Joint Optimization of Communication Enhancement and Location Privacy Protection in RIS-Assisted Underwater Communication System
Abstract
As the demand for underwater communication continues to grow, underwater acoustic RIS (UARIS), as an emerging paradigm in underwater acoustic communication (UAC), can significantly improve the communication rate of underwater acoustic systems. However, in open underwater environments, the location of the source node is highly susceptible to being obtained by eavesdropping nodes through correlation analysis, leading to the issue of location privacy in underwater communication systems, which has been overlooked by many studies. To enhance underwater communication and protect location privacy, we propose a novel UARIS architecture integrated with an artificial noise (AN) module. This architecture not only improves communication quality but also introduces noise to interfere with the eavesdroppers’ attempts to locate the source node. We derive the Cramér-Rao Lower Bound (CRLB) for the localization method deployed by the eavesdroppers and, based on this, model the UARIS-assisted communication scenario as a multi-objective optimization problem. This problem optimizes transmission beamforming, reflective precoding, and noise factors to maximize communication performance and location privacy protection. To efficiently solve this non-convex optimization problem, we develop an iterative algorithm based on fractional programming. Simulation results validate that the proposed system significantly enhances data transmission rates while effectively maintaining the location privacy of the source node in UAC systems.
Index Terms:
Underwater acoustic RIS, communication enhancement, location privacy, noise factor.I Introduction
In recent years, with the flourishing development of the marine economy, underwater Internet of Things devices based on acoustic communication, such as underwater sensors and Autonomous Underwater Vehicles (AUVs), have become extremely important for the exploration and utilization of the ocean. Meanwhile, underwater acoustic communication (UAC) has a wide range of applications, including real-time data collection on water, natural disaster prevention, marine resource exploration, and maritime security [1], [2]. However, compared to terrestrial wireless communication systems, the data rate of UAC systems is so low, remaining at the kilobits per second (kbps) level, that it is difficult for UAC to support the normal operation of most underwater applications [3], [4]. This low data rate issue is caused by the characteristics of the underwater environment, particularly in shallow water, where the low bandwidth of sound waves and severe multipath fading contribute to the problem [5].
To ensure the reliability and stability of UAC systems, many existing studies aim to improve the transmission rate of these systems through underwater acoustic reconfigurable intelligent surfaces (UARIS). Specifically, UARIS can be deployed beneath ships, buoys, or AUVs for underwater operations [6]. The UARIS is capable of altering the amplitude and phase of incident acoustic signals and generating strongly reflected paths through beamforming [7]. Compared to natural UAC channels, this newly formed reflected path can significantly enhance the signal-to-noise ratio (SNR) at the receiver, thereby achieving higher data transmission rates.
Many existing studies focus on enhancing communication in underwater environments, but few have considered the issue of location privacy in underwater communication. Due to the openness of the underwater communication environment, the source node (SN) of the transmitted signal is highly susceptible to being located by illegal eavesdropping nodes (ENs) through analysis of the received signals, thereby threatening the privacy and security of the node. In this context, the challenge lies in leveraging Reconfigurable Intelligent Surface (RIS) technology to enhance underwater communication while protecting the location information of the source. Some studies achieve interference with ENs through the synergy of artificial noise (AN) from the transmitter and RIS [8], [9]. However, these studies assume that the source and RIS have prior knowledge of the eavesdropper location, which does not align with real-world eavesdropping scenarios.
Therefore, we add an AN module to the UARIS, enabling the UARIS to intelligently control the reflected signals while ensuring communication quality, and simultaneously introduce additional noise signals to interfere with the attempts of ENs to infer the SN location. The main contributions of this paper are summarized as follows:
The main contributions of this work are outlined as follows:
-
•
We propose a UARIS architecture with an AN module. This module introduces noise into the reflected signals to interfere with illegal ENs, preventing them from locating the SN. This design overcomes the limitation of previous assumptions that required prior knowledge of the locations of the ENs, enhancing privacy protection in real-world eavesdropping scenarios.
-
•
We design a mechanism for underwater communication enhancement and location privacy protection based on acoustic RIS and AN. Specifically, by intelligently controlling the amplitude and phase of the reflected signals, UARIS not only improves the SNR at the receiver, enhancing communication performance but also introduces dynamically controllable AN to protect the location privacy of the SN. This mechanism not only enhances communication stability but also addresses the need to protect the location privacy of the SN.
-
•
We model underwater communication enhancement and location privacy protection as a multi-objective optimization problem. This problem optimizes transmission beamforming, reflective precoding, and noise factors to maximize communication performance while protecting the privacy of the SN. The paper provides a detailed derivation of the Signal-to-Interference-plus-Noise Ratio (SINR) calculation and analyzes the impact of the noise factor on location privacy based on the Cramér-Rao Lower Bound (CRLB).
-
•
To address the non-convexity of the optimization problem, this work employs fractional programming (FP) to decouple it and proposes an iterative algorithm for jointly optimizing the transmission beamforming, reflection matrix, and noise factor. In each iteration, the auxiliary variables, noise factor, beamforming vector, and reflection matrix are optimized step by step, gradually converging to a locally optimal solution, thereby improving the algorithm’s efficiency and stability.
The structure of this paper is as follows: Section II introduces the related works. Section III presents a detailed exposition of a downlink shallow water communication scenario based on UARIS. Section IV describes a semi-blind localization method for ENs without prior channel information and conducts a CRLB analysis. Section V designs an optimization scheme for joint transmit beamforming, reflective precoding, and noise factor. Section VI validates the performance and relevant metrics of the proposed mechanism. Section VII is the conclusion of the entire paper.
Notations: , and denote the sets of complex, real and positive real numbers, respectively. , , and represent the transpose, conjugate, conjugate-transpose and inverse operations of a matrix, respectively. and denote the Euclidean norm and the Frobenius norm of the argument, respectively. is the identity matrix. denotes the -th column of the identity matrix. and denote the real and imaginary parts of the complex-valued arguments, respectively. represents the largest eigenvalue of the matrix. forms an diagonal matrix from a -dimensional vector argument. denotes the complex multivariate Gaussian distribution with mean and variance .
II Related Works
II-A Reconfigurable Intelligent Surface
RIS is an emerging paradigm in the field of wireless communications that controls and optimizes signal propagation paths by intelligently adjusting the phase and amplitude of its reflective elements [10]. Comprising a large number of controllable reflective units, RIS can dynamically alter the direction, strength, and coverage of electromagnetic waves, thereby enhancing signal quality, improving communication efficiency, and reducing interference. Specifically, Huang [11] proposed a multi-user MISO system based on passive RIS, significantly improving the energy efficiency by optimizing the power allocation of the base station and the passive RIS reflection phase design. However, during the research on passive RIS, it was found that RIS introduces a ”multiplicative fading effect,” where the path loss of the transmitter-RIS-receiver link is the product of the path losses of the transmitter-RIS link and the RIS-receiver link (rather than their sum), resulting in the gain of the reflected link being much smaller than that of the direct link [12]. To overcome the multiplicative fading introduced by RIS, Zhang [13] proposed an active RIS architecture integrated with reflection-type amplifiers and optimizes joint beamforming and reflective precoding in a multi-user MISO system, significantly enhancing the capacity gain of the communication system.
Different from wireless channels, the highly complex characteristics of underwater acoustic channels make the application of RIS in UAC systems more challenging. Wang [14] proposed an acoustic RIS design, which enhances the capacity and reliability of underwater communication systems through new hardware, ultra-wideband beamforming, and practical operational protocols. Simulations verify that this system significantly improves data transmission rates in underwater environments, addressing the low data rate and unreliable channel issues in traditional UAC systems. However, the current designs and optimizations of UARIS are only focused on communication enhancement. To further protect the location privacy, we need to improve the existing UARIS architecture.
II-B Underwater Acoustic Localization Method
Due to the complexity and high dynamics of the underwater environment, underwater acoustic localization (UAL) is highly challenging. Currently, most existing UAL methods can be divided into two categories: Direction of Arrival (DoA)-based methods and Time of Arrival (ToA)-based methods. The DoA methods estimate the position of the SN by measuring the direction of arrival of sound waves from the source to the receiver and using the angle information from multiple receivers. Zhang [15] proposed an array aperture extension method based on covariance matrix reconstruction, which increases virtual array elements by constraining the amplitude and phase, thereby improving the precision and resolution capability of DoA estimation in underwater acoustic systems. Liu [16] proposed an iterative technique for joint estimation of position and sound propagation speed in underwater environments characterized by an isogradient sound speed profile. Through stratification compensation and iterative refinement, the accuracy of the source DoA estimation was improved.
Meanwhile, the ToA method estimates the position of the SN by measuring the propagation time of sound waves from the source to the receiver and using known sound speed and measurements from multiple receiving nodes (RNs). Sun [17] proposed an underwater acoustic localization algorithm based on the Generalized Second-Order ToA to locate a black box sunk on the seabed, addressing the impact of signal period drift on localization accuracy. Li [18] proposed a long baseline underwater acoustic localization method based on particle filtering and ”track-before-detect” technology, aiming to address the direct sound selection problem in traditional ToA localization methods.
However, in most current research on UAL, the nodes performing localization often have access to a significant amount of prior knowledge, which may be challenging to obtain in practical underwater localization scenarios. Therefore, in UAC systems, an EN requires a method for localization that does not rely on extensive prior knowledge.
II-C Underwater Location Privacy Protection
Whether in terrestrial wireless communication or UAC, the openness of the communication environment can expose the SN to localization attacks by unauthorized ENs. Therefore, to protect the location privacy of the SN, many studies have proposed interference and defense strategies against ENs. Fan [19] proposed a secure localization scheme for underwater acoustic sensor networks based on autonomous underwater vehicle formation and cooperative beamforming to defend against eavesdropping attacks. Liu [20]employed an unmanned aerial vehicle (UAV) to jam eavesdroppers by optimizing its trajectory and jamming power. It improved physical layer security by emitting AN, which degrades the eavesdropping channel while maintaining good communication with legitimate receivers. Hou [21] defended against eavesdropping localization attacks by using UAVs to emit AN and optimizing the UAV trajectory and jamming power.
However, most studies assume that the SN can obtain the location information or even the channel information of the ENs, which is difficult to achieve in real eavesdropping scenarios. Therefore, we need a method that can perform jamming without requiring any prior knowledge of the ENs to protect the location privacy of the SN.
III System Model
In this paper, we consider a typical downlink UARIS-assisted shallow water communication scenario, which is shown in Fig. 1, consisting of one SN with underwater antennas, one UARIS with reflection elements, and legitimate single-antenna RNs, of which the set is . The position coordinates of these three entities are defined as , and , respectively, and assume that the three can share location information. Additionally, in the open shallow water environment, there are ENs that attempt to illegally locate the SN by analyzing the received signals. The set of ENs is denoted as , and their position are defined as . We assume that the SN is static and located sufficiently far from the RNs and all ENs, allowing for a plane wavefront (far-field) approximation in the shallow water waveguide.

In this communication scenario, we assume ENs can share all information, including the received signals and their respective location. Furthermore, the ENs can obtain the location of the UARIS, while the UARIS cannot obtain the location information of the ENs.
III-A Underwater Acoustic RIS
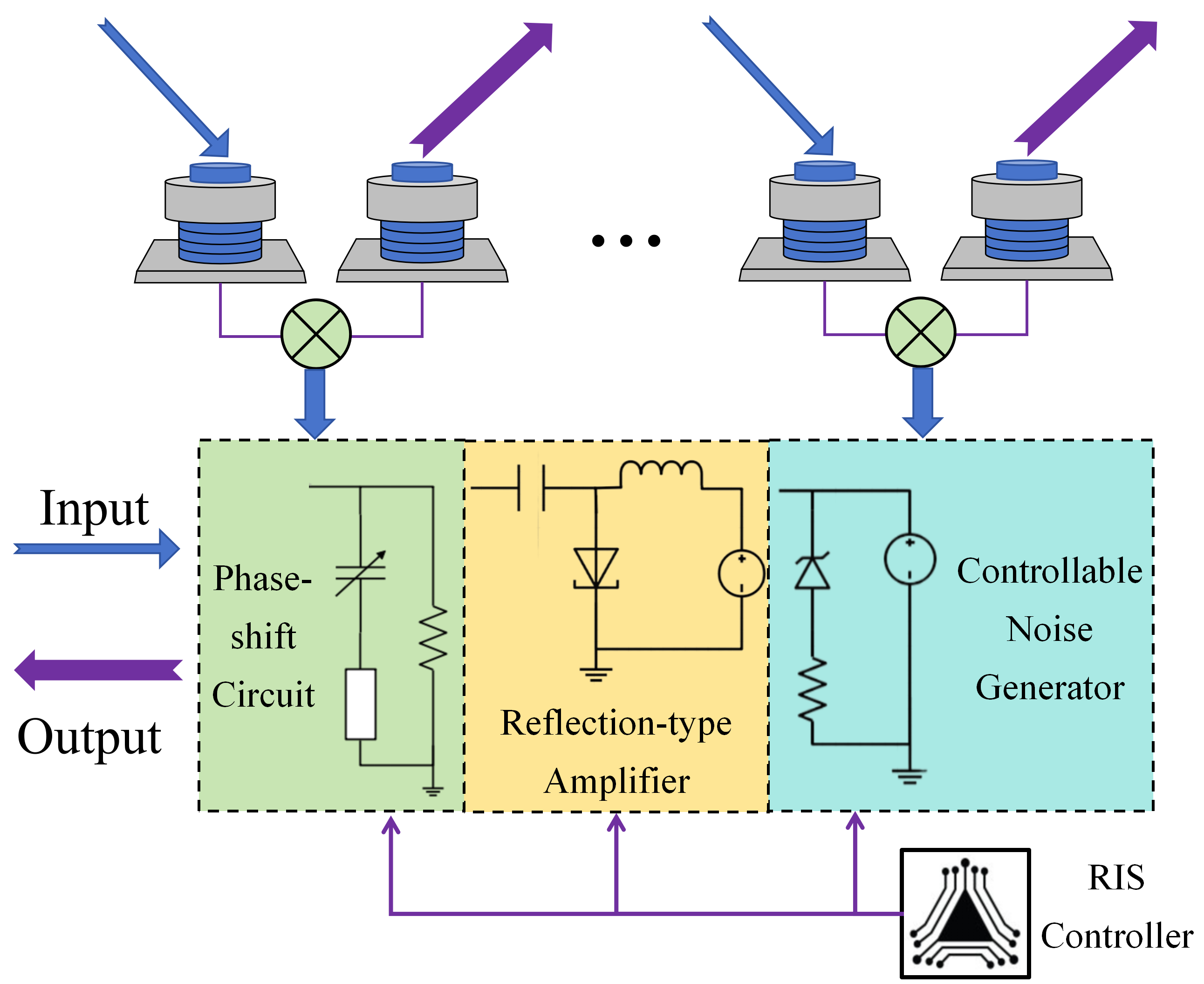
The UARIS enhances underwater communication by absorbing and radiating sound waves, with its working mechanism summarized as ”absorption first, radiation later.” Specifically, each reflection unit of the UARIS consists of two piezoelectric elements. When sound waves impinge on the surface of the acoustic UARIS, the piezoelectric elements first absorb the acoustic energy and adjust the phase and amplitude of the reflected sound waves through internal circuits. The adjusted sound waves are then radiated by another piezoelectric element, thereby achieving intelligent control of the sound waves. Additionally, each reflection unit is integrated with a reflection-type power amplifier, allowing the UARIS to amplify the signal while reflecting it, thus overcoming the attenuation of underwater acoustic signals. This active feature not only effectively improves the quality and SNR of the communication signal but also enables the protection of the SN’s location privacy by adding AN.
With the support of the existing UARIS architecture, the reflected and amplified signals of the -element UARIS can be formulated as follows:
| (1a) | |||
| (1b) | |||
where represents the reflection coefficient matrix of the UARIS, in which and denote the amplification factor and the phase shift factor of element . Meanwhile, the active characteristics of UARIS introduce corresponding noise, which can be categorized into dynamic noise and static noise . Specifically, is related to the input noise of UARIS and the inherent device noise, while mainly represents the noise generated by the phase shift circuit. Since the energy of is extremely small compared to , is neglected in the subsequent analysis.
Additionally, the noise generated at the UARIS can be considered the AN to interfere with the ENs [22]. To further protect the location privacy of the SN, we introduce a controllable noise generator to dynamically adjust the AN introduced at the UARIS, of which the architecture is shown in Fig. 2. Specifically, based on the structure shown in Fig. 2, we can model the AN as , wherein denotes the noise factor of the AN generated at the UARIS.
III-B Underwater Acoustic Channel Model
In this work, the primary research scenario is the acoustic propagation environment in shallow water areas. Different from wireless communications, the unique characteristics of underwater acoustic channels make the study of underwater signal transmission more complex and challenging. The attenuation pattern of underwater acoustic signals with respect to distance and frequency can be modeled as
| (2) |
where denotes the propagation factor. According to [23], the absorption coefficient can be obtained using Thorp’s formula, which is formulated as
| (3) |
III-C Communication Model of the Receiving Node
In this subsection, we will provide a detailed introduction to the application scenarios of UARIS-assisted UAC enhancement. Specifically, we consider a downlink UAC scenario and denote the symbol vector transmitted to RNs as , which satisfies . As shown in Fig. 1 , let , and denote the channel matrix between the SN and RN , that between the SN and the UARIS and that between the UARIS and RN . Then, according to (1a), signal received at RN can be modeled as
| (4) |
where denotes the beamforming vector designed by the SN for symbol . Additionally, denotes the AN introduced by the UARIS, while denote the background noise introduced at RN , with .
III-D Reception Signal Model of the Eavesdropping Node
This subsection will introduce modeling the signals received by ENs in a shallow water environment. Specifically, assume that ENs possess spatial diversity and time synchronization characteristics, and each EN is equipped with an omni-directional hydrophone. Meanwhile, each EN records the received acoustic signals at predetermined observation intervals, then producing samples after sampling and baseband conversion. In addition, the scope of this work focuses on (approximately) constant-velocity environments and high-frequency signals, where the straight-line model is approximately valid.
Based on the three-ray model in [24], we added a transmission path through the UARIS, thus forming the four-ray model for shallow water transmission, illustrated in Fig. 1. In this model, the four signal transmission paths are respectively:
-
1.
: The direct LOS path;
-
2.
: The sea surface reflected NLOS path;
-
3.
: The seabed reflected NLOS path;
-
4.
: The UARIS reflected NLOS path.
According to Fig. 1, the corresponding distances of these four paths can be further obtained, which are given by
| (5a) | |||
| (5b) | |||
| (5c) | |||
| (5d) | |||
where denotes the depth of the seabed, and represents the horizontal distance between the SN and EN , which is defined as . We can further obtain the transmission delays for each path as follows:
| (6) |
where represents the sound speed in shallow water.
Formally, the frequency domain representation of the sampled baseband-converted signal obtained from EN can be modeled as
| (7) |
where denotes the frequency domain representation of the signal transmitted by the SN and represents the angular frequency of the -th frequency component. Additionally, let and denote the channel matrix between the SN and EN , and that between the UARIS and EN . Then, the noise can be denoted as
| (8) |
where is the background noise which satisfies . Meanwhile, we can obtain the attenuation coefficients , which can be formulated as
| (9a) | ||||
| (9b) | ||||
| (9c) | ||||
| (9d) | ||||
where is the seabed reflection coefficient.
For shorthand, we further define
| (10a) | |||
| (10b) | |||
| (10c) | |||
| (10d) | |||
IV Semi-Blind Localization Method of the Eavesdropping Node
In this section, we introduce a localization method deployed at the ENs. Traditional underwater acoustic localization methods require a significant amount of prior knowledge, including channel information; however, such assumptions are difficult to establish in the eavesdropping localization model. Therefore, the ENs require a more robust localization method that do not rely on prior channel information to localize the SN, named Semi-Blind Localization (SBL) method [24]. The following will provide a detailed analysis of this method and its Cramér-Rao Lower Bound (CRLB).
IV-A Semi-Blind Localization Method
To more accurately reflect the eavesdropping issue in a shallow open-sea environment, we assume the EN has no access to any information about the SN. Specifically, the EN has no prior knowledge of the channel matrix or the signal waveform transmitted by the SN. The EN only knows the seabed depth and the sound speed . Without of generality, we can further assume that viz., , where denotes the -dimensional unit sphere [24].
The solution of the SBL method can be regarded as the Maximum Likelihood Estimate (MLE) of , obtained through the joint estimation of all unknown deterministic model parameters. In this case, the maximum likelihood value of is the solution to a nonlinear least squares problem:
| (12) |
Different from other traditional shallow sea localization methods, the SBL method we employ introduces some additional computational complexity but is more suited to practical eavesdropping localization scenarios and offers higher robustness. The method is summarized in Algorithm 1, of which further analysis can be obtained in [24].
| (13) |
| (14) |
| (15) |
| (16) |
IV-B The Cramér-Rao Lower Bound Analysis for SBL
In this subsection, we primarily analyze the Cramér-Rao Lower Bound (CRLB) for the SBL method. Specifically, without loss of generality, we focus on analyzing a spectrally flat waveform [24]. Therefore, for all , which means that the ENs can directly estimate the phase of the unknown source signal waveform. Meanwhile, since the EN also needs to estimate the unknown channel attenuation coefficient, the phase parameters to be estimated have only degrees of freedom, that is, the ENs only need to estimate .
To facilitate further derivation, we additionally define , , and . Thus, (11) can be rewritten as
| (17) |
Furthermore, according to (8), we can obtain that . Denoting , wherein , it follows that
| (18) |
Thus, we can calculate the Fisher information matrix (FIM) elements for the Complex Normal (CN) signal model , which can be formulated as [26]
| (19) | ||||
where let denote the vector of all unknown deterministic parameters that the ENs need to estimate, which is defined as
| (20) |
where represents the number of parameters to be estimated, and we define as the FIM.
In the received signal model of the ENs, the parameters to be estimated differ between the mean vector and the covariance matrix. Therefore, we can further deduce that
| (21a) | |||
| (21b) | |||
namely the FIM has a block diagonal structure. Consequently, the elements in corresponding to the estimated parameters related to the signal model can be calculated as
| (22) |
To obtain the complete FIM, we also need to compute the derivative of with respect to the parameters , which can be formulated as for all , , and
| (23) |
| (24) |
| (25) |
| (26) |
By substituting (23)-(26) into (22), the complete FIM can be computed. Furthermore, according to (22), it can be observed that the FIM block related to the signal components is inversely proportional to the noise introduced by the UARIS. Therefore, the CRLB block associated with the signal components is directly proportional to . Finally, the CRLB for this signal estimation model can be given by
| (27a) | |||
| (27b) | |||
V Joint Transmit Bemaforming and Reflect Precoding Design with Artificial Noise
To investigate the communication enhancement and location privacy protection supported by the underwater acoustic RIS with AN sources in underwater communication scenarios, we will model a multi-objective optimization problem for this scenario in this section. Furthermore, a joint optimization scheme for transmit beamforming, reflective precoding, and noise factor is proposed.
V-A Problem Formulation
According to the underwater communication model in (4), the signal-to-interference-plus-noise ratio (SINR) at RN can be calculated as
| (28a) | |||
| (28b) | |||
where represents the equivalent channel vector between the SN and RN .
Furthermore, to jointly optimize the UARIS-assisted communication enhancement and location privacy protection, we formulate the following optimization problem:
| (29a) | ||||
| s.t. | (29b) | |||
| (29c) | ||||
| (29d) | ||||
where .
According to the CRLB analysis in Subsection IV-B, since the is directly proportional to the controllable noise introduced by the UARIS, the optimization problem (29) can be reformulated as
| (30a) | ||||
| s.t. | (30b) | |||
| (30c) | ||||
| (30d) | ||||
where represents the weight parameter that balances communication enhancement and location privacy protection, and we further define . Moreover, for sufficiently large and , can be approximated by . Thus, the optimization problem (30) can be reformulated as
| (31a) | ||||
| s.t. | (31b) | |||
| (31c) | ||||
| (31d) | ||||
The non-convexity of (31) makes it challenging to solve directly. To handle this non-convex logarithmic and fractional problem, we employ the Fractional Programming (FP) method to decouple (31), enabling the optimization of multiple variables separately. Therefore, the following lemma needs to be introduced [27]:
Lemma 1
By introducing auxiliary variables and based on (31), it can be equivalently transformed into
| (32a) | ||||
| s.t. | (32b) | |||
| (32c) | ||||
| (32d) | ||||
Detailed proof can be found in [27].
V-B Joint Optimization Scheme for Beamforming, Reflection Matrix, and Noise Factor
Based on Lemma 1, the original joint optimization problem can be decoupled into an alternate optimization of the SN beamforming vector , UARIS reflection matrix , noise factor , auxiliary variables and . According to [27], if all variables in Problem 1 are optimal in each iteration update, a locally optimal solution to (32) can be obtained after convergence. Therefore, we will provide a detailed introduction to the optimization steps for each variable, and summarize the proposed joint optimization scheme in Algorithm 2.
-
1.
Optimize : Fix variables , and optimize auxiliary variables as
(33) -
2.
Optimize : Fix variables , and optimize auxiliary variables by solving as
(34) -
3.
Optimize : Fix variables , and optimize the noise factor by solving as
(35a) (35b) -
4.
Optimize : For shorthand, we further define
(36a) (36b) Then, fix variables , and obtain a new optimization problem for the SN beamforming vector based on (32), which can be formulated as
(37a) s.t. (37b) (37c) As a standard quadratic constraint quadratic programming, optimization problem (37) can be solved directly using CVX tool to obtain the optimal beamforming vector .
-
5.
Optimize : For shorthand, we further define
(38a) (38b) (38c) Then, fix variables , and obtain a new optimization problem for the UARIS reflection matrix based on (32), which can be formulated as
(39a) s.t. (39b) Furthermore, we use the Lagrange multiplier method to solve optimization problem (39). Specifically, we introduce the Lagrange multiplier and construct the Lagrange function as
(40) Next, take the derivative of the Lagrange function with respect to and set the derivative to zero:
(41)
V-C Convergence Analysis
In this subsection, we will conduct a convergence analysis of the proposed joint optimization algorithm. Specifically, Algorithm 2 decouples the joint optimization problem of beamforming, reflection matrix, and noise factors into several subproblems. Since the updates in each iteration of Algorithm 2 are optimal solutions to these subproblems, the algorithm can converge to a local optimum after multiple iterations. A detailed proof will be provided next.
To facilitate the proof, we introduce the superscript for each variable to denote its value in the -th iteration. Then, the convergence of Algorithm 2 can be formulated as
| (43) | ||||
wherein the validity of (i) and (ii) holds because, in the -th iteration, and are the optimal solutions to subproblems (37) and (39), respectively, in that iteration. Meanwhile, (iii), (iv) and (v) follow since in the -th iteration, , , and are all updates that maximize . Therefore, the optimization objective is monotonically non-decreasing in each iteration. Additionally, due to the constraints in (32b), (32c) and (32d), the value of is upper-bounded, which ensures that Algorithm 2 will converge to a local optimum.
VI Simulation Results and Analysis
In this subsection, we will conduct a simulation to validate the proposed joint optimization scheme. Specifically, in Subsection VI-B, we validate the CRLB analysis provided in (27). In Subsection VI-C, simulation results are presented to evaluate the coverage performance of the UARIS-assisted underwater communication system with AN. In Subsection VI-D and VI-E, we discuss the impact of optimized weight on the performance optimization of the proposed scheme. Finally, in Subsection VI-F, the impact of the number of UARIS elements on optimization performance is explored from the hardware perspective.
VI-A Simulation Setting
In the simulation experiments, we assume the presence of four legitimate receiving nodes, all evenly distributed on a spherical surface with point as the center of the sphere. Meanwhile, let denote the average distance between the SN and the RNs, and represents the average distance between the ENs and the RNs. The other simulation parameters are summarized in Table I. Additionally, to ensure the fairness of the comparative experiments, we define a total power limit . Specifically, for the UARIS-assisted UAC system, the total power is given by , wherein and . For the UAC system without UARIS, the total power is given by . To demonstrate the effectiveness of the proposed joint optimization scheme, we conduct simulations for the following three schemes:
-
1.
Without UARIS (M1): In an underwater communication system without UARIS, the WMMSE algorithm proposed in [29] is used to optimize the beamforming of the SN.
-
2.
UARIS with fixed noise (M2): In a UARIS-assisted underwater communication system with fixed noise, the algorithm proposed in [13] is used to jointly optimize the beamforming of the SN and the reflection matrix of the UARIS.
-
3.
UARIS with AN (M3): In a UARIS-assisted underwater communication system with AN, the proposed Algorithm 2 is used to jointly optimize the beamforming of the SN, the reflection matrix of the UARIS and the noise factor.



| Parameters | Value |
|---|---|
| Propagation factor [30] | 1.5 |
| Acoustic signal frequency | 5kHz |
| Number of underwater antennas | 4 |
| Number of reflection elements | 512 |
| Background noise power | -60dBm |
| Minimum AN power | -60dBm |
| Seabed reflection coefficient [24] | 0.85 |
| Sampling time interval of the ENs | 0.001s |
| Number of sampling points | 64 |
| Speed of underwater sound | 1500m/s |
| Seabed depth | 100m |
| Position of SN | (200.7m,140.6m,50.2m) |
| Position of UARIS | (500m,210m,30m) |


VI-B Validation of the CRLB
In this subsection, we validate the CRLB analysis of (27). Specifically, the experimental parameters are set as , , and . Then, we solve the 95% confidence ellipses for the three schemes based on (27) and overlay the estimated pSBL results from 50 Monte Carlo experiments.
As shown in Fig. 3, due to the CRLB, the empirical results exhibit a good fit with the predicted theoretical accuracy, which aligns with our analytical derivation of the bound. Meanwhile, comparing Fig. 3(c) with Fig. 3(a) and Fig. 3(b), it can be observed that the proposed scheme significantly reduces the theoretical localization accuracy of the ENs for the SN. This aligns with the inference shown in (22), which states that the CRLB of the eavesdropping localization is proportional to the noise introduced by UARIS.
VI-C Coverage Performance of Different Schemes
In this subsection, to observe the coverage performance of the proposed UARIS-based new architecture, we plot the relationship between the sum-rate and the average distance between the SN and the RNs by adjusting and conducting Monte Carlo experiments.
As shown in Fig. 4, compared to the UAC without UARIS, although the case of UARIS with fixed noise significantly improves the sum rate of the underwater communication system, it fails to ensure the location privacy of the SN. When the distance is larger, the Root Mean Square (RMS) miss distance of its localization is smaller than that of the UAC without UARIS. Furthermore, compared to the UAC without UARIS, the proposed scheme not only improves the sum rate of the underwater communication system by 97%, but also enhances the RMS miss distance of the eavesdropping localization by approximately 5.5 times. Compared to the case of UARIS with fixed noise, although the proposed scheme reduces the sum-rate by 21.4%, it enhances the RMS miss distance of the eavesdropping localization by approximately 11.2 times.
These results indicate that the proposed scheme can enhance the communication performance of the underwater communication system while protecting the location privacy of the SN.
VI-D Effect of the Optimization Weight
As a critical parameter in optimization problem (31), the optimization weight plays a decisive role in the final optimization result. Therefore, to explore the impact of different optimization weights on performance, under the experimental settings of , and , we conducted Monte Carlo experiments with various values of the weight .
As shown in Fig. 5, when the optimization weight is minimal, such as , the optimization result of the proposed scheme is almost identical to that of UARIS with fixed noise. This indicates that a minimal weight leads the proposed scheme to focus solely on optimizing the sum rate. However, when the optimization weight is larger, such as and , the proposed scheme can improve the sum rate of the UAC system while protecting the SN location privacy. Specifically, when the optimization weight , compared to the case of UARIS with fixed noise, the proposed scheme improves the eavesdropping localization error by approximately 14.5 times while only reducing the sum-rate by 12.7%. When the optimization weight , compared to Scheme 2, the proposed scheme improves the eavesdropping localization error by approximately 18.0 times while only reducing the communication rate by 18.9%.
Additionally, it can be observed from Fig. 5 that as the weight increases, the optimized system sum rate decreases, while the RMS miss distance of eavesdropping localization increases. This demonstrates that the optimization weight influences the tendency of the proposed scheme toward optimizing the two objectives.

VI-E Iampact of the Total Power Limit


In this subsection, we will evaluate the impact of power levels on the optimization performance of the proposed scheme. Specifically, under the experimental settings of , , we adjust the total power limit and conduct Monte Carlo experiments to plot the relationship between the total power limit and the optimization performance.
As shown in Fig. 6, with the increase in the total power limit , both the UAC without UARIS and the the case of UARIS with fixed noise exhibit an upward trend in system sum rate, while the RMS miss distance of eavesdropping localization decreases. This is because the increase in total system power improves the SNR at the EN, thereby enhancing its localization accuracy. In contrast, the proposed scheme not only increases the sum rate as the total power increases, but also enhances the RMS miss distance of eavesdropping localization. This is because, as the total power increases, UARIS can allocate more power to emit AN. Meanwhile, through UARIS beamforming, it reduces the interference of the added noise on the RN while enhancing the interference on eavesdropping localization.
Furthermore, as observed in Fig. 6, when the optimization weight is minimal, specifically , the proposed scheme is almost unable to protect the location privacy of the SN. On the other hand, when the optimization weight is huge, such as , the proposed scheme struggles to improve the sum rate. Therefore, The simulation results in Fig. (a) indicate a clear trade-off between communication rate and localization protection. A smaller value of can provide a certain degree of localization protection while maintaining a higher communication rate. In contrast, a larger value of significantly increases the eavesdropper localization error but has a more significant impact on the communication rate. Therefore, the weight should be chosen appropriately according to the specific application scenario to achieve a balance between security and communication efficiency.
VI-F Impact of the Number of UARIS Elements


In this subsection, we will evaluate the impact of the number of UARIS elements on the optimization performance of the proposed scheme. Specifically, under the experimental settings of , and , we adjust the number of UARIS elements and conduct Monte Carlo experiments to plot the relationship between the element number and the optimization performance.
As shown in Fig. 7(a), with the increase in the number of UARIS reflecting elements , the sum-rate is significantly improved both in the case of UARIS with fixed noise and the proposed scheme with different optimization weight values . Furthermore, as observed from Fig. 7(b), the number of UARIS elements has no significant impact on the eavesdropping localization error in the case of UARIS with fixed noise. However, the eavesdropping localization error of the proposed scheme increases as the number of UARIS elements increases. This phenomenon is because more UARIS elements can provide finer beamforming and signal control, thereby improving the system communication performance, while saving more energy for transmitting AN to enhance the protection of location privacy.
VII Conclusion
In this paper, we proposed a novel UARIS architecture integrated with an AN module to address the dual challenge of communication enhancement and location privacy protection in shallow water environments. Our system leverages the intelligent control of reflected signals to significantly improve the communication quality while introducing controllable noise to disrupt the attempts to locate the SN. Through the derivation of the CRLB and the formulation of a multi-objective optimization problem, we designed an efficient algorithm based on FP to optimize transmission beamforming, reflective precoding, and noise factor. Simulation results validated that our proposed scheme not only enhances data transmission rates but also effectively safeguards the location privacy of the SN. Specifically, compared to the traditional UARIS, the proposed scheme improved the eavesdropping localization error by approximately 14.5 times while only reducing the sumrate by 12.7%.
This work conducts an initial exploration into secure and efficient underwater communication systems, particularly in scenarios where privacy concerns are critical. Further research may explore the adaptability of our approach under varying underwater conditions and broader network configurations.
References
- [1] S. A. H. Mohsan, Y. Li, M. Sadiq, J. Liang, and M. A. Khan, “Recent advances, future trends, applications and challenges of internet of underwater things (iout): A comprehensive review,” J. Mar. Sci. Eng., vol. 11, no. 1, p. 124, Dec. 2023.
- [2] A. S. Ghazy, G. Kaddoum, and S. Satinder, “Irs-aided secure reliable underwater acoustic communications,” IEEE Trans. Veh. Technol., Jun. 2024.
- [3] Z. Zhu, Y. Zhou, R. Wang, and F. Tong, “Internet of underwater things infrastructure: A shared underwater acoustic communication layer scheme for real-world underwater acoustic experiments,” IEEE Trans. Aerosp. Electron. Syst., vol. 59, no. 5, pp. 6991–7003, May 2023.
- [4] Y. Cao, W. Shi, L. Sun, and X. Fu, “Channel state information-based ranging for underwater acoustic sensor networks,” IEEE Trans. Wireless Commun., vol. 20, no. 2, pp. 1293–1307, Oct. 2020.
- [5] X. Feng, J. Wang, X. Kuai, M. Zhou, H. Sun, and J. Li, “Message passing-based impulsive noise mitigation and channel estimation for underwater acoustic ofdm communications,” IEEE Trans. Veh. Technol., vol. 71, no. 1, pp. 611–625, Nov. 2021.
- [6] Y. Dong, Z. Chen, Z. Song, Y. Chen, and X. Zhang, “Reconfigurable intelligent surface transmission for data importance classification in underwater acoustic networks with energy holes,” in 2023 IEEE Int. Conf. Signal Process. Commun. Comput., ZHENGZHOU, China, Nov. 2023, pp. 1–4.
- [7] P. Bo, W. Tu, X. Tu, F. Qu, and F.-Y. Wang, “Dual ris-aided parallel intelligence surface for ioamvss: A co-design approach for 3c problems,” IEEE Trans. Intell. Veh., Jan. 2024.
- [8] Y. Han, N. Li, Y. Liu, T. Zhang, and X. Tao, “Artificial noise aided secure noma communications in star-ris networks,” IEEE Wirel. Commun. Lett., vol. 11, no. 6, pp. 1191–1195, Mar. 2022.
- [9] S. Arzykulov, A. Celik, G. Nauryzbayev, and A. M. Eltawil, “Artificial noise and ris-aided physical layer security: Optimal ris partitioning and power control,” IEEE Wirel. Commun. Lett., vol. 12, no. 6, pp. 992–996, Mar. 2023.
- [10] M. A. ElMossallamy, H. Zhang, L. Song, K. G. Seddik, Z. Han, and G. Y. Li, “Reconfigurable intelligent surfaces for wireless communications: Principles, challenges, and opportunities,” IEEE Trans. Cogn. Commun. Netw., vol. 6, no. 3, pp. 990–1002, May 2020.
- [11] C. Huang, A. Zappone, G. C. Alexandropoulos, M. Debbah, and C. Yuen, “Reconfigurable intelligent surfaces for energy efficiency in wireless communication,” IEEE Trans. Wirel. Commun., vol. 18, no. 8, pp. 4157–4170, Jun. 2019.
- [12] K. Liu, Z. Zhang, L. Dai, S. Xu, and F. Yang, “Active reconfigurable intelligent surface: Fully-connected or sub-connected?” IEEE Commun. Lett., vol. 26, no. 1, pp. 167–171, Oct. 2021.
- [13] Z. Zhang, L. Dai, X. Chen, C. Liu, F. Yang, R. Schober, and H. V. Poor, “Active ris vs. passive ris: Which will prevail in 6g?” IEEE Trans. Commun., vol. 71, no. 3, pp. 1707–1725, Dec. 2022.
- [14] H. Wang, Z. Sun, H. Guo, P. Wang, and I. F. Akyildiz, “Designing acoustic reconfigurable intelligent surface for underwater communications,” IEEE Trans. Wireless Commun., vol. 22, no. 12, pp. 8934–8948, Apr. 2023.
- [15] G. Zhang, K. Liu, J. Fu, and S. Sun, “Covariance matrix reconstruction method based on amplitude and phase constraints with application to extend array aperture,” J. Acoust. Soc. Am., vol. 151, no. 5, pp. 3164–3176, May 2022.
- [16] Y. Liu, Y. Wang, C. Chen, and C. Liu, “Unified underwater acoustic localization and sound speed estimation for an isogradient sound speed profile,” IEEE Sens. J., vol. 24, no. 3, pp. 3317–3327, Dec 2023.
- [17] S. Sun, S. Qin, Y. Hao, G. Zhang, and C. Zhao, “Underwater acoustic localization of the black box based on generalized second-order time difference of arrival (gstdoa),” IEEE Trans. Geosci. Remote Sens., vol. 59, no. 9, pp. 7245–7255, Nov. 2020.
- [18] X. Li, Y. Wang, B. Qi, and Y. Hao, “Long baseline acoustic localization based on track-before-detect in complex underwater environments,” IEEE Trans. Geosci. Remote Sens., vol. 61, pp. 1–14, May 2023.
- [19] R. Fan, P. Pan, Z. Jin, Y. Su, and F. Dou, “A secure localization scheme for uwsns based on auv formation cooperative beamforming,” in ICC 2024-IEEE International Conference on Communications, Denver, CO, USA, Aug. 2024, pp. 73–78.
- [20] Z. Liu, B. Zhu, Y. Xie, K. Ma, and X. Guan, “Uav-aided secure communication with imperfect eavesdropper location: Robust design for jamming power and trajectory,” IEEE Trans. Veh. Technol., vol. 73, no. 5, pp. 7276–7286, Dec. 2023.
- [21] K. Hou and S. Zhang, “Optimal beamforming for secure integrated sensing and communication exploiting target location distribution,” IEEE J. Sel. Areas Commun., Aug. 2024.
- [22] B. Lyu, C. Zhou, S. Gong, D. T. Hoang, and Y.-C. Liang, “Robust secure transmission for active ris enabled symbiotic radio multicast communications,” IEEE Trans. Wireless Commun., vol. 22, no. 12, pp. 8766–8780, Apr. 2023.
- [23] F. B. Jensen, W. A. Kuperman, M. B. Porter, H. Schmidt, and A. Tolstoy, Computational ocean acoustics. New York, NY, USA: Springer, 2011.
- [24] A. Weiss, T. Arikan, H. Vishnu, G. B. Deane, A. C. Singer, and G. W. Wornell, “A semi-blind method for localization of underwater acoustic sources,” IEEE Trans. Signal Process., vol. 70, pp. 3090–3106, May 2022.
- [25] A. R. Conn, N. I. Gould, and P. L. Toint, Trust region methods. Philadelphia, Philadelphia, USA: SIAM, 2000.
- [26] S. L. Collier, “Fisher information for a complex gaussian random variable: Beamforming applications for wave propagation in a random medium,” IEEE Trans. Signal Process., vol. 53, no. 11, pp. 4236–4248, Nov. 2005.
- [27] K. Shen and W. Yu, “Fractional programming for communication systems—part i: Power control and beamforming,” IEEE Trans. Signal Process., vol. 66, no. 10, pp. 2616–2630, Mar. 2018.
- [28] S. Boyd, N. Parikh, E. Chu, B. Peleato, J. Eckstein et al., “Distributed optimization and statistical learning via the alternating direction method of multipliers,” Found. Trends Mach. Learn., vol. 3, no. 1, pp. 1–122, Jul. 2011.
- [29] Q. Shi, M. Razaviyayn, Z.-Q. Luo, and C. He, “An iteratively weighted mmse approach to distributed sum-utility maximization for a mimo interfering broadcast channel,” IEEE Trans. Signal Process., vol. 59, no. 9, pp. 4331–4340, Apr. 2011.
- [30] B. Jiang, J. Du, C. Jiang, Z. Han, and M. Debbah, “Underwater searching and multi-round data collection via auv swarms: An energy-efficient aoi-aware mappo approach,” IEEE Internet Things J., vol. 11, no. 7, pp. 12 768–12 782, Nov. 2023.