Neuromorphic Integrated Sensing and Communications
Abstract
Neuromorphic computing is an emerging technology that support event-driven data processing for applications requiring efficient online inference and/or control. Recent work has introduced the concept of neuromorphic communications, whereby neuromorphic computing is integrated with impulse radio (IR) transmission to implement low-energy and low-latency remote inference in wireless Internet-of-Things (IoT) networks. In this paper, we introduce neuromorphic integrated sensing and communications (N-ISAC), a novel solution that enables efficient online data decoding and radar sensing. N-ISAC leverages a common IR waveform for the dual purpose of conveying digital information and of detecting the presence or absence of a radar target. A spiking neural network (SNN) is deployed at the receiver to decode digital data and to detect the radar target using directly the received signal. The SNN operation is optimized by balancing performance metrics for data communications and radar sensing, highlighting synergies and trade-offs between the two applications.
I Introduction
Integrated sensing and communications (ISAC), a key enabling technology for 6G systems, leverages shared radio resources and hardware to realize the functions of sensing and communication. ISAC can enhance energy and spectral efficiencies by supporting context-aware decision making, whereby wireless devices, such as mobile phones and vehicles, act based on information about their surrounding environment [1].
As an example of an application that can benefit from ISAC, consider the inter-vehicle communication scenario in Fig. 1. In it, a car wishes to send a message to a second car, while also enabling the latter to detect the presence of a possible target, e.g., of a pedestrian. While conventional systems would use two separate radio resources for data transmission and radar detection, ISAC solutions reuse the same transmitted waveform for the dual role of carrier of digital information and radar signal [2, 1]. A natural radio interface to serve this dual function is impulse radio (IR), also known as ultrawideband (UWB). In fact, IR encodes information in the timing of pulses, which can in turn be repurposed for radar detection [3, 4].
This paper proposes to leverage the synergy between IR transmission and neuromorphic computing [5, 6] to realize efficient ISAC systems. Neuromorphic computing is an emerging computing technology that can efficiently process information encoded in binary signals known as spikes [7]. With the aim of reducing energy consumption and facilitating online and always-on operation on specialized hardware, as illustrated in Fig. 1, we introduce a neuromorphic ISAC (N-ISAC) receiver that leverages spiking neural network (SNN)-based processing to demodulate digital information and detect the radar signal.

I-A Related Work
IR is widely used for low-power communications, e.g., in the IEEE 802.15.4z standard [8], and is envisaged to be part of the “gearbox” of the physical layer of 6G systems [9]. Among the key advantages of IR is the possibility to implement receivers that can operate using efficient analog or neuromorphic hardware [10, 11, 12]. The integration of IR and neuromorphic computing was investigated in [5, 6], which proposed an end-to-end neuromorphic architecture for remote inference that replaces traditional digital blocks with SNNs as encoder and decoder. Hardware implementations includes [10], which introduced an IR-based communication protocol to convey digital packets between SNN chips (see also [13]); and reference [11], which proposed an all-digital spike-based IR wireless transmission scheme for miniaturized biomedical applications.
I-B Main Contributions
To our best of knowledge, this is the first work to propose the implementation of ISAC via neuromorphic computing. The main contributions of this letter are summarized as follows.
-
•
We introduce the novel N-ISAC system illustrated in Fig. 2, which exploits neuromorphic computing and IR to achieve simultaneous data transmission and target detection. The proposed SNN-based architecture demodulates digital data and detects the presence of a radar target in an online fashion;
-
•
We propose a supervised learning method for the design of the N-ISAC receiver in Fig. 2;
-
•
Numerical results are provided that demonstrate the advantages of the proposed N-ISAC system over conventional separate sensing and communication (SSAC) solutions.
II System Model
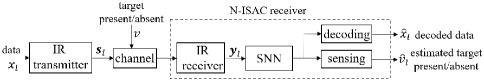
As illustrated in Fig. 1 and Fig. 2, we consider an ISAC system in which digital communication and radar sensing leverage the same IR transmitted signal. In order to efficiently and simultaneously decode the digital data and detect the possible presence of a target at a known delay cell, the receiver processes the received signal via an SNN. Given the use of time-encoded information and neuromorphic computing, we refer to the proposed system as neuromorphic ISAC (N-ISAC).
II-A IR Transmission
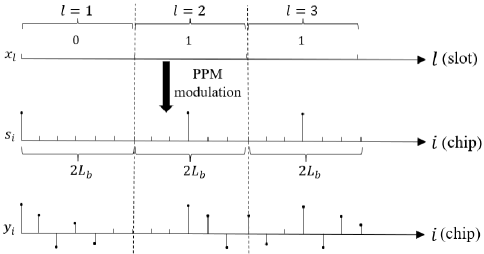
The IR transmitter modulates and transmits digital data , for each discrete-time instant , using pulse position modulation (PPM) through a single antenna. Each bit is encoded within the th time slot of duration seconds. Specifically, given an information bit sequence of bits, the PPM-modulated signal is given as [16]
| (1) |
where is the pulse waveform of bandwidth ; and is the chip time. The number of chips within each slot is , where integer is referred to as the bandwidth expansion factor. Accordingly, as illustrated in Fig. 3, in each slot , bit is encoded by a pulse on the first chip when , and by a pulse in the middle of the slot, i.e., at the th chip, when . The energy of the pulse waveform is constrained to be smaller than a given value , i.e., .
II-B Multipath Channel and Radar Target
The modulated signal is transmitted over a multi-path fading channel to the receiver. The multi-path channel depends on the possible presence of a radar target, as well as on scatterers located between the transmitter and receiver that act as clutter for radar processing. We use the binary variable to indicate the presence or absence of the radar target, identified respectively by setting and . Specifically, following a standard radar model (see, e.g., [17]), we assume that a target may or may not be present at a radar cell corresponding to a known propagation delay . Accordingly, the continuous-time channel response can be expressed as
| (2) |
where is the receiver filter response, which is matched to the transmitted waveform ; the amplitude of the target follows a complex Gaussian distribution with power , i.e., ; and the amplitudes of the clutter components are independent with uniform phases and Weibull absolute values having shape parameter and scale parameter [17]. With , the amplitudes are complex Gaussian random variables [17]. The amplitudes and and delays are assumed to be unknown.
We note that the model (2) could be generalized to allow for a time-varying presence/absence pattern for the target, in the sense that the variable could change over the time slot index . We will not consider this situation in this paper, although the extension is straightforward.
II-C Receiver Processing
The signal obtained by the single-antenna receiver is given by
| (3) |
where the channel response is given in (2); is additive white Gaussian noise with power spectral density ; and “” denotes the convolution operation. The receiver samples the received signal at the chip rate , yielding the discrete-time signal , for . For each slot time , we collect the samples , with . Assuming a maximum delay spread , upon sampling, the effective discrete-time channel has taps. Accordingly, the channel between the transmitter and the receiver is described by the vector . Note that, if , there is no interference between pulses transmitted in successive slots; while, otherwise, transmission of the pulse encoding the th bit may interfere with the pulse encoding the following bits .
Using (3), the received discrete-time signal for the th chip can be expressed as
| (4) |
where we have defined the vector , with and if ; and are the noise samples, where is the pulse bandwidth. By the assumed PPM scheme, for each slot , we have all zero samples except for one sample, namely if and if .
The receiver feeds the received samples to the SNN successively for each slot . To this end, we collect the received samples corresponding to the time slot into a vector . Since is generally complex, we define the real-value vector
| (5) |
with and being the element-wise real and imaginary parts of the input vector, respectively. The received signal is input to the SNN at each time step .
As described in the next section, an SNN is a recurrent discrete-time model that operates along the slot index . It takes as input the real samples , with one output neuron producing the decoding output , which provides an estimate of the data symbol , and the other output neuron producing the sensing output , which estimates the binary variable representing the presence or absence of the target. Note that the detection decision about the target varies over time as more information is acquired by the receiver.
III Neuromorphic Receiver Processing
In this section, we first describe the SNN model used at the receiver, and then we detail the proposed data-aided optimization of the model parameters of the SNN.
III-A Spiking Neural Network Model
An SNN is specified as a network connecting a set of spiking neurons via an arbitrary directed graph, in which a directed edge represents a synapse. To model the spiking neurons, we adopt the standard discrete-time spike response model (SRM), in which each spiking neuron outputs a binary signal , with “1” representing the emission of a spike and “0” an idle neuron at time step . Each neuron maintains an internal analog state variable , known as the membrane potential, over time step .
The membrane potential evolves over time as a function of the spikes that neuron receives from the neurons that have synapses ending at neuron . The neuron spikes when the membrane potential crosses a threshold, after which the membrane potential is reduced below the threshold. Mathematically, the membrane potential is defined by the sum of filtered contributions from incoming spikes and from the neuron ’s own past outputs. Accordingly, the evolution of the membrane potential is modelled as
| (6) |
where is the set of neurons with synapses ending at neuron ; is the synaptic weight between neuron and neuron ; represents the synaptic response to a spike from a neuron ; describes the synaptic response to the spike emitted by neuron itself; and “” is the convolution operator. Typical choices for synaptic spike responses include the first-order feedback filter , and the second-order synaptic filer , for , with finite positive constants , and . We refer to [18, 19] for further details.
Neuron outputs a spike at time step if its membrane potential passes some fixed threshold . Accordingly, the output of neuron can be expressed as
| (7) |
where is the Heaviside step function ( if and otherwise). We denote as the vector of all parameters for the SNN of the receiver.
The SNN at the receiver has two read-out neurons producing decisions and . Denoting as the index of the communication readout neuron, and as the index of the radar readout neuron, by (7) we have the estimates and .
III-B Optimization
To optimize the model parameters of the SNN, we adopt a supervised learning approach, and we assume the availability of a dataset consisting of examples of the form . Each example contains the sequence of transmitted bits with ; the corresponding received samples obtained via (5); and the binary value indicating the presence or absence of the target, which is assumed to be the same across samples. For each example , at each th step, the received signal serves as input to the SNN, while and are ground-truth labels for data decoding and target detection, respectively.
To define the training criterion, we evaluate the performance of communication and sensing via two separate cross-entropy losses. To this end, defining the sigmoid function , we write the probability of the communication readout neuron to produce the estimate ; and the probability of the radar readout neuron to produce the estimate . They are both functions of the model parameters . The training loss related to data decoding is then measured by the cross-entropy loss
| (8) |
while the training loss for sensing is similarly defined as
| (9) |
The overall training losses for each data point are defined as the sums over time and . For the considered SNN architecture, we adopt the weighted sum
| (10) |
of the communication and sensing losses, where is a weight factor determining the relative priority between the two losses. The model parameters are updated based on stochastic gradient descent (SGD). To this end, we address the nondifferentiable threshold activation (7) via surrogate gradient [20] by replacing the Heaviside step function in (7) with a differentiable surrogate function, namely the sigmoid , during training.
IV Experiments
In this section, we provide experimental results on the proposed N-ISAC system. We start by describing setting and benchmarks.
IV-A Setting
The system operates over slots. The information bits and target are i.i.d. generated as -Bernoulli variables, i.e., , and . The target delay is set to , and the amplitudes are all i.i.d. variables, while the delays are uniformly distributed between 0 and . We set the number of clutter paths in the channel (2) as . We generate training examples and test examples as described in Section II-B. The SNN has a fully connected architecture with a single hidden layer, with input neurons and or hidden neurons. The average signal-to-noise ratio (SNR) is defined as , where is the average squared norm of the channel. We set the SNR to dB.
IV-B Benchmark
For comparison, we consider a conventional SSAC scheme. SSAC divides the slots into slots used to transmit information, and slots used for radar sensing, where . The transmitted signal for radar sensing is given by the PPM waveform (1) with bits fixed to . For SSAC, two SNNs are implemented at the receiver, one performing data decoding for the first slots, and the other responsible for radar sensing in the rest of the time slots. The architecture of both SNNs is as described above, with each SNN having hidden neurons.
IV-C Results
We adopt the following performance metrics for data transmission and radar sensing:
-
•
Normalized test throughput, i.e., the ratio of the average number of correctly decoded bits over the total number of time slots ;
-
•
Radar test detection error, i.e., the probability that the sensing decision is not correctly taken upon processing all time slots. The final decision for each example is made based on the majority rule, predicting the presence of a target if the SNN produces the decision for a majority of the time slots .
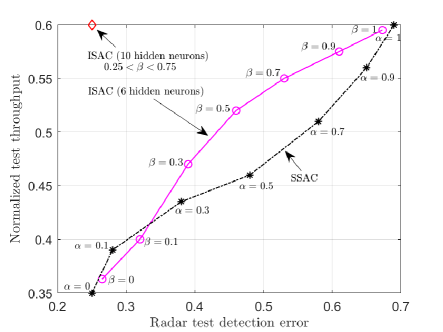

We demonstrate the normalized test throughput versus the radar test detection error for ISAC and SSAC when there is no bandwidth expansion, e.g., for , in Fig. 4. For the ISAC scheme, we vary in the loss (10), while we change the fraction for SSAC. As increases, more priority is given by ISAC to communication over radar detection; and, similarly, as increases, SSAC assigns more slots to communications. The performance of ISAC with an SNN having hidden neurons is essentially independent of for any . A first observation is that, for SSAC, there is a trade-off between communication and sensing performance levels caused by the slot allocation. A similar trade-off is also observed for ISAC when using an SNN with hidden neurons. This is due to the limited capacity of the shared common hidden layer of the SNN. In contrast, when hidden neurons are available at the SNN, ISAC is seen to optimize both data decoding and target sensing performance, obtaining significant gains over SSAC.
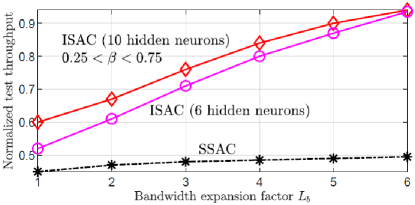
In Fig. 5, we demonstrate the normalized test throughput and radar test detection error versus the bandwidth expansion factor for ISAC and SSAC by setting . Both ISAC and SSAC are observed to benefit from the bandwidth expansion due to the reduced inter-slot interference. However, the throughput achievable by SSAC is bounded by , while ISAC can obtain larger throughputs; and a similar behavior is observed also in terms of the probability of detection error. Furthermore, when the bandwidth expansion is sufficiently large, e.g., when , ISAC with hidden neurons obtains a similar performance as that with neurons, which indicates a larger bandwidth simplifies receiver design in terms of SNN’s capacity.
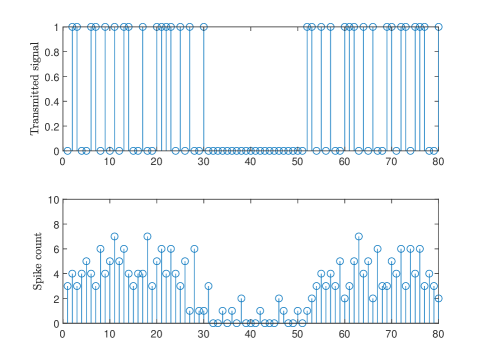
Finally, Fig. 6 illustrates how the SNN receiver can leverage the temporal sparsity of the IR signals to enhance energy efficiency. In this regard, we recall that energy consumption in an SNN is essentially proportional to the number of spikes produced by the SNN, given extremely low idle energy of neuromorphic chips [7]. The top panel shows the transmitted IR signal consisting of two frames of transmitted signals with , separated by an idle frame of duration of slots. We observe that in the idle frame, the spike count is significantly reduced, showing that the neuromorphic receiver can adjust its energy consumption to the activity level of the transmitter.
V Conclusions
In this paper, we have proposed a novel ISAC solution that leverages the synergy of neuromorphic computing and IR transmission for both data transmission and radar detection. Data are encoded on an IR waveform that is used for the dual purpose of data decoding and target sensing. A SNN-based receiver architecture is considered to estimate data and the presence/absence of a target. Experiments have demonstrated the advantage of the proposed neuromorphic ISAC over conventional separate sensing and communications in terms of normalized test throughput and radar test detection error. We have also highlighted the capacity of the neuromorphic receiver to adapt its computing energy consumption to the activity level of the transmitter.
References
- [1] F. Liu, C. Masouros, A. P. Petropulu, H. Griffiths, and L. Hanzo, “Joint radar and communication design: applications, state-of-the-art, and the road ahead,” IEEE Transactions on Communications, vol. 68, no. 6, pp. 3834–3862, 2020.
- [2] S. Jeong, O. Simeone, A. Haimovich, and J. Kang, “Beamforming design for joint localization and data transmission in distributed antenna system,” IEEE Transactions on Vehicular Technology, vol. 64, no. 1, pp. 62–76, 2014.
- [3] A. Nezirovic, A. G. Yarovoy, and L. P. Ligthart, “Signal processing for improved detection of trapped victims using UWB radar,” IEEE Transactions on Geoscience and Remote Sensing, vol. 48, no. 4, pp. 2005–2014, 2009.
- [4] C. Zhang, M. J. Kuhn, B. C. Merkl, A. E. Fathy, and M. R. Mahfouz, “Real-time noncoherent UWB positioning radar with millimeter range accuracy: theory and experiment,” IEEE Transactions on Microwave Theory and Techniques, vol. 58, no. 1, pp. 9–20, 2009.
- [5] N. Skatchkovsky, H. Jang, and O. Simeone, “End-to-end learning of neuromorphic wireless systems for low-power edge artificial intelligence,” in Proc. Asilomar Conference on Signals, Systems, and Computers, pp. 166–173, 2020.
- [6] J. Chen, N. Skatchkovsky, and O. Simeone, “Neuromorphic wireless cognition: event-driven semantic communications for remote inference,” arXiv preprint arXiv:2206.06047, 2022.
- [7] M. Davies, N. Srinivasa, T.-H. Lin, G. Chinya, Y. Cao, S. H. Choday, G. Dimou, P. Joshi, N. Imam, S. Jain et al., “Loihi: A neuromorphic manycore processor with on-chip learning,” IEEE Micro, vol. 38, no. 1, pp. 82–99, 2018.
- [8] M. Z. Win and R. A. Scholtz, “Impulse radio: how it works,” IEEE Communications letters, vol. 2, no. 2, pp. 36–38, 1998.
- [9] G. P. Fettweis and H. Boche, “6G: the personal tactile Internet—and open questions for information theory,” IEEE BITS the Information Theory Magazine, vol. 1, no. 1, pp. 71–82, 2021.
- [10] A. Cassidy, Z. Zhang, and A. G. Andreou, “Impulse radio address event interconnects for body area networks and neural prostheses,” in Proc. IEEE Argentine School of Micro-Nanoelectronics, Technology and Applications, pp. 87–92, 2008.
- [11] A. Shahshahani, M. Shahshahani, P. M. Ros, A. Bonanno, M. Crepaldi, M. Martina, D. Demarchi, and G. Masera, “An all-digital spike-based ultra-low-power IR-UWB dynamic average threshold crossing scheme for muscle force wireless transmission,” in Proc. IEEE Design, Automation & Test in Europe Conference & Exhibition (DATE), pp. 1479–1484, 2015.
- [12] Z. Jouni, T. Soupizet, S. Wang, A. Benlarbi-Delai, and P. M. Ferreira, “1.2 nW neuromorphic enhanced wake-up radio,” in Proc. ACM IEEE Symp. Integr. Circuits Syst. Design, 2022.
- [13] F. Roth, N. Bidoul, T. Rosca, M. Dörpinghaus, D. Flandre, A. M. Ionescu, and G. Fettweis, “Spike-based sensing and communication for highly energy-efficient sensor edge nodes,” in Proc. IEEE International Symposium on Joint Communications & Sensing (JC&S), pp. 1–6, 2022.
- [14] J. A. Zhang, F. Liu, C. Masouros, R. W. Heath, Z. Feng, L. Zheng, and A. Petropulu, “An overview of signal processing techniques for joint communication and radar sensing,” IEEE Journal of Selected Topics in Signal Processing, vol. 15, no. 6, pp. 1295–1315, 2021.
- [15] Z. Xiao and Y. Zeng, “Integrated sensing and communication with delay alignment modulation: performance analysis and beamforming optimization,” arXiv preprint arXiv:2207.03647, 2022.
- [16] M. Z. Win and R. A. Scholtz, “Ultra-wide bandwidth time-hopping spread-spectrum impulse radio for wireless multiple-access communications,” IEEE Transactions on Communications, vol. 48, no. 4, pp. 679–689, 2000.
- [17] D. A. Shnidman, “Generalized radar clutter model,” IEEE Transactions on Aerospace and Electronic Systems, vol. 35, no. 3, pp. 857–865, 1999.
- [18] N. Skatchkovsky, H. Jang, and O. Simeone, “Spiking neural networks—Part II: Detecting spatio-temporal patterns,” IEEE Communications Letters, vol. 25, no. 6, pp. 1741–1745, 2021.
- [19] H. Jang, O. Simeone, B. Gardner, and A. Gruning, “An introduction to probabilistic spiking neural networks: probabilistic models, learning rules, and applications,” IEEE Signal Processing Magazine, vol. 36, no. 6, pp. 64–77, 2019.
- [20] E. O. Neftci, H. Mostafa, and F. Zenke, “Surrogate gradient learning in spiking neural networks: bringing the power of gradient-based optimization to spiking neural networks,” IEEE Signal Processing Magazine, vol. 36, no. 6, pp. 51–63, 2019.