Contract-based Scheduling of URLLC Packets in Incumbent EMBB Traffic
Abstract
Recently, the coexistence of ultra-reliable and low-latency communication (URLLC) and enhanced mobile broadband (eMBB) services on the same licensed spectrum has gained a lot of attention from both academia and industry. However, the coexistence of these services is not trivial due to the diverse multiple access protocols, contrasting frame distributions in the existing network, and the distinct quality of service requirements posed by these services. Therefore, such coexistence drives towards a challenging resource scheduling problem. To address this problem, in this paper, we first investigate the possibilities of scheduling URLLC packets in incumbent eMBB traffic. In this regard, we formulate an optimization problem for coexistence by dynamically adopting a superposition or puncturing scheme. In particular, the aim is to provide spectrum access to the URLLC users while reducing the intervention on incumbent eMBB users. Next, we apply the one-to-one matching game to find stable URLLC-eMBB pairs that can coexist on the same spectrum. Then, we apply the contract theory framework to design contracts for URLLC users to adopt the superposition scheme. Simulation results reveal that the proposed contract-based scheduling scheme achieves up to 63% of the eMBB rate for the ”No URLLC” case compared to the ”Puncturing” scheme.
Index Terms:
Contract theory, enhance mobile broadband (eMBB), fifth-generation new radio, matching theory, scheduling, ultra-reliable and low-latency communication (URLLC).I Introduction
As a result of rapid technological developments in the recent years, there has been a growing interest in tactile internet applications such as industrial automation, autonomous vehicles, massive IoT connectivity, and digital entertainment expansion. These novel applications have very stringent and diverse communication requirements such as coverage, data rate, latency and reliability. To meet these diverse communication requirements of diverse applications, the International Telecommunication Union (ITU) has classified fifth-generation new-radio (5G NR) services into three categories: ultra-reliable and low-latency communication (URLLC), enhanced mobile broadband (eMBB), and massive machine type communication (mMTC) [1]. Among these services, URLLC is designed for the event-driven, mission-critical, and industrial scenarios, in which it can contribute to meet the quality-of-service (QoS) requirements such as ultra-low latency and ultra-high reliability. Furthermore, the standard URLLC imposes strict latency and reliability requirements, typically of 1 ms/packet and up to 99.999% successful packet delivery, respectively [2, 3].
Since both the eMBB and URLLC are essential components of communication traffic in 5G cellular networks, various studies have addressed the coexistence issue of these services [4]. From the perspective of network throughput, the eMBB generates an enormous amount of data communication traffic over cellular networks. Unlike the eMBB, URLLC produces less data as it has stringent latency and reliability requirements. Therefore, the coexistence of these two services involves the challenge of achieving sufficient eMBB throughput while satisfying URLLC requirements [5]. Due to the time-sensitivity of mission-critical applications, such as UAV automation, autonomous vehicular control, and critical medical apparatus management, URLLC is prioritized over eMBB for scheduling. In general, eMBB scheduling involves the enhancement of network throughput to improve spectral efficiency while the reliability of packet delivery is ensured through re-transmissions. However, eMBB scheduling approaches may not ensure the reliability and latency thresholds required for URLLC, and thus cannot be applied in URLLC scheduling. On the contrary, URLLC involves the transmission of short packets within certain latency and reliability bounds.
One well-thought way to handle the aforementioned constraints is using re-transmissions approach. However, it is impractical to simultaneously satisfy the contradicting requirements of latency and reliability in URLLC only through re-transmissions approach. For instance, a greater number of transmissions ensures reliability while compromising latency, and vice versa. To address this challenge, small-packet communication has been proposed for URLLC, as it can meet the reliability requirements at the cost of reduced spectrum efficiency due to additional control overhead. However, it does not suffice as an efficient scheduling scheme is further required for the coexistence of URLLC and eMBB services such that the penalization of the eMBB traffic is minimized [6].
In this regard, conventional scheduling schemes based on orthogonal channel allocation are proven to be inefficient and underutilized when applied to the coexistence scenarios of URLLC and eMBB networks. In fact, the third generation partnership project (3GPP) suggested a short and long transmission time interval (TTI)-based frame distribution for these coexistence scenarios. In this frame distribution, eMBB traffic is scheduled for a long TTI and URLLC is opportunistically scheduled for a short TTI over the existing eMBB traffic by adopting a puncturing or superposition scheme [7]. The puncturing scheme involves the scheduling of URLLC packets by halting the eMBB communication during the URLLC transmission for the duration of a short TTI. Note that the puncturing scheme can significantly reduce the throughput of eMBB users. Thus, to compensate for this loss, the superposition scheme is proposed that involves the non-orthogonal scheduling of both eMBB and URLLC traffic on the single channel simultaneously. This is achieved by exploiting the non-orthogonal multiple access (NOMA) scheme, in which the difference between the channel gains of the cellular users is exploited to pack the coexisting users on a single channel resource [8, 9].
I-A Contribution
In this study, we propose an efficient scheduling scheme for the coexistence of eMBB and URLLC by dynamically adopting puncturing or superposition schemes. For this purpose, we consider a cellular network in which many URLLC and eMBB users are associated with a base-station (BS). The BS performs eMBB scheduling at the start of a long TTI, and URLLC scheduling is performed for a short TTI using the puncturing or superposition scheme. To meet the latency requirements of URLLC users, their scheduling is performed in the same or next URLLC TTI of the scheduling request. Moreover, the reliability requirement is met by either using the puncturing or the superposition scheme to ensure certain channel quality. To perform the pairing between URLLC and eMBB users, we apply a one-to-one matching scheme that is based on the preference profiles of the eMBB and URLLC users. The BS attempts to enhance the eMBB throughput by reducing the effects of URLLC scheduling, which is achieved by selecting the superposition scheme. To encourage URLLC users to opt for the superposition scheme, we propose a contract-based incentive mechanism that involves sharing the payoff received by the BS for applying the superposition scheme with the contributing URLLC users. In addition, the URLLC users prefer opting for the superposition scheme unless their QoS requirements are satisfied; otherwise, they select the puncturing scheme.
In the case of the proposed contract-based incentive mechanism, superposition is well-suited for both URLLC and eMBB users. However, in some cases, both type of the users experience similar channel gains that makes the adoption of the superposition scheme infeasible. In these cases, the puncturing scheme is essential. Therefore, we propose applying the puncturing or superposition scheme based on network and channel conditions. For this purpose, we use the contract theory framework [10] to design a bundle of contracts by the BS for URLLC users. Contract theory is useful because the BS cannot reveal complete information (i.e., channel gain, willingness for superposition, and the matching with a particular eMBB user) from URLLC users in a timely manner due to the strict latency requirements. As a result, an asymmetric information problem arises due to the lack of complete information that is solved by using contract theory [11]. Note that the pairing of eMBB and URLLC users before designing the contracts using the one-to-one matching is essential for better spectrum efficiency. In case of not using the matching pairs, it is possible to select the pairs which may not coexist on a single channel.
The main contributions of this paper are summarized as follows:
-
•
We model the problem of URLLC and eMBB coexistence, in which eMBB users are modeled using the Shannon rate, and finite block length codes are used to model the rates for URLLC users. In addition, we model the superposition and puncturing framework for the coexistence of URLLC and eMBB users on the same channels.
-
•
For URLLC scheduling, we formulate the optimization problem to maximize the eMBB rate under the URLLC QoS requirements of latency and reliability to optimize the puncturing or superposition scheme and URLLC power allocation.
-
•
To solve the formulated problem, we first pair each URLLC user with a suitable eMBB user. This pairing is performed by applying the one-to-one matching considering the preference profiles of both participants.
-
•
Based on the pairing, appropriate contracts are designed for each URLLC type. The URLLC type refers to the classification of URLLC users for the adoption of superposition scheme. After verifying the feasibility and optimality of the contracts, power allocation to the URLLC users is performed according to their utility constraints. Furthermore, we formulate a convex problem that maximizes the BS profit by optimizing the power allocation.
-
•
Numerical results validate the performance of the proposed contract-based scheme. The results demonstrate that the proposed contract-based superposition scheme achieves up to 63% of the eMBB rate for the non-URLLC case compared to the puncturing scheme.
The remainder of this paper is organized as follows. The related work is summarized in Section II. The system model is presented in Section III. Subsequently, in Section III-B, the problem is formulated to maximize the eMBB rate subject to URLLC requirements. In Section IV, after performing the one-to-one matching, a contract design for URLLC users is presented which is used for the resource allocation to the URLLC users. Finally, numerical results and conclusions are provided in Sections V and VI, respectively.
II Related Works
In this section, we discuss some of the significant related works and challenges, which are grouped into three categories: (a) 5G-NR, (b) contract theory, and (c) matching theory.
II-A 5G-NR
Recently, numerous puncturing-based scheduling schemes have been proposed in the literature. For instance, the authors in [12] utilized puncturing and superposition schemes to schedule URLLC traffic over pre-scheduled eMBB communication. However, the authors did not consider the reliability constraints of URLLC communication. A statistical analysis of URLLC communication over a wireless channel was performed in [13]. The authors proposed a method of selecting a transmission rate according to the channel conditions and reliability requirements. In [14], the authors considered a CRAN environment where the decoding of eMBB traffic was performed on the cloud while URLLC decoding was performed by edge nodes to meet the latency requirements. In [15], the authors solved the URLLC resource allocation problem in the short blocklength regime. However, the global optimal solution was identified in the subset of the feasible region only. The authors demonstrated the insignificance of power control for small URLLC packets. In [16], the authors proposed URLLC packet transmission among device-to-device (D2D) users, in which the D2D pairs communicated opportunistically for short packets. However, the authors did not consider the reliability requirements in their formulation. In [17], machine learning based adaptive TTI interval is proposed for the scheduling in eMBB and URLLC coexistence networks.
The problem of ensuring ultra-low latency and ultra-reliability has been addressed in the literature. For instance, backbone network latency can be improved using a dedicated link for URLLC communication. Similarly, fronthaul latency reduction is possible by reducing the transmission overhead. Furthermore, the control signaling mechanism can be improved to eliminate the signaling latency in the LTE systems [18]. In [19], the authors proposed a risk-sensitive based formulation for the coexistence problem of eMBB and URLLC traffics that aims at maximizing the eMBB data rate while considering the URLLC reliability. In [20], the authors proposed a scheduling scheme for the URLLC downlink traffic. The main cause of reliability losses in current LTE systems is erroneous channel estimation. Therefore, URLLC reliability can be increased by the improving channel estimation, which can be achieved by improving the control signaling mechanism. As mentioned earlier, one solution to the problem of simultaneously meeting reliability and latency requirements involves reducing the packet size in URLLC, which results in meeting the reliability constraints for a given latency at the cost of low achievable rates. Furthermore, spatial diversity can be used to achieve an improved URLLC reliability i.e., using multiple transmitters for sending duplicate URLLC packets. In this way, the required reliability can be achieved at the cost of spectrum efficiency [21].
II-B Contract Theory
Contract theory has been widely used in various wireless communication schemes for situations involving information asymmetry, as well as to encourage agents to contribute to tasks assigned by the principal [22]. For instance, the study conducted in [23] proposed an incentive mechanism to encourage D2D users to share content. Similarly, in a cloud radio access network, contract theory was used to motivate the content providers to rent the cache to the network operator [24]. In addition, the use of contract theory for the case of incomplete information was exploited in [25]. In [26], the authors addressed the problem of secure data sharing in the Internet of Vehicles by leveraging blockchain. Moreover, to address the problem of minor selection, the authors applied contract theory. In [27], the authors proposed task offloading from the BS to nearby underutilized vehicular fog nodes. They proposed a contract-matching based incentive and task assignment scheme. In [28], the contract theory was used to model communication among D2D users. A multi-principal multi-agent problem was mapped to the D2D communication problem. The aforementioned works thus indicate the utility of using contract theory in real-world problems.
II-C Matching Theory
In economics, a Nobel prize-winning mathematical framework called matching theory has been developed that is applied in the formation of collectively valuable groups among participants. Recently matching theory has been extensively used for efficient resource management in wireless networks [29]. For instance, the authors of [30] used matching theory to associate users for task offloading in mobile edge computing (MEC). Similarly, the problem of user association and resource allocation in a fog network was solved using matching theory for the two-way association between fog nodes and (IoT) users [4]. Furthermore, a matching-based D2D resource allocation with interference management was proposed in [31]. The aforementioned research that demonstrates the significance and contribution of matching-based approaches in wireless networks.
To the best of our knowledge, the present study is the first to employ contract theory to address the problem of coexistence of URLLC and eMBB users in cellular networks.
III System Model and Problem Formulation

In the system model, we consider a downlink radio access network (RAN) consisting of a set of BSs denoted by , each connected to the core network through backhaul links. Each BS is associated with the corresponding sets of URLLC and eMBB users denoted by and , respectively as shown in Figure 1. The eMBB users are scheduled according to the standard LTE scheduling while URLLC communication is overlaid on the pre-scheduled eMBB traffic. Specifically, both eMBB and URLLC networks coexist to share the same spectral resources consisting of a set of resource blocks (RBs) denoted by . In order to enable coexistence, either the puncturing scheme or the superposition scheme can be used. Figure 2 demonstrates the frame structure for eMBB and URLLC scheduling through both the aforementioned schemes. Each eMBB user is assigned a timeslot of duration ms and bandwidth of an RB . We assume eMBB users are pre-scheduled and each eMBB user experiences a level of signal-to-interference-plus-noise ratio (SINR) that is known to the BS. The arrival of a URLLC transmission request is modeled as a Poisson distribution with an arrival rate of . In each mini-slot of duration ms, there is a random arrival of URLLC users that are scheduled over the incumbent eMBB allocation using the puncturing or superposition scheme.

III-A Wireless Model
In our model, we assume a saturated network scenario in which eMBB users always have packets to transmit and the number of eMBB users are more than the available BS resources. Then, the BS assigns its resources to a set of optimal eMBB users for downlink communication. On the other hand, with respect to the URLLC traffic, we model the arrival of a URLLC request using Poisson distribution [32].
III-A1 eMBB traffic
In wireless networks, we have orthogonal and non-orthogonal channel access schemes. In the scenarios of URLLC and eMBB coexistence, the orthogonal channel access scheme corresponds to the puncturing scheme and non-orthogonal channel access scheme corresponds to superposition scheme, respectively. Upon the arrival of URLLC requests, appropriate mini-slots are allocated to URLLC users according to two schemes: 1) puncturing scheme, in which eMBB transmission is stopped to schedule a URLLC user, and 2) superposition scheme, in which both eMBB and URLLC can operate in the same mini-slot while utilizing the successive interference cancellation (SIC) technique. Under the superposition scheme, the SINR at the eMBB user from the BS is defined as:
| (1) |
where and are the transmit power and channel gain, respectively, from the BS to the eMBB user . denote the received interference from the coexisting URLLC users and denote the noise level. Similarly, the SINR for the puncturing scheme denoted by from the BS to the eMBB user is expressed as follows:
| (2) |
| (3) |
where denotes the bandwidth of RB, and denotes the corresponding SINR for the superposition or puncturing case. The total eMBB rate using superposition and puncturing scheme is expressed as .
III-A2 URLLC traffic
The traditional Shannon capacity rates cannot be used due to small packet size in URLLC traffic [15]. Therefore, we use the finite blocklength to define the URLLC rate to deliver the number of bits using RB with a certain error probability .
The SINR for the puncturing and superposition cases denoted by is given below:
| (4) |
| (5) |
where and denote the transmit power and channel gain, respectively, from the BS to the URLLC user . denotes the received interference from the coexisting eMBB users.
Using (4) and (5), the corresponding URLLC rate based on finite block length codes is given as follows [33]:
| (6) |
where denotes the packet size of URLLC user , denotes the inverse Q-function and denotes the reliability threshold of URLLC, respectively.
The adoption of superposition or puncturing scheme by the URLLC user is represented by and , respectively and defined as follows:
For the coexistence of eMBB and URLLC, we set the eMBB TTI to ms and the URLLC TTI (also called mini-slot) to ms. In each eMBB TTI, we spatially divided the TTI to form a set of RBs, where each RB has spectrum bandwidth . At the start of each subframe, eMBB users are scheduled for an eMBB TTI of ms and spectrum bandwidth .
Fig. 2 indicates that eMBB users are scheduled for eMBB TTI and URLLC users are scheduled in the mini-slot. Note that an appropriate selection of mini-slots for URLLC traffic is required for spectrum efficiency and to achieve high eMBB rate. Each eMBB user experiences a different SINR level, depending on the distance from the BS and the corresponding channel gain. Therefore, suitable eMBB users can operate on the same channel with an appropriate URLLC user. In a traditional superposition scheme, URLLC users receive interference from coexisting eMBB users, as given in (4), which can compromise reliability. Therefore, we propose a superposition scheme in which URLLC reliability is not affected.
For the case of superposition in which , both eMBB and URLLC transmit on the same channel . The BS transmits the superposed signal to both eMBB and URLLC users, where and denote the messages for eMBB and URLLC users, respectively [34]. The superimposed signal is received by both eMBB and URLLC users, and each user performs SIC to decode its own message. The eMBB user decodes the interference signal from the URLLC user and cancels it to get its own message. Conversely, the URLLC user can receive the message without any SIC. The corresponding rates for the eMBB and URLLC users are given as follows:
| (7) |
| (8) |
III-B Problem Formulation
The objective of this work is to maximize the eMBB rate while satisfying the latency and reliability constraints for the URLLC users. Therefore, the goal is to select the optimal mini-slots from the pre-scheduled eMBB traffic such that the latency constraints are not violated. Moreover, it is also required to choose the optimal channel and power to satisfy the reliability constraints for the URLLC traffic.
| (9) | ||||
| s.t. | (9a) | |||
| (9b) | ||||
| (9c) | ||||
| (9d) | ||||
The objective to maximize the network rate of eMBB users is dependent on the superposition and puncturing schemes represented by and , respectively. represents the power allocated to the URLLC users. The constraint in (9a) ensures that URLLC packets are strictly scheduled just after the arrival of transmission requests. (9b) ensures ultra reliability of each URLLC user . Equations (9c) and (9d) contain the bounds for the decision variables.
The aforementioned problem optimizes the use of superposition/puncturing scheme for URLLC traffic scheduling. The problem is a large mixed integer linear programming (MILP) problem with very high complexity and is difficult to solve. To solve this problem, we use the contract theory framework to determine the willingness of the URLLC users to adopt the superposition scheme. In order to reduce the number of contracts for each URLLC user and to make the contract design scalable, we use one-to-one matching between the eMBB and URLLC users. After the optimal contract design for the superposition, the power allocation is performed for the URLLC users to meet the reliability constraint.
IV Solution Approach
IV-A Contract Theory for Superposition
The wireless spectrum and number of RBs at each BS are limited. In the coexistence environment of URLLC and eMBB, the aim of the BS is to meet the URLLC QoS requirements and maximize the served number of eMBB users. This can be achieved by efficiently packing the URLLC users on the ongoing eMBB communication using the superposition. Therefore, each BS requires an incentive mechanism to encourage URLLC users to opt for superposition. Moreover, the URLLC users must also meet their QoS requirements. However, the BS does not know the willingness of URLLC users in the network to opt for superposition. Therefore, the problem of optimal resource allocation becomes difficult for each BS, which results in information asymmetry between the BS and URLLC users. We use the contract theory framework to motivate URLLC users for superposition, and each BS designs a bundle of contracts for the URLLC users.

First, we define the types of URLLC users based on their preference to opt for superposition based on the geographical location of the URLLC user, as illustrated in Fig. 3. A URLLC user with a higher type is more willing to opt for the superposition than a URLLC user with a lower type.
Definition 1.
We define the willingness of URLLC users to opt for superposition by considering number of tiers in a geographical cell. The URLLC users closer to the BS are more willing to opt for superposition. Therefore, the URLLC users are classified into a set with their corresponding willingness for superposition provided in descending order .
IV-A1 Utility of URLLC Users
The utility of URLLC user is defined as follows:
| (10) |
where denotes the parameter of choosing between superposition or puncturing scheme by the URLLC user which is function of the matched eMBB and URLLC pair . Depending on the utility obtained from the matched pair, each URLLC user selects the optimal superposition or puncturing scheme or , respectively. and denote the price per mega bytes (MB) paid by the URLLC and eMBB users to the BS, respectively, and denotes the proportion of the incentive paid to the URLLC user on choosing the superposition scheme.
IV-A2 BS Utility
The utility of the BS is the difference between the profit obtained from URLLC and eMBB users, and the resources allocated to them:
| (11) |
where and denote the normalizing constants. We consider , which signifies that the price paid by URLLC users is significantly greater than the price paid by eMBB users. Therefore, the BS preferes scheduling URLLC users over eMBB users. and denote the expenses of the BS in terms of channel and power allocation to URLLC and eMBB users, respectively.
Next, we present the one-to-one matching scheme between the URLLC and eMBB users which is essential for the scalability of the designed number of contracts.
IV-B Matching URLLC and eMBB users
In the coexistence scenario of eMBB and URLLC, each URLLC user can be paired with only one eMBB user and vice versa. Therefore, we formulate a one-to-one matching game between URLLC and eMBB networks. The matching is defined as follows:
Definition 2.
A matching is defined by a function from the set such that:
-
1.
and
-
2.
and
-
3.
if and only if is in ,
where for and represents the cardinality of the matching outcome .
The first two properties ensure that the matching between the eMBB and URLLC networks has a one-to-one relation in that an eMBB user can be paired with only one URLLC user . Additionally, when a matching pair cannot be paired for any reason, we have .
IV-B1 Preference Profiles of Players
In this subsection, we first formulate pair selection as a two-sided matching game. In our model, there are two types of cellular users. The first type is eMBB users , while the second type is URLLC users . In the two-sided matching game, each player of one side must rank the players of the other side in descending order of priority, which is represented by a preference profile.
The willingness of URLLC users to adopt the superposition scheme is determined by the BS through the geographical locations of URLLC users. Each eMBB user ranks the potential URLLC users on the basis of their willingness to adopt the superposition scheme. For a URLLC user, the preference of the eMBB user is high for URLCC users that posses low channel gain so that it can help adopt the superposition scheme according to (7) and (8). The URLLC user creates a preference profile based on the following preference function:
| (12) |
Similarly, the preference of the eMBB user is to select a URLLC user whose willingness to adopt the superposition scheme is the highest. Then, in such case, the superposition scheme is selected for the URLLC transmission. The preference profile for the URLLC user is based on the classification of the superposition according to Definition 1 expressed as follows:
| (13) |
Note that once both sides build their respective preference profiles, then, the all eMBB users propose to find their best suited URLLC user based on their preference profiles. We can adopt the deferred acceptance algorithm to execute this process.
Next, we present our URLLC-eMBB matching algorithm which is based on the deferred acceptance algorithm. In the initialization phase (lines 1 3), all variables are initialized. Then, each eMBB user will send proposals to their most preferred URLLC user based on their preference profiles (line 7). The URLLC users on receiving the proposals compare them with existing proposals and choose the one which is the highest ranked in its preference profile (lines 8 11). Note that if the received proposal is ranked lower in the URLLC profile it is immediately rejected which prevents blocking pairs in our scheme (lines 13 14). These rejected proposals are then removed from both preference lists of emBB and URLLC users (lines 15 19). Note that this process of removal ensures the stability of the matching game and prevents blocking pairs to occur. Finally, we receive a stable matching after a number of iterations once the set of matching pairs to do not change (lines 21).
Note that the one-to-one matching is used to select the suitable eMBB and URLLC pairs for the superposition. However, in some cases superposition scheme is not possible to adopt due to the channel gains of matched pairs. In such cases, the puncturing scheme is adopted by the URLLC users.
IV-C Contract feasibility and optimality
Using matching theory, which is discussed in previous section, the suitable contracts for URLLC users are designed. To provide the conditions for the feasibility of the designed contracts, the following conditions apply:
Definition 3.
(Individual Rationality (I.R)) For any , .
Definition 4.
(Incentive Compatibility (I.C)) For any , .
In addition to the above conditions, there are sufficient and necessary conditions for the feasibility of the contracts given as follows:
Definition 5.
(Necessary Condition) For any , if and only if .
A similar proof of the Definition 5 is provided in [25]. This definition states that a URLLC user who is more willing to opt for superposition has higher utility than a user , who is less willing to select superposition.
IV-D Contract-based Problem Formulation
After solving the adoption of superposition or puncturing scheme and for the URLLC users in 10, the rest of the problem is the power allocation to the URLLC users. In this section, we formulate a contract-based optimization problem which is equivalent to (9). The proof of equivalence is given in Appendix A.
| (14) | ||||
| s.t. | (14a) | |||
| (14b) | ||||
| (14c) | ||||
The objective (14) is to maximize the profit of BS . The constraints (14a) and (14b) are individual rationality (IR) and incentive compatibility (IC) constraints, respectively. Problem (14) is a constrained maximization problem for and the solution can be found at the boundary of constraint (14b). Therefore, optimal power allocation, , is performed such that the conditions in (10) are satisfied. Note that, the power allocated to the URLLC user is same for both puncturing and superposition schemes; however, the URLLC user utility is less in the puncturing case as compared to the superposition case because the user is not given the contribution incentive .
Contract-based resource association is performed as described in Algorithm 2. The inputs are the total number of BSs , total number of URLLC users , total number of eMBB users , set of classification of the URLLC users’ willingness to opt for superposition, , which is the set of SINR levels for the URLLC and eMBB users, and , which is set of matching pairs. In Algorithm 2, the contract is first designed for every URLLC user after identifying the class . Next, the feasibility and optimality of the contract are verified such that the URLLC QoS requirements are satisfied. Then, power allocation is performed by selecting the superposition or puncturing scheme based on the designed contract.
V Numerical Results

We perform extensive simulations to evaluate the proposed contract-based scheduling scheme in the URLLC and eMBB coexistence network. Firstly, we model a system having a single macro BS (MBS) located at the center of a geographical area of m m, with two coexisting eMBB and URLLC networks. We uniformly deploy URLLC and eMBB users in the area, as illustrated in Figure 4. Then, we simulate the network for multiple runs to obtain the average results with a different number of URLLC users. Figure 4 presents a snapshot of the network topology. Other simulation parameters are summarized in Table I. We compare the proposed contract-based scheduling scheme with the following two baseline schemes: 1) The ”No URLLC” scheme refers that there are no URLLC users in the network. This scheme is used to determine the impact of URLLC users and compare the loss in eMBB rate. 2) The ”Puncturing” scheme refers to the traditional URLLC scheduling scheme in which eMBB traffic is paused during URLLC transmission.

Figure 5 displays the snapshot of the matching pairs of URLLC and eMBB users in the network, where the dots and triangles represent the eMBB and URLLC users, respectively while the same colors are assigned to matched users.
Figure 6 shows the dependence of the URLLC utility on the contract type. It can be observed that the user with certain contract type gets the maximum utility as compared to the other users. For instance, the user with type will get maximum utility on choosing the contract type . Therefore each URLLC user chooses the contract according to its type maximize its utility.



Figure 7 displays the eMBB rate against an increasing number of URLLC users in the network. It can be observed that as the number of URLLC users increases, the eMBB rate decreases due to scheduling of the URLLC users. It can also be seen that the eMBB rate in the contract-based scheme approaches % for the non-URLLC case compared to the puncturing scheme. This is due to the use of superposition, in which both URLLC and eMBB users operate on the same channel.
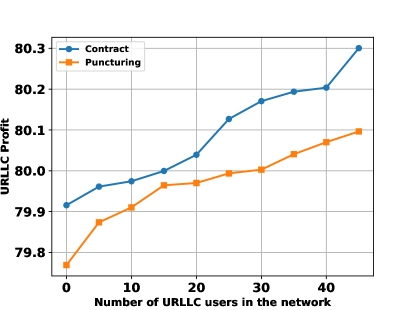
Figure 8 illustrates the BS profit against an increasing number of URLLC users in the network. Because the price paid by URLLC users is significantly higher than that paid by eMBB users, the BS profit is increased by serving a larger number of URLLC users. It can be observed that the proposed contract-based scheme provides up to % of the puncturing scheme’s profit. This is due to the fact that in the contract-based scheme, the BS offers a portion of the eMBB profit to the participating URLLC users as an incentive.
Figure 9 illustrates the URLLC network utility against an increasing number of URLLC users in the network. Because the proposed contract-based scheme use an incentive mechanism to encourage the URLLC users for the adoption of superposition scheme, the URLLC profit using the proposed scheme is greater than the puncturing scheme. For instance, when there are number of URLLC users in the network, the proposed contract-based scheme provides up to % of the No URLLC scheme’s profit while the puncturing scheme provides only % of the profit. The contract-based scheme also offers a portion of the profit to the participating URLLC users as an incentive.
Figure 10 illustrates the effect of various reliability values on the eMBB rate against an increasing number of URLLC users in the network. We tested the proposed contract-based approach for different values of reliability parameters . It can be observed that the eMBB rate is reduced for high reliability values. This is due to the fact that the high reliability constraint causes higher SINR requirement for the URLLC users. As a result of this high SINR requirement of SINR requirement, the eMBB users are penalized by choosing the puncturing scheme by the URLLC users to meet the high reliability constraints. Moreover the trends of reduction in eMBB rates with the increase in the number of URLLC users in the network are observed same as shown in Figure. 7.
VI Conclusion
In this paper, we have addressed the resource allocation problem in URLLC and eMBB coexistence networks. We have formulated an optimization problem to maximize the eMBB network rate with respect to the QoS requirements imposed by the URLLC traffics in the cellular network. Using the puncturing scheme, URLLC users significantly affect the performance of an eMBB network, therefore, we used the contract theory framework to encourage URLLC users to opt for the superposition scheme such that eMBB loss was minimized. This has been achieved by classifying the URLLC users according to their willingness to opt for the superposition scheme, which is favorable for the eMBB network. By using such contracts, resource allocation has been performed to the URLLC users. The numerical results have revealed that the contract-based scheme outperformed the puncturing scheme.

Appendix A Proof of equivalence of problem (9) and problem (14):
The utility of the BS in (14) is a function of the achievable rates of eMBB and URLLC users as given in (11). Therefore maximizing and is equivalent to maximizing the corresponding URLLC and eMBB rate. Moreover, the high prices paid by the URLLC users prioritize their scheduling over eMBB scheduling. From this pricing model, the constraint (9a) is ensured. Further, the individual rationality constraint (14a) ensures the individual utility of each URLLC user to satisfy the reliability requirement given in (9b). Therefore the problem (9) is equivalent to problem (14).
References
- [1] P. Popovski, Č. Stefanović, J. J. Nielsen, E. De Carvalho, M. Angjelichinoski, K. F. Trillingsgaard, and A.-S. Bana, “Wireless access in ultra-reliable low-latency communication (URLLC),” IEEE Transactions on Communications, vol. 67, no. 8, pp. 5783–5801, August 2019.
- [2] Qualcom Tech White paper, “Making 5G NR a commercial reality : For enhanced mobile broadband and beyond,” April 2018.
- [3] C. Marco, “Key features and requirements of 5G/IMT-2020 networks,” Internetsociety.org, 2018.
- [4] S. F. Abedin, M. G. R. Alam, S. M. A. Kazmi, N. H. Tran, D. Niyato, and C. S. Hong, “Resource allocation for ultra-reliable and enhanced mobile broadband IoT applications in fog network,” IEEE Transactions on Communications, vol. 67, no. 1, pp. 489–502, January 2019.
- [5] S. E. Elayoubi, P. Brown, M. Deghel, and A. Galindo-Serrano, “Radio resource allocation and retransmission schemes for URLLC over 5G networks,” IEEE Journal on Selected Areas in Communications, vol. 37, no. 4, pp. 896–904, April 2019.
- [6] P. Popovski, J. J. Nielsen, C. Stefanovic, E. De Carvalho, E. Strom, K. F. Trillingsgaard, A.-S. Bana, D. M. Kim, R. Kotaba, J. Park et al., “Wireless access for ultra-reliable low-latency communication: Principles and building blocks,” IEEE Network, vol. 32, no. 2, pp. 16–23, March 2018.
- [7] 3GPP, Downlink Multiplexing of eMBB and URLLC Transmissions. 3GPP TSG RAN WG1 NR Ad-Hoc Meeting, R1-1700374, 2017.
- [8] S. M. A. Kazmi, N. H. Tran, T. M. Ho, A. Manzoor, D. Niyato, and C. S. Hong, “Coordinated device-to-device communication with non-orthogonal multiple access in future wireless cellular networks,” IEEE Access, vol. 6, pp. 39 860–39 875, June 2018.
- [9] T. M. Ho, N. H. Tran, S. M. A. Kazmi, Z. Han, and C. S. Hong, “Wireless network virtualization with non-orthogonal multiple access,” in NOMS 2018 - 2018 IEEE/IFIP Network Operations and Management Symposium, April 2018, pp. 1–9.
- [10] P. Bolton, M. Dewatripont et al., Contract theory. Cambridge, MA, USA: MIT press, 2005.
- [11] J.-J. Laffont and D. Martimort, The theory of incentives: the principal-agent model. Princeton, NJ, USA: Princeton university press, 2009.
- [12] A. Anand, G. De Veciana, and S. Shakkottai, “Joint scheduling of URLLC and eMBB traffic in 5G wireless networks,” in Proc. of the IEEE Conference on Computer Communications (INFOCOM). Honolulu, HI, USA: IEEE, April 2018.
- [13] M. Angjelichinoski, K. F. Trillingsgaard, and P. Popovski, “A statistical learning approach to ultra-reliable low latency communication,” arXiv preprint arXiv:1809.05515, 2018.
- [14] R. Kassab, O. Simeone, and P. Popovski, “Coexistence of URLLC and eMBB services in the C-RAN uplink: An information-theoretic study,” arXiv preprint arXiv:1804.06593, 2018.
- [15] C. Sun, C. She, C. Yang, T. Q. S. Quek, Y. Li, and B. Vucetic, “Optimizing resource allocation in the short blocklength regime for ultra-reliable and low-latency communications,” IEEE Transactions on Wireless Communications, vol. 18, no. 1, pp. 402–415, January 2019.
- [16] Z. Chu, W. Yu, P. Xiao, F. Zhou, N. Al-Dhahir, A. u. Quddus, and R. Tafazolli, “Opportunistic spectrum sharing for D2D-based URLLC,” IEEE Transactions on Vehicular Technology, vol. 68, no. 9, pp. 8995–9006, September 2019.
- [17] J. Zhang, X. Xu, K. Zhang, B. Zhang, X. Tao, and P. Zhang, “Machine learning based flexible transmission time interval scheduling for eMBB and uRLLC coexistence scenario,” IEEE Access, vol. 7, pp. 65 811–65 820, May 2019.
- [18] H. Ji, S. Park, J. Yeo, Y. Kim, J. Lee, and B. Shim, “Ultra-reliable and low-latency communications in 5G downlink: Physical layer aspects,” IEEE Wireless Communications, vol. 25, no. 3, pp. 124–130, June 2018.
- [19] M. Alsenwi, N. H. Tran, M. Bennis, A. Kumar Bairagi, and C. S. Hong, “embb-urllc resource slicing: A risk-sensitive approach,” IEEE Communications Letters, vol. 23, no. 4, pp. 740–743, April 2019.
- [20] S. R. Pandey, M. Alsenwi, Y. K. Tun, and C. S. Hong, “A downlink resource scheduling strategy for URLLC traffic,” in Proc. of the IEEE International Conference on Big Data and Smart Computing (BigComp), Kyoto, Japan, February 2019.
- [21] J. J. Nielsen, R. Liu, and P. Popovski, “Ultra-reliable low latency communication using interface diversity,” IEEE Transactions on Communications, vol. 66, no. 3, pp. 1322–1334, March 2018.
- [22] Y. Zhang, M. Pan, L. Song, Z. Dawy, and Z. Han, “A survey of contract theory-based incentive mechanism design in wireless networks,” IEEE Wireless Communications, vol. 24, no. 3, pp. 80–85, June 2017.
- [23] Y. Zhang, L. Song, W. Saad, Z. Dawy, and Z. Han, “Contract-based incentive mechanisms for device-to-device communications in cellular networks,” IEEE Journal on Selected Areas in Communications, vol. 33, no. 10, pp. 2144–2155, October 2015.
- [24] T. H. T. Le, N. H. Tran, P. L. Vo, Z. Han, M. Bennis, and C. S. Hong, “Joint cache allocation with incentive and user association in cloud radio access networks using hierarchical game,” IEEE Access, vol. 7, pp. 20 773–20 788, February 2019.
- [25] L. Duan, L. Gao, and J. Huang, “Cooperative spectrum sharing: A contract-based approach,” IEEE Transactions on Mobile Computing, vol. 13, no. 1, pp. 174–187, January 2012.
- [26] J. Kang, Z. Xiong, D. Niyato, D. Ye, D. I. Kim, and J. Zhao, “Toward secure blockchain-enabled internet of vehicles: Optimizing consensus management using reputation and contract theory,” IEEE Transactions on Vehicular Technology, vol. 68, no. 3, pp. 2906–2920, March 2019.
- [27] Z. Zhou, P. Liu, J. Feng, Y. Zhang, S. Mumtaz, and J. Rodriguez, “Computation resource allocation and task assignment optimization in vehicular fog computing: A contract-matching approach,” IEEE Transactions on Vehicular Technology, vol. 68, no. 4, pp. 3113–3125, April 2019.
- [28] Y. Hu, X. Li, Y. Chen, and B. Zeng, “Multi-principal multi-agent contract design: Theory and application to device-to-device communications,” IEEE Transactions on Vehicular Technology, vol. 68, no. 3, pp. 2535–2544, March 2019.
- [29] Y. Gu, W. Saad, M. Bennis, M. Debbah, and Z. Han, “Matching theory for future wireless networks: Fundamentals and applications,” IEEE Communications Magazine, vol. 53, no. 5, pp. 52–59, May 2015.
- [30] C. Liu, M. Bennis, M. Debbah, and H. V. Poor, “Dynamic task offloading and resource allocation for ultra-reliable low-latency edge computing,” IEEE Transactions on Communications, vol. 67, no. 6, pp. 4132–4150, June 2019.
- [31] S. M. A. Kazmi, N. H. Tran, W. Saad, Z. Han, T. M. Ho, T. Z. Oo, and C. S. Hong, “Mode selection and resource allocation in device-to-device communications: A matching game approach,” IEEE Transactions on Mobile Computing, vol. 16, no. 11, pp. 3126–3141, November 2017.
- [32] A. Anand and G. de Veciana, “Resource allocation and harq optimization for urllc traffic in 5g wireless networks,” IEEE Journal on Selected Areas in Communications, vol. 36, no. 11, pp. 2411–2421, November 2018.
- [33] P. Popovski, K. F. Trillingsgaard, O. Simeone, and G. Durisi, “5G wireless network slicing for eMBB, URLLC, and mMTC: A communication-theoretic view,” IEEE Access, vol. 6, pp. 55 765–55 779, September 2018.
- [34] P. K. Sharma and D. I. Kim, “UAV-enabled downlink wireless system with non-orthogonal multiple access,” in Proc. of the IEEE Globecom Workshops (GC Wkshps), Singapore, Singapore, December 2017.