, Phys. Rev. E 78 (2008) 048101.
doi:10.1103/PhysRevE.78.048101.
URL https://link.aps.org/doi/10.1103/PhysRevE.78.048101 -
[152]
M. E. J. Newman,
Random graphs
with clustering, Phys. Rev. Lett. 103 (2009) 058701.
doi:10.1103/PhysRevLett.103.058701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.103.058701 -
[153]
J. C. Miller,
Percolation and
epidemics in random clustered networks, Phys. Rev. E 80 (2009) 020901.
doi:10.1103/PhysRevE.80.020901.
URL https://link.aps.org/doi/10.1103/PhysRevE.80.020901 -
[154]
J. P. Gleeson, S. Melnik, A. Hackett,
How clustering
affects the bond percolation threshold in complex networks, Phys. Rev. E 81
(2010) 066114.
doi:10.1103/PhysRevE.81.066114.
URL https://link.aps.org/doi/10.1103/PhysRevE.81.066114 -
[155]
M. A. Serrano, M. Boguñá,
Percolation and
epidemic thresholds in clustered networks, Phys. Rev. Lett. 97 (2006)
088701.
doi:10.1103/PhysRevLett.97.088701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.97.088701 - [156] M. P. Rombach, M. A. Porter, J. H. Fowler, P. J. Mucha, Core-periphery structure in networks, SIAM J. Appl. Math. 74 (2014) 167–190. doi:10.1137/120881683.
- [157] P. Rombach, M. A. Porter, J. H. Fowler, P. J. Mucha, Core-periphery structure in networks (revisited), SIAM Rev. 59 (2017) 619–646. doi:10.1137/17M1130046.
-
[158]
P. Colomer-de Simón, M. Boguñá,
Double percolation
phase transition in clustered complex networks, Phys. Rev. X 4 (2014)
041020.
doi:10.1103/PhysRevX.4.041020.
URL https://link.aps.org/doi/10.1103/PhysRevX.4.041020 - [159] A. Allard, B. M. Althouse, S. V. Scarpino, L. Hébert-Dufresne, Asymmetric percolation drives a double transition in sexual contact networks, Proc. Natl. Acad. Sci. U.S.A. 114 (2017) 8969–8973. doi:10.1073/pnas.1703073114.
-
[160]
L. Hébert-Dufresne, A. Allard,
Smeared
phase transitions in percolation on real complex networks, Phys. Rev.
Research 1 (2019) 013009.
doi:10.1103/PhysRevResearch.1.013009.
URL https://link.aps.org/doi/10.1103/PhysRevResearch.1.013009 -
[161]
M. E. J. Newman,
Properties of
highly clustered networks, Phys. Rev. E 68 (2003) 026121.
doi:10.1103/PhysRevE.68.026121.
URL https://link.aps.org/doi/10.1103/PhysRevE.68.026121 -
[162]
M. A. Serrano, M. Boguñá,
Clustering in
complex networks. ii. percolation properties, Phys. Rev. E 74 (2006) 056115.
doi:10.1103/PhysRevE.74.056115.
URL https://link.aps.org/doi/10.1103/PhysRevE.74.056115 -
[163]
J. P. Gleeson, Bond
percolation on a class of clustered random networks, Phys. Rev. E 80 (2009)
036107.
doi:10.1103/PhysRevE.80.036107.
URL https://link.aps.org/doi/10.1103/PhysRevE.80.036107 - [164] R. L. Graham, P. Hell, On the history of the minimum spanning tree problem, IEEE Ann. Hist. Comput. 7 (1985) 43–57. doi:10.1109/MAHC.1985.10011.
- [165] D. Cheriton, R. E. Tarjan, Finding minimum spanning trees, SIAM J. Comput. 5 (1976) 724–742. doi:10.1137/0205051.
-
[166]
R. Dobrin, P. M. Duxbury,
Minimum spanning
trees on random networks, Phys. Rev. Lett. 86 (2001) 5076–5079.
doi:10.1103/PhysRevLett.86.5076.
URL https://link.aps.org/doi/10.1103/PhysRevLett.86.5076 -
[167]
B. Karrer, M. E. J. Newman,
Random graphs
containing arbitrary distributions of subgraphs, Phys. Rev. E 82 (2010)
066118.
doi:10.1103/PhysRevE.82.066118.
URL https://link.aps.org/doi/10.1103/PhysRevE.82.066118 -
[168]
P. Mann, V. A. Smith, J. B. O. Mitchell, S. Dobson,
Percolation in random graphs with
higher-order clustering, arXiv preprint arXiv:2006.06744 (2020).
URL https://arxiv.org/abs/2006.06744 -
[169]
G. Ghoshal, V. Zlatić, G. Caldarelli, M. E. J.
Newman, Random
hypergraphs and their applications, Phys. Rev. E 79 (2009) 066118.
doi:10.1103/PhysRevE.79.066118.
URL https://link.aps.org/doi/10.1103/PhysRevE.79.066118 -
[170]
I. Derényi, G. Palla, T. Vicsek,
Clique
percolation in random networks, Phys. Rev. Lett. 94 (2005) 160202.
doi:10.1103/PhysRevLett.94.160202.
URL https://link.aps.org/doi/10.1103/PhysRevLett.94.160202 - [171] G. Palla, I. Derényi, I. Farkas, T. Vicsek, Uncovering the overlapping community structure of complex networks in nature and society, Nature 435 (2005) 814–818. doi:10.1038/nature03607.
-
[172]
A. Vázquez, Y. Moreno,
Resilience to
damage of graphs with degree correlations, Phys. Rev. E 67 (2003) 015101.
doi:10.1103/PhysRevE.67.015101.
URL https://link.aps.org/doi/10.1103/PhysRevE.67.015101 -
[173]
A. V. Goltsev, S. N. Dorogovtsev, J. F. F. Mendes,
Percolation on
correlated networks, Phys. Rev. E 78 (2008) 051105.
doi:10.1103/PhysRevE.78.051105.
URL https://link.aps.org/doi/10.1103/PhysRevE.78.051105 -
[174]
C. Schmeltzer, J. Soriano, I. M. Sokolov, S. Rüdiger,
Percolation of
spatially constrained Erdös-Rényi networks with degree
correlations, Phys. Rev. E 89 (2014) 012116.
doi:10.1103/PhysRevE.89.012116.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.012116 -
[175]
J. D. Noh,
Percolation
transition in networks with degree-degree correlation, Phys. Rev. E 76
(2007) 026116.
doi:10.1103/PhysRevE.76.026116.
URL https://link.aps.org/doi/10.1103/PhysRevE.76.026116 - [176] S. Mizutaka, T. Hasegawa, Percolation on a maximally disassortative network, Europhys. Lett. 128 (4) (2020) 46003. doi:10.1209/0295-5075/128/46003.
-
[177]
L. D. Valdez, C. Buono, L. A. Braunstein, P. A. Macri,
Effect of degree
correlations above the first shell on the percolation transition, Europhys.
Lett. 96 (2011) 38001.
doi:10.1209/0295-5075/96/38001.
URL https://doi.org/10.1209%2F0295-5075%2F96%2F38001 -
[178]
E. Agliari, C. Cioli, E. Guadagnini,
Percolation on
correlated random networks, Phys. Rev. E 84 (2011) 031120.
doi:10.1103/PhysRevE.84.031120.
URL https://link.aps.org/doi/10.1103/PhysRevE.84.031120 -
[179]
C. Schmeltzer, J. Soriano, I. M. Sokolov, S. Rüdiger,
Percolation of
spatially constrained Erdös-Rényi networks with degree
correlations, Phys. Rev. E 89 (2014) 012116.
doi:10.1103/PhysRevE.89.012116.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.012116 -
[180]
A. Allard, L. Hébert-Dufresne, P.-A. Noël, V. Marceau, L. J. Dubé,
Bond
percolation on a class of correlated and clustered random graphs, J. Phys.
A: Math. Theor. 45 (2012) 405005.
doi:10.1088/1751-8113/45/40/405005.
URL https://doi.org/10.1088%2F1751-8113%2F45%2F40%2F405005 -
[181]
A. Allard, L. Hébert-Dufresne, P.-A. Noël, V. Marceau, L. J. Dubé,
Exact solution of
bond percolation on small arbitrary graphs, Europhys. Lett. 98 (2012) 16001.
doi:10.1209/0295-5075/98/16001.
URL https://doi.org/10.1209%2F0295-5075%2F98%2F16001 - [182] S. N. Dorogovtsev, J. F. F. Mendes, A. N. Samukhin, Giant strongly connected component of directed networks, Phys. Rev. E 64 (2001) 025101. doi:10.1103/physreve.64.025101.
- [183] N. Schwartz, R. Cohen, D. ben Avraham, A.-L. Barabási, S. Havlin, Percolation in directed scale-free networks, Phys. Rev. E 66 (2002) 015104. doi:10.1103/physreve.66.015104.
-
[184]
M. Boguñá, M. A. Serrano,
Generalized
percolation in random directed networks, Phys. Rev. E 72 (2005) 016106.
doi:10.1103/PhysRevE.72.016106.
URL https://link.aps.org/doi/10.1103/PhysRevE.72.016106 -
[185]
M. Ángeles Serrano, P. De Los Rios,
Interfaces and the
edge percolation map of random directed networks, Phys. Rev. E 76 (2007)
056121.
doi:10.1103/PhysRevE.76.056121.
URL https://link.aps.org/doi/10.1103/PhysRevE.76.056121 -
[186]
J. P. Gleeson, Mean
size of avalanches on directed random networks with arbitrary degree
distributions, Phys. Rev. E 77 (2008) 057101.
doi:10.1103/PhysRevE.77.057101.
URL https://link.aps.org/doi/10.1103/PhysRevE.77.057101 -
[187]
J. G. Restrepo, E. Ott, B. R. Hunt,
Weighted
percolation on directed networks, Phys. Rev. Lett. 100 (2008) 058701.
doi:10.1103/PhysRevLett.100.058701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.100.058701 -
[188]
P. van der Hoorn, N. Litvak,
Phase transitions
for scaling of structural correlations in directed networks, Phys. Rev. E 92
(2015) 022803.
doi:10.1103/PhysRevE.92.022803.
URL https://link.aps.org/doi/10.1103/PhysRevE.92.022803 -
[189]
X. Liu, L. Pan, H. E. Stanley, J. Gao,
Controllability of
giant connected components in a directed network, Phys. Rev. E 95 (2017)
042318.
doi:10.1103/PhysRevE.95.042318.
URL https://link.aps.org/doi/10.1103/PhysRevE.95.042318 -
[190]
L. A. Meyers, M. Newman, B. Pourbohloul,
Predicting
epidemics on directed contact networks, J. Theor. Biol. 240 (2006) 400 –
418.
doi:https://doi.org/10.1016/j.jtbi.2005.10.004.
URL http://www.sciencedirect.com/science/article/pii/S0022519305004418 -
[191]
J. Hoshen, R. Kopelman,
Percolation and
cluster distribution. i. cluster multiple labeling technique and critical
concentration algorithm, Phys. Rev. B 14 (1976) 3438–3445.
doi:10.1103/PhysRevB.14.3438.
URL https://link.aps.org/doi/10.1103/PhysRevB.14.3438 -
[192]
M. E. J. Newman, R. M. Ziff,
Fast monte carlo
algorithm for site or bond percolation, Phys. Rev. E 64 (2001) 016706.
doi:10.1103/PhysRevE.64.016706.
URL https://link.aps.org/doi/10.1103/PhysRevE.64.016706 -
[193]
S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
-core
organization of complex networks, Phys. Rev. Lett. 96 (2006) 040601.
doi:10.1103/PhysRevLett.96.040601.
URL https://link.aps.org/doi/10.1103/PhysRevLett.96.040601 -
[194]
D. J. Watts, A simple model of
global cascades on random networks, Proc. Natl. Acad. Sci. U.S.A. 99 (2002)
5766–5771.
doi:10.1073/pnas.082090499.
URL https://www.pnas.org/content/99/9/5766 -
[195]
R.-R. Liu, W.-X. Wang, Y.-C. Lai, B.-H. Wang,
Cascading dynamics
on random networks: Crossover in phase transition, Phys. Rev. E 85 (2012)
026110.
doi:10.1103/PhysRevE.85.026110.
URL https://link.aps.org/doi/10.1103/PhysRevE.85.026110 -
[196]
G. J. Baxter, S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Bootstrap
percolation on complex networks, Phys. Rev. E 82 (2010) 011103.
doi:10.1103/PhysRevE.82.011103.
URL https://link.aps.org/doi/10.1103/PhysRevE.82.011103 - [197] Y. Yang, J. Wang, A. E. Motter, Network observability transitions, Phys. Rev. Lett. 109 (2012) 258701. doi:10.1103/physrevlett.109.258701.
-
[198]
Y. Shang, W. Luo, S. Xu,
-hop
percolation on networks with arbitrary degree distributions and its
applications, Phys. Rev. E 84 (2011) 031113.
doi:10.1103/PhysRevE.84.031113.
URL https://link.aps.org/doi/10.1103/PhysRevE.84.031113 - [199] M. Li, L. Lü, Y. Deng, M.-B. Hu, H. Wang, M. Medo, H. E. Stanley, History-dependent percolation on multiplex networks, Natl. Sci. Rev. 7 (2020) 1296–1305. doi:10.1093/nsr/nwaa029.
-
[200]
M. Hu, Y. Sun, D. Wang, J.-P. Lv, Y. Deng,
History-dependent
percolation in two dimensions, Phys. Rev. E 102 (2020) 052121.
doi:10.1103/PhysRevE.102.052121.
URL https://link.aps.org/doi/10.1103/PhysRevE.102.052121 - [201] D. Achlioptas, R. M. D’Souza, J. Spencer, Explosive percolation in random networks, Science 323 (2009) 1453–1455. doi:10.1126/science.1167782.
-
[202]
E. J. Friedman, A. S. Landsberg,
Construction
and analysis of random networks with explosive percolation, Phys. Rev. Lett.
103 (2009) 255701.
doi:10.1103/PhysRevLett.103.255701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.103.255701 -
[203]
R. A. da Costa, S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Explosive
percolation transition is actually continuous, Phys. Rev. Lett. 105 (2010)
255701.
doi:10.1103/PhysRevLett.105.255701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.105.255701 -
[204]
R. M. D’Souza, M. Mitzenmacher,
Local cluster
aggregation models of explosive percolation, Phys. Rev. Lett. 104 (2010)
195702.
doi:10.1103/PhysRevLett.104.195702.
URL https://link.aps.org/doi/10.1103/PhysRevLett.104.195702 -
[205]
A. A. Moreira, E. A. Oliveira, S. D. S. Reis, H. J. Herrmann, J. S. Andrade,
Hamiltonian
approach for explosive percolation, Phys. Rev. E 81 (2010) 040101.
doi:10.1103/PhysRevE.81.040101.
URL https://link.aps.org/doi/10.1103/PhysRevE.81.040101 -
[206]
S. Boccaletti, J. Almendral, S. Guan, I. Leyva, Z. Liu, I. Sendiña-Nadal,
Z. Wang, Y. Zou,
Explosive
transitions in complex networks’ structure and dynamics: Percolation and
synchronization, Phys. Rep. 660 (2016) 1 – 94.
doi:https://doi.org/10.1016/j.physrep.2016.10.004.
URL http://www.sciencedirect.com/science/article/pii/S0370157316303180 -
[207]
E. López, R. Parshani, R. Cohen, S. Carmi, S. Havlin,
Limited path
percolation in complex networks, Phys. Rev. Lett. 99 (2007) 188701.
doi:10.1103/PhysRevLett.99.188701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.99.188701 -
[208]
J.-Q. Dong, Z. Shen, Y. Zhang, Z.-G. Huang, L. Huang, X. Chen,
Finite-size
scaling of clique percolation on two-dimensional moore lattices, Phys. Rev.
E 97 (2018) 052133.
doi:10.1103/PhysRevE.97.052133.
URL https://link.aps.org/doi/10.1103/PhysRevE.97.052133 -
[209]
S. M. Krause, M. M. Danziger, V. Zlatić,
Color-avoiding
percolation, Phys. Rev. E 96 (2017) 022313.
doi:10.1103/PhysRevE.96.022313.
URL https://link.aps.org/doi/10.1103/PhysRevE.96.022313 -
[210]
A. Kadović, S. M. Krause, G. Caldarelli, V. Zlatic,
Bond and site
color-avoiding percolation in scale-free networks, Phys. Rev. E 98 (2018)
062308.
doi:10.1103/PhysRevE.98.062308.
URL https://link.aps.org/doi/10.1103/PhysRevE.98.062308 -
[211]
S. B. Seidman,
Network
structure and minimum degree, Soc. Networks 5 (1983) 269 – 287.
doi:https://doi.org/10.1016/0378-8733(83)90028-X.
URL http://www.sciencedirect.com/science/article/pii/037887338390028X - [212] B. Bollobás (Ed.), Graph Theory and Combinatorics: Proceedings of the Cambridge Combinatorial Conference in Honour of Paul Erdös, [Trinity College, Cambridge, 21-25 March 1983], Academic Press, 1984.
-
[213]
B. Pittel, J. Spencer, N. Wormald,
Sudden
emergence of a giant k-core in a random graph, J. Comb. Theory B 67 (1996)
111 – 151.
doi:https://doi.org/10.1006/jctb.1996.0036.
URL http://www.sciencedirect.com/science/article/pii/S0095895696900362 -
[214]
Y.-X. Kong, G.-Y. Shi, R.-J. Wu, Y.-C. Zhang,
k-core:
Theories and applications, Phys. Rep. 832 (2019) 1 – 32.
doi:https://doi.org/10.1016/j.physrep.2019.10.004.
URL http://www.sciencedirect.com/science/article/pii/S037015731930328X -
[215]
J. Chalupa, P. L. Leath, G. R. Reich,
Bootstrap
percolation on a bethe lattice, J. Phys. C: Solid State Phys. 12 (1979)
L31–L35.
doi:10.1088/0022-3719/12/1/008.
URL https://doi.org/10.1088%2F0022-3719%2F12%2F1%2F008 - [216] H. Schawe, A. K. Hartmann, Large-deviation properties of the largest biconnected component for random graphs, Eur. Phys. J. B 92 (2019) 73. doi:10.1140/epjb/e2019-90667-y.
-
[217]
Y. Zhu, X. Chen, Revealing the phase
transition behaviors of k-core percolation in random networks, arXiv
preprint arXiv:1710.02959 (2017).
URL https://arxiv.org/abs/1710.02959 -
[218]
P. Kim, D.-S. Lee, B. Kahng,
Phase transition
in the biconnectivity of scale-free networks, Phys. Rev. E 87 (2013) 022804.
doi:10.1103/PhysRevE.87.022804.
URL https://link.aps.org/doi/10.1103/PhysRevE.87.022804 -
[219]
D. Lee, M. Jo, B. Kahng,
Critical behavior
of -core percolation: Numerical studies, Phys. Rev. E 94 (2016) 062307.
doi:10.1103/PhysRevE.94.062307.
URL https://link.aps.org/doi/10.1103/PhysRevE.94.062307 -
[220]
A. B. Harris, J. M. Schwarz,
expansion
for -core percolation, Phys. Rev. E 72 (2005) 046123.
doi:10.1103/PhysRevE.72.046123.
URL https://link.aps.org/doi/10.1103/PhysRevE.72.046123 - [221] C. Farrow, P. Shukla, P. Duxbury, Dynamics of k-core percolation, J. Phys. A: Math. Theor. 40 (2007) F581. doi:10.1088/1751-8113/40/27/F02.
-
[222]
G. Parisi, T. Rizzo,
-core
percolation in four dimensions, Phys. Rev. E 78 (2008) 022101.
doi:10.1103/PhysRevE.78.022101.
URL https://link.aps.org/doi/10.1103/PhysRevE.78.022101 -
[223]
T. Rizzo, Fate
of the hybrid transition of bootstrap percolation in physical dimension,
Phys. Rev. Lett. 122 (2019) 108301.
doi:10.1103/PhysRevLett.122.108301.
URL https://link.aps.org/doi/10.1103/PhysRevLett.122.108301 -
[224]
S. Dorogovtsev, A. Goltsev, J. Mendes,
k-core
architecture and k-core percolation on complex networks, Physica D 224
(2006) 7 – 19, dynamics on Complex Networks and Applications.
doi:https://doi.org/10.1016/j.physd.2006.09.027.
URL http://www.sciencedirect.com/science/article/pii/S0167278906003617 -
[225]
A. V. Goltsev, S. N. Dorogovtsev, J. F. F. Mendes,
-core
(bootstrap) percolation on complex networks: Critical phenomena and nonlocal
effects, Phys. Rev. E 73 (2006) 056101.
doi:10.1103/PhysRevE.73.056101.
URL https://link.aps.org/doi/10.1103/PhysRevE.73.056101 -
[226]
J. P. Gleeson, S. Melnik,
Analytical results
for bond percolation and -core sizes on clustered networks, Phys. Rev. E
80 (2009) 046121.
doi:10.1103/PhysRevE.80.046121.
URL https://link.aps.org/doi/10.1103/PhysRevE.80.046121 -
[227]
U. Bhat, M. Shrestha, L. Hébert-Dufresne,
Exotic phase
transitions of -cores in clustered networks, Phys. Rev. E 95 (2017)
012314.
doi:10.1103/PhysRevE.95.012314.
URL https://link.aps.org/doi/10.1103/PhysRevE.95.012314 -
[228]
X. Yuan, Y. Dai, H. E. Stanley, S. Havlin,
-core
percolation on complex networks: Comparing random, localized, and targeted
attacks, Phys. Rev. E 93 (2016) 062302.
doi:10.1103/PhysRevE.93.062302.
URL https://link.aps.org/doi/10.1103/PhysRevE.93.062302 - [229] M. Sellitto, G. Biroli, C. Toninelli, Facilitated spin models on bethe lattice: Bootstrap percolation, mode-coupling transition and glassy dynamics, Europhys. Lett. 69 (2005) 496. doi:10.1209/epl/i2004-10372-5.
- [230] J. M. Schwarz, A. J. Liu, L. Chayes, The onset of jamming as the sudden emergence of an infinite k-core cluster, Europhys. Lett. 73 (2006) 560. doi:10.1209/epl/i2005-10421-7.
-
[231]
J. I. Alvarez-Hamelin, A. Puglisi,
Dynamical
collision network in granular gases, Phys. Rev. E 75 (2007) 051302.
doi:10.1103/PhysRevE.75.051302.
URL https://link.aps.org/doi/10.1103/PhysRevE.75.051302 -
[232]
P. Klimek, S. Thurner, R. Hanel,
Pruning
the tree of life: k-core percolation as selection mechanism, J. Theor. Biol.
256 (2009) 142 – 146.
doi:https://doi.org/10.1016/j.jtbi.2008.09.030.
URL http://www.sciencedirect.com/science/article/pii/S0022519308004979 -
[233]
N. Chatterjee, S. Sinha,
Understanding
the mind of a worm: hierarchical network structure underlying nervous system
function in c. elegans, in: R. Banerjee, B. K. Chakrabarti (Eds.), Models of
Brain and Mind, Vol. 168 of Progress in Brain Research, Elsevier, 2007, pp.
145 –153.
doi:https://doi.org/10.1016/S0079-6123(07)68012-1.
URL http://www.sciencedirect.com/science/article/pii/S0079612307680121 - [234] J.-H. Zhao, H.-J. Zhou, Y.-Y. Liu, Inducing effect on the percolation transition in complex networks, Nat. Commun. 4 (2013) 1–6. doi:10.1038/ncomms3412.
- [235] M. Iwata, S.-I. Sasa, Dynamics of k-core percolation in a random graph, J. Phys. A: Math. Theor. 42 (2009) 075005. doi:10.1088/1751-8113/42/7/075005.
-
[236]
G. J. Baxter, S. N. Dorogovtsev, K.-E. Lee, J. F. F. Mendes, A. V. Goltsev,
Critical dynamics
of the -core pruning process, Phys. Rev. X 5 (2015) 031017.
doi:10.1103/PhysRevX.5.031017.
URL https://link.aps.org/doi/10.1103/PhysRevX.5.031017 -
[237]
R.-J. Wu, Y.-X. Kong, G. yuan Shi, Y.-C. Zhang,
Using nonbacktracking expansion to
analyze k-core pruning process, arXiv preprint arXiv:1811.04295 (2018).
URL https://arxiv.org/abs/1811.04295 -
[238]
R.-J. Wu, Y.-X. Kong, G.-Y. Shi, Y.-C. Zhang,
Analytical results of k-core pruning
process on multi-layer networks, arXiv preprint arXiv:1812.11111 (2018).
URL https://arxiv.org/abs/1812.11111 -
[239]
G.-Y. Shi, R.-J. Wu, Y.-X. Kong, H. E. Stanley, Y.-C. Zhang,
An analytical solution to the
-core pruning process, arXiv preprint arXiv:1810.08936 (2018).
URL https://arxiv.org/abs/1810.08936 - [240] J. I. Alvarez-Hamelin, L. Dall’Asta, A. Barrat, A. Vespignani, K-core decomposition: a tool for the visualization of large scale networks, Advances in Neural Information Processing Systems 18 (2006) 41.
-
[241]
S. Carmi, S. Havlin, S. Kirkpatrick, Y. Shavitt, E. Shir,
A model of internet topology
using k-shell decomposition, Proc. Natl. Acad. Sci. U.S.A. 104 (2007)
11150–11154.
doi:10.1073/pnas.0701175104.
URL https://www.pnas.org/content/104/27/11150 - [242] M. Kitsak, L. K. Gallos, S. Havlin, F. Liljeros, L. Muchnik, H. E. Stanley, H. A. Makse, Identification of influential spreaders in complex networks, Nat. Phys. 6 (2010) 888. doi:10.1038/nphys1746.
- [243] V. Batagelj, M. Zaversnik, An algorithm for cores decomposition of networks, Advances in Data Analysis and Classification 5 (2011) 129–145.
-
[244]
M. Eidsaa, E. Almaas,
-core network
decomposition: A generalization of -core analysis to weighted networks,
Phys. Rev. E 88 (2013) 062819.
doi:10.1103/PhysRevE.88.062819.
URL https://link.aps.org/doi/10.1103/PhysRevE.88.062819 -
[245]
L. Lü, D. Chen, X.-L. Ren, Q.-M. Zhang, Y.-C. Zhang, T. Zhou,
Vital
nodes identification in complex networks, Phys. Rep. 650 (2016) 1 – 63.
doi:https://doi.org/10.1016/j.physrep.2016.06.007.
URL http://www.sciencedirect.com/science/article/pii/S0370157316301570 - [246] N. Branco, Probabilistic bootstrap percolation, J. Stat. Phys. 70 (1993) 1035–1044. doi:10.1007/BF01053606.
-
[247]
D. Cellai, A. Lawlor, K. A. Dawson, J. P. Gleeson,
Tricritical
point in heterogeneous -core percolation, Phys. Rev. Lett. 107 (2011)
175703.
doi:10.1103/PhysRevLett.107.175703.
URL https://link.aps.org/doi/10.1103/PhysRevLett.107.175703 -
[248]
G. J. Baxter, S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Heterogeneous
-core versus bootstrap percolation on complex networks, Phys. Rev. E 83
(2011) 051134.
doi:10.1103/PhysRevE.83.051134.
URL https://link.aps.org/doi/10.1103/PhysRevE.83.051134 -
[249]
D. Cellai, A. Lawlor, K. A. Dawson, J. P. Gleeson,
Critical phenomena
in heterogeneous -core percolation, Phys. Rev. E 87 (2013) 022134.
doi:10.1103/PhysRevE.87.022134.
URL https://link.aps.org/doi/10.1103/PhysRevE.87.022134 -
[250]
H. Chae, S.-H. Yook, Y. Kim,
Complete set of
types of phase transition in generalized heterogeneous -core percolation,
Phys. Rev. E 89 (2014) 052134.
doi:10.1103/PhysRevE.89.052134.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.052134 -
[251]
M. Sellitto, D. De Martino, F. Caccioli, J. J. Arenzon,
Dynamic
facilitation picture of a higher-order glass singularity, Phys. Rev. Lett.
105 (2010) 265704.
doi:10.1103/PhysRevLett.105.265704.
URL https://link.aps.org/doi/10.1103/PhysRevLett.105.265704 - [252] D. Cellai, J. P. Gleeson, Singularities in ternary mixtures of k-core percolation, in: G. Ghoshal, J. Poncela-Casasnovas, R. Tolksdorf (Eds.), Complex Networks IV, Springer Berlin Heidelberg, Berlin, Heidelberg, 2013, pp. 165–172.
-
[253]
J. P. Gleeson, D. J. Cahalane,
Seed size strongly
affects cascades on random networks, Phys. Rev. E 75 (2007) 056103.
doi:10.1103/PhysRevE.75.056103.
URL https://link.aps.org/doi/10.1103/PhysRevE.75.056103 - [254] D. Centola, V. M. Eguíluz, M. W. Macy, Cascade dynamics of complex propagation, Physica A 374 (2007) 449–456. doi:10.1016/j.physa.2006.06.018.
-
[255]
A. Galstyan, P. Cohen,
Cascading dynamics
in modular networks, Phys. Rev. E 75 (2007) 036109.
doi:10.1103/PhysRevE.75.036109.
URL https://link.aps.org/doi/10.1103/PhysRevE.75.036109 -
[256]
J. P. Gleeson,
Cascades on
correlated and modular random networks, Phys. Rev. E 77 (2008) 046117.
doi:10.1103/PhysRevE.77.046117.
URL https://link.aps.org/doi/10.1103/PhysRevE.77.046117 -
[257]
D. E. Whitney,
Dynamic theory of
cascades on finite clustered random networks with a threshold rule, Phys.
Rev. E 82 (2010) 066110.
doi:10.1103/PhysRevE.82.066110.
URL https://link.aps.org/doi/10.1103/PhysRevE.82.066110 -
[258]
A. Hackett, S. Melnik, J. P. Gleeson,
Cascades on a
class of clustered random networks, Phys. Rev. E 83 (2011) 056107.
doi:10.1103/PhysRevE.83.056107.
URL https://link.aps.org/doi/10.1103/PhysRevE.83.056107 -
[259]
A. Hackett, J. P. Gleeson,
Cascades on
clique-based graphs, Phys. Rev. E 87 (2013) 062801.
doi:10.1103/PhysRevE.87.062801.
URL https://link.aps.org/doi/10.1103/PhysRevE.87.062801 -
[260]
Y. Shang, Impact of
self-healing capability on network robustness, Phys. Rev. E 91 (2015)
042804.
doi:10.1103/PhysRevE.91.042804.
URL https://link.aps.org/doi/10.1103/PhysRevE.91.042804 -
[261]
C. D. Brummitt, K.-M. Lee, K.-I. Goh,
Multiplexity-facilitated
cascades in networks, Phys. Rev. E 85 (2012) 045102.
doi:10.1103/PhysRevE.85.045102.
URL https://link.aps.org/doi/10.1103/PhysRevE.85.045102 -
[262]
A. E. Motter, Y.-C. Lai,
Cascade-based
attacks on complex networks, Phys. Rev. E 66 (2002) 065102.
doi:10.1103/PhysRevE.66.065102.
URL https://link.aps.org/doi/10.1103/PhysRevE.66.065102 -
[263]
J. Adler,
Bootstrap
percolation, Physica A 171 (1991) 453 – 470.
doi:https://doi.org/10.1016/0378-4371(91)90295-N.
URL http://www.sciencedirect.com/science/article/pii/037843719190295N -
[264]
M. A. Di Muro, L. D. Valdez, H. E. Stanley, S. V. Buldyrev, L. A. Braunstein,
Insights into
bootstrap percolation: Its equivalence with k-core percolation and the giant
component, Phys. Rev. E 99 (2019) 022311.
doi:10.1103/PhysRevE.99.022311.
URL https://link.aps.org/doi/10.1103/PhysRevE.99.022311 -
[265]
M. A. Di Muro, S. V. Buldyrev, L. A. Braunstein,
Reversible
bootstrap percolation: Fake news and fact checking, Phys. Rev. E 101 (2020)
042307.
doi:10.1103/PhysRevE.101.042307.
URL https://link.aps.org/doi/10.1103/PhysRevE.101.042307 - [266] R. Cerf, E. N. Cirillo, Finite size scaling in three-dimensional bootstrap percolation, Ann. Probab. 27 (1999) 1837–1850. doi:10.1214/aop/1022874817.
- [267] A. E. Holroyd, Sharp metastability threshold for two-dimensional bootstrap percolation, Probab. Theory Rel. 125 (2003) 195–224.
- [268] A. Holroyd, et al., The metastability threshold for modified bootstrap percolation in dimensions, Electron. J. Probab. 11 (2006) 418–433.
- [269] J. Balogh, B. Bollobás, Bootstrap percolation on the hypercube, Probab. Theory Rel. 134 (2006) 624–648.
- [270] J. Balogh, Y. Peres, G. Pete, Bootstrap percolation on infinite trees and non-amenable groups, Comb. Probab. Comput. 15 (2006) 715–730. doi:10.1017/S0963548306007619.
-
[271]
J. Balogh, B. G. Pittel,
Bootstrap
percolation on the random regular graph, Random Struct. Alg. 30 (2007)
257–286.
doi:10.1002/rsa.20158.
URL https://onlinelibrary.wiley.com/doi/abs/10.1002/rsa.20158 - [272] L. R. Fontes, R. H. Schonmann, Bootstrap percolation on homogeneous trees has 2 phase transitions, J. Stat. Phys. 132 (2008) 839–861.
-
[273]
C. Castellano, S. Fortunato, V. Loreto,
Statistical physics
of social dynamics, Rev. Mod. Phys. 81 (2009) 591–646.
doi:10.1103/RevModPhys.81.591.
URL https://link.aps.org/doi/10.1103/RevModPhys.81.591 -
[274]
Y.-Y. Liu, A.-L. Barabási,
Control
principles of complex systems, Rev. Mod. Phys. 88 (2016) 035006.
doi:10.1103/RevModPhys.88.035006.
URL https://link.aps.org/doi/10.1103/RevModPhys.88.035006 - [275] M. Bauer, O. Golinelli, Core percolation in random graphs: a critical phenomena analysis, Eur. Phys. J. B 24 (2001) 339–352. doi:10.1007/s10051-001-8683-4.
- [276] M. Catanzaro, R. Pastor-Satorras, Analytic solution of a static scale-free network model, Eur. Phys. J. B 44 (2005) 241–248. doi:10.1140/epjb/e2005-00120-9.
-
[277]
N. Azimi-Tafreshi, S. Osat, S. N. Dorogovtsev,
Generalization of
core percolation on complex networks, Phys. Rev. E 99 (2019) 022312.
doi:10.1103/PhysRevE.99.022312.
URL https://link.aps.org/doi/10.1103/PhysRevE.99.022312 - [278] D. B. West, Introduction to Graph Theory, Upper Saddle River, NJ: Prentice hall, 1996.
-
[279]
J. Holm, K. de Lichtenberg, M. Thorup,
Poly-logarithmic deterministic
fully-dynamic algorithms for connectivity, minimum spanning tree, 2-edge, and
biconnectivity, J. ACM 48 (2001) 723–760.
doi:10.1145/502090.502095.
URL https://doi.org/10.1145/502090.502095 - [280] F. Morone, H. A. Makse, Influence maximization in complex networks through optimal percolation, Nature 524 (2015) 65–68. doi:10.1038/nature14604.
-
[281]
I. Tishby, O. Biham, R. Kühn, E. Katzav,
Statistical
analysis of articulation points in configuration model networks, Phys. Rev.
E 98 (2018) 062301.
doi:10.1103/PhysRevE.98.062301.
URL https://link.aps.org/doi/10.1103/PhysRevE.98.062301 -
[282]
A.-K. Wu, L. Tian, Y.-Y. Liu,
Bridges in complex
networks, Phys. Rev. E 97 (2018) 012307.
doi:10.1103/PhysRevE.97.012307.
URL https://link.aps.org/doi/10.1103/PhysRevE.97.012307 -
[283]
S. M. Krause, M. M. Danziger, V. Zlatić,
Hidden connectivity
in networks with vulnerable classes of nodes, Phys. Rev. X 6 (2016) 041022.
doi:10.1103/PhysRevX.6.041022.
URL https://link.aps.org/doi/10.1103/PhysRevX.6.041022 - [284] R. Molontay, K. Varga, On the complexity of color-avoiding site and bond percolation, in: B. Catania, R. Královič, J. Nawrocki, G. Pighizzini (Eds.), SOFSEM 2019: Theory and Practice of Computer Science, Springer International Publishing, Cham, 2019, pp. 354–367. doi:https://doi.org/10.1007/978-3-030-10801-4_28.
- [285] I. Kryven, Bond percolation in coloured and multiplex networks, Nat. Commun. 10 (2019) 404. doi:10.1038/s41467-018-08009-9.
-
[286]
Y. S. Cho, J. S. Lee, H. J. Herrmann, B. Kahng,
Hybrid
percolation transition in cluster merging processes: Continuously varying
exponents, Phys. Rev. Lett. 116 (2016) 025701.
doi:10.1103/PhysRevLett.116.025701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.116.025701 -
[287]
D. Lee, Y. S. Cho, B. Kahng,
Diverse types
of percolation transitions, J. Stat. Mech. 2016 (2016) 124002.
doi:10.1088/1742-5468/2016/12/124002.
URL https://doi.org/10.1088%2F1742-5468%2F2016%2F12%2F124002 - [288] D. Lee, W. Choi, J. Kertész, B. Kahng, Universal mechanism for hybrid percolation transitions, Sci. Rep. 7 (2017) 5723. doi:10.1038/s41598-017-06182-3.
- [289] D. Lee, B. Kahng, Y. S. Cho, K.-I. Goh, D.-S. Lee, Recent advances of percolation theory in complex networks, J. Korean Phys. Soc. 73 (2018) 152–164. doi:10.3938/jkps.73.152.
- [290] J. Park, S. Yi, K. Choi, D. Lee, B. Kahng, Interevent time distribution, burst, and hybrid percolation transition, Chaos 29 (2019) 091102. doi:10.1063/1.5121775.
- [291] J. Park, S. Yi, B. Kahng, Hysteresis and criticality in hybrid percolation transitions, Chaos 30 (2020) 051102. doi:10.1063/5.0008189.
-
[292]
G. J. Baxter, S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Avalanche
collapse of interdependent networks, Phys. Rev. Lett. 109 (2012) 248701.
doi:10.1103/PhysRevLett.109.248701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.109.248701 -
[293]
P. Grassberger,
Percolation
transitions in the survival of interdependent agents on multiplex networks,
catastrophic cascades, and solid-on-solid surface growth, Phys. Rev. E 91
(2015) 062806.
doi:10.1103/PhysRevE.91.062806.
URL https://link.aps.org/doi/10.1103/PhysRevE.91.062806 -
[294]
S.-W. Son, P. Grassberger, M. Paczuski,
Percolation
transitions are not always sharpened by making networks interdependent,
Phys. Rev. Lett. 107 (2011) 195702.
doi:10.1103/PhysRevLett.107.195702.
URL https://link.aps.org/doi/10.1103/PhysRevLett.107.195702 -
[295]
S.-W. Son, G. Bizhani, C. Christensen, P. Grassberger, M. Paczuski,
Percolation theory on
interdependent networks based on epidemic spreading, Europhys. Lett. 97
(2012) 16006.
doi:10.1209/0295-5075/97/16006.
URL https://doi.org/10.1209%2F0295-5075%2F97%2F16006 -
[296]
M. Li, B.-H. Wang,
Percolation on
networks with dependence links, Chin. Phys. B 23 (2014) 076402.
doi:10.1088/1674-1056/23/7/076402.
URL https://doi.org/10.1088%2F1674-1056%2F23%2F7%2F076402 - [297] L. Feng, C. P. Monterola, Y. Hu, The simplified self-consistent probabilities method for percolation and its application to interdependent networks, New J. Phys. 17 (6) (2015) 063025. doi:10.1088/1367-2630/17/6/063025.
-
[298]
D. Zhou, A. Bashan, R. Cohen, Y. Berezin, N. Shnerb, S. Havlin,
Simultaneous
first- and second-order percolation transitions in interdependent networks,
Phys. Rev. E 90 (2014) 012803.
doi:10.1103/PhysRevE.90.012803.
URL https://link.aps.org/doi/10.1103/PhysRevE.90.012803 - [299] A. Bashan, Y. Berezin, S. V. Buldyrev, S. Havlin, The extreme vulnerability of interdependent spatially embedded networks, Nat. Phys. 9 (2013) 667–672. doi:10.1038/nphys2727.
-
[300]
W. Li, A. Bashan, S. V. Buldyrev, H. E. Stanley, S. Havlin,
Cascading
failures in interdependent lattice networks: The critical role of the length
of dependency links, Phys. Rev. Lett. 108 (2012) 228702.
doi:10.1103/PhysRevLett.108.228702.
URL https://link.aps.org/doi/10.1103/PhysRevLett.108.228702 -
[301]
S. Lowinger, G. A. Cwilich, S. V. Buldyrev,
Interdependent
lattice networks in high dimensions, Phys. Rev. E 94 (2016) 052306.
doi:10.1103/PhysRevE.94.052306.
URL https://link.aps.org/doi/10.1103/PhysRevE.94.052306 -
[302]
A. Hackett, D. Cellai, S. Gómez, A. Arenas, J. P. Gleeson,
Bond percolation on
multiplex networks, Phys. Rev. X 6 (2016) 021002.
doi:10.1103/PhysRevX.6.021002.
URL https://link.aps.org/doi/10.1103/PhysRevX.6.021002 - [303] T. Nogawa, T. Hasegawa, Monte carlo simulation study of the two-stage percolation transition in enhanced binary trees, J. Phys. A: Math. Theor. 42 (2009) 145001. doi:10.1088/1751-8113/42/14/145001.
-
[304]
G. Bianconi, S. N. Dorogovtsev,
Multiple
percolation transitions in a configuration model of a network of networks,
Phys. Rev. E 89 (2014) 062814.
doi:10.1103/PhysRevE.89.062814.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.062814 - [305] C. Wu, S. Ji, R. Zhang, L. Chen, J. Chen, X. Li, Y. Hu, Multiple hybrid phase transition: Bootstrap percolation on complex networks with communities, Europhys. Lett. 107 (2014) 48001. doi:10.1209/0295-5075/107/48001.
- [306] R.-R. Liu, D. A. Eisenberg, T. P. Seager, Y.-C. Lai, The “weak” interdependence of infrastructure systems produces mixed percolation transitions in multilayer networks, Sci. Rep. 8 (2018) 2111. doi:10.1038/s41598-018-20019-7.
- [307] I. Kryven, G. Bianconi, Enhancing the robustness of a multiplex network leads to multiple discontinuous percolation transitions, Phys. Rev. E 100 (2019) 020301. doi:10.1103/physreve.100.020301.
- [308] S. M. Oh, S.-W. Son, B. Kahng, Discontinuous percolation transitions in growing networks, J. Stat. Mech. 2019 (2019) 083502. doi:10.1088/1742-5468/ab3110.
-
[309]
N. Azimi-Tafreshi, J. Gómez-Gardeñes, S. N. Dorogovtsev,
-core
percolation on multiplex networks, Phys. Rev. E 90 (2014) 032816.
doi:10.1103/PhysRevE.90.032816.
URL https://link.aps.org/doi/10.1103/PhysRevE.90.032816 -
[310]
G. J. Baxter, S. N. Dorogovtsev, J. F. F. Mendes, D. Cellai,
Weak percolation
on multiplex networks, Phys. Rev. E 89 (2014) 042801.
doi:10.1103/PhysRevE.89.042801.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.042801 -
[311]
Z. Wang, D. Zhou, Y. Hu,
Group percolation
in interdependent networks, Phys. Rev. E 97 (2018) 032306.
doi:10.1103/PhysRevE.97.032306.
URL https://link.aps.org/doi/10.1103/PhysRevE.97.032306 -
[312]
C. M. Schneider, N. A. M. Araújo, H. J. Herrmann,
Algorithm to
determine the percolation largest component in interconnected networks,
Phys. Rev. E 87 (2013) 043302.
doi:10.1103/PhysRevE.87.043302.
URL https://link.aps.org/doi/10.1103/PhysRevE.87.043302 -
[313]
S. Hwang, S. Choi, D. Lee, B. Kahng,
Efficient
algorithm to compute mutually connected components in interdependent
networks, Phys. Rev. E 91 (2015) 022814.
doi:10.1103/PhysRevE.91.022814.
URL https://link.aps.org/doi/10.1103/PhysRevE.91.022814 -
[314]
D. Lee, S. Choi, M. Stippinger, J. Kertész, B. Kahng,
Hybrid phase
transition into an absorbing state: Percolation and avalanches, Phys. Rev. E
93 (2016) 042109.
doi:10.1103/PhysRevE.93.042109.
URL https://link.aps.org/doi/10.1103/PhysRevE.93.042109 -
[315]
M. Stippinger, J. Kertész,
Universality and
scaling laws in the cascading failure model with healing, Phys. Rev. E 98
(2018) 042303.
doi:10.1103/PhysRevE.98.042303.
URL https://link.aps.org/doi/10.1103/PhysRevE.98.042303 -
[316]
P. L. Leath, Cluster
size and boundary distribution near percolation threshold, Phys. Rev. B 14
(1976) 5046–5055.
doi:10.1103/PhysRevB.14.5046.
URL https://link.aps.org/doi/10.1103/PhysRevB.14.5046 - [317] M. Kivelä, A. Arenas, M. Barthelemy, J. P. Gleeson, Y. Moreno, M. A. Porter, Multilayer networks, J. Complex Networks 2 (2014) 203–271.
- [318] K.-M. Lee, B. Min, K.-I. Goh, Towards real-world complexity: an introduction to multiplex networks, Eur. Phys. J. B 88 (feb 2015). doi:10.1140/epjb/e2015-50742-1.
-
[319]
E. A. Leicht, R. M. D’Souza, Percolation
on interacting networks, arXiv preprint arXiv:0907.0894 (2009).
URL https://arxiv.org/abs/0907.0894 -
[320]
J. Nagler, T. Tiessen, H. W. Gutch,
Continuous
percolation with discontinuities, Phys. Rev. X 2 (2012) 031009.
doi:10.1103/PhysRevX.2.031009.
URL https://link.aps.org/doi/10.1103/PhysRevX.2.031009 - [321] J. Nagler, A. Levina, M. Timme, Impact of single links in competitive percolation, Nat. Phys. 7 (2011) 265–270. doi:10.1038/nphys1860.
-
[322]
O. Riordan, L. Warnke,
Achlioptas
processes are not always self-averaging, Phys. Rev. E 86 (2012) 011129.
doi:10.1103/PhysRevE.86.011129.
URL https://link.aps.org/doi/10.1103/PhysRevE.86.011129 -
[323]
T. Bohman, A. Frieze, N. C. Wormald,
Avoidance of
a giant component in half the edge set of a random graph, Random Struct.
Alg. 25 (2004) 432–449.
doi:10.1002/rsa.20038.
URL https://onlinelibrary.wiley.com/doi/abs/10.1002/rsa.20038 - [324] O. Riordan, L. Warnke, Explosive percolation is continuous, Science 333 (2011) 322–324. doi:10.1126/science.1206241.
-
[325]
W. Chen, R. M. D’Souza,
Explosive
percolation with multiple giant components, Phys. Rev. Lett. 106 (2011)
115701.
doi:10.1103/PhysRevLett.106.115701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.106.115701 -
[326]
W. Chen, Z. Zheng, R. M. D’Souza,
Deriving an
underlying mechanism for discontinuous percolation, Europhys. Lett. 100
(2012) 66006.
doi:10.1209/0295-5075/100/66006.
URL https://doi.org/10.1209%2F0295-5075%2F100%2F66006 -
[327]
K. J. Schrenk, A. Felder, S. Deflorin, N. A. M. Araújo, R. M. D’Souza, H. J.
Herrmann,
Bohman-frieze-wormald
model on the lattice, yielding a discontinuous percolation transition, Phys.
Rev. E 85 (2012) 031103.
doi:10.1103/PhysRevE.85.031103.
URL https://link.aps.org/doi/10.1103/PhysRevE.85.031103 -
[328]
Y. Zhang, W. Wei, B. Guo, R. Zhang, Z. Zheng,
Formation
mechanism and size features of multiple giant clusters in generic percolation
processes, Phys. Rev. E 86 (2012) 051103.
doi:10.1103/PhysRevE.86.051103.
URL https://link.aps.org/doi/10.1103/PhysRevE.86.051103 -
[329]
W. Chen, X. Cheng, Z. Zheng, N. N. Chung, R. M. D’Souza, J. Nagler,
Unstable
supercritical discontinuous percolation transitions, Phys. Rev. E 88 (2013)
042152.
doi:10.1103/PhysRevE.88.042152.
URL https://link.aps.org/doi/10.1103/PhysRevE.88.042152 -
[330]
W. Chen, M. Schröder, R. M. D’Souza, D. Sornette, J. Nagler,
Microtransition
cascades to percolation, Phys. Rev. Lett. 112 (2014) 155701.
doi:10.1103/PhysRevLett.112.155701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.112.155701 -
[331]
Y. S. Cho, B. Kahng,
Suppression
effect on explosive percolation, Phys. Rev. Lett. 107 (2011) 275703.
doi:10.1103/PhysRevLett.107.275703.
URL https://link.aps.org/doi/10.1103/PhysRevLett.107.275703 -
[332]
J. Li, M. Östling,
Corrected
finite-size scaling in percolation, Phys. Rev. E 86 (2012) 040105.
doi:10.1103/PhysRevE.86.040105.
URL https://link.aps.org/doi/10.1103/PhysRevE.86.040105 -
[333]
S. D. Yi, W. S. Jo, B. J. Kim, S.-W. Son,
Percolation
properties of growing networks under an achlioptas process, Europhys. Lett.
103 (2013) 26004.
doi:10.1209/0295-5075/103/26004.
URL https://doi.org/10.1209%2F0295-5075%2F103%2F26004 -
[334]
R. A. da Costa, S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Critical exponents
of the explosive percolation transition, Phys. Rev. E 89 (2014) 042148.
doi:10.1103/PhysRevE.89.042148.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.042148 -
[335]
R. A. da Costa, S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Solution of the
explosive percolation quest: Scaling functions and critical exponents, Phys.
Rev. E 90 (2014) 022145.
doi:10.1103/PhysRevE.90.022145.
URL https://link.aps.org/doi/10.1103/PhysRevE.90.022145 -
[336]
R. A. da Costa, S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Solution of the
explosive percolation quest. ii. infinite-order transition produced by the
initial distributions of clusters, Phys. Rev. E 91 (2015) 032140.
doi:10.1103/PhysRevE.91.032140.
URL https://link.aps.org/doi/10.1103/PhysRevE.91.032140 -
[337]
R. A. da Costa, S. N. Dorogovtsev, A. V. Goltsev, J. F. F. Mendes,
Inverting the
achlioptas rule for explosive percolation, Phys. Rev. E 91 (2015) 042130.
doi:10.1103/PhysRevE.91.042130.
URL https://link.aps.org/doi/10.1103/PhysRevE.91.042130 -
[338]
Y. S. Cho, B. Kahng,
Discontinuous
percolation transitions in real physical systems, Phys. Rev. E 84 (2011)
050102.
doi:10.1103/PhysRevE.84.050102.
URL https://link.aps.org/doi/10.1103/PhysRevE.84.050102 -
[339]
Y. S. Cho, Y. W. Kim, B. Kahng,
Discontinuous
percolation in diffusion-limited cluster aggregation, J. Stat. Mech. 2012
(2012) P10004.
doi:10.1088/1742-5468/2012/10/p10004.
URL https://doi.org/10.1088%2F1742-5468%2F2012%2F10%2Fp10004 -
[340]
R. M. Ziff, Getting
the jump on explosive percolation, Science 339 (2013) 1159–1160.
doi:10.1126/science.1235032.
URL https://science.sciencemag.org/content/339/6124/1159 -
[341]
Y. S. Cho, S. Hwang, H. J. Herrmann, B. Kahng,
Avoiding a
spanning cluster in percolation models, Science 339 (2013) 1185–1187.
doi:10.1126/science.1230813.
URL https://science.sciencemag.org/content/339/6124/1185 -
[342]
N. A. M. Araújo, J. S. Andrade, R. M. Ziff, H. J. Herrmann,
Tricritical
point in explosive percolation, Phys. Rev. Lett. 106 (2011) 095703.
doi:10.1103/PhysRevLett.106.095703.
URL https://link.aps.org/doi/10.1103/PhysRevLett.106.095703 -
[343]
L. Cao, J. M. Schwarz,
Correlated
percolation and tricriticality, Phys. Rev. E 86 (2012) 061131.
doi:10.1103/PhysRevE.86.061131.
URL https://link.aps.org/doi/10.1103/PhysRevE.86.061131 -
[344]
J. Fan, M. Liu, L. Li, X. Chen,
Continuous
percolation phase transitions of random networks under a generalized
achlioptas process, Phys. Rev. E 85 (2012) 061110.
doi:10.1103/PhysRevE.85.061110.
URL https://link.aps.org/doi/10.1103/PhysRevE.85.061110 - [345] R. M. D’Souza, J. Nagler, Anomalous critical and supercritical phenomena in explosive percolation, Nat. Phys. 11 (2015) 531–538. doi:10.1038/nphys3378.
- [346] A. Waagen, R. M. D’souza, Given enough choice, simple local rules percolate discontinuously, Eur. Phys. J. B 87 (2014) 304. doi:10.1140/epjb/e2014-50278-x.
-
[347]
P. Grassberger, C. Christensen, G. Bizhani, S.-W. Son, M. Paczuski,
Explosive
percolation is continuous, but with unusual finite size behavior, Phys. Rev.
Lett. 106 (2011) 225701.
doi:10.1103/PhysRevLett.106.225701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.106.225701 -
[348]
N. Bastas, K. Kosmidis, P. Argyrakis,
Explosive site
percolation and finite-size hysteresis, Phys. Rev. E 84 (2011) 066112.
doi:10.1103/PhysRevE.84.066112.
URL https://link.aps.org/doi/10.1103/PhysRevE.84.066112 -
[349]
Y. S. Cho, S.-W. Kim, J. D. Noh, B. Kahng, D. Kim,
Finite-size
scaling theory for explosive percolation transitions, Phys. Rev. E 82 (2010)
042102.
doi:10.1103/PhysRevE.82.042102.
URL https://link.aps.org/doi/10.1103/PhysRevE.82.042102 -
[350]
F. Radicchi, S. Fortunato,
Explosive
percolation: A numerical analysis, Phys. Rev. E 81 (2010) 036110.
doi:10.1103/PhysRevE.81.036110.
URL https://link.aps.org/doi/10.1103/PhysRevE.81.036110 -
[351]
H. K. Lee, B. J. Kim, H. Park,
Continuity of the
explosive percolation transition, Phys. Rev. E 84 (2011) 020101.
doi:10.1103/PhysRevE.84.020101.
URL https://link.aps.org/doi/10.1103/PhysRevE.84.020101 - [352] L. Tian, D.-N. Shi, The nature of explosive percolation phase transition, Phys. Lett. A 376 (2012) 286–289. doi:10.1016/j.physleta.2011.11.039.
- [353] M. E. J. Newman, The structure and function of complex networks, SIAM Rev. 45 (2003) 167–256. doi:10.1137/s003614450342480.
- [354] A.-L. Barabási, R. Albert, H. Jeong, Mean-field theory for scale-free random networks, Physica A 272 (1999) 173–187. doi:10.1016/s0378-4371(99)00291-5.
-
[355]
S. N. Dorogovtsev, J. F. F. Mendes, A. N. Samukhin,
Anomalous
percolation properties of growing networks, Phys. Rev. E 64 (2001) 066110.
doi:10.1103/PhysRevE.64.066110.
URL https://link.aps.org/doi/10.1103/PhysRevE.64.066110 - [356] I. S. Weaver, Preferential attachment in randomly grown networks, Physica A 439 (2015) 85–92. doi:10.1016/j.physa.2015.06.019.
-
[357]
J. Kim, P. L. Krapivsky, B. Kahng, S. Redner,
Infinite-order
percolation and giant fluctuations in a protein interaction network, Phys.
Rev. E 66 (2002) 055101.
doi:10.1103/PhysRevE.66.055101.
URL https://link.aps.org/doi/10.1103/PhysRevE.66.055101 - [358] B. Bollobás, S. Janson, O. Riordan, The phase transition in the uniformly grown random graph has infinite order, Random Struct. Alg. 26 (2004) 1–36. doi:10.1002/rsa.20041.
- [359] P. Krapivsky, B. Derrida, Universal properties of growing networks, Physica A 340 (2004) 714–724. doi:10.1016/j.physa.2004.05.020.
- [360] V. L. Berezinskii, Destruction of long-range order in one-dimensional and two-dimensional systems having a continuous symmetry group I. classical systems, Sov. Phys.–JETP 32 (1971) 493.
- [361] J. M. Kosterlitz, D. J. Thouless, Long range order and metastability in two dimensional solids and superfluids. (application of dislocation theory), J. Phys. C: Solid State Phys. 5 (1972) L124–L126. doi:10.1088/0022-3719/5/11/002.
-
[362]
H. Hu, Y. Deng, H. W. J. Blöte,
Berezinskii-kosterlitz-thouless-like
percolation transitions in the two-dimensional model, Phys.
Rev. E 83 (2011) 011124.
doi:10.1103/PhysRevE.83.011124.
URL https://link.aps.org/doi/10.1103/PhysRevE.83.011124 - [363] T. Hasegawa, T. Nogawa, K. Nemoto, Profile and scaling of the fractal exponent of percolations in complex networks, Europhys. Lett. 104 (2013) 16006. doi:10.1209/0295-5075/104/16006.
- [364] F. Wu, P. P. Kärenlampi, Phase transition in a growing network, J. Complex Networks 6 (2017) 788–799. doi:10.1093/comnet/cnx058.
- [365] S. N. Dorogovtsev, Renormalization group for evolving networks, Phys. Rev. E 67 (2003) 045102. doi:10.1103/PhysRevE.67.045102.
-
[366]
S. N. Dorogovtsev, J. F. F. Mendes, A. N. Samukhin,
Structure of
growing networks with preferential linking, Phys. Rev. Lett. 85 (2000)
4633–4636.
doi:10.1103/PhysRevLett.85.4633.
URL https://link.aps.org/doi/10.1103/PhysRevLett.85.4633 - [367] A. Zen, A. Kabakçıoğlu, A. L. Stella, Percolation transition in a dynamically clustered network, Phys. Rev. E 76 (2007) 026110. doi:10.1103/PhysRevE.76.026110.
-
[368]
V. S. Vijayaraghavan, P.-A. Noël, A. Waagen, R. M. D’Souza,
Growth dominates
choice in network percolation, Phys. Rev. E 88 (2013) 032141.
doi:10.1103/PhysRevE.88.032141.
URL https://link.aps.org/doi/10.1103/PhysRevE.88.032141 -
[369]
S. M. Oh, S.-W. Son, B. Kahng,
Explosive
percolation transitions in growing networks, Phys. Rev. E 93 (2016) 032316.
doi:10.1103/PhysRevE.93.032316.
URL https://link.aps.org/doi/10.1103/PhysRevE.93.032316 -
[370]
S. M. Oh, S.-W. Son, B. Kahng,
Suppression effect
on the berezinskii-kosterlitz-thouless transition in growing networks, Phys.
Rev. E 98 (2018) 060301.
doi:10.1103/PhysRevE.98.060301.
URL https://link.aps.org/doi/10.1103/PhysRevE.98.060301 -
[371]
A. N. Berker, M. Hinczewski, R. R. Netz,
Critical
percolation phase and thermal berezinskii-kosterlitz-thouless transition in a
scale-free network with short-range and long-range random bonds, Phys. Rev.
E 80 (2009) 041118.
doi:10.1103/PhysRevE.80.041118.
URL https://link.aps.org/doi/10.1103/PhysRevE.80.041118 - [372] S. Boettcher, V. Singh, R. M. Ziff, Ordinary percolation with discontinuous transitions, Nat. Commun. 3 (jan 2012). doi:10.1038/ncomms1774.
- [373] D. Lancaster, Cluster growth in two growing network models, J. Phys. A: Math. Gen. 35 (2002) 1179–1194. doi:10.1088/0305-4470/35/5/305.
- [374] L. Kullmann, J. Kertész, Preferential growth: Exact solution of the time-dependent distributions, Phys. Rev. E 63 (2001) 051112. doi:10.1103/physreve.63.051112.
-
[375]
P. L. Krapivsky, S. Redner,
Organization of
growing random networks, Phys. Rev. E 63 (2001) 066123.
doi:10.1103/PhysRevE.63.066123.
URL https://link.aps.org/doi/10.1103/PhysRevE.63.066123 - [376] S. Coulomb, M. Bauer, Asymmetric evolving random networks, Eur. Phys. J. B 35 (2003) 377–389. doi:10.1140/epjb/e2003-00290-4.
-
[377]
T. Hasegawa, K. Nemoto,
Critical phase of
bond percolation on growing networks, Phys. Rev. E 81 (2010) 051105.
doi:10.1103/PhysRevE.81.051105.
URL https://link.aps.org/doi/10.1103/PhysRevE.81.051105 -
[378]
U. Bhat, P. L. Krapivsky, R. Lambiotte, S. Redner,
Densification and
structural transitions in networks that grow by node copying, Phys. Rev. E
94 (2016) 062302.
doi:10.1103/PhysRevE.94.062302.
URL https://link.aps.org/doi/10.1103/PhysRevE.94.062302 -
[379]
R. Lambiotte, P. L. Krapivsky, U. Bhat, S. Redner,
Structural
transitions in densifying networks, Phys. Rev. Lett. 117 (2016) 218301.
doi:10.1103/PhysRevLett.117.218301.
URL https://link.aps.org/doi/10.1103/PhysRevLett.117.218301 - [380] J. Shao, S. V. Buldyrev, R. Cohen, M. Kitsak, S. Havlin, H. E. Stanley, Fractal boundaries of complex networks, Europhys. Lett. 84 (2008) 48004. doi:10.1209/0295-5075/84/48004.
-
[381]
T. Kalisky, R. Cohen, O. Mokryn, D. Dolev, Y. Shavitt, S. Havlin,
Tomography of
scale-free networks and shortest path trees, Phys. Rev. E 74 (2006) 066108.
doi:10.1103/PhysRevE.74.066108.
URL https://link.aps.org/doi/10.1103/PhysRevE.74.066108 -
[382]
M. E. J. Newman,
Scientific
collaboration networks. i. network construction and fundamental results,
Phys. Rev. E 64 (2001) 016131.
doi:10.1103/PhysRevE.64.016131.
URL https://link.aps.org/doi/10.1103/PhysRevE.64.016131 -
[383]
M. E. J. Newman,
Scientific
collaboration networks. ii. shortest paths, weighted networks, and
centrality, Phys. Rev. E 64 (2001) 016132.
doi:10.1103/PhysRevE.64.016132.
URL https://link.aps.org/doi/10.1103/PhysRevE.64.016132 -
[384]
R. Cohen, S. Havlin,
Scale-free
networks are ultrasmall, Phys. Rev. Lett. 90 (2003) 058701.
doi:10.1103/PhysRevLett.90.058701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.90.058701 -
[385]
S. Dorogovtsev, J. Mendes, A. Samukhin,
Metric
structure of random networks, Nucl. Phys. B 653 (2003) 307 – 338.
doi:https://doi.org/10.1016/S0550-3213(02)01119-7.
URL http://www.sciencedirect.com/science/article/pii/S0550321302011197 -
[386]
J. Shao, S. V. Buldyrev, L. A. Braunstein, S. Havlin, H. E. Stanley,
Structure of
shells in complex networks, Phys. Rev. E 80 (2009) 036105.
doi:10.1103/PhysRevE.80.036105.
URL https://link.aps.org/doi/10.1103/PhysRevE.80.036105 -
[387]
X. Yuan, S. Shao, H. E. Stanley, S. Havlin,
How breadth of
degree distribution influences network robustness: Comparing localized and
random attacks, Phys. Rev. E 92 (2015) 032122.
doi:10.1103/PhysRevE.92.032122.
URL https://link.aps.org/doi/10.1103/PhysRevE.92.032122 - [388] D.-S. Lee, H. Rieger, Maximum flow and topological structure of complex networks, Europhys. Lett. 73 (2006) 471–477. doi:10.1209/epl/i2005-10407-5.
- [389] G. Dong, J. Fan, L. M. Shekhtman, S. Shai, R. Du, L. Tian, X. Chen, H. E. Stanley, S. Havlin, Resilience of networks with community structure behaves as if under an external field, Proc. Natl. Acad. Sci. U.S.A. 115 (2018) 6911–6915. doi:10.1073/pnas.1801588115.
-
[390]
M. E. J. Newman,
Mixing patterns in
networks, Phys. Rev. E 67 (2003) 026126.
doi:10.1103/PhysRevE.67.026126.
URL https://link.aps.org/doi/10.1103/PhysRevE.67.026126 -
[391]
L. K. Gallos, R. Cohen, P. Argyrakis, A. Bunde, S. Havlin,
Stability and
topology of scale-free networks under attack and defense strategies, Phys.
Rev. Lett. 94 (2005) 188701.
doi:10.1103/PhysRevLett.94.188701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.94.188701 -
[392]
H. Hooyberghs, B. Van Schaeybroeck, A. A. Moreira, J. S. Andrade, H. J.
Herrmann, J. O. Indekeu,
Biased percolation
on scale-free networks, Phys. Rev. E 81 (2010) 011102.
doi:10.1103/PhysRevE.81.011102.
URL https://link.aps.org/doi/10.1103/PhysRevE.81.011102 -
[393]
T. Hasegawa, K. Nemoto,
Hierarchical
scale-free network is fragile against random failure, Phys. Rev. E 88 (2013)
062807.
doi:10.1103/PhysRevE.88.062807.
URL https://link.aps.org/doi/10.1103/PhysRevE.88.062807 -
[394]
G. Paul, R. Cohen, S. Sreenivasan, S. Havlin, H. E. Stanley,
Graph
partitioning induced phase transitions, Phys. Rev. Lett. 99 (2007) 115701.
doi:10.1103/PhysRevLett.99.115701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.99.115701 -
[395]
A. X. C. N. Valente, A. Sarkar, H. A. Stone,
Two-peak and
three-peak optimal complex networks, Phys. Rev. Lett. 92 (2004) 118702.
doi:10.1103/PhysRevLett.92.118702.
URL https://link.aps.org/doi/10.1103/PhysRevLett.92.118702 -
[396]
A. Srivastava, B. Mitra, N. Ganguly, F. Peruani,
Correlations in
complex networks under attack, Phys. Rev. E 86 (2012) 036106.
doi:10.1103/PhysRevE.86.036106.
URL https://link.aps.org/doi/10.1103/PhysRevE.86.036106 -
[397]
T. P. Peixoto, S. Bornholdt,
Evolution of
robust network topologies: Emergence of central backbones, Phys. Rev. Lett.
109 (2012) 118703.
doi:10.1103/PhysRevLett.109.118703.
URL https://link.aps.org/doi/10.1103/PhysRevLett.109.118703 -
[398]
X. Huang, J. Gao, S. V. Buldyrev, S. Havlin, H. E. Stanley,
Robustness of
interdependent networks under targeted attack, Phys. Rev. E 83 (2011)
065101.
doi:10.1103/PhysRevE.83.065101.
URL https://link.aps.org/doi/10.1103/PhysRevE.83.065101 - [399] C. M. Schneider, A. A. Moreira, J. S. Andrade, S. Havlin, H. J. Herrmann, Mitigation of malicious attacks on networks, Proc. Natl. Acad. Sci. U.S.A. 108 (2011) 3838–3841. doi:10.1073/pnas.1009440108.
- [400] H. J. Herrmann, C. M. Schneider, A. A. Moreira, J. S. A. Jr, S. Havlin, Onion-like network topology enhances robustness against malicious attacks, J. Stat. Mech. 2011 (2011) P01027. doi:10.1088/1742-5468/2011/01/p01027.
-
[401]
T. Tanizawa, S. Havlin, H. E. Stanley,
Robustness of
onionlike correlated networks against targeted attacks, Phys. Rev. E 85
(2012) 046109.
doi:10.1103/PhysRevE.85.046109.
URL https://link.aps.org/doi/10.1103/PhysRevE.85.046109 -
[402]
H. K. Lee, P.-S. Shim, J. D. Noh,
Epidemic threshold
of the susceptible-infected-susceptible model on complex networks, Phys.
Rev. E 87 (2013) 062812.
doi:10.1103/PhysRevE.87.062812.
URL https://link.aps.org/doi/10.1103/PhysRevE.87.062812 -
[403]
A. Caligiuri, C. Castellano,
Degree-ordered-percolation on
uncorrelated networks, J. Stat. Mech. 2020 (11) (2020) 113401.
doi:10.1088/1742-5468/abc1da.
URL https://doi.org/10.1088/1742-5468/abc1da - [404] S. Shao, X. Huang, H. E. Stanley, S. Havlin, Percolation of localized attack on complex networks, New J. Phys. 17 (2015) 023049. doi:10.1088/1367-2630/17/2/023049.
- [405] Y. Berezin, A. Bashan, M. M. Danziger, D. Li, S. Havlin, Localized attacks on spatially embedded networks with dependencies, Sci. Rep. 5 (2015) 08943. doi:10.1038/srep08934.
- [406] G. Dong, R. Du, H. Hao, L. Tian, Modified localized attack on complex network, Europhys. Lett. 113 (2016) 28002. doi:10.1209/0295-5075/113/28002.
- [407] D. Vaknin, M. M. Danziger, S. Havlin, Spreading of localized attacks in spatial multiplex networks, New J. Phys. 19 (2017) 073037. doi:10.1088/1367-2630/aa7b09.
- [408] G. Dong, H. Xiao, F. Wang, R. Du, S. Shao, L. Tian, H. E. Stanley, S. Havlin, Localized attack on networks with clustering, New J. Phys. 21 (2019) 013014. doi:10.1088/1367-2630/aaf773.
-
[409]
T. C. McAndrew, C. M. Danforth, J. P. Bagrow,
Robustness of
spatial micronetworks, Phys. Rev. E 91 (2015) 042813.
doi:10.1103/PhysRevE.91.042813.
URL https://link.aps.org/doi/10.1103/PhysRevE.91.042813 -
[410]
N. Almeira, O. V. Billoni, J. I. Perotti,
Scaling of
percolation transitions on erdös-rényi networks under centrality-based
attacks, Phys. Rev. E 101 (2020) 012306.
doi:10.1103/PhysRevE.101.012306.
URL https://link.aps.org/doi/10.1103/PhysRevE.101.012306 -
[411]
G. Bianconi,
Fluctuations in
percolation of sparse complex networks, Phys. Rev. E 96 (2017) 012302.
doi:10.1103/PhysRevE.96.012302.
URL https://link.aps.org/doi/10.1103/PhysRevE.96.012302 -
[412]
F. Coghi, F. Radicchi, G. Bianconi,
Controlling the
uncertain response of real multiplex networks to random damage, Phys. Rev. E
98 (2018) 062317.
doi:10.1103/PhysRevE.98.062317.
URL https://link.aps.org/doi/10.1103/PhysRevE.98.062317 -
[413]
M. Kitsak, A. A. Ganin, D. A. Eisenberg, P. L. Krapivsky, D. Krioukov, D. L.
Alderson, I. Linkov,
Stability of a
giant connected component in a complex network, Phys. Rev. E 97 (2018)
012309.
doi:10.1103/PhysRevE.97.012309.
URL https://link.aps.org/doi/10.1103/PhysRevE.97.012309 -
[414]
G. Bianconi, Rare
events and discontinuous percolation transitions, Phys. Rev. E 97 (2018)
022314.
doi:10.1103/PhysRevE.97.022314.
URL https://link.aps.org/doi/10.1103/PhysRevE.97.022314 - [415] G. Bianconi, Large deviation theory of percolation on multiplex networks, J. Stat. Mech. 2019 (2019) 023405. doi:10.1088/1742-5468/ab02dd.
- [416] E. López, L. A. Braunstein, Disorder-induced limited path percolation, Europhys. Lett. 97 (2012) 66001. doi:10.1209/0295-5075/97/66001.
-
[417]
M. Cuquet, J. Calsamiglia,
Limited-path-length
entanglement percolation in quantum complex networks, Phys. Rev. A 83 (2011)
032319.
doi:10.1103/PhysRevA.83.032319.
URL https://link.aps.org/doi/10.1103/PhysRevA.83.032319 -
[418]
D. Zhou, H. E. Stanley, G. D’Agostino, A. Scala,
Assortativity
decreases the robustness of interdependent networks, Phys. Rev. E 86 (2012)
066103.
doi:10.1103/PhysRevE.86.066103.
URL https://link.aps.org/doi/10.1103/PhysRevE.86.066103 - [419] X. Huang, S. Shao, H. Wang, S. V. Buldyrev, S. Havlin, H. E. Stanley, The robustness of interdependent clustered networks, Europhys. Lett. 101 (2012) 18002. doi:10.1209/0295-5075/101/18002.
- [420] X. Liu, H. E. Stanley, J. Gao, Breakdown of interdependent directed networks, Proc. Natl. Acad. Sci. U.S.A. 113 (2016) 1138–1143. doi:10.1073/pnas.1523412113.
-
[421]
G. Dong, J. Gao, L. Tian, R. Du, Y. He,
Percolation of
partially interdependent networks under targeted attack, Phys. Rev. E 85
(2012) 016112.
doi:10.1103/PhysRevE.85.016112.
URL https://link.aps.org/doi/10.1103/PhysRevE.85.016112 -
[422]
D. Zhou, J. Gao, H. E. Stanley, S. Havlin,
Percolation of
partially interdependent scale-free networks, Phys. Rev. E 87 (2013) 052812.
doi:10.1103/PhysRevE.87.052812.
URL https://link.aps.org/doi/10.1103/PhysRevE.87.052812 -
[423]
S. V. Buldyrev, N. W. Shere, G. A. Cwilich,
Interdependent
networks with identical degrees of mutually dependent nodes, Phys. Rev. E 83
(2011) 016112.
doi:10.1103/PhysRevE.83.016112.
URL https://link.aps.org/doi/10.1103/PhysRevE.83.016112 -
[424]
B. Min, S. D. Yi, K.-M. Lee, K.-I. Goh,
Network robustness
of multiplex networks with interlayer degree correlations, Phys. Rev. E 89
(2014) 042811.
doi:10.1103/PhysRevE.89.042811.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.042811 - [425] R. Parshani, C. Rozenblat, D. Ietri, C. Ducruet, S. Havlin, Inter-similarity between coupled networks, Europhys. Lett. 92 (2010) 68002. doi:10.1209/0295-5075/92/68002.
-
[426]
Y. Hu, D. Zhou, R. Zhang, Z. Han, C. Rozenblat, S. Havlin,
Percolation of
interdependent networks with intersimilarity, Phys. Rev. E 88 (2013) 052805.
doi:10.1103/PhysRevE.88.052805.
URL https://link.aps.org/doi/10.1103/PhysRevE.88.052805 -
[427]
D. Cellai, E. López, J. Zhou, J. P. Gleeson, G. Bianconi,
Percolation in
multiplex networks with overlap, Phys. Rev. E 88 (2013) 052811.
doi:10.1103/PhysRevE.88.052811.
URL https://link.aps.org/doi/10.1103/PhysRevE.88.052811 - [428] M. Li, R.-R. Liu, C.-X. Jia, B.-H. Wang, Critical effects of overlapping of connectivity and dependence links on percolation of networks, New J. Phys. 15 (2013) 093013. doi:10.1088/1367-2630/15/9/093013.
-
[429]
L. D. Valdez, P. A. Macri, H. E. Stanley, L. A. Braunstein,
Triple point in
correlated interdependent networks, Phys. Rev. E 88 (2013) 050803.
doi:10.1103/PhysRevE.88.050803.
URL https://link.aps.org/doi/10.1103/PhysRevE.88.050803 - [430] R.-R. Liu, M. Li, C.-X. Jia, Cascading failures in coupled networks: The critical role of node-coupling strength across networks, Sci. Rep. 6 (2016) 35352. doi:10.1038/srep35352.
-
[431]
L.-W. Kong, M. Li, R.-R. Liu, B.-H. Wang,
Percolation on
networks with weak and heterogeneous dependency, Phys. Rev. E 95 (2017)
032301.
doi:10.1103/PhysRevE.95.032301.
URL https://link.aps.org/doi/10.1103/PhysRevE.95.032301 - [432] R.-R. Liu, C.-X. Jia, Y.-C. Lai, Asymmetry in interdependence makes a multilayer system more robust against cascading failures, Phys. Rev. E 100 (2019) 052306. doi:10.1103/PhysRevE.100.052306.
- [433] R.-R. Liu, M. Li, C.-X. Jia, B.-H. Wang, Cascading failures in coupled networks with both inner-dependency and inter-dependency links, Sci. Rep. 6 (2016) 25294. doi:10.1038/srep25294.
-
[434]
J. Shao, S. V. Buldyrev, S. Havlin, H. E. Stanley,
Cascade of
failures in coupled network systems with multiple support-dependence
relations, Phys. Rev. E 83 (2011) 036116.
doi:10.1103/PhysRevE.83.036116.
URL https://link.aps.org/doi/10.1103/PhysRevE.83.036116 -
[435]
A. Bashan, R. Parshani, S. Havlin,
Percolation in
networks composed of connectivity and dependency links, Phys. Rev. E 83
(2011) 051127.
doi:10.1103/PhysRevE.83.051127.
URL https://link.aps.org/doi/10.1103/PhysRevE.83.051127 - [436] A. Bashan, S. Havlin, The combined effect of connectivity and dependency links on percolation of networks, J. Stat. Phys. 145 (2011) 686–695. doi:10.1007/s10955-011-0333-5.
- [437] H. Wang, M. Li, L. Deng, B.-H. Wang, Percolation on networks with conditional dependence group, PLoS ONE 10 (2015) e0126674. doi:10.1371/journal.pone.0126674.
- [438] H. Wang, M. Li, L. Deng, B.-H. Wang, Robustness of networks with assortative dependence groups, Physica A 502 (2018) 195–200. doi:10.1016/j.physa.2018.02.150.
- [439] M. Li, R.-R. Liu, C.-X. Jia, B.-H. Wang, Cascading failures on networks with asymmetric dependence, Europhys. Lett. 108 (2014) 56002. doi:10.1209/0295-5075/108/56002.
-
[440]
J. Gao, S. V. Buldyrev, S. Havlin, H. E. Stanley,
Robustness of
a network of networks, Phys. Rev. Lett. 107 (2011) 195701.
doi:10.1103/PhysRevLett.107.195701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.107.195701 - [441] J. Gao, S. V. Buldyrev, H. E. Stanley, S. Havlin, Networks formed from interdependent networks, Nat. Phys. 8 (2012) 40–48. doi:10.1038/nphys2180.
-
[442]
J. Gao, S. V. Buldyrev, H. E. Stanley, X. Xu, S. Havlin,
Percolation of a
general network of networks, Phys. Rev. E 88 (2013) 062816.
doi:10.1103/PhysRevE.88.062816.
URL https://link.aps.org/doi/10.1103/PhysRevE.88.062816 -
[443]
J. Gao, D. Li, S. Havlin, From a
single network to a network of networks, Natl. Sci. Rev. 1 (2014) 346–356.
doi:10.1093/nsr/nwu020.
URL https://doi.org/10.1093/nsr/nwu020 -
[444]
G. D’Agostino, A. Scala (Eds.),
Networks
of Networks: The Last Frontier of Complexity, Springer International
Publishing, 2014.
URL https://www.ebook.de/de/product/21612217/networks_of_networks_the_last_frontier_of_complexity.html - [445] S. Havlin, D. Kenett, A. Bashan, J. Gao, H. Stanley, Vulnerability of network of networks, Eur. Phys. J. Spec. Top. 223 (2014) 2087–2106. doi:10.1140/epjst/e2014-02251-6.
- [446] D. Y. Kenett, M. Perc, S. Boccaletti, Networks of networks – An introduction, Chaos Soliton Fract. 80 (2015) 1 – 6. doi:https://doi.org/10.1016/j.chaos.2015.03.016.
-
[447]
S. Shao, X. Huang, H. E. Stanley, S. Havlin,
Robustness of a
partially interdependent network formed of clustered networks, Phys. Rev. E
89 (2014) 032812.
doi:10.1103/PhysRevE.89.032812.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.032812 -
[448]
G. Dong, J. Gao, R. Du, L. Tian, H. E. Stanley, S. Havlin,
Robustness of
network of networks under targeted attack, Phys. Rev. E 87 (2013) 052804.
doi:10.1103/PhysRevE.87.052804.
URL https://link.aps.org/doi/10.1103/PhysRevE.87.052804 -
[449]
L. M. Shekhtman, Y. Berezin, M. M. Danziger, S. Havlin,
Robustness of a
network formed of spatially embedded networks, Phys. Rev. E 90 (2014)
012809.
doi:10.1103/PhysRevE.90.012809.
URL https://link.aps.org/doi/10.1103/PhysRevE.90.012809 - [450] F. Radicchi, G. Bianconi, Redundant interdependencies boost the robustness of multiplex networks, Phys. Rev. X 7 (2017) 011013. doi:10.1103/PhysRevX.7.011013.
-
[451]
M. Dickison, S. Havlin, H. E. Stanley,
Epidemics on
interconnected networks, Phys. Rev. E 85 (2012) 066109.
doi:10.1103/PhysRevE.85.066109.
URL https://link.aps.org/doi/10.1103/PhysRevE.85.066109 -
[452]
G. Rapisardi, A. Arenas, G. Caldarelli, G. Cimini,
Fragility and
anomalous susceptibility of weakly interacting networks, Phys. Rev. E 99
(2019) 042302.
doi:10.1103/PhysRevE.99.042302.
URL https://link.aps.org/doi/10.1103/PhysRevE.99.042302 - [453] S. Melnik, M. A. Porter, P. J. Mucha, J. P. Gleeson, Dynamics on modular networks with heterogeneous correlations, Chaos 24 (2014) 023106. doi:10.1063/1.4869983.
-
[454]
S. Shai, D. Y. Kenett, Y. N. Kenett, M. Faust, S. Dobson, S. Havlin,
Critical tipping
point distinguishing two types of transitions in modular network structures,
Phys. Rev. E 92 (2015) 062805.
doi:10.1103/PhysRevE.92.062805.
URL https://link.aps.org/doi/10.1103/PhysRevE.92.062805 -
[455]
A. Faqeeh, S. Melnik, P. Colomer-de Simón, J. P. Gleeson,
Emergence of
coexisting percolating clusters in networks, Phys. Rev. E 93 (2016) 062308.
doi:10.1103/PhysRevE.93.062308.
URL https://link.aps.org/doi/10.1103/PhysRevE.93.062308 - [456] J. Gao, X. Liu, D. Li, S. Havlin, Recent progress on the resilience of complex networks, Energies 8 (2015) 12187–12210. doi:10.3390/en81012187.
- [457] L. M. Shekhtman, M. M. Danziger, S. Havlin, Recent advances on failure and recovery in networks of networks, Chaos Soliton Fract. 90 (2016) 28–36. doi:10.1016/j.chaos.2016.02.002.
-
[458]
S. Fortunato,
Community
detection in graphs, Phys. Rep. 486 (2010) 75 – 174.
doi:https://doi.org/10.1016/j.physrep.2009.11.002.
URL http://www.sciencedirect.com/science/article/pii/S0370157309002841 -
[459]
J. Fan, X. Chen, General
clique percolation in random networks, Europhys. Lett. 107 (2014) 28005.
URL http://stacks.iop.org/0295-5075/107/i=2/a=28005 - [460] M. Piraveenan, M. Prokopenko, L. Hossain, Percolation centrality: quantifying graph-theoretic impact of nodes during percolation in networks, PLoS ONE 8 (2013) e53095. doi:10.1371/journal.pone.0053095.
- [461] G. D. Ferraro, A. Moreno, B. Min, F. Morone, Ú. Pérez-Ramírez, L. Pérez-Cervera, L. C. Parra, A. Holodny, S. Canals, H. A. Makse, Finding influential nodes for integration in brain networks using optimal percolation theory, Nat. Commun. 9 (2018) 2274. doi:10.1038/s41467-018-04718-3.
- [462] S. Osat, A. Faqeeh, F. Radicchi, Optimal percolation on multiplex networks, Nat. Commun. 8 (2017) 1540. doi:10.1038/s41467-017-01442-2.
-
[463]
S. Ji, L. Lü, C. H. Yeung, Y. Hu,
Effective spreading from
multiple leaders identified by percolation in the
susceptible-infected-recovered (SIR) model, New J. Phys. 19 (2017) 073020.
doi:10.1088/1367-2630/aa76b0.
URL https://doi.org/10.1088%2F1367-2630%2Faa76b0 -
[464]
Y. Hu, S. Ji, Y. Jin, L. Feng, H. E. Stanley, S. Havlin,
Local structure can identify
and quantify influential global spreaders in large scale social networks,
Proc. Natl. Acad. Sci. U.S.A. 115 (2018) 7468–7472.
doi:10.1073/pnas.1710547115.
URL https://www.pnas.org/content/115/29/7468 -
[465]
A. Allard, L. Hébert-Dufresne, J.-G. Young, L. J. Dubé,
Coexistence of
phases and the observability of random graphs, Phys. Rev. E 89 (2014)
022801.
doi:10.1103/PhysRevE.89.022801.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.022801 - [466] T. Hasegawa, T. Takaguchi, N. Masuda, Observability transitions in correlated networks, Phys. Rev. E 88 (2013) 042809. doi:10.1103/PhysRevE.88.042809.
- [467] S. Yang, Q. Yang, X. Xu, D. Lu, D. Li, Observability transitions in networks with betweenness preference, PLoS ONE 11 (2016) e0156764. doi:10.1371/journal.pone.0156764.
- [468] Y. Yang, F. Radicchi, Observability transition in real networks, Phys. Rev. E 94 (2016) 030301. doi:10.1103/PhysRevE.94.030301.
- [469] S. Osat, F. Radicchi, Observability transition in multiplex networks, Physica A 503 (2018) 745–761. doi:10.1016/j.physa.2018.02.157.
- [470] R. M. Anderson, R. M. May, Infectious Diseases in Humans, Oxford University Press, Oxford, 1992.
- [471] A. Vespignani, Modelling dynamical processes in complex socio-technical systems, Nat. Phys. 8 (2012) 32–39. doi:10.1038/nphys2160.
- [472] H. W. Hethcote, The mathematics of infectious diseases, SIAM Rev. 42 (2000) 599–653. doi:10.1137/S0036144500371907.
- [473] W. Wang, M. Tang, H. E. Stanley, L. A. Braunstein, Unification of theoretical approaches for epidemic spreading on complex networks, Rep. Prog. Phys. 80 (2017) 036603. doi:10.1088/1361-6633/aa5398.
-
[474]
R. Parshani, S. Carmi, S. Havlin,
Epidemic
threshold for the susceptible-infectious-susceptible model on random
networks, Phys. Rev. Lett. 104 (2010) 258701.
doi:10.1103/PhysRevLett.104.258701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.104.258701 -
[475]
M. Barthélemy, A. Barrat, R. Pastor-Satorras, A. Vespignani,
Velocity and
hierarchical spread of epidemic outbreaks in scale-free networks, Phys. Rev.
Lett. 92 (2004) 178701.
doi:10.1103/PhysRevLett.92.178701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.92.178701 - [476] P. Grassberger, Two-dimensional SIR epidemics with long range infection, J. Stat. Phys. 153 (2013) 289–311. doi:10.1007/s10955-013-0824-7.
-
[477]
R. Juhász, I. A. Kovács, F. Iglói,
Long-range
epidemic spreading in a random environment, Phys. Rev. E 91 (2015) 032815.
doi:10.1103/PhysRevE.91.032815.
URL https://link.aps.org/doi/10.1103/PhysRevE.91.032815 -
[478]
A. L. Ziff, R. M. Ziff,
Fractal
kinetics of covid-19 pandemic, medRxiv 2020.02.16.20023820 (2020).
doi:10.1101/2020.02.16.20023820.
URL https://www.medrxiv.org/content/early/2020/03/03/2020.02.16.20023820 -
[479]
M. Li, J. Chen, Y. Deng, Scaling
features in the spreading of covid-19, arXiv preprint arXiv:2002.09199
(2020).
URL https://arxiv.org/abs/2002.09199 - [480] H. M. Singer, The covid-19 pandemic: growth patterns, power law scaling, and saturation, Phys. Biol. 17 (2020) 055001. doi:10.1088/1478-3975/ab9bf5.
- [481] B. F. Maier, D. Brockmann, Effective containment explains subexponential growth in recent confirmed COVID-19 cases in China, Science 368 (2020) 742–746. doi:10.1126/science.abb4557.
- [482] G. Chowell, L. Sattenspiel, S. Bansal, C. Viboud, Mathematical models to characterize early epidemic growth: A review, Phys. Life Rev. 18 (2016) 66–97. doi:10.1016/j.plrev.2016.07.005.
-
[483]
M. Barthélemy, A. Barrat, R. Pastor-Satorras, A. Vespignani,
Dynamical
patterns of epidemic outbreaks in complex heterogeneous networks, J. Theor.
Biol. 235 (2005) 275 – 288.
doi:https://doi.org/10.1016/j.jtbi.2005.01.011.
URL http://www.sciencedirect.com/science/article/pii/S0022519305000251 - [484] Y. Moreno, R. Pastor-Satorras, A. Vespignani, Epidemic outbreaks in complex heterogeneous networks, Eur. Phys. J. B 26 (2002) 521–529. doi:10.1140/epjb/e20020122.
- [485] E. Volz, L. A. Meyers, Epidemic thresholds in dynamic contact networks, J. R. Soc. Interface 6 (2009) 233–241. doi:10.1098/rsif.2008.0218.
- [486] K. T. D. Eames, M. J. Keeling, Modeling dynamic and network heterogeneities in the spread of sexually transmitted diseases, Proc. Natl. Acad. Sci. U.S.A. 99 (2002) 13330–13335. doi:10.1073/pnas.202244299.
- [487] K. J. Sharkey, Deterministic epidemiological models at the individual level, J. Math. Biol. 57 (2008) 311–331.
- [488] K. J. Sharkey, Deterministic epidemic models on contact networks: Correlations and unbiological terms, Theor. Popul. Biol. 79 (2011) 115 – 129.
- [489] J. Lindquist, J. Ma, P. van den Driessche, F. H. Willeboordse, Effective degree network disease models, J. Math. Biol. 62 (2011) 143–164.
- [490] K. J. Sharkey, I. Z. Kiss, R. R. Wilkinson, P. L. Simon, Exact equations for sir epidemics on tree graphs, Bull. Math. Biol. 77 (2015) 614–645.
- [491] I. Z. Kiss, C. G. Morris, F. Sélley, P. L. Simon, R. R. Wilkinson, Exact deterministic representation of markovian sir epidemics on networks with and without loops, J. Math. Biol. 70 (2015) 437–464.
-
[492]
P. Grassberger,
On
the critical behavior of the general epidemic process and dynamical
percolation, Math. Biosci. 63 (1983) 157 – 172.
doi:https://doi.org/10.1016/0025-5564(82)90036-0.
URL http://www.sciencedirect.com/science/article/pii/0025556482900360 - [493] H. Andersson, T. Britton, Lecture Notes in Statistics, Springer, New York, 2000.
-
[494]
R. Pastor-Satorras, A. Vespignani,
Epidemic
spreading in scale-free networks, Phys. Rev. Lett. 86 (2001) 3200–3203.
doi:10.1103/PhysRevLett.86.3200.
URL https://link.aps.org/doi/10.1103/PhysRevLett.86.3200 -
[495]
A. L. Lloyd, R. M. May,
How viruses
spread among computers and people, Science 292 (2001) 1316–1317.
doi:10.1126/science.1061076.
URL https://science.sciencemag.org/content/292/5520/1316 -
[496]
M. Boguñá, R. Pastor-Satorras, A. Vespignani,
Absence of
epidemic threshold in scale-free networks with degree correlations, Phys.
Rev. Lett. 90 (2003) 028701.
doi:10.1103/PhysRevLett.90.028701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.90.028701 -
[497]
C.-R. Cai, Z.-X. Wu, J.-Y. Guan,
Effective degree
markov-chain approach for discrete-time epidemic processes on uncorrelated
networks, Phys. Rev. E 90 (2014) 052803.
doi:10.1103/PhysRevE.90.052803.
URL https://link.aps.org/doi/10.1103/PhysRevE.90.052803 -
[498]
C.-R. Cai, Z.-X. Wu, M. Z. Q. Chen, P. Holme, J.-Y. Guan,
Solving the
dynamic correlation problem of the susceptible-infected-susceptible model on
networks, Phys. Rev. Lett. 116 (2016) 258301.
doi:10.1103/PhysRevLett.116.258301.
URL https://link.aps.org/doi/10.1103/PhysRevLett.116.258301 -
[499]
R. Pastor-Satorras, A. Vespignani,
Immunization of
complex networks, Phys. Rev. E 65 (2002) 036104.
doi:10.1103/PhysRevE.65.036104.
URL https://link.aps.org/doi/10.1103/PhysRevE.65.036104 -
[500]
P. Holme, B. J. Kim, C. N. Yoon, S. K. Han,
Attack
vulnerability of complex networks, Phys. Rev. E 65 (2002) 056109.
doi:10.1103/PhysRevE.65.056109.
URL https://link.aps.org/doi/10.1103/PhysRevE.65.056109 - [501] C. M. Schneider, T. Mihaljev, S. Havlin, H. J. Herrmann, Suppressing epidemics with a limited amount of immunization units, Phys. Rev. E 84 (2011) 061911. doi:10.1103/PhysRevE.84.061911.
-
[502]
Y. Chen, G. Paul, S. Havlin, F. Liljeros, H. E. Stanley,
Finding a
better immunization strategy, Phys. Rev. Lett. 101 (2008) 058701.
doi:10.1103/PhysRevLett.101.058701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.101.058701 -
[503]
R. Cohen, S. Havlin, D. ben Avraham,
Efficient
immunization strategies for computer networks and populations, Phys. Rev.
Lett. 91 (2003) 247901.
doi:10.1103/PhysRevLett.91.247901.
URL https://link.aps.org/doi/10.1103/PhysRevLett.91.247901 -
[504]
P. Holme, Efficient local
strategies for vaccination and network attack, Europhys. Lett. 68 (2004)
908–914.
doi:10.1209/epl/i2004-10286-2.
URL https://doi.org/10.1209%2Fepl%2Fi2004-10286-2 -
[505]
P. S. Dodds, J. L. Payne,
Analysis of a
threshold model of social contagion on degree-correlated networks, Phys.
Rev. E 79 (2009) 066115.
doi:10.1103/PhysRevE.79.066115.
URL https://link.aps.org/doi/10.1103/PhysRevE.79.066115 -
[506]
P. S. Dodds, D. J. Watts,
Universal
behavior in a generalized model of contagion, Phys. Rev. Lett. 92 (2004)
218701.
doi:10.1103/PhysRevLett.92.218701.
URL https://link.aps.org/doi/10.1103/PhysRevLett.92.218701 -
[507]
B. Samuelsson, J. E. S. Socolar,
Exhaustive
percolation on random networks, Phys. Rev. E 74 (2006) 036113.
doi:10.1103/PhysRevE.74.036113.
URL https://link.aps.org/doi/10.1103/PhysRevE.74.036113 -
[508]
V.-P. Backlund, J. Saramäki, R. K. Pan,
Effects of
temporal correlations on cascades: Threshold models on temporal networks,
Phys. Rev. E 89 (2014) 062815.
doi:10.1103/PhysRevE.89.062815.
URL https://link.aps.org/doi/10.1103/PhysRevE.89.062815 - [509] P. H. Taro Takaguchi, Naoki Masuda, Bursty communication patterns facilitate spreading in a threshold-based epidemic dynamics, PLoS ONE 8 (2013) e68629. doi:10.1371/journal.pone.0068629.
-
[510]
F. Karimi, P. Holme,
Threshold
model of cascades in empirical temporal networks, Physica A 392 (2013) 3476
– 3483.
doi:https://doi.org/10.1016/j.physa.2013.03.050.
URL http://www.sciencedirect.com/science/article/pii/S0378437113002835 - [511] D. Li, B. Fu, Y. Wang, G. Lu, Y. Berezin, H. E. Stanley, S. Havlin, Percolation transition in dynamical traffic network with evolving critical bottlenecks, Proc. Natl. Acad. Sci. U.S.A. 112 (2014) 669–672. doi:10.1073/pnas.1419185112.
- [512] G. Zeng, D. Li, S. Guo, L. Gao, Z. Gao, H. E. Stanley, S. Havlin, Switch between critical percolation modes in city traffic dynamics, Proc. Natl. Acad. Sci. U.S.A. 116 (2018) 23–28. doi:10.1073/pnas.1801545116.
- [513] F. Wang, D. Li, X. Xu, R. Wu, S. Havlin, Percolation properties in a traffic model, Europhys. Lett. 112 (2015) 38001. doi:10.1209/0295-5075/112/38001.
- [514] P. Echenique, J. Gómez-Gardeñes, Y. Moreno, Dynamics of jamming transitions in complex networks, Europhys. Lett. 71 (2005) 325–331. doi:10.1209/epl/i2005-10080-8.
- [515] A. Baggag, S. Abbar, T. Zanouda, J. Srivastava, Resilience analytics: coverage and robustness in multi-modal transportation networks, EPJ Data Sci. 7 (2018) 14. doi:10.1140/epjds/s13688-018-0139-7.
- [516] H. S. Mahmassani, 50th anniversary invited article—autonomous vehicles and connected vehicle systems: Flow and operations considerations, Transp. Sci. 50 (2016) 1140–1162. doi:10.1287/trsc.2016.0712.
- [517] G. A. Ubiergo, W.-L. Jin, Mobility and environment improvement of signalized networks through vehicle-to-infrastructure (v2i) communications, Transp. Res. Part C 68 (2016) 70–82. doi:10.1016/j.trc.2016.03.010.
- [518] H. M. Ammari, S. K. Das, Integrated coverage and connectivity in wireless sensor networks: A two-dimensional percolation problem, IEEE Trans. Comput. 57 (2008) 1423–1434. doi:10.1109/tc.2008.68.
- [519] M. Khanjary, M. Sabaei, M. R. Meybodi, Critical density for coverage and connectivity in two-dimensional fixed-orientation directional sensor networks using continuum percolation, J. Netw. Comput. Appl. 57 (2015) 169–181. doi:10.1016/j.jnca.2015.08.010.
- [520] X. Jin, W. Su, Y. Wei, A study of the VANET connectivity by percolation theory, in: 2011 IEEE Consumer Communications and Networking Conference (CCNC), IEEE, 2011. doi:10.1109/ccnc.2011.5766628.
- [521] A. Talebpour, H. S. Mahmassani, S. H. Hamdar, Effect of information availability on stability of traffic flow: Percolation theory approach, Transp. Res. Procedia 23 (2017) 81–100. doi:10.1016/j.trpro.2017.05.006.
- [522] A. Mostafizi, S. Dong, H. Wang, Percolation phenomenon in connected vehicle network through a multi-agent approach: Mobility benefits and market penetration, Transp. Res. Part C 85 (2017) 312–333. doi:10.1016/j.trc.2017.09.013.
- [523] N. Serok, O. Levy, S. Havlin, E. Blumenfeld-Lieberthal, Unveiling the inter-relations between the urban streets network and its dynamic traffic flows: Planning implication, Environment and Planning B: Urban Analytics and City Science 46 (2019) 1362–1376. doi:10.1177/2399808319837982.
- [524] M. Behnisch, M. Schorcht, S. Kriewald, D. Rybski, Settlement percolation: A study of building connectivity and poles of inaccessibility, Landscape Urban Plann. 191 (2019) 103631. doi:10.1016/j.landurbplan.2019.103631.
- [525] Y. Jiang, H. J. Timmermans, B. Yu, Relocation of manufacturing industry from the perspective of transport accessibility – an application of percolation theory, Transport Policy 63 (2018) 10–29. doi:10.1016/j.tranpol.2017.11.003.
- [526] D. Piovani, C. Molinero, A. Wilson, Urban retail location: Insights from percolation theory and spatial interaction modeling, PLoS ONE 12 (2017) e0185787. doi:10.1371/journal.pone.0185787.
- [527] Y. Zhou, J. Wang, J.-B. Sheu, On connectivity of post-earthquake road networks, Transp. Res. Part E 123 (2019) 1–16. doi:10.1016/j.tre.2019.01.009.
- [528] S. Guo, R. Wu, Q. Tong, G. Zeng, J. Yang, L. Chen, T. Zhu, W. Lv, D. Li, Is city traffic damaged by torrential rain?, Physica A 503 (2018) 1073–1080. doi:10.1016/j.physa.2018.08.044.
- [529] H.-X. Yang, Z. Rong, W.-X. Wang, Cooperation percolation in spatial prisoner’s dilemma game, New J. Phys. 16 (2014) 013010. doi:10.1088/1367-2630/16/1/013010.
-
[530]
W. Choi, S.-H. Yook, Y. Kim,
Percolation in
spatial evolutionary prisoner’s dilemma game on two-dimensional lattices,
Phys. Rev. E 92 (2015) 052140.
doi:10.1103/PhysRevE.92.052140.
URL https://link.aps.org/doi/10.1103/PhysRevE.92.052140 - [531] H.-X. Yang, J. Yang, Cooperation percolation in spatial evolutionary games, Europhys. Lett. 124 (2019) 60005. doi:10.1209/0295-5075/124/60005.
- [532] M. Lin, N. Li, L. Tian, D.-N. Shi, Spatial evolutionary game with bond dilution, Physica A 389 (2010) 1753–1758. doi:10.1016/j.physa.2009.12.029.
-
[533]
C. K. Yun, N. Masuda, B. Kahng,
Diversity and
critical behavior in prisoner’s dilemma game, Phys. Rev. E 83 (2011) 057102.
doi:10.1103/PhysRevE.83.057102.
URL https://link.aps.org/doi/10.1103/PhysRevE.83.057102 -
[534]
Z. Wang, A. Szolnoki, M. Perc,
Percolation
threshold determines the optimal population density for public cooperation,
Phys. Rev. E 85 (2012) 037101.
doi:10.1103/PhysRevE.85.037101.
URL https://link.aps.org/doi/10.1103/PhysRevE.85.037101 - [535] Z. Wang, A. Szolnoki, M. Perc, If players are sparse social dilemmas are too: Importance of percolation for evolution of cooperation, Sci. Rep. 2 (2012) 369. doi:10.1038/srep00369.
-
[536]
D. Peng, M. Li, Organization of
cooperation in fractal structures, arXiv preprint arXiv:2010.06800 (2020).
URL https://arxiv.org/abs/2010.06800 -
[537]
M. H. Vainstein, C. Brito, J. J. Arenzon,
Percolation and
cooperation with mobile agents: Geometric and strategy clusters, Phys. Rev.
E 90 (2014) 022132.
doi:10.1103/PhysRevE.90.022132.
URL https://link.aps.org/doi/10.1103/PhysRevE.90.022132 - [538] C. H. Yeung, D. Saad, Networking–A statistical physics perspective, J. Phys. A: Math. Theor. 46 (2013) 103001. doi:10.1088/1751-8113/46/10/103001.
- [539] M. Barthélemy, Spatial networks, Phys. Rep. 499 (2011) 1–101. doi:10.1016/j.physrep.2010.11.002.
- [540] F. D. Malliaros, M. Vazirgiannis, Clustering and community detection in directed networks: A survey, Phys. Rep. 533 (2013) 95–142. doi:10.1016/j.physrep.2013.08.002.
-
[541]
G. Bianconi, R. M. Ziff,
Topological
percolation on hyperbolic simplicial complexes, Phys. Rev. E 98 (2018)
052308.
doi:10.1103/PhysRevE.98.052308.
URL https://link.aps.org/doi/10.1103/PhysRevE.98.052308 -
[542]
G. Bianconi, I. Kryven, R. M. Ziff,
Percolation on
branching simplicial and cell complexes and its relation to interdependent
percolation, Phys. Rev. E 100 (2019) 062311.
doi:10.1103/PhysRevE.100.062311.
URL https://link.aps.org/doi/10.1103/PhysRevE.100.062311 -
[543]
I. Kryven, R. M. Ziff, G. Bianconi,
Renormalization
group for link percolation on planar hyperbolic manifolds, Phys. Rev. E 100
(2019) 022306.
doi:10.1103/PhysRevE.100.022306.
URL https://link.aps.org/doi/10.1103/PhysRevE.100.022306 - [544] G. Bianconi, S. N. Dorogovstev, The spectral dimension of simplicial complexes: a renormalization group theory, J. Stat. Mech. 2020 (1) (2020) 014005. doi:10.1088/1742-5468/ab5d0e.
-
[545]
N. Fountoulakis, M. Przykucki,
High-dimensional bootstrap processes
in evolving simplicial complexes, arXiv preprint arXiv:1910.10139 (2020).
URL https://arxiv.org/abs/1910.10139 -
[546]
H. Sun, R. M. Ziff, G. Bianconi,
Renormalization group theory of
percolation on pseudo-fractal simplicial and cell complexes, arXiv preprint
arXiv:2005.02984 (2020).
URL https://arxiv.org/abs/2005.02984