Evolutionary stability of cooperation in indirect reciprocity under noisy and private assessment
Abstract
Indirect reciprocity is a mechanism that explains large-scale cooperation in humans. In indirect reciprocity, individuals use reputations to choose whether or not to cooperate with a partner and update others’ reputations. A major question is how the rules to choose their actions and the rules to update reputations evolve. In the public reputation case, where all individuals share the evaluation of others, social norms called Simple Standing (SS) and Stern Judging (SJ) have been known to maintain cooperation. However, in the case of private assessment where individuals independently evaluate others, the mechanism of maintenance of cooperation is still largely unknown. This study theoretically shows for the first time that cooperation by indirect reciprocity can be evolutionarily stable under private assessment. Specifically, we find that SS can be stable, but SJ can never be. This is intuitive because SS can correct interpersonal discrepancies in reputations through its simplicity. On the other hand, SJ is too complicated to avoid an accumulation of errors, which leads to the collapse of cooperation. We conclude that moderate simplicity is a key to success in maintaining cooperation under the private assessment. Our result provides a theoretical basis for evolution of human cooperation.
1 Introduction
Cooperation benefits others but is costly to the cooperator itself. Nevertheless, cooperation is widespread from microscopic to macroscopic scales, such as among microorganisms, animals, humans, and nations. One way to sustain cooperation is that agents conditionally cooperate with others who cooperate with them, which is realized by, for example, repeated interactions [1, 2, 3] and partner choice [4, 5, 6, 7]. Such conditional cooperation based on personal experiences is applicable only to a small population where members can interact directly and repeatedly with most of the others.
However, cooperative behavior is observed even in a large-scale society (e.g., human societies). Since individuals inevitably encounter strangers there, they need reputations of those strangers in order not to cooperate unconditionally. Only individuals with good reputations can receive cooperation. The system that individuals indirectly reward others via their reputations as described above is called indirect reciprocity [8, 9, 10]. In reality, humans are particularly interested in reputations and gossip about themselves and others [11, 12, 13]. Furthermore, many experiments have pointed out that gossips concern cooperative behaviors [14, 15, 16].
Errors that inevitably occur in actions and in assessment hinder cooperation by indirect reciprocity. Indeed, the simplest social norm called image scoring [9, 10] fails to maintain full cooperation under errors [17, 18] (a similar failure is also seen in direct reciprocity [19, 20, 18]). This is because one erroneous defection triggers further defection. Nevertheless, previous studies have theoretically shown that cooperation can be maintained by the so-called “leading eight” social norms [21, 22] even in the presence of such errors when all individuals share the reputation of the same individual (i.e., public assessment). Public reputation cases have been thoroughly studied for about two decades [23, 24, 25, 26, 27, 28, 29, 30, 31, 32, 33, 34, 35, 36, 37]. When individuals cannot share their evaluations of the same target (i.e., private assessment), however, errors cast a shadow over cooperation more crucially. In this case, a single disagreement in opinions between two individuals can lead to further disagreements [38, 39, 40, 41, 42]. Whether cooperation is maintained under the noisy and private assessment is still largely unsolved in theory and is one of the major open problems in studies of indirect reciprocity [43, 44, 36].
Previous studies have shown that maintaining cooperation with indirect reciprocity is very difficult under noisy and private assessment. For example, Hilbe et al. [42] showed by an evolutionary simulation that the above leading eight strategies cannot succeed in cooperation under private assessment. Some studies [45, 46, 47] have demonstrated the emergence of cooperation under noisy and private assessment, but under the restrictive assumption that only local mutations in the strategy space are allowed, thus excluding the possibility that a fully cooperative strategy is directly invaded by free-riders. Other studies have shown that a mechanism to synchronize opinions between individuals has a positive influence on cooperation in indirect reciprocity, such as empathy, generosity, spatial structure, and so on [48, 49, 50, 51, 52, 53, 54, 55, 56, 57].
Most of these studies of private assessment have been performed by computer simulations [45, 42]. This is because two-dimensional information of who assigns a reputation to whom (its matrix representation is called “image matrix” [38, 58, 39, 59]) becomes too complex to analyze. For example, its possible transition is illustrated in Fig. 1-A, where a single assessment error can be amplified with time, leading to a mosaic structure in the image matrix. An evolutionary analysis between wild-type and mutant makes the image matrix further complex because the image matrix now includes four compartments based on different rules of reputation assignment adopted by wild-type and mutant individuals (Fig. 1-B). In spite of these difficulties, here we report that we have successfully developed an analytical machinery to study the image matrix by applying a technique previously developed by the authors [60]. This enables us to make a general prediction of when cooperation is sustained under noisy and private assessment over the full parameter region.
In the following, we will first introduce the setting of indirect reciprocity under noisy and private assessment and explain a method to analytically calculate the expected payoff of each individual through analyzing a complex image matrix. Then, we will discuss which strategy can be an evolutionarily stable strategy (ESS) [61, 62] under which condition, and provide intuitive reasons for the result. To our knowledge, this is the first systematic study that has analytically investigated evolutionary stability of strategies in indirect reciprocity under noisy and private assessment.

Model
We consider a model of indirect reciprocity in a well-mixed population of size . We assume that, in every step, a binary reputation is assigned independently from everyone to everyone, either good or bad, which is summarized by image matrix , where (resp. ) if individual assigns a good (resp. bad) reputation to individual . The model proceeds as follows. First, a donor and a recipient are randomly chosen from this population. Next, the donor takes its action, cooperation or defection, to the recipient. When the donor cooperates, the donor incurs a cost but gives a benefit to the recipient instead. On the other hand, when the donor defects, no change occurs in the payoff of the donor or the recipient. Here, a rule that specifies how the donor chooses its action is called “action rule”. Throughout this paper, we assume that all the individuals adopt the “discriminator” action rule [9, 63], with which they choose cooperation (resp. defection) to a good (resp. bad) recipient in their own eyes; that is, donor chooses cooperation toward recipient if , and chooses defection if . We assume that the donor unintentionally takes the opposite action to the intended one with probability (action error). All the individuals in the population observe this social interaction between the donor and the recipient and independently update the reputation of the donor in their eyes.
A rule that specifies how each observer updates the reputations of the others is called its “social norm”. In models of public reputation, it has often been assumed that all the individuals in the population adopt the same social norm [21, 64, 29] (but see [38]), otherwise, they cannot share the reputation of the same individual. Because we consider a model of private reputation here, however, we instead assume that individuals can adopt different social norms. This study deals with a situation where each observer (say, ) refers to (i) whether the donor (say, ) cooperates (C) or defects (D) (first-order information) and (ii) whether the recipient (say, ) is good (G) or bad (B) in the eyes of the observer (second-order information, represented by ) when this observer updates the reputation of the donor in the eyes of the observer, denoted by . Such social norms are called “second-order” social norms [10, 18, 33, 36]. An observer who adopts a second-order social norm can face four different cases, denoted by GC(“toward a Good recipient the donor Cooperates”), BC(“toward a Bad recipient the donor Cooperates”), GD(“toward a Good recipient the donor Defects”), and BD(“toward a Bad recipient the donor Defects”), respectively, and in each case, the observer assigns either a good (G) or bad (B) reputation to the donor. Thus, a social norm is represented by a four-letter string. For example, is the social norm that assigns to the donor a good reputation in GC- and BD-cases, and a bad reputation in BC- and GD-cases. There are such social norms in total, and we lexicographically order them with the rule that G comes first and B comes second, and number them from to . Table 1 shows a full list of 16 social norms studied here. When updating the reputation, each observer independently commits an assessment error with probability , in which case he/she accidentally assigns the opposite reputation to the intended one to the donor.
| Social norm | GC | BC | GD | BD | |
|---|---|---|---|---|---|
| (ALLG) | G | G | G | G | |
| G | G | G | B | ||
| (SS; Simple Standing) | G | G | B | G | |
| (SC; Scoring) | G | G | B | B | |
| G | B | G | G | ||
| G | B | G | B | ||
| (SJ; Stern Judging) | G | B | B | G | |
| (SH; Shunning) | G | B | B | B | |
| B | G | G | G | ||
| B | G | G | B | ||
| B | G | B | G | ||
| B | G | B | B | ||
| B | B | G | G | ||
| B | B | G | B | ||
| B | B | B | G | ||
| (ALLB) | B | B | B | B | |
Several norms are especially important in previous studies, so we explain them below. We call ALLG and call ALLB because these norms unconditionally assign good or bad reputations. Next, , , , and belong to GB family. These norms share the same feature that they regard cooperation toward a good recipient as good, and defection toward a good recipient as bad. They only differ when the recipient is bad in the observer’s eyes. First, is called Scoring (SC), which regards cooperation toward a bad recipient as good and defection toward a bad recipient as bad, and therefore reputation assignment is independent of whether the recipient is good or bad in the observer’s eyes (thus, categorized as a first-order norm). Next, is called Stern Judging (SJ), which regards cooperation toward a bad recipient as bad and defection toward a bad recipient as good, as opposed to SC. Third, is called Simple Standing (SS) and it regards any action toward a bad recipient as good, and therefore it is the most generous norm in this family. Finally, is called Shunning (SH) and it regards any action toward a bad recipient as bad, and therefore it is the most intolerant one. Notably, SJ and SS are the two second-order norms that are included in the “leading eight” norms [21], which are norms that can successfully maintain cooperation under the noisy and public reputation that are found in the search within third-order norms. In particular, SJ has long been considered promising because it is evolutionarily successful [23] and because it sustains a very high level of cooperation despite its simplicity [33, 36]. SJ always suggests only one correct action to keep you good; it recommends cooperation toward good individuals and defection toward bad ones, and failure to follow this rule leads to a bad reputation. Under the noisy public reputation, SH cannot achieve full cooperation against itself but can prevent the invasion of ALLB (see SI for detailed calculation).
Under these settings, the strategy of an individual is its social norm. For this reason, we use “strategy” and “(social) norm” interchangeably in the following. We ask which strategy is evolutionarily stable. To this end, we study invasibility of a mutant strategy against a wild-type one. A strategy is ESS if it is not invaded by any other 15 mutant strategies. To derive their payoffs, we need to analyze the image matrix, which we shall perform below.
Analysis of reputation structure
Let us consider a situation where individuals with mutant norm invade the population of wild-type norm . Here, the proportion of mutants is given by . By extending the Fujimoto & Ohtsuki’s method [60] we can describe the image matrix by two probability distributions. Specifically, take a focal individual whose norm is , and let (hereafter called “goodness”) be the proportion of individuals among norm users who assign a good reputation to the focal individual, for . Thus, a wild-type individual is characterized by a pair of goodnesses, , and we represent its distribution over all wild-type individuals by . In the same way, a mutant is characterized by a pair of goodnesses, , and represents its distribution over all mutants. In SI, we derive the dynamics of and by formulating a stochastic transition of the donor’s goodnesses under the assumption of (the population is large), (mutants are rare), and (yet the number of mutants is sufficiently large). Then, we derive the equilibrium distributions, and . These equilibrium distributions give expected payoffs of wild-types and mutants, which enable us to study the invasibility condition of mutants to wild-types (see SI again).

We find that each of the two equilibrium distributions is well approximated by a weighted sum of two-dimensional Gaussian functions with zero covariance, where each Gaussian can be systematically labeled by a nonzero integer, (see an example in Fig. 2-B and the rule of labeling in Fig. 2-C). Hence the number of Gaussians that appear in the sum is infinitely but countably many. In some cases, however, these labels degenerate (i.e., two or more Gaussians are identical but they are given different labels) and the number of Gaussians can be finite. Weights to Gaussians decay exponentially as becomes large positive or large negative, so a truncation at some finite number of terms approximates well the infinite sum for numerical calculations.
ESS norms
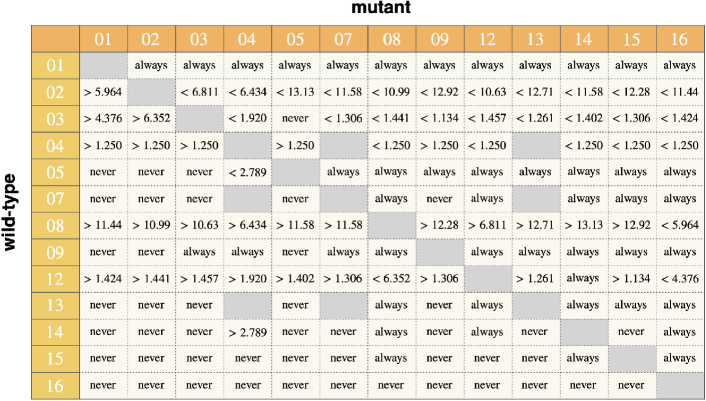
Based on the analysis of the image matrix above, we have studied pairwise invasibility for all the pairs of wild-type and mutant . In the following, we set the action error rate as , because this error, especially when it is small positive, does not have a qualitative impact on our results as far as we studied. Thus, the cost-benefit ratio and the assessment error rate are our environmental parameters.
We first find that the four strategies, , (SJ), , and , are completely indistinguishable, both as wild-types and as mutants. This is because these norms always give the goodness of to anyone in the population at equilibrium due to an accumulation of assessment errors and hence they appear to choose cooperation and defection in a random manner. In particular, they are neutral to each other. For these reasons, we will discuss only (SJ) as a representative of them and exclude the other three in the following analysis.
Our exhaustive analysis demonstrates that only three norms, (SS), (SH), and (ALLB) can be ESS, and all the others cannot. As shown in Fig. 3-A, ALLB is ESS independent of and , because it is the norm that assigns a bad reputation to everyone, saves the own cost, and provides no benefit to others. On the other hand, SS and SH achieve ESS for some and ; there are upper and lower bounds of for them to be ESS, which depend on . Below we will look at its details.

Conditions for ESS
The ESS condition of (SS) is shown in Fig. 3-B. When exceeds the upper bound, the norm is invaded by (ALLG) (compare the right and center panels of Fig. 3-A). On the other hand, when falls below the lower bound, the norm is invaded by (SC) (compare the left and center panels of Fig. 3-A). Fig. 3-C shows that these theoretical bounds are also supported by individual-based simulations. Notably, the smaller is, the wider the ESS region of (SS) becomes.
The ESS region of (SH) is quite narrow in comparison to that of (SS), as seen in Fig. 3-B. In addition, when exceeds the upper bound or falls below the lower bound, the norm is invaded by (SC) and (ALLB), respectively. The range of -ratios that make SH evolutionarily stable is the widest at an intermediate (about ).
In contrast to these results, we find that (SJ), which is known to be a successful norm when reputation is public, is invaded by norms such as (ALLB) and (SH) independent of the value of (and also independent of ), and therefore that it is never an ESS. This is summarized in Fig. 3-A.
To summarize, SS, SH, and SJ are all the ESS norms under the public assessment, but whether they remain ESS in the private assessment critically differs. This difference is clearly understood by focusing on how the reputation structure they give differs between the public and private reputation cases under a sufficiently small but positive assessment error rate, . Let us consider below, for example, whether each norm can prevent the invasion of ALLB, a potential invader norm.
Success of Simple Standing: The reputation structure that (SS) gives differs little between the public and private reputation cases (see Fig. 3-D). Under the public reputation (see SI for the calculation), SS assigns good reputations to SS themselves (represented by the bar at goodness in the top-left panel in Fig. 3-D), while bad reputations to ALLB (represented by the bar at goodness in the top-right panel in Fig. 3-D). Thus, SS distinguishes between SS itself and the invader ALLB and prevents the invasion of ALLB. Even under the private reputation, SS still assigns good reputations to SS themselves (see the bottom-left panel in Fig. 3; high goodness of are given to the fraction of SS individuals, for example), and assigns bad reputations to ALLB (see the bottom-right panel in Fig. 3; low goodness of are given to the fraction of ALLB individuals, for example). Thus, the distinction between SS and ALLB is maintained. For that reason, SS succeeds in achieving ESS even under the private assessment. The cooperation rate at this ESS is as high as for small , so it entails nearly perfect cooperation.
Failure of Stern Judging: Contrary to SS, the reputation structure that (SJ) gives extremely differs between the public and private reputation cases (see Fig. 3-E). Under the public reputation (see SI for the calculation), wild-type SJ gives high goodness to other SJ (top-left in Fig. 3-E) and wild-type SJ gives low goodness to ALLB (top-right in Fig. 3-E). Thus, SJ prevents the invasion of ALLB. Under the private assessment, however, SJ gives goodness of 1/2 to other SJ individuals (bottom-left in Fig. 3-E) [39] while SJ gives goodness of 1/2 to ALLB individuals as well (bottom-right in Fig. 3-E). Thus, the distinction between SJ and ALLB is lost. This is why SJ fails to be ESS under the private assessment.
Shunning can be ESS, but the level of cooperation is low: We can understand why (SH) achieves ESS only in a narrow region under private reputation (see SI for the detailed calculation and see Fig. S3 for the illustration for easy interpretation). Under the public reputation, SH gives good reputations to the half of other SH and bad reputations to the other half (top-left in Fig. S3) while SH gives bad reputations to almost all ALLB (top-right in Fig. S3). Thus, SH prevents the invasion of ALLB. Under private reputation, on the other hand, SH gives low goodness to both SH and ALLB (bottom-left and bottom-right in Fig. S3). Here, however, SH has a slightly better chance to receive good reputations than ALLB, in the order of . This explains why SH prevents the invasion from ALLB only in a narrow region and also explains why its ESS condition becomes more strict for a smaller assessment error rate, . The cooperation rate at a realized ESS is as low as for small , so we conclude that (SH) does not contribute to cooperation.
Discussion
This study considered indirect reciprocity under noisy and private assessment. We focused on goodness of individual (i.e., what proportion of individuals gives the individual good reputations) between different norms and developed an analytical method to calculate the distribution of goodness at equilibrium. Using this methodology we studied whether a mutant norm succeeds in the invasion into a wild-type norm. Although both (SS) and (SJ) can be ESS under public reputation, we found that their evolutionary stability is totally different under private assessment. In particular, we found that (SS) remains to be ESS under private assessment if the assessment error rate is small, while (SJ) cannot be ESS no matter how small the error rate is.
The reason for this difference between (SS) and (SJ) comes from the difference in the complexity of these two norms. In the world of private assessment, errors in assessment accumulate independently among observers, which is a potential source of collapse of cooperation in the population. However, since (SS) regards a cooperating donor as good no matter whether the recipient is good or bad, a discrepancy in the opinion toward the recipient between two different observers does not produce further discrepancy; those two observers can agree that such a cooperating donor is good. In contrast, (SJ) is more complex than (SS) and recipient’s reputation is always decisive information (see Table 1), so this complexity becomes an obstacle for correcting discrepancy between observers.
Hilbe et al. [42] studied by computer simulations whether the leading eight norms can sustain cooperation under the noisy and private assessment. They concluded that (SS) (referred to as “L3” in their paper) and (SJ) (“L6”) fail to achieve cooperation, which is contrary to our result. This difference is because we studied evolutionary stability in a deterministic model, while they studied fixation probability in a stochastic model. Because those two criteria are different, drawing a general conclusion is difficult, but the significance of our study lies in that we have shown that cooperation can be evolutionarily sustained even under private assessment.
A future direction of this study would be to examine ESS conditions of social norms when some of the assumptions are changed. For example, we have assumed second-order norms, in which individuals refer to a donor’s action (first-order information) and a recipient’s reputation (second-order one) when they update the donor’s reputation. However, humans may use more complex norms than the second-order ones. Studying the effect of higher-order information [65, 32, 33, 36], such as the previous reputation of the donor (third-order information), would further deepen our understanding. We have also assumed that all individuals simultaneously update their opinions toward the same donor. However, in a real society, the number of people who can observe a single person’s behavior is limited. Thus, the effect of asynchronous updates of reputations is worth studying. Last but not least, we have implicitly assumed that game interactions last sufficiently long so that we can use equilibrium distributions of goodness for calculating payoffs (i.e. discount factor is ). However, the effect of initial reputation cannot necessarily be ignored in some cases.
In conclusion, we have demonstrated that cooperation can be evolutionarily stable even under the noisy and private assessment. Specifically, we have shown that Stern Judging, which is one of the most leading norms under public reputation, cannot distinguish between cooperators and defectors under private assessment and thus fails to achieve ESS. On the other hand, we have revealed that Simple Standing can be stable in a wide range of parameters. Based on these results, we predict that Simple Standing should play a key role in sustaining cooperation by indirect reciprocity under noisy private assessment. These findings provide a rigid theoretical basis for understanding human cooperation and pave the way for future studies in biology, psychology, sociology, and economics.
Acknowledgement
Y.F. acknowledges the support by JSPS KAKENHI Grant Number JP21J01393. H.O. acknowledges the support by JSPS KAKENHI Grant Number JP19H04431.
References
- [1] Robert L Trivers. The evolution of reciprocal altruism. The Quarterly Review of Biology, 46(1):35–57, 1971.
- [2] Robert Axelrod and William D Hamilton. The evolution of cooperation. Science, 211(4489):1390–1396, 1981.
- [3] Robert Axelrod. The Evolution of Cooperation. Basic, New York, 1984.
- [4] Toshio Yamagishi, Nahoko Hayashi, and Nobuhito Jin. Prisoner’s dilemma networks: selection strategy versus action strategy. In Social dilemmas and cooperation, pages 233–250. Springer, 1984.
- [5] Ronald Noë and Peter Hammerstein. Biological markets: supply and demand determine the effect of partner choice in cooperation, mutualism and mating. Behavioral Ecology and Sociobiology, 35(1):1–11, 1994.
- [6] Ronald Noë and Peter Hammerstein. Biological markets. Trends in Ecology & Evolution, 10(8):336–339, 1995.
- [7] Pat Barclay. Strategies for cooperation in biological markets, especially for humans. Evolution and Human Behavior, 34(3):164–175, 2013.
- [8] Richard D Alexander. The biology of moral systems. Aldine de Gruyter: New York, 1987.
- [9] Martin A Nowak and Karl Sigmund. Evolution of indirect reciprocity by image scoring. Nature, 393(6685):573–577, 1998.
- [10] Martin A Nowak and Karl Sigmund. Evolution of indirect reciprocity. Nature, 437(7063):1291–1298, 2005.
- [11] Nicholas Emler. Gossip, reputation, and social adaptation. University Press of Kansas, 1994.
- [12] Robin Ian MacDonald Dunbar. Grooming, gossip, and the evolution of language. Harvard University Press, 1998.
- [13] Robin IM Dunbar. Gossip in evolutionary perspective. Review of General Psychology, 8(2):100–110, 2004.
- [14] Matthew Feinberg, Robb Willer, Jennifer Stellar, and Dacher Keltner. The virtues of gossip: reputational information sharing as prosocial behavior. Journal of Personality and Social Psychology, 102(5):1015, 2012.
- [15] Matthew Feinberg, Robb Willer, and Michael Schultz. Gossip and ostracism promote cooperation in groups. Psychological Science, 25(3):656–664, 2014.
- [16] Junhui Wu, Daniel Balliet, and Paul AM Van Lange. Reputation, gossip, and human cooperation. Social and Personality Psychology Compass, 10(6):350–364, 2016.
- [17] Karthik Panchanathan and Robert Boyd. A tale of two defectors: the importance of standing for evolution of indirect reciprocity. Journal of Theoretical Biology, 224(1):115–126, 2003.
- [18] Karl Sigmund. The calculus of selfishness. Princeton University Press, 2010.
- [19] Martin Nowak and Karl Sigmund. A strategy of win-stay, lose-shift that outperforms tit-for-tat in the prisoner’s dilemma game. Nature, 364(6432):56–58, 1993.
- [20] Jianzhong Wu and Robert Axelrod. How to cope with noise in the iterated prisoner’s dilemma. Journal of Conflict Resolution, 39(1):183–189, 1995.
- [21] Hisashi Ohtsuki and Yoh Iwasa. How should we define goodness?—reputation dynamics in indirect reciprocity. Journal of Theoretical Biology, 231(1):107–120, 2004.
- [22] Hisashi Ohtsuki and Yoh Iwasa. The leading eight: social norms that can maintain cooperation by indirect reciprocity. Journal of Theoretical Biology, 239(4):435–444, 2006.
- [23] Jorge M Pacheco, Francisco C Santos, and Fabio AC C Chalub. Stern-judging: A simple, successful norm which promotes cooperation under indirect reciprocity. PLoS Computational Biology, 2(12):e178, 2006.
- [24] Shinsuke Suzuki and Eizo Akiyama. Evolution of indirect reciprocity in groups of various sizes and comparison with direct reciprocity. Journal of Theoretical Biology, 245(3):539–552, 2007.
- [25] Francisco C Santos, Fabio ACC Chalub, and Jorge M Pacheco. A multi-level selection model for the emergence of social norms. In European Conference on Artificial Life, pages 525–534. Springer, 2007.
- [26] Feng Fu, Christoph Hauert, Martin A Nowak, and Long Wang. Reputation-based partner choice promotes cooperation in social networks. Physical Review E, 78(2):026117, 2008.
- [27] Shinsuke Suzuki and Eizo Akiyama. Evolutionary stability of first-order-information indirect reciprocity in sizable groups. Theoretical Population Biology, 73(3):426–436, 2008.
- [28] Satoshi Uchida and Karl Sigmund. The competition of assessment rules for indirect reciprocity. Journal of Theoretical Biology, 263(1):13–19, 2010.
- [29] Hisashi Ohtsuki, Yoh Iwasa, and Martin A Nowak. Reputation effects in public and private interactions. PLoS Computational Biology, 11(11):e1004527, 2015.
- [30] Fernando P Santos, Francisco C Santos, and Jorge M Pacheco. Social norms of cooperation in small-scale societies. PLoS Computational Biology, 12(1):e1004709, 2016.
- [31] Fernando P Santos, Jorge M Pacheco, and Francisco C Santos. Evolution of cooperation under indirect reciprocity and arbitrary exploration rates. Scientific Reports, 6(1):1–9, 2016.
- [32] Tatsuya Sasaki, Isamu Okada, and Yutaka Nakai. The evolution of conditional moral assessment in indirect reciprocity. Scientific reports, 7(1):1–8, 2017.
- [33] Fernando P Santos, Francisco C Santos, and Jorge M Pacheco. Social norm complexity and past reputations in the evolution of cooperation. Nature, 555(7695):242–245, 2018.
- [34] Fernando Santos, Jorge Pacheco, and Francisco Santos. Social norms of cooperation with costly reputation building. Proceedings of the AAAI Conference on Artificial Intelligence, 32(1), Apr. 2018.
- [35] Chengyi Xia, Carlos Gracia-Lázaro, and Yamir Moreno. Effect of memory, intolerance, and second-order reputation on cooperation. Chaos: An Interdisciplinary Journal of Nonlinear Science, 30(6):063122, 2020.
- [36] Fernando P Santos, Jorge M Pacheco, and Francisco C Santos. The complexity of human cooperation under indirect reciprocity. Philosophical Transactions of the Royal Society B, 376(1838):20200291, 2021.
- [37] Shirsendu Podder, Simone Righi, and Károly Takács. Local reputation, local selection, and the leading eight norms. Scientific Reports, 11(1):1–10, 2021.
- [38] Satoshi Uchida. Effect of private information on indirect reciprocity. Physical Review E, 82(3):036111, 2010.
- [39] Satoshi Uchida and Tatsuya Sasaki. Effect of assessment error and private information on stern-judging in indirect reciprocity. Chaos, Solitons & Fractals, 56:175–180, 2013.
- [40] Isamu Okada, Tatsuya Sasaki, and Yutaka Nakai. Tolerant indirect reciprocity can boost social welfare through solidarity with unconditional cooperators in private monitoring. Scientific Reports, 7(1):1–11, 2017.
- [41] Isamu Okada, Tatsuya Sasaki, and Yutaka Nakai. A solution for private assessment in indirect reciprocity using solitary observation. Journal of Theoretical Biology, 455:7–15, 2018.
- [42] Christian Hilbe, Laura Schmid, Josef Tkadlec, Krishnendu Chatterjee, and Martin A Nowak. Indirect reciprocity with private, noisy, and incomplete information. Proceedings of the National Academy of Sciences, 115(48):12241–12246, 2018.
- [43] Samuel Bowles and Herbert Gintis. A cooperative species. In A Cooperative Species. Princeton University Press, 2011.
- [44] Isamu Okada. A review of theoretical studies on indirect reciprocity. Games, 11(3):27, 2020.
- [45] Hitoshi Yamamoto, Isamu Okada, Satoshi Uchida, and Tatsuya Sasaki. A norm knockout method on indirect reciprocity to reveal indispensable norms. Scientific Reports, 7(1):1–7, 2017.
- [46] Sanghun Lee, Yohsuke Murase, and Seung Ki Baek. Local stability of cooperation in a continuous model of indirect reciprocity. Scientific Reports, 11(1):1–13, 2021.
- [47] Sanghun Lee, Yohsuke Murase, and Seung Ki Baek. A second-order perturbation theory for the continuous model of indirect reciprocity. arXiv preprint arXiv:2203.03920, 2022.
- [48] Eleanor Brush, Åke Brännström, and Ulf Dieckmann. Indirect reciprocity with negative assortment and limited information can promote cooperation. Journal of Theoretical Biology, 443:56–65, 2018.
- [49] Roger M Whitaker, Gualtiero B Colombo, and David G Rand. Indirect reciprocity and the evolution of prejudicial groups. Scientific Reports, 8(1):1–14, 2018.
- [50] Arunas L Radzvilavicius, Alexander J Stewart, and Joshua B Plotkin. Evolution of empathetic moral evaluation. Elife, 8:e44269, 2019.
- [51] Marcus Krellner and The Anh Han. Putting oneself in everybody’s shoes-pleasing enables indirect reciprocity under private assessments. In Artificial Life Conference Proceedings 32, pages 402–410. MIT Press One Rogers Street, Cambridge, MA 02142-1209, USA, 2020.
- [52] Ji Quan, Xiukang Yang, Xianjia Wang, Jian-Bo Yang, Kaibiao Wu, and Zilong Dai. Withhold-judgment and punishment promote cooperation in indirect reciprocity under incomplete information. EPL (Europhysics Letters ), 128(2):28001, 2020.
- [53] Marcus Krellner and The Anh Han. Pleasing enhances indirect reciprocity-based cooperation under private assessment. Artificial Life, 31:1–31, 2021.
- [54] Laura Schmid, Pouya Shati, Christian Hilbe, and Krishnendu Chatterjee. The evolution of indirect reciprocity under action and assessment generosity. Scientific Reports, 11(1):1–14, 2021.
- [55] Taylor A Kessinger and Joshua B Plotkin. Indirect reciprocity in populations with group structure. arXiv preprint arXiv:2204.10811, 2022.
- [56] Ji Quan, Jiacheng Nie, Wenman Chen, and Xianjia Wang. Keeping or reversing social norms promote cooperation by enhancing indirect reciprocity. Chaos, Solitons & Fractals, 158:111986, 2022.
- [57] Pengfei Gu and Yanling Zhang. Reputation-based rewiring promotes cooperation in complex network. In Advances in Guidance, Navigation and Control, pages 1405–1415. Springer, 2022.
- [58] Karl Sigmund. Moral assessment in indirect reciprocity. Journal of Theoretical Biology, 299:25–30, 2012.
- [59] Koji Oishi, Takashi Shimada, and Nobuyasu Ito. Group formation through indirect reciprocity. Physical Review E, 87(3):030801, 2013.
- [60] Yuma Fujimoto and Hisashi Ohtsuki. Reputation structure in indirect reciprocity under noisy and private assessment. Scientific Reports, 12(1):1–13, 2022.
- [61] J Maynard-Smith and George R Price. The logic of animal conflict. Nature, 246(5427):15–18, 1973.
- [62] John Maynard-Smith. Evolution and the Theory of Games. Cambridge university press, 1982.
- [63] Martin A Nowak and Karl Sigmund. The dynamics of indirect reciprocity. Journal of Theoretical Biology, 194(4):561–574, 1998.
- [64] Hisashi Ohtsuki and Yoh Iwasa. Global analyses of evolutionary dynamics and exhaustive search for social norms that maintain cooperation by reputation. Journal of Theoretical Biology, 244(3):518–531, 2007.
- [65] Robert Sugden. The economics of rights, co-operation and welfare. Basil Blackwell, 1986.
Supplementary Material
S1 Calculation of joint distribution of goodnesses
This section proposes an analytical method to obtain the reputation structure under indirect reciprocity. We assume a situation where rare mutants with norm of ratio invade other wild-types with norm of ratio . We denote the population ratio of norm as ; when , while when . To characterize the reputation structure, we define as a proportion of individuals of norm who assign good reputations to individual . We call a goodness of individual from norm .
In the following, let us consider a stochastic transition of in each round. In a single round, a recipient and a donor are chosen and labeled as and , respectively. In this round, , i.e., the goodness of donor from norm , changes into the next goodness for all . Below, we formulate the stochastic change separately for cases that the donor chooses to cooperate or defect.
C-map case: First, we consider a case that the donor cooperates with the recipient, occurring with a probability of
| (1) |
In this case, , i.e., the number of observers with norm who give good reputations to the donor in the next round, follows a probability distribution of
| (2) | ||||
| (3) | ||||
| (4) |
Here, denotes a binomial distribution with success probability and trial number . In addition, denotes the probability that an observer with norm who evaluates the recipient as newly gives a good reputation to the donor whose action is . , , , and are obtained by converting corresponding and pivots into and in Table 1 of the main manuscript. Instead of (3), we use a shorthand notation;
| (5) |
Because is sufficiently large, the mean and variance of are given by
| (6) | ||||
| (7) |
In (6), represents a map from the recipient’s goodness in the present round to the donor’s goodness in the next round. Because this map is applied only when the donor cooperates, we call it “C-map”.
D-map case: On the other hand, we consider a case that the donor defects with the recipient, occurring with a probability of
| (8) |
In this case, follows a probability distribution of
| (9) |
From this equation, the mean and variance of are given by
| (10) | ||||
| (11) |
Because the map is applied when the donor defects, we call it D-map in the same way as C-map.
The above C-map and D-map are illustrated in Fig. 1 for all .

S2 Time evolution of reputation structure
Because the population of wild-types and mutants are sufficiently large, we can continualize the distribution of individual goodness with separating into the cases that the norm of individual is or . In the following, denotes a continualized goodness of an individual with norm in the eyes of individuals with norm . Let us consider a time change of the distribution of . As shown above, however, we should keep in mind that and are simultaneously changed by the C-map or D-map. Thus, we consider dynamics of , a joint probability distribution of and . Note that a norm of the chosen recipient is only with a probability of , which contributes the dynamics of only in a scale of . By ignoring this scale of , the dynamics of is given by
| (12) |
Here, denotes a Gaussian function with the mean and variance as
| (13) |
Equation (12) explains an update of the donor’s goodness per time. The first (resp. second) term in the right side represents decrements (increments) by updating goodnesses. In detail, in the second term shows the density that the recipient’s goodness is (resp. ) in the eyes of wild-types (resp. mutants). shows the probability that the donor cooperates, and the donor’s goodnesses after the update in the eyes of observers with norm and are described by and , respectively. A similar explanation holds when the donor chooses to defect.
The equilibrium state of (12), i.e., , satisfies
| (14) |
To solve this equation, we assume that the equilibrium state can be described by a summation of two-dimensional Gaussian functions without correlation as
| (15) |
The assumption of Gaussian is justified by the above transition process of the donor’s goodness, where the goodness is virtually determined only by the mean and variance in a sufficiently large population. No correlation is assumed because the variance is given independently by observers with different norms.
We now derive equations which the equilibrium state satisfies for each norm . First, substituting (15) into (14) for , we obtain
| (16) |
This equation gives a constraint for . Next, when , in a similar manner, we obtain
| (17) |
This equation gives a constraint for .
To solve (16), let us consider a set of solutions . From the equilibrium condition of (16), the equal set must be restored by applying C-map and D-map to all the elements of the set. In other words, the condition is given by
| (18) |
Similarly, to obtain the equilibrium condition for (17), we should consider a set of solutions satisfying
| (19) |
Here, although the appearance of the variables are different, the problems are essentially between (18) and (19). Thus, the problem to be solved is
| (20) |
Furthermore, because , we can generalize the problem as
| (21) |
Now, for all and, let us consider a set satisfying
| (22) | ||||
| (23) | ||||
| (24) | ||||
| (25) |
(the proof for these equations will be given later). This set gives a solution to problem (21), and thus solves (16) and (17). In (22)-(25), we consistently label each such that sequentially applying C-map (resp. D-map) times leads to label (resp. ) (see the illustration in Fig. 1). In the following, we show that such actually exists for all .
1. When neither C-map nor D-map is constant: First, we consider a case of and . Four norms of correspond to this case. In this case, C-map and D-map have the same fixed point (at ). Only the position given by this fixed point is achieved at an equilibrium. Indeed, if we substitute for all , (22)-(25) are simultaneously satisfied without any contradiction.
2. When both C-map and D-map are constant: Second, we consider a case of and . Four norms of correspond to this case. Because is a constant map, (22) and (23) are satisfied by substituting the mapped value of this map into for all . In the same way, because is a constant map, (24) and (25) are satisfied by substituting the mapped value into for all . Thus, no contradiction occurs.
3. When only C-map is constant: Third, we consider a case of and . Four norms correspond to this case. Because is a constant map, (22) and (23) are satisfied by substituting the mapped value of this map into for all . Then, we define as the value to which D-map maps all the same value , and (24) is satisfied. Finally, we sequentially define by applying D-map to one by one. Thus, no contradiction occurs.
4. When only D-map is constant: Finally, we consider a case of and . Four norms correspond to this case. Because is a constant map, (24), (25) are satisfied by substituting the mapped value of this map into for all . Then, we define as the value to which D-map maps all the same value , and (24) is satisfied. Finally, we sequentially define by applying C-map to one by one. Thus, no contradiction occurs.
As summarized in Table 2, the set can be analytically described. Furthermore, we also define as the variance in Gaussian corresponding to the mean . Similarly to the mean values above, we solve the variances as
| (26) |
The recursion that the set should satisfy is
| (27) | ||||
| (28) | ||||
| (29) | ||||
| (30) |
and the solution exists for all (see Table. 2 for the solution of these equations). Table. 2 shows .
We also calculate a set of the masses of Gaussian functions, i.e., and . By substituting the values in Table 2 into (16), we obtain the following relational expressions
| (31) | |||
| (32) | |||
| (33) | |||
| (34) |
Similarly, by substituting the values in Table 2 into (17), we obtain
| (35) | |||
| (36) | |||
| (37) | |||
| (38) |
(31)-(38) includes the infinite summations. Because these infinite summation cannot be analytically calculated, one should set a cutoff of the summations in the numerical calculation of (31)-(38).
Fig. 2-B in the main manuscript shows an example of . In this example, the elements in are all different for different , and thus the labeling in this study is at least necessary for the description of the reputation structure. This figure also shows that the obtained analytical solutions well approximate simulations of the image matrix.
S3 Calculation of expected payoff
In order to consider an evolutionary process, we derive expected payoffs of wild-types and mutants from joint probability distribution of goodnesses, i.e., and . In the limit that mutants are rare , the expected payoffs of the wild-types and mutants are given by
| (39) |
Here, indicates the average goodnesses of , i.e., described as
| (40) |
This average goodness can be analytically calculated by Gaussian approximation of . According to the conditions for the ESS, mutants can invade the population of wild-types if .
Regions where a mutant norm can invade a wild-type norm are given by Fig. 2. From this figure, we can obtain the invasibilities for a certain , as shown in Fig. 3-A in the main manuscript.
S4 Calculation of equilibrium state in public reputation
In this section, we derive the equilibrium distribution of reputations under public assessment, based on the previous study [28]. The basic setting is the same whether the reputation is publicly shared or privately held. We assume a population of size which consists of mutants with norm and wild-type individuals with norm . A donor and a recipient are randomly chosen every round. The donor chooses cooperation to the good recipient and defection to the bad recipient. Here, the donor erroneously chooses the opposite action to the intended one with probability . Then, all the individuals update their reputations of the donor. The difference between the public and private reputation cases is seen in the observers’ ways to update reputations. We assume that one mutant observer and one wild-type observer are chosen as representatives of each norm, and each gives a good or bad reputation to the donor according to its norm. Here, each representative observer commits an assignment error independently, in which case it erroneously assigns the opposite reputation to the intended one with probability . (such an assessment error was not assumed in [28]) Then, all the individuals with the same norm copy the reputation of the donor assigned by their representative. Thus, the reputation of the same individual, even an erroneously assigned one, is shared among all the individuals with the same norm. In other words, each individual at any given time has two reputations, one is shared by all the mutant individuals, and the other is shared by all the wild-type individuals in the population.
Here we specifically consider the situation where rare mutants with norm (ALLB) invades a wild-type population with norm . We use the same definition of , i.e., goodness of an individual with norm in the eyes of norm users. Because reputations are public, can be either (the individual is assigned as good from all) or (the individual is assigned as bad from all). Below we will derive , the probability that a norm user has a good reputation in the eyes of norm users.
Since the mutant norm is ALLB, the probability that mutants assign a good reputation to the donor is always . Thus we obtain .
Next we aim to solve the equilibrium average goodnesses in the eyes of wild-types, and . First, let us calculate , which is relevant when the donor and the observer use norm . Note that we can assume that the recipient uses norm , because mutants are rare. should satisfy
| (41) |
The equality between the left- and right-hand sides shows that the proportion of good individuals balances before and after updating the chosen donor’s reputation. In the right-hand side, and in the first and the second terms indicate the probabilities that a randomly chosen recipient of norm is good or bad from the viewpoint of norm , respectively. When the recipient is good, the donor chooses cooperation or defection with probabilities and . Then, and indicate the probabilities that the cooperating or defecting donor receives a good reputation from observers of norm . When the recipient is bad, the donor chooses cooperation or defection with probabilities and . Then, and indicate the probabilities that the cooperating or defecting donor receives a good reputation from observers of norm . The solution is
| (42) |
Second, let us calculate , which is relevant when the donor uses norm and the observer uses norm . Note that we can once again assume that the recipient uses norm because mutants are rare. should satisfy
| (43) |
Here, and in the first and second terms of the right-hand side indicate the probabilities that the recipient is good or bad from the viewpoint of norm , respectively. In both terms, and are the probabilities that the donor with norm executes cooperation or defection, which is independent of whether the recipient is good or bad from the viewpoint of norm . In the first term, and indicate the probabilities that the cooperating and defecting donor receives a good reputation from the observers of norm . In the second term, and indicate the probabilities that the cooperating and defecting donor receives a good reputation from the observers of norm .
We summarize the solutions, and , in Table 3.
Based on Table 3, we can see how the reputation structure differs between the public and private reputation cases. The reputation structure for norms (SS) and (SJ) are illustrated in Fig. 3-D and E in the main manuscript, while that of (SH) is in Fig. 3.

S5 Numerical algorithm and error estimate
This section provides how to computationally calculate (31)-(34) and (35)-(38) with sufficient accuracy.
Instead of (31)-(34), we aim to compute
| (44) | |||
| (45) | |||
| (46) | |||
| (47) |
(see Fig. 4 for the illustration of this computation). Via these equations, we obtain by rescaling as
| (48) |
which satisfies (31)-(34). We should also obtain average goodnesses
| (49) |
in order to obtain Fig. 2.
In a practical computer simulation, we approximate (44)-(47) by
| (50) | |||
| (51) | |||
| (52) | |||
| (53) | |||
| (54) | |||
| (55) |
with sufficient large (see Fig. 4 for the illustration of this computation). We will show below that these computationally obtained well approximate . Note that in the following calculations we use the fact that
| (56) |
holds for all and .

From the definition, we obtain
| (57) |
Then, we obtain
| (58) | |||
| (59) |
Then, we have
| (60) | |||
| (61) | |||
| (62) |
We also obtain
| (63) | |||
| (64) | |||
| (65) |
From the above error estimations, we can obtain upper and lower bounds of (48) and (49) as
| (66) | |||
| (67) |
Here, we used
| (68) | ||||
| (69) | ||||
| (70) | ||||
| (71) | ||||
| (72) | ||||
| (73) | ||||
| (74) |
In the same way, let us consider (35)-(38) and compute
| (75) | |||
| (76) | |||
| (77) | |||
| (78) |
Via these equations, we obtain by rescaling as
| (79) |
which satisfies (35)-(38). We also need to obtain average goodnesses
| (80) |
in order to obtain Fig. 2.
In a practical computer simulation, we approximate (75)-(78) by
| (81) | |||
| (82) | |||
| (83) | |||
| (84) | |||
| (85) | |||
| (86) |
with sufficient large .
By exactly similar calculations, we obtain
| (87) | |||
| (88) | |||
| (89) | |||
| (90) |
The difference from exists only in , as
| (91) | ||||
| (92) |
(see the area surrounded by dots in Fig. 4 for the illustration of this computation).