Comprehensive Performance Analysis of
Homomorphic Cryptosystems for
Practical Data Processing
Abstract
Oblivious data processing has been an on and off topic for the last decade or so. It provides great opportunities for secure data management and processing, especially in the cloud. At the same time, modern computing resources seem to be affordable enough to allow for practical use of homomorphic cryptography. Yet, the availability of products that offer practical homomorphic data processing is extremely scarce. As part of a project aimed at developing a practical homomorphic data management platform, we have conducted an extensive study of homomorphic cryptosystems’ performance, the results of which are presented in this work. For this work we chose the following five cryptosystems: fully homomorphic HElib and SEAL, somewhat fully homomorphic PyAono, and partially homomorphic Paillier and ElGamal. In the discussion of the aggregated results, we suggest that partially homomorphic cryptosystems could be used today in certain practical applications, whereas time has not yet come for the fully homomorphic ones.
Index Terms:
Cryptography; Data processing; Performance analysis# At the time of publication at NUS–Singtel Cyber Security Research & Development Laboratory, email: [email protected]
I Introduction
Oblivious data processing can solve a spectrum of security issues, mitigate a wide range of business risks, facilitate migration to the cloud for the companies that are still on the fence, and help with compliance in the view of new data protection regulations such as GDPR, PDPA or CCPA. Cryptography is an obvious candidate on how to achieve obliviousness; however, typically cryptosystems do have the capability for any meaningful manipulations with the encrypted data.
Homomorphic encryption is a type of encryption that is capable of carrying out specific types of computations directly on ciphertext and generates an encrypted result which, when decrypted, matches the result of operations would they have been performed on the plaintexts [1]. Typically, homomorphic cryptosystems possess a homomorphic property with respect to one or several arithmetic operations, i.e., allowing for encrypted addition, multiplication, etc. However, there also are some other types of homomorphic cryptosystems, e.g., Goldwasser-Micali probabilistic cryptosystem that allows for encrypted XOR (addition modulo 2) [2].
Strictly speaking, a homomorphic cryptosystem could be defined as follows. Assume and to be the encryption and decryption functions, to be plaintext values, and to be an -ary plaintext operation. Then, if there exists an operation such that for any : , then the encryption scheme is said to have a property of homomorphism, i.e., it preserves operation .
For arithmetic homomorphic cryptosystems (ones that preserve arithmetic operations), we can distinguish two groups: partially and fully homomorphic cryptosystems. Using partially homomorphic encryption, it is possible to perform only one operation on encrypted data—multiplication or addition—but not both [3]. There are numerous ciphers capable of performing partially homomorphic encryption, but determining a feasible cipher for real world applications can be exceedingly challenging, primarily due to functional requirements and efficiency concerns. A cryptosystem that is capable of performing both addition and multiplication over ciphertexts is called a fully homomorphic cryptosystem.
This work seeks to examine the practicality of homomorphic cryptography in the light of computing resources that are available today. For this work we have chosen five implementations of homomorphic cryptosystems; namely, three fully homomorphic cryptosystems: Homomorphic Encryption Library (HElib), Simple Encrypted Arithmetic Library (SEAL), and an implementation of the somewhat111Somewhat fully homomorphic scheme is a scheme that enables both addition and multiplication but exposes limits to the number of operations that can be executed. Typically, this refers to a scheme that can perform many additions and a small amount (sometimes, just one) multiplications. Some fully homomorphic schemes overcome this by executing a procedure called bootstrapping — an operation of “refreshing” the ciphertext. Bootstrapping is usually a very expensive operation. Unlike PyAono, both HElib and SEAL implement bootstrapping, which makes them fully homomorphic. homomorphic encryption scheme by Y. Aono et al. (PyAono); and our own implementations of Paillier (additive) and ElGamal (multiplicative) partially homomorphic cryptosystems.
This choice was influenced by several factors. First, we were looking for solutions that reached a certain level of maturity and recognition in the research community, as an indication that both the underlying cryptographic scheme and the implementation can be considered thoroughly reviewed. Cryptographic analysis of the schemes and analysis of implementation fidelity were not in the scope of this work. In addition to that, we only considered implementations that had their license indicate that it is allowed to carry out research on them. Furthermore, after extensive attempts we were still unable to get some of the available implementations to work due to compilation errors, lack of documentation, runtime errors, etc. Those were eventually removed from the experiments.
The examination presented in this paper arose from our research on practicality of emulating fully homomorphic computations using partially homomorphic cryptosystems and a trusted re-encryption agent equipped with a smart computation scheduler that enables re-encryptions between the partial schemes to be done while other portions of homomorphic computation are carried out. In this research, our own implementations of Paillier and ElGamal are used as partially homomorphic cryptosystems in the emulation; thus, they were also selected for the final list of contenders. The work presented in this paper is a continuation of our earlier short analysis on the topic [4].
For each cipher, we obtained the source code and applied minor tweaks to measure precisely the computation time with the execution of each operation. We additionally tested the performance of each cipher under a full spectrum of cryptosystem initialization parameters; the data collected from these tests is presented in charts in the annex of the paper.
The rest of the paper is structured as follows: Section II reviews some of the previous works in a similar direction; Section III discusses details of the comparative testing that was carried out; Section IV presents the findings and a short commentary; Section V presents a concluding discussion of the results and indicates directions of future work; performance charts are appended at the end of the paper.
II Related Work
There is a multitude of homomorphic schemes: unpadded RSA [5] and ElGamal [6] schemes are multiplicative homomorphic; Benaloh [7], Paillier [8], and Boneh-Goh-Nissim [9] schemes are additive homomorphic. However, a fully homomorphic scheme, i.e., a scheme that supports both addition and multiplication, remained undiscovered for a long time and was referred to by some researchers as a “holy grail of cryptography” [10]. A breakthrough in the area was made in 2009 when Dr. Craig Gentry has published his work on the first fully homomorphic encryption scheme [11].
Most researchers agree that currently the Gentry’s scheme is impractical for general-purpose computations due to its poor performance. There have been multiple studies of its performance as well as attempts to improve it [12, 13, 14], but it is still considered to be far from being practical.
Although several researchers have approached the issue of measuring the performance of homomorphic computations and comparing it to plaintext computations, there are not many empirical results in that direction. Certain insights could be gathered from the work by Gentry et al. that covers implementation details of his scheme and how its behavior in practice [14]. An attempt to secure third-party applications by amending the binaries to work over homomorphically encrypted data was done by Tople et al. [15]. Performance analysis done in their project AutoCrypt could provide an approximate understanding of performance drop after switching from plaintext to homomorphic computations. Thorough performance analysis of Gentry’s scheme was done by Liu et al. [16]. However, the work omits to compare homomorphic computation performance to the plaintext alternative and focuses on the relation between the computation time and key length.
III Methodology
Preliminary research was carried out to select the candidates for comparison. Five solutions were identified based on existing use cases, code availability, license, and implementation stability.
III-A Homomorphic Ciphers
Started in 2013, HElib is written in C++ and is still under active development by Shai Halevi (IBM), Victor Shoup (NYU, IBM), and others, and is one of the most comprehensive fully homomorphic encryption libraries available today. It is built on top of the Brakerski-Gentry-Vaikuntanathan (BGV) lattice-based encryption scheme but delivers enhanced performance via the Smart-Vercauteren ciphertext packing and Gentry-Halevi-Smart homomorphic optimizations. HElib is a prime candidate for research on appliances such as establishing cloud security, search engine query encryption, and spam filtering. HElib is available on GitHub [17].
SEAL project was started in 2015 but has changed its underlying cryptosystem to a variation of BFV cryptosystem [18] with the release of v2.0 in 2016. It was initiated in the Cryptography Research Group at Microsoft Research and is still undergoing active development. Its engineering is mainly focused on providing a secure platform for cloud computing through fully homomorphic properties. Implementation of SEAL, written in C++ and C#, can be found on Microsoft’s web page [19]. In our experiments, we used v2.3.1 of the library.
PyAono is an implementation of an LWE-based homomorphic cryptosystem suggested by Y. Aono et al. [20]. PyAono is also available GitHub [21]. This repository contains a homomorphic library written in C++ and an interoperability layer for Python. For the experiments, the homomorphic library was extracted and imported into a simplified C++ testing program, fully capable of measuring and logging computation time of each of its operations.
The Paillier cryptosystem was invented by Pascal Paillier in the year 1999 [8]. It is a probabilistic asymmetric public-key encryption scheme with partially homomorphic features based on the problem of computing residue classes. In its base form, the Paillier cryptosystem is only capable of homomorphic addition of ciphertexts and multiplication by a plaintext constant. Paillier scheme happened to be especially popular in application to electronic voting systems, with the motive of creating a fast, secure, and just approach to collecting votes. Our implementation of the Paillier cryptosystem is written in C# and can be found on GitHub [22].
The ElGamal encryption system was developed and first presented by Taher ElGamal in 1985 [6]. Its cryptography is based on the computational Diffie-Hellman problem (CDH). Similar to the Paillier cryptosystem, ElGamal encryption is a probabilistic asymmetric partially homomorphic public key encryption scheme. ElGamal is a multiplicative partially homomorphic cryptosystem. ElGamal scheme is mostly used for digital cryptographic signatures and more rarely for encryption; it is used in such popular systems as GNU Privacy Guard (GPG) and Pretty Good Privacy (PGP). Our C# implementation of ElGamal encryption can be found on GitHub [23].
III-B Technical Details
HELib, SEAL, and PyAono have support for three operations (addition, subtraction, multiplication, but not division) and support negative numbers out of the box. However, a “textbook” version of Paillier cryptosystem only supports addition (no subtraction) of only positive integers. Similarly, a textbook version of the ElGamal cryptosystem only supports multiplication of positive integers. In our implementations we designed variations to the schemes to add support for inverse operations (subtraction and division) and for negative numbers.
In both cases, we implement a multi-step encoding. As a first step, we convert the to-be-encrypted number to a rational (fixed-point decimal) number , where is some pre-defined constant ( in our experiments), and store the number as a pair (numerator, denominator). When encrypted, the numerator and denominator are encrypted separately:
This immediately enables division for ElGamal encryption: multiplication of and is ; division of by is . So, effectively, we reduced division to multiplication. Paillier cryptosystem can operate on these encodings without any issues as well: as all numbers have the same denominator , we can just add the numerators.
Clearly, this encoding also automatically enables fractional numbers with precision up to positions after the decimal point. Upon decryption of the ciphertext, the number is converted back from a rational fraction by performing the final division of the decrypted numerator by the decrypted denominator.
The next step in the encoding process enables negative numbers. For the encryption of negative numbers, we adopted the two’s complement approach that is used in modern computers when dealing with signed integers, effectively transforming negative values to positive numbers before encryption. With a predefined threshold , this scheme allows to encode numbers in the range from by doing a 1-to-1 mapping of the interval to . Algorithm 1 illustrates this process.
During decoding, the decrypted numbers undergo a modulus of . This is to reduce these numbers to their two’s complement representation, which is a necessary step following any computation involving negative numbers in two’s complement representation. As an example, assume we have two 4-bit signed integers, and . Their binary form in two’s complement would be 0010 and 1111 respectively. When we add and , the answer would be 1 in decimal form, but if we perform the same operation on their two’s complement form, we will get . In this case, , and by evaluating we obtain the correct answer of . If the result of modulus is larger than , it will be converted back to its negative value by subtracting from it.
The prime limitation of this method is that the results of computation on ciphertexts must be within the range . Hence, should be a value that is sufficiently large to store the expected results of the computation. However, this behavior replicates the behavior of plaintext arithmetics implementation in modern computers, which is a useful property as the computation produces an expected result with under- and over-flows where they would occur in plaintext arithmetics as well.

For operations of , values are in form , where is time in ms, and is the ratio of and the time execution of the same operation took over plaintexts.
E.g., PyAono’s addition is 246,897 times slower than plaintext addition.
To ensure fairness and consistency in test results, we ran every program that collected performance metrics on the same machine with an Intel Xeon E5-1650 v4 CPU with 6 cores running at 3.60GHz under Ubuntu 16.04. We wrote a script to standardize the execution of all five ciphers and log the computation time for each run of the test program. This allowed us to perform each test with the same general input, for instance, the number of iterations.
For each cipher, additional tests were conducted to determine the implications of each cipher’s initialization parameters to its performance. This was done in part to ensure that shifts in each parameter are impactful enough to have a separate record in the results and not too big to break the system. This also helped to simplify the results of the experiment by identifying parameters with dependant values or values that were advised to be left unchanged. Those were then removed from the scope of the experiment.
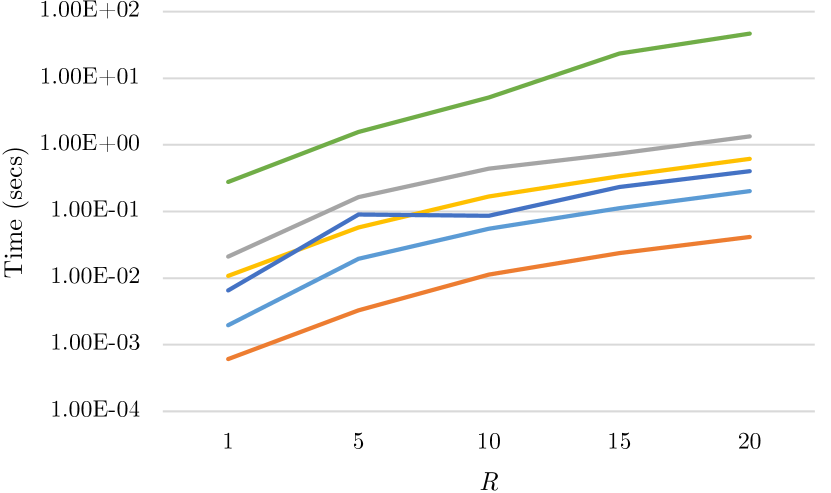
For every test, a single parameter of each cipher is changed, and each cipher is tested individually. A control test was conducted using the default value of each parameter, to act as a point of reference in every test. Data from all tests were recorded and charted, as demonstrated in sections below and in the Appendix.
IV Empirical Results
Due to the irregular range of data values collected, charts were plotted using a logarithmic scale. Please note that differences in bar length are not linearly proportional to differences in computation time.
Tests were run on the three basic operations, namely addition, subtraction, and multiplication. Division was left out due to SEAL, PyAono and Paillier not supporting division, whereas for ElGamal division is completely equivalent to multiplication. We considered applying our number encoding scheme to support division in SEAL and PyAono, but eventually decided that the results are more informative if the implementations are tested in their “vanilla” form.
Results were obtained using operations on ciphertexts from all five ciphers, as well as on plaintext for scale. All tests were conducted without bootstrapping (where applicable), as the strategy on deciding when to execute this computationally expensive procedure is non-trivial and varies from one use-case to another. All three plain text operations ran at the same efficiency, which was on average seconds per one execution, which is also times as fast as the fastest homomorphic operation, which appeared to be multiplication by ElGamal.
All tests conducted were ran on 1000 pairs of 2-digit plaintext numbers. Each test was repeated 5 times and the mean result was tabulated for each operation. Aggregated results are presented in Figure 1. Paillier possesses the fastest addition, subtraction, and key generation operations, ElGamal — the fastest multiplication operation, HElib demonstrates the fastest encryption, and SEAL has the fastest decryption. PyAono was least efficient in four operations, namely multiplication, encryption, decryption, and key generation. Its addition and subtraction operations are also relatively inefficient, topping only that of HElib. During the research period, PyAono was declared deprecated, so it is unlikely to be optimized in the future. We still include the empirical numbers for PyAono for reference, but we will not focus on it in discussing the results.
V Discussion & Conclusion
Results clearly suggest that partially homomorphic cryptosystems are significantly faster at homomorphic operations and relatively on par in en-/decryption times with HElib and SEAL. Paillier and ElGamal are consistently about 20–30k times slower than plaintext. At the same time, HElib is 500k times slower for subtraction, 1.6M times slower for addition, and almost 19M times slower for multiplication. SEAL shows relatively acceptable performance on addition and subtraction: 60–100k times slower than plaintext; but 15M times slower for multiplication (not to forget that it doesn’t support division). PyAono takes the middle ground performing around 235k times slower than plaintext addition/subtraction; however, it absolutely breaks records in all other measurements: 2.2B (sic!) times slower in multiplication, 4.5 seconds for en-/decryption and over 700 seconds (sic!) for key generation.
Let us imagine that we use an emulation of fully homomorphic properties based on Paillier and ElGamal and a trusted re-encryption agent. Re-encryption agent uses a serialized strategy of executing a computation: it performs all operations that are possible with current encryptions, then re-encrypts intermediate values into a different encryption scheme, and continues (see Algorithm 2 for an example). Note that this strategy does not involve any parallelization; e.g., step 2 does not need to wait for the agent to finish encryption of and , and the agent can start the decryption of in step 4 while step 3 is not yet complete. We also do not take into account network latency and speed between the compute engine and the agent.
Using the numbers that are presented in Figure 1, we can estimate the comparative efficiency of SEAL and HElib and the emulation described above on some sample tasks. E.g., on a simple task of computing , the emulation works with the same speed as SEAL and 1.46 times slower than HElib.
A slightly more complex task of computing a weighted sum of a large number of elements is emulated at 0.9 the time of SEAL and is 1.35 times slower than HElib. However, if we assume that the numbers were pre-encrypted (therefore eliminating the initial encryption), emulation finishes in 0.63 the time of SEAL and 0.75 the time of HElib. Somewhere in between these two scenarios is such task as secure linear regression: the weights of the model are pre-encrypted, but the values that we are applying the model to are coming in online; in this case, the emulation performs the computation in 0.81 the time of SEAL and 1.1 the time of HElib.
As we can see, on more complex tasks, the emulation can be on par or even better than fully homomorphic schemes. It is important to notice that in reality, these theoretical numbers will be significantly corrected in favor of the emulation due to 1) bootstrapping in fully homomorphic schemes, that will happen on more complex tasks and is a very expensive operation (600 ms bootstrapping a single ciphertext in HElib as compared to 1–20 ms for a homomorphic operation [24]); 2) parallelization of work between the agent and the compute engine, which can significantly improve overall timings for the emulation.
It is also clear that due to the requirement in re-encryption under the emulation protocol, the en-/decryption efficiency of the partially homomorphic scheme becomes crucial for the overall performance. We plan to continue our work on optimizing Paillier and ElGamal en-/decryption procedures and investigate other partially and fully homomorphic cryptosystems that could provide better overall performance.
References
- [1] X. Yi, R. Paulet, and E. Bertino, “Homomorphic encryption,” in Homomorphic Encryption and Applications. Springer, 2014, pp. 27–46.
- [2] S. Goldwasser and S. Micali, “Probabilistic encryption,” Journal of computer and system sciences, vol. 28, no. 2, pp. 270–299, 1984.
- [3] M. Ogburn, C. Turner, and P. Dahal, “Homomorphic encryption,” Procedia Computer Science, vol. 20, pp. 502–509, 2013.
- [4] V. Sidorov and W. K. Ng, “Towards performance evaluation of oblivious data processing emulated with partially homomorphic encryption schemes,” in 2016 IEEE 2nd International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS), April 2016, pp. 113–115.
- [5] R. L. Rivest, A. Shamir, and L. Adleman, “A method for obtaining digital signatures and public-key cryptosystems,” Communications of the ACM, vol. 21, no. 2, pp. 120–126, 1978.
- [6] T. ElGamal, “A public key cryptosystem and a signature scheme based on discrete logarithms,” IEEE transactions on information theory, vol. 31, no. 4, pp. 469–472, 1985.
- [7] J. Benaloh, “Dense probabilistic encryption,” in Proceedings of the workshop on selected areas of cryptography, 1994, pp. 120–128.
- [8] P. Paillier, “Public-key cryptosystems based on composite degree residuosity classes,” in International Conference on the Theory and Applications of Cryptographic Techniques. Springer, 1999, pp. 223–238.
- [9] D. Boneh, E.-J. Goh, and K. Nissim, “Evaluating 2-dnf formulas on ciphertexts,” in Theory of Cryptography Conference. Springer, 2005, pp. 325–341.
- [10] D. Micciancio, “A First Glimpse of Cryptography’s Holy Grail,” Commun. ACM, vol. 53, no. 3, pp. 96–96, Mar. 2010. [Online]. Available: http://doi.acm.org/10.1145/1666420.1666445
- [11] C. Gentry, “Computing Arbitrary Functions of Encrypted Data,” Commun. ACM, vol. 53, no. 3, pp. 97–105, Mar. 2010. [Online]. Available: http://doi.acm.org/10.1145/1666420.1666444
- [12] N. Smart and F. Vercauteren, “Fully Homomorphic Encryption with Relatively Small Key and Ciphertext Sizes,” in Public Key Cryptography – PKC 2010, ser. Lecture Notes in Computer Science, P. Nguyen and D. Pointcheval, Eds. Springer Berlin Heidelberg, 2010, vol. 6056, pp. 420–443. [Online]. Available: http://dx.doi.org/10.1007/978-3-642-13013-7_25
- [13] Z. Brakerski and V. Vaikuntanathan, “Efficient Fully Homomorphic Encryption from (Standard) LWE,” SIAM Journal on Computing, vol. 43, no. 2, pp. 831–871, 2014. [Online]. Available: http://dx.doi.org/10.1137/120868669
- [14] C. Gentry and S. Halevi, “Implementing Gentry’s Fully-Homomorphic Encryption Scheme,” in Advances in Cryptology–EUROCRYPT 2011, ser. Lecture Notes in Computer Science, K. Paterson, Ed. Springer Berlin Heidelberg, 2011, vol. 6632, pp. 129–148. [Online]. Available: http://dx.doi.org/10.1007/978-3-642-20465-4_9
- [15] S. Tople, S. Shinde, Z. Chen, and P. Saxena, “AUTOCRYPT: Enabling Homomorphic Computation on Servers to Protect Sensitive Web Content,” in Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, ser. CCS’13. New York, NY, USA: ACM, 2013, pp. 1297–1310. [Online]. Available: http://doi.acm.org/10.1145/2508859.2516666
- [16] J. Liu, Y.-H. Lu, and C.-K. Koh, “Performance Analysis of Arithmetic Operations in Homomorphic Encryption,” 2010.
- [17] “HELib: a C++ implementation of Brakerski-Gentry-Vaikuntanathan (BGV) homomorphic encryption scheme,” https://github.com/shaih/HElib, accessed: November 20, 2015.
- [18] J. Fan and F. Vercauteren, “Somewhat practical fully homomorphic encryption,” Cryptology ePrint Archive, Report 2012/144, 2012, https://eprint.iacr.org/2012/144.
- [19] “Microsoft SEAL: Fast and Easy-to-Use Homomorphic Encryption Library,” https://www.microsoft.com/en-us/research/project/microsoft-seal/, accessed: February 27, 2019.
- [20] Y. Aono, T. Hayashi, L. T. Phong, and L. Wang, “Fast and secure linear regression and biometric authentication with security update.” IACR Cryptology ePrint Archive, vol. 2015, p. 692, 2015.
- [21] “PyAono – A Python implementation of the homomorphic encryption scheme by Yoshinori Aono et al.” https://github.com/iamtrask/PyAono, accessed: February 25, 2019.
- [22] “PaillierExt: a .NET framework extension implementing the Paillier encryption scheme,” https://github.com/bazzilic/PaillierExt, accessed: February 23, 2019.
- [23] “ElGamalExt: a .NET framework extension implementing the ElGamal encryption scheme,” https://github.com/bazzilic/ElGamalExt, accessed: February 23, 2019.
- [24] L. Ducas and D. Micciancio, “Fhew: bootstrapping homomorphic encryption in less than a second,” in Annual International Conference on the Theory and Applications of Cryptographic Techniques. Springer, 2015, pp. 617–640.