Passivity-based Attack Identification and Mitigation with Event-triggered Observer Feedback and Switching Controller
Abstract
This paper addresses the problem of output consensus in linear passive multi-agent systems under a False Data Injection (FDI) attack, considering the unavailability of complete state information. Our formulation relies on an event-based cryptographic authentication scheme for sensor integrity and considers FDI attacks at the actuator end, inspired by their practical nature and usages. For secure consensus, we propose (i) a passivity-based approach for detecting FDI attacks on the system and (ii) a Zeno-free event-triggered observer-based switching controller, which switches between the normal and the defense modes following an attack detection. We show that the closed-loop system achieves practical consensus under the controller’s action in the defense mode. Simulation examples are provided to support the theoretical findings.
Index Terms:
Consensus, false data injection attack, event-triggered observer, networked system, passive systems.I Introduction
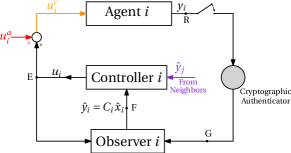
Cyber-Physical Systems (CPS) are often exposed to adversarial attacks due to their operation over insecure communication networks. In particular, FDI attacks are a major threat to the secure operation of a CPS, as they can corrupt both the actuation signal and the sensor measurements [9, 12]. Since the sensor feedback cannot be trusted in this situation, cryptographic tools like message authentication code [6], etc., have been popular as these guarantee sensor measurement integrity from such attacks by preventing data alteration in transit [6]. This situation is shown in Fig. 1, where a cryptographic authenticator is employed in conjunction with an observer to design the secure controllers. However, continuous use of cryptographic tools can generate computation and communication overhead primarily due to the limited resources of CPS [15]. As a remedy, one could employ an event-based cryptographic authentication scheme where the communication is realized using sensors (such as ultrasonic and infrared) that are practically discrete or event-based [2]. Consequently, the controller can ignore an attack injected in between adjacent events, limiting adverse effects on the system. On the other hand, actuators usually work in a continuous fashion and have faster actuation than sensor measurements (for example, the motor in Khepera IV mobile robot [13]). Thereby, an attack injected in between adjacent events at the actuator side cannot be rejected by the actuator. For these practical reasons, it is viable to consider an event-based cryptographic authentication at the sensor end and the FDI attacks at the actuator end.
For the secure control of CPS, attack detection is often the foremost objective [25]. While most of the existing works focus on residual-based and estimation-based attack detectors, these might be vulnerable to destabilizing stealthy attacks [15, 8]. The authors in [5] presented an energy equivalence-based attack detection approach that checks for equality between the supplied, and the dissipated and stored energies. Consequently, the attacks are classified as passive and non-passive. A generalized notion of this is referred to as passivity theory [14], which relies on an inequality between the supplied energy and the change in stored energy. Besides being a flexible tool for control design and analyzing the system’s stability, the passivity property can be leveraged in identifying an attack in a CPS. Unlike [5], our attack identification approach relies on a passivity inequality between the energy supplied and the change in the system’s stored energy, along with an event-based observer setting. With an observer, while an event-triggering mechanism can be implemented either by continuously monitoring the system output [21] or the observer output [24], we consider the former case in this paper where the event condition is independent of the observer state in the presence of a malicious attack.
Attack mitigation is the second necessary step for securely controlling a CPS towards its desired goal following an attack detection. For this, it is essential to have (accurate) knowledge of the attack signal to mitigate its effect, usually accomplished using attack estimators designed as part of the state observers. Some popular works in this direction are [18, 11], where the attack estimators operate continuously irrespective of the absence of an attack signal and hence, are computationally expensive [28]. Unlike these works, this paper proposes a switching-based controller scheme employing the attack estimator only in the case of attack detection and works according to an event-triggered authentication scheme.
Main Contributions: As shown in Fig. 1, we consider a multi-agent system comprising linear passive agents interacting towards achieving output consensus over a network susceptible to malicious FDI attacks. We envisage the presence of actuator attacks while relying on an event-based cryptographic authentication for sensor measurement integrity. The proposed controller receives information about estimated states from its cascaded observer and the estimated outputs from the neighboring agents and works in the dual modes, namely, the normal mode (no-attack detection) and the defense mode (attack detection). We first obtain the Zeno-free event condition for cryptographic authentication for the stable operation of the observer, independent of the overall system’s stability. We then propose a passivity-based approach for the detection of actuator attacks. It is shown that the difference between the agents’ output remains bounded under the action of the proposed switching controller in the defense mode and the previously derived event condition. Alternatively, it can be said that the system achieves practical output consensus.
Paper Organization: Section II describes the system and attack models, followed by the problem statement. Section III introduces the Zeno-free event condition for observer stability. Section IV discusses attack detection and mitigation by introducing the idea of the switching controller, followed by proof of the closed-loop system’s stability. Section V provides simulation results before we conclude the paper and discuss the future direction of work in Section VI.
I-A Notations
The set of real, non-negative real numbers and positive integers is denoted by , , and , respectively. , are column vectors with all entries , , respectively. is an identity matrix. The induced -norm (resp., Euclidean norm) for any matrix (resp., vector ) is represented by (resp., ). The symbol denotes the Kronecker product of two matrices and denotes a diagonal matrix with diagonal entries . The maximum and minimum eigenvalues of a symmetric matrix are represented by and , respectively. The Moore–Penrose pseudo-inverse of a matrix is , having the property . If has full column rank, and [23]. For a digraph with edge set , is a directed edge from node to node . The Laplacian for a graph with nodes is denoted by (please refer to [7] for details).
I-B Preliminaries
Definition 1 (Passive System [14]).
Consider the system
| (1) |
with state , control input , and output . The function is locally Lipschitz, is continuous, and . The system (1) is said to be passive if there exists a continuously differentiable storage function , , such that
| (2) |
Note that the storage function in (2) (which is also referred to as passivity inequality) is not unique. However, the quadratic storage function of the form has its own vantages over others in analyzing linear systems, as it is computationally moderate, easy to implement, and close to the concept of energy in linear systems. Particularly, it is shown in [26] that any storage function can be represented as a quadratic storage function for a linear dynamical system. Motivated by this fact, we exploit the quadratic storage function in our analysis in this paper.
Lemma 1 (Implications of Passivity [4]).
II System Modeling and Problem Description
II-A The Agent and Attack Models
II-A1 Agent Model
We consider a multi-agent system comprising linear passive agents under the influence of FDI attack and having combined system dynamics (see Fig. 1):
| (4) |
where , and are the stacked state, input and output vectors, respectively, where , and . Further, , , and are the stacked system, input and output block diagonal matrices, respectively. We incorporate the following reasonable assumptions on system (4) (unless otherwise explicitly stated):
-
(A1)
The matrix pair is controllable and is observable for all .
-
(A2)
The matrix has full column rank for all .
-
(A3)
The agents are strongly connected over a fixed directed network having Laplacian .
Remark 1.
Note that the assumption (A2) follows from the fact that the agents are usually under-actuated where . If the rank of is less than the number of columns for an under-actuated system, there exists a set of inputs that do not affect the system dynamics, which is not practically desired. Further, in over-actuated systems, if the columns of are linearly dependent, some inputs will be redundant. Thus, it is reasonable to remove dependent columns and corresponding inputs with the assumption that has full column rank (please refer to [3, Section 6.2.1]). Some of the most widely used robotic models, like quadcopter and car-like models, among others, satisfy (A2) [28, 17]. Other examples are tugboats [10], which follow second-order Lagrangian dynamics, and harmonic oscillators [27]. Both these systems are passive and satisfy the preconditions (A1) and (A2).
II-A2 FDI Attack Model
The FDI attack on the agent can be modeled as shown in Fig. 1, implying that the compromised signal reaching its actuator can be written as
| (5) |
for each , where , , and are designed control, actuator attack, and compromised control signals, respectively. As discussed in Section I, since we employ an event-based cryptographic authentication scheme for the sensor measurements collected at point R in Fig. 1, the attack at the sensor end can be neglected for a suitably chosen event condition such that the observer error dynamics remains stable. The following reasonable limitations are considered on the actuator attack signal:
Assumption 1.
The attack signal is bounded and has a bounded derivative, that is, and , for some .
Assumption 1 is motivated by the fact that the attack signal cannot be arbitrarily large, as the attacker has limited resources [20]. Secondly, arbitrarily large attack signals are easy to detect, while the attacker generally wants to remain stealthy. Further, this paper does not deal with sensor noise. In practice, noise and attacks have inherently different characteristics; noise is caused randomly and unintentionally, while attacks are injected intentionally by an intruder to mislead or even paralyze the whole network’s behaviors while remaining undetected [12].
II-B Event-based Observer and Switching Controller
II-B1 The Observer
Due to event-triggered sensor feedback, the latest measurements are not always available at point G (in Fig. 1). Let the sensor measurement at the last event be . We define an error variable . Clearly, . With the error term , the event-triggered observer dynamics is given by:
| (6) |
where is the observer gain matrix, is the estimated state and is the estimated input attack signal proposed as:
| (7) |
where is a small constant reaction time, representing the time required to observe the effect of control on the sensor output. Clearly, is Lipschitz under Assumption 1, i.e.,
| (8) |
for some constant . Ideally, , however, it may not be feasible in practice due to the components’ response time and can be assumed sufficiently small. Next, we define the state estimation error , whose time-derivative, using (4) and (6), is obtained as
| (9) |
In the absence of an attack (i.e., ), attack estimator is inactive, that is, , and hence, (9) can be written as , which is independent of , and can be stabilized with the event condition as provided in further analysis in the paper. Without loss of generality, we consider the following assumption for the initialization of the observer states:
Assumption 2.
The state estimation error is zero at the instant of time when an attack starts. For instance, if the attack begins at time , .
Please note that Assumption 2 does not imply a prior knowledge of the attack time and only assumes that the observer error is small at the beginning of an attack. Similar assumptions have been made in literature [1], as such assumptions are generally required for attack detection with residual based attack detection approaches but not mentioned explicitly. We have the following proposition about the boundedness of the signal (whose proof is discussed in Section IV):
Proposition 1.
Under the proposed event-based observer (6), it holds that , where is a constant.
II-B2 The Controller
Let us introduce a logic such that indicates “no attack detection”, while indicates an “attack detection”. Based on this, the following switching-based control strategy is proposed:
| (10) |
where and are the control actions in normal (no attack detection) and defense (attack detection) modes, respectively. In the absence of an attack, it follows from [4, Theorem 2.1] that the system (4), under passivity assumption, achieve output consensus with the following control:
| (11) |
where is the extended Laplacian, is a constant gain, and is the stacked input vector under normal operation. Under the action of an observer, (11) can be written equivalently in terms of the estimated measurement signal as [16]:
| (12) |
which would be used in the subsequent analysis in this paper.
II-C The Problem
Consider the linear passive system (4) under FDI attacks (5) with observer dynamics (6) equipped with an event-based authentication mechanism as shown in Fig. 1. Let the system be governed by a switching-based control protocol (10), where the attack estimator operates only in the defense mode and the event-authentication mechanism is in operation for all time. Suppose that the aforementioned assumptions hold. The following problems are addressed in this paper:
-
(P1)
Obtain an event condition for authentication feedback to the observer such that the observer error dynamics (9) is practically stable and the estimation error remains near the origin, i.e., .
-
(P2)
Device an FDI attack detection mechanism using passivity inequality (2) with the quadratic storage function.
-
(P3)
Design the switching control law in (10) (effectively ) such that the system achieves (practical) output consensus, i.e., there exists a small constant such that .
III Event Condition and Zeno Behavior
In this section, we introduce the event condition and show that the observer states follow the agents’ states closely with a small error. To ensure that the observer error dynamics (9) is stable and converges to zero, could be a candidate Lyapunov function, where is a symmetric positive definite matrix satisfying for some symmetric positive definite matrix . The time-derivative of the Lyapunov function , along the error dynamics (9), is
From the inequality111The proof follows from the fact that the arithmetic mean is greater than or equal to geometric mean for any two positive numbers and . for some and , it follows that and . Using these, it can be written that
where , , , and is a design variable. If the event condition is set as for some , , implying stability of the observer error dynamics. However, non-availability of the entire error vector and requirement to monitor both system and observer states restricts its implementation, as discussed in Section I. Therefore, motivated by the dynamic event-triggered scheme [21], we introduce an auxiliary variable with dynamics:
| (13) |
where , and and are design parameters. Clearly, solution of (13) is given by , which non-negative for . Thus, .
Theorem 1.
The observer error dynamics (9) is stable and the error converges to a small ball around the origin under the following dynamic event condition:
| (14) |
where , and are arbitrary design constants ( are defined as above).
Proof.
Consider the composite Lyapunov function , whose time-derivative, along (9) and (13), is . Under the event condition (14) and substituting for , yields . Now, it can be concluded that the dynamics (9) is practically stable and the estimation error converges to a small ball near the origin having its radius dependent on . ∎
Next, we prove the exclusion of Zeno behavior by showing that there exists a positive minimum inter event time (MIET). Before proceeding, we consider that the system’s output has bounded derivative, i.e., , where is arbitrary large positive constant.
Theorem 2.
Proof.
Differentiating for we get . For MIET , the event triggers when the right side of the equality in (14) is minimum, which is achieved when (since , see (13)). The value of error at MIET is
| (15) |
and using (15) in the expression of , we get
| (16) |
Integrating (16) for , we get . Since and substituting from (15), we get . ∎
IV Attack Detection, Mitigation and Closed-Loop System Stability
IV-A Passivity-Based Attack Detection
The proposed passivity-based attack detector relies on the verification of passivity inequality (2) for the measurable signals in Fig. 1. Note that the agents’ output , controllers’ output , and observers’ state and the output are measurable. Note that the original input signal is measurable and the corrupted input , applied to the agent, is not measurable. However, the output is available only at events of cryptographic authentication. This suggests verification of (2) for the input-output pair across the observer (i.e., points E and F in Fig. 1) with the quadratic storage function associated with the observer’s states . It is straightforward that (2) holds for appropriately designed observer, across points E and F if there is no attack on the system [22], while this might not be true in case of an actuator attack. We leverage this fact in detecting the presence of an attack . We classify the attack signal as detectable and undetectable as follows:
Definition 2.
Note that it is sufficient to check (2) for the detection of an attack on the system. However, we also provide the following theorem to establish a connection between the system and network properties (in terms of the matrices , and ) under the attack signal on the system, however, it is not necessary for the purpose of implementation verifying only (2) is sufficient.
Theorem 3.
Proof.
We prove it by contradiction. Assume that (2) is satisfied across points E and F with . This implies that . Since the system is operating in normal mode, we have as in (10). Substituting and from (6) and (12) results in , where . Rearranging, we get . Replacing by as defined in the statement of theorem, the preceding inequality becomes . Now, substituting , where is given by (4), we get . Now, it can be concluded that any which violates the preceding inequality (i.e., satisfies (17)) does not satisfy (2) across points E and F in Fig. 1, and hence, are detectable. ∎
IV-B Attack Mitigation
Once the attack is detected, the controller (10) switches to the defense mode, i.e., and . Relying on the estimated attack signal in (7), we propose the control in defense mode as
| (18) |
where is given by (12). As a result, the compromised control input to the actuators becomes
| (19) |
We are now ready to prove Proposition 1.
Proof of Proposition 1.
Left multiplying (7) with on both sides, yields
| (20) |
From (9), substituting and , we obtain . Substituting for and from (4) and (19), respectively, and using the property (as stated in notations), we get , where . Rearranging, we have . Using (8), we get . According to Assumption 2 and Theorem 1, as , this implies that as . Now, it follows that there exists a constant such that , proving our claim. ∎
Remark 2.
Multiplying by on both sides of the inequality , we have . Since for the full column rank matrix (see (A2)) and , it follows from the preceding relation that . Clearly, for sufficiently small reaction time .
Note that there seems to be an inter-dependency among Proposition 1 and Theorem 1. However, under Assumption 2, Theorem 1 holds independently for , as the attack estimator is “OFF” (i.e., ) in the absence of an attack (i.e., ), and can be considered as initialization to our problem. On the other hand, in the presence of an attack (i.e., ), we make sure with the aid of Assumption 1 that when an attack starts at , the state observer has a small error for accurate detection and estimation of the attack signal (similar assumption is also made in [1]).
IV-C Closed-Loop System Stability
In the below theorem, we show that the difference among agents’ outputs remain bounded during attack and the closed-loop system achieves practical consensus.
Theorem 4.
Consider the closed-loop system as shown in Fig. 1 with agent, observer and attack estimator models (4), (6) and (7), respectively. Let the system be governed by the switching controller (10) where and are defined in (12) and (18), respectively. Then, the system achieves (practical) output consensus, i.e., there exists a small constant such that . Additionally, if the communication topology is balanced, then is given by , where depends on and .
Proof.
Under no attack condition, the convergence directly follows from [4], as (see (12)). Our main goal here is to prove convergence in case when the controller operates in the defense mode under attack, i.e., , given by (18). Since the agents (4) are passive, Lemma 1 assures existence of a candidate Lyapunov function such that its time-derivative along agent dynamics (4) satisfies , where . Substituting for from (12) and , we obtain
where . If , the trajectories converges to the set . The set is characterized by all the trajectories such that . If , it can be written that . Following Proposition 1 and Remark 2, it can be concluded that for some , which is a small positive constant for small values of and . Consequently, , and the convergence follows in the sense of practical stability.
To prove the second statement, we analyze the time-derivative . Clearly, , if . Since the preceding inequality must hold even in the worst-case scenario where , the condition must be satisfied. In this situation, as outside the region where , it follows from [14, Lemmea 4.6] that all the solution trajectories fall within the region where , as . For balanced and strongly connected digraphs (i.e., ), the preceding inequality can be written as for each . As relies on and , small values of and the reaction time (see Remark 2) will lead to small value of , and hence, . Alternatively, by increasing , can be made small. ∎

V Simulation Example
Consider agents interacting according to a communication graph as shown in Fig. 2. Agent’s initial states are taken randomly in the interval . The FDI attack on actuator is of the form , where are chosen randomly in the interval and , respectively, for , and , i.e., no attack on agent . Note that the attack information is given only for the purpose of illustration and is unavailable to the controller. We consider that the attack remains active for . We discuss three case studies as follows:
V-A Passive Agents with Real Poles
Consider heterogeneous agents with the following governing matrices in (4):
respectively, where . It can be easily verified that the agents are passive as the associated transfer function is positive real (please refer to positive real lemma [14, Lemma 6.4]). Further, the preconditions (A1) and (A2) are trivially satisfied.
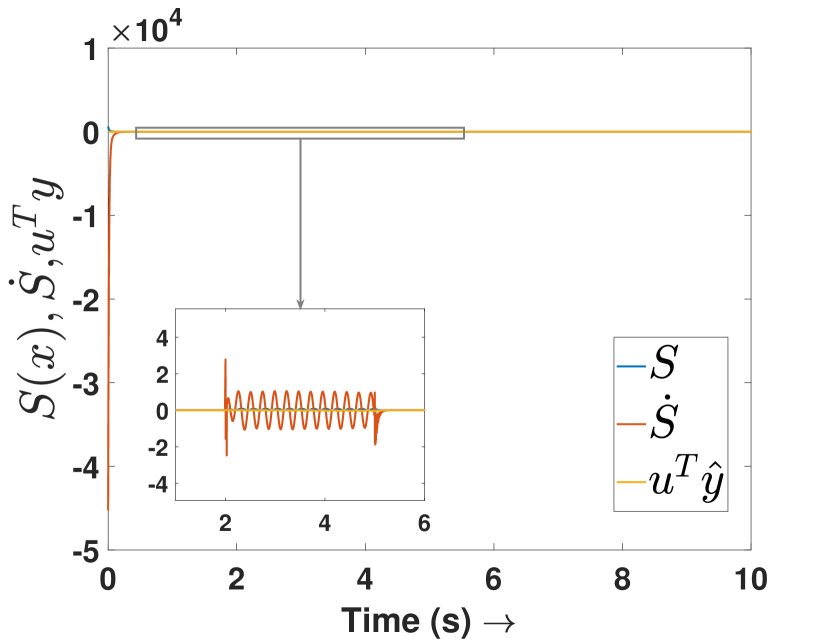
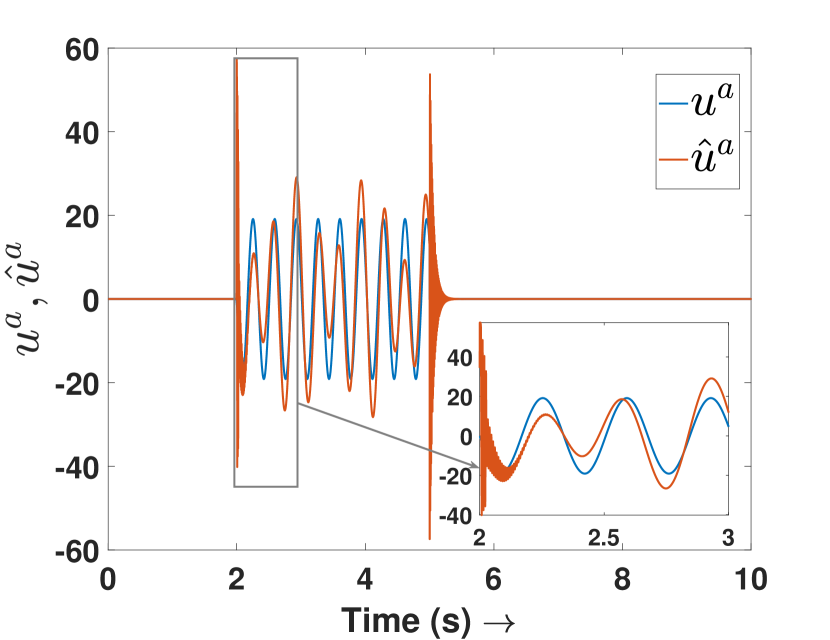
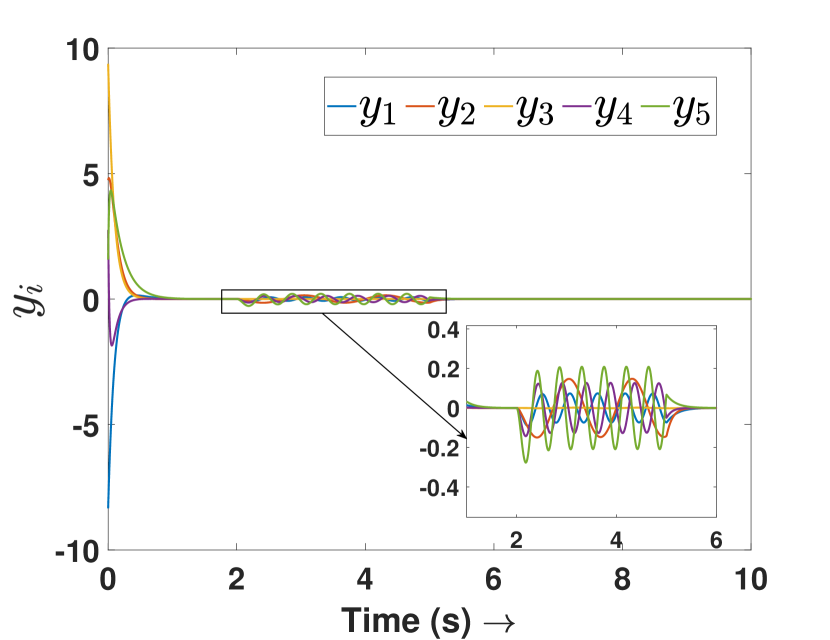
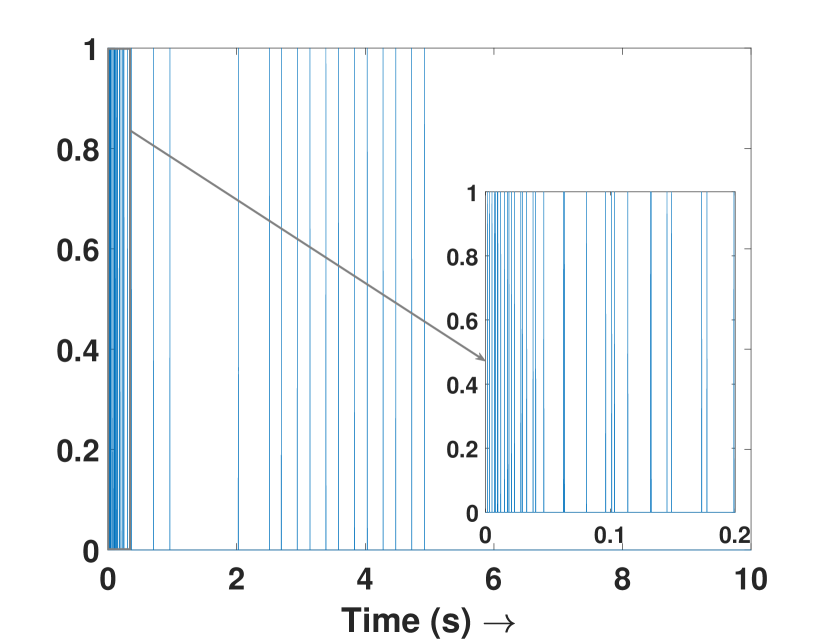
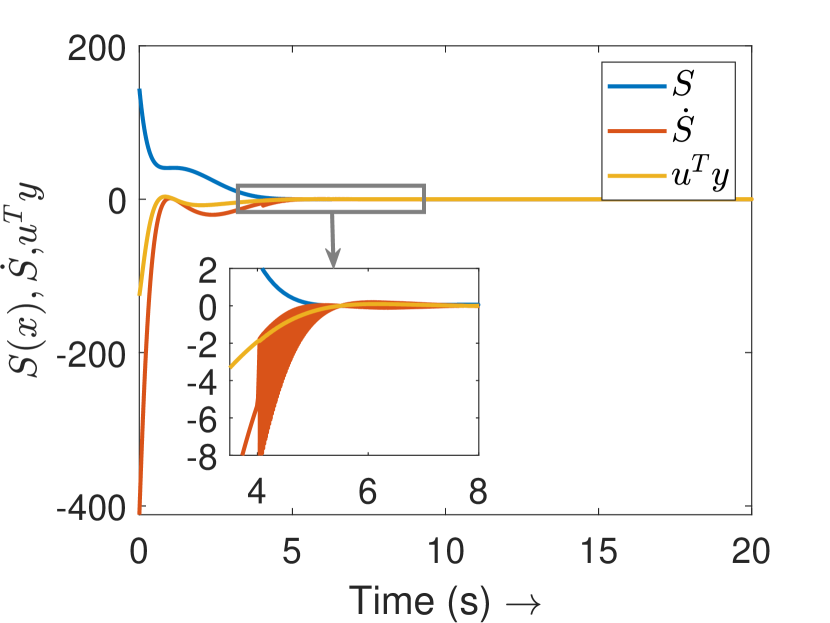
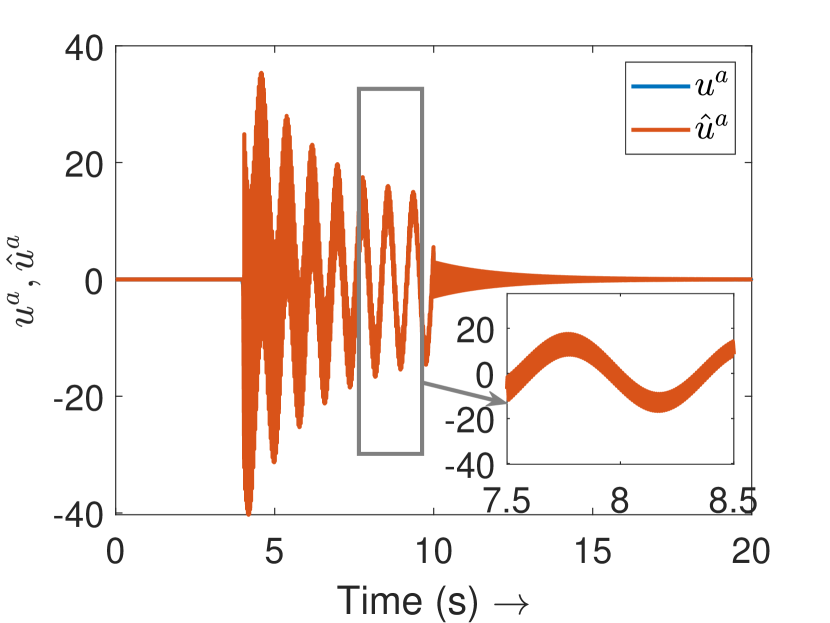
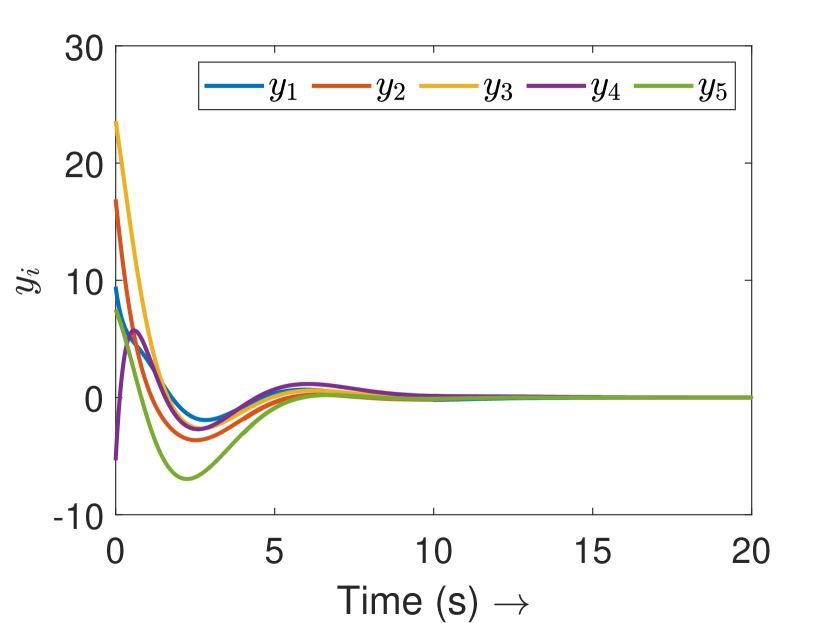
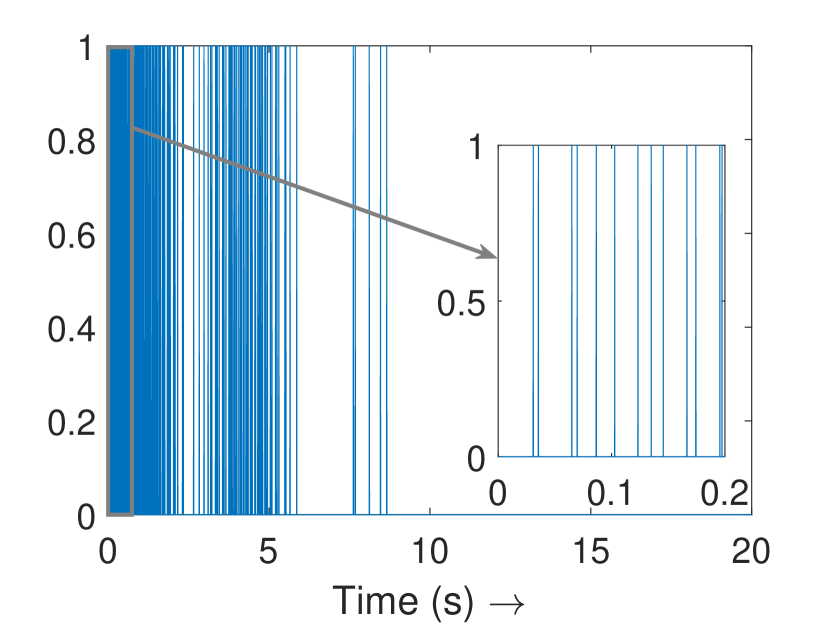
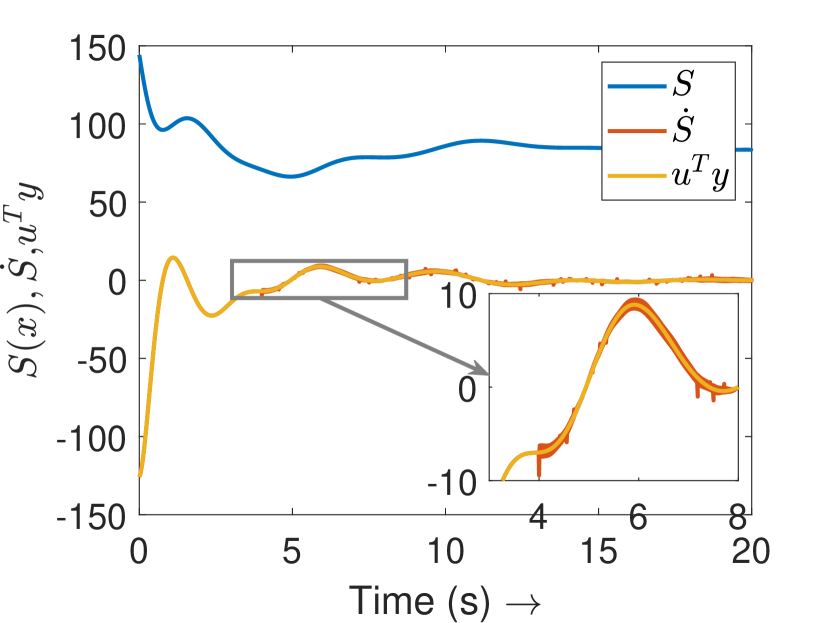
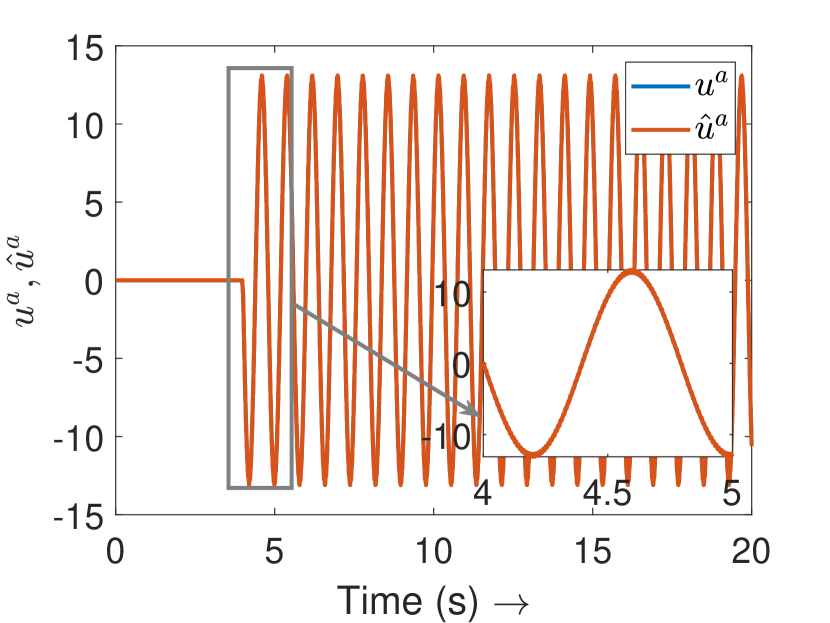
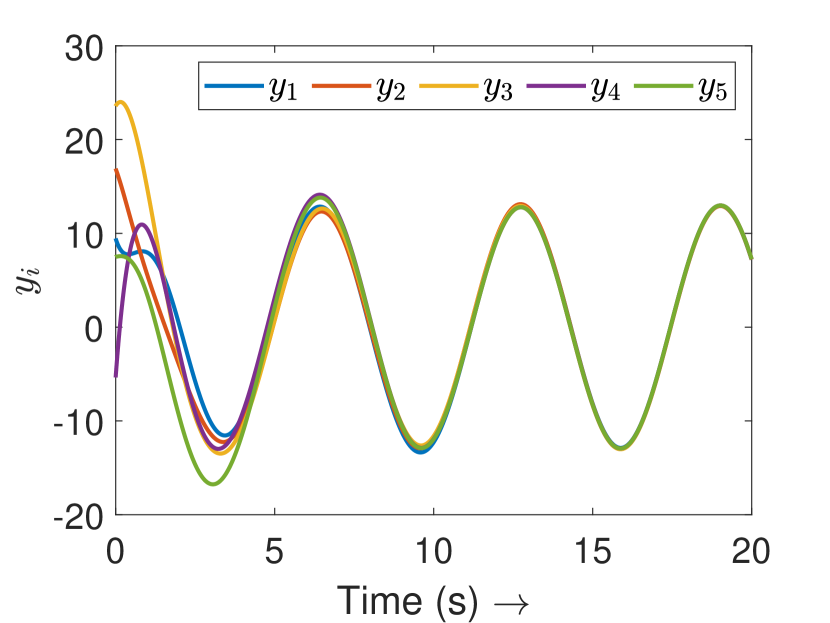
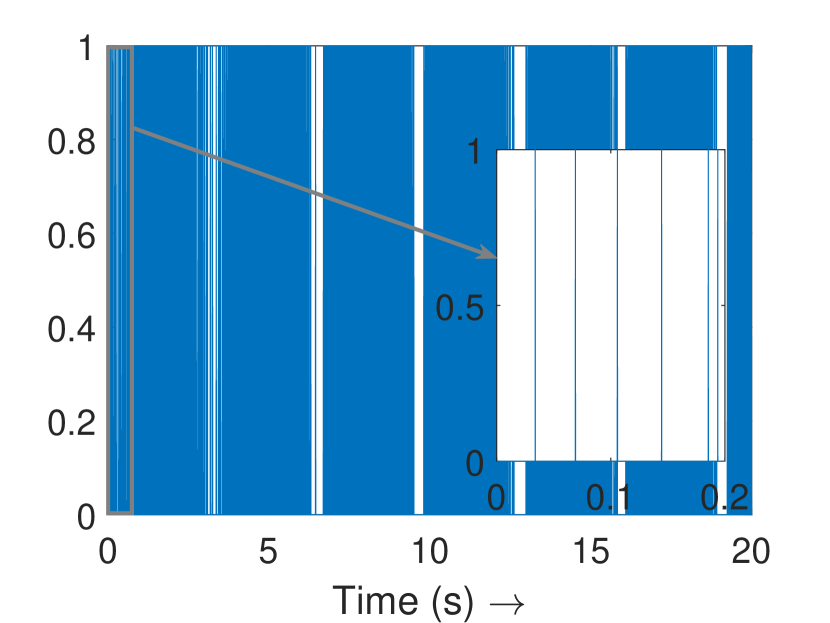
Fig. 3(a) depicts the plots for storage function , change in the stored energy , and the supplied energy for agent 4. It can be observed that the passivity is lost at s as soon as the attack begins. Consequently, the attack is detected and the controller switches to defense mode. Fig. 3(b) shows the attack estimation and the actual attack signals it is clearly visible that their difference is finite. The plots for other agents are similar and omitted for brevity. Fig. 4(a) shows that the output (of all the agents) remains bounded even under attack, as established in Theorem 4. Finally, Fig. 4(b) depicts the events generated for the observer and shows the absence of Zeno behavior. Because of the fast-moving system states, there is a higher density of events initially and during the attack period, and a lower density when the states do not change.
V-B Passive Agents with Complex Poles
Consider the network of homogeneous harmonic oscillators [27], characterized by the following matrices in (4):
is a passive system according to the positive real lemma [14, Section 6.3] and satisfy the preconditions (A1) and (A2). Figs. 5 and 6 show the simulation results for this case where conclusions, similar to the previous case, can be drawn. It is observed that the presence of complex poles degrades the attack estimation performance of the system due to the presence of oscillations in the system output.
V-C Passive Agents with Imaginary Poles
We consider the network of homogeneous harmonic oscillators [27], having the following matrices:
Again, the agents are passive and satisfy the preconditions (A1) and (A2). Figs. 7 and 8 show the simulation results for this case. It can be noted that i) the presence of imaginary poles degrades the attack estimation performance of the system, and ii) the number of events is relatively higher, as compared to earlier cases, which is expected due to the oscillating nature of output [19].
VI Conclusions
The problem of output consensus for networked linear passive agents under FDI actuator attacks is examined in this paper. To reduce the computation and communication overhead, an event-triggered observer-based switching controller was proposed in conjunction with cryptographic authentication for estimating the non-measurable states. It was shown that the proposed event condition does not result in Zeno behavior and has a positive MIET. Relying on the measurements from the observer, a passivity-based attack detection approach was presented. It was shown that the error between the estimated and the actual attack signal is norm-bounded during the controller’s functioning in the defense mode. Finally, the system was shown to achieve practical output consensus.
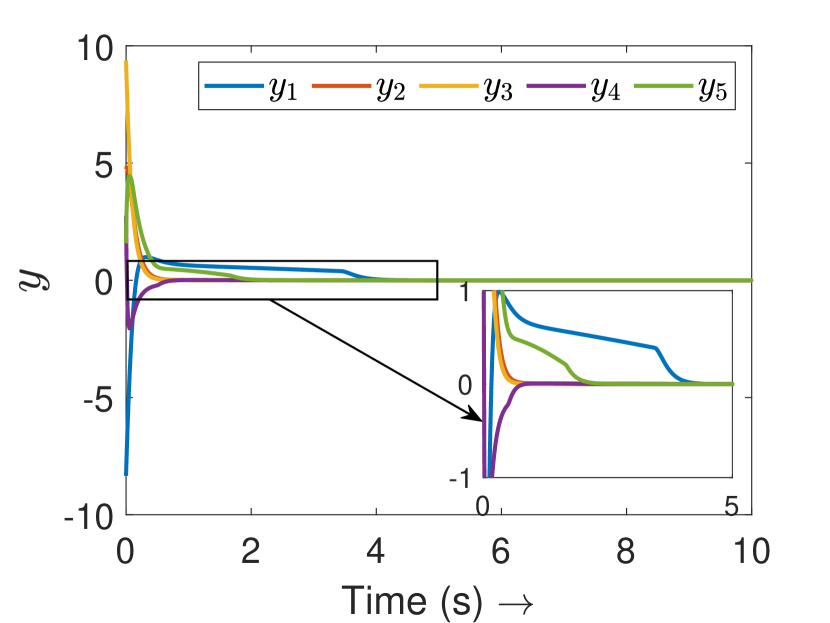
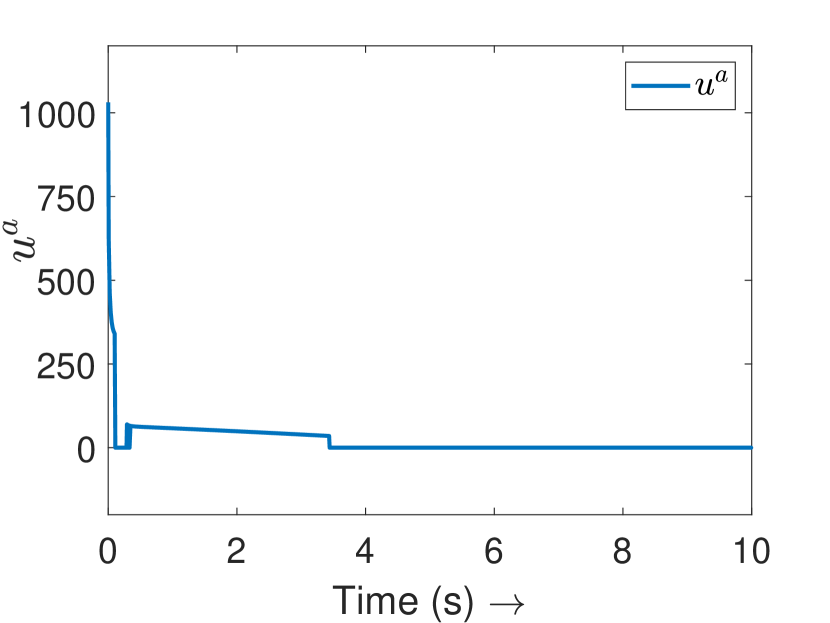
As discussed in Definition 2, only the attacks that violate the passivity condition (2) are detected and mitigated in this paper. Since undetectable attacks do not cause the system to lose passivity (Definition 2), they are not of concern as the system’s consensus properties are unaffected by such attacks. We have simulated a result in this direction as shown in Fig. 9 for the agents in Subsection V-A, which supports our claim. This happens because the total energy of passive agents approaches zero towards consensus for undetectable attacks, forcing the attack signal to eventually converge to zero to remain undetectable (see Fig. 9(b)). This shows that the undetectable attacks are decrescent with time and asymptotically converge to zero.
It would be interesting to also consider the attack on the global communication network and generalize the problem for more complex systems.
References
- [1] Francesca Boem, Alexander J Gallo, Giancarlo Ferrari-Trecate, and Thomas Parisini. A distributed attack detection method for multi-agent systems governed by consensus-based control. In 2017 IEEE 56th Annual Conference on Decision and Control (CDC), pages 5961–5966. IEEE, 2017.
- [2] Alessio Carullo, Marco Parvis, et al. An ultrasonic sensor for distance measurement in automotive applications. IEEE Sensors journal, 1(2):143, 2001.
- [3] Chi-Tsong Chen. Linear System Theory and Design. Oxford University Press, 1999.
- [4] Nikhil Chopra. Output synchronization on strongly connected graphs. IEEE Transactions on Automatic Control, 57(11):2896–2901, 2012.
- [5] Emeka Eyisi and Xenofon Koutsoukos. Energy-based attack detection in networked control systems. In Proceedings of the 3rd international conference on High confidence networked systems, pages 115–124, 2014.
- [6] Behrouz A. Forouzan. Cryptography and Network Security. McGraw-Hill Forouzan networking series. McGraw-Hill, 2008.
- [7] Chris Godsil and Gordon F Royle. Algebraic graph theory, volume 207. Springer Science & Business Media, 2001.
- [8] Haibin Guo, Jian Sun, and Zhong-Hua Pang. Stealthy false data injection attacks with resource constraints against multi-sensor estimation systems. ISA transactions, 2022.
- [9] Shicheng Huo, Ya Zhang, Frank L Lewis, and Changyin Sun. Observer-based resilient consensus control for heterogeneous multi-agent systems against cyber-attacks. IEEE Transactions on Control of Network Systems, 2022.
- [10] Ivar-André F Ihle, Murat Arcak, and Thor I Fossen. Passivity-based designs for synchronized path-following. Automatica, 43(9):1508–1518, 2007.
- [11] Xu Jin, Wassim M Haddad, and Tansel Yucelen. An adaptive control architecture for mitigating sensor and actuator attacks in cyber-physical systems. IEEE Transactions on Automatic Control, 62(11):6058–6064, 2017.
- [12] Youngjun Joo, Zhihua Qu, and Toru Namerikawa. Resilient control of cyber-physical system using nonlinear encoding signal against system integrity attacks. IEEE Transactions on Automatic Control, 66(9):4334–4341, 2020.
- [13] K-Team. KHEPERA IV NEW - K-Team Corporation. Accessed on 2023-01-19.
- [14] H.K. Khalil. Nonlinear Systems. Pearson Education. Prentice Hall, 2002.
- [15] Amir Khazraei and Miroslav Pajic. Attack-resilient state estimation with intermittent data authentication. Automatica, 138:110035, 2022.
- [16] Zhongkui Li, Xiangdong Liu, Peng Lin, and Wei Ren. Consensus of linear multi-agent systems with reduced-order observer-based protocols. Systems & Control Letters, 60(7):510–516, 2011.
- [17] Kevin M Lynch and Frank C Park. Modern robotics. Cambridge University Press, 2017.
- [18] Min Meng, Gaoxi Xiao, and Beibei Li. Adaptive consensus for heterogeneous multi-agent systems under sensor and actuator attacks. Automatica, 122:109242, 2020.
- [19] Cameron Nowzari, Eloy Garcia, and Jorge Cortés. Event-triggered communication and control of networked systems for multi-agent consensus. Automatica, 105:1–27, 2019.
- [20] Chen Peng and Hongtao Sun. Switching-like event-triggered control for networked control systems under malicious denial of service attacks. IEEE Transactions on Automatic Control, 65(9):3943–3949, 2020.
- [21] Elena Petri, Romain Postoyan, Daniele Astolfi, D Nešić, and WP Maurice H Heemels. Event-triggered observer design for linear systems. In 2021 60th IEEE Conference on Decision and Control (CDC), pages 546–551. IEEE, 2021.
- [22] Li Qin, Zhang Qingling, Zhang Yanjuan, and An Yichun. Observer-based passive control for descriptor systems with time-delay. Journal of Systems Engineering and Electronics, 20(1):120–128, 2009.
- [23] C.R. Rao, Sujit Kumar Mitra, and J.K. Mitra. Generalized Inverse of Matrices and Its Applications. Probability and Statistics Series. Wiley, 1971.
- [24] Dawei Shi, Tongwen Chen, and Ling Shi. Event-triggered maximum likelihood state estimation. Automatica, 50(1):247–254, 2014.
- [25] Sen Tan, Josep M Guerrero, Peilin Xie, Renke Han, and Juan C Vasquez. Brief survey on attack detection methods for cyber-physical systems. IEEE Systems Journal, 14(4):5329–5339, 2020.
- [26] Harry L Trentelman and Jan C Willems. Storage functions for dissipative linear systems are quadratic state functions. In Proceedings of the 36th IEEE Conference on Decision and Control, volume 1, pages 42–47. IEEE, 1997.
- [27] Tian Xia and Luca Scardovi. Synchronization of linear time-invariant systems on rooted graphs. In 2016 IEEE 55th Conference on Decision and Control (CDC), pages 4376–4381. IEEE, 2016.
- [28] Yang Yan, Panos Antsaklis, and Vijay Gupta. A resilient design for cyber physical systems under attack. In 2017 American Control Conference (ACC), pages 4418–4423. IEEE, 2017.