Instability of the solitary waves for the Generalized Benjamin-Bona-Mahony Equation
Abstract.
In this work, we consider the generalized Benjamin-Bona-Mahony equation
with . This equation has the traveling wave solutions for any frequency It has been proved by Souganidis and Strauss [6] that, there exists a number , such that solitary waves with is orbitally unstable, while for is orbitally stable. The linear exponential instability in the former case was further proved by Pego and Weinstein [5]. In this paper, we prove the orbital instability in the critical case .
Key words and phrases:
generalized Benjamin-Bona-Mahony equation, instability, critical frequency, traveling wave.2010 Mathematics Subject Classification:
Primary 35B35; Secondary 35L701. Introduction
It is well known that the KdV equation is a classical model used to describe the characteristics of water waves of long wave length in river channels. When studying nonlinear dispersive long wave unidirectional propagation, Benjamin, Bona, and Mahony [1] considered a new model named the Benjamin-Bona-Mahony (BBM) equation, which can describe physical properties of long waves better. The BBM equation reads
In this paper, we consider the following generalized Benjamin-Bona-Mohony (gBBM) equation
| (1.1) |
with For -solution, the momentum and the energy are conserved under the flow, where
| (1.2) | ||||
| (1.3) |
In particular, the equation (1.1) can be expressed in the following Hamiltonian form
| (1.4) |
In [6], Souganidis and Strauss proved that if there exists a unique global solution of (1.1) in .
The equation (1.1) has the solitary waves solution given by for any , where is the ground state solution of the following elliptic equation
| (1.5) |
The ground state solution is a smooth, even, and positive function, which decays exponentially as , in the sense that for some Then a natural problem is the stability theory of the solitary waves solution , which is defined as follows. For we denote the set as:
| (1.6) |
Then we define the orbital stability/instability of the solitary waves as
Definition 1.1.
Regarding the stability theory of these solitary waves, Souganidis and Strauss [6] proved that when , the solitary waves solution is orbitally stable for all , while when , the solitary waves solution is orbitally unstable in for and orbitally stable in for . Here
Denote , the critical parameter is determined by
Since the operator is not onto, the framework of Grillakis, Shatah, and Strauss [2, 3] cannot be directly applied to study the stability of the solitary waves . Therefore, the work [6] is not a direct application of the theories established in [2, 3]. For further discussion on these cases, readers are referred to the more recent paper [4] by Lin and Zeng.
In [5], Pego and Weinstein established criteria for the linear exponential instability of solitary waves solution of the gBBM equation. They further proved the linear exponential instability of for each when .
So far, the stability of the solitary waves has been nearly established, except for the critical case , which corresponds to the degenerate case where . In this paper, our aim is to fully establish the stability of the solitary waves by studying the degenerate case of .
Before presenting our theorem, let us clarify some definitions that will be used. We define the functional as
| (1.7) |
Then the equation (1.5) is equivalent to . For convenience, we denote that
and
| (1.8) |
Then by (1.5), we find that satisfies the following equation:
| (1.9) |
As mentioned earlier, our objective is to demonstrate the instability of the solitary waves in the critical frequency case: . Our argument relies on the assumption of the negativity of a specific direction of the Hessian operator , which is confirmed numerically. More precisely, let
| (1.10) | ||||
| (1.11) |
where
We assume that
| (1.12) |
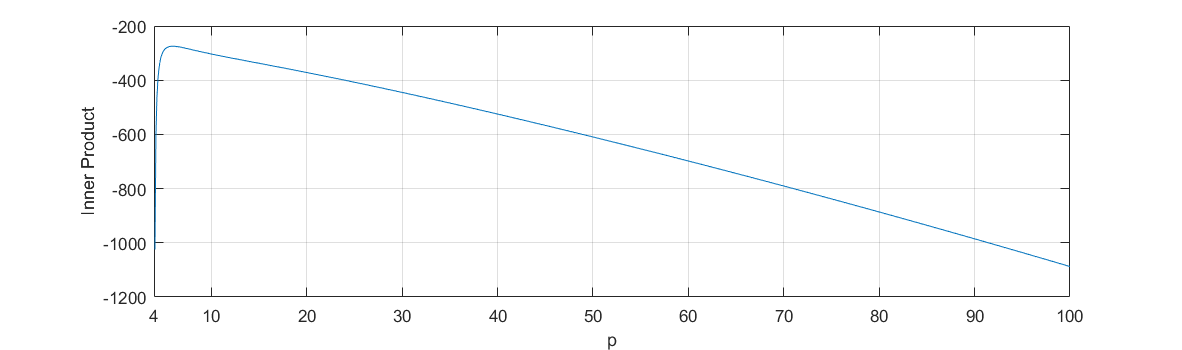
which is checked numerically 111According to Appendix A.4, we use Matlab to compute It suffices in practice to run the computations until to check as the inner product is decreasing fastly as a power function when is bigger than We refer to “Appendix A.4” for more details. in Appendix A.4.
The main result in the present paper is the following.
Theorem 1.2.
Remark 1.3.
(1) In the previous works [5] and [6], the stability and instability results of solitary waves solution for the non-degenerate case in the gBBM equation have already been established. Under (1.12), Theorem 1.2 closes the only remaining gap for the degenerate case and thereby completes the entire stability theory of solitary waves solution for the gBBM equation. We also give an element numerical computation to check (1.12).
(2) The instability of the solitary waves with has been demonstrated using the Lyapunov stability argument based on the monotonicity of the Lyapunov functional in the non-degenerate cases However, this argument does not apply to the degenerate cases, as the Lyapunov functional loses monotonicity when Therefore, we need to construct a new monotonic functional. The outline of the proof will be provided in the following subsection.
1.1. Sketch of the proof
The main approach is to construct a monotonic quantity based on virial quantities and the modulation argument, drawing inspiration from [9], which established the instability of standing wave solutions of the Klein-Gordon equation in the degenerate case. The methodology involves analyzing the orthogonality conditions and the dynamics of the modulated parameters. However, due to the intricate structure of the gBBM equation, constructing the monotonic functional in this paper is much more complex than the Klein-Gordon equation case. In particular, the non-onto property of the skew symmetry operator poses significant obstacles. The key ingredients of the proof can be summarized as follows.
Step1: Modulation. First of all, we assume the solitary wave is stable. The modulation argument allows us to find two parameters, and and a perturbation function , such that the solution can be expressed as
| (1.13) |
where is a scaling parameter suitably defined, and is a spatial translation parameter. We also need to find two different orthogonality conditions, namely:
| (1.14) |
To find suitable and it is natural to consider the spectrum of the Hessian of the action . The study of [7] indicates that and has a unique negative eigenvalue. The properties of spectrum of helpfully identify the origin of and specifically:
| (1.15) |
It is worth noting that is not unique and it is not necessary to choose the negative eigenfunction. Indeed, the choice of is crucial as its concrete expression has a significant impact on the construction of monotonicity, which will be addressed in Step 6 below.
Step2: Coercivity. Having determined the properties of and (i.e.,(1.15)), we shall prove the the coercivity of the Hessian as shown in Proposition A.3 for a general criterion by means of spectral decomposition argument, which can be expressed as follows:
In addition, in the degenerate case , we have
| (1.16) |
This flatness equality (1.16), combined with the coercivity of , implies an important estimate:
| (1.17) |
This means that the perturbation of the solution can be controlled by the scaling increment .
We emphasize that the Step 1 and Step 2 here are similar to the paper in [9], however, the following steps are of much problem-dependence and much more complicated for BBM mainly due to its poor Hamiltonian structure.
Step 3: Dynamic of the modulation parameters. Directly following the Implicit Function Theorem, the (translation) modulation parameter has a trivial bound given by
| (1.18) |
In simpler terms, is actually the first-order of However, the rough estimate is not enough to support the later analysis. To obtain a more accurate estimate, we apply (1.13) to (1.4), which yields
| (1.19) |
This gives us the key expression of the dynamic of :
| (1.20) |
for any satisfying
| (1.21) |
Obviously, the function satisfying condition (1.21) is not unique. The estimate (1.20) is therefore relatively flexible, depending on the choice of . Indeed, the latter almost determines the expression of the first-order of which appears in defined later. This constitutes the first key ingredient in our proof.
Step 4: Design of the virial identity. We are now in the position to consider the construction of virial identity Our goal is to show that it exhibits monotonic behavior, i.e., or The virial identity typically arises from conservation laws such as (1.2)-(1.3) and the dynamic of the modulated function as in (1.19). The ideal form of is as follows:
| (1.22) |
where the high-order term is in fact that has been estimated in Step 2. If is a positive quantity, and is also a positive quantity satisfying which requires that
| (1.23) |
then the monotonicity of virial identity is guaranteed. This constitutes the second key ingredient in our proof.
Step 5: Construction of the monotonicity. Unlike the Lyapunov functional, the main monotonic functional here comes from the localized virial identity. Specifically, we first define
where is a suitable smooth cutoff function. By the expansion (1.13), we observe that has the following structure:
Since the precise estimate of is already known in Step 3, we obtain the structure of as follows:
Move the term to the left-hand side, and we further obtain that
| (1.24) |
This inspires us to make a bold assumption: After suitably choosing , if
| (1.25) |
then will become the ideal form (1.22). In order to match the form in (1.15), we need the existence and the explicit expressions of the pre-images of and . As a matter of fact, we need to find and such that
It is not an easy task, but we accomplished it. In fact, we observe that
where satisfying (1.9). This constitutes the third key ingredient in our proof.
Step 6: Verification of the negative direction. Inspired by (1.25), we denote
It is time to verify the negativity of on . More precisely, the problem finally reduces to the following claim:
Claim 1.4.
There exists a function verifying (1.21), such that
| (1.26) |
This claim is established by choosing as presented in the assumption (1.12). Due to the complexity of the expression , we decide to check it by numerical experiments. Suppose the claim is true, then we choose and thus obtain the form of in (1.22) as we expected. This constitutes the fourth key ingredient in our proof.
Step 7: Contradiction. Based on the works before, the structure of monotonicity becomes clear. Indeed,
Then using (1.17), we can infer that
The positivity of can be verified by suitably choosing initial data Thus we establish the monotonicity of The contradiction between uniformly boundedness and monotonicity of proves the instability in the end.
1.2. Organization of the paper
The remainder of the paper is organized as follows. In Section 2, we provide some preliminaries. In Section 3, we establish the coercivity of the Hessian and control the modulation parameters. In Section 4, we demonstrate the localized virial identities and define the monotonicity functional. In Section 5, we establish the monotonicity of the functional obtained in Section 4 and prove the main theorem. Finally, in Appendix A, we present a general coercivity property of the Hessian of the action and the numerical result of the negative eigenfunction of .
2. Notations
2.1. Notations
For we define
and regard as a real Hilbert Space. For a function , its -norm and its -norm
Further, we write or to indicate for some constant We use the notation to denote We also use to denote any quantity such that and use to denote any quantity such that if Throughout the whole paper, the letter will denote various positive constants which are of no importance in our analysis.
2.2. Some basic definitions and properties
In the rest of this paper, we consider the case of and Recall the expression of conserved equality and the functional , we have
| (2.1) |
Taking derivative, then we have
| (2.2) | ||||
| (2.3) | ||||
Note that Moreover, for the real-valued function a direct computation shows
| (2.4) |
Taking the derivative of with respect to gives
| (2.5) |
For any function we have
| (2.6) |
Moreover, taking the derivative of with respect to gives
| (2.7) |
Next, we give some basic properties on the momentum, energy and the functional .
Lemma 2.1.
Let then the following equality holds:
Proof.
Note that
Taking inner product of (1.5) and respectively, by integration-by-parts, we can get
This gives that
| (2.8) |
This further yields that
By scaling, we find
| (2.9) |
where is the solution of
Hence,
| (2.10) |
By a straightforward computation, we have
| (2.11) |
Finally, we substitute into the equality above, and thus we complete the proof. ∎
Then a consequence of Lemma 2.1 is
Corollary 2.2.
Let , then
Proof.
The next lemma gives pairs of pre-image and image of
Lemma 2.3.
Proof.
3. Modulation and dynamic of the parameter
Under the assumption (1.12), in order to obtain a contradiction, we assume that the solitary waves solution is stable, that is: for any , there exists such that when
we have
| (3.1) |
Proposition 3.1.
Let Suppose that for any . Then there exist functions
such that for
| (3.2) |
the following orthogonality conditions hold:
| (3.3) |
where
| (3.4) |
and lies in the positive direction of that is,
| (3.5) |
Furthermore, the following estimate holds:
| (3.6) |
Proof.
From Proposition A.5, we first verify satisfying (A.27). By (2.7) and Lemma 2.1, we have
Then by Corollary A.4, we obtain
Therefore, there exists such that for there exists unique -functions
such that
By (1.12), we have that satisfying (A.5). From Proposition A.3, we obtain (3.5). Furthermore,
This implies that
This finishes the proof of the proposition. ∎
Some consequences of Proposition 3.1 are the follows. The first one is the rough estimate on and
Corollary 3.2.
Proof.
Recall the definition in (3.2), that is
| (3.7) |
Taking the derivative of (3.7) with respect to we have
| (3.8) |
Inserting (3.8) into equation (1.4), we get
| (3.9) |
where we note that Adding to both sides of (3.9), we have
We note that then the above equality can be rewritten as follows:
| (3.10) |
Using Taylor’s type expansion, we have
| (3.11) |
where we used Inserting (3) into (3), we have
| (3.12) |
where verifies
Taking inner product by (3.12) and respectively, by integration-by-parts, we have
| (3.13) | ||||
| (3.14) |
By the even property of it is known that is an even function. Moreover, we note that is also an even function since has the same parity as . Using orthogonality conditions in (3.3), we simplify (3.13) and (3.14) as
| (3.15) | ||||
| (3.16) |
where is a constant denoted by which only depends on We denote
Combining (3.15) and (3.16), by a direct computation, we have
| (3.17) |
Thus we obtain the desired results. ∎
The second is a precise estimate on the spatial transform parameter .
Corollary 3.3.
Proof.
Taking inner product by (3.12) and by integration-by-parts, we have
| (3.19) |
It’s worth noting that since is exponential decaying. Now we consider terms in (3) one by one. First, from the rough estimate in Corollary 3.2, we have
| (3.20) |
The term vanishes since is an even function. Then, direct calculation gives that
| (3.21) |
Using the property of in (2.6), we have
| (3.22) |
4. The localized virial identity
The following lemma is the localized virial identity. Let be the parameters and function obtained in Corollary 3.2, are the same as Corollary 3.3. Denote
| (4.1) |
From the equation (1.4), we obtain that Inserting the expression of in (3.7) into (4.1), we have
Noting that satisfies
| (4.2) |
and
| (4.3) |
From (4.2) and (4.3), we obtain that
| (4.4) |
where has the same property as in (3.12) which verifies that
We also denote that
where
Lemma 4.1.
Let be the solution of (1.1), then
Proof.
First, a direct computation gives that
Multiplying (1.4) by gives:
Further, noting that
we get that
where we used in the last step. Then by integration-by-parts, we obtain that
Second, a direct computation shows that
here we used the estimate of in Corollary 3.2 in the last step. This completes the proof. ∎
5. The monotonic functional
This section is devoted to prove our main theorem.
5.1. Virial identities
Let be a smooth cutoff function, where
| (5.1) |
for any and is a large constant decided later. Moreover, we denote
Then we have the following lemma.
Lemma 5.1.
Let be the parameters and function obtained in Corollary 3.2. Then
| (5.2a) | ||||
| (5.2b) | ||||
Proof.
From (4.1) and the conversation law of energy, we change the form of as
where
| (5.3) |
Then we need to consider the terms and
Estimate on
Now we consider terms and respectively. We recall the expression of in (4.4), we have
Now we estimate the terms above one by one.
(i) The term .
| (5.4) |
(ii) The term . We recall (3.15) and insert the rough estimates of and obtained in Corollary 3.2 into (3.15), we have that
We note that then we have
| (5.5) |
(iii) The term . Using the expression of in (4.3), we have
Thus by Young’s inequality, we have
| (5.6) |
where we used in the last step.
(iv) The term . By Hölder’s inequality and (5.1), we obtain that
| (5.7) |
Collecting all the estimates above, we obtain that
| (5.8) |
Arguing similarly, taking the derivative of (4.4) with respect to , we have that
| (5.9) |
Repeating the process above, we obtain that
| (5.10) |
From (5.8) and (5.10), we have
| (5.11) |
Estimate on .
Using the definition of the cutoff function in (5.1), we have
By Hölder’s inequality, Corollary 3.2, (1.5), (4.3), (5.8) and (5.10), we have
Further, using the property of exponential decay of we have
Then Young’s inequality gives that
| (5.12) | |||
| (5.13) | |||
| (5.14) |
Therefore, we combine (5.12)–(5.14) to obtain
| (5.15) |
5.2. Structure of
Denote
| (5.16) | ||||
| (5.17) | ||||
| (5.18) |
where
Lemma 5.2.
It holds that
Lemma 5.3.
We estimate as follows:
| (5.19) |
Proof.
Recall the definition of in (5.2):
First, from Lemma 2.3, we have already known that and both have pre-image with respect to then we have
| (5.20) |
By (3.7) and Taylor’s type expansion, we have
From Lemma 2.1 and (2.8), we have
Combining the rough estimate of in Corollary 3.2 and the precise estimate of in (3.18), we have
| (5.21) |
Inserting (5.20) and (5.2) into the expression of , we have
We note that . By the second orthogonality condition (3.3) in Proposition 3.1, we complete the proof. ∎
5.2.1. Lower bound of
Lemma 5.4.
Let for some small positive constant . Then there exist a constant , such that
5.2.2. Lower bound of
Lemma 5.5.
There exists a positive constant such that
Proof.
Recall the definition of from (5.17):
We claim that
| (5.23) |
We prove the claim by the following three steps.
Step 1.
Step 2.
Step 3.
From the expression of in (5.24), we have
From (5.26), we have
So we get
noting that when then This proves the claim (5.23).
Using (5.23) and Taylor’s type expansion, we get
where Thus we obtain the conclusion of this lemma. ∎
5.2.3. Upper bound of
Lemma 5.6.
Let be defined in (3.2), then for any
Proof.
First, since in (3.7), by Taylor’s type extension and , we have
Using and Taylor’s type extension, we have
Then by Proposition 3.1, we get
Second, note that
and the expression of in (2.1) gives that
Using the Taylor’s type expansion, by (2.3) and (2.8), we have
So we obtain
Moreover, by Corollary 2.2, we have
Finally, we get the desired result
This completes the proof. ∎
5.3. Proof of Theorem 1.2
As in the discussion above, we assume that and thus We note that from the definition of and (2.8) we have the uniform boundedness of
| (5.28) |
Now we estimate From (5.27) and Lemma 5.6, we have
By (3.6), choosing satisfying and small enough, we obtain that for any
This implies when which is contradicted with (5.28). Hence we prove the instability of solitary wave solution and thus give the proof of Theorem 1.2.
Appendix A
A.1. Spectrum of
First, we study the kernel of in the following lemma. The proof is standard, and it is a consequence of the result from [7].
Lemma A.1.
The kernel of satisfies that
Proof.
First, we need to show the relationship For any using (1.5), we have
| (A.1) |
Then (A.1) implies that is in the kernel of and we have the conclusion
Second, we prove the reverse relationship By the expression of in (2.18), we have
for any that is
| (A.2) |
By the work of Weinstein [7], the only solution to (A.2) are
Note that
This implies that and we have
Finally, combining the two relationship gives us
This gives the proof of the lemma. ∎
The second lemma is the uniqueness of the negative eigenvalue of
Lemma A.2.
exists only one negative eigenvalue.
Proof.
It is known that the operator has only one negative eigenvalue(see [7]), and we denote it by Then there exists a unique associated eigenfunction such that
| (A.3) |
Using the expression of in (2.18), we have
Note that then we have
This implies that has at least one negative eigenvalue Assume its associated eigenfunction that is,
Using the expression of in (2.18) again, the last equality yields
Then we have Hence, by (A.3), is exactly the pair satisfying
| (A.4) |
This implies that has exactly one simple negative eigenvalue. This completes the proof of Lemma (A.2). ∎
A.2. Coercivity
In this subsection, we give a general coercivity property on the Hessian of the action
Proposition A.3.
Let be any functions satisfying that
| (A.5) |
Suppose that satisfies
| (A.6) |
Then
Proof.
From the expression of in (2.18), we can write as
where
and
Hence is a compact perturbation of the self-adjoint operator
Step 1. Analyze the spectrum of
We first compute the essential spectrum of
Note that for any
| (A.7) |
Since we can get and thus
This means that there exists
such that the essential spectrum of is
By Weyl Theorem,
and
share the same essential spectrum.
So we obtain the essential spectrum of
Recall that we have obtained the only one negative eigenvalue of in Lemma A.2 and the kernel of in Lemma A.1.
So the discrete spectrum of is and the essential spectrum is
Step 2. Positivity.
By Lemma A.2, we have the unique negative eigenvalue and the eigenfunction of
For convenience, we normalize the eigenfunction such that
Hence, for
by the spectral decomposition theorem we can write the decomposition of along the spectrum of
where and lies in the positive eigenspace of that is, satisfies
and there exists an absolute constant such that
| (A.8) |
Since satisfies the orthogonality condition in (A.6) and we have and thus
| (A.9) |
Substituting (A.9) into we get
Due to the orthogonality property of we have
| (A.10) |
To by spectral decomposition theorem again, we may write
where and lies in the positive eigenspace of We note that
| (A.11) |
Therefore, a similar computation as above shows that
For convenience, let Then by (A.5), we know that Moreover, we have
| (A.12) |
By (A.9) and (A.11), using the orthogonality assumption in (A.6) we have
So we get the equality
By the Cauchy-Schwartz inequality, we have
This gives
| (A.13) |
The last inequality combining with (A.12) implies that
that is
| (A.14) |
Inserting (A.14) into (A.10), we obtain
Recalling that satisfies (A.8), we have
| (A.15) |
From the expression of in (A.9) and the inequality (A.10), we have
Therefore, this gives
| (A.16) |
To obtain the final conclusion, we still need to estimate
Using the expression of in (2.4), we have
Thus by (A.16), we get
| (A.17) |
Therefore, together (A.16) and (A.2), we obtain
Thus we obtain the desired result. ∎
Corollary A.4.
Assume
| (A.18) |
then for any s.t.
| (A.19) |
we have
Proof.
Using the similar spectral decomposition argument as in Proposition A.3, we apply the notation from Proposition A.3, that is: the unique negative eigenvalue and its corresponding normalized eigenfunction of So for we can write the decomposition of as
| (A.20) |
where and lies in the positive eigenspace of that is satisfies
| (A.21) |
and there exists an absolute constant such that
| (A.22) |
Since satisfies there exists an absolute constant such that
| (A.23) |
By Lemma A.1, and combining (A.20) and (A.21), we have
So we obtain that
| (A.24) |
Similarly, we write as where and lies in the positive eigenspace of We note that
| (A.25) |
From condition (A.19), we have
So we get
where we used Cauchy-Schwartz inequality in the last step. Combining (A.2), the last inequality implies that
| (A.26) |
Inserting (A.2) into (A.25), we have
Thus we complete the proof.
∎
A.3. Modulation
The modulation theory shows that by choosing suitable parameters, some orthogonality conditions as in (A.3) can be verified.
Proposition A.5.
Assume that be the function satisfying
| (A.27) |
Moreover, suppose that there exists such that for any , and any then the following properties are verified. There exist -functions
such that if we define by
| (A.28) |
then satisfies the following orthogonality conditions:
| (A.29) |
Proof.
We use the Implicit Function Theorem to prove this proposition. Here we only give the important steps of the proof and refer the readers to [7, 8] for the similar argument. Define
Let be the parameter decided later, and define the functional pair as
We claim that there exists such that for any there exists a unique map: such that Indeed, we have
Second, we prove that
Indeed, a direct computation gives that
When we observe that and the second term vanishes. So we get
as is an even function. A similar computation shows that
By (A.27), we find that
Therefore, the Implicit Function Theorem implies that there exists such that for there exist unique -functions
such that
| (A.30) |
This proves the Proposition. ∎
A.4. The negativity of (numerically checked).
The expression of From Lemma 2.3, we have already known that
| (A.31) | |||
| (A.32) |
By the expression of in (2.4), we have
From equation (1.5), we have
| (A.33) |
Thus we obtain
| (A.34) |
Using the expression of in (2.4) again, we obtain
| (A.35) |
Inserting (A.33) into (A.4), and by (1.5), we have
| (A.36) |
Combining (A.31), (A.32), (A.34) and (A.36), we finally obtain the concrete expression of that is
| (A.37) |
The numerical result of According to [5], the solution of elliptic equation (1.5) is explicitly given by
| (A.38) |
By (1.8) and the expression of in (1.10), we have
Using (A.38), and by direct computation we obtain that
| (A.39) | ||||
| (A.40) | ||||
| (A.41) |
We check in the following case:
The limit of integration is
(1) for
(2) for
(3) for
(4) for
(5) for
(6) for
(7) for
(8) for
(9) for
(10) for
The graph of as a function of p is shown as below:
Acknowledgment
R. Jia and Y. Wu are partially supported by NSFC 12171356. The authors would like to thank Professor Zeng Chongchun for many valuable discussions and suggestions.
Data Availability
There is no additional data associated to this article.
Declarations
Conflict of interest
On behalf of all authors, the corresponding author states that there is no conflict of interest. Data sharing is not applicable to this article as no datasets were generated or analysed during the current study.
References
- [1] T. B. Benjamin, J. L. Bona, and J. J. Mahony, Model equations for long waves in nonlinear dispersive equations, Philos. Trans. Roy. Soc. London Ser. A, 272 (1972), 47-78.
- [2] M. Grillakis, J. Shatah, and W. Strauss, Stability theory of solitary waves in the presence of symmetry, I, J. Funct. Anal., 74 (1987), pp. 160–197.
- [3] M. Grillakis, J. Shatah, and W. Strauss, Stability theory of solitary waves in the presence of symmetry, II, J. Funct. Anal., 94 (1990), pp. 308–348.
- [4] Z. Lin; C. Zeng, Instability, index theorem, and exponential trichotomy for linear Hamiltonian PDEs. Mem. Amer. Math. Soc., 275 (2022), no. 1347, v+136 pp.
- [5] R. Pego and M. Weinstein, Eigenvalues, and instabilities of solitary waves. Philos. Trans. Roy. Soc. London Ser. A, 340 (1992), 47–94.
- [6] P. E. Souganidis, and W. A. Strauss, Instability of a class of dispersive solitary waves, Proc. R. Soc. Edinb, 114 (1990), 195-212.
- [7] M. Weinstein, Modulational stability of ground states of nonlinear Schrödinger equations, SIAM J. Math. Anal., 16 (1985), 472-491.
- [8] M. Weinstein, Lyapunov stability of ground states of nonlinear Schrödinger equations, Comm. Pure Appl. Math, 39 (1986), 51-67.
- [9] Y. Wu, Instability of the standing waves for the nonlinear Klein-Gordon equations in one dimension, Trans. Amer. Math.Soc.,376 (2023), no. 6, 4085–4103.