Mean-Field Approximation based Scheduling for Broadcast Channels with Massive Receivers
Abstract
The emerging Industrial Internet of Things (IIoT) is driving an ever increasing demand for providing low latency services to massive devices over wireless channels. As a result, how to assure the quality-of-service (QoS) for a large amount of mobile users is becoming a challenging issue in the envisioned sixth-generation (6G) network. In such networks, the delay-optimal wireless access will require a joint channel and queue aware scheduling, whose complexity increases exponentially with the number of users. In this paper, we adopt the mean field approximation to conceive a buffer-aware multi-user diversity or opportunistic access protocol, which serves all backlogged packets of a user if its channel gain is beyond a threshold. A theoretical analysis and numerical results will demonstrate that not only the cross-layer scheduling policy is of low complexity but is also asymptotically optimal for a huge number of devices.
I Introduction
With the development of the fifth-generation (5G) and future sixth-generation (6G) [1] wireless networks, the Industrial Internet of Things (IIoT) has emerged as an important class of applications. The emerging IIoT applications stimulated an ever-increasing demand to provide low latency services for massive devices [2]. However, the scarce spectrum resources and limited transmission power is a major challenge and is hindering the support of required quality of service (QoS) for massive users. How to efficiently utilize the limited resources to support QoS for massive users is becoming critical and has been gaining much attention in recent years.
In order to reduce the communication latency, a line of works focused on the design of efficient stochastic optimization based resources allocation schemes. In [3], a dynamic server allocation scheme for parallel queues with random varying connectivity was investigated. It was shown that the allocation policy which serves the longest queue first performs well in stabilizing the system. In [4], an optimal delay-power tradeoff was revealed in the case of asymptotically small delays with fading channels. In [5], a unified framework for queue-based transmission scheduling was proposed. The optimal scheduling policy was proved to have a threshold-based structure. Work [5] has been extended to different scenarios by works [6, 7, 8]. In [6] and [7], the optimal queue-aware scheduling policies under the multi-state fading channels and the Markov arriving process were investigated, respectively. In [8], a queue status based non-orthogonal multiple access was investigated to reduce the latency in multiple user access scenarios. This line of works focused on the queue status based resource allocation optimization to match the traffic dynamics of users, thereby achieving better performance than other allocation schemes. However, the complexity of this line of works increases exponentially with the number of users, leading to an intrinsic difficulty in analyzing and optimizing the queue status based resource allocation scheme. Motivated by this, this paper aims to apply a mean-field approximation method to analyze the queue status based resource allocation schemes with massive users.
In this paper, we consider a downlink wireless communication scenario, which includes a base station (BS) and a massive number of users where the BS transmits each user’s data packets through a common broadcast channel. To serve massive users with low implementation complexity, the BS applies the time division multiple access (TDMA) protocol. In the order to minimize the average total queueing latency, we derive an optimal channel resources allocation policy by analyzing established stochastic optimization problems. Under the optimal allocation policy, the BS serves the user with the best channel state first. Moreover, the optimal policy is based on the channel status and queue status of all the users. As a result, it is not a trivial work to exactly evaluate the optimal policy. To address this challenge, we propose a mean-field approximation method to approximately evaluate the performance of the optimal policy. When the user number becomes massive, all users’ influences on a certain user’s queue dynamic characteristics become certain. As a result, we can decompose the influences among each user. After decomposing the complex massive user system, we establish an equivalent one-dimensional single user queue model for each user to analyze the queueing latency. Numerical results will demonstrate that the proposed mean-field approximation method can well estimate the optimal policy’s delay performance.
II System Model
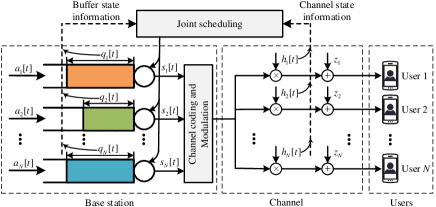
As depicted in Fig. 1, we consider a multi-user downlink wireless communication scenario, which is comprised of a BS and users. The transmission power at the BS is set to a constant to help reduce implementation complexity. At the BS, each user is allocated with a separate buffer to store the packets of independent identically distributed (i.i.d.) arrival processes. To serve the packets backlogged in the buffers, all users share a common broadcast channel to transmit their data packets. Moreover, a central scheduler is adopted to allocate the common channel resources based on the buffer states and channel states of each user.
II-A The Physical Layer
In this subsection, we present the physical layer of the downlink wireless system. In this downlink wireless system, time is denoted by . We divide time into slots. Each timeslot has a duration of seconds. The th timeslot denotes the time interval . Moreover, the bandwidth of the channel is denoted by . We consider a block fading channel model, which has been used to model the slowly varying flat-fading channel. Assume each user’s channel quality follows an i.i.d fading process with an i.i.d additive white Gaussian noise (AWGN). The channel gain of each user in each timeslot over a bandwidth does not change much. Let and denote the magnitude of channel gain of user in timeslot and the noise power at each user’s receiver, respectively.
To serve all the users through a common broadcast channel, a general superposition coding scheme can achieve good performance but with intolerably high complexity in analysis and implementation when . To avoid tackling the high complexity of the superposition coding scheme, we apply a suboptimal time division multiple access (TDMA) protocol. Especially, it was shown in [9] that the TDMA achievable capacity region converges to the capacity region achieved by the superposition coding scheme as the power decreases. Under the TDMA protocol, the BS shall allocate all the transmission power and bandwidth to one user at a time instant . Let denote a channel allocation policy as a time instant . Especially, indicates that user is allowed to access the common channel at the time instant . If , the user is not served at time instant . In particular, we have . Let denote the information rate of user at time instant . According to the channel capacity [10], we have
| (1) |
where denotes the signal-to-noise ratio.
II-B Discrete-time Queue Model
We consider a discrete-time continuous-length queue model, which can be obtained by sampling the fluid model with sampling rate . Next, we present the variation of user ’s queue length in a timeslot. Assume that the arrival process of each user is i.i.d.. At the start of timeslot , 111In this paper, we denote by the set . packets arrive at user ’s buffer. Let the probability be denoted by , where and . Without loss of generality, suppose that all packets are the same in size and each packet contains bits. As a result, the average number of bits arriving at each user’s buffer in a timeslot is given by
| (2) |
Let denote the number of bits remained in user ’s buffer by the end of the timeslot . The number of bits in user ’s buffer that are transmitted in timeslot is denoted by . Since the number of bits in a user’s buffer cannot be negative, shall satisfy that . By the end of timeslot , the number of bits remained in user ’s buffer, i.e. , is updated as
| (3) |
Let denote the total number of bits transmitted in timeslot . According to the Nyquist’s theorem, the value of is given by
| (4) |
III Delay-Optimal Scheduling with Massive Users
In this section, we aim to derive an optimal scheduling policy to minimize the average total queueing latency in the aforementioned downlink wireless system.
In each timeslot , the BS dynamically adjust the power allocated to each user based on each user’s queue state and channel state. A power allocation policy in timeslot can be given by .Based on the power allocation policy, each user’s queue length updates as Eq. (3). According to little’s law, we can formulate a following optimization problem to minimize the average total queueing delay, which is given by
| (5a) | ||||
| (5b) | ||||
where denotes the expectation operator.
However, it is a non-trivial work to solve the optimization problem (5). The intrinsic high complexity of optimization problem (5) is due to we aim to minimize the average queueing delay in a infinite time horizon by determining the power allocated at each time instant . To overcome the difficulty in solving the optimization problem (5), we aim to convert Problem (5) into an equivalent optimization problem, which is given in the following theorem.
Theorem 1: The optimization problem (5) is is asymptotically equivalent to the following optimization problem as .
| (6a) | ||||
| (6b) | ||||
Proof:
Due to space limitations, we mainly present the main idea of the proof. We first present an equivalent expression of the objective function Eq. (5a). Let denote the total number of bit that can be transmitted in timeslot . According to Eq. (3), Eq. (5a) is equivalent to
| (7) |
As a result, we shall minimize . For a policy that does not maximize in some timeslots, we prove that their exists a new policy can achieve lower or equal for all . The main idea of the proof is completed. ∎
Let the optimal channel allocation scheme at time be denoted by , which is given in the following theorem.
Theorem 2: One of the optimal channel allocation scheme at time is given by
| (8) |
Proof:
We denote by
| (9) |
the average information rate over time interval . It is obvious that we shall maximize to minimize (6a). It can be verified that the solution given by Theorem 2 can minimize for all . The proof is completed. ∎
According to Theorem 2, the BS shall serve each user from the user with the best channel state to the user with the worst channel state in each timeslot. The corresponding optimal scheduling policy is referred to as a good-channel-first-serve (GCFS) policy.
Next, we derive under the GCFS policy. Let denote the set of users whose buffer is not empty in timeslot just after the arrival process, i.e., for . The number is the number of users who need service in timeslot . Without loss of generality, suppose that . Let
| (10) |
denote the number of channel symbols used to clear user ’s buffer. Under the GCFS policy, is then given by the following corollary.
Corollary 1: There exits a threshold given by
| (11) |
For users in set , . For user ,
| (12) |
Finally, for users in set , .
Proof:
The proof is omitted due to space limitations. ∎
According to Corollary 1, the first users in set will surely get their data buffer cleared by the end of timeslot .
IV Mean-Field Approximation based
Delay Analysis
In this section, we aim to analyze the delay performance of the GCFS policy. Under the GCFS policy, a discrete-time continuous-state -dimensional Markov chain is induced. Due to the curse of dimensionality, it is hard to analyze the performance of the GCFS policy by deriving the stationary distribution of the Markov chain when . To evaluate the delay performance of the GCFS policy, we apply a mean-field approximation method introduced in [11].
IV-A Mean-Field Approximation and Threshold-based policy
In this section, we aim to analyze the delay performance of the GCFS policy via a mean-field approximation method. Let denote the stationary probability density function (PDF) of the Markov chain . According to the mean field approximation, we have
| (13) |
when . This is due to that all users’ impacts on a single user become certain when . In other words, the dependence among users vanishes in this downlink system as . Besides, since all users’ arrival process and channel quality are i.i.d., the PDFs shall be identical. As a result, variables are i.i.d. when the induced Markov chain is stationary. According to the law of large numbers, we have
| (14) |
Similarly, we have . That is to say that the average queue length and the average number of arriving bits in a timeslot are two constant when . The average number bits served in a timeslot, i.e., shall also be constant that equals to . As a result, we have
| (15) |
Under the GCFS policy, there exist a threshold on the channel gain that a user will get served when his channel gain is greater than . Let be the PDF of the channel gain . The cumulative distribution function of is denoted by , where . Set . According to , each user has the same probability to get served. As a result, there are about users get served. Let denote the users where . According to Corollary 1, the first users will get their buffer cleared and the last user’s bits are partially served. As a result, the total number of bits served in a timeslot is given by
| (16) |
According to Eqs. (14) and (15), we have
| (17) |
Eq. (17) indicates that and is a constant. As a result, a threshold-based policy which serves all backlogged packets of users whose channel gains are beyond can approximately achieves the minimum queueing latency, which has a lower complexity when compared with the GCFS policy. Besides, by Eq. (17), the average queue delay of each user is given by
| (18) |
Next, we aim to establish a self-consistent equation to derive the unknown threshold and constant . Based on the channel threshold , the most average number of bits that can be transmitted in each timeslot can be computed as
| (19) |
Let . The feasible region of is given by . The property of function is presented in the following lemma.
Lemma 1: is non-decreasing in .
Proof:
We derive the derivative of the function , which is given by
| (20) |
Since
| (21) |
we have . As a result, is a non-decreasing function of the threshold . ∎
According to Lemma 1, the supremum of is given by
| (22) |
The minimum of is . In order to keep this queueing system stable, the average number of bits transmitted in each timeslot shall equal the average number of bits arriving in each timeslot. As a result, we have
| (23) |
Eq. (23) is the self-consistent equation we want to establish. By solving Eq. (23), we can obtain the unknown threshold and the unknown constant . In particular, when , this queueing system is unstable. More transmission power shall be applied in this case to enhance the service capability of the system. When , we can reduce the transmission power to make full use of the spectrum resources. Since is a non-decreasing function, we can apply Algorithm 1 to derive the threshold .
IV-B Equivalent Single User Queue via Decomposition
In this subsection, we aim to approximate the stationary distribution of the each user’s queue length based on the mean filed approximation results in the last subsection.
Eq. (13) indicates that the dependence among users vanishes as . As a result, we can decompose the complex massive user downlink system into multiple equivalent single user systems. Eq. (17) indicates we can ignore the user whose bits are partially served. As a result, in each single user system, all packets in a user’s buffer are approximately either all transmitted with probability or all remained in the buffer with probability in each timeslot. Let denote the number of packets that remain in the buffer of user by the end of timeslot . According to the arrival process , we can construct a discrete-time discrete-state Markov chain to model the queue length dynamics of each single user system, which is illustrated in Fig. 2. Let be the one-step transition probability of this new Markov chain, which is given in the following lemma.

Lemma 2: The one-step transition probability of the new Markov chain is given by
| (24) |
where and .
Proof:
The proof is omitted due to space limitations. ∎
Let denote the steady-state probability of state of the discrete-time discrete-state Markov chain . According to Lemma 2, we have
| (25) |
It should be noted that Eq. (25) is the local balance equation of the new discrete-time discrete-state Markov chain. Let . As a result, we have
| (26) |
By submitting Eq. (26) into Eq. (25), we have
| (27) |
where , and for . Eq. (27) is a linear difference equation. To solve Eq. (27), boundary conditions are needed, which are given in the following lemma.
Lemma 3: The boundary conditions of the linear difference Eq. (27) are given by
| (28) |
Proof:
The proof is omitted due to space limitations. ∎
Next, we aim to solve the linear difference Eq. (27) with boundary conditions by the unilateral -transforms. Let and denote the unilateral -transforms of sequences and , respectively. The unilateral -transform of Eq. (27) is given in the following theorem.
Theorem 3: The unilateral -transform of the linear difference Eq. (27) is given by
| (29) |
Proof:
The proof is omitted due to space limitations. ∎
Similar to Theorem 3, we can derive the unilateral -transform of Eq. (26). By deriving the unilateral -transform of Eq. (26), we can obtain
| (30) |
We omit the derivation of Eq. (30) due to space limitations. Let denote the inverse unilateral -transform operator. The steady-state probability of the discrete-state Markov chain is then given by
| (31) |
In particular, when , the steady-state probabilities are given in the following corollary.
Corollary 2: When , the steady-state probabilities are given by
| (32) |
Proof:
The proof is omitted due to space limitations. ∎
V Numerical Result
In this section, numerical results are presented to demonstrate the theoretical analysis. In the simulations, the number of users and the maximum number of packets arriving at each user’s buffer are set to and , respectively. The length of a packet is set to . The bandwidth and the time interval of a slot are set to and , respectively. The noise power at each user’s receiver is set to . Assume that the magnitude of user ’s channel gain, i.e., is a Rayleigh random variable, which has a density distribution . In each timeslot, the packet arrival of each user’s buffer follows a Bernoulli arrival process with parameter . The BS allocates channel symbols according to Theorem 1. Each user’s buffer evolves according to Eq. (3) with each simulation running over timeslots. The simulation results and the results derived by the mean-field approximation are presented in the following figures.

Fig. 3 present the delay performance of the GCFS policy under different arrival rates . In Fig. 3, the average packet delay approximated by the mean-field approximation method and the average bit delay derived through simulation are denoted by solid lines and marks ‘o’, respectively. From Fig. 3, it can be seen that the average bit delay under the GCFS policy can be well approximated by the average packet delay derived through the mean-field approximation method proposed in this paper. Fig. 3 also presents the basic tradeoffs between the queueing delay and the power consumption. When more transmission power is applied, the queueing delay decreases.
Fig. 4 present the probability distribution of the number of packets in one user’s buffer under different transmission powers . In Fig. 4, the arrival rate and the time interval of a slot are set to and , respectively. The probability distributions of the number of packets in one user’s buffer derived by mean-field approximation and simulation are denoted by solid lines and marks ‘o’, respectively. From Fig. 4, it can be seen that the probability distributions of the number of packets in one user’s buffer derived by the mean-field approximation and simulation match well. This demonstrates that the established discrete-state Markov chain depicted in Fig. 2 well reflects the dynamic characteristics of each user’s queue length.
VI Conclusion
In this paper, we have investigated the problem of queueing delay minimization in a downlink communication scenario with massive receivers. To minimize the average total queueing delay, we have derived the optimal scheduling policy, referred to as the GCFS policy, by analyzing the established stochastic optimization problem. Furthermore, to overcome the difficulty in analyzing the performance of the GCFS policy due to the massive users, we have applied a mean-field approximation method. We have obtained a threshold-based policy with lower complexity which can approximately achieve minimum delay. Moreover, we have shown that the complex downlink system with massive users can be decomposed into massive single-user scenarios. Besides, we have established a Markov chain model for the equivalent single-user scenario to analyze the stationary distribution of each user’s queue length. Numerical results have demonstrated that the average queueing delay under the GCFS policy can be well evaluated by the mean-field approximation method.

References
- [1] K. B. Letaief, W. Chen, Y. Shi, J. Zhang, and Y. A. Zhang, “The roadmap to 6G: AI empowered wireless networks,” IEEE Communications Magazine, vol. 57, no. 8, pp. 84–90, Aug. 2019.
- [2] W. Saad, M. Bennis, and M. Chen, “A vision of 6g wireless systems: Applications, trends, technologies, and open research problems,” IEEE Network, vol. 34, no. 3, pp. 134–142, May/Jun. 2020.
- [3] L. Tassiulas and A. Ephremides, “Dynamic server allocation to parallel queues with randomly varying connectivity,” IEEE Transactions on Information Theory, vol. 39, no. 2, pp. 466–478, Mar. 1993.
- [4] R. A. Berry, “Optimal power-delay tradeoffs in fading channels-small-delay asymptotics,” IEEE Transactions on Information Theory, vol. 59, no. 6, pp. 3939–3952, Jun. 2013.
- [5] W. Chen, Z. Cao, and K. B. Letaief, “Optimal delay-power tradeoff in wireless transmission with fixed modulation,” in 2007 International Workshop on Cross Layer Design, Sept. 2007, pp. 60–64.
- [6] J. Liu, W. Chen, and K. B. Letaief, “Delay optimal scheduling for arq-aided power-constrained packet transmission over multi-state fading channels,” IEEE Transactions on Wireless Communications, vol. 16, no. 11, pp. 7123–7137, Nov. 2017.
- [7] X. Zhao, W. Chen, J. Lee, and N. B. Shroff, “Delay-optimal and energy-efficient communications with markovian arrivals,” IEEE Transactions on Communications, vol. 68, no. 3, pp. 1508–1523, Mar. 2020.
- [8] X. Zhao and W. Chen, “Non-orthogonal multiple access for delay-sensitive communications: A cross-layer approach,” IEEE Transactions on Communications, vol. 67, no. 7, pp. 5053–5068, Jul. 2019.
- [9] G. Caire, D. Tuninetti, and S. Verdu, “Suboptimality of tdma in the low-power regime,” IEEE Transactions on Information Theory, vol. 50, no. 4, pp. 608–620, Apr. 2004.
- [10] T. M. Cover and J. A. Thomas, Elements of Information Theory, 1991.
- [11] P. M. Chaikin and T. C. Lubensky, Principles of Condensed Matter Physics. Cambridge University Press, 1995.