Mitigation of Cyberattacks through Battery Storage for Stable Microgrid Operation
Abstract
In this paper, we present a mitigation methodology that leverages battery energy storage system (BESS) resources in coordination with microgrid (MG) ancillary services to maintain power system operations during cyberattacks. The control of MG agents is achieved in a distributed fashion, and once a misbehaving agent is detected, the MG’s mode supervisory controller (MSC) isolates the compromised agent and initiates self-healing procedures to support the power demand and restore the compromised agent. Our results demonstrate the practicality of the proposed attack mitigation strategy and how grid resilience can be improved using BESS synergies. Simulations are performed on a modified version of the Canadian urban benchmark distribution model.
Index Terms:
Cyber-physical microgrids, battery energy storage systems, attacks, detection, mitigation.I Introduction
In recent decades, the power grid has undergone significant overhauls. Microgrids (MGs), demand response schemes, day-ahead markets, etc. support the provision of flexible energy to consumers, overcoming the dependence on centrally generated energy from geographically dispersed facilities. Inverter-based resources (IBRs) and battery energy storage systems (BESS) contribute significantly to this end, while alleviating power consumption “hotspots” supporting peak-shaving mechanisms.
As information and communication technologies are incorporated into power systems to harness the advantages of the deployed distributed generations (DGs), the threat landscape of such cyber-physical energy systems (CPES) is expanded. Thus, it is crucial to realize security mechanisms that can effectively detect malicious grid behavior and leverage the power grid’s resources to overcome such adverse phenomena. Diverse cyberattacks targeting different layers of CPES have been explored in literature [1]. For instance, attacks could target the communication between DGs, delaying or modifying packages, thus causing denial-of-service (DoS) attacks [2]. Attackers could also perform firmware modification attacks on IBRs that lead to uneconomical system operation or even trigger blackouts and jeopardize grid equipment [3].
To harden CPES against adversaries, compound security and intrusion-tolerant mechanisms, that can detect anomalous behavior and proactively perform remediation actions, leveraging system resources need to be automated. For example, in [4], the authors propose the use of matrix subspace methods for the detection of cyberattacks targeting autonomously operating MGs and present the potential impact of such attacks if not immediately identified. The importance of system resources, such as BESS, in supporting ancillary services of the grid is discussed in [5]. Different scenarios are presented where BESS can be used to minimize power fluctuations, regulate grid voltage and frequency, and support distributed systems under cyberattacks or other unexpected conditions. In [6], the authors present an algorithm that can coordinate the contribution of distributed energy resources (DERs), in terms of active and reactive power, thus enhancing the stability of the system.
Control strategies have also been employed to maintain security and resiliency in CPES [7]. For instance, a control mechanism, leveraging power sharing between multiple energy storage resources, to regulate the frequency and voltage in autonomous MGs is proposed in [8]. A resilient controller for multi-agent systems under sensor and actuator attacks is presented in [9]. The control follows the leader-follower scheme where the leader indicates the objectives that the follower agents should track. Similarly, two distributed control strategies utilizing a consensus-based leader-follower approach are demonstrated in [10]. In both schemes, the agents’ behavior is monitored for malicious actions and a linear quadratic regulator problem is defined to ensure the optimal power exchange between multiple storage resources. In [11], an acknowledgment-based detection algorithm is presented that serves as a preliminary step before recovering the compromised grid agents. The successful agent recovery is contingent upon the capability of the BESS to support power demand and meet the operation and transient constraints of power systems. Hence, an adapted secondary control scheme is proposed to maintain the frequency within acceptable limits.
The contribution of this work aims to leverage both aforementioned verticals, i.e., control and BESS resource allocation, and provide an automated and resilient methodology for the detection of maliciously operating DG agents in a MG setup. By isolating the affected DGs, their behavior can be detained safeguarding the operation of the rest of the grid. Then, leveraging the BESS resources, the power demand of the compromised (islanded DG) can be supplied while the MG system operator attempts to reactively restore the misbehaving agent to an trusted operating condition.
The rest of the paper is structured as follows. Section II presents the cyber and physical system modeling of this work. Section III details the attack preliminaries and describes the cyber-attack mitigation methodology leveraging BESS resources, while Section IV provides the experimental evaluation of our approach. Last, Section V concludes the paper and provides directions for future work.
II Microgrid model and Control Objectives
Centralized, decentralized, and distributed controls are commonly used in MGs. Although centralized control can monitor the entire system operation and realize accurate power sharing between converters, the communication burden limits its application to large-scale systems. Decentralized control alleviates the single point of failure and the communication overheads as it depends on local information. In contrast, distributed control reduces the overall communication dependency by utilizing local data from neighboring nodes.
II-A Cyber Layer Modeling
Distributed control schemes utilize peer-to-peer communication between neighboring nodes via sparse distributed communication networks. The communication network can be seen as a topological map represented by an undirected graph with nodes , and edges . If , the nodes and are adjacent, thus can exchange information through the communication network. is the adjacency matrix with non-negative adjacency elements, i.e., , and . The neighbors of node are defined as .

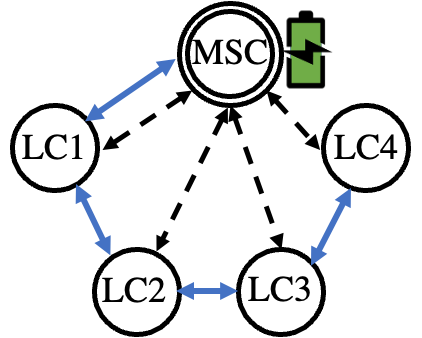
In this work, a modified version of the Canadian urban benchmark distribution system is utilized to demonstrate the leader-follower distributed control scheme, shown in Fig. 1 with blue color. It is considered that each converter has a local controller (LC), operating under such control. The data is exchanged between neighboring nodes to achieve primary control objectives, where are the active and reactive power sharing values. For example, LC2 communicates and collects the data from LC1 and LC3, which can be represented as LC2 , where and are the data collected from LC1 and LC3 and transferred to LC2, respectively. Furthermore, a mode supervisory controller (MSC) is placed close to the point of common coupling (PCC), which can exchange measurements and multicast signals to the respective LCs, realizing secondary control objectives.
II-B Physical Layer Modeling
DGs can be integrated into an AC MG through power converters. When the MG is connected to the main grid, known as the grid-tied mode, the converters perform as current-controlled sources. The MG voltage and frequency are mainly regulated by the main grid. Otherwise, when the MG is disconnected from the main grid, known as the grid-forming or islanded mode, it will be stabilized by the converters which can operate in voltage-source or current-source mode. The modeling of MGs operating in their autonomous mode is investigated in this work. Furthermore, we leverage BESS resources to overcome adverse deliberate scenarios. Droop control is widely utilized to share power among parallel-connected converters and improve system reliability by imitating the parallel operation behavior of synchronous generators. It is considered an independent or autonomous form of control since it maintains stability while eliminating the synchronous communication requirement between grid converters [12].
In order to model the MG system, we consider nodes consisting of loads and DGs (e.g., renewable sources or energy storage systems). The complex power delivered to the MG from the converter on node can be calculated by , where represents the grid voltage and is the current injected into the grid. Thus, the converter active and reactive power output can be expressed as Eq. (3), where is the converter output voltage and represents the output filter and line lumped impedance between the converter and grid.
| (3) |
When the phase difference is small enough and impedance is assumed to be purely inductive with , the and droop control characteristic, also known as primary control, can be described by Eq. (4), where and are the angular frequency and converter output voltage of the inverter, respectively, with and when there is no load, and and are the droop coefficients.
| (4) |
Although the droop control can achieve independent active and reactive power control in the primary level or converter level without intercommunication between nodes, secondary level or system level control can assist in compensating the frequency and voltage deviation caused by the primary level droop control. In the distributed control scheme under investigation, the secondary level control takes the voltage () and frequency () of the PCC point. Ultimately, the droop control can be formulated as Eq. (5), where and are the secondary frequency and voltage contribution, respectively.
| (5) |
In terms of Eqs. (3) – (5), a converter can be linearized as the following state-space model in Eq. (6) with inputs, states, and outputs [13]. The state derivatives are calculated using the state variables at time and system control input . is the system output (sensor measurements). , , are the state, control, and output matrices of the physical system and denotes the noise vector of sensed measurements.
| (6) |
The state variable and control input are expressed as: where , , , , , are the - and -axis output currents, output voltages, and currents of the converter.
III BESS Mitigation Methodology
In this section, we define adversarial capabilities and attack assumptions. We detail the formalization for the leader-follower distributed control scheme and provide constraints for the BESS nominal operation. Finally, we discuss the malicious agent detection methodology and designate the steps of our proposed BESS-assisted MG self-healing mechanism.
III-A Adversary and Attack Model
We consider an adversary capable of attacking the cyber/communication layer by sending incorrect measurements to deceive the surrounding nodes. The actual measurement – forwarded to the nodes – changes to once the vulnerability of the communication channel between these neighboring nodes is exploited, where denotes an attacked channel. Since the relationship between the received measurements () and the control signals () can generally be expressed as in Eq. (7), where is a feedback control gain [14], when the controller takes the malicious measurement instead of the true measurement , where , the control scheme is misled by the attacker.
| (7) |
To establish such attacks targeting measurement signals, several models can be utilized [15]. The attack measurement can be described by , where is the true measurement, and is the attack duration between and .
III-A1 The scaling attack
This type of attack could increase or reduce times the measurement from the actual value by using the scaling attack vector as shown in Eq. (10).
| (10) |
III-A2 The additive attack
It adds an additive attack vector on the original measurement during the attack period.
| (13) |
III-A3 The ramping attack
The attack vector is multiplied by the time scaling factor as following:
| (16) |
We assume that there are two ways to inject the signal of such attacks. The constant signal is considered a one-time attack, where the attacker implements the attack in a specific instant (e.g., ). Another is called a periodic signal, where the attacker repeatedly injects malicious vectors within a period (e.g., ). Specifically, when information is transferred between nodes through the cyber layer, the active and reactive power of neighboring converters can be manipulated. The primary droop control scheme can be deceived if malicious measurements are considered. Therefore, the system frequency and voltage stability are disturbed directly via droop control with incorrect (manipulated) measurements.
III-B Distributed Control for Agent Systems
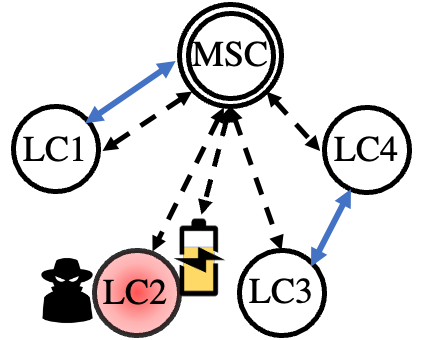
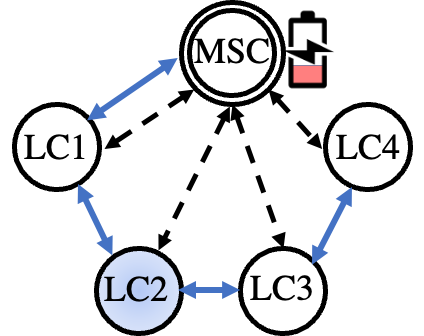
Leveraging the cyber modeling (Section II-A), we opted for a leader-follower consensus scheme to harden the control of MG agents in the presence of adversaries [10]. Fig. 2 depicts the communication architecture of the leader-follower scheme under nominal operation (Fig. 2a), unexpected conditions (Fig. 2b), where the malicious agent is removed from the distributed consensus set, and after agent restoration (Fig. 2c). In Fig. 2, the blue arrows represent the communication links between neighboring agents (exchanging information for their distributed primary control objectives), while the dashed arrows illustrate the information exchanged between MSC and DG agents (e.g., secondary control objectives, BESS coordination, MG restoration commands, etc.). Access to every agent is maintained at all times by the MSC leader (dashed arrows). In such a distributed control system, the agents’ (i.e., DGs) objective is to track the state of the leader. The control goal at time for the agent is described by Eq. (17) [10].
| (17) |
where , , and are the state information, the control input, and the element of the adjacency matrix for the agent at time . Agent is the leader and its corresponding state that the rest of the agents need to track is . is the local control gain and is equal to if the control information originates from the leader, else it is . In leader-follower distributed control schemes, the DG LCs are responsible to track the operational system state as indicated by the leader. As a result, to attain consensus between all system nodes Eq. (18) needs to be satisfied.
| (18) |
III-C Microgrid Recovery Mechanism using Energy Storage
In our case, the leader of the system is MSC. The MSC monitors and supervises the nominal operation of the system by issuing control commands to the DG agents, enforcing the economic operation, managing the BESS resources (at the PCC), and providing remediation actions in case of adverse events. For instance, after the detection of a misbehaving agent [4], the leader will issue a disconnect command to the circuit breaker (CB) of that agent and at the same time instruct the remaining DG agents to remove the node from their consensus set. Recovery of the compromised agent will then be initiated with coordination between the affected node and the MSC. Leveraging the BESS reserves, the MSC will attempt the recovery of the maloperating DGs. The process is performed according to the secondary frequency control mechanism (Eq. (5)). The automatic recovery of the abnormally operating DGs can be performed granted that Eqs. (19) – (21) are satisfied. However, if BESS storage cannot meet the power demand, MSC will enforce incremental load shedding to maintain critical loads online until the agent recovery.
| (19) | |||
| (20) |
where and are the minimum and maximum limits of power that the BESS can supply, respectively, and and describe the state-of-charge (SOC) range within which the BESS should be operated.
| (21) |
Furthermore, the frequency of the DG when supported by BESS () should be regulated to the reference frequency within the system settling timing constraint .
III-D Malicious Agent Behavior Mitigation
In the event of a cyberattack or an arbitrary adverse fault condition, one or more agents might start operating erroneously. Fault conditions are efficiently detected as they violate the system semantics in a congruent way, and automated mitigations to overcome such diverse effects are built-in within critical systems such as power grids. On the other hand, a cyberattack will manipulate an agent’s operation in an “indistinguishable from normal” manner, by poisoning the information it shares with other agents, causing communication delays, blocking the data exchanged between agents, corrupting the control inputs to the underlying LC devices (within the DG), etc. By propagating the compromised information to the rest of the agents, the distributed control scheme can also be corrupted, hence jeopardizing the efficient operation of the whole MG. For instance, the state information of the compromised agent can be described using Eq. (17).
| (22) |
where follows Eq. (7), and includes the attacked measurement components under attack models of Eqs. (10) – (16).
It is crucial for the MG system operation to detect and mitigate the effects of maliciously operating agents before their propagation to the system. For the detection of such conditions, different approaches have been pursued in the literature. Related work leverages acknowledgment-based messages exchanged between nodes that should arrive within predefined time limits to verify the nominal agent behavior [11, 10]. Other approaches utilize anomaly detection or reputation-based schemes to detect misbehaving agents [16].
Our methodology is based on the leader-follower control mechanism and leverages the information exchanged between DG agents and the MSC (e.g., system states) to identify suspicious behavior. Namely, conventional state estimation algorithms, targeted at transmission systems, cannot be applied to distribution systems as in our case. System state observability is limited in DGs due to the lack of temporal granularity, accuracy, and synchronization in the system measurements (contrary to the measurements provided by phasor measurement units in transmission systems). As a result, to improve the fidelity of the DG system models, synthetic or other data (from microPMUs, smart meters, DER assets, etc.) are used to enhance the accuracy of state estimation [17].
Physics-informed methodologies considering the dynamics of power system assets, and their response (in attack-free cases and/or during different perturbations) have been explored in literature for the attack detection [18, 4]. In this work, we utilize a threshold-based approach where the cyber-physical properties of the system, i.e., state information in Eq. (LABEL:eq:xandu), are supplemented with the DG inverter’s controller dynamics, i.e., settling time, total harmonic distortion (THD), etc., and can signal abnormal operation. To maintain stable operation, acceptable levels for such properties in the attack-free case are defined by the system operators and device vendors [19]. The data collected during the DG operation account for measurement noise and other transient events that could occur during the system operation. As a result, custom-built system-specific models are developed for each DG (in the attack-free case). However, during malicious operations, including additive, scaling, or ramp attacks, the behavior of compromised agents can diverge from their expected values, as can be seen in Fig. 3. Leveraging the custom-built data-driven DG models, cyberattacks can be distinguished from nominal behavior and/or other anomalous conditions (e.g., faults).
Once abnormal agent behavior is identified, the MSC immediately issues an islanding command disconnecting the attacked DG from the system detaining the attack propagation to the rest of the DGs. Furthermore, the local communication links between the compromised agent and its neighbors are disconnected, as can be seen in Fig. 2b, to limit the spread of untrustworthy false data (e.g., active, reactive power information). In the event that multiple DG agents are compromised simultaneously, the detection and isolation steps remain the same. However, the restoration process will differ since resources will have to be optimally allocated based on different criteria, e.g., load criticality, dispatchable BESS units, etc.
After the DG isolation, i.e., while operating in autonomous mode, the MSC will attempt the recovery of the compromised DG. The self-healing process can be performed either in coordination with the DG unit (if the controller has the ability to overcome the attack) or in a supervisory mode. In the latter case, which is presented in this work, the MSC (leader) will decouple the compromised unit (e.g., the inverter within the DG), and utilize the available BESS resources to supply the power demand of the DG. Granted that the BESS can support the corresponding demand (Eqs. (19)–(21) are satisfied), the agent will be seamlessly reconnected with the rest of the system (plug-and-play capability). Once agent reconnection has succeeded, the MSC will attempt a black-start, that is, rebooting and restoring the DG inverter controller to a safe operational mode [20]. Contrary to transmission systems, the radial nature of distribution systems, i.e., low connectivity index, allows the concurrent restoration of multiple DGs with minimal impact on the stability of the rest of the system nodes. The algorithm delineating the steps of the BESS-assisted MG self-healing process is outlined in Alg. 1.
IV Simulation Results
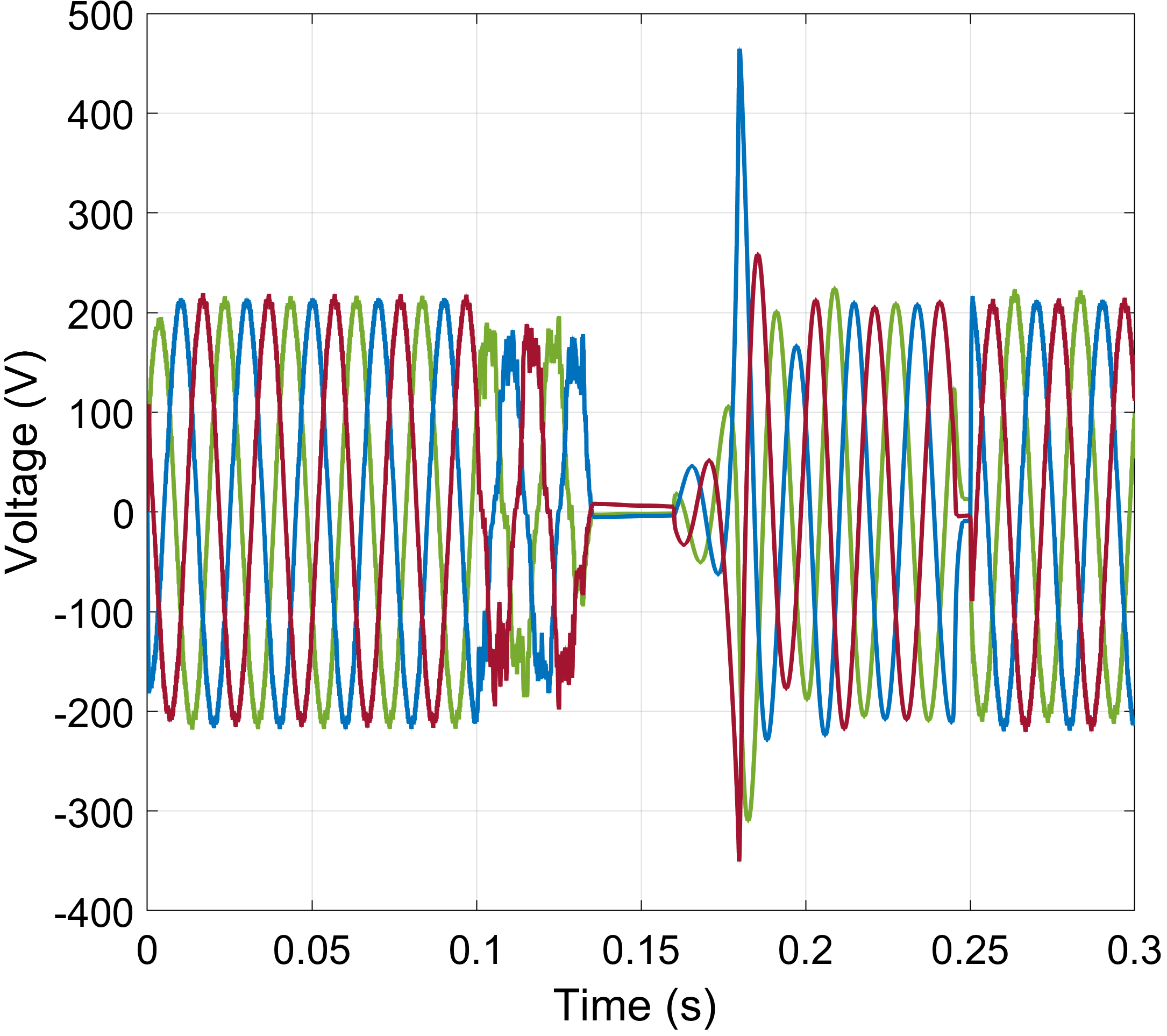
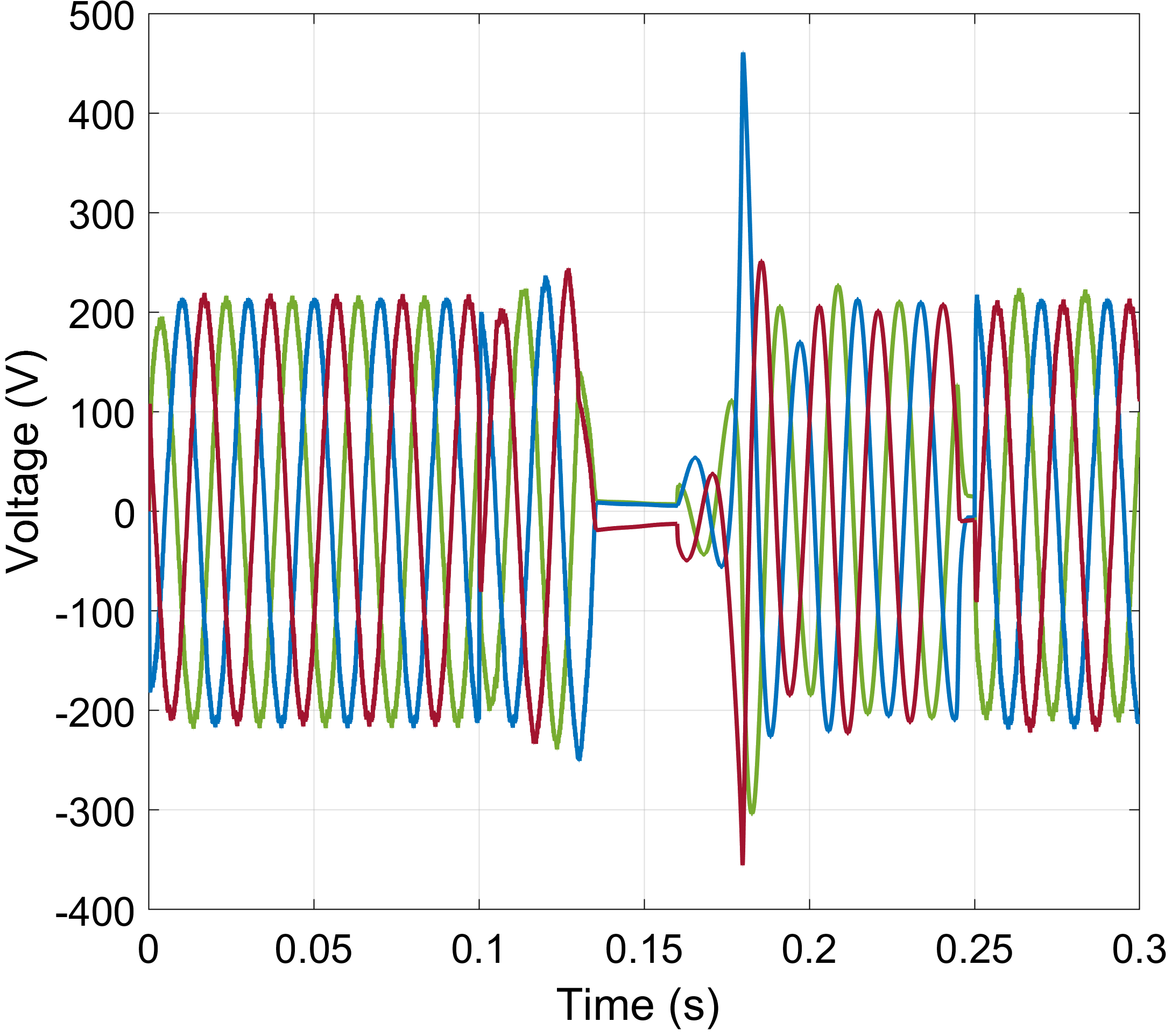
For the evaluation of our BESS-assisted cyberattack mitigation strategy, we use MATLAB’s Simscape Electrical toolkit. We simulate a modified version of the Canadian urban distribution system (depicted in Fig. 1) that has been adjusted to include a BESS. The MG (bus 1) is connected through a CB to the utility grid via a 120kV/12.5kV distribution substation transformer. A 2.75MVar capacitor bank responsible for harmonic frequency suppression is also connected to bus 1 via a CB. The remaining MG buses support aggregated residential loads that operate with a constant power demand of 2 MW. The BESS, furnishing a capacity of MWh, is placed at the PCC and is controlled by the MSC. It is interfaced with the MG feeder similarly to the DG nodes, i.e., via a kV/V step-down transformer. More details on the Canadian urban benchmark model can be found in [4].
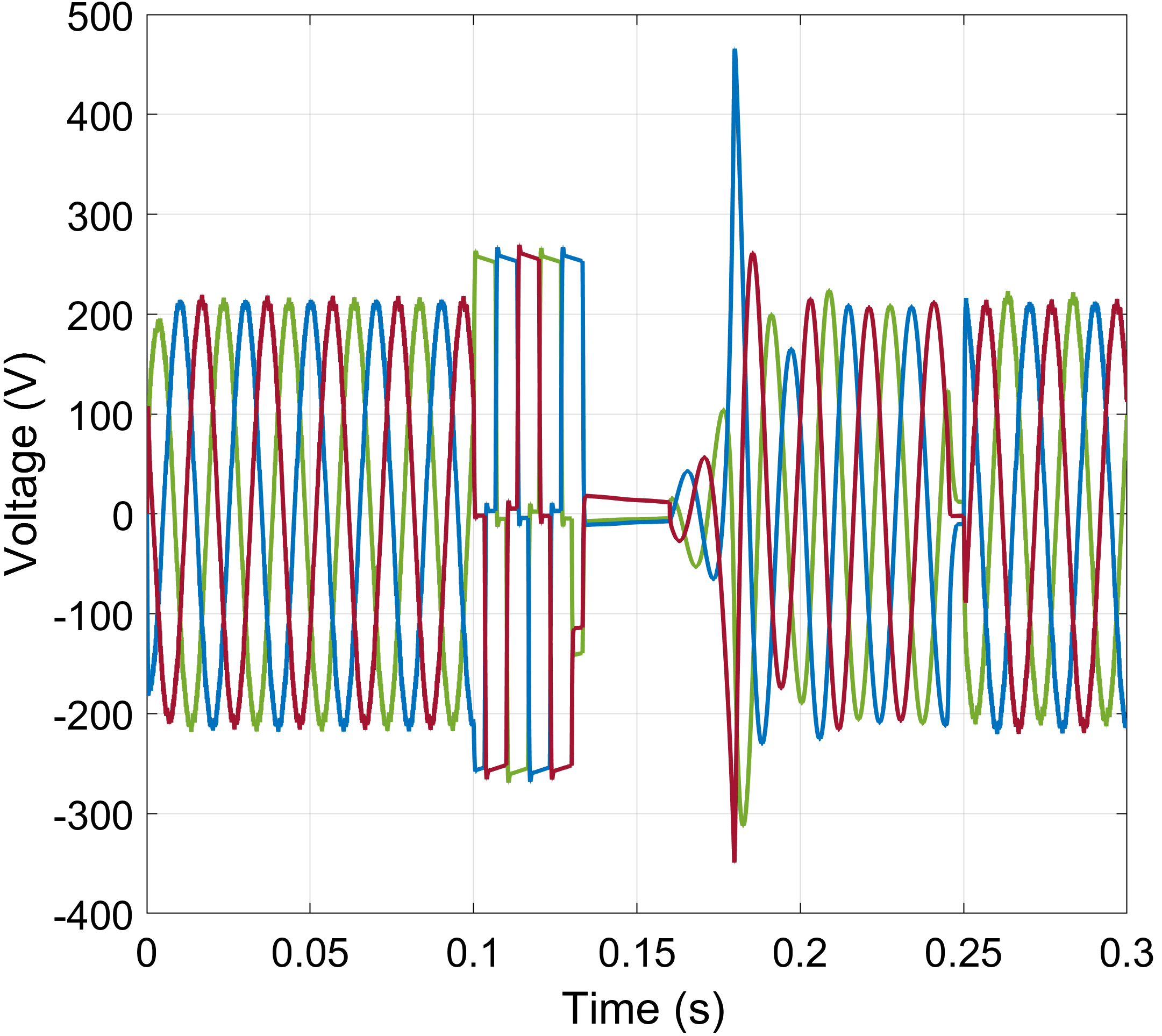
We have implemented three attack scenarios targeting primary control objectives of the DGs converters. Following the models described in Section III-A, we perform a scaling, an additive, and a ramping attack targeting the converter modulation controller. In Fig. 3, we demonstrate the impact of these attack types on the three-phase voltages of the DG. In the scaling attack case (Fig. 3a), we observe that the converter’s controller is saturated, thus producing an almost square output voltage waveform, while also exceeding the acceptable operational voltage limits (overvoltage condition). In the additive attack scenario (Fig. 3b), we can observe that the attack is initiated at and manifests itself as a superposition of a random noise signal on the three-phase voltage envelopes. In the ramping attack scenario (Fig. 3c), the output voltage follows an arbitrarily increasing pattern. Once anomalous agent behavior is detected (), the MSC issues a sectionalization command to the compromised DG’s CB, and at the BESS is employed to support the DG power demand. While the compromised DG is supported by the BESS, the MSC attempts to recover the attacked agent (similar to black-start procedures). The DG controller restoration process is outside the scope of this work. Agent restoration could be performed by rolling back to a trusted/trustworthy firmware version, operation of the agent using only trusted functions (hardware-isolated security enclaves), secure updates, etc. Once the DG agent is restored in coordination with the MSC, the BESS-to-converter handover occurs. In our experiment, this handover takes place at , when we can observe a small transient perturbation, mainly attributed to the plug-and-play features of the BESS.
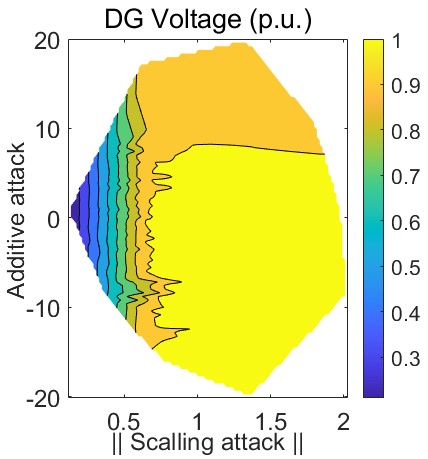
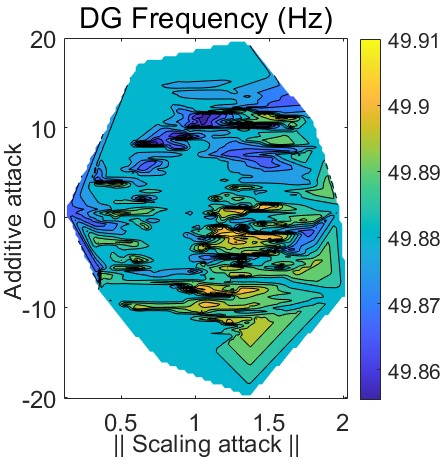
Sensitivity analysis methodologies can be used to identify the most critical components and how they affect system behavior. Monte Carlo simulations exhaustively search for such components or configurations and assist in prioritizing and mitigating undesirable conditions [21]. In our case, sensitivity analysis is used to identify which additive, scaling, or ramping factors can maximize the impact of cyberattacks. In Fig. 4, we demonstrate a heat map of the steady-state impact of control input attacks on the voltage and frequency of the DG, respectively. The vertical axis represents the additive attack magnitudes, whereas the horizontal axis accounts for scaling perturbations. The attack-free scenario occurs when the additive attack magnitude (y-axis) is and the scaling attack factor (x-axis) is equal to . Deviating from this operating point, the steady-state impact of additive and scaling attack combinations can be observed in Fig. 4. Ramping attacks can be abstracted as a combination of additive and scaling attacks; therefore, their steady-state impact is considered in Fig. 4. The Monte Carlo-based sensitivity analysis illustrated in Fig. 4, also indicates which composite additive and scaling attacks should be subverted, since they would maximize adversarial objectives and degrade system performance.
V Conclusions and Future Work
This paper proposes a BESS-assisted mitigation scheme that can maintain stable MG operation under unintentional or deliberate disturbances (e.g., faults, cyberattacks, etc.). The proposed mitigation methodology is two-fold. The first part is responsible for the detection of the attack and the isolation of the compromised agent. The second leverages the BESS to support the MG’s power demand avoiding load shedding, while attempting the automated restoration of the attacked agent and its IBR distributed generator. Our future work will focus on compound mitigation strategies which will ensure the optimal power dispatch leveraging synergies between BESS and other DERs during disruptive attack models. Furthermore, robust distributed misbehaving agent detectors in coordination with BESS planning will be employed to improve grid resilience in weakly connected MG systems.
References
- [1] I. Zografopoulos et al., “Cyber-physical energy systems security: Threat modeling, risk assessment, resources, metrics, and case studies,” IEEE Access, vol. 9, pp. 29 775–29 818, 2021.
- [2] I. Zografopoulos and C. Konstantinou, “Derauth: a battery-based authentication scheme for distributed energy resources,” in IEEE Computer Society Annual Symposium on VLSI (ISVLSI), 2020, pp. 560–567.
- [3] I. Zografopoulos et al., “Time series-based detection and impact analysis of firmware attacks in microgrids,” Energy Reports, vol. 8, pp. 11 221–11 234, 2022.
- [4] I. Zografopoulos and C. Konstantinou, “Detection of malicious attacks in autonomous cyber-physical inverter-based microgrids,” IEEE Transactions on Industrial Informatics, 2021.
- [5] X. Li and S. Wang, “A review on energy management, operation control and application methods for grid battery energy storage systems,” CSEE Journal of Power and Energy Systems, 2019.
- [6] A. D. Dominguez-Garcia, C. N. Hadjicostis, and N. H. Vaidya, “Resilient networked control of distributed energy resources,” IEEE Journal on Selected Areas in Communications, vol. 30, no. 6, pp. 1137–1148, 2012.
- [7] C. Konstantinou and O. M. Anubi, “Resilient cyber-physical energy systems using prior information based on gaussian process,” IEEE Transactions on Industrial Informatics, 2021.
- [8] C. Deng et al., “Distributed resilient control for energy storage systems in cyber–physical microgrids,” IEEE Transactions on Industrial Informatics, vol. 17, no. 2, pp. 1331–1341, 2021.
- [9] R. Moghadam and H. Modares, “Resilient autonomous control of distributed multiagent systems in contested environments,” IEEE Transactions on Cybernetics, vol. 49, no. 11, pp. 3957–3967, 2019.
- [10] D. D. Sharma et al., “Agent-based distributed control schemes for distributed energy storage systems under cyber attacks,” IEEE JETCAS, vol. 7, no. 2, pp. 307–318, 2017.
- [11] L. Ding et al., “Distributed resilient finite-time secondary control for heterogeneous battery energy storage systems under dos attacks,” IEEE Trans. on Industrial Informatics, vol. 16, no. 7, pp. 4909–4919, 2019.
- [12] C.-H. Lo and N. Ansari, “Decentralized controls and communications for autonomous distribution networks in smart grid,” IEEE transactions on smart grid, vol. 4, no. 1, pp. 66–77, 2012.
- [13] J. Mahdavi et al., “Analysis of power electronic converters using the generalized state-space averaging approach,” IEEE Transactions on Circuits and Systems I, vol. 44, no. 8, pp. 767–770, 1997.
- [14] Y. Zhou et al., “A secure control learning framework for cyber-physical systems under sensor and actuator attacks,” IEEE Transactions on Cybernetics, 2020.
- [15] A. M. Mohan, N. Meskin, and H. Mehrjerdi, “A comprehensive review of the cyber-attacks and cyber-security on load frequency control of power systems,” Energies, vol. 13, no. 15, p. 3860, 2020.
- [16] W. Zeng and M.-Y. Chow, “A reputation-based secure distributed control methodology in d-ncs,” IEEE Transactions on Industrial Electronics, vol. 61, no. 11, pp. 6294–6303, 2014.
- [17] K. Dehghanpour et al., “A survey on state estimation techniques and challenges in smart distribution systems,” IEEE Transactions on Smart Grid, vol. 10, no. 2, pp. 2312–2322, 2018.
- [18] S. Sahoo et al., “On detection of false data in cooperative dc microgrids—a discordant element approach,” IEEE Transactions on Industrial Electronics, vol. 67, no. 8, pp. 6562–6571, 2019.
- [19] R. Majumder et al., “Improvement of stability and load sharing in an autonomous microgrid using supplementary droop control loop,” IEEE Transactions on Power Systems, vol. 25, no. 2, pp. 796–808, 2010.
- [20] J. P. Lopes et al., “Control strategies for microgrids emergency operation,” in Int’l Conf. on Future Power Systems. IEEE, 2005, pp. 6–pp.
- [21] J. V. Milanović, “Probabilistic stability analysis: the way forward for stability analysis of sustainable power systems,” Philosophical Transactions of the Royal Society A, vol. 375, no. 2100, p. 20160296, 2017.