Label Embedding via Low-Coherence Matrices
Abstract
Label embedding is a framework for multiclass classification problems where each label is represented by a distinct vector of some fixed dimension, and training involves matching model output to the vector representing the correct label. While label embedding has been successfully applied in extreme classification and zero-shot learning, and offers both computational and statistical advantages, its theoretical foundations remain poorly understood. This work presents an analysis of label embedding in the context of extreme multiclass classification, where the number of classes is very large. We present an excess risk bound that reveals a trade-off between computational and statistical efficiency, quantified via the coherence of the embedding matrix. We further show that under the Massart noise condition, the statistical penalty for label embedding vanishes with sufficiently low coherence. Our analysis supports an algorithm that is simple, scalable, and easily parallelizable, and experimental results demonstrate its effectiveness in large-scale applications.
1 Introduction
In standard classification, the goal is to learn from feature-label pairs a classifier that maps a feature vector in the feature space to its label in the label space . Label embedding is a framework that represents each label by a vector of fixed dimension, and learns a function to map each feature vector to the vector representing its label. At inference time, the label of a test data point is assigned to match the nearest label representative in the embedding space. The standard classification setup can be viewed as a special case of label embedding, where each label is one-hot encoded.
This work examines labeling embedding in the context of extreme classification, which refers to multiclass and multilabel classification problems involving thousands of classes or more (Wei et al.,, 2022). Extreme classification has emerged as an essential research area in machine learning, owing to an increasing number of real-world applications involving massive numbers of classes, such as image recognition (Zhou et al.,, 2014), natural language processing (Le and Mikolov,, 2014; Jernite et al.,, 2017), and recommendation systems (Bhatia et al.,, 2015; Chang et al.,, 2019). Traditional classification methods often struggle to scale effectively in these scenarios due to the high computational cost and memory requirements associated with handling large label spaces. Consequently, there is a growing need for efficient and scalable algorithms that can tackle extreme classification problems without compromising on performance (Prabhu and Varma,, 2014; Prabhu et al.,, 2018; Deng et al.,, 2018). Successful applications of label embedding to extreme classification include Yu et al., (2014); Jain et al., (2019); Bhatia et al., (2015); Guo et al., (2019); Evron et al., (2018); Hsu et al., (2009). Furthermore, Rodríguez et al., (2018) argues that label embedding can accelerate the convergence rate and better capture latent relationships between categories.
Despite its widespread use, the theoretical basis of label embedding has not been thoroughly explored. This paper presents a new excess risk bound that provides insight into how label embedding algorithms work. The bound establishes a trade-off between computational efficiency and classification accuracy, and explains the accuracy penalty in terms of the coherence of the embedding matrix. Our theory applies to various types of embedding: data-independent embeddings (Weston et al.,, 2002; Hsu et al.,, 2009), those anchored in auxiliary information (Akata et al.,, 2013), and embeddings co-trained with models (Weston et al.,, 2010). Intriguingly, under the multiclass noise condition of Massart and Nédélec, (2006), the statistical penalty associated with a positive matrix coherence, which is unavoidable when reducing the dimension of the label space, disappears. Guided by this theory, we investigate a simple yet efficient label embedding algorithm, and show empirically that in extreme classification tasks, this algorithms outperforms existing methods.
2 Related Work
While label embedding has also been successfully applied to zero-shot learning (Wang et al.,, 2019; Akata et al.,, 2013), we focus here on extreme classification, together with related theoretical contributions.
2.1 Extreme Classification
Besides label embedding, existing methods for extreme multiclass classification can be grouped into three main categories: label hierarchy, one-vs-all methods, and other methods.
Label Embedding. A natural approach involves representing each label as a vector in a low-dimensional space. LEML (Yu et al.,, 2014) leverages a low-rank assumption on linear models and effectively constrains the output space of models to a low-dimensional space. SLICE (Jain et al.,, 2019) is designed to train on low-dimensional dense features, with each label represented by the mean of all feature vectors associated with that label. SLEEC (Bhatia et al.,, 2015) is a local embedding framework that preserves the distance between label vectors. Guo et al., (2019) point out that low-dimensional embedding-based models could suffer from significant overfitting. Their theoretical insights inspire a novel regularization technique to alleviate overfitting in embedding-based models. WLSTS (Evron et al.,, 2018) is an extreme multiclass classification framework based on error correcting output coding, which embeds labels with codes induced by graphs. Hsu et al., (2009) use column vectors from a matrix with the restricted isometry property (RIP) to represent labels. Their analysis is primarily tailored to multilabel classification.They deduce bounds for the conditional -error, which measures the squared -norm difference between the prediction and the label vector — a metric that is not a standard measure of classification error. In contrast, our work analyzes the standard classification error.
Label Hierarchy. Numerous methods such as Parabel (Prabhu et al.,, 2018), Bonsai (Khandagale et al.,, 2020), AttentionXML (You et al.,, 2019), lightXML (Jiang et al.,, 2021), XR-Transformer (Zhang et al.,, 2021), X-Transformer (Wei et al.,, 2019), XR-Linear (Yu et al.,, 2022), and ELIAS (Gupta et al.,, 2022) partition the label spaces into clusters. This is typically achieved by performing -means clustering on the feature space. The training process involves training a cluster-level model to assign a cluster to a feature vector, followed by training a label-level model to assign labels within the cluster.
One-vs-all methods. One-vs-all (OVA) algorithms address extreme classification problems with labels by modeling them as independent binary classification problems. For each label, a classifier is trained to predict its presence. DiSMEC (Babbar and Schölkopf,, 2017) introduces a large-scale distributed framework to train linear OVA models, albeit at an expensive computational cost. ProXML (Babbar and Schölkopf,, 2019) mitigates the impact of data scarcity with adversarial perturbations. PD-Sparse (Yen et al.,, 2016) and PPD-Sparse (Yen et al., 2017a, ) propose optimization algorithms to exploit a sparsity assumption on labels and feature vectors.
Other methods. Beyond the above categories, DeepXML (Dahiya et al.,, 2021) uses a negative sampling procedure that shortlists relevant labels during training and prediction. VM (Choromanska and Langford,, 2015) constructs trees with depth that have leaves with low label entropy. Based on the standard random forest training algorithm, FastXML (Prabhu and Varma,, 2014) proposes to directly optimize the Discounted Cumulative Gain to reduce the training cost. AnnexML (Tagami,, 2017) constructs -nearest neighbor graph of the label vectors and attempts to reproduce the graph structure in a lower-dimension feature space.
2.2 Excess risk bounds
Our theoretical contributions are expressed as excess risk bounds, which quantify how the excess risk associated to a surrogate loss relates to the excess risk for the 01 loss. Excess risk bounds for classification were developed by Zhang, (2004); Bartlett et al., (2006); Steinwart, (2007) and subsequently developed and extended by several authors. Ramaswamy and Agarwal, (2012) shows that one needs to minimize a convex surrogate loss defined on at least a dimension space to achieve consistency for the standard -class classification problem, , any convex surrogate loss function operating on a dimension less than inevitably suffers an irreducible error. We draw insights from (Steinwart,, 2007) to establish a novel excess risk bound for the label embedding framework, quantifying this irreducible error.
From a different perspective, Ramaswamy et al., (2018) put forth a novel surrogate loss function for multiclass classification with an abstain option. This abstain option enables the classifier to opt-out from making predictions at a certain cost. Remarkably, their proposed methods not only demonstrate consistency but also effectively reduce the multiclass problems to binary classification problems by encoding the classes with their binary representations. In particular, the region in that causes the irreducible error in our excess risk bound is abstained in Ramaswamy et al., (2018) to achieve lossless dimension reduction in the abstention setting.
3 Matrix Coherence
Our theory relies on the notion of the coherence of a matrix , which is the maximum magnitude of the dot products between distinct columns.
Definition 1.
Let be columns of the matrix , where for all . The coherence of is defined as .
If , is when the columns of are orthonormal. When , however, the coherence must be positive. Indeed, (Welch,, 1974) showed that for and , .
There are a number of known constructions of low-coherence matrices when . A primary class of examples is the random matrices with columns of unit norms that satisfy the Johnson-Lindenstrauss property (Johnson and Lindenstraus,, 1984). For example, a Rademacher matrix has entries that are sampled from a uniform distribution on . With high probability, a Rademacher random matrix of shape achieves a coherence for some constant (Achlioptas,, 2001). While random matrices can be easily obtained and have a low coherence in general, they require explicit storage (Nelson and Temlyakov,, 2011) and can be outperformed in practical problems by some carefully crafted deterministic matrices (Naidu et al.,, 2016; Liu and Jia,, 2020). Numerous deterministic constructions of low-coherence matrices have been proposed (Nelson and Temlyakov,, 2011; Yu,, 2011; Li et al.,, 2012; Xu,, 2011; Naidu et al.,, 2016). In particular, Nelson and Temlyakov, (2011) proposes a deterministic construction that can achieve with , which avoids explicit storage of the matrix and can achieve a lower coherence in practice. There are also algorithms that directly optimize matrices for a smaller coherence (Wei et al.,, 2020; Abolghasemi et al.,, 2010; Obermeier and Martinez-Lorenzo,, 2017; Li et al.,, 2013; Lu et al.,, 2018).
4 Label Embedding by Low-Coherence Matrices
We first introduce the notations and problem statement in Section 4.1, and then present the associated algorithm in Section 4.2. The excess risk bound and its interpretation are presented in Section 4.3. Finally, we introduce the condition for lossless label embedding in Section 4.4.
4.1 Problem Statement
We first introduce the notations. Let denote the feature space and denote the label space where . Let be random variables in , and let be the probability measure that governs . We use to denote the marginal distribution of on .
To define the standard classification setting, denote the 0-1 loss by . The risk of a classifier is , and the goal of classification is to learn a classifier from training data whose risk is as close as possible to the Bayes risk , where is the set of all measurable functions to .
We now describe an approach to classification based on label embedding, which represents labels as vectors in dimensional . In particular, let be an matrix with unit norm columns, called the embedding matrix, having coherence . The columns of are denoted by , and the column is used to embed the -th label.
Given an embedding matrix , the original -class classification problem may be reduced to a multi-output regression problem, where the classification instance translates to the regression instance . Given training data for classification, we create training data for regression, and apply any algorithm for multi-output regression to learn a regression function .
At test time, given a test point , a label is obtained by taking the nearest neighbor to among the columns of . In particular, define the decoding function , , where is the output of a regression model. Then the label assigned to is . In the rare case where multiple nearest neighbors exist for , this ambiguity is resolved by taking the label with smallest index.
Thus, label embedding searches over classifiers of the form , where . Fortunately, according to the following result, no expressiveness is lost by considering classifiers of this form.
Proposition 2.
=
Proof.
This stems from the following facts: (i) for any given , the function is also measurable, (ii) for all , the function ensures that , and (iii) such are measurable because , . ∎
It follows that is the Bayes risk for classification as defined earlier. This allows us to focus our attention on learning . Toward that end, we now formalize notions of loss and risk for the task of learning a multi-output function for multiclass classification via label embedding.
Definition 3.
Let be a loss function. Define the -risk of with distribution to be and the -Bayes risk to be
Using this notation, the target loss for learning is the loss function associated with embedding matrix defined by . By Prop. 2, the -risk of is the usual classification risk of the associated classifier . Given , we’d like to find an that minimizes , or in other words, an that makes the excess risk as small as possible.
While the target loss defines our learning goal, it is not practical as a training objective because of its discrete nature. Therefore, for learning purposes, Hsu et al., (2009); Akata et al., (2013); Yu et al., (2014) suggest a surrogate loss, namely, the squared distance between and . More precisely, for a given embedding matrix , define as . This surrogate allows us to learn by applying existing multi-output regression algorithms as we describe next. Thus, the label embedding learning problem is to learn with small surrogate excess risk. Our subsequent analysis will connect to .
4.2 Learning Algorithms
The theory presented below motivates the use of a with low coherence, and an with small surrogate risk . In light of this theory, the problem statement just introduced leads to a natural meta-algorithm for label embedding. This meta-algorithm should not be considered novel as its essential ingredients have been previously introduced Akata et al., (2013); Rodríguez et al., (2018). Our contribution is the theory below, and the experimental assessment of the meta-alogrithm with low-coherence matrices for extreme multiclass classification.
Let the training dataset be realizations of . Given an embedding matrix , replace each label with its embedding vector to form the regression dataset . Next, train a regression model on the regression dataset. For example, this may be achieved by solving where is some model class, such as a multilayer perceptron with nodes in the output layer.
can either be fixed or trained jointly with . Our analysis is independent of model training, and thus applies to either case. Given a new data point , to assign a label we search for the nearest embedding vector of and annotate with the label . The full meta-algorithm is presented in Alg. 1.
4.3 Excess Risk Bound
We present an excess risk bound, which relates the excess surrogate risk to the excess target risk. This bound justifies the use of the squared error surrogate, and also reveals a trade-off between the reduction in dimensionality (as reflected by ) and the potential penalty in accuracy.
To state the bound, define the class posterior where . Define , which is a measure of “noise” at . We discuss this quantity further after the main result, which we now state.
Theorem 4.
Let be an embedding matrix with coherence . Then
| (1) | |||
| (2) | |||
| (3) | |||
| (4) |
We begin by sketching the proof, and after the sketch offer a discussion of the bound. Full proofs and associated lemmas are provided in the Appendix. Before delving into the proof sketch, the concept of conditional risk is needed.
Definition 5.
Let be a loss function and be a probability measure on . For a point , define the conditional risk at as and .
The conditional risk represents the expected value of a loss given the model output and a feature vector . Note that . For brevity, we introduce the notation .
Proof sketch for Theorem 4.
We begin by demonstrating in Lemma 11 that there exists a unique such that . Here, represents the optimal model output at a specific point . We establish in Lemma 12 that ,
| (5) | |||
| (6) |
This implies that if a model output is sufficiently close to and the probability for label to occur exceeds the probability for label by a some margin, then is closer to than to .
By leveraging the above property along with the convexity of , we demonstrate in Lemma 13 that , , and ,
| (7) |
This means a small will lead to a small up to the noise tolerance .
As mentioned earlier, the goal of learning is to minimize the excess target risk . The theorem shows that this goal can be achieved up to the first (irreducible) term by minimizing the excess surrogate risk . The excess surrogate risk can be driven to zero by any consistent algorithm for multi-output regression with squared error loss.
The quantity can be viewed as a measure of noise (inherent in the joint distribution of ) at a point . While represents the probability of the most likely label occurring, represents the probability of the second most likely label occurring, A large implies that is, with high confidence, the correct prediction at . In contrast, if is small, our confidence in predicting is reduced, as the second most likely label has a similar probability of being correct.
As pointed out by Ramaswamy and Agarwal, (2012), any convex surrogate loss function operating on a dimension less than inevitably suffers an irreducible error, which is measured by the coherence of the embedding matrix , in the label embedding framework. From the proof outline, we can see that the model minimizing the -risk may potentially make a suboptimal prediction at point when . Conversely, when , will always make the optimal prediction at point . Given a classification problem with classes, a larger embedding dimension will lead to a smaller coherence , making on a larger region in at the cost of increasing computational complexity. On the other hand, by choosing a smaller , on a larger region in , increasing the first term in Theorem 4. This interpretation highlights the balance between the benefits of dimensionality reduction and the potential impact on prediction accuracy, as a function of the coherence of the embedding matrix, , and the noisiness measure, .
4.4 Improvement Under Low Noise
While Theorem 4 holds universally (for all distributions ), by considering a specific subset of distributions, we can derive a more conventional form of the excess risk bound. As a direct consequence of Theorem 4, under the multiclass extension of the Massart noise condition (Massart and Nédélec,, 2006), which requires with probability 1 for some , the first and second terms in Theorem 4 vanish. In this case, we recover a conventional excess risk bound, where tends to with . We now formalize this.
Definition 6 (Multiclass Massart Noise Condition).
The distribution on is said to satisfy the Multiclass Massart Noise Condition if and only if such that .
Corollary 7.
Assume satisfies the Multiclass Massart Noise Condition. If , then
| (10) |
where is the essential infimum of , .
5 Experiments
In this section, we present an experimental evaluation of the label embedding framework using low coherence embedding matrices and the squared loss on extreme multiclass classification problems where . We have aimed to empirically investigate the connections between the coherence of the embedding matrix and the accuracy. We also verify the computational advantage of label embedding by comparing it against PD-Sparse (Yen et al.,, 2016) and PPD-Sparse (Yen et al., 2017b, ), which are the most computationally efficient methods for extreme classification to the best of our knowledge. Although methods like AttentionXML (You et al.,, 2019), lightXML (Jiang et al.,, 2021), XR-Transformer (Zhang et al.,, 2021), X-Transformer (Wei et al.,, 2019), and ELIAS (Gupta et al.,, 2022) have been designed for language datasets and leverage language models like BERT, our focus is to assess label embedding as a general purpose method. Thus, we compare our method with more general approaches, including Parabel (Prabhu et al.,, 2018), PD-Sparse (Yen et al.,, 2016), PPD-Sparse (Yen et al., 2017a, ), and AnnexML (Tagami,, 2017), which are applicable across a broader range of multiclass extreme classification problems.
5.1 Experiment Setup
We conduct experiments on three large-scale datasets, DMOZ, LSHTC1, and ODP, which are extensively used for benchmarking extreme classification algorithms. The details of these datasets are provided in Table 1, with DMOZ and LSHTC1 available from (Yen et al.,, 2016), and ODP from (Medini et al.,, 2019). We adapt our method to fully connected neural networks, which are implemented using Pytorch, with a 2-layer fully connected neural network used for the LSHTC1 and DMOZ datasets and a 4-layer fully connected neural network for the ODP dataset. We tune the hyperparameters for all models on a held-out dataset. For our embedding matrix, we employ the Rademacher matrix, the Gaussian matrix, the complex Gaussian matrix, and the matrix proposed by (Nelson and Temlyakov,, 2011), which has demonstrated superior empirical performance in our tests. For the competing methods, we use the hyperparameters as suggested in their respective papers or accompanying code.
| Dataset | ||||
|---|---|---|---|---|
| LSHTC1 | 83805 | 5000 | 328282 | 12046 |
| DMOZ | 335068 | 38340 | 561127 | 11879 |
| ODP | 975936 | 493014 | 493014 | 103361 |
We compare our method against the following state-of-the-art methods:
-
•
PD-Sparse (Yen et al.,, 2016): an efficient solver designed to exploit the sparsity in extreme classification.
-
•
PPD-Sparse (Yen et al., 2017a, ): a multi-process extension of PD-Sparse (Yen et al.,, 2016).
-
•
Parabel (Prabhu et al.,, 2018): a tree-based method which builds a label-hierarchy.
-
•
AnnexML (Tagami,, 2017): a method which constructs a -nearest neighbor graph of the label vectors and attempts to reproduce the graph structure from a lower-dimension feature space.
-
•
MLP (CE Loss): Standard multilayer perceptron classifier with cross-entropy loss.
-
•
MLP (SE Loss): Standard multilayer perceptron classifier with squared error loss.
We experiment with the following types of embedding matrices:
-
•
Rademacher: entries are sampled from a uniform distribution on .
-
•
Gaussian: entries are sampled from . We normalize each column to have unit norm.
-
•
Complex Gaussian: the real and imaginary parts of each entry are sampled from . We normalize each column to have unit norm.
-
•
Nelson (Nelson and Temlyakov,, 2011): a deterministic construction of low-coherence complex matrices. If is an integer, is a prime number, and , then the coherence of the constructed matrix is at most . We choose in experiments.
While our theoretical framework is adaptable to any form of embedding, whether trained, fixed, or derived from auxiliary information, we focus on fixed embeddings in our empirical studies. This choice stems from the absence of a standardized approach to train or construct embeddings with auxiliary data. By centering on fixed embeddings, we ensure a controlled evaluation, minimizing confounding factors and emphasizing the role of coherence of the embeddings.
All neural network training is performed on a single NVIDIA A40 GPU with 48GB of memory. For our neural networks models, we explore different embedding dimensions and provide figures showing the relationship between the coherence of the embedding matrix and the accuracy. The full details of the experiments are presented in the appendix.
5.2 Experimental Results
The experimental results presented in Tables 2, 3, and 4 highlight the superior performance of our proposed method across various datasets. In Tables 2, 3, and 4, the first column is the name of the method or embedding type, the second column is the embedding dimension for label embedding methods, and the third column is the mean and standard deviation of accuracy in 5 randomized repetitions. We highlight the best-performing method for each dataset.
We plot the accuracies as the coherence of the embedding matrix decreases in Figures 1, 2, and 3 for the LSHTC1, DMOZ, and ODP datasets, respectively. Figures 1, 2, and 3 demonstrate a negative correlation between the coherence of the embedding matrix and the accuracy, confirming our theoretical analysis.
| Method | Dim | Acc. (Mean Std) |
|---|---|---|
| Gaussian | 32 | |
| Gaussian | 64 | |
| Gaussian | 128 | |
| Gaussian | 256 | |
| Gaussian | 512 | |
| Complex Gaussian | 32 | |
| Complex Gaussian | 64 | |
| Complex Gaussian | 128 | |
| Complex Gaussian | 256 | |
| Complex Gaussian | 512 | |
| Rademacher | 32 | |
| Rademacher | 64 | |
| Rademacher | 128 | |
| Rademacher | 256 | |
| Rademacher | 512 | |
| Nelson | 113 | |
| Nelson | 127 | |
| Nelson | 251 | |
| Nelson | 509 | |
| MLP (CE Loss) | N/A | |
| MLP (SE Loss) | N/A | |
| Annex ML | N/A | |
| Parabel | N/A | |
| PD-Sparse | N/A | |
| PPD-Sparse | N/A |
| Method | Dim | Acc. (Mean Std) |
|---|---|---|
| Gaussian | 32 | |
| Gaussian | 64 | |
| Gaussian | 128 | |
| Gaussian | 256 | |
| Gaussian | 512 | |
| Complex Gaussian | 32 | |
| Complex Gaussian | 64 | |
| Complex Gaussian | 128 | |
| Complex Gaussian | 256 | |
| Complex Gaussian | 512 | |
| Rademacher | 32 | |
| Rademacher | 64 | |
| Rademacher | 128 | |
| Rademacher | 256 | |
| Rademacher | 512 | |
| Nelson | 113 | |
| Nelson | 127 | |
| Nelson | 251 | |
| Nelson | 509 | |
| MLP (CE Loss) | N/A | |
| MLP (SE Loss) | N/A | |
| Annex ML | N/A | |
| Parabel | N/A | |
| PD-Sparse | N/A | |
| PPD-Sparse | N/A |
| Method | Dim | Acc. (Mean Std) |
|---|---|---|
| Gaussian | 128 | |
| Gaussian | 256 | |
| Gaussian | 512 | |
| Gaussian | 1024 | |
| Gaussian | 2048 | |
| Gaussian | 4096 | |
| Rademacher | 128 | |
| Rademacher | 256 | |
| Rademacher | 512 | |
| Rademacher | 1024 | |
| Rademacher | 2048 | |
| Rademacher | 4096 | |
| Complex Gaussian | 128 | |
| Complex Gaussian | 256 | |
| Complex Gaussian | 512 | |
| Complex Gaussian | 1024 | |
| Complex Gaussian | 2048 | |
| Complex Gaussian | 4096 | |
| Nelson | 331 | |
| Nelson | 509 | |
| Nelson | 1021 | |
| Nelson | 2039 | |
| MLP (CE Loss) | N/A | |
| MLP (SE Loss) | N/A | |
| Annex ML | N/A | |
| Parabel | N/A | |
| PD-Sparse | N/A | Train Time 50 hrs |
| PPD-Sparse | N/A |

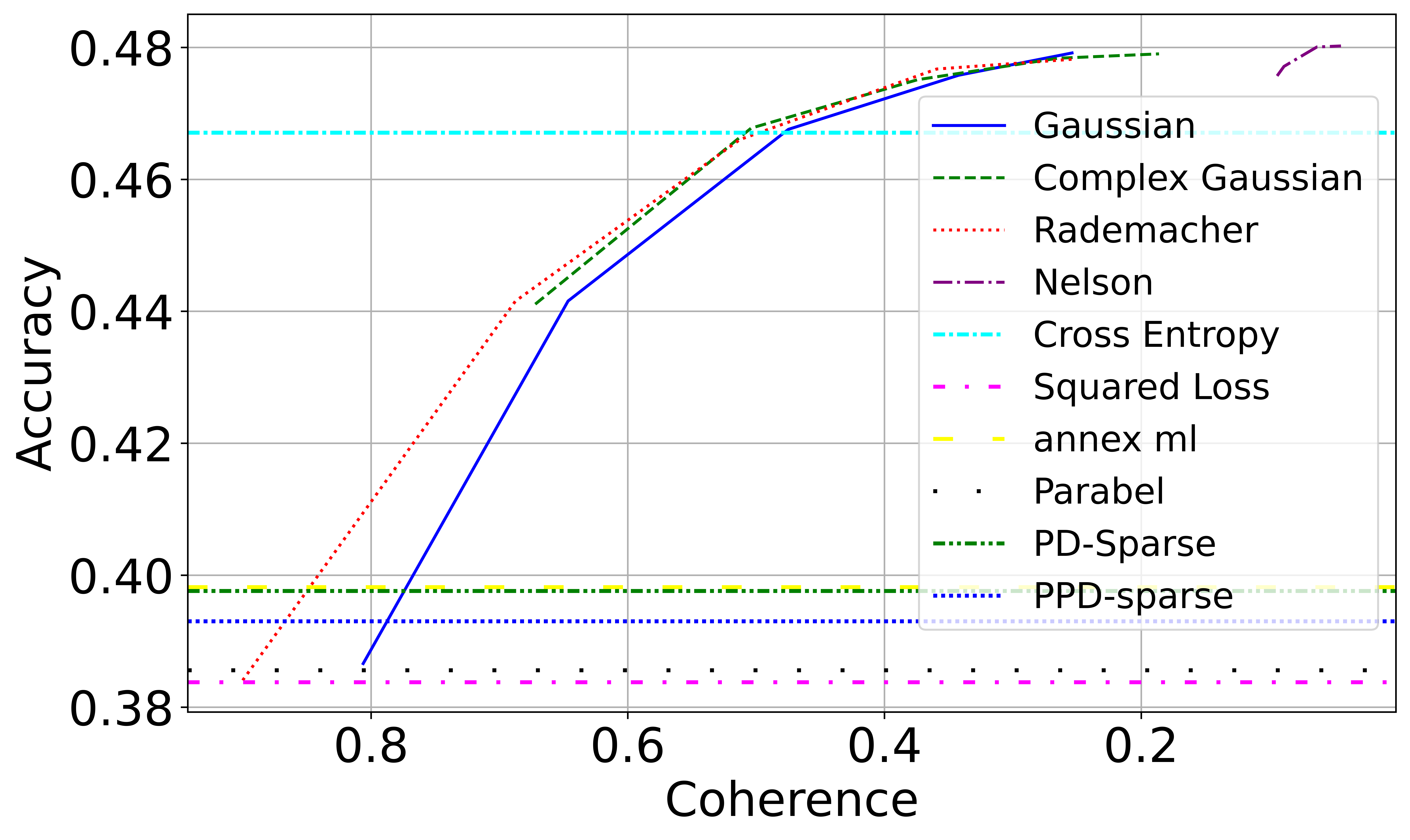
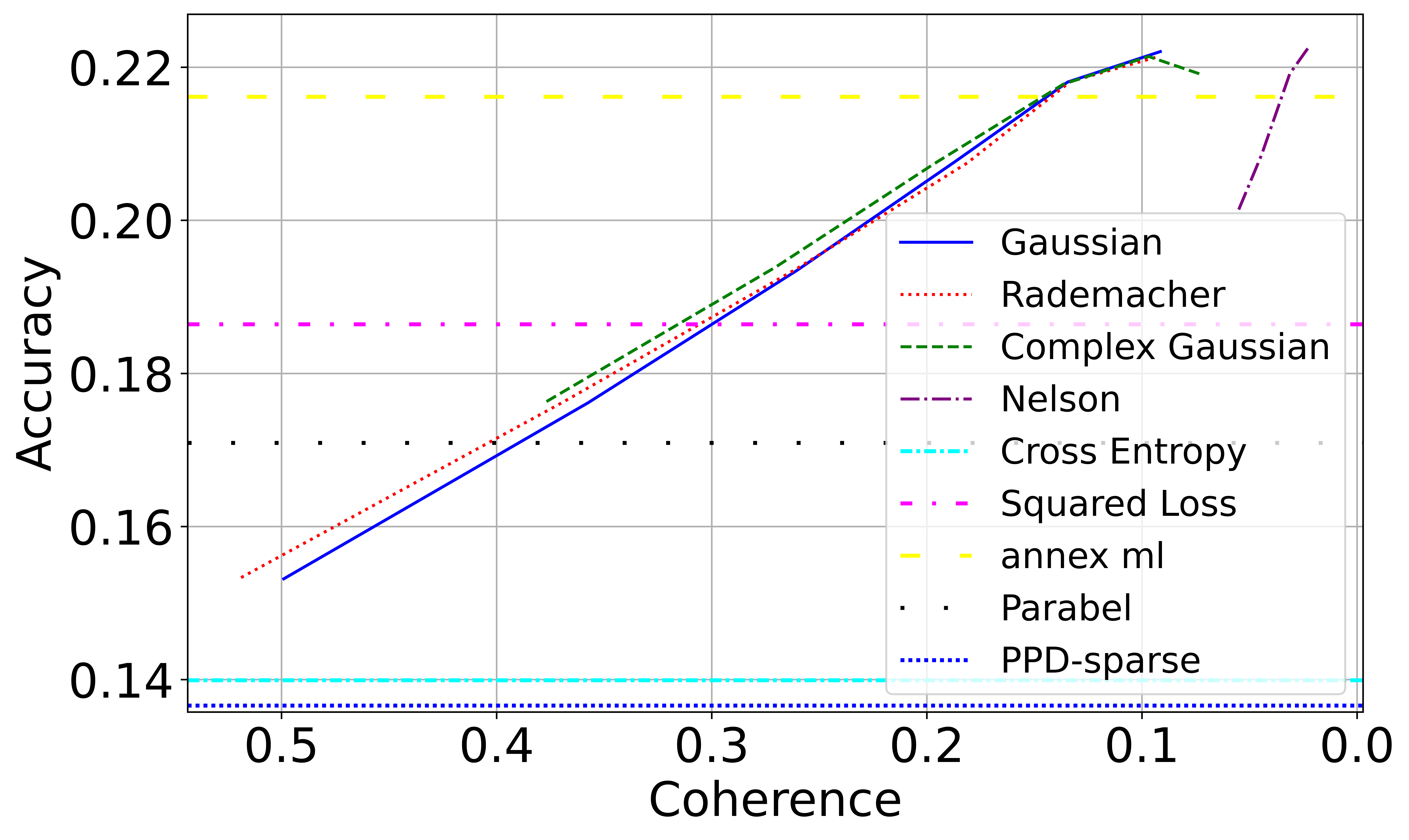
5.3 Computational Advantage
PD-Sparse (Yen et al.,, 2016) and PPD-Sparse (Yen et al., 2017b, ) are among the most computationally efficient methods for training for extreme classification, to the best of our knowledge. PD-Sparse and PPD-Sparse both solve an elastic net efficiently leveraging the sparsity in extreme classification. To allow for a fair comparison, we also use the Rademacher embedding with an elastic net, which is a linear model regularized by both and penalties. To compare the computational efficiency, we consistently set the embedding dimension to . In our distributed implementation, each node independently solves a subset of elastic nets with real-value output, effectively spreading out the computation. As shown in the table, the Rademacher embedding not only trains faster but also achieves higher accuracy. We train the PD-Sparse method and the Single-Node Rademacher embedding on Intel Xeon Gold 6154 processors, equipped with 36 cores and 180GB of memory. Our distributed approach and the PPD-Sparse method — also implemented in a distributed fashion — are trained across 10 CPU nodes, harnessing 360 cores and 1.8TB of memory in total. In Table 5, we compare Rademacher embedding with PD-sparse and PPD-sparse. The Rademacher embedding clearly outperforms PD-sparse and PPD-sparse in both runtime and accuracy.
6 Conclusion and Future Work
We provide a theoretical analysis for label embedding methods in the context of extreme multiclass classification. Our analysis offers a deeper understanding of the tradeoffs between dimensionality reduction and the potential penalty in accuracy. We derive an excess risk bound that quantifies this tradeoff in terms of the coherence of the embedding matrix, and show that the statistical penalty for label embedding vanishes under the multiclass Massart condition. Through extensive experiments, we demonstrated that label embedding with low-coherence matrices outperforms state-of-the-art techniques.
While our analysis focuses on excess risk, our reduction of classification to regression means that existing generalization error bounds (for multi-output regression with squared error loss) can be applied to analyze the generalization error in our context. The work of Zhai and Wang, (2018) shows that the generalization error grows linearly as the dimension of the output space grows. This suggests that smaller embedding dimensions lead to tighter control of the generalization error.
Future work may consider extension to multilabel classification, online learning, zero-shot learning, and learning with rejection. Our theoretical framework provides a solid foundation for future research in this area.
| Method | LSHTC1 | DMOZ | ODP |
|---|---|---|---|
| PD-Sparse (Single Node) | |||
| Accuracy | N/A | ||
| Training Time | 230s | 829s | 50 hrs |
| PPD-Sparse (Distributed) | |||
| Accuracy | |||
| Training Time | 135s | 656s | 668s |
| Rademacher (Single Node) | |||
| Accuracy | |||
| Training Time | 55s | 254s | 2045s |
| Rademacher (Distributed) | |||
| Accuracy | |||
| Training Time | 14s | 68s | 350s |
References
- Abolghasemi et al., (2010) Abolghasemi, V., Ferdowsi, S., Makkiabadi, B., and Sanei, S. (2010). On optimization of the measurement matrix for compressive sensing. In 2010 18th European Signal Processing Conference, pages 427–431.
- Achlioptas, (2001) Achlioptas, D. (2001). Database-friendly random projections. In Proceedings of the Twentieth ACM SIGMOD-SIGACT-SIGART Symposium on Principles of Database Systems, PODS ’01, page 274–281, New York, NY, USA. Association for Computing Machinery.
- Akata et al., (2013) Akata, Z., Perronnin, F., Harchaoui, Z., and Schmid, C. (2013). Label-embedding for attribute-based classification. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR).
- Babbar and Schölkopf, (2017) Babbar, R. and Schölkopf, B. (2017). DiSMEC: Distributed Sparse Machines for Extreme Multi-Label Classification. In Proceedings of the Tenth ACM International Conference on Web Search and Data Mining, WSDM ’17, page 721–729, New York, NY, USA. Association for Computing Machinery.
- Babbar and Schölkopf, (2019) Babbar, R. and Schölkopf, B. (2019). Data scarcity, robustness and extreme multi-label classification. Machine Learning, 108.
- Bartlett et al., (2006) Bartlett, P. L., Jordan, M. I., and McAuliffe, J. D. (2006). Convexity, classification, and risk bounds. Journal of the American Statistical Association, 101(473):138–156.
- Bhatia et al., (2015) Bhatia, K., Jain, H., Kar, P., Varma, M., and Jain, P. (2015). Sparse Local Embeddings for Extreme Multi-label Classification. In Cortes, C., Lawrence, N., Lee, D., Sugiyama, M., and Garnett, R., editors, Advances in Neural Information Processing Systems, volume 28. Curran Associates, Inc.
- Chang et al., (2019) Chang, W.-C., Yu, H.-F., Zhong, K., Yang, Y., and Dhillon, I. S. (2019). A Modular Deep Learning Approach for Extreme Multi-label Text Classification. ArXiv, abs/1905.02331.
- Choromanska and Langford, (2015) Choromanska, A. E. and Langford, J. (2015). Logarithmic Time Online Multiclass prediction. In Cortes, C., Lawrence, N., Lee, D., Sugiyama, M., and Garnett, R., editors, Advances in Neural Information Processing Systems, volume 28. Curran Associates, Inc.
- Dahiya et al., (2021) Dahiya, K., Saini, D., Mittal, A., Dave, K., Jain, H., Agarwal, S., and Varma, M. (2021). DeepXML: A deep extreme multi-Label learning framework applied to short text documents. In ACM International Conference on Web Search and Data Mining.
- Deng et al., (2018) Deng, H., Han, J., Zhao, Z., and Liu, H. (2018). Dual principal component pursuit: Improved analysis and efficient algorithms. In Advances in Neural Information Processing Systems, pages 1514–1524.
- Evron et al., (2018) Evron, I., Moroshko, E., and Crammer, K. (2018). Efficient Loss-Based Decoding on Graphs for Extreme Classification. In Bengio, S., Wallach, H., Larochelle, H., Grauman, K., Cesa-Bianchi, N., and Garnett, R., editors, Advances in Neural Information Processing Systems, volume 31. Curran Associates, Inc.
- Guo et al., (2019) Guo, C., Mousavi, A., Wu, X., Holtmann-Rice, D. N., Kale, S., Reddi, S., and Kumar, S. (2019). Breaking the Glass Ceiling for Embedding-Based Classifiers for Large Output Spaces. In Wallach, H., Larochelle, H., Beygelzimer, A., d'Alché-Buc, F., Fox, E., and Garnett, R., editors, Advances in Neural Information Processing Systems, volume 32. Curran Associates, Inc.
- Gupta et al., (2022) Gupta, N., Chen, P., Yu, H.-F., Hsieh, C.-J., and Dhillon, I. (2022). ELIAS: End-to-End Learning to Index and Search in Large Output Spaces. In Koyejo, S., Mohamed, S., Agarwal, A., Belgrave, D., Cho, K., and Oh, A., editors, Advances in Neural Information Processing Systems, volume 35, pages 19798–19809. Curran Associates, Inc.
- Hsu et al., (2009) Hsu, D., Kakade, S. M., Langford, J., and Zhang, T. (2009). Multi-Label Prediction via Compressed Sensing. In Proceedings of the 22nd International Conference on Neural Information Processing Systems, NIPS’09, page 772–780, Red Hook, NY, USA. Curran Associates Inc.
- Jain et al., (2019) Jain, H., Balasubramanian, V., Chunduri, B., and Varma, M. (2019). Slice: Scalable Linear Extreme Classifiers trained on 100 Million Labels for Related Searches. In WSDM ’19, February 11–15, 2019, Melbourne, VIC, Australia. ACM. Best Paper Award at WSDM ’19.
- Jernite et al., (2017) Jernite, Y., Choromanska, A., and Sontag, D. (2017). Simultaneous Learning of Trees and Representations for Extreme Classification and Density Estimation. In Precup, D. and Teh, Y. W., editors, Proceedings of the 34th International Conference on Machine Learning, volume 70 of Proceedings of Machine Learning Research, pages 1665–1674. PMLR.
- Jiang et al., (2021) Jiang, T., Wang, D., Sun, L., Yang, H., Zhao, Z., and Zhuang, F. (2021). LightXML: Transformer with Dynamic Negative Sampling for High-Performance Extreme Multi-label Text Classification. Proceedings of the AAAI Conference on Artificial Intelligence, 35(9):7987–7994.
- Johnson and Lindenstraus, (1984) Johnson, W. B. and Lindenstraus, J. (1984). Extensions of Lipschitz mappings into Hilbert space. Contemporary mathematics, 26:189–206.
- Khandagale et al., (2020) Khandagale, S., Xiao, H., and Babbar, R. (2020). Bonsai: Diverse and Shallow Trees for Extreme Multi-Label Classification. Mach. Learn., 109(11):2099–2119.
- Le and Mikolov, (2014) Le, Q. and Mikolov, T. (2014). Distributed representations of sentences and documents. In International conference on machine learning, pages 1188–1196. PMLR.
- Li et al., (2013) Li, G., Zhu, Z., Yang, D., Chang, L., and Bai, H. (2013). On projection matrix optimization for compressive sensing systems. IEEE Transactions on Signal Processing, 61(11):2887–2898.
- Li et al., (2012) Li, S., Gao, F., Ge, G., and Zhang, S. (2012). Deterministic construction of compressed sensing matrices via algebraic curves. IEEE Transactions on Information Theory, 58(8):5035–5041.
- Liu and Jia, (2020) Liu, X. and Jia, L. (2020). Deterministic construction of compressed sensing matrices via vector spaces over finite fields. IEEE Access, 8:203301–203308.
- Lu et al., (2018) Lu, C., Li, H., and Lin, Z. (2018). Optimized projections for compressed sensing via direct mutual coherence minimization. Signal Processing, 151:45–55.
- Massart and Nédélec, (2006) Massart, P. and Nédélec, E. (2006). Risk Bounds for Statistical Learning. The Annals of Statistics, 34(5):2326–2366.
- Medini et al., (2019) Medini, T. K. R., Huang, Q., Wang, Y., Mohan, V., and Shrivastava, A. (2019). Extreme Classification in Log Memory using Count-Min Sketch: A Case Study of Amazon Search with 50M Products. In Wallach, H., Larochelle, H., Beygelzimer, A., d'Alché-Buc, F., Fox, E., and Garnett, R., editors, Advances in Neural Information Processing Systems, volume 32. Curran Associates, Inc.
- Naidu et al., (2016) Naidu, R. R., Jampana, P., and Sastry, C. S. (2016). Deterministic compressed sensing matrices: Construction via euler squares and applications. IEEE Transactions on Signal Processing, 64(14):3566–3575.
- Nelson and Temlyakov, (2011) Nelson, J. and Temlyakov, V. (2011). On the size of incoherent systems. Journal of Approximation Theory, 163(9):1238–1245.
- Obermeier and Martinez-Lorenzo, (2017) Obermeier, R. and Martinez-Lorenzo, J. A. (2017). Sensing matrix design via mutual coherence minimization for electromagnetic compressive imaging applications. IEEE Transactions on Computational Imaging, 3(2):217–229.
- Prabhu et al., (2018) Prabhu, Y., Kag, A., Harsola, S., Agrawal, R., and Varma, M. (2018). Parabel: Partitioned Label Trees for Extreme Classification with Application to Dynamic Search Advertising. In ACM International WWW Conference, pages 993–1002. International World Wide Web Conferences Steering Committee, International World Wide Web Conferences Steering Committee.
- Prabhu and Varma, (2014) Prabhu, Y. and Varma, M. (2014). FastXML: A Fast, Accurate and Stable Tree-Classifier for Extreme Multi-Label Learning. In Proceedings of the 20th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, KDD ’14, page 263–272, New York, NY, USA. Association for Computing Machinery.
- Ramaswamy and Agarwal, (2012) Ramaswamy, H. G. and Agarwal, S. (2012). Classification calibration dimension for general multiclass losses. In Pereira, F., Burges, C., Bottou, L., and Weinberger, K., editors, Advances in Neural Information Processing Systems, volume 25. Curran Associates, Inc.
- Ramaswamy et al., (2018) Ramaswamy, H. G., Tewari, A., and Agarwal, S. (2018). Consistent algorithms for multiclass classification with an abstain option. Electronic Journal of Statistics, 12(1):530 – 554.
- Rodríguez et al., (2018) Rodríguez, P., Bautista, M. A., Gonzàlez, J., and Escalera, S. (2018). Beyond one-hot encoding: Lower dimensional target embedding. Image and Vision Computing, 75:21–31.
- Steinwart, (2007) Steinwart, I. (2007). How to compare different loss functions and their risks. Constructive Approximation, 26:225–287.
- Tagami, (2017) Tagami, Y. (2017). AnnexML: Approximate Nearest Neighbor Search for Extreme Multi-Label Classification. In Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, KDD ’17, page 455–464, New York, NY, USA. Association for Computing Machinery.
- Wang et al., (2019) Wang, W., Zheng, V. W., Yu, H., and Miao, C. (2019). A survey of zero-shot learning: Settings, methods, and applications. ACM Trans. Intell. Syst. Technol., 10(2).
- Wei et al., (2022) Wei, T., Mao, Z., Shi, J.-X., Li, Y.-F., and Zhang, M.-L. (2022). A survey on extreme multi-label learning.
- Wei et al., (2019) Wei, T., Tu, W.-W., and Li, Y.-F. (2019). Learning for Tail Label Data: A Label-Specific Feature Approach. In Proceedings of the 28th International Joint Conference on Artificial Intelligence, IJCAI’19, page 3842–3848. AAAI Press.
- Wei et al., (2020) Wei, Z., Zhang, J., Xu, Z., and Liu, Y. (2020). Measurement matrix optimization via mutual coherence minimization for compressively sensed signals reconstruction. Mathematical Problems in Engineering, 2020:7979606.
- Welch, (1974) Welch, L. (1974). Lower bounds on the maximum cross correlation of signals (corresp.). IEEE Transactions on Information Theory, 20(3):397–399.
- Weston et al., (2010) Weston, J., Bengio, S., and Usunier, N. (2010). Large scale image annotation: learning to rank with joint word-image embeddings. Machine Learning, 81(1):21–35.
- Weston et al., (2002) Weston, J., Chapelle, O., Elisseeff, A., Schölkopf, B., and Vapnik, V. (2002). Kernel dependency estimation. In Proceedings of the 15th International Conference on Neural Information Processing Systems, NIPS’02, page 897–904, Cambridge, MA, USA. MIT Press.
- Xu, (2011) Xu, Z. (2011). Deterministic sampling of sparse trigonometric polynomials. Journal of Complexity, 27(2):133–140.
- (46) Yen, I. E., Huang, X., Dai, W., Ravikumar, P., Dhillon, I., and Xing, E. (2017a). PPDsparse: A Parallel Primal-Dual Sparse Method for Extreme Classification. In Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, KDD ’17, page 545–553, New York, NY, USA. Association for Computing Machinery.
- (47) Yen, I. E., Huang, X., Dai, W., Ravikumar, P., Dhillon, I., and Xing, E. (2017b). PPDsparse: A Parallel Primal-Dual Sparse Method for Extreme Classification. In Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, KDD ’17, page 545–553, New York, NY, USA. Association for Computing Machinery.
- Yen et al., (2016) Yen, I. E.-H., Huang, X., Ravikumar, P., Zhong, K., and Dhillon, I. (2016). PD-Sparse : A Primal and Dual Sparse Approach to Extreme Multiclass and Multilabel Classification. In Balcan, M. F. and Weinberger, K. Q., editors, Proceedings of The 33rd International Conference on Machine Learning, volume 48 of Proceedings of Machine Learning Research, pages 3069–3077, New York, New York, USA. PMLR.
- You et al., (2019) You, R., Zhang, Z., Wang, Z., Dai, S., Mamitsuka, H., and Zhu, S. (2019). AttentionXML: Label Tree-Based Attention-Aware Deep Model for High-Performance Extreme Multi-Label Text Classification. Curran Associates Inc., Red Hook, NY, USA.
- Yu et al., (2014) Yu, H.-F., Jain, P., Kar, P., and Dhillon, I. S. (2014). Large-scale multi-label learning with missing labels. In Proceedings of the 31st International Conference on International Conference on Machine Learning - Volume 32, ICML’14, page I–593–I–601. JMLR.org.
- Yu et al., (2022) Yu, H.-F., Zhong, K., Zhang, J., Chang, W.-C., and Dhillon, I. S. (2022). PECOS: Prediction for enormous and correlated output spaces. Journal of Machine Learning Research.
- Yu, (2011) Yu, N. Y. (2011). Deterministic compressed sensing matrices from multiplicative character sequences. In 2011 45th Annual Conference on Information Sciences and Systems, pages 1–5.
- Zhai and Wang, (2018) Zhai, K. and Wang, H. (2018). Adaptive dropout with rademacher complexity regularization. In International Conference on Learning Representations.
- Zhang et al., (2021) Zhang, J., Chang, W.-C., Yu, H.-F., and Dhillon, I. (2021). Fast Multi-Resolution Transformer Fine-tuning for Extreme Multi-label Text Classification. In Ranzato, M., Beygelzimer, A., Dauphin, Y., Liang, P., and Vaughan, J. W., editors, Advances in Neural Information Processing Systems, volume 34, pages 7267–7280. Curran Associates, Inc.
- Zhang, (2004) Zhang, T. (2004). Statistical behavior and consistency of classification methods based on convex risk minimization. The Annals of Statistics, 32(1):56–85.
- Zhou et al., (2014) Zhou, D.-X., Tang, J., and Yang, Y. (2014). Large scale multi-label learning with missing labels. In International Conference on Machine Learning, pages 593–601. PMLR.
Appendix A Proof of Theorem 4
Recall that .
Lemma 8.
. .
Proof.
Recall that . The result follows from the observation that and . ∎
Lemma 9.
is strictly convex and minimized at .
Proof.
| (11) | ||||
| (12) | ||||
| (13) | ||||
| (14) | ||||
| (15) |
So is strictly convex and minimized at . ∎
We’ll use to denote henceforward.
Lemma 10.
Let be a normed space with norm . Let be a strictly convex function. Let be minimized at with . , , if , then .
Proof.
We first confirm the fact that and , .
| (16) | ||||
| (17) | ||||
| (18) | ||||
| (19) |
Assume the opposite: For some , , and . Then
which results in a contradiction. ∎
Lemma 11.
Fix . , .
To facilitate our proofs, we denote , , and .
Lemma 12.
, , , ,
Proof.
We first consider the general case when . Write where and . Recall that . Note the inequality immediately implies .
| (23) | ||||
| (24) | ||||
| (25) | ||||
| (26) | ||||
| (27) | ||||
| (28) | ||||
| (29) | ||||
| (30) | ||||
| (31) | ||||
| (32) |
Inequality (27) follows the fact that . Inequality (29) follows from and . Inequality (30) is implied by the Cauchy-Schwarz inequality. In the last inequality (32), we use the fact that .
Now let . Let .
| (34) | ||||
| (35) | ||||
| (36) | ||||
| (37) | ||||
| (38) | ||||
| (39) |
∎
Lemma 13.
, , and ,
Proof.
By Lemma 11, Fix . Recall that . We claim
Assume and . By Lemma 12, , contradicting the definition of . Hence, .
∎
Now we’re ready to prove Theorem 4.
Proof of Theorem 4.
| (40) | ||||
| (41) |
We bound each integral individually.
By Lemma 13, , , and ,
| (42) |
Hence,
| (43) | ||||
| (44) |
Note the last inequality actually holds for all , that is, it holds even when . Then,
| (45) | ||||
| (46) | ||||
| (47) | ||||
| (48) | ||||
| (49) |
In inequality (48), we apply Holder’s inequality.
When , . By (42), if and , then . As , and . It is trivial that also holds when . Thus, and , . Therefore,
| (50) | ||||
| (51) | ||||
| (52) |
∎
Appendix B Experiment Details
In this section, we provide the details of our experiments.
B.1 Neural Networks
In this section, we provide details on the architectures and hyperparameter choices for the neural networks used in our experiments. The architectures and hyperparameters are selected by trial-and-error on a heldout dataset.
B.1.1 LSHTC1
The proposed embedding strategy adopts a 2-layer neural network architecture, employing a hidden layer of 4096 neurons with ReLU activation. The output of the neural network is normalized to have a Euclidean norm of 1. An Adamax optimizer with a learning rate of is utilized together with a batch size of 128 for training. The model is trained for a total of 5 epochs. In order to effectively manage the learning rate, a scheduler is deployed, which scales down the learning rate by a factor of 0.1 at the second epoch.
Our cross-entropy baseline retains a similar network architecture to the embedding strategy, with an adjustment in the output layer to reflect the number of classes. Here, the learning rate is and the batch size is 128 for training. The model undergoes training for a total of 5 epochs, with a scheduler set to decrease the learning rate after the third epoch.
Finally, the squared loss baseline follows the architecture of our cross-entropy baseline, with the learning rate and batch size mirroring the parameters of the embedding strategy. As with the embedding strategy, the output is normalized. The model is trained for a total of 5 epochs, and the learning rate is scheduled to decrease after the third epoch.
B.1.2 DMOZ
For the DMOZ dataset, our proposed label embedding strategy employed a 2-layer neural network with a hidden layer of 2500 neurons activated by the ReLU function. The output of the network is normalized to have a norm of 1. We trained the model using the Adamax optimizer with a learning rate of and a batch size of 256. The model was trained for 5 epochs, and the learning rate was scheduled to decrease at the second and fourth epochs by a factor of 0.1.
For the cross-entropy loss baseline, we used the same network architecture with an adjustment in the output layer to match the number of classes. The learning rate was and the batch size was 256. The model underwent training for a total of 5 epochs, with the learning rate decreasing after the third epoch as determined by the scheduler.
Lastly, the squared loss baseline utilized the same architecture, learning rate, and batch size as the proposed label embedding strategy. Similarly, the model’s output was normalized. The model was trained for 5 epochs, with the learning rate scheduled to decrease after the third epoch.
B.1.3 ODP
For the ODP dataset, the experiments utilized a neural network model composed of 4 layers. The size of the hidden layers progressively increased from to , then decreased to . Each of these layers employed the ReLU activation function and was followed by batch normalization to promote faster, more stable convergence. The final layer output size corresponded with the embedding dimension for the label embedding strategy and the number of classes for the cross-entropy and squared loss baselines.
In the label embedding framework, the output was normalized to yield a norm of 1. This model was trained using the Adamax optimizer, a learning rate of 0.001, and a batch size of 2048. The training spanned 20 epochs, with a learning rate decrease scheduled after the 10th epoch by a factor of 0.1.
For the cross-entropy loss baseline, the same network architecture was preserved, with an adjustment to the penultimate layer, reduced by half, and the final output layer resized to match the number of classes. This slight modification in the penultimate layer was necessary to accommodate the models within the 48GB GPU memory. Notably, the neural network output was normalized by dividing each output vector by its Euclidean norm before applying the softmax function, a non-standard operation that significantly enhanced performance. This model was trained using a learning rate of 0.01 over 20 epochs, following a similar learning rate schedule.
Finally, the squared loss baseline used the same architecture as the cross-entropy baseline and the same learning rate and batch size as the label embedding model. Here, the output was also normalized. The model underwent training for 20 epochs, with a learning rate decrease scheduled after the 10th epoch.
B.2 Elastic Net
We aim to solve
| (53) |
where is the data matrix, the rows of are embedding vectors.
The problem (53) can be broken down into independent real-output regression problems of the form
| (54) |
where is the -th column of and is the -th column of . Consequently, We can distribute the real-output regression problems across multiple cores.
We develop a regression variant of the Fully-Corrective Block-Coordinate Frank-Wolfe (FC-BCFW) algorithm (Yen et al.,, 2016) and use it to solve the real-output regression problems. As the solver operates iteratively, we set it to run for a predefined number of iterations, denoted as . The chosen hyperparameters are outlined in table 6.
| Dataset | |||
|---|---|---|---|
| LSHTC1 | 0.1 | 1 | 20 |
| DMOZ | 0.01 | 0.01 | 20 |
| ODP | 0.01 | 0.1 | 40 |