Joint Radio Frequency Fingerprints Identification via Multi-antenna Receiver
Abstract
In Internet of Things (IoT), radio frequency fingerprints (RFF) technology has been widely used for passive security authentication to identify the special emitter. However, few works took advantage of independent oscillator distortions at the receiver side, and no work has yet considered filtering receiver distortions. In this paper, we investigate the RFF identification (RFFI) involving unknown receiver distortions, where the phase noise caused by each antenna oscillator is independent. Three RFF schemes are proposed according to the number of receiving antennas. When the number is small, the Mutual Information Weighting Scheme (MIWS) is developed by calculating the weighted voting of RFFI result at each antenna; when the number is moderate, the Distortions Filtering Scheme (DFS) is developed by filtering out the channel noise and receiver distortions; when the number is large enough, the Group-Distortions Filtering and Weighting Scheme (GDFWS) is developed, which integrates the advantages of MIWS and DFS. Furthermore, the ability of DFS to filter out the channel noise and receiver distortions is theoretically analyzed at a specific confidence level. Experiments are provided when both channel noise and receiver distortions exist, which verify the effectiveness and robustness of the proposed schemes.
Index Terms:
Emitter distortions, multiple independent oscillators, mutual information (MI), radio frequency fingerprinting identification (RFFI), receiver distortions.I Introduction
The number of IoT access devices deployed in practical systems is rising quickly as a result of the expansion of IoT application scenarios including automotive industry [1], healthcare [2], smart living [3], etc. According to the International Data Corporation, approximately 40 billion IoT devices will be available globally by 2025. As a large number of IoT devices have plunged into human life, network security has emerged as a growing public concern worldwide [4, 5].
Traditional cryptography-based algorithms are used in most existing wireless communication systems to achieve secure authentication of upper-layer mechanisms [6, 7]. However, these algorithms suffer from some limitations such as computer-limited assumptions, replay attack susceptibility, high communication overhead, complexity, etc [8]. In contrast, radio frequency fingerprints (RFF) as a very promising non-cryptographic authentication technology has recently gained a lot of research interest because of its information-theoretic security, low complexity, and high compatibility.
The concept of RFF was first introduced in 2003 [9]. It extracts the inherent, stable, and unique fingerprints of different emitters to distinguish their physical layer properties [10]. Such fingerprints exist due to the unavoidable accuracy errors and randomness in the device production process [11], which presents as the unintentional modulation at the emitter side, causing minor emitter distortions of the signal that are difficult to imitate.
Although this unintentional modulation is not conducive to the demodulation of the signal, it is the basis for RFF identification (RFFI) to extract radio frequency (RF) features with uniqueness, stability, and intrinsicality to complete the special emitter identification. The current RF features can be categorized into transient and steady-state features [12]. For the transient features, though some scholars have confirmed their feasibility [13], it is difficult to determine its starting point accurately due to the extremely short transient signal, which disables complete feature extraction. Therefore, a lot of researches focus on the feature extraction of the steady-state signal segment. For example, Q. Li et al. adopt the self-phase optical function to optimize variational mode decomposition (VMD) and suppress the modal aliasing after signal decomposition [14]. Y. Li et al. extract features through entropy information and spectral feature method [15].
In addition to RF feature extraction, RFFI contains another two steps: signal pre-processing and signal classification. The signal pre-processing, e.g., transformation [16, 17], data cleaning [18], etc., is used to improve the distinguishability of the subsequent extracted features among different emitters. In terms of signal classification, some traditional classifiers, such as K-means, support vector machine (SVM), and neural networks [12], are commonly adopted to classify the extracted RF features.
Although the above-mentioned works have studied various methods of each step in RFFI, few of them have taken into account receiver distortions. Such distortions unavoidably affect the accurate extraction of emitter fingerprints, and thus impact the performance of RFFI [19]. It has been suggested to complement additional hardware to compensate for the distortions at the receiving side [20], but it might lead to extra distortions that cannot be further explored.
Taking into account the impacts of receiver distortions and complemented hardware, B. He et al. suggest that the performance of RFFI can be enhanced by utilizing the diversity gain of multiple received versions [21]. Therefore, a configuration of multiple receiving antennas is expected to obtain similar benefits. On the other hand, multiple-input multiple-output technology is indispensable in 5G communication. It is pointed out in [22] that the large and heterogeneous antenna systems equipped with separate oscillators for each antenna, which generate oscillator distortions with independent identical distribution characteristics, are necessary for the future. Thus, it is obvious that the independent oscillators generate an independent phase noise to the signal received at each antenna. Currently, no scholars have employed this independent identical distribution property in their RFFI studies.
Considering the above two facts when multiple receiving antennas are configured, we propose three schemes to enhance the robustness and recognition accuracy of RFF. These three schemes are respectively suited to the scenarios with different numbers of receiving antennas. To begin with, Mutual Information Weighting Scheme (MIWS) is proposed when the number of receiving antennas is small. The MIWS is a weighting algorithm that performs a weighted voting operation on the RFFI result at each antenna. It estimates weights based on the mutual information (MI) between the emitter and the received signal at each antenna. Then, when the number of receiving antennas is moderate, Distortions Filtering Scheme (DFS) is proposed to filter out the channel noise and the receiver distortions by exploiting the independent identical distribution property of the received signal. Further, the Group-Distortions Filtering and Weighting Scheme (GDFWS) is proposed to solve the performance saturation phenomenon of DFS when the number of receiving antennas is large. Finally, we use absolute accuracy and confidence level as the metrics of filtering ability to theoretically derive the minimum number of receiving antennas required to satisfy certain performance of DFS. Thereby, the specific scenario in terms of the number of receiving antennas that is applicable for each scheme is derived.
The contributions of our work can be summarized as follows.
-
1)
Firstly, when the number of receiving antennas is small, the MIWS scheme is proposed. It utilizes the MI between the transmitting signal and each receiving signal to measure the quality of the latter. Then, the weights of signals at each antenna are calculated accordingly to get the weighted voting of the RFFI results.
-
2)
Secondly, when the number of receiving antennas is moderate, the DFS scheme is proposed to deal with channel noise and receiver distortions. To our knowledge, this is the first attempt to filter out the receiver distortions in current literature.
-
3)
Thirdly, when the number of receiving antennas is large, the GDFWS scheme is proposed, which enjoys the advantages of both DFS and MIWS. The GDFWS uniformly divides all the antennas into groups first, then filters out channel noise and receiver distortions using DFS within each group to get robust RFFI results, and obtains the weighted voting result of all groups by MIWS.
-
4)
Finally, based on the absolute accuracy and confidence level metrics, we theoretically derive the ability of DFS to filter out negative factors to determine the application scenario of DFS. The results simultaneously indicate the specific application scenarios of another two schemes.
The remainder of this paper is organized as follows. Section II briefly reviews the signal distortion model and generalizes the uplink multi-antenna received RFF system model. Three RFFI schemes with multi-antenna receive are described in Section III. In Section IV, we theoretically analyze the impact of the number of receiving antennas on the performance of DFS. Section V shows the results of the experiments, followed by the conclusion in Section VI.
II Background and system model
In this section, we first describe the emitter distortion, channel, and receiver distortion models, and then the uplink multi-antenna received RFF system model is established.
II-A Emitter distortion model
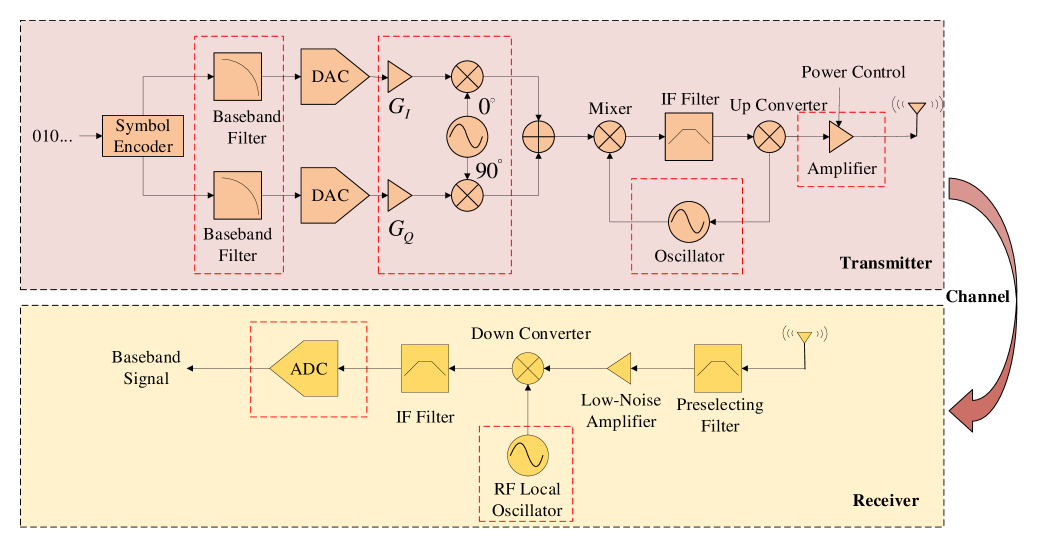
Fig. 1 depicts a typical end-to-end transceiver link and shows the source of both the emitter and receiver distortions highlighted with red dashed lines. As shown in this figure, the distortions experienced by the transmitted signal at the emitter include filter distortions, I/Q imbalance, spurious tones, and power amplifier nonlinearities. With reference to [21] and [23], the specific mathematical models for these distortions are given as follows.
-
1)
Transmit shaping filter distortion:
We denote the th transmitted symbol after constellation mapping as , and the symbol interval is . Subsequently, passes through transmit shaping filter. Considering the inevitable filter distortions due to the limited precision during the manufacturing process, the actual transmit shaping filter is written as
(1) where stands for the convolution, is assumed to be the ideal transmit shaping filter, and denotes the filter distortion. The Fourier transform form of is as follows:
(2) where and denote the amplitude distortion and phase distortion of the filter, respectively. Current literature generally uses the second-order Fourier series model to characterize these two distortions [21], such that
(3) (4) where , , , , are the parameters of the Fourier series. With the filter in (1), the transmission symbols after filter shaping can be written as
(5) -
2)
I/Q distortion:
We denote the in-phase and quadrature components of in (5) by and , respectively. The imbalance between and caused by the modulator is called I/Q distortion, which is mainly manifested as a gain mismatch and quadrature error, then the signal in (5) changes into
(6) where and represent the gain mismatches of these two components, denotes the quadrature error, and stands for conjugate operation. To facilitate the following discussion, we define
(7) -
3)
Spurious tone:
Affected by oscillators and other active devices, DC offset commonly exists in the signal. The presence of DC offset will result in harmonic components, which we refer to as spurious tone. Considering the impact of spurious tone, the signal in (6) becomes
(8) where is the number of harmonic components, and are the amplitude and frequency offset of the th harmonic component, respectively. It is worth noting that when and , the th harmonic component is also known as carrier leakage.
-
4)
Power amplifier nonlinearities:
The nonlinearity of the power amplifier causes distortions in both the amplitude and phase of the signal. We express these nonlinear distortions by the Taylor series [19]. Considering a Taylor series of order , the distorted signal in (8) further becomes
(9) where is the th coefficient of the Taylor polynomial.
II-B Channel and receiver distortion models
In this subsection, we consider the case of single antenna reception for simplicity. This discussion can be extended to multi-antenna reception easily, which will be described in detail in the next subsection. The channel attenuation is denoted by and the additive white Gaussian noise (AWGN) is defined as , then the signal received by the antenna is
| (10) |
In the aspect of receiver distortions, we concentrate on the phase noise caused by the oscillator, as well as the sampling jitter and quantization error caused by the ADC, which have a greater impact on the received signal compared with other hardware modules [23]. These receiver distortions are modeled as follows.
-
1)
Phase noise:
Assume a phase-locked loop (PLL) is used at the receiver side for phase synchronization. As a typical signal frequency tracker, PLL has the advantages of high output stability and continuously adjustable phase, etc. However, it inevitably produces phase noise, under the impact of which the output signal of PLL is given as:
(11) where
(12) is the local oscillator frequency and denotes its phase noise. Similar to most studies, e.g., [21, 23], we model the phase noise as a Wiener process as follows:
(13) where is the 3 dB bandwidth of the phase noise power spectrum and is the noise obeying the standard Gaussian distribution.
-
2)
Sampling jitter:
Sampling jitter means the deviation of the sampling point from the optimal position when the signal is downsampled by the ADC. In the presence of sampling jitter, the signal in (11) changes into
(14) where denotes the th sampling point, is the sampling period and , and denotes the relative sampling jitter, which is a random process, and .
-
3)
Quantization error:
The signal is quantized after sampling, and the quantization error is usually modeled as additive noise in the case of uniform quantization. The quantized version of (14) is written as:
(15) where denotes the quantization error at the th sampling point. If quantization accuracy is and the dynamic range is , then obeys a uniform distribution within the interval with a variance of .
To summarize, based on (9) to (15), when the effects of the emitter distortions, channel, and receiver distortions are considered, the down-converted signal at the receiver is expressed as (16) written at the top of next page, where the second equation is the simplified form of (16) since sampling jitter does not affect the distribution of .
| (16) |
| (17) |
| Scheme | MIWS | DFS | GDFWS |
|---|---|---|---|
| Basic ideas | MI weighting | distortions filtering | intra-group distortions filtering, inter-group weighting |
| Underline principle | diversity gains | statistical characteristics | statistical characteristics and diversity gains |
| Application scenario | small numbers of receiving antenna | medium numbers of receving antenna | large numbers of receving antenna |
II-C RFF system model with multiple receiving antennas
Based on the single-antenna reception model in the previous subsection, this subsection extends it to a multi-antenna reception scenario. Assuming an uplink multi-antenna received RFF system model consists of single-antenna IoT devices and a -antenna receiver, each antenna of which is equipped with an independent oscillator.
Suppose that multiple emitters adopt orthogonal access technology to communicate with the receiver, thus this paper does not consider the interference among multiple emitters. According to the previous subsections, the down-converted signal at the th antenna is established as:
| (18) |
where
| (19) |
| (20) |
represents the th sample in the th frame. is the channel fading coefficient between the emitter and the th antenna of the receiver, represents the phase noise of the th antenna at the receiver side, denotes the sampling jitter, indicates the quantization error at the th antenna, is the AWGN at the th antenna, and in the form of (9) for the th emitter.
As mentioned in the previous subsection, the antenna oscillator inevitably generates phase noise. Fortunately, it is reasonable to assume the phase noise remains constant within a single frame while varies frame-by-frame in this paper [24, 25]. Meanwhile, we assume a slow fading channel, so remains constant within a signal frame. Based on these two assumptions, we define and for any , and the model in (18) is further simplified as
| (21) |
III RFFI schemes with multi-antenna receiver

In this section, we propose three schemes to realize RFFI as summarized in Table I. These three schemes are applicable to scenarios with different numbers of receiving antennas. As shown in Table I, MIWS is first proposed in case the number of receiving antennas is small. Then, when the number of receiving antennas is sufficient to derive the statistical characteristics of the received signals, we propose DFS to filter out channel noise and receiver distortions. Finally, to address the issue of performance saturation that DFS encounters when the number of antennas is too large, GDFWS is proposed. Fig. 2 depicts the framework of RFFI with these three schemes, where only one scheme is activated by the control signal according to the number of configured antennas, and the modules that we propose are highlighted in yellow.
III-A Mutual information weighting scheme
The MI between the emitted signal and the received signal reflects their information similarity. In this paper, the larger the MI is, the less the emitter signal is affected by channel noise and receiver distortions. Based on this fact, we first estimate the MI between the emitter signal and the received signal at each antenna. Then the weight of the received signal at each antenna is set to be proportional to its corresponding MI. Finally, the RFFI result is obtained as the weighted voting of all classification results predicted from received signals.
In this subsection, we calculate the MI between the emitter signal and the received signal by taking one receiving antenna as an illustration, which can be extended to other antennas easily. For simplicity, the subscript of the th antenna in the subsequent discussion is ignored. Based on the previous analysis, we know that the emitter signal undergoes channel fading , AWGN , and receiver distortions before completing the classification. To facilitate subsequent analysis, we define
| (22) |
Firstly, with the definition in (22), we transform the signal in (10) into the frequency domain and get
| (23) |
where , , and are the expressions in frequency domain of , , and , respectively. According to [26], the MI between and is calculated as
| (24) |
where and are the variance of and , respectively. The function implements entropy calculation.
Consider a special case of (24), i.e., no receiver distortion exists. In this case, , where represents the variance of . Then the special case of above equation is
| (25) |
Note that (25) is only an ideal case, which does not exist in practical systems. To measure the quality of the received signal, we calculate the difference between (24) and (25) as follows,
| (26) |
where and indicate the variance of and in (10), respectively. In practical applications, and can be derived by some Signal to Noise Ratio (SNR) estimation techniques [27, 28, 29], and channel coefficient estimation techniques[30, 31]. Additionally, can also be estimated based on the received pilots.
Obviously, a smaller indicates fewer distortions at the receiver. Based on this fact, we define the weight of as,
| (27) |
where represents the MI difference at the th receiving antenna in the form of (26).
We use to denote the classification result of . Then the weighted voting of all results is implemented based on their corresponding weights in (27), and the final RFFI result can be obtained.
III-B Distortions filtering scheme
Though the MIWS described in the previous subsection realizes the reduction of the negative impact of channel noise and receiver distortions through diversity gain, a more direct way is to eliminate these negative effects. Thus, this subsection proposes DFS to filter out the channel noise and receiver distortions when the number of receiving antennas is sufficiently large.
If not specifically mentioned, the following derivations are given for single-frame signal, thus we omit the label . By defining , the overall system model in (21) is rewritten as
| (28) |
To improve the quality of , DFS attempts to filter out the adverse factors, i.e., , , and .
First, by considering all the sampling points of all antennas, (28) is converted into the matrix form
| (29) |
where
| (30) |
| (31) |
| (32) |
with the th element of the th row being , with the th element of the th row being , and is the number of sampling points in a frame.
The basic idea of DFS is to recover the matrix from , and then recover based on its relationship with given in (32). In doing so, the impacts of , , and are expected to be eliminated.
To better illustrate the statistical properties of the received signals, the matrix is rewritten as (33) shown at the top of the next page,
| (33) |
where
| (34) |
It should be noted that and follow the uniform and Gaussian distribution, respectively. Both of them have a mean of 0. Hence, the mean of is 0. Based on this property, we calculate the mean of each row of the matrix in (33) to obtain
| (35) |
where denotes the th row of the matrix in (33),
| (36) |
and calculates the mean of the vector . Based on (35), it is easy to obtain
| (37) |
Next, we reconstruct the th row of from , the processes of which apply to the other rows of as well. By multiplying the th row of (33) by with , which has been obtained by (35) and (37), the matrix in (33) becomes (38).
| (38) |
With the derived in (38), by calculating its column mean, we get
| (39) |
where calculates the column mean of the matrix . It is worth noting that is exactly the th row of , which is denoted as . Following the above procedures, we are able to recover all the rows of by varying the value of from 1 to in order.
By observing , we find that directly separating it into and without any prior knowledge of is impossible. Fortunately, by defining as the first symbol of this frame, we have
| (40) |
where
| (41) |
It is obvious that is highly correlated with .
Since retains all the information of , it is reasonable to use rather than as the signal for the subsequent RF feature extraction and classification without affecting the performance of RFFI.
We find that in (35) and (39) the calculation of the mean is implemented. However, in practical scenarios, it can only be approximated by averaging. To ensure the effect of filtering out channel noise and receiver distortions, and should be large enough. Generally, is sufficiently large in practical applications. Therefore, the filtering ability of DFS mainly depends on the value of , and their relationship will be analyzed in detail in Section IV.
III-C Group-distortions filtering and weighting scheme
The previous analysis has suggested the larger is, the smaller the difference between the averaging result and the actual mean 0. When is sufficiently large, this difference will be definitely very small. At this moment, even if we further increase , the difference will converge and thus no significant performance enhancement will appear. We call such phenomenon of DFS as performance saturation. To alleviate this problem when the number of receiving antennas is large, this subsection proposes GDFWS that divides all antennas into several groups to avoid the appearance of saturation phenomenon.

Fig. 3 illustrates the overall structure of GDFWS, where signals received by all antennas are divided into four groups for illustration. In this figure, , and . First, DFS is applied in each group to filter out channel noise and receiver distortions. Then, the obtained are delivered to the feature extraction module and weight calculation module, where the former extracts RF features that are subsequently fed into the classification module to obtain classification results , and the later calculates their respective weights . Finally, the classification result and its corresponding weight are sent into the weighted voting module to obtain the final RFFI result.
Obviously, GDFWS enjoys the advantages of both MIWS and DFS in terms of diversity gain and adverse factors elimination. Meanwhile, the above structure can be easily extended to the case of multiple groups, where the number of antennas in each group is smaller than the one when DFS exhibits performance saturation.
IV Theoretical analysis of DFS and Applicable scenario discussion
In this section, we theoretically analyze the ability of DFS to filter out channel noise and receiver distortions with varying numbers of receiving antennas. The metrics that we consider are confidence level and absolute accuracy. By revealing the relationship between and these metrics, we obtain the conclusion about which scheme is more desirable for the case with different numbers of receiving antennas.
We consider the asymptotic case, where , and then study the approximation degree of using averaging operation instead of the actual mean, which reveals its dependence on . By averaging each column of (38), the statistical average of the th column is derived as:
| (42) |
where
| (43) |
In the above equation, represents the difference between the average result and the mean 0. Therefore, the smaller is, the better the filtering effect of DFS on adverse factors, i.e., channel noise and receiver distortions. For simplicity, we define
| (44) |
where . According to (34), the in the above equation can be rewritten as
| (45) |
where the definition of each variable remains the same as in Section II.B. To further simplify, in the following analysis, we ignore in the above equation, which reduces to
| (46) |
To obtain the distribution of , i.e., in (43), we first analyze the distribution of . Referring to Section II.B, we know that is uniformly distributed between . Suppose the number of quantization bits is 16, i.e., , and , we have
| (47) |
The following discussions can be easily extended to the other cases of and . On the other hand, obeys a Gaussian distribution with mean 0 and variance , and obeys a standard Gaussian distribution, so we easily obtain
| (48) |
According to (10), we have
| (49) |
where and are the same as defined in Section III.A. For better illustration, we assume that and , thus the above equation is further simplified as
| (50) |
When , it is clear that
| (51) |
thus
| (52) |
Considering that the average of possible samples selected randomly from also follows the Gaussian distribution, so in (43) obeys the Gaussian distribution. Furthermore, based on the sampling properties of the sample means [32], it is known that
| (53) |
Next, we discuss two performance metrics, i.e., confidence level and absolute accuracy . If is required to be less than with a confidence level , we have
| (54) |
Let , then the above equation is rewritten as
| (55) |
where . As a result, the mathematical relationship between the confidence level , absolute accuracy , and the number of receiving antennas is
| (56) |
Clearly, a smaller indicates that DFS is more effective at filtering the adverse factors. To measure the advantage of DFS, we define the performance gain such that
| (57) |
where
| (58) |
Only when the gain is larger than a threshold , we regard that introducing DFS can bring benefits. That is
| (59) |
In this paper, we set , and get based on the above equation. It means that when , no obvious gain can be obtained when DFS is employed. In such a scenario, MIWS serves as an alternative.
Table II presents the relationship between and in (56) when confidence level and SNR=15dB.
| 4 | 8 | 16 | 32 | 64 | 128 | 256 | 512 | |
| 0.1743 | 0.1232 | 0.0871 | 0.0616 | 0.0436 | 0.0308 | 0.0218 | 0.0154 | |
| 0.0510 | 0.0361 | 0.0255 | 0.0180 | 0.0128 | 0.0090 | 0.0064 | ||
| Scheme | MIWS | DFS | GDFWS | |||||
From this table, we note that the decreasing rate of , i.e., , slows down as increases. When , the decreasing rate of is much slower than that when . This coincides with the expectation in the previous subsection, i.e., the performance of DFS will be saturated when is large enough. To avoid this saturation phenomenon, we use the GDFWS scheme in the cases with medium to high SNR to divide the antenna set into groups of no more than 128 antennas each, which avoids the saturation of DFS in each group.
| 4 | 8 | … | 256 | 512 | 1024 | 2048 | 4096 | |
| 0.5510 | 0.3897 | … | 0.0689 | 0.0487 | 0.0344 | 0.0244 | 0.0172 | |
| 0.1614 | … | 0.0285 | 0.0202 | 0.0143 | 0.0101 | 0.0071 | ||
| Scheme | MIWS | DFS | GDFWS | |||||
Table III gives the relationship between and in low SNR, where and SNR=5dB. It is noted that the saturation of DFS appears when , which is much larger than that in Table II. This means that DFS is more likely to saturate with a smaller when SNR is higher. In practical applications, the number of receiving antennas is generally limited, i.e., it will not reach 2048, thus DFS is still preferable rather than GDFWS at low SNR.
V Experiment and discussion
In this section, some experiments are provided to verify the efficiency of the proposed schemes.
V-A Experimental setting
According to the produces of RFF, we describe the settings of the simulation experiments in this paper from five aspects in turn: emitters, channel, receiver, RF feature extraction methods, and classifiers, the detail of which are as follows.
-
1)
The settings of emitters:
TABLE IV: The Parameters Settings of Emitters. 1 1 1 1 1 0.03 0.06 0.085 0.073 0.040 4 4 4 4 4 1 1 1 1 1 0.0302 0.0295 0.0290 0.0310 0.0313 4 4 4 4 4 0.998 1.0056 1.0102 0.9992 0.9982 -0.018∘ 0.0175∘ 0.012∘ 0.003∘ 0.024∘ 0.0013+0.0082j 0.0015+0.0072j 0.0011+0.0068j 0.0017+0.009j 0.002+0.0065j 0.0082 0.0075 0.0070 0.0087 0.0090 0 0 0 0 0 0.0129 0.0132 0.0123 0.0135 0.0119 1 1 1 1 1 0.3 0.6 0.01 0.4 0.08 The RF signal is generated according to the emitter distortion model described in Section II. It should be noted that we assume the number of harmonic components in (8) and the order of the Taylor series in (9) both are 2. We consider 5 emitters with the distortion parameters provided in Table IV, where the E and P are abbreviations for Emitters and Parameters, respectively, and to labels for emitter 1 to emitter 5. The modulation mode of the RF signal is QPSK, with the oversampling factor , MHz, and the signal center frequency is 1GHz. A frame consists of 128 symbols, wherein 32 symbols carry pilots.
-
2)
The settings of channel:
AWGN channel is considered in our experiments, so the channel fading coefficients in (21) is set to be 1. Nonetheless, the following experimental conclusions also apply to the case where the channel coefficients are random. -
3)
The settings of the receiver:
The receiver distortions are generated according to the receiver distortion model described in Section II. The distortion parameters of sampling jitter and quantization errors are set as follows: , , . The parameter in (13) for phase noise varies to show its influence on RFFI accuracy. -
4)
RF feature extraction methods:
Two classical RF feature extraction methods, i.e., least mean square (LMS)-based feature extraction [33] and intrinsic time-scale decomposition (ITD)-based feature extraction [21], are used in our experiments. The LMS-based feature extraction method updates its filter weights recursively based on some criteria until convergence, then uses its converged weight vector as features. The ITD-based feature extraction method first decomposes the signal by ITD and then calculates the skewness and kurtosis of each decomposed signal as the feature vector. -
5)
Classifiers:
Currently, there have been many successful classifiers applied to RFFI. However, since classifiers are not the focus of our paper, we choose the typical multi-classification SVM for RFF classification.
In the following experiments, the number of training frames and testing frames for each emitter is 200 and 100, respectively. Each experiment result is obtained by averaging over 1000 trials. We use ORS to represent the original scheme without distortion filtering and the weighted voting operation, which is used as a benchmark for the proposed schemes.
V-B Experimental results of MIWS
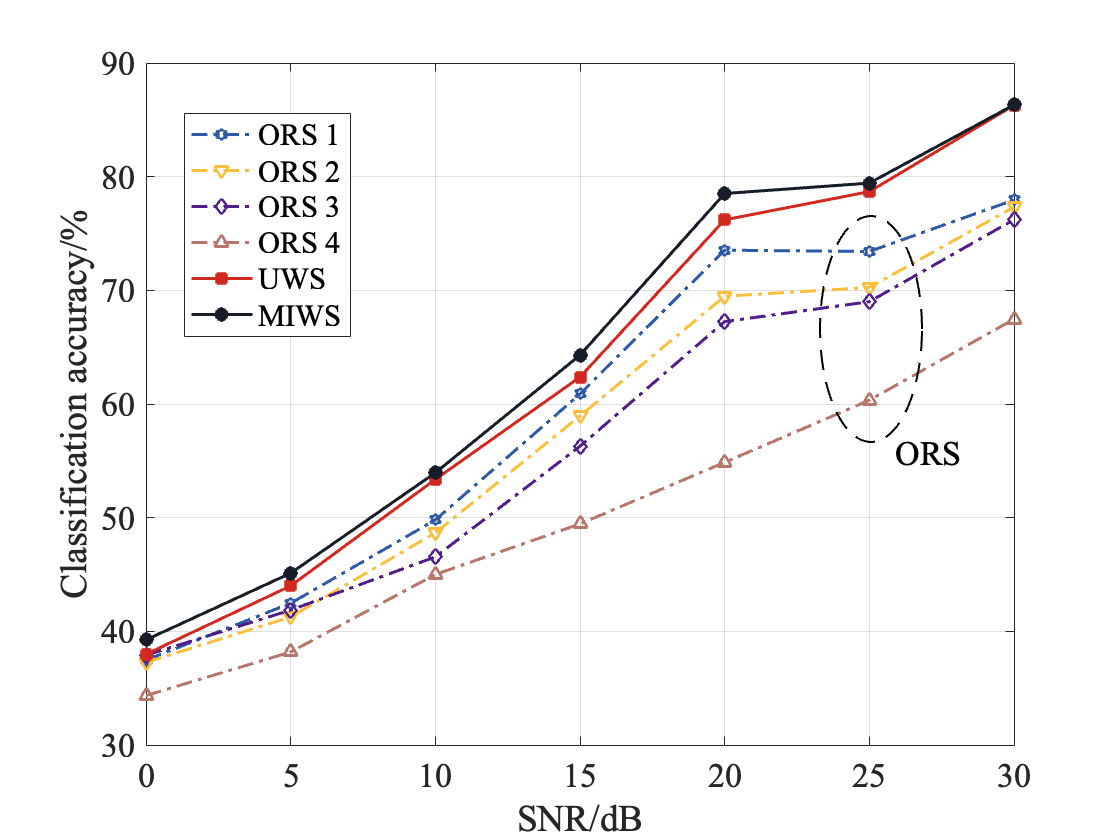
Fig. 4 depicts the results of RFFI accuracy with varying SNR for MIWS, where five emitters are present, the ITD-based feature extraction method is adopted, and the receiver is equipped with four antennas with of 0.001, 0.01, 0.1, 1, respectively. In this figure, UWS stands for the scheme of equally weighting the signals received by each antenna, while ORS represents the scheme that directly uses the signals at the th receiving antenna without any distortion filtering or weighting operation. It is noteworthy that the results of each ORS in this figure reveal that the larger the , the lower the recognition accuracy, which indicates that the ITD-based feature extraction method is sensitive to the phase noise at the receiver. Furthermore, the experimental results indicate that both MIWS and UWS outperform the ORS of each antenna, while the performance of MIWS is better than that of UWS, which highlights the benefit of setting weights according to MI.

Fig. 5 depicts the results of RFFI accuracy with varying SNR for MIWS, where the LMS-based feature extraction method is employed, and the other settings are the same as those in Fig. 4. Unlike the ORS with significant differences in Fig. 4, the ORS of each antenna maintains similar RFFI accuracy when varies in this figure. This observation suggests that the ITD-based feature extraction method is sensitive to phase noise at the receiver, whereas the LMS-based feature extraction method is robust to it. Therefore, there is no significant difference in the performance of MIWS and UWS when the LMS-based feature extraction method is applied. We also note that both MIWS and UWS enjoy a 10% accuracy gain when compared with ORS, thereby confirming the benefit of weighting when multiple received versions are configurated.
V-C Experimental results of DFS
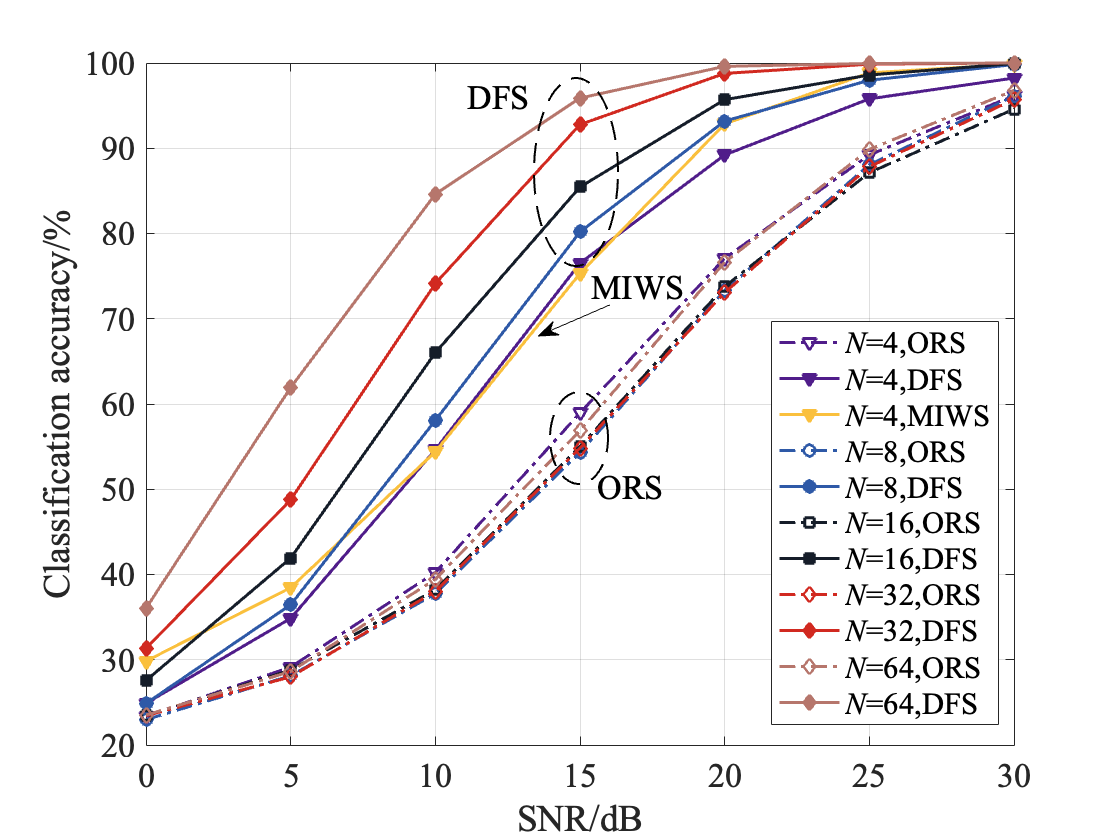
Fig. 6 shows the RFFI results of DFS, where the LMS-based feature extraction method is adopted with and for all receiver antennas. As can be seen from this figure, the superiority of DFS over ORS becomes increasingly apparent as increases. Such phenomenon that DFS outperforms ORS in terms of RFFI accuracy demonstrates that DFS can effectively filter out channel noise and receiver distortions. Moreover, there are two noteworthy points: 1) when , DFS performs worse than MIWS, suggesting that MIWS is more appropriate when ; 2) when SNR0dB, the performance gain of DFS over ORS is not obvious, whereas when SNR15dB, such gain becomes more significant for different s, indicating that the level of the performance gain of DFS with respect to ORS is related to the SNR. These two observations are consistent with the statements in Section IV.


Fig. 7 and Fig. 8 show the RFFI accuracy versus receiving phase noise when using the ITD-based RF feature extraction method. The former varies SNR with , and the latter varies with SNRdB. As seen from these two figures, the larger the , the worse the RFFI accuracy of ORS. In contrast, DFS shows its stability and robustness under different , which indicates that DFS filters out receiver phase noise effectively. Fig. 8 illustrates that the performance of DFS becomes better with the increasing number of receiving antennas, which remains consistent with the conclusion of Fig. 6.
V-D Experimental results of GDFWS

Figure 9 provides the performance of BDFWS in comparison with DFS when the LMS-based RF feature extraction method is employed. The receiving antennas are evenly divided into four groups, and the other settings are consistent with those in Fig. 6. When SNR10 dB and or , GDFWS with weighted voting outperforms DFS. However, when SNR10 dB, performance saturation does not appear in DFS, thus its performance is comparable with that of GDFWS. Moreover, when , the overall performance of GDFWS is inferior to that of DFS, which suggests that GDFWS is unsuitable for scenarios where . Overall, the results presented in this figure demonstrate the effectiveness of GDFWS with weighted voting in scenarios where and SNR10 dB when compared with DFS, the finding of which is consistent with the theoretical analysis presented in Section IV.
VI Conclusion
This paper investigates three RFFI schemes to cater to the different numbers of receiving antennas. When the number is small, we propose MIWS that uses the weighted voting of intermediate classification results for RFFI. For a moderate quantity of receiving antennas, DFS is proposed to perform statistical averaging to filter out channel noise and receiver distortions. If a large amount of receiving antennas are available, GDFWS, which enjoys the advantages of both MIWS and DFS, is developed to solve the performance saturation problem in DFS and improve classification accuracy. We further study the impact of the number of receiving antennas on DFS performance, and provide guidelines on selecting appropriate schemes for different scenarios in the following aspects: 1) When the number of antennas is , MIWS is recommended. 2) When the number of antennas is , DFS is the best choice. 3) The performance saturation in DFS occurs commonly when SNR is high. Hence, when and SNR10dB, GDFWS is preferable.
References
- [1] D. C. Nguyen, M. Ding, P. N. Pathirana, A. Seneviratne, J. Li, D. Niyato, O. Dobre, and H. V. Poor, “6g internet of things: A comprehensive survey,” IEEE Internet of Things Journal, vol. 9, no. 1, pp. 359–383, 2022.
- [2] F. Alshehri and G. Muhammad, “A comprehensive survey of the internet of things (iot) and ai-based smart healthcare,” IEEE Access, vol. 9, pp. 3660–3678, 2021.
- [3] R. Yu, X. Zhang, and M. Zhang, “Smart home security analysis system based on the internet of things,” in 2021 IEEE 2nd International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE), pp. 596–599, 2021.
- [4] J. Kurmi and R. Matam, “Device identification in iot networks using network trace fingerprinting,” in 2022 International Conference on Smart Applications, Communications and Networking (SmartNets), pp. 1–6, 2022.
- [5] I. Yaqoob, I. A. T. Hashem, A. Ahmed, S. A. Kazmi, and C. S. Hong, “Internet of things forensics: Recent advances, taxonomy, requirements, and open challenges,” Future Generation Computer Systems, vol. 92, pp. 265–275, 2019.
- [6] T. Nandy, M. Y. I. Idris, R. M. Noor, A. W. A. Wahab, S. Bhattacharyya, R. Kolandaisamy, and M. Yahuza, “A secure, privacy-preserving, and lightweight authentication scheme for vanets,” IEEE Sensors Journal, vol. 21, no. 18, pp. 20998–21011, 2021.
- [7] S. A. Jan, N. U. Amin, M. Othman, M. Ali, A. I. Umar, and A. Basir, “A survey on privacy-preserving authentication schemes in vanets: attacks, challenges and open issues,” IEEE Access, vol. 9, pp. 153701–153726, 2021.
- [8] N. Xie, Z. Li, and H. Tan, “A survey of physical-layer authentication in wireless communications,” IEEE Communications Surveys & Tutorials, vol. 23, no. 1, pp. 282–310, 2021.
- [9] J. Hall, M. Barbeau, E. Kranakis, et al., “Detection of transient in radio frequency fingerprinting using signal phase,” Wireless and optical communications, pp. 13–18, 2003.
- [10] Y. Chen, X. Chen, and Y. Lei, “Emitter identification of digital modulation transmitter based on nonlinearity and modulation distortion of power amplifier,” Sensors, vol. 21, no. 13, p. 4362, 2021.
- [11] W. Nie, Z.-C. Han, M. Zhou, L.-B. Xie, and Q. Jiang, “Uav detection and identification based on wifi signal and rf fingerprint,” IEEE Sensors Journal, vol. 21, no. 12, pp. 13540–13550, 2021.
- [12] N. Soltanieh, Y. Norouzi, Y. Yang, and N. C. Karmakar, “A review of radio frequency fingerprinting techniques,” IEEE Journal of Radio Frequency Identification, vol. 4, no. 3, pp. 222–233, 2020.
- [13] J. Toonstra and W. Kinsner, “Transient analysis and genetic algorithms for classification,” in IEEE WESCANEX 95. Communications, Power, and Computing. Conference Proceedings, vol. 2, pp. 432–437, 1995.
- [14] Q. Li, Y. Jin, S. Yan, and S. Han, “Emitter identification based on improved variational modal decomposition at low snr,” in 2021 International Conference on Artificial Intelligence and Electromechanical Automation (AIEA), pp. 152–156, 2021.
- [15] Y. Li, X. Chen, Y. Lin, G. Srivastava, and S. Liu, “Wireless transmitter identification based on device imperfections,” IEEE Access, vol. 8, pp. 59305–59314, 2020.
- [16] M. Zeng, Z. Liu, Z. Wang, H. Liu, Y. Li, and H. Yang, “An adaptive specific emitter identification system for dynamic noise domain,” IEEE Internet of Things Journal, vol. 9, no. 24, pp. 25117–25135, 2022.
- [17] L. Sun, X. Wang, Z. Huang, and B. Li, “Radio-frequency fingerprint extraction based on feature inhomogeneity,” IEEE Internet of Things Journal, vol. 9, no. 18, pp. 17292–17308, 2022.
- [18] H. Yuan, Y. Yan, Z. Bao, C. Xu, J. Gu, and J. Wang, “Multipath canceled rf fingerprinting for wireless ofdm devices based on hammerstein system parameter separation,” IEEE Canadian Journal of Electrical and Computer Engineering, vol. 45, no. 4, pp. 401–408, 2022.
- [19] M. Shi, Y. Huang, and G. Wang, “Carrier leakage estimation method for cross-receiver specific emitter identification,” IEEE Access, vol. 9, pp. 26301–26312, 2021.
- [20] A. D’Andrea, V. Lottici, and R. Reggiannini, “RF power amplifier linearization through amplitude and phase predistortion,” IEEE Transactions on Communications, vol. 44, no. 11, pp. 1477–1484, 1996.
- [21] B. He, F. Wang, Y. Liu, and S. Wang, “Specific emitter identification via multiple distorted receivers,” in 2019 IEEE International Conference on Communications Workshops (ICC Workshops), pp. 1–6, 2019.
- [22] P. Zhang, Y. Shen, X. Jiang, and B. Wu, “Physical layer authentication jointly utilizing channel and phase noise in mimo systems,” IEEE Transactions on Communications, vol. 68, no. 4, pp. 2446–2458, 2020.
- [23] Y. Huang and H. Zheng, “Theoretical performance analysis of radio frequency fingerprinting under receiver distortions,” Wireless Communications and Mobile Computing, vol. 15, no. 5, pp. 823–833, 2015.
- [24] Y. Liu and P. Zhang, “Physical layer authentication utilizing carrier frequency offset in dynamic mimo systems,” in 2020 International Conference on Networking and Network Applications (NaNA), pp. 16–21, 2020.
- [25] P. Zhang, J. Liu, Y. Shen, and X. Jiang, “Exploiting channel gain and phase noise for phy-layer authentication in massive mimo systems,” IEEE Transactions on Information Forensics and Security, vol. 16, pp. 4265–4279, 2021.
- [26] M. R. Bell, Information theory and radar: Mutual information and the design and analysis of radar waveforms and systems. PhD thesis, California Institute of Technology, 1988.
- [27] X. Wang, S. Ju, X. Zhang, S. Ramjee, and A. E. Gamal, “Efficient training of deep classifiers for wireless source identification using test snr estimates,” IEEE Wireless Communications Letters, vol. 9, no. 8, pp. 1314–1318, 2020.
- [28] N. Alagha, “Cramer-rao bounds of snr estimates for bpsk and qpsk modulated signals,” IEEE Communications Letters, vol. 5, no. 1, pp. 10–12, 2001.
- [29] J. Stahl and P. Mowlaee, “A simple and effective framework for a priori snr estimation,” in 2018 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), pp. 5644–5648, 2018.
- [30] M. Ju, L. Xu, L. Jin, and D. Defeng Huang, “Data aided channel estimation for massive mimo with pilot contamination,” in 2017 IEEE International Conference on Communications (ICC), pp. 1–6, 2017.
- [31] A. N. Uwaechia and N. M. Mahyuddin, “Spectrum-efficient distributed compressed sensing based channel estimation for ofdm systems over doubly selective channels,” IEEE Access, vol. 7, pp. 35072–35088, 2019.
- [32] S. M. Ross, Introductory statistics. Academic Press, 2017.
- [33] Y. Yang, A. Hu, Y. Xing, J. Yu, and Z. Zhang, “A data-independent radio frequency fingerprint extraction scheme,” IEEE Wireless Communications Letters, vol. 10, no. 11, pp. 2524–2527, 2021.