Automated Trajectory Synthesis for UAV Swarms Based on Resilient Data Collection Objectives
Abstract
The use of Unmanned Aerial Vehicles (UAVs) for collecting data from remotely located sensor systems is emerging. The data can be time-sensitive and require to be transmitted to a data processing center. However, planning the trajectory of a collaborative UAV swarm depends on multi-fold constraints, such as data collection requirements, UAV maneuvering capacity, and budget limitation. Since a UAV may fail or be compromised, it is important to provide necessary resilience to such contingencies, thus ensuring data security. It is important to provide the UAVs with efficient spatio-temporal trajectories so that they can efficiently cover necessary data sources. In this work, we present Synth4UAV, a formal approach for automated synthesis of efficient trajectories for a UAV swarm by logically modeling the aerial space and data point topology, UAV moves, and associated constraints in terms of the turning and climbing angle, fuel usage, data collection point coverage, data freshness, and resiliency properties. We use efficient, logical formulas to encode and solve the complex model. The solution to the model provides the routing and maneuvering plan for each UAV, including the time to visit the points on the paths and corresponding fuel usage such that the necessary data points are visited while satisfying the resiliency requirements. We evaluate the proposed trajectory synthesizer, and the results show that the relationship among different parameters follow the requirements while the tool scales well with the problem size.
Keywords— UAV swarm; trajectory design; formal model
1 Introduction
Unmanned Aerial Vehicles (UAVs) are increasingly being used for data collection. They are successfully used in scenarios where it is highly dangerous, as well as monotonous for human observers, or in some cases, excessively costly [1]. For example, UAVs may be used in surveillance of sensitive points in industrial networks, such as the smart grid bus system [2]. They can also be used in UAV-assisted wireless sensor networks to collect data directly from sensor nodes [3]. Sensor nodes can be planted at prespecified remote locations on the ground. Some of the UAV waypoints can be located in close proximity to the data sensors. In many cases, UAVs start their flights from one or more base stations or data centers and collect data from different waypoints along the trajectories before reaching endpoints.
The trajectory planning in scenarios that consider multi-fold constraints of the UAVs, such as maneuvering restriction, budget limitation, and data collection requirements, is generally an NP-hard problem [4]. The trajectories of UAVs may contain predefined waypoints in the three-dimensional Euclidean space; however, the UAVs have certain limitations in maneuvering and fuel capacity while going from one point to another. The operators of such data collection systems generally employ a swarm of UAVs to collect data from the data sources collaboratively but may have budget limitations. The data collection is time-sensitive, as data freshness is important in practical scenarios. For example, the operator may want a data point to be resiliently covered by multiple UAVs, so that even if some of the UAVs fail to operate normally due to malfunction or cyberattacks, some others can still perform the job successfully. Moreover, they need to make sure that the difference in the time of the data collection is below certain thresholds. This calls the need for a comprehensive UAV trajectory designer for a UAV swarm, although the problem is combinatorially hard.
In this paper, we aim to address this challenge by developing Synth4UAV, a formal model-based trajectory planner for a UAV swarm. We use Satisfiability Modulo Theories (SMT) [5] to implement, encode, and solve the corresponding formal model. The solution synthesizes a trajectory for the UAV swarm, if there is one, satisfying all the given constraints, including data freshness and budget constraints. The evaluation results show that our tool scales well to solve problems with large spatial systems. Our major contributions in this research consist of the following:
-
1.
We formally model the UAV trajectory planning as a constraint satisfaction problem. We model the UAV moves and associated constraints, such as UAV maneuver limitations, fuel usage, data freshness, budget limitation, and resiliency requirements for data collection.
-
2.
We encode the formal model using SMT as a constraint satisfaction problem and solve it using an efficient SMT solver to find the trajectory of the UAV swarm. We demonstrate the developed tool on a case study.
-
3.
We analyze various characteristics of the trajectory synthesis problem. We evaluate the scalability of the tool. We build a graphical simulator for visual analysis.
The rest of this paper is organized as follows: Section 2 presents the research problems, challenges, and related works. We discuss the framework of our developed solution in Section 3. Section 4 describes the formal model of the constraints and requirements. The implementation details and a case study are presented in Section 5. The evaluation results of the implemented tool is presented in Section 6. Finally, we conclude the paper in Section 7.
2 Background
In this section, we discuss the research problem, the challenges associated with it, and the related works.
2.1 Research Problem
A UAV swarm is a network of UAVs that can communicate with each other (mostly following the ad-hoc wireless networking) and usually perform a common task, autonomously or with the instructions from operators. It is important to maintain appropriate trajectories for all the UAVs in a network in order to avoid mid-air-collision or restricted areas (e.g., adverse territory or restricted private locations). It is also required to maintain successful communication between the neighboring UAVs and cover the surveillance points within a time constraint. In this research, we propose a formal framework that plans for the trajectories of the UAVs in a swarm, so that all or at least a fraction of the points near the data sources are covered within a given period. The coverage requirement may ensure that at least one of the available UAVs should cover each data point once or at each operator-specified time interval within the period. The resiliency specification considered in this research states that even if a certain number ( or ) of UAVs fail to operate due to technical failures or cyberattacks, the surveillance goal is still fulfilled. In other words, the trajectory plan for the remaining UAVs can still securely surveil the required percentage of the data points.
Fig. 1 presents two sample trajectories for two different UAVs. They collect the available data in a combined way. The figure shows the starting points for both the UAVs, as well as the positions or waypoints from where they can collect the data. In our research problem, we consider a set of points in the three-dimensional space where the UAVs can travel, as well as subsets of the points where data is available and where traveling is forbidden.

2.2 Research Challenges
A swarm of UAVs is deployed to collect data over an area from a set of predefined sensors planted on the ground. The sensors are located on the plane of the three-dimensional Euclidean space with , , and axes. There are multiple points with coordinates, of which some are directly above the data sensors or near to them from where the UAVs can collect the transmitted data. Higher value denotes points with higher altitude. A subset of the points are restricted, which must be avoided during the flight. Designing trajectories of all the UAVs so that the budget and time restrictions are met, they do not collide with one another, avoid restricted areas, and still perform the desired data collection surveillance is a multi-objective problem (NP-hard). We use satisfiability modulo theories (SMT) to solve this problem and generate the trajectories in the 3D space that satisfies all the constraints and requirements.
2.3 Related Works
There are several works in the literature that provides solutions to the problems of path projection and path planning for UAVs. For example, Tisdale et al. proposed a mechanism to perform path planning while minimizing the uncertainty in sensing missions by considering a blend of online sensor models and estimation objectives [6]. Yeung et al. proposed two heuristic-based techniques to find an optimal route of aerial vehicles so that the original target and waypoints are not affected [4, 7]. They also consider the flight maneuvering constraints of the UAVs and keep the deviation from the original route to a minimum while maximizing the number of sensor tasks from the ground. They also consider the time deadlines to cover the taskpoints and maintenance of QoS. Mekala et al. proposed a similar method to generate the flight trajectory, which is a collection of predefined waypoints [8]. They also propose an algorithm to optimize the flight path. Liu et al. studied the age-optimal trajectory planning in UAV-enabled wireless sensor networks [9]. They ensure that the age of the data collected from different sensor nodes is bounded by a threshold. They proposed a dynamic programming method and a genetic algorithm-based method.
Beard et al. designed semi-autonomous UAVs and proposed their graph-based approach to path planning and trajectory generation [10]. Ceccarelli et al. developed a path planning model for micro UAVs to obtain video footage of a set of known targets [11]. In the presence of constant winds, they find the best selection of waypoints for achieving the reconnaissance goals. A pheromone model, where the movement of a group of UAVs is guided by pheromone, was proposed by Kuiper et al. [12]. This model performs well in reconnaissance.
A two-step algorithm was proposed by Bortoff to obtain a path for UAVs traveling through unauthorized sites [13]. The algorithm performed a trade-off between the shortest path for traveling and avoiding radars. A trajectory design with the aid of an iterative algorithm was proposed by Wu et al. where aerial base stations for a wireless communication system on the ground were mounted on the UAVs [14]. Bagherian proposed a genetic and particle swarm algorithm to generate the optimal three-dimensional path planning in an adverse environment [15]. They considered the terrain information and the kinematic constraints of the UAVs.
Tsourdos et al. presented a Kripke model for UAV path planning to cope with uncertainties and decision making involved in the process of collaboratively reaching the goal while covering a certain area of interest, avoiding obstacles [16]. They modeled the collision avoidance with the help of conditions such as minimum separation and non-intersection of paths at equal length. Their model can find the shortest path for each UAV. Ruz et al. proposed a Mixed Integer Linear (MILP)-based solution which modifies the A* algorithm to optimize paths in dynamic environments where pop-ups appear according to a known future probability and need to be avoided [17]. Their ILP model can choose the most suitable trajectory among different alternatives provided fuel and time constraints. The authors also presented a similar approach to trajectory optimization for UAVs in the presence of obstacles, waypoints, and risk zones in another research [18]. Jakaria et al. presented a formal model for verification of a resilient communication in a UAV swarm while maintaining safe flight trajectories for all the UAVs [1, 19]. Jameson proposed a fuel consumption algorithm for UAVs that addresses the additional fuel requirements issue in the Aviation Weather Routing Tool (AWRT) developed by the Army Research Laboratory [20]. They developed a prototype algorithm that computes the ground speeds along the different mission segments, fuel consumed, and fuel remaining while rerouting during adverse weather conditions.
Chen et al. optimized the trajectory of quad-rotor UAVs in collaborative environments [21]. They proposed a hierarchic optimization technique to solve the trajectory optimization problem of quad-rotor UAVs. Sun et al. created a trajectory-tracking controller where the autopilot is involved in the feedback control loop [22]. They proposed a generalized trajectory design model using Lyapunov based backstepping. Fadlullah et al. proposed a simple trajectory control algorithm for UAVs that manages the throughput of UAV-aided networks, where UAVs work as network nodes [23]. Kvarnstrom et al. presented a framework for UAV mission planning that combines ideas from forward-chaining planning and partial order planning [24]. They met the requirements of centralization, abstraction, and distribution of task assignments. Bethke et al. proposed a health management system for UAV teams that perform persistent surveillance [25]. Their methodology for planning missions can anticipate the negative effects of various types of anomalies on future mission states, as well as choosing actions to mitigate the effects.
However, none of these works present the path planning for resilient coverage of data points. We consider the resiliency of the planned trajectories, which ensures a certain coverage of the data sources with a certain frequency of timely visits of multiple UAVs. We solve an NP-hard problem [26], which involves trajectory synthesis while satisfying multi-objective constraints such as budget and maneuvering limitations, and operator requirements, such as resilient coverage.
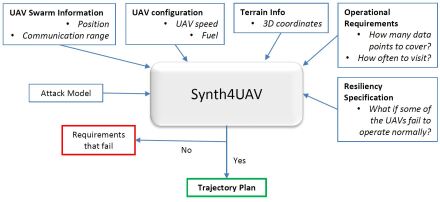
3 Synth4UAV Framework
We develop Synth4UAV, a formal model-based tool that creates a trajectory plan for each UAV of a UAV swarm, where a trajectory is a sequence of waypoints through which the UAV will fly. The trajectory depends on current positions of the UAVs, their velocity, climb angle, and turn angle, etc. Different UAVs may have different speeds, which are assumed to be constant throughout their flight time while performing the surveillance. The UAVs can start from different base stations. For a time period (represented as a series of time steps), the trajectory is modeled. Within a unit time step, the UAVs will not alter their flight parameters. The output trajectory is a set of coordinates in the 3D space, along with the climb angle and turn angle in each step. We model the fuel consumption where a UAV starts traveling with a certain amount of fuel and returns to a base station for refueling if needed.
Fig. 2 presents the framework of Synth4UAV. The framework takes necessary inputs, such as the UAV swarm and individual UAV properties, terrain information, and data coverage requirements. The swarm information includes the number of UAVs, initial positions of the UAVs, as well as their speeds and directions. Surveillance requirements specify the points to visit and the characteristics/constraints associated with these visits. The formal model is eventually solved using SMT logic/solver, to identify the trajectory plan (e.g., the flight angles), satisfying the requirements and constraints of the surveillance. Our trajectory planning considers necessary invariants. For example, the climb and turn angles must be within the (practical) capacity of a UAV.
4 Model
This section provides the formal modeling of the requirements and the constraints of the UAV trajectory planning. Table 1 lists several variables used in the model. It is notable that no multiplication of two parameters is performed in the paper without the multiplication sign.
4.1 Preliminary of Model
To model the trajectory planning for the UAVs, we consider a set of predefined points (waypoints) in the three-dimensional space. Each point is considered to have Cartesian () coordinates in the Euclidean space. The UAVs start and end their flights at certain points, which are generally base stations or fueling stations. Between the starting and ending points, the UAVs may visit several other points. All these points constitute the trajectories for all the available UAVs. Our basic intention is to automatically generate these trajectories such that certain constraints and requirement goals are met. Here we formally model the route constraints, as well as the requirements of the users of the implemented tool. We make sure that the points containing the data sensors are covered with certain resiliency specifications. In other words, even if some of the UAVs fail to operate normally to visit certain data points, the points are still covered by others so that the data is collected efficiently.
| Notation | Definition |
|---|---|
| Boolean representing movement of UAV from point to | |
| Boolean representing that UAV has visited point | |
| Boolean representing the possibility of traveling from point to | |
| Real expression denoting the cost of fuel for UAV for reaching point | |
| Real expression denoting the time taken by UAV to reach point since its starting point | |
| Integer expression denoting the time a UAV hovers over point |
4.2 Modeling UAV Movement
If denotes whether UAV moves from to , UAV has already visited point . This is denoted by . Also it must be possible for the UAVs to travel from point to . In other words, there should be a link between point and point , which is denoted by .
| (1) |
We define the Boolean variable as true only if the distance between point and () is within a certain threshold, . The threshold is specified by the properties of UAV .
| (2) |
The UAVs have certain maneuvering constraints. We consider the restrictions on the turn angle and the climb angle in three-dimensional space [15]. The turn angle is the angle that a UAV has to turn with respect to the existing direction on the horizontal plane. We first calculate the angle for a UAV for going from to and the existing angle which the UAV is following to reach from . Then we calculate the deviation which the UAV has to turn. Similarly, we calculate the climb angle on the vertical plane. Fig. 3 shows an example scenario of moving from one point to another in the three-dimensional space. is the turn angle for moving from point to , provided the direction of a UAV at is parallel to the axis. is the climb angle. Fig. 3 also provides the formulas for calculating the angles based on the horizontal and vertical movements.
The deviation of turn angle to reach from , given a UAV reached from is represented by , while the deviation of climb angle to reach from , given it reached from , is denoted by . The deviations must be within certain thresholds ( and ). If this is satisfied, then we can say that there is a link that a UAV can move.
| (3) |
Similarly, if a UAV moves from to followed by , then the deviation of the turn angle and climb angle to move from the path to and the path to should be within user-defined thresholds.
| (4) |

A UAV visits a particular point from one of its neighboring points. If UAV has visited the point , that means it has traveled from one of the neighboring points, .
| (5) |
The starting point is the first point on the trajectory of any UAV. If the current point that a UAV is visiting is the starting point, then it has not come from any other point . This can be presented by the following equation:
| (6) |
If a UAV has reached the destination point , it should not move to anywhere from there. This is represented by the following equation:
| (7) |
A UAV can travel to a certain point only from another point (not from multiple points). If a UAV has moved from to , then it should not have come from any other point .
| (8) |
Similarly, from any particular point, a UAV can only travel to one point and not multiple points. If UAV goes from to , then it must not have gone to any other point from . This is formally represented as the following:
| (9) |
A UAV must visit the starting point and the destination point . This is true for all the collaborating UAVs in the network and is presented by the following:
| (10) |
Some of the points where the UAVs can go are in close proximity to the data collecting sensors. These points need to be visited by the UAVs so that they can collect the data. If is the set of all the points that have data-points, then at least a threshold () fraction of all the data-points must be visited by the UAVs during their journeys towards the destination.
| (11) |
Some of the points in the three-dimensional space may have to be avoided by the UAVs while making their journeys, for these points may currently reside in restricted zones. If denotes the set of all the forbidden points that should be avoided, then no UAV should visit them.
| (12) |
4.3 Modeling UAV Fuel Consumption and Cost
While calculating the fuel consumption, we not only consider the distance but also consider the turn and climb angles for going from a certain point to another. The direction of the turn angle has no effect on fuel consumption, but the direction of the climb angle does affect the amount of fuel consumption. If a UAV is going up against gravity, then it has to burn more fuel. On the other hand, if it is going down, then less fuel is required. We provision a positive climb angle if the UAV is going up with respect to its current direction, while it is counted as negative if it is doing downwards. If is the distance between point and , denotes the turn angle of UAV for going to from , is the climb angle to move, and is the fuel consumption rate (e.g., mpg) of a UAV , then the required fuel, , is calculated as follows:
Here, and are simple constants that regulate the impact of turn and climb angles, respectively, of the UAV. The fuel usage does not depend on the direction of the turn angle , while it directly depends on the direction of the climb angle . If the UAV is moving to a point located at a lower altitude than the source point, then it is traveling with gravity. As a result, there is less usage of fuel. On the other hand, if it has to travel against gravity, then fuel usage increases.
If is the cost of per unit fuel, then the cost, , for a UAV for moving from to is calculated as follows:
The cumulative cost for traveling to point for UAV is the cost up to the previous point , plus the cost to move from to , .
| (13) |
If is the starting point, the cost at the starting point for any UAV should be zero.
| (14) |
4.4 Modeling UAV Travel Time
We assume a constant speed for each UAV while it is making its flight from a point to another particular point. is the time taken by UAV to move from to if is the speed of the UAV. This is calculated as follows:
is the time taken by UAV to reach up to from the starting point. is the time of hovering of UAV at a previous point . We consider this hovering time to be either or , for simplicity. A UAV may or may not hover over a point depending on the requirement of avoiding collision.
| (15) |
| (16) |
If is the start time, then it is the time for all the UAVs at the starting point .
| (17) |
The following constraint ensures that no two UAVs visit the same point at the same time. This restriction is required to avoid collision between any two UAVs.
| (18) |
In fact, there should be a threshold time difference between the times of visit of any two UAVs to a certain point. If both UAVs and visit the same point , then there must be some time difference between their visits to avoid mid-air collision.
| (19) |
4.5 Modeling User Requirements
One of the objectives of the trajectory planning model is to keep the budget within a limit. We consider the budget or cost limit for each UAV to be , while is the budgeted time or time boundary within which the flights need to be performed. The cost of the fuel by UAV should be less than a user-specified budget, .
| (20) |
Each UAV should reach the destination point from the starting point within a certain time limit, .
| (21) |
Again, a point cannot be reached by the UAVs by taking more cost than the budget or the time allows. If a UAV visits point , then the cost for reaching up to that point should be less than the budget.
| (22) |
The time taken in reaching any point should be within the time limit.
| (23) |
4.6 Modeling Resiliency Specifications
Our trajectory modeling considers resiliency with respect to attack/contingency scenarios. The satisfaction of the resiliency specification provides resilient trajectory plans. The resiliency specification is stated such that at least a certain percentage (%) of the surveillance points are (securely) covered by a set of UAVs (Equation 27), even if a certain number () of UAVs among them fail to operate or are compromised.
We abstract the resiliency requirement by introducing constraints on surveillance requirements. If is a data point () and it satisfies the resiliency data collection, then at least number of UAVs must visit (collect data at) this point during their travel to the destination. That is, to provide a single () UAV failure resiliency to a surveillance point, two () UAVs will need to visit the point. If specifies that if point is under resilient surveillance, we can formalize the above resiliency requirement as follows:
| (24) |
The resilient trajectory design often needs to satisfy further requirements. A requirement can be data freshness or closeness constraint that ensures that the times at which data is collected by UAVs at a data point should not be apart from one another more than a threshold value (say ), so that the collected data records can be verified for any discrepancy. We call such a data point to be under resilient surveillance. Such a constraint may differ for different data points based on the data change frequency (which may depend on the data type, location, etc.) and/or the criticality of the data. This constraint ensures that even if UAVs fail to visit a point , there is at least a UAV , which along with another UAV will cover this point. This constraint is formalized below:
| (25) |
Here, specifies that if UAVs and visit point , then the visiting times ( earlier than , required for ordering with respect to the visiting time) are no more than the threshold time apart. This is defined as follows:
| (26) |
We need to make sure that at least a certain percentage (%) of the data points are covered by the UAVs such that the points follow the resiliency property.
| (27) |
5 Implementation and A Case Study
In this section, we present the implementation details of our proposed model. We also present a detailed case study for further explaining how the model works. The main objective of our configuration synthesis problem is to synthesize the trajectories of the UAVs by satisfying various requirements, as well as the user’s business and operating constraints. The synthesis problem is formalized as the satisfaction of the conjunction of all the constraints in the equations of Section 4.
5.1 SMT Encoding and Target Variables
We implement Synth4UAV by encoding the above formal model into SMT formulas [27]. In this encoding purpose, we use Z3, an efficient SMT solver [28]. The solver checks the verification constraints and provides a satisfiable (SAT) result if all the constraints are satisfied. The SAT result provides a SAT instance, which represents the value assignments to the parameters of the model. According to our objective, we are mainly interested in the assignments to the following variables: (i) the decision variable referring to whether a UAV has visited a particular point , and (ii) the variable denoting whether a UAV travels from a point to , . We can retrieve the trajectories for all the UAVs with the values of these two variables. The assignments of the variables are printed in an output text file. The values of other variables such as can provide information on which point was traveled at what time, while can tell about the fuel cost associated with traveling up to certain points. Appendix B presents an excerpt from the generated z3 code. It shows a few of the expressions that assert the constraints according to our trajectory synthesis model.
Throughout the model of the network synthesis, for simplicity, we have used the sum of Boolean variables several times for formally modeling the constraints. While encoding the summation of Boolean variables, we have created corresponding integer variables ( or ) and used their sum for calculation.
5.2 Optimal Trajectory Synthesis
The synthesis result represents a comprehensive trajectory plan for the UAVs to perform the intended tasks. There is usually more than one satisfiable model that can satisfy the constraints. These models will provide different costs and times for the overall process, although all of them will be less than the budgeted cost () and time (). We can choose the most cost- and time-efficient trajectory plans among all alternative satisfiable models for the same set of constraints. We use Algorithm 1 which updates the minimum () and maximum () values of the budget, and finds the optimal trajectory plan. Their values are used to update , which is used to try for a more optimal solution. Initially, is set to the initial user-defined budget () and is set to zero. We use a binary search-based method to find the optimal budget.
However, finding the optimal solution using the algorithm usually requires more time than a single satisfiable model. The algorithm requires several invocations of the model solver and often confronts UNSAT results, which usually take a longer time. The time complexity of this algorithm becomes , where is the time for one model solution and is the difference between and . The user can control the number of iterations of the model () and generate a sub-optimal solution if required.
5.3 Trajectory Smoothing
The synthesized trajectories can be smoothed by applying a 3D Bezier curve interpolation [26]. Careful studies need to be done to make sure that the smooth trajectories remain adequately close to the data sources so that the UAVs and the sources are within range of each other. While this is out of the scope of this research, we leave it for our future works.
5.4 An Example Case Study
UAVs can be used to collect data from sensors deployed in remote points, which is essentially an alternative to the use of UAVs in a surveillance purpose. This is efficient technology when it is not feasible (either technically or economically) to deploy necessary communication infrastructures. If sensors cannot transmit data by themselves to the data center due to the lack of proper infrastructure or energy-saving purposes, UAVs are convenient options to collect data from them. We need to make sure that a certain percentage of the points with sensors are covered by the set of UAVs, even if a certain number of UAVs fail while in flight.
In this case study, we consider 30 waypoints in the three-dimensional coordinate space, of which 15 contain data sources. The coordinates are depicted in the input file presented in Appendix A. For example, (100, 100, 0), (500, 1000, 100), (500, 2000, 100), etc. are some of the points that the UAVs can travel to. In other words, these points may or may not be parts of the trajectories of the UAVs. The indices of the data points are provided from the input file. The start point and end point of the UAV trajectories are specified, which can be the coordinates of base stations. In this case, point 1 is the starting point and point 18 is the ending point for all the UAVs. There are four forbidden points, 6, 14, 19, and 30, which should be avoided by the UAVs while flying from the starting point to the ending point.
We consider 5 UAVs. The average velocity, mileage, and angle with axis (at the beginning) of the UAVs are also provided. The restrictions of turn and climb angles (in degrees) of the UAVs while moving from one point to another are given in the input file. We consider the deviation of the moving direction of the UAVs. That is, after a UAV reaches a particular point, how much it can deviate from its current trajectory both vertically and horizontally in order to move to the next point.
A Satisfiable Case: The data coverage threshold is selected to be 80% in this case study. That means, at least 80% of the data points must be covered by the UAVs while they are making their journeys. The data freshness threshold specifies the time (in seconds) within which a certain number of UAVs must visit a data point to ensure the freshness of the data. At the beginning of this case study, we consider this to be 20 sec. At this point, we consider the value of to be 2, while the resilient data coverage is chosen to be 70%. This means there should be at least 70% of the data points, such that they are covered by at least UAVs every 20 seconds. We also need to make sure that at least 70% of the data points are covered by a minimum of UAVs.
The price of fuel is provided in the input file. The available budget and the total available time within which the UAVs need to finish their task by traveling from the start point to the end point are also provided. For the first run of the tool in this case study, we consider a budget of $6000, and the total allowed time is chosen to be 2000 sec.
Now we try to solve this multi-objective problem in order to find the trajectories of the UAVs. The solution should provide the paths for each of the UAVs that satisfy all the conditions mentioned in Section 4. In this case, the solver gives a SAT result. The result is printed in an output file, which is presented in Appendix A. The output file provides the times at which the UAVs visit each of the points on their trajectories. For example, UAV 1 is at point 1 at the beginning (0 sec), it is at point 2 at 20.79 sec, at point 3 at 41.79 sec, and so on. If a UAV needs to hover over any point to avoid a mid-air crash, the time of hovering is also presented in the output file. The output also provides the trajectories. For example, UAV 1 visits the following points during its journey in sequence: 1, 2, 3, 27, 29, 21, 20, 12, 11, 13, 16, 17, and 18. Similarly, the trajectories of all other UAVs are printed. Fig. 4 presents a top view of the overall trajectory plan for 3 of the 5 UAVs on the plane. The data points are colored green, while the forbidden ones are red. All other points are colored blue. All of the UAVs start from waypoint 1 and end their flight at waypoint 18. During their flights, they cover the points that have the data sources with the required resiliency.

An Unsatisfiable Case: For the next run, we increase the value of to 3. In this scenario, the solver provides an UNSAT result, which means there is no satisfiable solution to the problem, and there cannot be any trajectory for the UAVs unless some conditions are modified. Increasing the budget, number of UAVs, etc. may provide us with a SAT result.
6 Evaluation






In this section, we present the evaluation of the proposed framework for synthesizing the UAV trajectories.
6.1 Methodology
We create synthetic problem sets in a three-dimensional Cartesian space, where there are different points indicating the probable points for UAVs to fly. We randomly specify some data points (50-80% of all the points), which must be covered by the UAVs while performing their flights from a pre-specified starting point to an end point. There are several forbidden points in the space as well, indicating the areas of geographical obstacles or unauthorized zones.
We run the tool that implements the formal model on a Windows 10 machine equipped with an Intel Core i5 processor and 12 GB of memory. We change different parameters of the model from the input file and observe the scalability of the tool, as well as the relationships between the parameters. The evaluation heavily depends on the placement of the available points in the 3D space and the allowed ranges of the UAVs. The maximum allowed turn angle and climb angle are chosen according to the placements of the points.
6.2 Relationship between Different Parameters
We present the relationship among different parameters in Fig. 6 and 7. We observe the maximum coverage produced by a SAT result while varying the budget for each UAV in Fig. 5. We present the analysis for two cases: one with 2 UAVs and the other with 4 UAVs while allowing adequate time for coverage. It is obvious that more points can be covered by the UAVs if there is more budget for fuel. If we use more UAVs, then we can cover 100% of the data points with less budget per UAV. For example, if we use 2 UAVs, then we can cover 77% of the data points with a budget of $700 per UAV. On the other hand, using 4 UAVs with the same budget allows us to cover all the data points.
In Fig. 5, we present the coverage time of the data points for the different numbers of UAVs. We show results for the requirement of 40% coverage and 60% coverage. If there are more than 1 UAVs, they reach the destination point at different times, as they may have different speeds and are not allowed to visit the same point at the same time. We take the time required by the last UAV to reach the destination. We can observe that the required time decreases slowly if we have more UAVs to cover our intended percentage of data points.
We present the minimum number of required UAVs to cover different percentages of the data points in Fig. 6. As we increase our requirement of coverage, the minimum number of required UAVs also increases if we keep the budget cost per UAV, and the total budgeted time constant. We show the results for two problem sets: one with 50 points and another with 90 points.
The change in the percentage of coverage with respect to the budgeted time is presented in Fig. 6. This is the maximum total time allowed for all the UAVs to reach the end point of their trajectories. We show two cases for 2 UAVs and 5 UAVs for a total of 100 points and 40 data points. We keep the values of and as 2 and 3, respectively. We can observe that as the allowed time increases, more of the data points can be covered. The higher number of UAVs means that more of the data points can be covered. For a budgeted time of 1800 sec, 5 UAVs can visit all the data points and reach the final point on their trajectories.
Next, we present the minimum required budget per UAV while varying the number of data points in Fig. 7. We keep the total number of points, required coverage, the values of and , etc. unchanged for this evaluation. The minimum required budget is the budget for which the solver returns a SAT answer, which means that trajectories are possible. As expected, the required budget increases with the increment of the number of data points.
The minimum required budget per UAV with the change of the value of is presented in Fig. 7. We can observe that with the increment of , the required budget increases quickly. As the value of increases, higher numbers of UAVs need to cover more data points, which results in the complex trajectories of the UAVs. Hence, a bigger budget is required to cover the fuel cost of the UAVs.





6.3 Scalability
We present the scalability of our developed tool based on the formal model discussed earlier in Fig. 8 and 10. Fig. 8 shows the trajectory synthesis time for different sizes of the problem space. We vary the number of points in 3D space and observe the time required to obtain the trajectory plan. We can observe that the required time increases with the increment of the number of points. As we have more points in the problem space, the solver requires to solve more constraints, which leads to the almost linear increment of synthesis time. We can also observe that the UNSAT cases require more synthesis time than the SAT cases.
In Fig. 8, we show the required synthesis time by varying the number of UAVs. We show two cases for two problem sizes: 60 points and 90 points. In these cases, we keep the required percentage of coverage and other parameters constant. We observe that as the number of UAVs increases, the required synthesis time also increases. In the case of 90 points, the number of clauses to satisfy the problem increases quickly with the increment of UAVs. As a result, the time also increases quickly.
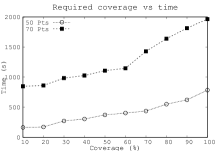
We present the trajectory synthesis time by varying the required coverage of the data points in Fig. 9. As the requirement to cover more points grows, the synthesis time also increases. For larger problem sets, the time grows quickly, as more constraints are needed to be satisfied.
The required verification time with respect to the number of data points is observed in Fig. 9. We show the time for two cases: one which is for a total of 50 points, and another is for 80 total points where the UAVs can go. We keep all other parameters constant. For example, the required coverage is kept constant at 80%, the value for is 2, while is kept at 3. We can observe that the verification time increases slowly with the increment of the number of data points for a certain problem size (number of total points). This is because, with the increment of data points, the UAVs need to make sure to visit more points, and the solver needs to solve a more strict set of constraints; however, the number of clauses does not increase drastically.
Next, we present the verification time by varying the value of , which is the minimum number of UAVs that need to visit at least a certain percentage of data points. We can observe that the required time increases quickly as increases. However, the increment rate is less than the case of increasing . This is because the solver needs to verify less strict conditions when increases than when increases.
Fig. 10 presents the change in verification time with the change of the value of , which is the minimum number of UAVs visiting a certain percentage of the data points while visiting them at a certain time difference. We keep other parameters, such as the number of UAVs and total points, required coverage, etc., constant and show the results for 30 data points and 50 data points. As the value of increases, the verification time increases rapidly. With the increment of , the constraints become strict very quickly, as the solver needs to find more complex trajectories for the UAVs so that they can visit more points.
6.4 Graphical Simulator
We developed a simulator program to verify the effectiveness of the trajectory generation tool. The simulator is developed in Unity 3D [29]. A user of the simulator can specify the coordinates of the possible waypoints in a three-dimensional space. The simulator reads the number of UAVs and their properties, such as speed, mileage, turning angle constraints, etc., from a user-provided input file. The trajectories are provided based on the output of the trajectory generator. The times of reaching each waypoint on their trajectories, hovering times, etc. are also provided to the simulator. When started, the simulator shows the movement of the UAVs according to its input and proves the effectiveness of the trajectory generator by showing that the UAVs do not collide, but collectively collect the required data and complete the job before the deadline in order to prevent fuel outage, as well as satisfy the resiliency requirements. Appendix C provides further information on this simulator, including a screenshot of the interface.
7 Conclusion
UAVs are increasingly used in surveillance, as well as data collection from remote sensors. In this paper, we have developed Synth4UAV that can automatically generate the efficient trajectories of a set of UAVs to perform their intended tasks collaboratively. We have considered the routing and maneuvering constraints, budget and time constraints, and the resiliency requirements of the data collection process. We have designed the trajectory planning, which is a combinatorially hard problem, as an SMT-based constraint satisfaction problem, the solution of which generates the trajectories that the UAVs should follow. We have analyzed the relation between different design factors like data coverage, swarm size, budget, resiliency, etc. The evaluation results have proved the scalabiity of Synth4UAV.
References
- [1] AHM Jakaria and Mohammad Ashiqur Rahman. Formal analysis of k-resiliency for collaborative uavs. In 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), pages 583–592. IEEE, 2018.
- [2] Chung Deng, Shengwei Wang, Zhi Huang, Zhongfu Tan, and Junyong Liu. Unmanned aerial vehicles for power line inspection: A cooperative way in platforms and communications. J. Commun, 9(9):687–692, 2014.
- [3] Ahmed EAA Abdulla, Zubair Md Fadlullah, Hiroki Nishiyama, Nei Kato, Fumie Ono, and Ryu Miura. An optimal data collection technique for improved utility in uas-aided networks. In INFOCOM, 2014 Proceedings IEEE, pages 736–744. IEEE, 2014.
- [4] San Yeung, Sanjay Kumar Madria, Mark Linderman, and James Milligan. Routing and scheduling of spatio-temporal tasks for optimizing airborne sensor system utilization. In Proceedings of the 10th ACM Intl. Conf. on Distributed and Event-based Systems, pages 145–152. ACM, 2016.
- [5] Leonardo De Moura and Nikolaj Bjørner. Satisfiability modulo theories: introduction and applications. Communications of the ACM, 54(9):69–77, 2011.
- [6] John Tisdale, Zuwhan Kim, and J Karl Hedrick. Autonomous uav path planning and estimation. IEEE Robotics & Autom. Mag., 16(2), 2009.
- [7] San Yeung, Sanjay Kumar Madria, and Mark Linderman. A trajectory recommendation system via optimizing sensors utilization in airborne systems (demo paper). In International Symposium on Spatial and Temporal Databases, pages 508–513. Springer, 2015.
- [8] Amarender Reddy Mekala, Sanjay Madria, and Mark Linderman. Aerial vehicle trajectory design for spatio-temporal task aggregation. In Unmanned Aircraft Systems (ICUAS), 2016 International Conference on, pages 1085–1094. IEEE, 2016.
- [9] Juan Liu, Xijun Wang, Bo Bai, and Huaiyu Dai. Age-optimal trajectory planning for uav-assisted data collection. arXiv preprint arXiv:1804.09356, 2018.
- [10] Randal W Beard, Derek B Kingston, Morgan Quigley, Deryl Snyder, Reed Christiansen, Walt Johnson, Timothy W McLain, and Michael A Goodrich. Autonomous vehicle technologies for small fixed-wing uavs. JACIC, 2(1):92–108, 2005.
- [11] Nicola Ceccarelli, John J Enright, Emilio Frazzoli, Steven J Rasmussen, and Corey J Schumacher. Micro uav path planning for reconnaissance in wind. In American Control Conf., 2007. ACC’07, pages 5310–5315. IEEE, 2007.
- [12] Erik Kuiper and Simin Nadjm-Tehrani. Mobility models for uav group reconnaissance applications. In Wireless and Mobile Communications, 2006. ICWMC’06. International Conf. on, pages 33–33. IEEE, 2006.
- [13] Scott A Bortoff. Path planning for uavs. In American Control Conference, 2000. Proceedings of the 2000, volume 1, pages 364–368. IEEE, 2000.
- [14] Qingqing Wu, Yong Zeng, and Rui Zhang. Joint trajectory and communication design for multi-uav enabled wireless networks. IEEE Transactions on Wireless Communications, 17(3):2109–2121, 2018.
- [15] M Bagherian and A Alos. 3d uav trajectory planning using evolutionary algorithms: A comparison study. The Aeronautical Journal, 119(1220):1271–1285, 2015.
- [16] Antonios Tsourdos. A formal model approach for the analysis and validation of the cooperative path planning of a uav team. 2005.
- [17] José J Ruz, Orlando Arévalo, Gonzalo Pajares, and M Jesús. Decision making among alternative routes for uavs in dynamic environments. In Emerging Technologies and Factory Automation, 2007. ETFA. IEEE Conference on, pages 997–1004. IEEE, 2007.
- [18] Jose J Ruz, Orlando Arevalo, Gonzalo Pajares, and M Jesus. Uav trajectory planning for static and dynamic environments. In Aerial Vehicles. InTech, 2009.
- [19] AHM Jakaria and Mohammad Ashiqur Rahman. Safety analysis for uav networks. In 2018 IEEE/ACM Third International Conference on Internet-of-Things Design and Implementation (IoTDI), pages 294–295. IEEE, 2018.
- [20] Terry Jameson. A fuel consumption algorithm for unmanned aircraft systems. Technical report, Army Research Lab White Sands Missile Range NM Computational And Information Science Directorate, 2009.
- [21] Yongbo Chen, Jianqiao Yu, Yuesong Mei, Siyu Zhang, Xiaolin Ai, and Zhenyue Jia. Trajectory optimization of multiple quad-rotor uavs in collaborative assembling task. Chinese Journal of Aeronautics, 29(1):184–201, 2016.
- [22] Liang Sun and Randal W Beard. Trajectory tracking for unmanned aerial vehicles with autopilot in the loop.
- [23] Zubair Md Fadlullah, Daisuke Takaishi, Hiroki Nishiyama, Nei Kato, and Ryu Miura. A dynamic trajectory control algorithm for improving the communication throughput and delay in uav-aided networks. IEEE Network, 30(1):100–105, 2016.
- [24] Jonas Kvarnström and Patrick Doherty. Automated planning for collaborative uav systems. In Control Automation Robotics & Vision (ICARCV), 2010 11th International Conference on, pages 1078–1085. IEEE, 2010.
- [25] Brett Bethke, Jonathan P How, and John Vian. Group health management of uav teams with applications to persistent surveillance. In American Control Conference, 2008, pages 3145–3150. IEEE, 2008.
- [26] Ozgur Koray Sahingoz. Generation of bezier curve-based flyable trajectories for multi-uav systems with parallel genetic algorithm. Journal of Intelligent & Robotic Systems, 74(1-2):499–511, 2014.
- [27] Leonardo de Moura and Nikolaj Bjørner. Satisfiability modulo theories: An appetizer. In Brazilian Symposium on Formal Methods, 2009.
- [28] Leonardo De Moura and Nikolaj Bjørner. Z3: An efficient SMT solver. Tools and Algorithms for the Construction and Analysis of Sys, pages 337–340, 2008.
- [29] Unity 3D. https://unity.com//.
Appendix A Input and Output to the Case Study
| # Number of waypoints |
| 30 |
| # UAV x-coordinates |
| 100 500 500 1000 1000 2000 2000 2000 2500 3000 3000 3000 4000 4500 4500 5000 5500 6000 1000 2700 2000 500 2000 3500 5000 4000 500 5500 1500 3500 |
| # UAV y-coordinates |
| 100 1000 2000 500 2000 500 1500 2500 2000 1000 1500 2500 1500 1000 2500 2000 1500 2000 3000 3400 4000 3500 2000 3500 3500 3000 3000 500 3500 4000 |
| # UAV z-coordinates |
| 0 100 100 200 250 200 150 150 200 200 200 200 200 200 200 200 150 200 200 200 200 200 200 200 200 200 150 100 50 0 |
| # Number of UAVs |
| 5 |
| # UAV velocities (m/s) |
| 50 48 49 51 52 |
| # UAV mileage (mpg) |
| 10 12 11 10 12 |
| # Initial UAV angles (degree with x-axis) |
| 0 |
| # Turn angle threshold |
| 90 |
| #Climb angle threshold |
| 30 # Source, Destination |
| 1 18 |
| # Forbidden points |
| 4 |
| 6 14 19 30 |
| # Points with data sources |
| 15 |
| 2 3 5 9 10 13 20 12 16 18 29 8 26 7 22 |
| # Data coverage threshold (%) |
| 80 |
| # Data freshness threshold (sec) |
| 20 |
| # resiliency |
| 3 |
| # Resilient data coverage threshold (%) |
| 70 |
| # Fuel price ($/gal) |
| 3 |
| # Time constraint (sec) |
| 2000 |
| # Cost constraint ($) |
| 6000 |
Table 2 lists the input file for the trajectory generator tool for the example case study in Section 5.4. The file includes the number of waypoints, the Cartesian coordinates of the points in the three dimensional space, the number of UAVs that will be considered, along with their velocities, mileages, etc. It also includes the initial direction of the UAVs with x axis, the thresholds on turn and climb angles. The source and destination points, the forbidden points which the UAVs should avoid, and the points that are on top or in close proximity of the data sources are also supplied in the input file. The data coverage threshold specifies percentage of the data points that need to covered by the UAVs collectively. The required resiliency specifications are also provided in the input file. The time constraint or the deadline and the available cost constraint or the budget are also supplied.
| #Required verification time: 336.77 | |||
| #We have a solution | |||
| UAV | Point | Time | Hover |
| 1 | 1 | 0 | 0 |
| 1 | 2 | 20.79898987 | 1 |
| 1 | 3 | 41.79898987 | 0 |
| 1 | 27 | 62.82397427 | 0 |
| … | … | … | … |
| 1 | 17 | 194.898209 | 0 |
| 1 | 18 | 209.0756559 | 0 |
| … | … | … | … |
| 4 | 1 | 0 | 1 |
| 4 | 4 | 19.7056384 | 0 |
| 4 | 5 | 38.7084393 | 1 |
| … | … | … | … |
| #All trajectories: | |||
| UAV | Src | Dest | |
| 1 | 1 | 2 | |
| 1 | 2 | 3 | |
| 1 | 3 | 27 | |
| 1 | 27 | 29 | |
| … | … | … | |
| 1 | 21 | 20 | |
| 1 | 20 | 12 | |
| 1 | 12 | 11 | |
| … | … | … | |
| 4 | 1 | 4 | |
| 4 | 4 | 5 | |
| … | … | … | |
Table 3 presents the contents of the output file generated by the trajectory generation tool. As can be seen from the output file, it provides the waypoints on the trajectories of all the UAVs. It also provides the times when the UAVs should reach the waypoints and the time of hovering at those points.
Appendix B Sample Z3 Code
Table 4 presents a short listing of the z3 code generated by the trajectory generation tool. It shows a few of the expressions that assert the constraints according to our constraints satisfaction model. These expressions are generated for the satisfiable case study shown in Section 5.4. For example, the first line in the presented code has two Boolean variables Visit_1_18 and Visit_1_18, which denote that UAV should visit both point and .
(assert (and Visit_1_1 Visit_1_18))
(assert (and Visit_2_1 Visit_2_18))
...
(assert (not Visit_2_6))
(assert (not Visit_2_14))
...
(assert (=> Travel_1_1_2 (and Visit_1_1 Links_1_2)))
(assert (=> Travel_1_1_2
(= T_1_2 (+ T_1_1 TTmp_1_2 (to_real Hover_1_2)))))
(assert (=> Travel_1_1_2 (= P_1_2 (+ P_1_1 PTmp_1_2))))
...
(assert (=> (and Visit_1_2 Visit_2_2) (or
(>= (- T_1_2 T_2_2) 1.0) (>= (- T_2_2 T_1_2) 1.0))))
...
(assert (<= T_1_18 2000.0))
(assert (<= P_1_18 6000.0))
...
|
This is asserted by the solver because we have a constraint in equation 10 in Section 4.2, which basically states that all the UAVs must visit the starting and ending points. Similarly, line 5 of the code states that if UAV travels from point to (Travel_1_1_2), then it must be true that it has already visited point (Visit_1_1) and there is a possible path/link from point to (Links_1_2) based on its direction at point and the distance between points and .

Appendix C Simulator Development
The simulator has been developed with Unity 3D using C# programming language111https://tinyurl.com/y2z8aena. Fig. 11 presents a screenshot of the simulator tool that we developed. The figure shows two UAVs flying from point to point collecting data. The spheres represent the waypoints above or in close proximity to the data sources. The red spheres denote the forbidden points which the UAVs avoid. A user can provide the trajectory of one or more UAVs as a combination of points as Cartesian coordinates in a three-dimensional space. The times of reaching each points, as well as the hovering time at the points to avoid collision and proper data collection are also provided from an input text file. The simulator presents an animation of the data collection scenario by the UAVs in a 3D environment. The simulation confirms the effectiveness of the generated trajectories by showing the absence of collisions, as well as the time to reach the end points of the trajectories of the UAVs.