Efficient Quantum Digital Signatures without Symmetrization Step
Abstract
Quantum digital signatures (QDS) exploit quantum laws to guarantee non-repudiation, unforgeability and transferability of messages with information-theoretic security. Current QDS protocols face two major restrictions, including the requirement of the symmetrization step with additional secure classical channels and quadratic scaling of the signature rate with the probability of detection events. Here, we present an efficient QDS protocol to overcome these issues by utilizing the classical post-processing operation called post-matching method. Our protocol does not need the symmetrization step, and the signature rate scales linearly with the probability of detection events. Simulation results show that the signature rate is three orders of magnitude higher than the original protocol in a 100-km-long fiber. This protocol is compatible with existing quantum communication infrastructure, therefore we anticipate that it will play a significant role in providing digital signatures with unconditional security.
I Introduction
Cryptography is essential for uncounted amount of applications that rely on non-repudiation, integrity and confidentiality of data. The two pillars of modern cryptography are encryption and digital signatures Diffie and Hellman (1976), where encryption guarantees confidentiality and digital signatures provide integrity and non-repudiation. Traditionally, public-key cryptography algorithms, such as the Rivest-Shamir-Adleman algorithm Rivest et al. (1978), are designed to simultaneously provide encryption and digital signature service. However, relying on the computational difficulty of certain mathematical problems, public-key cryptosystems are usually vulnerable to quantum computing attacks Shor (1994). Quantum key distribution (QKD) allows two remote users to share a secret key string with information-theoretic security Bennett and Brassard (1984); Ekert (1991). By combining one-time pad encryption Shannon (1949) and QKD, one can implement information communication with perfect confidentiality Chen et al. (2009). In addition, the direct transmission of private information is made possible in principle by quantum encryption Qi et al. (2019).
Digital signatures are widely applied in e-mails, electronic commerce and software distribution to ensure data integrity and non-repudiation Pirandola et al. (2020). Similar to QKD used for encryption service, quantum digital signatures (QDS) are expected to provide information-theoretic security to sign documents. The first QDS protocol was proposed in 2001 Gottesman and Chuang (2001), but it is unfeasible because of challenging experimental requirements. In the next decade or so, great efforts have been made in developing QDS protocols and an important achievement was the removal of the requirement of quantum memory Clarke et al. (2012); Dunjko et al. (2014); Collins et al. (2014); Wallden et al. (2015); Croal et al. (2016). Nevertheless, the security analysis of the early QDS protocols are based on secure quantum channels, i.e., there is no eavesdropping, which is a conflicting assumption. In 2016, two independent QDS protocols were proposed and proved to be secure against the general attacks without the assumption of secure quantum channels Yin et al. (2016a); Amiri et al. (2016). Importantly, their experimental devices and techniques have already been widely employed in QKD. These two protocols are important steps towards practical QDS Pirandola et al. (2020). The one in Yin et al. (2016a) is based on non-orthogonal encoding. The other Amiri et al. (2016) utilizes orthogonal encoding, which results in the need of an additional symmetrization step in the protocol. In addition, great achievements have been made in the experimental and theoretical research of information-theoretically secure QDS Puthoor et al. (2016); Yin et al. (2017a); Collins et al. (2017); Yin et al. (2017b); Roberts et al. (2017); Zhang et al. (2018); Thornton et al. (2019); An et al. (2019); Ding et al. (2020); Zhang et al. (2020); Wang et al. (2015, 2017), including the field test of measurement-device-independent (MDI) QDS Yin et al. (2017b).
For the orthogonal encoding based protocol Amiri et al. (2016) (see also Puthoor et al. (2016); Zhang et al. (2020)), the need of the symmetrization step, which requires an additional secure classical channel, is the main issue. Currently, secure classical channels can only be realized by combining QKD and one-time pad encryption. The symmetrization step will consume bits of secret key generated by QKD if one uses bits as the signature Yin et al. (2017b). Specially, in the worst case where the signer is located in the middle of two receivers, the low secret key rate of QKD between the two receivers severely limits the real-time signature rate of QDS. Besides, considering a quantum network with users, there will be a need of secure classical channels Roberts et al. (2017), which is an unrealistically high amount in a real quantum network. For the non-orthogonal encoding based protocol Yin et al. (2016a), it does not require the symmetrization step. However, the signer has to send the same quantum states to two receivers. Only coincidence detection events, i.e., the two receivers both have click, are valid events. Let be the probability that one receiver has click, if the signer sends quantum states to the two receivers, there will be only valid events. Therefore, the signature rate quadratically scales with the probability of detection events.
Here, inspired by the original protocol in Yin et al. (2016a), we propose an efficient quantum digital signature protocol without symmetrization step. A novel classical post-processing operation called post-matching method is exploited in our protocol. With the help of the post-matching method, the requirement of coincidence detection is removed. Given that the signer sends quantum states to receivers, there will be valid events. Therefore the signature rate decays linearly with the probability of detection events. Simulation results show that the signature rate of our scheme is or even orders of magnitude higher than that of Ref. Yin et al. (2016a) in large attenuation case, and is comparable to orthogonal encoding based protocol.
II Protocol Description
There are three participants in our protocol, namely the signer Alice and the receiver Bob and Charlie. As determined by Alice, either Bob or Charlie can be the authenticator of the signature, and the other becomes the verifier. There are noisy insecure quantum channels connecting Alice-Bob and Alice-Charlie, and authenticated classical channels between the three participants. There are three stages in our protocol: key generation, estimation and messaging. In our protocol, the three stages can be performed separately, which means they can generate raw keys and store them for a long time, and continue the estimation and messaging stage whenever Alice wants to sign the message. This makes our protocol more practical.
Our protocol exploits non-orthogonal encoding to generate logical bits Scarani et al. (2004). There are four quantum states: , , and , where and are the eigenstates of the Pauli Z operator and and ( ) are the eigenstates of the Pauli X operator. These four quantum states can be arranged into four sets: , , , , where the first state in each set is encoded with bit value 0 and the second is encoded with 1. Alice randomly sends quantum states to receivers and assigns each quantum state to a set. The receivers randomly choose Z or X basis to perform polarization measurement on each quantum state. If the measurement outcome is orthogonal to one of the states in the set, the receiver obtains a conclusive result with bit value 0 or 1, otherwise the receiver obtains an inconclusive result, denoted by . Note that the set assigned by Alice should contain the quantum state she sent. For example, if Alice sends , she should assign it to set or . When she assigns it to the set and Bob’s measurement outcome is (), Bob obtains a conclusive result with bit value .
The decoy-state method Wang (2005); Lo et al. (2005) with three intensities is exploited to deal with photon-number-splitting attack for coherent state source. Data from the decoy state and vacuum state will be used for parameter estimation, and only data from the signal state will be used as test bits and secret keys. The setup for our QDS protocol is presented in Fig. 1. In the following part of the paper, we use superscripts , , , , overline (underline), to denote conclusive results, untest bits, test bits, expected value and the upper bound (lower bound) of expected value, respectively. We also use subscripts (), and () to denote Alice (Bob, Charlie), single-photon pair components and intensity respectively. Detailed descriptions of our protocol are given below.
1. Key generation. (1) Alice randomly selects a quantum state with the same possibility and an intensity (signal, decoy and vacuum state) with possibilities , and respectively. For each possible message ( or ), Alice prepares two different quantum state sequences with length , namely , and . Alice sends to Bob and to Charlie through insecure quantum channels.

(2) For each quantum state, Bob and Charlie randomly choose X or Z basis to perform polarization measurement. Bob announces all the click events in through authenticated classical channel. Alice and Bob discard all the data that has no click. They keep the left data of length , denote as (kept by Alice) and (kept by Bob). Alice and Charlie perform the same step. As a result, Alice has four data strings , , and , Bob (Charlie) has two strings () and (). Since Alice randomly and independently chooses quantum states, the quantum states that Bob and Charlie receive are uncorrelated.
(3) Alice announces the intensity information of all pulses. According to the intensity information, the three participants divide each of their data strings into three strings, namely string, string and string. For example, Bob divides into , and .
(4) For the data strings corresponding to each intensity (), Alice takes as the reference and changes the order of elements in . Denote the changing result as , Alice should make and identical. Without loss of generality, she requests Charlie to change the order of elements in into the same order. We call this the post-matching method. After post-matching, the data obtained by Bob and Charlie can be correlated. Detailed description of post-matching method is given in Fig. 2.
(5) Using the rules for generating logical bits, Alice randomly assigns each element in a set. The three participants ‘translate’ their data strings into raw key strings denoted as , and . Note that they do not announce which bits are conclusive results.

2. Estimation. (1) The signer Alice chooses the desired authenticator of the signature, and the other participant automatically becomes the verifier. Here we assume Bob is the authenticator. The three participants publicly announce all data of strings and strings and the value of (the length of string). They estimate bit error rate of single-photon pair components in strings using decoy state method. The verifier Charlie randomly selects a proportion of in the string as test bits and asks Alice to publicly announce the value of these bits. We denote test bit strings as , and . Let () be the mismatch rate of conclusive results between and ( and ). Bob and Charlie calculate and . Note that when or gets too high, the signing process of this round is highly possible to fail. In this case they abort the protocol. In addition, Bob and Charlie calculate the proportion of conclusive results in and , denoted as and , respectively. If or shows a big deviation from the ideal value , they will also abort the protocol. The three participants discard the test bits and keep the remaining untest bits in strings with length . We denote these untest bit strings as , and . They will be used as secret keys to sign the message in the messaging stage.
(2) Bob and Charlie announce , and , . The three participants publicly negotiate to determine the values of authentication security threshold and verification security threshold .
3. Messaging. (1) To sign a one-bit message , Alice sends the message and the corresponding secret key to the authenticator Bob. Bob calculates the mismatch rate of conclusive results between and , which is denoted as . If , Bob accepts the message and forwards to Charlie, otherwise he rejects the message and announces to abort the protocol.
(2) After receiving forwarded by Bob, Charlie calculates the mismatch rate of conclusive results between and . Charlie accepts the message if . When both Bob and Charlie accept the message, Alice successfully signs the message.
III Security Analysis
In our protocol, Alice randomly chooses unrelated quantum states to send to Bob and Charlie. After post-matching, it is equivalent to Alice simultaneously sending the same quantum states to Bob and Charlie. To perform post-matching, Alice exposes information of order, but does not leak information of quantum states. In this case, eavesdroppers can not obtain more information of quantum states compared with the case where Alice actually sends two copies of quantum states. Thus the security analysis of our protocol can directly follow the lines in Ref. Yin et al. (2016a). In the three-participant scenario, transferability and nonrepudiation are equivalent. Accordingly, there are three security criteria: robustness, security against forging and security against repudiation. For simplicity, we just briefly present our results. For more detail, refer to Ref. Yin et al. (2016a).
1. Robustness. The robustness means the probability of an honest abort . In messaging stage, Bob rejects the message sent by Alice when . In the case of finite sample size, the robustness can be quantified by exploiting random sampling without replacement theorem Yin et al. (2020).
2. Security against forging. In a forgery attack, Bob sends the message he wishes to forge and its corresponding secret key to Charlie. The forgery attack is successful if Charlie accepts Bob’s forged message. An honest Bob knows only about of conclusive results in . If Bob is an adversary, his optimal strategy is to acquire information of quantum states Charlie receives as much as possible, which is equivalent to the eavesdropping attack of Eve in four-state Scarani-Acin-Ribordy-Gisin 2004 (SARG04) QKD with two-photon source Scarani et al. (2004); Tamaki and Lo (2006); Yin et al. (2016b).
We assume only single-photon pairs that Alice sends to Bob and Charlie are secure. In this case, Bob and Charlie both receive a single-photon. Using Chernoff bound Chernoff (1952), the probability of a successful forgery attack can be given by
| (1) |
where is the expected value of minimum mismatch rate of conclusive results of the single-photon pair components between and , is the error rate threshold of single-photon pair, is the number of conclusive results in , is the number of single-photon pair components in and is the number of events in which Bob and Charlie both receive a single-photon in string and Charlie has a conclusive result.
To obtain the value of , one should exploit decoy state method to estimate and , where is the number of events that Bob and Charlie both receive a single-photon in string, Charlie has a conclusive result, and his classical bit is mismatching with Alice’s. We use to denote the number of detection events of the participant of intensity and to denote the number of mismatching bits. The expected value of parameter can be acquired by the variant of Chernoff bound Yin et al. (2020): and with , where is the failure probability of the Chernoff bound.
Separately consider the process that Alice sends pulses to Bob and to Charlie, we have
| (2) |
and
| (3) |
where is the number of single-photon events in Bob’s string and is is the number of conclusive single-photon events in Charlie’s string. can be given by
| (4) |
| (5) |
We also have
| (6) |
and
| (7) |
where is the number of single-photon errors of Charlie’s conclusive results in string with respect to Alice. can be given by:
| (8) |
Bring in Eqs. (6) (7), we have
| (9) |
3. Security against repudiation. Alice successfully repudiates the message when Bob accepts the message while Charlie rejects it, i.e., and . Alice does not know which bits are conclusive results for Bob (Charlie) and has to treat each bit in and with the same status. For Bob and Charlie, the difference between and can be restricted by inequalities of the relative Hamming distance. The upper bound of the relative Hamming distance between and (denoted by ) can be given by using the random sampling without replacement theorem Yin et al. (2020). The probability of successful repudiation can be given by
| (10) |
where is the solution of the following equation and inequalities:
| (11) |
with .
The overall secrecy is:
| (12) |
where is the failure probability of random sampling without replacement.
IV Performance
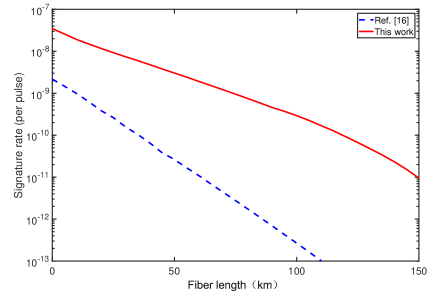
In order to show the performance of our protocol, we simulate a fiber-based QDS system. Define signature rate , where is the minimum number of pulses required to securely sign a one-bit message. Fig. 3 shows the signature rate as a function of transmission distance. We consider the case where channels between Alice-Bob and Alice-Charlie are symmetric.
The security bounds are set to , , and . We numerically optimize the minimum number of pulses required to securely sign a one-bit message with the free parameters by global search algorithm. For a fair comparison, we simulate the performance of the original protocol in Ref. Yin et al. (2016a) with the same experimental parameters. As shown in Fig. 3, the solid red line represents the signature rate of this work and the blue dashed line represents the original QDS protocol. Obviously, our protocol requires far less number of pulses to sign a one-bit message. Specifically, at km and km, our protocol requires and pulses to sign a one-bit message, but the protocol in Ref. Yin et al. (2016a) requires and pulses. The signature rate of our protocol is 2 or even 3 orders of magnitude higher than the original protocol at long distance.

We also simulate the performance of orthogonal encoding based protocol Amiri et al. (2016) with the cost of symmetrization taken into consideration. Assume Bob and Charlie utilize three-intensity decoy-state BB84 QKD protocol to perform symmetrization. Define the effective signature rate , where is the length of key generated by key generation protocol in [17] and is the secret key rate of QKD. Note that is the number of pulses required for QKD to perform symmetrization Yin et al. (2017b). is simulated by the key rate formula in Lim et al. (2014), where we choose error-correction efficiency , data post-processing block size , secrecy and the same experimental parameters as Fig. 3.
Denote the angle between Alice-Bob and Alice-Charlie as , the distance between Alice and Bob (Charlie) as (), and the distance between Bob and Charlie as . In symmetric case, , and . At short distance where is very high, is mainly determined by . When is close to , the transmission distance of QKD () increases much faster than . In this case, is determined by at long distance. We simulate the case of and . As shown in Fig. 4, the signature rate of Amiri et al. (2016) is higher than that of our protocol at short distance, but when distance between the two receivers is large, the signature rate will be severely limited by the low secret key rate of QKD in the symmetrization step. By contrast, our protocol decays much slower and has a significantly longer transmission distance.
In addition, the typical experimental parameters and corresponding signature rate of some recent QDS experiments are listed in Table. 1. This work shows a comparable performance with orthogonal encoding based protocol An et al. (2019) even though the latter does not execute the symmetrization step. We remark that the symmetrization step is essential to the complete protocol, as demonstrated in experiments Roberts et al. (2017); Yin et al. (2017b).
| Ref. Yin et al. (2017a) | Ref. Yin et al. (2017b) | Ref. Roberts et al. (2017) | Ref. Ding et al. (2020) | Ref. An et al. (2019) | This work | |
| Protocol | SARG04 | MDI | MDI | BB84 | BB84 | SARG04 |
| Repetition rate | 75MHz | 75MHz | 1GHz | 50MHz | 1GHz | 1GHz |
| Transmission distance | 102 km | 55.6 km | 50 km | 280 km | 125 km | 125 km |
| Security parameter | ||||||
| Signature time per bit (s) | 66840 | 149987 | 45 | 21407 | 22.7 | 14.9 |
| Symmetrization step | No need | Yes | Yes | Non-execution | Non-execution | No need |
V Conclusion
In this paper, we have proposed a non-orthogonal encoding based efficient quantum digital signature protocol. A novel method called post-matching is applied, which can increase the signature rate from decaying with to . Our protocol has a high signature rate and does not require the symmetrization operation thereby overcomes the major obstacles of existing QDS protocols. This protocol can be directly implemented with current commercially available QKD devices. Therefore, it should be the preferred solution to the application of QDS. This work is a great step for the development of quantum network with QDS. Moreover, we believe the key idea of post-matching method has the potential to be applied in various cryptographic tasks that require to establish multiparty correlations, such as multiparty quantum communication Fu et al. (2015).
Funding
National Natural Science Foundation of China (61801420); Key Research and Development Program of Guangdong Province (2020B0303040001); Fundamental Research Funds for the Central Universities.
References
- Diffie and Hellman (1976) W. Diffie and M. Hellman, IEEE Trans. Inf. Theory 22, 644 (1976).
- Rivest et al. (1978) R. L. Rivest, A. Shamir, and L. Adleman, Commun. ACM 21, 120 (1978).
- Shor (1994) P. W. Shor, in Proceedings 35th Annual Symposium on Foundations of Computer Science (IEEE, 1994) pp. 124–134.
- Bennett and Brassard (1984) C. H. Bennett and G. Brassard, in Proceedings of the Conference on Computers, Systems and Signal Processing (IEEE Press, 1984) pp. 175–179.
- Ekert (1991) A. K. Ekert, Phys. Rev. Lett. 67, 661 (1991).
- Shannon (1949) C. E. Shannon, Bell Syst. Tech. J. 28, 656 (1949).
- Chen et al. (2009) T.-Y. Chen, H. Liang, Y. Liu, W.-Q. Cai, L. Ju, W.-Y. Liu, J. Wang, H. Yin, K. Chen, Z.-B. Chen, C.-Z. Peng, and J.-W. Pan, Opt. Express 17, 6540 (2009).
- Qi et al. (2019) R. Qi, Z. Sun, Z. Lin, P. Niu, W. Hao, L. Song, Q. Huang, J. Gao, L. Yin, and G.-L. Long, Light Sci. Appl. 8, 22 (2019).
- Pirandola et al. (2020) S. Pirandola, U. L. Andersen, L. Banchi, M. Berta, D. Bunandar, R. Colbeck, D. Englund, T. Gehring, C. Lupo, C. Ottaviani, J. L. Pereira, M. Razavi, J. S. Shaari, M. Tomamichel, V. C. Usenko, G. Vallone, P. Villoresi, and P. Wallden, Adv. Opt. Photon. 12, 1012 (2020).
- Gottesman and Chuang (2001) D. Gottesman and I. Chuang, arXiv preprint quant-ph/0105032 (2001).
- Clarke et al. (2012) P. J. Clarke, R. J. Collins, V. Dunjko, E. Andersson, J. Jeffers, and G. S. Buller, Nat. Commun. 3, 1174 (2012).
- Dunjko et al. (2014) V. Dunjko, P. Wallden, and E. Andersson, Phys. Rev. Lett. 112, 040502 (2014).
- Collins et al. (2014) R. J. Collins, R. J. Donaldson, V. Dunjko, P. Wallden, P. J. Clarke, E. Andersson, J. Jeffers, and G. S. Buller, Phys. Rev. Lett. 113, 040502 (2014).
- Wallden et al. (2015) P. Wallden, V. Dunjko, A. Kent, and E. Andersson, Phys. Rev. A 91, 042304 (2015).
- Croal et al. (2016) C. Croal, C. Peuntinger, B. Heim, I. Khan, C. Marquardt, G. Leuchs, P. Wallden, E. Andersson, and N. Korolkova, Phys. Rev. Lett. 117, 100503 (2016).
- Yin et al. (2016a) H.-L. Yin, Y. Fu, and Z.-B. Chen, Phys. Rev. A 93, 032316 (2016a).
- Amiri et al. (2016) R. Amiri, P. Wallden, A. Kent, and E. Andersson, Phys. Rev. A 93, 032325 (2016).
- Puthoor et al. (2016) I. V. Puthoor, R. Amiri, P. Wallden, M. Curty, and E. Andersson, Phys. Rev. A 94, 022328 (2016).
- Yin et al. (2017a) H.-L. Yin, Y. Fu, H. Liu, Q.-J. Tang, J. Wang, L.-X. You, W.-J. Zhang, S.-J. Chen, Z. Wang, Q. Zhang, T.-Y. Chen, Z.-B. Chen, and J.-W. Pan, Phys. Rev. A 95, 032334 (2017a).
- Collins et al. (2017) R. J. Collins, R. Amiri, M. Fujiwara, T. Honjo, K. Shimizu, K. Tamaki, M. Takeoka, M. Sasaki, E. Andersson, and G. S. Buller, Sci. Rep. 7, 3235 (2017).
- Yin et al. (2017b) H.-L. Yin, W.-L. Wang, Y.-L. Tang, Q. Zhao, H. Liu, X.-X. Sun, W.-J. Zhang, H. Li, I. V. Puthoor, L.-X. You, E. Andersson, W. Zhen, Y. Liu, X. Jiang, X.-F. Ma, Q. Zhang, C. Marcos, T.-Y. Chen, and J.-W. Pan, Phys. Rev. A 95, 042338 (2017b).
- Roberts et al. (2017) G. Roberts, M. Lucamarini, Z. Yuan, J. Dynes, L. Comandar, A. Sharpe, A. Shields, M. Curty, I. Puthoor, and E. Andersson, Nat. Commun. 8, 1098 (2017).
- Zhang et al. (2018) C.-H. Zhang, X.-Y. Zhou, H.-J. Ding, C.-M. Zhang, G.-C. Guo, and Q. Wang, Phys. Rev. Appl. 10, 034033 (2018).
- Thornton et al. (2019) M. Thornton, H. Scott, C. Croal, and N. Korolkova, Phys. Rev. A 99, 032341 (2019).
- An et al. (2019) X.-B. An, H. Zhang, C.-M. Zhang, W. Chen, S. Wang, Z.-Q. Yin, Q. Wang, D.-Y. He, P.-L. Hao, S.-F. Liu, X.-Y. Zhou, G.-C. Guo, and Z.-F. Han, Opt. Lett. 44, 139 (2019).
- Ding et al. (2020) H.-J. Ding, J.-J. Chen, L. Ji, X.-Y. Zhou, C.-H. Zhang, C.-M. Zhang, and Q. Wang, Opt. Lett. 45, 1711 (2020).
- Zhang et al. (2020) C.-H. Zhang, Y.-T. Fan, C.-M. Zhang, G.-C. Guo, and Q. Wang, arXiv preprint arXiv:2003.11262 (2020).
- Wang et al. (2015) T.-Y. Wang, X.-Q. Cai, Y.-L. Ren, and R.-L. Zhang, Sci. Rep. 5, 9231 (2015).
- Wang et al. (2017) T.-Y. Wang, J.-F. Ma, and X.-Q. Cai, Quantum Information Processing 16, 19 (2017).
- Scarani et al. (2004) V. Scarani, A. Acin, G. Ribordy, and N. Gisin, Phys. Rev. Lett. 92, 057901 (2004).
- Wang (2005) X.-B. Wang, Phys. Rev. Lett. 94, 230503 (2005).
- Lo et al. (2005) H.-K. Lo, X. Ma, and K. Chen, Phys. Rev. Lett. 94, 230504 (2005).
- Yin et al. (2020) H.-L. Yin, M.-G. Zhou, J. Gu, Y.-M. Xie, Y.-S. Lu, and Z.-B. Chen, Sci. Rep. 10, 14312 (2020).
- Tamaki and Lo (2006) K. Tamaki and H.-K. Lo, Phys. Rev. A 73, 010302 (2006).
- Yin et al. (2016b) H.-L. Yin, Y. Fu, Y. Mao, and Z.-B. Chen, Sci. Rep. 6, 29482 (2016b).
- Chernoff (1952) H. Chernoff, Ann. Math. Stat. 23, 493 (1952).
- Lim et al. (2014) C. C. W. Lim, M. Curty, N. Walenta, F. Xu, and H. Zbinden, Phys. Rev. A 89, 022307 (2014).
- Fu et al. (2015) Y. Fu, H.-L. Yin, T.-Y. Chen, and Z.-B. Chen, Phys. Rev. Lett. 114, 090501 (2015).