Joint Data Association, NLOS Mitigation, and Clutter Suppression for Networked Device-Free Sensing in 6G Cellular Network
Abstract
Recently, there is a growing interest in achieving integrated sensing and communication (ISAC) in the sixth-generation (6G) cellular network. Inspired by this trend and the success of cooperative communication in cloud radio access network, this paper considers a networked device-free sensing architecture based on base station (BS) cooperation to transform the cellular network into a huge sensor that can provide ubiquitous and high-performance sensing services. Under this framework, the BSs first transmit the downlink communication signals to the mobile users and then estimate the range information of the targets based on their echoes. Next, a central processor collects the range information from all the BSs via the fronthaul links and localizes each target based on its distances to various BSs. To enable the above strategy in the 6G network, we will perform joint data association, non-line-of-sight (NLOS) mitigation, and clutter suppression, such that the central processor is able to find out the useful range estimations extracted from the line-of-sight (LOS) paths and match them to the right targets for localization. Numerical results show that our interested networked device-free sensing scheme for the 6G network can localize the targets with high accuracy in the challenging multi-path propagation environment.
Index Terms— Integrated sensing and communication (ISAC), networked sensing, 6G, data association, non-line-of-sight (NLOS) mitigation, clutter suppression.
1 Introduction
Thanks to the wide bandwidth at the millimeter wave/Terahertz band and the large antenna array brought by the massive multiple-input multiple-output (MIMO) technique, the cellular network tends to be capable of sensing the environment via the communication signals with ultra-high range and angle resolution, similar to the radar systems. Hence, there is a recent trend in both the academia and the industry to achieve integrated sensing and communication (ISAC) in the sixth-generation (6G) cellular network, where the base stations (BSs) can employ a common wireless signal for conveying information to the mobile users and localizing the targets simultaneously [1, 2, 3, 4, 5, 6, 7, 8, 9]. It is anticipated that the 6G-enabled ISAC technique will play an important role in an enormous number of newly emerging applications from smart transportation systems, smart factories, etc., where both the sensing function and the communication function are of paramount significance.
In the literature of the ISAC technology, the performance trade-off between the capacity in communication and the estimation distortion in sensing have been optimized in various works [10, 11, 12, 13], because the optimal waveforms for the communication signals and the sensing signals are quite different [14]. Apart from the performance optimization, several interesting works have been done to design the practical signal processing techniques for embedding the sensing function into the 6G cellular network. For example, efficient algorithms have been proposed such that a BS can extract the range/angle/Doppler information of the targets based on the orthogonal frequency division multiplexing (OFDM) signals [15, 16], the orthogonal frequency time space (OFTS) signals [17], and the millimeter wave signals [18], that are reflected by these targets. Moreover, [19, 20] have devised powerful estimation schemes such that a mobile user can utilize the cellular signals for realizing simultaneous localization and mapping (SLAM).
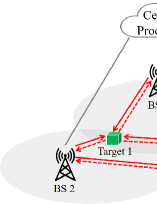
It is worth noting that the above works mainly consider the scenario where localization is performed with one transmitter and one collocated/separate receiver, as in the monostatic/bistatic radar systems. Inspired by the cloud radio access network where the BSs can collaborate with each other to mitigate the inter-cell interference, our recent work [21] proposed a novel networked device-free sensing architecture, as shown in Fig. 1. Specifically, all the BSs in a certain area first emit the OFDM signals in the downlink, then estimate the range information of all the targets based on their echoes, and at last send their range estimations to a central processor via the fronthaul links. Next, the central processor can localize each target based on its distances to various BSs. As pointed out by [21], one main challenge of the above scheme lies in data association, i.e., how to match the range information in each received echo to the right target. Under the line-of-sight (LOS) propagation environment, an efficient data association algorithm was proposed in [21] to enable networked device-free sensing.
In this paper, we generalize our results in [21] to a more practical but also more challenging multi-path propagation environment [22, 23], where besides the LOS paths, non-line-of-sight (NLOS) paths and paths arising from clutters may exist as well among the BSs and the targets, as shown in Fig. 1. Under the two-phase networked device-free sensing protocol, we design an efficient range estimation algorithm based on the OFDM channel estimation technique in Phase I, and perform joint data association, NLOS mitigation, and clutter suppression in Phase II. After the useful range estimations from the LOS paths are identified and each of them is matched to the right target, we can localize these targets accurately. Numerical results verify that our proposed scheme can achieve very high localization accuracy with low complexity.
2 System Model
In this paper, we consider a 6G-enabled ISAC system consisting of BSs, targets to be localized (the value of is unknown and needs to be estimated), and users for communication. Since the communication technology is very mature in the cellular network, we mainly focus on the sensing function in this ISAC system. Let and denote the 2D coordinates of the -th BS and the -th target, respectively, , . Then, the distance between the -th BS and the -th target is given by
| (1) |
Moreover, the sum of the distance between the -th BS and the -th target and that between the -th target and the -th BS is
| (2) |
In the downlink, the BSs will transmit the OFDM signals to the information receivers, while these signals can be reflected by the targets to different BSs as well. Based on the propagation delay from BS to target to BS , we can estimate if and if . Then, each target can be localized based on its estimated ranges to various BSs.
Specifically, let denote one frequency-domain OFDM symbol at the -th BS, , where is the signal at the -th sub-carrier and is the number of sub-carriers. Then, the time-domain modulated signal of BS over one OFDM symbol consisting of samples is given by , , where denotes the common transmit power at the BSs, and denotes the discrete Fourier transform (DFT) matrix with . After inserting the cyclic prefix (CP) consisting of OFDM samples, the time-domain signal transmitted by BS over one OFDM symbol period is given by , where if , denotes the useful signal, and if , denotes the CP.
Define as the -tap multi-path channel from BS to BS , where denotes the complex channel coefficient of the path with a delay of OFDM sample periods. Then, the received signal at the -th BS in the -th OFDM sample period can be expressed as
| (3) |
where denotes the maximum number of resolvable paths and denotes the noise at the -th BS in the -th OFDM sample period. Note that each BS can potentially receive the signals transmitted by BS via three types of paths - Type I path: the LOS path from BS to some target to BS ; Type II path: the NLOS path from BS to BS via some target and some other reflector/scatter; Type III path: the path from BS to some clutter to BS . Thereby, in (3), indicates that there exists a Type I/II/III path from BS to BS , whose propagation delay is of OFDM sample periods; and otherwise. Note that if is contributed by a Type I path from BS to some target to BS , then is equal to OFDM sample periods, where is the speed of the light. Therefore, the range information about the targets can be obtained by estimating the time-domain OFDM channels.
Based on the above observation, in this paper, we adopt a two-phase networked device-free sensing protocol [21]. Specifically, in Phase I, each BS estimates the time-domain OFDM channels, obtains the propagation delay information of each of its received signals based on the estimated channels, and send its delay (thus range) information to a central processor. However, the central processor does not know which ranges are obtained from the Type I paths that are useful for localization. Moreover, if a range is estimated from a Type I path, it is a challenging job to match the range of this path to the right target that reflects the signal on this path, as shown in [21]. In Phase II, the central processor thus needs to perform joint data association, NLOS mitigation, clutter suppression so as to identify the signals from the Type I paths that are useful for estimating ’s and match the range estimations of ’s to the right targets. Then, the number of the targets, i.e., , can be estimated, and each of the targets can be efficiently localized based on its distances to various BSs. In the following two sections, we show the details about Phase I and Phase II under the above protocol.
3 Phase I: Range Estimation
In this section, we show how to perform range estimation in Phase I of our considered two-phase localization protocol. It can be shown that the frequency-domain signal received at BS can be expressed as [24, 21]
| (4) |
where , with the -th element being , , and .
In this paper, we assume that all the BSs know sent by the BSs. For example, in the channel estimation phase for communication, ’s are pilot signals and can be known by all the BSs. In the data transmission phase, the BSs can exchange the messages ’s with each other over the fronthaul links as in cloud radio access network. Hence, in (4) is known by all the BSs. Moreover, due to the limited number of targets, scatters, and clutters, very few elements in ’s are non-zero, i.e., is a sparse channel vector, . This motivates us to utilize the LASSO technique to estimate the time-domain channels by solving the following problem [25]
| (5) |
where is a constant to control the sparsity of each . The above problem is convex and can be solved efficiently using CVX.
Let denote the optimal solution to problem (5), where , . As discussed in Section 2, if for some , then we claim that there exists a path from BS to BS whose propagation delay is of OFDM sample periods. In this case, we estimate the range of this path as follows [21]
| (6) |
where (in Hz) denotes the OFDM sub-carrier spacing such that is the bandwidth. Based on the definitions of Type I, Type II, and Type III paths in Section 2, if , then in (6) satisfies
| (7) |
where denotes the index of the target which reflects the signal from BS to BS with a delay of OFDM sample periods, denotes the error caused by the estimation shown in (6), denotes the bias introduce by the NLOS propagation, and denotes the estimated range of a Type III path with some clutter.
To summarize, after Phase I of our considered two-phase networked device-free sensing protocol, each BS will possess range estimation sets
| (8) |
Then, each BS will transmit the above range sets to the central processor via the fronthaul links. Note that contains the range information for all the paths (Types I, II, and III) from BS to BS . However, for each element in , we do not know whether it is the range of a Type I path, a Type II path, or a Type III path. Moreover, even if is identified to be the range estimation associated with a Type I path from BS to BS , we do not know whether is an estimation of , , or . Therefore, data association, NLOS mitigation, and clutter suppression should be jointly conducted by the central processor to localize the targets in Phase II of our considered protocol.
4 Phase II: Joint Data Association, NLOS Mitigation, and Clutter Suppression
With the knowledge about ’s, , the objectives of the central processor in Phase II are two-fold. First, it needs to estimate the number of targets in the network, i.e., . Second, it needs to estimate the coordinates of the targets, i.e., , . For convenience, given any set , let denote its -th largest element. Then, define as an integer such that is the range estimation of the LOS path from BS to target and then to BS , . Moreover, define as the solution of data association, NLOS mitigation, and clutter suppression for target to all the BSs, . If can be found out, then the number of the targets can be known as well by checking how many LOS estimations are matched to the targets. Further, given , the location of each target can be estimated based on its range information ’s, . In the following, we show how to estimate the number of the targets and their locations via a proper design of .
First, we define the conditions that a feasible solution of should satisfy. Note that given , the number of elements in the range set is denoted by its cardinality . Therefore, the elements in should satisfy
| (9) |
Moreover, if one range estimation in is matched to target , then it cannot be matched to another user , i.e.,
| (10) |
Another condition that should satisfy arises from (2): the length of the LOS path from BS to target to BS , i.e., , is equal to the sum of the distance between BS and target , i.e., , and that between BS and target , i.e., . Note that the imperfect estimations of , , and ’s are (also ), , and . Therefore, we set the following constraints for :
| (11) | |||
| (12) |
where is a given threshold. The last constraint about is on the localization residual associated with this solution about data association, NLOS mitigation, and clutter suppression. Specifically, given , the location of target is estimated by solving the following nonlinear least squared (NLS) problem
where ’s are given in (1). Problem (P1) is a non-convex problem. We can adopt the Gauss-Newton method to solve it [26]. Given for target , define as the value of problem (P1) achieved by the Gauss-Newton method. Therefore, can be interpreted as the residual for localizing target given . If is the right solution, then the localization residual should be small, . We thus set the following residual constraints about ’s:
| (13) |
where is some given threshold.
To summarize, any satisfying constraints (9)-(13) can be a feasible solution for data association, NLOS mitigation, and clutter suppression. Note that if is a feasible solution that satisfies constraints (9)-(13), then is also a new feasible solution, with target not detected. In this paper, we want to maximize the number of targets whose locations can be estimated. Therefore, the solution of data association solution, NLOS mitigation, and clutter suppression can be found by solving the following problem
The above problem can be solved by exhaustive search, i.e., given each and , we check whether conditions (9)-(13) hold. However, such an approach needs to solve the non-convex problem (P1) many times, which is of high complexity. To resolve this issue, we first ignore constraints (10) and (13) in problem (P2), which leads to the following problem
Let and denote the optimal solution to the above problem. Due to the sum distance constraints (11) and (12), the value of is generally small, because the probability that (11) and (12) hold for Type II paths and Type III paths is very small. For convenience, define . Then, we just need to check which subsets in satisfy constraint (13), i.e., the number of times to solve problem (P1) is significantly reduced compared to the exhaustive search approach to problem (P2). Define
| (14) |
In other words, by removing ’s that do not satisfy condition (13) from , we can obtain . Note that each subset contained in satisfies conditions (9), (11)-(13), i.e., it is a feasible solution of data association, NLOS mitigation, and clutter suppression to localize one target. However, for two subsets and , it is possible that for some , i.e., in these two solutions, some estiamted range at BS is matched to both target and target . Therefore, the last step to solve problem (P2) is to select the maximum number of subsets in such that condition (10) can be satisfied. Such a problem can be formulated as
Because the number of subsets in that satisfy so many conditions is small, problem (P4) can be efficiently solved. After this problem is solved, the number of targets is known, and we can solve problem (P1) to localize these targets.
Remark 1.
It is worth noting that a similar two-phase networked device-free sensing strategy was considered in our recent work [21], where Type II and Type III paths are assumed to be absent such that NLOS mitigation and clutter suppression are not needed. Moreover, the sum distance constraints (11) and (12) are not utilized in the data association algorithm design. In this work, we point out that the sum distance constraints (11) and (12) can greatly reduce the number of feasible solutions such that data association, NLOS mitigation, and clutter suppression can be jointly designed with low complexity.
5 Numerical Results
In this section, we provide numerical examples to verify the effectiveness of our considered two-phase networked device-free sensing scheme in the multi-path propagation environment. Specifically, the channel bandwidth is assumed to be MHz. Moreover, we assume that BSs and targets are uniformly distributed in a 120 m 120 m square, and randomly generate realizations of their locations. In each realization, we also randomly generate some Type II paths, i.e., the NLOS paths, and some Type III paths, i.e., the paths arising from clutters. Then, given the Types I, II, and III paths in each realization, we apply the two-phase protocol described in Sections 3 and 4 to estimate the number and the locations of the targets. Under our strategy, if target is not detected, or if target is detected, but the estimated location of it is not lying within a radius of m from its true location, then we claim that a missed detection event occurs for target . On the other hand, if a target that does not exit is detected, we claim that a false alarm event occurs. At the -th iteration, let and denote the numbers of the missed detection events and the false alarm events. Then, over the realizations, the probabilities of missed detection and false alarm are defined as and .
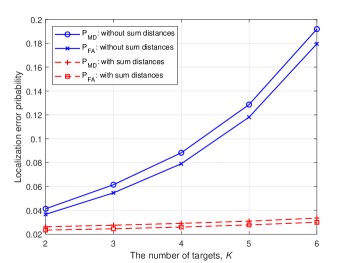
Fig. 2 shows the performance of our proposed two-phase networked device-free sensing scheme, when ranges from to . For the performance benchmark, we select the scheme in [21], where the sum distances, i.e., ’s, are not utilized for data association. It is observed from Fig. 2 that under our proposed scheme, the probabilities of missed detection and false alarm are below when ranges from to . Moreover, it is also observed that the utilization of the sum distances for joint data association, NLOS mitigation, and clutter suppression can significantly reduce the probabilities of missed detection and false alarm compared to the scheme proposed in [21]. At last, because the constraints associated with the sum distances, i.e., (11) and (12), can significantly reduce the number the times to solve NLS problem (P1), which is non-convex, the strategy proposed in this paper is observed to generate the localization solution with a significantly reduced CPU running time compared to the strategy proposed in [21].
6 Conlusion
In this paper, we considered the networked device-free sensing scheme in the 6G network under a multi-path propagation environment. A two-phase localization protocol was studied. In the first phase, range estimation was performance with the OFDM channel estimation techniques. In the second phase, we proposed an efficient algorithm for joint data association, NLOS mitigation, and clutter suppression. Then, the number and the locations of the targets are estimated based on the range estimations from the LOS paths. Numerical results showed that our proposed strategy can enable the BSs to accurately localize the targets with small probabilities of missed detection and false alarm.
References
- [1] F. Liu et al., “Integrated sensing and communications: Towards dual-functional wireless networks for 6G and beyond,” IEEE J. Sel. Areas Commun., vol. 40, no. 6, pp. 1728–1767, June 2022.
- [2] J. A. Zhang et al., “Enabling joint communication and radar sensing in mobile networks-A survey,” IEEE Commun. Surveys Tuts., vol. 24, no. 1, pp. 306–345, 1st Quart. 2021.
- [3] D. K. P. Tan, J. He, Y. Li, A. Bayesteh, Y. Chen, P. Zhu, and W. Tong, “Integrated sensing and communication in 6G: Motivations, use cases, requirements, challenges and future directions,” in Proc. 2021 1st IEEE Int. Online Symp. on Joint Commun. Sens. (JCS), Feb. 2021.
- [4] K. V. Mishra, M. R. Bhavani Shankar, V. Koivunen, B. Ottersten, and S. A. Vorobyov, “Toward millimeter-wave joint radar communications: A signal processing perspective,” IEEE Signal Process. Mag., vol. 36, no. 5, pp. 100–114, Sep. 2019.
- [5] A. Hassanien, M. G. Amin, E. Aboutanios, and B. Himed, “Dual-function radar communication systems: A solution to the spectrum congestion problem,” IEEE Signal Process. Mag., vol. 36, no. 5, pp. 115–126, Sep. 2019.
- [6] B. Paul, A. R. Chiriyath, and D. W. Bliss, “Survey of RF communications and sensing convergence research,” IEEE Access, vol. 5, pp. 252–270, 2016.
- [7] L. Zheng, M. Lops, Y. C. Eldar, and X. Wang, “Radar and communication coexistence: An overview: A review of recent methods,” IEEE Signal Process. Mag., vol. 36, no. 5, pp. 85–99, Sep. 2019.
- [8] F. Liu, C. Masouros, A. Petropulu, H. Griffiths, and L. Hanzo, “Joint radar and communication design: Applications, state-of-the-art, and the road ahead,” IEEE Trans. Commun., vol. 68, no. 6, pp. 3834–3862, June 2020.
- [9] A. Liu et al., “A survey on fundamental limits of integrated sensing and communication,” IEEE Commun. Surveys Tuts., vol. 24, no. 2, pp. 994–1034, 2nd Quart. 2022.
- [10] F. Liu, L. Zhou, C. Masouros, A. Li, W. Luo, and A. Petropulu, “Toward dual functional radar-communication systems: Optimal waveform design,” IEEE Trans. Signal Process., vol. 66, no. 16, pp. 4264–4279, Aug. 2018.
- [11] X. Mu, Y. Liu, L. Guo, J. Lin, and L. Hanzo, “NOMA-aided joint radar and multicast-unicast communication systems,” IEEE J. Sel. Areas Commun., vol. 40, no. 6, pp. 1978–1992, June 2022.
- [12] C. G. Tsinos, A. Arora, S. Chatzinotas, and B. Ottersten, “Joint transmit waveform and receive filter design for dual-function radar-communication systems,” IEEE J. Sel. Topics Signal Process., vol. 15, no. 6, pp. 1378–1392, Nov. 2021.
- [13] X. Liu, T. Huang, N. Shlezinger, Y. Liu, J. Zhou, and Y. C. Eldar, “Joint transmit beamforming for multiuser MIMO communications and MIMO radar,” IEEE Trans. Signal Process., vol. 68, pp. 3929–3944, 2020.
- [14] C. Sturm and W. Wiesbeck, “Waveform design and signal processing aspects for fusion of wireless communications and radar sensing,” Proc. IEEE, vol. 99, no. 7, pp. 1236–1259, Jul. 2011.
- [15] L. Zheng and X. Wang, “Super-resolution delay-Doppler estimation for OFDM passive radar,” IEEE Trans. Signal Process., vol. 65, no. 9, pp. 2197–2210, May 2017.
- [16] L. Liu and S. Zhang, “A two-stage radar sensing approach based on MIMO-OFDM technology,” in Proc. IEEE Global Commun. Conf. (Globecom) Wkshps., 2020.
- [17] L. Gaudio, M. Kobayashi, G. Caire, and G. Colavolpe, “On the effectiveness of OTFS for joint radar parameter estimation and communication,” IEEE Trans. Wireless Commun., vol. 19, no. 9, pp. 5951–5965, Sep. 2020.
- [18] S. H. Dokhanchi, B. S. Mysore, K. V. Mishra, and B. Ottersten, “A mmWave automotive joint radar-communications system,” IEEE Trans. Aerosp. Electron. Syst., vol. 55, no. 3, pp. 1241–1260, June 2019.
- [19] C. B. Barneto et al., “Millimeter-wave mobile sensing and environment mapping: Models, algorithms and validation,” IEEE Trans. Veh. Technol., vol. 71, no. 4, pp. 3900–3916, Apr. 2022.
- [20] J. Yang, C.-K. Wen, and S. Jin, “Hybrid active and passive sensing for SLAM in wireless communication systems,” IEEE J. Sel. Areas Commun., vol. 40, no. 7, pp. 2146–2163, July 2022.
- [21] Q. Shi, L. Liu, S. Zhang, and S. Cui, “Device-free sensing in OFDM cellular network,” IEEE J. Sel. Areas Commun., vol. 40, no. 6, pp. 1838–1853, June 2022.
- [22] S. Aditya, A. F. Molisch, and H. M. Behairy, “A survey on the impact of multipath on wideband time-of-arrival based localization,” IEEE Trans. Aerosp. Electron., , no. 7, pp. 1183–1203, July 2018.
- [23] I. Guvenc and C.-C. Chong, “A survey on TOA based wireless localization and NLOS mitigation techniques,” IEEE Commun. Surveys Tuts., , no. 3, pp. 107–124, 2009.
- [24] T. Hwang, C. Yang, G. Wu, S. Li, and G. Y. Li, “OFDM and its wireless applications: A survey,” IEEE Trans. Veh. Technol., , no. 4, pp. 1673–1694, May 2009.
- [25] M. Yuan and Y. Lin, “Model selection and estimation in regression with grouped variables,” J. R. Stat. Soc. Ser. B, Stat. Methodol., vol. 68, no. 1, pp. 49–67, Feb. 2006.
- [26] D. J. Torrieri, “Statistical theory of passive location systems,” Proc. IEEE, , no. 2, pp. 183–198, Mar. 1984.