Injecting Reliable Radio Frequency Fingerprints Using Metasurface for The Internet of Things
Abstract
In Internet of Things, where billions of devices with limited resources are communicating with each other, security has become a major stumbling block affecting the progress of this technology. Existing authentication schemes based on digital signatures have overhead costs associated with them in terms of computation time, battery power, bandwidth, memory, and related hardware costs. Radio frequency fingerprint (RFF), utilizing the unique device-based information, can be a promising solution for IoT. However, traditional RFFs have become obsolete because of low reliability and reduced user capability. Our proposed solution, Metasurface RF-Fingerprinting Injection (MeRFFI), is to inject a carefully-designed radio frequency fingerprint into the wireless physical layer that can increase the security of a stationary IoT device with minimal overhead. The injection of fingerprint is implemented using a low cost metasurface developed and fabricated in our lab, which is designed to make small but detectable perturbations in the specific frequency band in which the IoT devices are communicating. We have conducted comprehensive system evaluations including distance, orientation, multiple channels where the feasibility, effectiveness, and reliability of these fingerprints are validated. The proposed MeRFFI system can be easily integrated into the existing authentication schemes. The security vulnerabilities are analyzed for some of the most threatening wireless physical layer-based attacks.
Index Terms:
Metasurfaces, Intelligent Reflective Surfaces, Reconfigurable Intelligent Surfaces, Reconfigurable Reflect Array, Specific Emitter Identification, Smart Reflect Arrays, Physical Layer Security, RF Fingerprinting, IOT Security.I Introduction
Internet of things (IoT) is revolutionizing our daily life and gradually overwhelming over existing IT devices, such as PCs and mobiles, by their ubiquitous connectivity and diverse applications. It is forecasted that by 2022 around 18 billion connected devices will be related to IoT [1]. The global market for IoT technology has reached $190 billion in 2018, and it is projected to reach $1012 billion by 2026 according to a data and analytics company [2]. However, most IoT devices are operating without a secure authentication procedure which makes them vulnerable to cyber attacks.

The current state-of-the-art IoT connectivity technologies employ cryptographic protocols [3] which are vulnerable to attacks [4]. Increasing computational complexity of the algorithms is an obvious but costly solution. A promising cost-effective solution to tackle the aforementioned challenge for IoT came in the form of radio frequency fingerprinting (RFF) [5], which can be observed from the electromagnetic waves radiated by the transmitter. By verifying the RF-fingerprint, secure authentication can be established between IoT nodes. RFF is a type of device hardware-based fingerprinting, which is built on the fact that the fabrication process of the transmitter, especially, analog components, introduces certain distinctive imperfections that can act as the fingerprint of the device. To be qualified as a fingerprint, the RFF has to be unique, reliable, and unforgeable to be adopted into practical IoT systems. However, traditional RFF methods are becoming less prominent due to advanced manufacturing techniques, which results in certain limitations: a) lack of configurability– users have no control over the generation of fingerprint; b) limited distinguishability– extracted RFFs from different devices may exhibit similar properties with each other because of the reduced user capacity; c) low reliability– the RFFS are minuscule and when transmitted over the channel gets diminished, distorted and corrupted by noise d) complicated data processing– more computation is needed to mine inconspicuous device features caused by the reduced feature space.
To address the issues of low reliability, reduced user capacity, diminishing distinguishability, and complications in data processing of RFFs, we propose a novel injectable RFF scheme through electromagnetic metasurfaces (also termed Reconfigurable Intelligent Surfaces [6] or Intelligent Reflective Surfaces [7]). Specifically, we designed and developed a system called metasurface for radiofrequency fingerprint injection (MeRFFI). MeRFFI is a metasurface [8] designed to make small but detectable perturbations in the specific frequency band in which the IoT devices are communicating. The perturbations created by MeRFFI are multiple well-intended constructive interferences on the transmitter’s emission, which do not impact the wireless communication. MeRFFI is intended to be used for stationary IoT devices that use wideband RF channels for communication, making it useful for systems that require high security like printers, health gadgets, wireless cameras, backhaul of sensor networks, and industrial monitoring systems. MeRFFI is low cost (less than 20 cents) and consumes very little power (less than 50 millijoules per code), and its form factor is small enough to be conveniently attached to the IoT transmitters (e.g., as part of transmitter casing, cellphone cover or a health watch’s backplane). In this paper, we introduce MeRFFI specific to static application scenarios and discuss the possibility of further broadening its scope to everyday mobile applications like health watches and cell phones.
We present our system with two modes of operation, the passive (fixed pattern) mode provides easy and low-cost access to IoT devices that requires no further processing, while the active (adjustable pattern) mode can provide a time-varying signature by programmatically changing the electromagnetic properties of the metasurface with a microcontroller unit. Our key contributions are:
-
•
To the best of our knowledge, we are the first to propose and design a metasurface-based RFF injection system, which overcomes the problems of low reliability and reduced user capacity from traditional RFFs. We have modeled the metasurface enhanced signature injection scheme and further provided potential attack scenarios and security analysis.
-
•
We developed and implemented a low-cost MeRFFI prototype. With comprehensive evaluations, including distance, orientation, and multiple channels on the system, we demonstrate the feasibility of MeRFFI as a realistic security signature for IoT authentication.
-
•
The developed MeRFFI has an intrinsic flexible property that can be utilized in different applications based on different levels of security, cost restraints, and processing capabilities. We demonstrated how MeRFFI could be used in an IoT scenario using three easily integrable authentication protocols.
II Related Work
In this section, two predominantly used schemes for IoT authentication are discussed Radio Frequency fingerprinting and hardware signature embedding.
II-A RF-Fingerprinting (RFF):
The cost constraints on the manufacturing process of IoT transmitters have made the intrinsic variations caused by the components in it, unavoidable. In a typical Direct Conversion transmitter [9], which is commonly used in IoT transmitters, RFFs are produced by most of its functional components.
The digital to analog converters are often affected by integral non-linearity (INL). These nonlinear effects have been used as fingerprints [10]. Several variations can arise from the use of different signal processing techniques [11] in the transmitting hardware. These cannot be eliminated from the manufacturing process as they depend upon variable tolerances of the different device components. In the mixer part, the in-phase and the quadrature components are required to be at a specific phase angle apart (e.g., 90°). This imbalance between the in-phase and quadrature components have also been leveraged for RF fingerprinting [12]. The nonlinear characteristics of a PA often vary widely according to its average output [13], as the heat dissipation would alter the chip temperature and hence there would be device dependent signatures [14] present in the electromagnetic waves emitted by the transmitter. The RF front end that is the drive circuit along with the antenna and its effects on polarization and voltage has also been studied for RFFs [15]. Clock Jitter is another RFF [16], which remains fairly consistent over time, but the clock skews vary significantly across devices. Apart from these, observations have been made on turn-on and turn-off transient of the communication device. The energy envelope of the instantaneous transient signal has been researched as RFFs [16].
These RFFs have known vulnerabilities to two main types of replay attacks [17], the signal replay attack (receive and replay without modification), and feature replay attack (receive, analyze, generate and transmit). When the RF-fingerprinting features, modulation based RFF, and transient-based RFF were tested with feature replay attacks, it was found that modulation based RFFs can be feature replayed with almost 100 percent accuracy. This happens because of the simplicity of the modulation based features. Transient-based features have proven to be more effective. However, commercial wireless devices cannot capture the transient-based features as they do not have the required dynamic operating frequency range (They are generally processed from high frequencies).
II-B Hardware Signature Embedding:
This method uses intrinsic defect based properties to generate true random and unique numbers and apply these as a replacement for cryptographic codes. The most popular solution that came using this principle, applies physically unclonable functions (PUFs). PUF maps input challenges to output responses based on a function determined by inherent variations of that circuit. These responses are used in place of digital signature and are included in the communication packet transmitted by IoT devices for securing the communication between them [18]. The PUF based solutions are not really physical layer fingerprinting as they are digitally transmitting the signature with the sent packet and they are prone to machine learning based attacks [19].
III Problem Definition and Solution
RF-fingerprinting being an up-and-coming solution for the Internet of Things has certain well-established drawbacks :
III-A Reliability vs. Vulnerability
RFFs are either too feeble to survive the wireless channel, or the variations are too simple or obvious and can be easily attacked. There exists a trade-off between reliability and security [20], mainly due to the wireless channel. A high spoofing resistance means that the system has a low noise resistance. Conversely, if an RFF is designed to detect even the most feeble variations, its reliability takes a hit, as the channel variations make the legitimate devices unrecognizable.
III-B Weak Distiguishability and Reduced User Capacity
Typical experimental validations of RF-fingerprinting use either high-end measurement device (like software-defined radio [5]) or network analyzer) or use a line-of-sight (LOS) channel with high SNR [11]. When low-cost off-shelf devices are used (transmitter and receiver) in a noisy multipath channel, the distinguishability of the authenticating devices is greatly reduced [21]. This leads to the reduction of the user capacity of the RFFs.
III-C The Complication in Data Processing
Limited distinguishability and adverse effect of the channel leads to the usage of complicated data processing [22] or large time series data [21], including complex feature extraction mechanism for mining the RFFs. Noise and multipath components in the real world channel also adds to the complexity of RFF mining. Recently, an attempt to minimize the channel effects was proposed with the use of tunable FIR filter at the transmitter [5]. This FIR tuning required computation of the filter taps at the server, which are then downlinked back to the transmitter to improve the RFF accuracy. Although this improved the reliability, it increased the hardware and power cost of using a continuously tunable FIR filter in the hardware and a 3 step authentication procedure having security flaws.
III-D Design Consideration: Need for Configurability
Let us consider the mathematical model of an RF-Fingerprinting system. For an IoT network with nodes, let the node be transmitting a signal to the server. The received signal received by the server can be formulated as:
| (1) |
where is the transceiver effect imposed on user , is the transmitted signal, is the wireless channel, and is the noise. These features of each transceiver, i.e., , are unique RFFs and can be observed from the electromagnetic waves that are emitted by it. However, with developing manufacturing processes, these intrinsic variations are diminishing. The variation caused due to the function diminishes and becomes indistinguishable from that of the other node, given practical environmental noise. This greatly reduces the user capacity of the RF-Fingerprinting system. Furthermore, if the threshold conditions are adjusted to accommodate such a minute variation, it would make the system unreliable.
Design Requirements:
-
a)
Configurability: A discernible solution to the above problems, is to design the intrinsic variation , which would ensure that the patterns are different for different users. It can also be perceived as intentionally creating some perturbations in the transmitted signal unique to the IoT device. If is configured, a balance between reliability and security can be designed based on the wireless channel. It can also eliminate the limited distinguishability and the need for complicated data mining since the features are software controlled.
-
b)
Channel Robustness: The design has to allow the RFF to be prominent through the wireless channel.
-
c)
Low power consumption: IoT devices with batteries are power-constrained and cannot expend much energy for authentication alone.
-
d)
Non-intrusiveness and integrable: This solution should neither adversely affect the communication link not complicate the protocol in use.
-
e)
Cost-effectiveness:: Several IoT applications cannot afford expensive hardware.
III-E Proposed Solution
In this paper, we propose to use ‘metasurface’ (A brief introduction about metasurface is given in section IV) to inject a controlled, well-intended RF Fingerprint, which is more prominent and can carry more complex features in the physical layer economically. Using the metasurface (Intelligent reflective surface) we create constructive signal additions at different frequencies within the same band. Our system is very energy efficient as it can work with no power or with few hundred micro-joules depending on the application. Furthermore, It can be built cheaply for or less. Our solution also makes the signature injection part of the transmitter non-intrusive, i.e., Our metasurface can be attached to the transmitter (IoT device) and is designed to induce electromagnetic changes in the waves that are emitted by the transmitter (an example application would be cellphone case or additional inexpensive cover for the IoT device). Since this is attached at the transmitter end, the function would be a convolution of the designed property induced by our metasurface .

III-F Analysing IoT hardware for RFF injection
Since our solution is a low cost accessary to the IoT devices aiding in its authentication, it is necessary to analyze the hardware components of the IoT transmitter with the objective to find the answer to two important questions. The primary one is
a) Can a security signature be injected into the wireless physical layer by changing the existing hardware?
To answer this question let us consider the injection of such a signature by making changes specifically in the passband of the transmitted signal. In a typical IoT transmitter such as the direct conversion transmitter [9] shown in figure 2, the digital to analog converter (DAC’s)takes in data bits as in-phase and quadrature components. The output of the DAC is then filtered and sent to a mixer, where the baseband is up-converted to RF frequency. The Mixers are driven I and Q local oscillator inputs. The output is then passed through a power amplifier (PA) and is sent to the antenna drive circuit via a bandpass filter (BPF reduces out of band emissions). All the existing RFFS are created due to the imperfections in the above-mentioned components [23].
To create controlled perturbations of any of these respective components is not easy. Power Amplifiers of IoT transmitters are carefully designed with the tradeoff between nonlinearity and power-efficiency [24]. The power amplifier distortions, even though are hardware signatures, can result in a performance loss; hence, they are carefully designed in a certain operating point [24]. Thus designing a variation in PAs is too complicated, given the constraints of it affecting the performance. Similarly, reconfigurable mixers [25] do exist, but these reconfigurations do not create distortions. Mixer distortions would create synchronization and timing issues, thus affect communication performance. The DAC’s are also very carefully designed with complex constraints to reduce the power for IoT transmitters [26]. Thus introducing configurable distortions to these transmitter entities may prove very costly, which leaves us with the RF filters. Injection of an RFF can be made possible via a digital filtering technique, which would create that feeble variation or make deliberate changes to the hardware that would create uniquely identifiable signatures from device to device. Thus our questions on the feasibility of injecting RFF is narrowed down to the possibility of creating perturbations in the wireless physical layer with the help of carrier shaping digital RF- filter. This brings us to another important question that needs to be answered,
b) Can this signature injecting, RF-filter be cost effective and power efficient to be adopted for IoT authentication?
Let us consider the hardware realization of a passband filter that can generate a fingerprint. We group them as two main methods of realization, which is as described below:
III-F1 FIR filter with window
Firstly, we can design a digital finite impulse response (FIR) filter, apply a suitable window function, then approximate the functions to make them implementable [27]. They can be implemented either by using a separate DSP chip [28] or by designing a dedicated system on a chip (SoC) [29] comprising of latches, multipliers, and adders.
-
a)
Complexity analysis: Consider FIR filter with a Kaiser window that can alter the emitted carrier wave, which can supposedly act as an RFF. The choice of this specific method to analyze was considered primarily because the FIR method can be represented as integer math [27] and thus making them realizable with hardware compared to IIR filters. Secondly, a typical kaiser window [30] is applied here, which is appropriate for generating sharp peaks. This algorithm can be considered as 3 steps. Firstly, the computation of , which has a computational complexity of [30], where is the number of samples. Secondly, the computations of FIR filter output, which has a fixed number of multiplications and additions involved. Finally, the computation of a Kaiser window, which has the complexity of , where is the number of frequency samples points. The implementation of the first two steps can be performed either by DSP [27] or an SoC [29] as previously mentioned and the computation of custom window needs a numerical function generator (NFG) [31] unit.
-
b)
DSP implementation: Although there are very cheap DSP’s available for as small a price as [32], they have an idle power consumption of at supply [32]. Furthermore, the delays involved in using a DSP unit is larger because it needs to perform the total filter operation in iterations. This is because the DSP relies on a single efficient multiplication and adder unit (MAC) to perform the operation per loop [33]. The resulting power consumption and time delay are not affordable for an IoT device.
-
c)
SoC implementation: The same filter implemented using SoC, however, would be faster as they can perform the operation in a single flow, but the complexity of the 3 stages are tough to be designed in a single chip without significant approximations [27], as they rely on implementing the operation with only latches, multipliers, and adders. Also, the power consumption of such a filter to of size is estimated to be for low throughput applications [34], thus making them unaffordable for IoT devices.
III-F2 RF resonator Filters:
Another way of making the variation could be through RF filters [35]. Out of the RF filter technologies that exist, such as discrete inductor-capacitor (LC) filters, multilayer and monoblock ceramic filters, acoustic filters, and cavity filters, the current state of the art wireless communication chips employ BAW filters [36] to achieve operation. Even though devices with higher Q-factor and lower insertion loss have been designed, complex signatures with configurable BAW filters [37] of RFF capability are a few decades away from becoming a reality. It is difficult to design these filters with precise cutoff, group delay, selectivity, ripple, and isolation between input and output signals [38].
From the above discussion, it is clear that making the transmitter chip with reconfigurable hardware components for signature injection would prove to be costly, inefficient and may affect communication performance.
III-G Configuration for Different Security Level
We present two types of metasurfaces that can be employed with the design goals we have set.
-
a)
Passive metasurface - This metasurface has a well designed, feature rich signature injection capability but is static. Thus making it suitable for very low-cost applications.
-
b)
Active (programmable) metasurface - This metasurface can change its property based on a control input while maintaining the richness in the feature space. This feature is very suitable for IoT applications, which are not strictly energy constrained but needs a more secure solution as the injected signature can change with respect to control input.
With the capabilities as mentioned above, we designed and implemented the metasurface RF fingerprint injection (MeRFFI) System, which is a programmable metasurface, MeRFFI prototype has the capability to work in both the modes due to its programmability.
We present three different ways in which MeRFFI can be used for IoT authentication.
III-G1 Passive Mode
Protocol 1 - low power application : Here the MeRFFI Device used does not have channel selection or signature injection control mechanism. It is a passive meta-surface like a passive RFID card, which consumes no additional power. A different pattern is printed on MeRFFI, and these signatures are injected into the wireless physical layer. During authentication, the IoT node (I) sends an authentication request signal (Req) along with its device id (DevID) to the access point (A). This signal is injected with the physical signature (IRFF1) from MeRFFI.
The access point (A) extracts the injected channel state information (). It forwards this request () to the authentication server ().
The authentication server extracts the features () and checks for a match. If the feature and DevID match to that of the registered device, the server sends back an acknowledgment message with a hash code of the feature () along with the target DevID. When node receives this authentication acknowledgment, it can also verify that it is associating with the correct server from the hash .
III-G2 Active Mode
Protocol 2 - highly secure application and high power consumption : This protocol uses the active version of MeRFFI that uses control voltage based signature injection. The IoT node () sends a request to the authentication server () using the same message flow as in the previous protocol. The authentication sends back the acknowledgment along with the hash of the feature extracted from the pilot signal (). On receiving the the IoT node does a server hash correlation and verifies the hash. After the hash is verified the node pushes number of designated signatures, which are allotted to the node. On receiving all the signatures, the authentication server correlates all the received signatures () with the device id (DevID). MeRFFI’s high user capacity supports this highly secure protocol.
Protocol 3 - highly secure application and medium power consumption : In this protocol, multiple transmissions are made similar to protocol 2, but the property of the metasurface is not changed. Here the injected signature on the IoT node (I) is fixed, and transmissions are made from different channels to the authentication server (A). This protocol is suggested based on the hypothesis that the same signature appears as distinct from different channels. This is later validated with our experiments. The difference in the property of MeRFFI in different channels is leveraged here to create a highly secure protocol. The power consumption here would be less than protocol 2 since there is no need to switch the metasurface.



IV Meta-surface RF-Fingerprint Injection (MeRFFI) System Design
From section The radio frequency fingerprint injection system is described along with the basic user enrollment and authentication scheme. Consider a scenario as shown in figure 1 where there are nodes trying to connect with the authentication server. All the registered nodes in the network are attached with the MeRFFI. As it can been seen in the figure 3, during the enrollment phase, the legitimate node sends a known pilot signal to the server over the wireless channel. The attached MeRFFI device injects an RF security signature in this transmitted electromagnetic wave. The server on receiving the node’s signal measures the channel state information (CSI) and then extracts the injected features from the measured CSI. A classifier trains and classifies the signatures of all the legit user devices and stores them in a database. During the authentication phase, when the user nodes request access, the server measures the CSI and extracts the features of the signature from this request signal. The projected features are then matched with the enrolled user devices and is granted authentication on a match. An attacker node, on the other hand, would not have the injected signatures; hence their authentication will be denied.
MeRFFI knows the communication channel number (specific frequency) allocated for communication. It can tune to the present channel of operation. Then it supplies a software programmed voltage vector input, where all unit elements are controlled by each in the voltage values. This results in MeRFFI altering the wireless physical layer by injecting a physical signature.
IV-A Metasurface Preliminary
Metasurfaces [39] are ultra-thin and planar electromagnetic devices, which are made up of several unit elements. These unit elements are sub-wavelength in size compared to traditional microwave patches and printed antenna elements. They have heavily gained popularity because of the tunability of their individual unit elements [40].
The metasurface for RF-fingerprint injection is a prototype that has software programmed tunability. The material design specification and its tuning control are described below.

IV-B MeRFFI Prototype Design
MeRFFI is a software-controlled metasurface used for injecting the security signature. It is an Intelligent Reflective Surface (IRS), a.k.a Reconfigurable Reflect Array, which has many unit cell structures [7]. The typical IRS’s unit cells can change their resonant frequencies, which can be perceived as a change in its reflectance and phase. Our custom designed metasurface, MeRFFI, creates constructive reflections on the signals transmitted. These small perturbations appears as frequency peaks when observed from the channel state information at the receiver. To design this specific reflective surface, the unit element has two main requirements. Firstly, to bring the entire metasurface’s resonant frequency to the specific frequency channel where the transmission is taking place. Secondly, some finer modifications of resonances within this channel cause different electromagnetic variations in the wireless physical layer.
MeRFFI’s unit cell structure: MeRFFI prototype’s unit cell has three layers: 1) a frequency selective resonant layer; 2) loading plane, which helps in miniaturizing the dimensions of the metamaterial, and; 3) a reflective ground plane. The top layer is a split ring resonator (SRR), which at the designated frequency, reflects an incoming wave. There is a capacitor connected between the slit after split-ring resonator in top layer to change the resonant frequency this SRR. The second layer is a complementary split ring resonator (CSRR) used to miniaturize the unit element[41, 42]. Finally, between the there is a variable capacitor connected for changing larger values of resonance.
Specifications: The meta-surface unit element design is shown in figure 4. We have used a split ring resonator as the top plane. A complimentary split ring resonator is used as the loading plane [43, 8]. The dimensions of these layers are given in figure 6(a). We have used varactor [44] as C1 and C2. This lab prototype is shrunk to a half-wavelength dimension of its original size, but for usage in much smaller devices, this can be miniaturized further [42]. The entire unit element is built using an FR4 substrate, which is a common PCB material.
MeRFFI’s control mechanism : Figures 6(c) and 6(d) shows the voltage inputs given to all the varactors in MeRFFI prototype. By changing the input voltage to the capacitor , the capacitance between the loading plane and reflecting plane changes. Since this control voltage () is connected to all the unit cells, the total resonance of the meta-surface shifts to the desired frequency channel. Hence this voltage is the channel select voltage. The change in resonant frequency with variation in capacitance is shown in figure 7 (The graph shown is a Comsol simulation of MeRFFI, where the capacitance is changed by control voltages, the value displayed here is frequency vs. radar cross section [RCS()])

The other varactors on the top layer, however, have independent voltage connections. If MeRFFI has number of elements, then an line parallel but independent control voltage line is needed for controlling the varactors (. This line control voltage is what can be used to inject RF-fingerprints into the wireless physical layer. The MeRFFI prototype has 4 unit elements as shown in Figure 6 and two such prototypes were used for signature injection. Hence MeRFFI prototype had an 8 line control input vector. The metasurface prototype has eight such elements in which an 8-line control voltage feed can be given for creating many such variations.
IV-C Mathematical Modeling
For modeling the injection of a physical layer signature, consider the transmitting IoT node which has MeRFFI is placed in its proximity, such that any emission from the node reflects from the MeRFFI as shown in the figure 5. Let be the signal transmitted by the IoT node ( in the frequency domain) and is the function of the meta-surface. Any transmission going out from this node would be the convoluted with as it is emitted [7]. if represents the multipath channel between node and the authentication server, the expression for received signal can be written as,
| (2) |
The function can be considered as the sum of the reflection from individual unit elements whose magnitude and phase is controlled by the control voltage vector . The fourier transform of which has unit elements can be written as,
| (3) |
where and are the magnitude and phase of the response from the unit element, and is the time delay of the impulse in the time domain. The channel response received at the receiver as seen in equation 2 is a convolution of the MeRFFI’s transfer function () and the channel multipath () similar to the sum of the product of amplitude and phase responses caused by the individual path in the multipath, the fingerprint is also the sum of the effect caused by the individual unit elements in the reflect array [7]. In the frequency domain this injected channel response , is given as:
| (4) |
where represents the frequency sample of the signature injected channel and it is a complex number that includes the amplitude and the phase is shown as follows.
| (5) |
Thus at the receiver we get the injected channel vector for , CSI samples (here, the number of CSI samples ) , i.e ,
| (6) |
In general,
| (7) |
From the received signal vector we extract . The fingerprint induced CSI of the IoT node to the authentication server has to be extracted.
| (8) |
After obtaining the injected fingerprint has to be separated from this vector. Thus we can define a feature extraction space , where the feature of a single fingerprint is translated to an N-dimensional feature space.
| (9) |
where . After this we find a function , that can project the feature space of users, , to class space, , i.e.,
| (10) |
where the function belongs to a hypothesis space . After the projection, the feature of the specific user is classified to the corresponding class.
IV-D Signature Extraction and Classification
As mentioned in equation 6, we receive a vector of complex values corresponding to the number of CSI samples in the communication channel. A convolutional neural network (CNN) was used to extract the signature from the computed CSI vector . Although CNN is more computationally complex, a server in IoT can afford the computational expenditure during user enrollment, the matching (authentication) phase would be just as simple as any other classfier algorithm. In MeRFFI’s implementation, the first three layers of the CNN are used to extract features. In each layer of the CNN, one-dimensional kernels were used as the filters. This was followed by a batch norm layer to normalize the mean and variance of the data at each layer. For the third layer, a rectified linear unit (ReLU) was added to introduce nonlinearity and a max-pooling layer to reduce the size of the representation.If is the set of parameters for feature extraction in the CNN, then we get the feature as:
| (11) |
Depending on the outputs of feature extractor (i.e., F), a fully connected layer followed by another ReLU is used to learn the representation of as follows:
| (12) |
where and are the parameters to be learned and the softplus function is an activation function to introduce nonlinearity, in order to identify the injected signature, the feature representation into a new latent space , where is the total number of signatures to be classified. Finally, a Softmax layer is used to obtain the probability vector of signatures:
| (13) |
| (14) |
where and are parameters. From this, we obtain classes corresponding to the signatures . A loss function can be defined where is the estimated class. The expected loss of (the entire classification function) can be estimated while training, using an empirical risk function , where
| (15) |
This measure helps us in avoiding overfitting and underfitting scenarios while training. After the classifier is trained, the classified features of the enrolled users are then stored in a database. When a new incoming signal is received, its feature is extracted and its score is computed with the features saved in the database, which is then used for authentication.
IV-E Reconciling MeRFFI to Channel Dynamics
To design the MeRFFI metasurface to inject a robust RFF into the wireless channel, we need to take in to account the dynamics of the channel. Let’s consider a scenario where node is at a location and the receiving base station at . The received signal strength can be represented as a 2D non-stationary field made up of three types of channel dynamics [45]; path loss (), shadow fading () and the multipath fading component ().
| (16) |
Let the injected the injected signature be represented by the random variable , which is dependent only on the channel select voltage and signature inject voltage vector , the received signal strength becomes,
| (17) |
In Decibels this equation is,
| (18) | |||
From various indoor channel modeling based on real-world measurements [45] , is a distance dependent path loss, and follows a zero mean gaussian distribution and the channel multipath follows a rician distribution as given by,
| (19) |
Where is the Rician K factor, which is the ratio between the power in the direct-path () and the diffused power, and is the order Bessel function. By applying the expectation operator on equation 18 and rearrange it to inequalities we get,
| (20) | |||
Here the path loss has zero mean and we can deduce that the gain of the RF-fingerprint injected should be greater that the multipath power.
Consider a dynamic environment of an area of radius with moving objects each at distances of the receiver and having an average width of . These objects absorb some part of the energy, by an absorb factor and the total path power is . If the objects are uniformly distributed with in the area has the following [46],
| (21) |
From this equation, we can infer that the rician factor and hence mean dynamic value of the multipath power is influenced by the number of moving objects per unit area [46] ( means a highly dynamic channel).
IV-F Channel Robust Metasurface Design
For the injected signature to be prominent in this dynamic environment, MeRFFI metasurface’s SNR with in a short delay spread has to be above the threshold level of the maximum variations caused by channel dynamics. Practically this is the metasurface’s expected capability where it provides constructive interference on the channel, which aids the communication by enhancing certain narrow frequency components. This is contrary to the frequency selective fading introduced by the multipath and requires the metasurface to be tuned to the operating frequency. The maximum gain of the metasurface is obtained when the perimeter of the unit cell is of the order of the wavelength used for communication (). The gain reduces when the unit cell’s size is shrunk. The idea is to choose the metasurface’s size to make the constructively added perturbations to withstand channel variations and at the same time conform to the devices form factor. Our prototype is thus built with the perimeter of each unit cell of the order of (65 mm), which is sufficient for a time varying, dynamic, real-world indoor environment.
Remark: Designing the metasurface channel robust also has the advantage that the injected Rf-fingerprint dataset size becomes independent of the channel, robust to time variance and depends only on the injected code.
V Experiment and Results
As indicated in the previous sections, MeRFFI is a low cost and small attachment to the IoT transmitter’s hardware that can inject a radio frequency fingerprint (RFF) into the wireless physical layer. Technically, MeRFFI’s hardware can be used either in passive mode, where it injects a fixed physical signature, or in active mode, where it can inject varying physical signature according to an input control voltage vector and also has the capability to select the channel (frequency) of operation. To test MeRFFI’s performance both in active and passive mode, the prototype as shown in figure 6(b) was built in the lab. Extensive experiments have been performed using this MeRFFI prototype for testing its potency as a wireless physical layer injection system for the IoT applications. All the experiments were performed in a dynamic environment wherein between 2 and 6 people are always present in the testbed’s vicinity. The testing duration also spanned between 4 and 12 hours per day over 60 days to give the collected dataset a time varying factor.
In this section, we present MeRFFI’s control mechanism set up, performance measures used followed by the experiments in which the MeRFFI system was tested. Initially, we test MeRFFI’s control mechanism via an experimental setup using a Vector Network Analyzer (VNA), where we inject different control codes and visually observe the changes in the wireless channel. After making sure the proof-of-concept software programmability of MeRFFI works, we conduct our experiments on a WiFi commercial off the shelf (COTS) testbed to test MeRFFI. Our COTS testbed utilizes laptops Lenovo ThinkPad E570 and Dell Latitude E6530 with Intel 5300ac NIC card to replicate the different static IoT deployment scenarios and check whether MeRFFI satisfies the specified design goals:
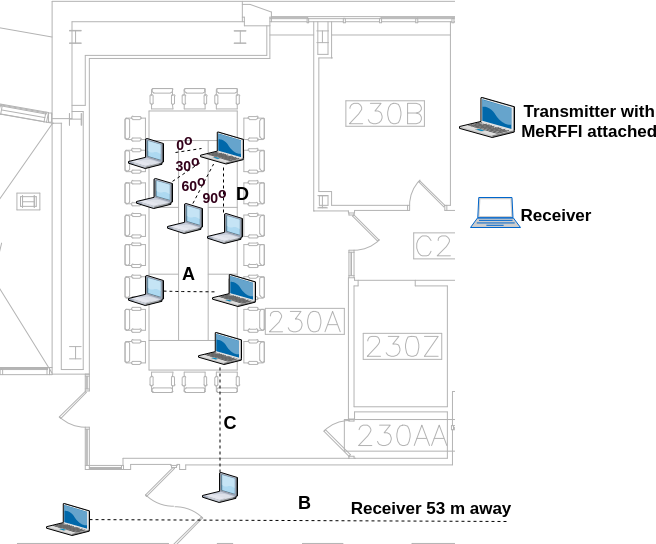
(a) Inject 208 closely-spaced control codes and observe the performance to estimate the user capacity of our prototype. (b) Test the performance with change in distance. Here, changes in distance upto 53 m in an indoor multipath channel were made and the resulting performance was analyzed. (c) Test the impact of orientations of the user devices. (d) Test the effect of blockage by the through-the-wall experiments. (e) Test the performance of the system, when same set of signatures are injected in different WiFi channels.
V-A MeRFFI Metasurface and Control Mechanism
Two 4-unit cell based structures were used in all the experiments(figure 6). As mentioned in section 5, two types of control (figure 6(c) & (d)) are required. control voltage , which is a single parallel voltage to be supplied to all the individual elements to select the channel of operation, control voltage vector , is used to inject different RF-signatures in the selected channel. We use an Arduino Mega 2560 to drive the DAC circuit to provide , and two similar sources were used to feed in the control vector .
Different inputs correspond to an individual unit cell control input, and this was made sure with the above mentioned voltage sources and voltage divider circuits.
V-B Performance Measures
For computing the performance of the classification system designed, we first compute the following:
a) true positive (TP): the digital signatures correctly identified, b) true negative (TN): the fingerprints correctly rejected, c) false positive (FP): the false signature wrongly identified, and d) false negative (FN): a valid signature misclassified as false. These values are used to compute the standard performance measures sensitivity ( recall, hit rate, or true positive rate (TPR), Fall-out or false positive rate (FPR), Precision or positive predictive value (PPV), Accuracy (ACC), F1 Score, area under the ROC (receiver operating characteristic) curve.
Since this is a multi-class classification problem. We compute the micro and macro average of all the performance measures shown above. Hence we perform an number of one vs. all classifications for all the classes and compute this micro and macro averages performance measure, which would give us an overall performance of the signatures classified at the receiver. A sample of how micro and macro averages are computed. An example for computing the micro and macro average of precision ( and ) is given as
| (22) |
| (23) |


We use the micro and macro averages to create the average ROC and then compute the , average, which would give us a good sense of the overall performance of the system.
V-C Testing MeRFFI’s Control Mechanism
Objective: To visually observe changes caused in the wireless channel caused by the control voltage input given to MeRFFI and thereby verifying if MeRFFI’s channel select and signature inject control mechanisms are working.
Experimental setup: To test whether the designed meta-surface performs as per the design specification, an Agilent Vector Network Analyzer (model-8753ES) was used. MeRFFI was kept near the TX antenna, and (forward gain) was observed from the receiver end, which is kept 2.54 m away. At first control input was changed, and changes were observed at the VNA. The experiment was done in a conference room with the setting as seen in figure 10.
Results and inferences: At 16.1 volts a peak was observed within the range 2.420 GHz and 2.425 GHz, which indicates that was functioning as the channel selector. Then random voltage vectors was applied and distinct (forward gain) patterns corresponding to different inputs were observed as seen in the figure 8. This pre-test helped us validate the channel select mechanism and different patterns observed at the VNA verify that the signature injection mechanism of MeRFFI is functional.
| Layer (Type) | Output Shape | Param# |
|---|---|---|
| conv1d_1 (Conv1D) | (30, 24) | 120 |
| activation_1 (Activation) | (30, 24) | 0 |
| flatten_1 (Flatten) | (720) | 0 |
| dense_1 (Dense) | (2048) | 1476608 |
| dropout_1 (Dropout) | (2048) | 0 |
| dense_2 (Dense) | (1024) | 2098176 |
| dense_3 (Dense) | (208) | 213200 |
| activation_2 (Activation) | (208) | 0 |
| Total params: 3,788,104 | ||
| Trainable params: 3,788,104 | ||
|
|
V-D Determining Signature Capacity of MeRFFI
Objective: In this experiment, 208 codes, which are very close to each other (very minimum voltage change in each input control), are given as input SV. This experiment is to classify these 208 closely-spaced signatures received at the receiver and estimate the signature capacity of MeRFFI.
Experimental setup: This experiment was performed in a conference room m, whose plan is displayed in figure 9 and the position is marked with label A. This room was chosen so that the environment is not controlled, which includes other commercial wireless interferences. The COTS experimental devices used were a Lenovo ThinkPad E570 equipped with an Intel 8265ac NIC card as the transmitter, and a Dell Latitude E6530 fitted with an Intel 5300ac NIC card as the receiver. MeRFFI was placed 2 cm in front of the transmitter’s inbuilt antenna as shown in figure 10. The receiver is placed 2.54 m away from the transmitter. The values of the control voltages for each unit cell are varied from 0 till 10, while the control inputs to other unit cells are kept zero. Twenty six voltage values were given to each capacitor, and the changes were done on all the eight different unit cells. Thus making it 208 different code words triggering that many injected codes, which have very minimum variation from one to the next. The number of voltage values that can be given to each unit element depends on the dynamic range of the varactor chosen. The data set collected 500 CSI vector values received for each signature. The structure of the CNN used for classifying this data is shown in table I.

Result and inference: Table II shows the accuracy and the F1 score (micro and macro averages) for 80:20 and 90:10 test to train percentage split. The values suggest that MeRFFI RF-Fingerprinting has a substantial signature capacity and is very reliable. In the above experiment, each unit cell was triggered by 26 voltage levels one after the other. Based on the technical specification of the varactor [44] used in creating this variation a maximum of 32 different physical signatures.
To generalize, consider a MeRFFI prototype that has unit elements in the metasurface. Each of these unit elements can create several capacitance variations depending on the dynamic characteristics of the varactor connected to them. If is the dynamic range of the varactor and is the minimum control voltage needed to create capacitance change of the varactor, the number of signatures that can be injected by MeRFFI can be written as :
| (24) |
From this equation, we can interpret that a high resolution varactor with a higher dynamic range can achieve a large design space for signatures.
In a perfect environment with low noise, the MeRFFI prototype in the lab that has 8 unit cells can create a maximum () signatures. Thus a more significant number of unit cells in MeRFFI would result in a higher signature capacity.
| Test-Train | |||||
|---|---|---|---|---|---|
| Split | Accuracy | ||||
| 80% test | 0.81 | 0.9848 | 0.9932 | 0.9 | 0.9 |
| 90% test | 0.7415 | 0.9774 | 0.9781 | 0.87 | 0.87 |
| Distance | Accuracy | ||||
|---|---|---|---|---|---|
| 7 m | 0.8914 | 0.9819 | 0.9407 | 0.9407 | 0.9412 |
| 27 m | 0.8297 | 0.9716 | 0.9071 | 0.9071 | 0.9062 |
| 53 m | 0.9128 | 0.9854 | 0.9524 | 0.9524 | 0.9527 |
| Angle | |||||
|---|---|---|---|---|---|
| (deg) | Accuracy | ||||
| 0 | 0.989 | 0.9981 | 0.994 | 0.994 | 0.9939 |
| 30 | 0.9542 | 0.9923 | 0.975 | 0.975 | 0.975 |
| 60 | 0.9792 | 0.9965 | 0.9887 | 0.9887 | 0.9887 |
| 90 | 0.9819 | 0.9969 | 0.9901 | 0.9901 | 0.9902 |
| Accuracy | F1_micro | F1_macro | AUC_micro | AUC_macro | |
| Blockage | 0.9678 | 0.9946 | 0.9824 | 0.9824 | 0.9825 |
| Test-Train | |||||
|---|---|---|---|---|---|
| Split | Accuracy | ||||
| 50% test | 0.9429 | 0.9799 | 0.9865 | 0.97 | 0.96 |
| 60% test | 0.9104 | 0.9866 | 0.9862 | 0.95 | 0.95 |
| 70% test | 0.93 | 0.9875 | 0.9872 | 0.97 | 0.97 |
| 80% test | 0.903 | 0.9746 | 0.9865 | 0.91 | 0.91 |
| 90% test | 0.8454 | 0.9704 | 0.9862 | 0.92 | 0.92 |
|
|
V-E Performance with Variation in Distance (Path Loss)
Objective: This experiment is performed to test the variation in the performance of the MeRFFI system with varying distances.
Experimental setup: This experiment is performed using the same COTS devices mentioned in the previous experiment. Here the distance of the receiver is varied in each experiment (distance). The receiver is kept at three different distances 7 m, 27 m and 53 m from the receiver location and the experiment is done on WiFi’s channel 5. The experimental setup is labeled as ’B’ in the figure 9 and as seen in the figure, is a 53 m long corridor, thus a complex environment from the wireless channel perspective. Twelve different signatures were injected through the MeRFFI device on the transmitted wireless signal. Packets are transmitted for 20 seconds for each signature. The signatures received at the receiver are classified using a CNN whose structure is similar to the one shown in the table I. Here only 20 percent of the data is used for training and the remaining 80 percent is used for testing.
Result and inference: Table III shows the performance of the MeRFFI system with different distances 7m, 27m, and 53m. It can be seen that the system performs well, despite the wireless channel being a complex tunnel-like environment. Hence MeRFFI’s injected signature does not significantly vanish from the wireless physical layer with distance. Since MeRFFI’s application scenario requires it to be kept very close to the transmitter, it can be inferred that the injected signatures exist at very short delay spread compared to other multipath components that come into picture when the communication distance increases.
V-F Impact of Orientation
Objective: This experiment is done to test whether a change in orientation between the transmitter and receiver affects the performance of MeRFFI’s RF-fingerprint injection capability.
Experimental setup: This experiment was performed in the same COTS equipment mentioned in the previous experiment. The transmitting laptop has the Intel 8265ac is attached with the MeRFFI device and is kept at a fixed location. The receiver laptop is at a distance of 2.54 m from the transmitter. The experimental setup is marked ’D’ in the figure 9. The position of the receiver is then varied by 30 degrees with the distance being the same. The same 12 voltage values are injected in four such orientations 0∘, 30∘, 60∘, and 90∘ respectively. This data is then classified using CNN for each location, and their performance is compared. Same as the previous experiment, 20 percent of the data is used for training, and the remaining 80 percent is used for testing.
Result and inference: Table IV shows the performance of the MeRFFI system with varying orientation. The minimum accuracy obtained was 95.42 percentage. It can be seen that the change of orientation does not affect the performance of this system.
V-G Through Wall Signature Injection
Objective: This experiment is done to test the MeRFFI’s signature injection capability when there is a blockage between the transmitter and the receiver.
Experimental setup: This experimental setup, which is represented as ’C’ in the figure 9 is placed such that the transmitter is in one room, 100 m away from the wall and the receiver is placed 0.3 m away from the wall in the next room. There is no other line of sight available for these COTS devices to communicate. The same 12 codes as in the previous experiment are injected by the transmitter. The received codes are classified using the CNN classifier with the structure as given in table I. Similar to the previous cases, 20 percent of the data was used for training, and the remaining 80 percent was used for testing.
Result and inference: As it can be seen from the table V, MeRFFI performs well through a wall. With 20 percent training and remaining test, MeRFFI has the potential to be applied for real-world scenarios with obstruction.
V-H Effect of Using Multiple Channels
Objective: To test the hypothesis that the same signature injected by MeRFFI appears as a different one if the devices use a different channel for communication.
Experimental setup: Here we use the test set up ’A’ as shown in figure 9. 24 signatures were injected in 4 different channels. Thus a 96 class recognition system had to be built.
Result and inference The minimum micro averaged AUC for test to train ratio varying from 50 to 80 was observed to be 0.95. Table VI shows the averaged F1 scores and accuracy. From the observations, we can validate this hypothesis that MeRFFI’s signature appears different when observed from a different channel number.
V-I Throughput, Power, Cost and other Inferences
All the above experiments were done using the very high throughput mode (VHT) of IEEE 802.11 ac. The data rate is always above 50 Mbps, thus indicating that the injected perturbations do not significantly hinder the datarate. We also did not observe any packet drops while MeRFFI was attached to the transmitting node.
The cost of manufacturing our prototype was less than 10 dollars including the price of commercial varactor chips used. The cost was kept low due to in lab design and fabrication. On mass production these materials would cost less than 20 cents per device.
The entire power including the control mechanism, i.e., channel select and signature inject code was less than 50 millijoules (0.05 Ws), which, when compared to DSP chip is less power consumed. The energy consumption of a programmable MeRFFI module does not vary with packet size. In our COTS testbed, the above results indicate that MeRFFI is very suitable for commercial IoT adoption.
VI Security Analysis
In this section, we discuss whether our proposed system is vulnerable to a man-in-the-middle scenario and replay attack.
VI-A Threat Model
Consider an RF-Fingerprint authentication scenario, as seen in figure 11, where an IoT node ’’, which has the MeRFFI module attached, is trying to access an authentication server ’’. There is a man-in-the-middle scenario where an attacker ’’ is trying to break this authentication mechanism. Here, ’’ can try to impersonate the genuine node ’’.
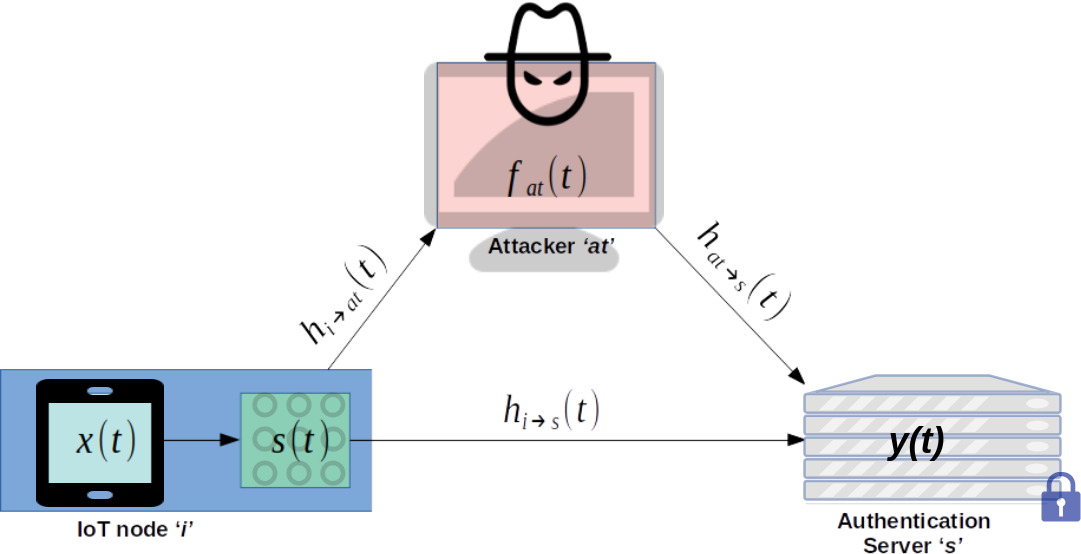
Let be the original signal from the node that is received at the server . This can be represented as
| (25) |
where is the transfer function of MeRFFI module and be the impulse response of the IoT node to the server channel. In comparison to this, the received signal replayed by the attacker and received by the server can is given by:
| (26) |
Here is the impulse response of node to attacker channel and is the channel response from attacker to server. let be the filter function of the attacker. From equations 25 and 26 we can see that in-order for the attacker to successfully replay the injected feature, the following condition should be satisfied:
| (27) |
Assumptions: The attacker can launch the replay attack in mainly two ways [17], signal replay attack and feature replay attack. In a signal replay attack, ’’ records node ’s signal and simply re-transmits the signal without any modification. Here the attacker does not need to know the features that are injected. In a feature replay attack, the attacker does not know the injected features but is trying to derive such information, in which the filter function of the attacker is tuned such that the signal from the attacker is same as that the original signal from node , i.e., .
VI-B Robustness Against Attacks
VI-B1 Against Signal Replay Attack :
From equation (26) we can see that the attacker has no way of reproducing the physical channel by merely doing a signal replay attack, since , in this case, would be equal to a constant gain value . The only case when a signal replay attack may work is when the attacker is very close (less than distance from the tx or rx, also known as the guard zone [47]). For 2.4 GHz WiFi, this would be 6.25 cm.
VI-B2 Against Feature Replay Attack :
Let the injected channel response be denoted as . Then the frequency domain representation of the filter function of the attacker can be derived from the previous equation as:
| (28) |
This equation shows the difficulty of the attacker as it has to simultaneously and accurately model three different channel models and then use it to precisely find a filter response that when transmitted through the air would physically be equal to the injected signature by MeRFFI in node ’s signal. Looking this difficulty from a computational aspect: if we are using a 64 subcarrier WiFi signal, the attacker has to accurately model three channel responses. For each of the three channel responses, the attacker has to find a vector of 64 complex numbers, then use this vector to accurately model the injected signal response, which is another complex vector of size 64.


VI-C Experimental Validation:
Objective: To perform a feature replay attack on MeRFFI system.
Experimental Setup:
For this experiment there are three entities involved: (a) the legitimate transmitter (Alice), (b) the receiver (Bob) and (c) the attacker (AT). Their specifications are as follows:
(a) Alice : A Lenovo ThinkPad E570 equipped with an Intel 8265ac NIC card with MeRFFI attached as the transmitting node.
(b) Bob: a Dell Latitude E6530 fitted with an Intel 5300ac NIC card as the receiver.
(c) AT : In-order to give the attacker, the best possible capabilities, we equipped it with the best devices we have. We designed the AT with four devices, (i) a Dell Latitude E6530 fitted with an Intel 5300ac NIC card, which acts as evesdropper for snooping the signal transmitted by Alice, (ii) Dell Precision tower server-T5810 with Intel Xeon CPU E5-1630 @ 3.7 GHz and 64 GB ram, for performing the feature learning, similar to equation 28 , (iii) A Lenovo ThinkPad E570 equipped with an Intel 8265ac NIC card for doing the feature replay transmission (iv) MeRFFI for injecting the features that were evesdropped.
The experimental setup can be seen in figure 12, and the distances between the entities are marked in the figure. In our setup, Alice transmits to Bob, AT is trying to perform a feature replay attack. AT has knowledge of the frequency channel used for communication, the channel control voltage to select that channel, and several signature control vectors (secret hardware key) and their responses. AT first receives the packet as an eavesdropper with equipment (i), then uses a deep learning-based supervised function approximator using the setup (ii) to train estimate the value of at the receiver, let the estimated value be (). AT then uses equipment (iii) to transmit packets to Bob by using MeRFFI, which is controlled with the estimated . Bob already has a classifier trained to accept only legitimate devices (here Alice’s RFFs generated with MeRFFI). Bob receives the packets from Alice and the Attacker and checks them for authenticity.
To quantify the attacking scenario. First, Alice transmits 5500 packets of 11 different MeRFFI signatures. The Attacker knows all the 11 signature control vectors , uses these as labels to train its deep learning based function approximator (from the 5500 packets, 4950 packets are used to train the network and 550 are used to validate, this is to avoid overfitting). The function approximator is a modified version of CNN shown in table I, where the output layer is modified to get smooth estimates[48, 49]. With this we perform our evaluation with 2 test procedures.
Test procedure 1: We test the linear separability of the received data of 12 different attacks (transmissions by AT). The separability is measured by Mahalanobis distance between Alice’s data and AT’s data, as seen by Bob. In each scenario AT listens for 5500 packets from 11 signals of Alice, and sends 25 attack signatures towards Bob.
Test procedure 2: In this test, we identify the CSI samples with the least distance from test procedure 1 and perform an attack on Bob. Bob has an authentication system built (using CNN shown in table I to accept all 12 signatures from Alice. Then Attacker uses its learned function approximator to generate 500 packets for which the signature control vector is , where is a secret between Alice and Bob. This estimated control signal, is used to send 500 packet burst with MeRFFI to force an authentication with Bob.
Result: From test procedure 1, we identified that test 5 has the least distance between Alice’s signature and AT’s signature, as seen by Bob. The distance, which is equal to 1, is still a good distance, which a strong classifier can classify. But this signature is the weakest among the one we tested. We then perform procedure 2, where we use this scenario to send 500 attack packets to Bob. Here Bob has an authentication system that is tailored to accept 12 different signatures from Alice. In this experiment, all the 500 packets from AT were rejected by Bob. We also checked if time variability affects the attack, hence we performed this attack again after one week, but the results were the same.
Inference: From this experiment, we can infer that even after knowing many of the signature control vectors , it is extremely difficult to attack the MeRFFI system if the control code is not known. This opens up the avenue for developing a data-dependent device procedure where a digital signature and physical signature are dependent, further improving the security condition. Another inference we can make is from test procedure-1 (figure 13). We can observe that certain attack signatures may have high similarity to the original injected CSI, as is the case with tests 5, 3, and 11. Although they were still rejected authentication by a carefully designed classifier at Bob, this weakness can be reduced using protocol 2 and 3, which uses multiple code injections to authenticate a node. Other than the attack scenario mentioned above, one may argue that the attacker may also have the capability to record the downlink channel without the signature, inverse it, and then compare it with the injected channel to isolate the signature. But reciprocity of the channel is usually an assumption to get approximate CSI, due to the detrimental changes in the transceiver components and the channel [50], thus making this measurement inadequate for the attacker.
VII Discussions
VII-A Security-Reliability Trade-off
The radio frequency fingerprint community has been trying to address the contradicting tradeoff between security and reliability [20]. With MeRFFI we have optimized the dimensions based on our theoretical deductions in section IV-E to maintain an optimum between security and reliability based on the environment.
VII-B Size Matters
The metamaterial research community has been actively researching the [42] area of Frequency Selective Surfaces (FSS). The Prototype created in our lab has been miniaturized to half the size of its original dimension. Size reduction up to of the original dimension is common in the metamaterial research community. This miniaturization is also accompanied by narrowed operating bandwidth of the frequency selective surface and reduced gain. The narrow bandwidth is good for RFF injection, a smaller number of perturbations can be made in the operating frequency, but a reduced gain can make the authentication system sensitive to environmental effects. Thus, while designing the size of MeRFFI, we have to take into consideration the application and the frequency of operation.
VII-C Enabling Node Movement
In MeRFFI’s classifier design, we used a CNN that is robust in a static environment, but if the receiver has a change in orientation or is required to be moved from one place to another, it would have to be retrained in the system. This is because the feature representation may not separate (linear separability) the injected signature from the environmental multipath. This can be solved either by generalization using transfer learning approaches [51, 52], or using 2 step transmission for authentication. To further clarify, if the feature representation of the injected signatures made in one position/orientation is termed source domain data and the representation in another position/orientation is the target domain data, we would want the features learned from the source domain to be valid in the target domain. In statistical terms, we need to generalize the injected features learned by reducing the difference between the distributions of the source and target domain data.
Another way to solve this problem is to use a two code transmission for authentication, where the difference in the injected CSI’s [53] at the receiver yields the actual code. Let the IoT node transmit three security signatures ,, and . These signatures are influenced by channel H. At the receiver, let the received signature be , and . Using and and using this difference to authenticate the TX node can make the system robust to movement. Our future work is focused on realizing this authentication scheme.
VII-D Energy Harvesting FSS
Our experimental results suggest that an active Frequency Selective Surface (FSS) offers much more secure physical layer signatures than a passive one. Although the active MeRFFI prototype made in the lab consumes very minimal power, low power IoT applications would need energy harvesting based FSS [54] that does not need an external battery.
VIII Conclusions
In this paper, we design and implement the MeRFFI, a small and inexpensive metasurface, which injects RF-fingerprints into the wireless physical layer. Through experiments on a COTS testbed, we have shown that these signatures are very reliable and have a large design space. MeRFFI consumes only very little power to produce distinguishable RFFs, thus making it very suitable for IoT applications. We have suggested three easily integrable protocols using MeRFFI, where we have suggested the scenarios where MeRFFI can be used in a passive form or active form depending on the priorities and needs of a specific IoT network. Our security analysis discusses how significantly more complex this system is to be cracked compared to the current state-of-the-art.
References
- [1] “Internet of things forecast,” Ericsson, Tech. Rep. [Online]. Available: https://www.ericsson.com/en/mobility-report/internet-of-things-forecast
- [2] “Internet of things market analysis-2026,” 2019. [Online]. Available: https://www.fortunebusinessinsights.com/industry-reports/internet-of-things-iot-market-100307/
- [3] S. Singh, P. K. Sharma, S. Y. Moon, and J. H. Park, “Advanced lightweight encryption algorithms for IoT devices: survey, challenges and solutions,” Journal of Ambient Intelligence and Humanized Computing, may 2017.
- [4] L. N. Whitehurst, T. R. Andel, and J. T. McDonald, “Exploring security in zigbee networks,” in CISR ’14. New York, NY, USA: ACM, 2014, pp. 25–28.
- [5] F. Restuccia, S. D’Oro, A. Al-Shawabka, M. Belgiovine, L. Angioloni, S. Ioannidis, K. Chowdhury, and T. Melodia, “Deepradioid: Real-time channel-resilient optimization of deep learning-based radio fingerprinting algorithms,” in Mobihoc ’19. New York, NY, USA: Association for Computing Machinery, 2019, p. 51–60.
- [6] E. Basar, M. Di Renzo, J. De Rosny, M. Debbah, M. Alouini, and R. Zhang, “Wireless communications through reconfigurable intelligent surfaces,” IEEE Access, vol. 7, pp. 116 753–116 773, 2019.
- [7] O. Özdogan, E. Björnson, and E. G. Larsson, “Intelligent reflecting surfaces: Physics, propagation, and pathloss modeling,” IEEE Wireless Communications Letters, vol. 9, no. 5, pp. 581–585, 2020.
- [8] F. Bayatpur, “Metamaterial-Inspired Frequency-Selective Surfaces,” Tese de doutorado, 2009.
- [9] C. Choi, J. Choi, M. Kim, H. Park, and I. Nam, “A low power 2.4-ghz cmos direct-conversion transmitter for ieee 802.15.4,” in IWS 2014, March 2014, pp. 1–4.
- [10] A. C. Polak, S. Dolatshahi, and D. L. Goeckel, “Identifying wireless users via transmitter imperfections,” IEEE JSAC, vol. 29, no. 7, pp. 1469–1479, August 2011.
- [11] V. Brik, S. Banerjee, M. Gruteser, and S. Oh, “Wireless device identification with radiometric signatures,” in MobiCom ’08. New York, NY, USA: ACM, 2008, pp. 116–127.
- [12] F. zhuo, Y. Huang, and J. chen, “Radio frequency fingerprint extraction of radio emitter based on i/q imbalance,” Procedia Computer Science, vol. 107, pp. 472 – 477, 2017, advances in Information and Communication Technology: Proceedings of 7th International Congress of Information and Communication Technology (ICICT2017).
- [13] D. H. Kwon, H. Li, Y. Chang, R. Tseng, and Y. Chiu, “Digitally equalized cmos transmitter front-end with integrated power amplifier,” IEEE Journal of Solid-State Circuits, vol. 45, no. 8, pp. 1602–1614, Aug 2010.
- [14] A. C. Polak and D. L. Goeckel, “Identification of wireless devices of users who actively fake their rf fingerprints with artificial data distortion,” IEEE Transactions on Wireless Communications, vol. 14, no. 11, pp. 5889–5899, Nov 2015.
- [15] B. Danev, T. S. Heydt-Benjamin, and S. Čapkun, “Physical-layer identification of rfid devices.”
- [16] D. Zanetti, B. Danev, and S. & capkun, “Physical-layer identification of uhf rfid tags,” in MobiCom ’10. New York, NY, USA: ACM, 2010, pp. 353–364.
- [17] B. Danev, K. E. Defrawy, U. C. Irvine, H. Luecken, S. Capkun, and K. El Defrawy, “Attacks on Physical-layer Identification,” ACM WiSec, pp. 89–98, 2010.
- [18] U. Chatterjee, V. Govindan, R. Sadhukhan, D. Mukhopadhyay, R. S. Chakraborty, D. Mahata, and M. M. Prabhu, “Building puf based authentication and key exchange protocol for iot without explicit crps in verifier database,” IEEE Transactions on Dependable and Secure Computing, pp. 1–1, 2018.
- [19] J. Delvaux, “Machine-learning attacks on polypufs, ob-pufs, rpufs, lhs-pufs, and puf–fsms,” Cryptology ePrint Archive, Report 2017/1134, 2017, https://eprint.iacr.org/2017/1134.
- [20] P. Robyns, P. Quax, and W. Lamotte, “Phy-layer security is no alternative to cryptography,” in WiSec ’17. New York, NY, USA: ACM, 2017, pp. 160–162.
- [21] W. Wang, Z. Sun, K. Ren, and B. Zhu, “User capacity of wireless physical-layer identification,” IEEE Access, vol. 5, pp. 3353–3368, 2017.
- [22] T. Zheng, Z. Sun, and K. Ren, “Fid: Function modeling-based data-independent and channel-robust physical-layer identification,” in IEEE INFOCOM 2019, 2019, pp. 199–207.
- [23] B. Danev, D. Zanetti, and S. Capkun, “On physical-layer identification of wireless devices,” ACM Comput. Surv., vol. 45, no. 1, pp. 6:1–6:29, Dec. 2012.
- [24] F. Edalat, “Effect of power amplifier nonlinearity on system performance metric, bit-error-rate,” Master’s thesis, Massachusetts Institute of Technology, Cambridge, Massachusetts, 8 2003.
- [25] R. Circa, D. Pienkowski, G. Boeck, R. Kakerow, M. Mueller, and R. Wittmann, “Resistive mixers for reconfigurable wireless front-ends,” in 2005 IEEE Radio Frequency integrated Circuits (RFIC) Symposium - Digest of Papers, 2005, pp. 513–516.
- [26] A. Khorami, R. Saeidi, and M. Sharifkhani, “An ultra low-power dac with fixed output common mode voltage,” AEU - International Journal of Electronics and Communications, vol. 96, pp. 279 – 293, 2018.
- [27] S. A. Alam, “Techniques for efficient implementation of fir and particle filtering,” Ph.D. dissertation, Linköping University, SE–581 83 Linköping, Sweden, 7 2016.
- [28] M. Mehendale, S. D. Sherlekar, and G. Venkatesh, “Low-power realization of fir filters on programmable dsps,” IEEE Transactions VLSI Systems, vol. 6, no. 4, pp. 546–553, 1998.
- [29] A. T. Erdogan and T. Arslan, “High throughput fir filter design for low power soc applications,” in Proceedings of 13th Annual IEEE International ASIC/SOC Conference (Cat. No.00TH8541), 2000, pp. 374–378.
- [30] S. G. Johnson and M. Frigo, “Implementing ffts in practice,” 2009.
- [31] T. A. Knudstrup, “A model for minimizing numeric function generator complexity and delay,” Master’s thesis, Naval postgraduate School, 1 University Circle, Monterey, CA 93943, 12 2007.
- [32] Fixed-Point Digital Signal Processors, Texas Instruments, 4 2014, rev. 2.
- [33] J. Serrano, “Digital signal processing using field programmable gate arrays,” in 13th Beam Instrumentation Workshop (BIW08), 5 2008, pp. 29–38.
- [34] B. K. Mohanty and P. K. Meher, “A high-performance fir filter architecture for fixed and reconfigurable applications,” IEEE Transactions on VLSI Systems, vol. 24, no. 2, pp. 444–452, 2016.
- [35] Y. Al-Yasir, N. Ojaroudi Parchin, R. Abd-Alhameed, A. Abdulkhaleq, and J. Noras, “Recent progress in the design of 4g/5g reconfigurable filters,” Electronics, vol. 8, no. 1, p. 114, Jan 2019.
- [36] C. C. W. Ruppel, “Acoustic wave filter technology–a review,” IEEE Transactions on Ultrasonics, Ferroelectrics, and Frequency Control, vol. 64, no. 9, pp. 1390–1400, 2017.
- [37] K. Hashimoto, S. Tanaka, and M. Esashi, “Tunable rf saw/baw filters: Dream or reality?” in 2011 Joint Conference of the IEEE International Frequency Control and the European Frequency and Time Forum (FCS) Proceedings, 2011, pp. 1–8.
- [38] L. Miller, RF Filter Technologies for Dummies- Quorvo edition. 111 River St. Hoboken, NJ 07030-5774: John Wiley & Sons, Inc, 7 2015, special Edition.
- [39] F. Liu, A. Pitilakis, M. S. Mirmoosa, O. Tsilipakos, X. Wang, A. C. Tasolamprou, S. Abadal, A. Cabellos-Aparicio, E. Alarcón, C. Liaskos, N. V. Kantartzis, M. Kafesaki, E. N. Economou, C. M. Soukoulis, and S. Tretyakov, “Programmable metasurfaces: State of the art and prospects,” in ISCAS 2018, May 2018, pp. 1–5.
- [40] S. B. Glybovski, S. A. Tretyakov, P. A. Belov, Y. S. Kivshar, and C. R. Simovski, “Metasurfaces: From microwaves to visible,” Physics Reports, vol. 634, pp. 1 – 72, 2016, metasurfaces: From microwaves to visible.
- [41] D. Oloumi, S. Ebadi, A. Kordzadeh, A. Semnani, P. Mousavi, and X. Gong, “Miniaturized reflectarray unit cell using fractal-shaped patch-slot configuration,” IEEE Antennas and Wireless Propagation Letters, vol. 11, pp. 10–13, 2012.
- [42] J. Tang, R. O. Ouedraogo, E. J. Rothwell, A. R. Diaz, and K. Fuchi, “A continuously tunable miniaturized patch antenna,” IEEE Antennas and Wireless Propagation Letters, vol. 13, pp. 1080–1083, 2014.
- [43] F. Meng, Y. Liu, and S. K. Sharma, “A miniaturized patch antenna with enhanced bandwidth by using reactive impedance surface ground and coplanar parasitic patches,” Int. J. RF Microw. Comput. Eng., vol. 30, no. 7, p. e22225, 2020.
- [44] D. Sheet, “Smv2019 to smv2023 series : Hyperabrupt junction tuning varactors,” pp. 1–10, 2015.
- [45] A. G. A. Gonzalez-Ruiz and Y. Mostofi, “A Comprehensive Overview and Characterization of Wireless Channels for Networked Robotic and Control Systems,” Journal of Robotics, vol. 5, p. 19, 2011.
- [46] Y. Ohta and T. Fujii, “Dynamic channel model for static mobile terminals in indoor los and nlos environments,” in IEEE VTC Spring 2008, May 2008, pp. 507–512.
- [47] X. He, H. Dai, W. Shen, P. Ning, and R. Dutta, “Toward Proper Guard Zones for Link Signature,” IEEE Transactions on Wireless Communications, vol. 15, no. 3, pp. 2104–2117, 2016.
- [48] S. Ferrari and R. F. Stengel, “Smooth function approximation using neural networks,” IEEE Transactions on Neural Networks, vol. 16, no. 1, pp. 24–38, 2005.
- [49] I. Ohn and Y. Kim, “Smooth Function Approximation by Deep Neural Networks with General Activation Functions,” Entropy, vol. 21, no. 7, 2019.
- [50] S. Haile, “Investigation of channel reciprocity for ofdm tdd systems,” Master’s thesis, University of Waterloo, Waterloo, Ontario, Canada, 7 2009.
- [51] N. Wagle and E. W. Frew, “Transfer learning for dynamic rf environments,” in ACC 2012, June 2012, pp. 1406–1411.
- [52] X. Lu, L. Xiao, T. Xu, Y. Zhao, Y. Tang, and W. Zhuang, “Reinforcement learning based phy authentication for vanets,” IEEE Transactions on Vehicular Technology, vol. 69, no. 3, pp. 3068–3079, 2020.
- [53] M. Dunna, C. Zhang, D. Sievenpiper, and D. Bharadia, “Scattermimo: Enabling virtual mimo with smart surfaces,” in Proceedings of the 26th Annual International Conference on Mobile Computing and Networking, ser. MobiCom ’20. New York, NY, USA: ACM, 2020.
- [54] S. Keyrouz, G. Perotto, and H. J. Visser, “Frequency selective surface for radio frequency energy harvesting applications,” IET Microwaves, Antennas Propagation, vol. 8, no. 7, pp. 523–531, May 2014.
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/3a0a54fc-0743-4770-8754-7c689d3858e5/Sek.jpg) |
Sekhar Rajendran (SM’19) received his B.Tech. degree in electronics and communication from Cochin University of Science and Technology, India and his M.Tech. degree in signal processing and control systems from the National Institute of Technology, Hamirpur, India. Currently, he is a Ph.D. student in the Department of Electrical Engineering at the University at Buffalo, The State University of New York. Prior to this role, he was an Assistant Professor in the Electronics and Communication Department in Rajagiri School of Engineering and technology (India) and has also worked in the wireless industry as a Network subsystem Engineer for Sasken Technologies Limited. His current research interests are in wireless physical layer security, reconfigurable wireless communications and wireless sensing. He is a Student Member of the IEEE. |
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/3a0a54fc-0743-4770-8754-7c689d3858e5/sun_2.jpg) |
Zhi Sun (S’06-M’11-SM’19) received the B.S. degree in telecommunication engineering from Beijing University of Posts and Telecommunications (BUPT), Beijing, China, in 2004, the M.S. degree in electronic engineering from Tsinghua University, Beijing, in 2007, and the Ph.D. degree in electrical and computer engineering from the Georgia Institute of Technology, Atlanta, GA, USA, in 2011. He was a Postdoctoral Fellow with Georgia Institute of Technology from 2011 to 2012. In 2012, he joined the Department of Electrical Engineering, University at Buffalo, The State University of New York, Buffalo, NY, USA, as an Assistant Professor. He is currently an Associate Professor with University at Buffalo. His research interests include physical-layer security, wireless communication and networking in extreme environments, metamaterial enhanced communication and security, wireless intrabody networks, wireless underground networks, wireless underwater networks, and cyber-physical systems. He was a recipient of the NSF CAREER Award in 2017, the UB Exceptional Scholar—Young Investigator Award in 2017, the Best Demo Award at IEEE Infocom 2017, the Best Paper Award at IEEE Globecom in 2010, the BWN Researcher of the Year Award at the Georgia Institute of Technology in 2009, and the Outstanding Graduate Award at Tsinghua University in 2007. He serves as an Editor for the IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS and Computer Networks (Elsevier). He is a senior member of IEEE. |
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/3a0a54fc-0743-4770-8754-7c689d3858e5/feng.jpg) |
Feng Lin (S’11-M’15-SM’20) received the Ph.D. degree from the Department of Electrical and Computer Engineering, Tennessee Technological University, USA, in 2015. He is currently a Professor with the School of Cyber Science and Technology, College of Computer Science and Technology, Zhejiang University, China. He was an Assistant Professor with the University of Colorado Denver, USA, a Research Scientist with the State University of New York (SUNY) at Buffalo, USA, and an Engineer with Alcatel-Lucent (currently, Nokia). His current research interests include mobile sensing, Internet of Things security, biometrics, AI security, and IoT applications. Dr. Lin was a recipient of the Best Paper Awards from ACM MobiSys’20, IEEE Globecom’19, IEEE BHI’17, and the Best Demo Award from ACM HotMobile’18, and the First Prize Design Award from the 2016 International 3D printing competition. |
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/3a0a54fc-0743-4770-8754-7c689d3858e5/ren.jpg) |
Kui Ren (M’07–SM’11–F’16) is Professor and Associate Dean of College of Computer Science and Technology at Zhejiang University, where he also directs the Institute of Cyber Science and Technology. Before that, he was SUNY Empire Innovation Professor at State University of New York at Buffalo. He received his PhD degree in Electrical and Computer Engineering from Worcester Polytechnic Institute. Kui’s current research interests include Data Security, IoT Security, AI Security, and Privacy. He received Guohua Distinguished Scholar Award from ZJU in 2020, IEEE CISTC Technical Recognition Award in 2017, SUNY Chancellor’s Research Excellence Award in 2017, Sigma Xi Research Excellence Award in 2012 and NSF CAREER Award in 2011. Kui has published extensively in peer-reviewed journals and conferences and received the Test-of-time Paper Award from IEEE INFOCOM and many Best Paper Awards from IEEE and ACM including MobiSys’20, Globecom’19, ASIACCS’18, ICDCS’17, etc. His h-index is 74, and his total publication citation exceeds 32,000 according to Google Scholar. Kui is a Fellow of IEEE, a Distinguished Member of ACM and a Clarivate Highly-Cited Researcher. He is a frequent reviewer for funding agencies internationally and serves on the editorial boards of many IEEE and ACM journals. He currently serves as Chair of SIGSAC of ACM China. |