Advantage of the key relay protocol over secure network coding
Abstract
The key relay protocol (KRP) plays an important role in improving the performance and the security of quantum key distribution (QKD) networks. On the other hand, there is also an existing research field called secure network coding (SNC), which has similar goal and structure. We here analyze differences and similarities between the KRP and SNC rigorously. We found, rather surprisingly, that there is a definite gap in security between the KRP and SNC; that is, certain KRPs achieve better security than any SNC schemes on the same graph. We also found that this gap can be closed if we generalize the notion of SNC by adding free public channels; that is, KRPs are equivalent to SNC schemes augmented with free public channels.
I Introduction
The key relay protocol (KRP) plays an important role in improving the performance and the security of quantum key distribution (QKD) networks [1, 2, 3, 4]. On the other hand, there exists another research field called secure network coding (SNC; see, e.g., Refs. [5, 6]), which has the goal and structure similar to the KRP. The goal of this paper is to analyze differences and similarities between the KRP and SNC rigorously.
QKD realizes distribution of secret keys to players at distant locations (see, e.g., Refs. [7, 8]). However, the communication distance achievable by a single QKD link is limited by the technological level of quantum optics [8]. KRPs are used to enable key distribution beyond such limitation of a single QKD link. The basic idea of the KRP is to pass a secret key of one QKD link on to another QKD link with the help of insecure public channels, such as the internet (cf. Figs. 2 and 3).
The KRP has similarities and differences with SNC (Table I). While they share the same goal of sharing secret messages, they differ in that 1) Public channels are available in KRPs, but not in SNC schemes, 2) KRPs use QKD links (or more generally, local key sources) while SNC schemes use secret channels, and 3) The messages in KRPs must be a random bit, while in SNC schemes each sender can freely choose its message.
Then the question naturally arises whether these differences are really essential. For example, is it not possible that there is actually a way of converting KRPs to SNC schemes, and that they are shown to be equivalent? The goal of this paper is to answer to this question. For the sake of simplicity, we will limit ourselves to the one-shot scenario.
The outline of our results is as follows (Fig. 1).
If we generalize SNC [5] by adding public channels (see the third column of Table I), then KRPs and SNC schemes (with public channels) on the same graph are always equivalent (Theorem 1).
On the other hand, if we do not generalize SNC and limit ourselves to its conventional form (without public channels; see the second column of Table I), then there is a definite gap in security between the KRP and SNC: On some graphs a KRP achieves better security than any conventional SNC schemes (Theorem 2 and Corollary 1). Hence the accumulation of past research on the conventional SNC is not sufficient to explore the potential of KRPs. This suggests that the KRP is a new research field.
| Key relay protocol | Secure network coding (SNC) | |||
| (KRP) | without public channels | SNC with public channels | KRP-by-SNC | |
| (Conventional SNC) | ||||
| Public channels | ✓ | ✓ | ||
| Local key sources | ✓ | |||
| (e.g., QKD links) | ||||
| Secret channels | ✓ | ✓ | ✓ | |
| Goal | Each sender-receiver pair (or each user pair) share a secret message | |||
| Content of the message | Random bit | Message chosen | Message chosen | Random bit |
| by the sender | by the sender | |||
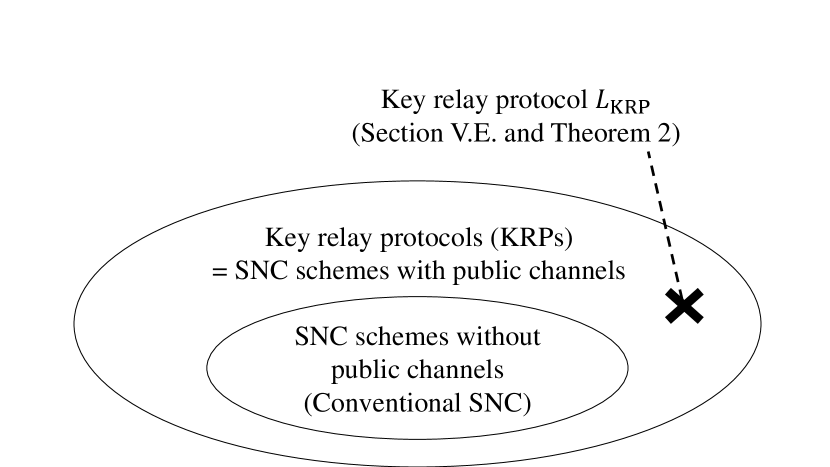
II Key relay protocol (KRP)
II-A Motivation and examples of the KRP
Quantum key distribution (QKD) distributes secret keys to two separate players. However, the communication distance achievable by a single set of QKD devices, or a QKD link, is limited by the technological level of quantum optics, and is currently in the order of 100 km [8]. For this reason, in this paper, we refer to a QKD link also as a local key source.
There is of course a strong demand to distribute secret keys globally, or beyond the reach of a single QKD link. The key relay protocol (KRP) [1, 2, 3] aims to fulfill this demand by connecting multiple QKD links, and also by using insecure public channels, such as the internet.
Fig. 2 illustrates the simplest example of such KRPs. Users and are separated by twice the reach of a local key source, and are connected by two local key sources and . From these local key sources, users and receive distinct local keys respectively. Then, in order for both and to share the same key , which we call the relayed key, they execute the following procedure with the help of the midpoint :
-
1.
The midpoint announces the difference of the two local keys, .
-
2.
Users and calculate the relayed keys and , respectively.
Note that is indeed satisfied. Note also that remain secret even if the announcement is revealed.
This idea can be generalized to more complex network configurations. For example, one can improve the distance by serially extending the above construction (Fig. 3(a)), or can improve the security by extending it in parallel (Fig. 3(b)). In the next subsection, we will give a formal definition of KRPs, applicable to an arbitrary network configuration.
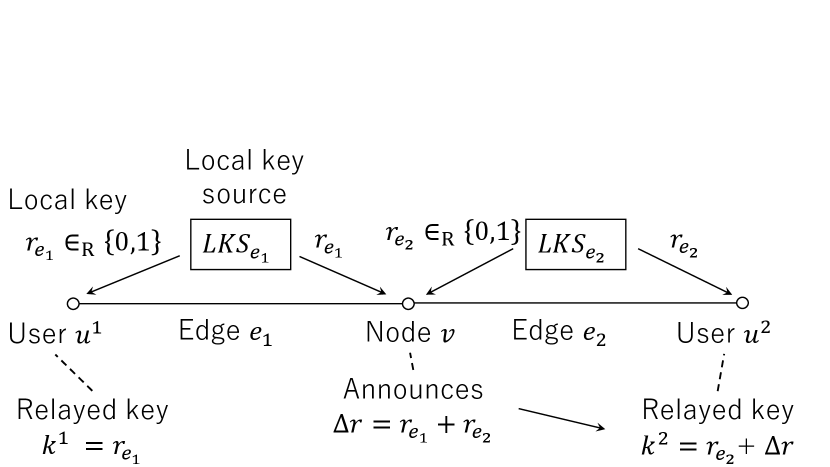

II-B Formal definition of the KRP
The outline is that: On an undirected graph , pairs of users wish to share a relayed key with the help of other players on nodes having access to local key sources and a public channels, without disseminating the message to the adversary.
II-B1 Setting
An undirected graph consists of a node set and an edge set . For the sake of simplicity, we assume that are connected. Each node has an individual player (denoted by the same symbol as the node), some of which constitute pairs of users with . There is also an adversary, who can wiretap some edges .
Each edge has a local key source and a public channel , which behave as follows.
Definition 1 (Local key sources and public channels).
and operate as follows:
-
•
Local key source (Fig. 4 (a)): On input “start” command from an end node or , it sends a local key, or a uniformly random bit to both and . When edge is wiretapped, it also sends to the eavesdropper.
-
•
Public channel (Fig. 4 (b)): On input a bit string from an end node (say, ), it sends to the other end node (say, ) and to the adversary.

II-B2 Key relay protocol
With the above setting, each user pair wish to share a relayed key with the help of players , without disseminating to the adversary. To this end, they request all nodes to execute a procedure of the the following type.
Definition 2.
A protocol of the following type, performed by players , is called a key relay protocol (KRP).
-
1.
All players communicate using public channels and local key sources 111More precisely, the outputs (, , or “start”) of players are defined as functions of previously received data () and of random variables generated by the player. Each player sends out the outputs whenever necessary data are all received..
Here each can only be used once, while can be used arbitrarily many times.
-
2.
Each user calculates a relayed key .
II-B3 Security criteria
There is a known collection of edge set which the adversary can wiretap on. In each round of the protocol, the adversary chooses and wiretaps edges .
Definition 3 (Security of the KRP).
A key relay protocol is secure against , if it satisfies the followings.
-
•
Soundness: The relayed keys generated by user pair are equal and uniformly distributed; i.e., , and .
Also, generated by different user pairs are independent.
-
•
Secrecy: The relayed key pairs are unknown to the adversary even when any edge set is wiretapped. That is, for any , we have
(1) where denotes the information that the adversary obtains by eavesdropping on edge set .
appearing in Definition 3 consists of local keys on edges , and of all public information ().
II-C Notes on KRPs used in practical QKD networks
In fact, the KRP defined above is slightly different from those used in actual QKD networks. Below we elaborate on their relation.
II-C1 Edge adversary model vs. node adversary model
In the above definition, we employed the edge adversary model (where the adversary eavesdrop on some edges), while in actual QKD networks the node adversary model (where the adversary can eavesdrop on information that goes in and out of a certain edges set) is usually assumed. This is not really a limitation, since the former model incorporates the latter: The situation where “the adversary eavesdrop on a node ” in the node adversary model can always be described as “all edges surrounding are wiretapped” in the edge adversary model.
II-C2 Passive adversary vs active adversary
Above we assumed that the adversary is passive (honest but curious), meaning that she eavesdrops on, but does not tamper with communication. On the other hand, in QKD, one usually assumes that the adversary is active; i.e., she can both eavesdrop on and tamper with communication.
The easiest way to convince oneself of this limitation, of course, is to accept it merely as a simplification introduced at the first step of continuing research.
On the other hand, there are also ways of justifying this limitation to some extent. That is, if the adversary is active, the following two problems arise,
-
•
Problem with soundness: The relayed keys may not match, .
-
•
Problem with secrecy: Players may malfunction and leak extra information to the adversary, damaging the secrecy.
but, in practical QKD networks, there are ways to solve or work around both these problems.
How to work around the problem with soundness
The basic idea here is the following. The relayed keys are random bits and are not meaningful by themselves, and thus can be discarded at any time. Hence, even if the event occurs, players can discard and repeat new rounds the KRP (including QKD as local key sources) until they obtain satisfying . This can generally decrease the key generation speed, but the secrecy remains intact.
Of course, in order for the above idea to actually function in practice, user pairs must be able to detect an error (check if or not) with a sufficiently small failure probability. This is also realizable by using information-theoretically secure message authentication codes (see, e.g., Section 4.6 of Ref. [9]).
Combining these ideas, we obtain the following method.
-
1.
User pairs repeat a KRP times and share -bit relayed keys .
- 2.
-
3.
User decrypts the received ciphertext to obtain . If , announces that the relayed keys must be discarded. (Here, authenticates his announcement by again using Construction 4.24 of Ref. [9].)
In this method, steps 2 and 3 each consume a pre-shared key222The security proofs of QKD require that its public communication be authenticated. A customary way to fulfill this requirement in practical QKD systems is that each user pair always keeps sharing a relatively small amount of secret key (pre-shared key), and uses it to authenticate their public communication, e.g., by the methods given in Ref. [10] and in Section 4.6, Ref. [9]. Here we use those pre-shared keys also for KRPs. of a length proportional to , the length of . However, one can set negligibly small compared with , with an appropriate choice of the function and for sufficiently large . Thus the net relayed key obtained by this method almost equals . For example, by using a polynomial-based -difference universal hash function, we have with being the failure probability of the error detection.
Countermeasure against problem with secrecy
As for the problem with secrecy, one countermeasure is to restrict ourselves with linear KRPs.
Here a linear KRP means the one where players are linear. A player being linear means that its outputs are all linear functions of previously received data () and of random variables generated by the player. In such restricted case we can prove the following lemma.
Lemma 1.
If a linear KRP is secure against passive (i.e., honest but curious) adversaries, it is also secure against active adversaries.
This lemma is a variant of Theorem 1, Ref. [11], which was previously obtained for the secure network coding (SNC). As the proof is essentially the same as in Ref. [11], we here only give a sketch: Suppose for example that the active adversary modifies a local key to , which is to be input to a node . With being linear, ’s subsequent outputs all change linearly in ; for example, a public message , which outputs, changes to with being a linear function. Since those linear response to tampering, such as , are all predictable, we can conclude that the adversary gains nothing by tampering with communication.
III Main results: Relation between the KRP and secure network coding (SNC)
As readers familiar with secure network coding (SNC; see, e.g., Refs. [5, 6]) may have already noticed, the KRP defined in the previous section have similarities and differences with SNC (Table I). That is, while they both share the same goal that each sender-receiver pair (or each user pair) share a secret message, they differ in that
-
1.
Public channels are used in the KRP, but not in SNC.
-
2.
The KRP uses local key sources , while SNC uses secret channels.
-
3.
In SNC, the sender can choose the massage freely. However, in the KRP, the message (which we called the relayed key in the previous section) must be uniformly random, and thus the sender does not have freedom to choose it.
From this observation the question naturally arises whether these differences are really essential. For example, is it not possible that there is actually a way of converting KRPs to SNC schemes, and that they are shown to be equivalent? In this section we answer to this question. The outline of our results is as follows.
First, if we eliminate difference 1) above by hand, that is, if we generalize SNC [5] by adding public channels, then we can simultaneously resolve the remaining differences, items 2) and 3), as well. As a result of this, we can show that the generalized form of SNC (i.e., SNC with public channels, in the third column of Table I) and the KRP are equivalent (Theorem 1).
On the other hand, if we do not generalize SNC and limit ourselves with its conventional form (the second column of Table I), then there is a definite gap in security between SNC and the KRP: There are situations where KRPs achieve better securities than the conventional SNC schemes, without public channels (Theorem 2).
III-A Definition of SNC with public channels
We begin with a formal definition of SNC with public channels, which is mentioned above and corresponds to the third column of Table I.
The conventional SNC (the second column of Table I) is the special case of this scheme where the use of public channels is prohibited.
III-A1 Setting
The setting is the same as that of the KRP, given in Section II-B1, except
-
•
Of each user pair , one user (say, ) is named the sender , and the other (say, ) the receiver . Thus either or holds.
The is necessary because, in SNC, messages are not a random bit (as in the KRP), but must be chosen by the sender ; see Definition 5 below.
-
•
Local key sources are replaced by the secret channels , defined in Definition 4 below.
Definition 4 (Secret channels).
On input a bit from one end node (say, ), secret channel sends to the other end node (say, ); see Fig. 5. When edge is wiretapped, it also sends to the eavesdropper.
In comparison with the conventional SNC [5], the setting above differs only in that players can use public channels in addition to secret channels (see Table I).

III-A2 SNC with public channels
The goal of our SNC with public channels is the same as that of the conventional SNC [5]: Each sender-receiver pair wish to exchange message with the help of other players on nodes , without disseminating to the adversary.
Definition 5 (SNC with public channels).
We call a protocol of the following type a secure network coding (SNC) scheme with public channels.
-
•
Each sender chooses a message aimed at the receiver .
-
•
Players communicate by using public channels and secret channels 333As in the case of the KRP, we assume that the outputs (, ) of players are defined as functions of previously received data () and of random variables generated by the player. We also assume that each player sends out the output whenever necessary data are all received..
Here, each can only be used once, while can be used arbitrarily many times.
-
•
Each receiver calculates message .
III-A3 Security criteria
The security criteria is essentially the same as Definition 3 for the case of the KRP. That is, there is again a known collection of wiretap sets . In each round of the SNC scheme, the adversary chooses and wiretap edges .
Definition 6 (Security of SNC with public channels).
A SNC scheme is secure against , if it satisfies the followings.
-
•
Soundness: Sender ’s message reaches receiver without error; .
-
•
Secrecy: Messages are unknown to the adversary even when any edge set is wiretapped. That is, for any , we have
(2) where denotes the information that the adversary obtains by eavesdropping on edges ; i.e., consists of secret bits on edges , and of all public information ().
III-B SNC with public channels and the KRP are equivalent
SNC with public channels thus defined are in fact equivalent to the KRP defined in the previous section.
Theorem 1 (The security of KRP The security of SNC with public channels).
KRPs and SNC schemes with public channels can always achieve the same security. That is,
-
1.
Given a KRP compatible with a graph and user configuration which is secure against wiretap sets , one can construct a SNC scheme with public channels which is compatible with the same and , and also secure against the same .
This is true whether the sender and the receiver for each user pair in are assigned as or (for the meaning of this notation, see Section III-A1).
-
2.
Given a SNC scheme (with or without public channels) compatible with a graph and a sender-receiver configutation which is secure against , one can construct a KRP compatible with the same and , which is secure against the same .
Therefore, if one wishes to analyze the potential and limitations of the KRP, it is necessary and sufficient to investigate SNC with public channels.
III-C SNC without public channels and the KRP are not equivalent
However, in order for Theorem 1 above to hold, it was in fact essential that we generalized SNC by adding public channels. The equivalence with the KRP no longer holds if we limit ourselves with the conventional SNC, i.e. SNC schemes without public channels. More precisely, we have the following theorem.
Theorem 2 (The security of KRP The security of SNC without public channels (conventional SNC)).
There exists a conbination of a graph , a user configuration , and wiretap sets for which there exists a secure KRP , but there exists no secure SNC scheme without public channels.
This is true whether the sender and the receiver for each user pair (in the SNC without public channels) are assigned as or (for the meaning of this notation, see Section III-A1). 444It is important to note that this theorem applies even to SNC schemes on un-directed graphs. If one is somehow allowed to limit oneself with SNC on directed graphs, the counterexample can be constructed straightforwardly.
The proof of this theorem is give in Section V.
In short, there are situations where the KRPs achieve better securities than the conventional SNC. Hence the accumulation of past research on the conventional SNC is not sufficient to explore the potential of the KRP. In this sense, the KRP is a new research field.
Corollary 1 (The security of SNC with public channels The security of SNC without public channels (conventional SNC)).
There exists a combination of a graph , a user configuration , and wiretap sets for which there exists a secure SNC scheme with public channel, but there exists no secure SNC scheme without public channels.
IV Proof of Theorem 1
To prove item 1), note that operations of can be simulated by using . That is, if an end node of edge wishes to send a local key to the other end node , it suffices that generates a random bit by itself and sends it to via (Fig. 6).
By applying this simulation to all included in , one obtains a protocol where user pairs share relayed key in the same setting as in SNC with public channel, given in Section III-A1.
Then by using thus obtained to encrypt message by the one-time pad (OTP) encryption scheme [9], one obtains . Here the OTP encryption scheme is the following: User encrypts as the ciphertext and sends it to via public channel. Then decrypts it as .
The soundness of is obvious from the construction. The secrecy of follows from that of , since the adversary’s information are the same in and . Indeed, in , the secrecy of on non-wiretapped edges is obvious by the construction, and thus the security of from that of . Then the secrecy of follows from that of the OTP. This completes the proof of item 1 of Theorem 1.

For the proof of item 2), note that can be simulated by the local key source and the public channel : When an end node wishes to send a bit to the other end node , it first distributes a random bit by switching on the local key source . Then sends to secretly by encrypting it by the OTP encryption scheme with being the secret key (Fig. 7).
By applying this construction to all secret channels included in , one obtains a new KRP, which we denote by . By construction, it is obvious that message as well as the adversary’s information are the same, whether in or in . This completes the proof of item 2 of Theorem 1.

V Proof of Theorem 2
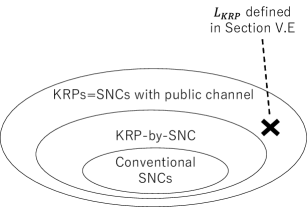
Theorem 2 asserts that the difference of structure between the KRP and the conventional SNC (shown in the first and the third columns of Table I, and also explained in the first paragraph of Section III) cause a definite gap in security (Fig. 1). Below, we prove this theorem by proving a set of more general lemmas (Fig. 8).
That is, we introduce another new type of protocols that we call KRP-by-SNC (KRP by the setting of SNC without public channels), which corresponds to the fourth column of Table I. Then we show that secure schemes satisfy the relations
-
Conventional SNC KRP-by-SNC KRP
-
KRP-by-SNC KRP.
(Lemma 4). These two relations together assert that the KRP is strictly more secure than the conventional SNC, which completes the proof of Theorem 2.
V-A Definition of KRP-by-SNC
KRP-by-SNC (KRP by the setting of SNC without public channels) is a variant of SNC corresponding to the fourth column of Table I. That is, it uses the same setting as in the conventional SNC, where players use the secret channels only. On the other hand, the goal is the same as in the KRP, where user pairs aim to share a random bit .
Alternatively, KRP-by-SNC can also be considered as a variant of KRP, obtained by replacing the public channels and the local key sources with the secret channels .
The formal definition of KRP-by-SNC is as follows.
V-A1 Setting
The setting is the same as that of SNC without public channels (the conventional SNC), except that
-
•
We denote user pairs by , as in the case of KRP. We make no distinction between the sender and the receiver.
We use this notation to stress that our goal here is to distribute a random bit , and thus no particular user ( or ) is entitled to choose the value .
V-A2 KRP-by-SNC
The goal here is the same as that of KRP: Each user pair share a uniformly random key , without disseminating it to the adversary. Thus the basic form of the protocol should be the same as that of the KRP given in Definition 2. However, as the setting here is different ( are used instead of and ), we need to modify Definition 2 as follows.
Definition 7 (KRP-by-SNC).
A protocol of the following type, performed by players , is called a KRP-by-SNC.
-
•
Players communicate by using secret channels 555We also assume that the outputs of players are defined as functions of previously received data and of random variables generated by the player, and that each player sends out the output whenever necessary data are all received..
Here, each can only be used once.
-
•
Each user calculates its relayed key .
V-A3 Security criteria of KRP-by-SNC
We use the same security criteria as in the KRP, namely, Definition 3. However, there is a caveat here: In the present case of KRP-by-SNC, the adversary’s information appearing in Definition 3 consists of the secret bits on wiretapped edges . This is because, in KRP-by-SNC, players use the secret channels only.
V-B Proof of Theorem 2
The following two lemmas assert that the security of KRP-by-SNC is between those of SNC and KRP.
Lemma 2 (Secure conventional SNC Secure KRP-by-SNC).
KRP-by-SNCs can always achieve the same security as the conventional SNC schemes. That is, given a conventional SNC scheme compatible with a graph and a sender-receiver configuration which is secure against wiretap sets , one can construct a KRP-by-SNC compatible with the same and which is secure against the same .
Proof.
Lemma 3 (Secure KRP-by-SNC Secure KRP).
KRP can always achieve the same security as KRP-by-SNC. That is, given a KRP-by-SNC compatible with a graph and a user configuration which is secure against wiretap sets , one can construct a KRP compatible with the same and which is secure against the same .
Proof.
This can be proved in the same manner as in the proof of item 2) of Theorem 1. By rewriting all the secret channels appearing in KRP-by-SNC as the OTP-encrypted channels using and , we obtain KRP . ∎
According to Lemma 3 above, there still remains the possibility that the securities of KRP-by-SNC and KRP are equal. Lemma 4 below disproves this possibility.
Lemma 4 (Secure KRP-by-SNC Secure KRP).
Hence there is a definite gap in security between KRP-by-SNC and KRP. Combined with Lemma 2, this also means that there is a definite gap in security between KRP and the conventional SNC, which completes the proof of Theorem 2.
The rest of this section is devoted to the proof of Lemma 4. The outline of the proof is as follows. First, we define a graph and a configuration of user pairs (Section V-D), as well as a KRP compatible with them (Section V-E1). Then we show that is secure secure against , i.e., secure when no edge is wiretapped (Section V-E2). Then we show that there exists no secure KRP-by-SNC compatible with the same and even when no edge is wiretapped (Section V-F).
V-C Notation
V-D Description of the graph and the user configuration
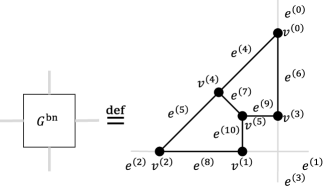
V-D1 Description using figures
That is, we first define a sub-graph by Fig. 9, which is in fact the well-known modified butterfly network [12]. Then we construct the graph by connecting subgraphs666Copies of the subgraph labeled with indices . and users , as in Figs. 10 and 11.


V-D2 Alternative description using equations
The same graph and the user pairs can also be defined using equations, as follows.
The node set consists of the user pairs , and of the nodes composing subgraphs , where indices are in the ranges , 777We use this notation to suggest that modulo 9 is implied in arithmetic involving variable . and .
The edge set consists of the internal edges of subgraphs ,
| (3) | ||||||||
edges connecting different subgraphs ,
| (4) | ||||
| (5) |
and edges connecting subgraphs and users :
| (6) |
where , .
V-D3 Notation related with
Below, for ease of notation, we will often suppress subscripts (corresponding to one of subgraphs ), if it is clear from the context which subgraph we focus on. Also, whenever we say a subgraph is a sender/receiver, it means that a node inside is a sender/receiver.
V-E KRP compatible with and
V-E1 Construction of
First step
The goal here is that: For all and , the node sends the local key to the node secretly.
In order to realize this task, we use the following idea: Note that, if secret channels were available, this task could be realized by using the well-known modified butterfly network coding in each sub-graph [12]. However, since we do not have secret channels in the present setting, we emulate them with the one-time pad (OTP) encrpytion using local keys supplied by and with public communication on (as we did in the proof of Theorem 1; also see Fig. 7). Namely, whenever a node wishes to secretly transmit a bit to an adjecent node , it encrypts using the key supplied by on the edge between and , and sends it to via the public channel . In the following, we often write this emulated secret transmission as .
Due to this idea and notation, our first step of takes the following form (Fig. 12):
| (7) | ||||
| (8) | ||||
| (9) | ||||
| (10) | ||||
| (11) | ||||
| (12) | ||||
| (13) |
and and obtain the values and respectively.

Second step
Next, using the local keys thus obtained, each user pair shares a relayed key. They do this by performing the serial KRP of Fig. 3 (a), on a straight path consisting of edges , , and .
Namely, the nodes in the middle of the path announce , , and , and then the user obtains the bit by summing up the published bits and the local key .
V-E2 Security of
From the construction above, we immediately have the following lemma.
Lemma 5 (Security of ).
The KRP is secure against wiretap sets .
Proof.
We give a detailed proof in Appendix. The basic idea of the proof is as follows.
The security (the secrecy and the soundness) of the emulated secret channels used in the first step is obvious by construction, and thus the security of the local key is guaranteed by that of the modified butterfly network coding. The security of the serial KRP is also obvious by construction. These two facts together guarantee the security of . ∎
V-F Proof that there exists no secure KRP-by-SNC compatible with and
Lemma 4 asserts that there exists no secure KRP-by-SNC compatible with and defined above, even when no edge is wiretapped. Below we prove this assertion by first supposing that such KRP-by-SNC exists and then deriving a contradiction.
In order to describe the contradiction, it is convenient to number edges according to the time when the secret channel is used. Obviously, such numbering is possible for any KRP-by-SNC. Formally, this numbering is equivalent to the following total order .
Definition 8 (Total order of edges).
Given a KRP-by-SNC on a graph , we write ( is smaller than ) if the secret channel is used before is used, in .
Now, if we suppose that there exists a secure KRP-by-SNC (compatible with , , and ), must satisfy the condition of the following lemma.
Lemma 6.
If a KRP-by-SNC compatible with and is secure against , then at least one of subgraphs must satisfy the following four requirements:
-
R1
For each, the secret bits conveyed on the edges and are completely random and completely correlated, i.e. .
-
R2
The secret bit on is independent of that on , i.e. .
-
R3
For each, is the sender of the larger edge of and .
-
R4
is the receiver of the second largest edge in the set .
We will prove this lemma in Section V-G.
However, we can also show that no KRP-by-SNC can satisfy such condition:
Lemma 7.
In any KRP-by-SNC compatible with and , no subgraph can satisfy the four requirements R1, , R4 of Lemma 6 simultaneously.
This is a contradiction, and thus a secure cannot exist. This completes the proof of Lemma 4.
Proof of Lemma 7.
We suppose that one of subgraphs satisfies R1, , R4, and derive a contradiction.
Below, as we concentrate on one such satisfying R1, , R4, we omit subscripts for ease of notation, on the subgraph , edges , and nodes . Also, as KRP-by-SNC here uses only one type of channels, , we will often identify an edge with the secret channel .
First note that the pair of the two largest edges in must either be and , or be and . This is because if it is not the case, then R3 says that () is the sender of the second largest edge, but this contradicts R4.
Then, of all the remaining cases, we will below focus on one particular case where edges are ordered as
-
1)
,
and derive a contradiction. (Other cases, such as , can also be shown similarly.) In this case, due to R1 and R2 we have
-
2)
,
-
3)
,
-
4)
.
Also, must be the sender of edges and due to R3, and also the receiver of due to R4. Thus we have
-
5)
is the sender of ,
-
6)
is the receiver of ,
-
7)
is the sender of .
From relations 1),,7) above, we can also prove the following two relations,
-
8)
A series of edges connecting and , e.g. , and , are smaller than ,
-
9)
A series of edges connecting and , e.g. , and , are larger than and smaller than .
However, these two relations contradict each other, and thus Lemma 7 is be proved.
Item 8) is obtained as follows: In order to realize relations 1), 2), and 5), the information of the secret bit on must be transferred from to before using the edge . For this transfer, a series of edges connecting and must be used. Here, we have used the fact that there is no correlation between nodes before executing protocol .
Item 9) is obtained as follows: Relations 2) and 4) imply that . Combining this fact and relations 1) and 6), we find that, before the secret channel on is used, any random variable obtained on the nodes is independent of . As a result, relations 1), 3) and 7) imply that, the secret bit on must be transferred from to before is used (and of course after is used). ∎
V-G Proof of Lemma 6
We first introduce the notion of the standard path along with three lemmas related with it, and then use them to prove Lemma 6.
V-G1 Standard path and the related lemmas
Definition 9 (Standard path ).
For each user pair , we define standard path connecting them via subgraphs (more precisely, subgraphs , , , and ) as in Fig. 13. The standard path consists of the following five edges,
| (14) |

We can show that all the edges on a standard path conveys essentially the same information, the relayed key .
Lemma 8.
In each standard path , the secret bits conveyed there must be equal to the relayed key shared by the user pair and at the end points, up to constants. That is, for any , and ,
| (15) |
with being constants.
We will prove this lemma in Section V-I.
Further, we can also show that is first generated locally by one entity (a subgraph or a user ) on the standard path , and then repeatedly conveyed to an adjacent entity, until it is shared by the users and at the end points; see Fig. 14. This phenomenon can be stated formally in terms of the ordering , as follows.
Lemma 9.
In each standard path , the edges are used in the following manner. Let denote the first edge used. Then,
-
•
Edges to the upper left of are used in order from lower right to upper left:
(16) and secret bits on these edges besides flow left or upward.
-
•
Similarly, edges to the lower right of are used in order from upper left to lower right:
(17) and secret bits on these edges besides flow right or downward.
We will prove this lemma in Section V-J.

We can also show the following lemma.
Lemma 10.
At least one of the following two conditions is false:
-
C1
For any subgraph , or is the smallest edge in the standard path containing the two edges and , when they are the two largest edges in .
-
C2
For any subgraph , or is the smallest edge in the standard path containing the two edges and , when they are the two largest edges in .
We will prove this lemma in Section V-K.
V-G2 Proof of Lemma 6
From Lemma 8 (respectively, from Lemma 9), all the subgraph satisfy R1 and R2 (respectively, R3) in Lemma 6. Here, in order to derive R2, we used the mutual independence of additionally.
Hence, it remains to show that R4 holds for some . To this end, we suppose that R4 does not hold for any , and derive a contradiction with Lemma 10.
This is equivalent to showing that, in any subgraph ,
-
(i)
C1 and C2 hold if R4 does not hold.
Below we will choose one of and show how to prove item (i). As is fixed, we omit subscripts on the notation for simplicity.
For the sake of the simplicity, we consider only the case of and ; all other cases can be shown similarly.
Then, we divide the remaining situation into three cases:
First, if the second largest edge in the set is or , the order must be derived from the assumptions and , i.e. item (i) holds.
Second, if the second largest edge in the set is , we find that holds (as a result, C2 holds) and the sender of must be . Here, we have used the assumption that R4 does not hold. From this fact and , Lemma 9 guarantees that is the smallest edge in the standard path where it belongs, i.e. C1 holds. Thus, the item (i) also holds in this case.
Finally, if the second largest edge in the set is , we can also show that item (i) holds in the same way as in the previous case.
This completes the proof of Lemma 6.
V-H Note on notation: and
In the proofs of Lemmas 8, 9 and 10 given below, we only need to consider communication between subgraphs , and do not need to refer to communication occurring inside each . Therefore, in order to simplify the presentation, we will often denote a subgraph as a single node . For example, the edge set denotes the set .
Accordingly, we will also regard the graph as consisting of edges that connect nodes () and , which we denote by . This edge set in fact consists of edges on the standard paths , defined in the previous section,
| (18) |
V-I Proof of Lemma 8
V-I1 Case of
We divide nodes into and the others:
| (19) | ||||
| (20) |
Since these two sets are connected by only, there must be functions which satisfy the relation
| (21) |
where denotes all the random variables possessed by node before executing protocol . The first (last) equality in (21) comes from the facts that the node () are in the set (). The second equality follows from the soundness of .
Recall that the two sets and are connected by only. Also, note that from the setting of the KRP-by-SNC, the secret bit must be generated locally by the sender. Then, we have
| (22) |
Also, since is one bit,
| (23) |
Lemma 11.
If , , and are random variables, and and are functions, satisfying
| (24) | ||||
| (25) |
with , where . Then, there is a bijective function such that .
Proof of this lemma is shown in Appendix. By using this lemma, we can find a bijective function such that
| (26) |
In other words, we can find a certain constant values such that the relation
| (27) |
holds for and . When we apply Lemma 11 above, we have substituted , , and into , , and in Lemma respectively.
Note, that from the constraint of soundness , we do not have to discriminate and hereafter. Therefore, we abbreviate the into below.
V-I2 Case of
This case can be shown completely in the same manner as the case of . We have the relation
| (28) |
for a certain constant .
V-I3 Cases of , , and
First, we use the same idea as in the case of . We define the sets
| (29) | ||||
| (30) | ||||
| (31) | ||||
| (32) |
and .
Since the two sets and are connected only by , , , , , and , there exists a bijective function :
| (33) |
Similarly, we have bijective functions for and such that
| (34) | |||
| (35) | |||
| (36) |
From these relations, we see that, for any , random variable is generated by at least one of bijective functions on a subset of , i.e. the eqs. (27), (28), (33), (34), (35) and (36). This fact and the complete randomness of guarantee that the must have the maximum entropy, i.e.
| (37) |
for .
The equations (33)(36) allow to write the random variable in multiple expressions as follows:
| (38) |
Here, denotes the -th element of the list of variables defined by the function . From the complete randomness of , must depend only on the inter section of the sets as arguments of these functions:
| (39) |
This fact and the relation (37) imply that
| (40) |
for a certain constant .
In the same way, from the multiple representations of and :
| (41) | ||||
| (42) |
we can find that there are certain constants such that the relation
| (43) |
hold for .
V-J Proof of Lemma 9
Protocol can be viewed as a communication protocol performed by the subgraphs using the standard paths.
In this picture, the communication between satisfy the following properties.
-
1)
Subgraphs are connected solely by the standard paths.
-
2)
Each standard path is a straight line.
-
3)
All edges in standard path convey the same random bit , up to a constant (Lemma 8).
-
4)
Random bits are independent of each other (due to the definition of the KRP).
For these properties to hold, it is necessary that
-
a)
Random bit is generated inside one of subgraphs on the standard path .
-
b)
Value of thus generated is conveyed repeatedly to adjacent subgraphs on the same standard path .
and thus the lemma holds.
Indeed, if a) is not true, i.e., if is generated independently by two or more of , there is a nonzero probability that their values differ. For other subgraphs to be able to send out thus generated, they must learn it from an adjacent subgraph which already knows .
V-K Proof of Lemma 10
We will take two steps.
First, we will show that, for any order , there is a subset of which satisfies the following four items:
-
1)
the subset contains the smallest edge in any standard path .
-
2)
,
-
3)
When is a value satisfying for and , the relation holds.
-
4)
When is a value satisfying for and , the relation holds.
Second, we will show that the existence of defined above and conditions and are incompatible for the order defined from a secure protocol .
Thus, Lemma Lemma 10 holds.
The first step is shown as follows: We constructively show that for any sequence , there is a subset which satisfies
-
1’)
,
2), 3), and 4). Such a subset is one of , , and for and defined below:
| (44) | ||||
| (45) | ||||
| (56) | ||||
| (67) | ||||
| (71) |
where . We can straightforwardly check that all the subsets satisfy the last three items 2), 3), and 4) directly. For any sequence , we can find that one of the above subsets satisfies the item 1’) as well. We confirmed this fact by a brute force search using a computer. This completes the first step of the proof.
For the second step, for any given order defined from a secure protocol , we will derive a contradiction from the assumptions that conditions C1 and C2 hold and that there exists which satisfies the four items 1), 2), 3), and 4). We pick up the smallest edge in . Existence of it guaranteed from the item 2). From the first item 1) and Lemma 9, there is a node such that .
When , we will give a contradiction, as an example. The third item 3) enforces
| (72) |
From this relation and the minimality of in , the order must hold. From this order, C1 enforces us that or must be a smallest edges in the standard path . Here, we have use the facts that , , , and . As a result, the item 1) enforces us that or must be in . However, this relation contradicts the relation (72).
In the same way, we can derive contradictions in the other cases, i.e. or or .
VI Summary and outlook
We investigated relations between the key relay protocol (KRP) and secure network coding (SNC) under the one-shot scenario, and also under the scenario where wiretap sets are restricted. We found that there is a definite gap in security between these two types of protocols; namely, certain KRPs achieve better security than any SNC schemes on the same graph. We also found that this gap can be closed by generalizing the notion of SNC by adding free public channels; that is the KRP is equivalent to SNC augmented with free public channels.
There are still many open problems. For example, does the gap we found here persist even under the asymptotic case?
It is also interesting to figure out on what types of graphs the gap occurs. Our conjecture is that there is no gap on plane graphs, and also for the case where there is only one sender-receiver pair, though the rigorous proofs remain as future works.
Formal proof of Lemma 5
Proof.
We prove the lemma by using a little bit modified protocol , such that being secure is equivalent to being secure.
is obtained by the following three process. First, when a public message made at any node in can be expressed as a linear combination of the other public messages and the local keys held by the node, i.e. , the corresponding message made at the node in is a linear combination of the local keys only, i.e. the parity of them . Second, all the public communications in are used only for sending the parities to all users. Finally, as relayed keys, the users evaluate the same values as for .
From this relation, we know that any bit obtained by the adversary in the case of can be evaluated by the adversary in the case of , and vice versa. This is why being secure is equivalent to being secure.
Self-contained definition of is as follows: is the protocol in which the following four phases are implemented in sequence.
-
•
Local key generation phase: All channels are used to generate local keys.
-
•
Parity evaluation phase: Each node evaluates parities of (part of) local keys held by the node.
-
•
Public communication phase: Evaluated parities are transferred from each node to users via public communications.
-
•
Relayed key generation phase: Each user generates the relayed key from received local keys and the parities.
Parity evaluation phase and Relayed key generation phase is explicitly identified by the following definitions:
-
•
All the parities each nodes evaluate: In each sub-graph , all the parities each nodes evaluate are
(73) (74) (75) (76) (77) (78) (79) (80) (81) In order to simplify the next expression, we introduce notations:
(82) (83) -
•
The function which gives the relayed keys: The relayed keys generated by and are
(84) (85) for .
From the definitions (73),,(• ‣ Proof.),
| (86) | ||||
| (87) |
is obtained for each sub-graph . Here, we have used the fact that for . By using the relations (86) and (87), the relayed keys (84) and (85) are evaluated as
| (88) |
This relation implies the soundness of . Since the generated relayed keys are part of the local keys, and the public information is linear combinations of the local keys, the secrecy can be checked from the fact that the relayed keys are linearly independent of all the published information. ∎
Proof of Lemma11
From the assumption (24)
| (89) |
This relatoin and the assumption (25), guarantee that
| (90) | ||||
| (91) |
The first relation and the assumption (24) imply
| (92) |
for any . Here we have used the fact that, if for , the relation holds. By summing up with respect to , the relation becomes
| (93) |
Since , we can define functions , and such that and hold, if . Using these functions, by substitute and into and respectively in the above relation,
| (94) |
is obtained. This relation guarantees the following relation
| (95) |
i.e. . Therefore,
| (96) |
holds where the eq.(91) is used in the second equality. As a result, there is a function such that . The last assumption, i.e. the number of candidates for is equal to that for , and the existence of the functions and guarantee the existence of the bijective function such that .
Acknowledgment
G.K. was supported in part by JSPS Kakenhi (C) No. 20K03779 and 21K03388. M.F. and T.T. were supported in part by “ICT Priority Technology Research and Development Project” (JPMI00316) of the Ministry of Internal Affairs and Communications, Japan.
References
- [1] L. Salvail, M. Peev, E. Diamanti, R. Allèaume, N. Lütkenhaus, and T. Länger, “Security of trusted repeater quantum key distribution networks,” Journal of Computer Security, vol. 18, pp. 61–87, Jan 2010.
- [2] R. Alléaume, C. Branciard, J. Bouda, T. Debuisschert, M. Dianati, N. Gisin, M. Godfrey, P. Grangier, T. Länger, N. Lütkenhaus, C. Monyk, P. Painchault, M. Peev, A. Poppe, T. Pornin, J. Rarity, R. Renner, G. Ribordy, M. Riguidel, L. Salvail, A. Shields, H. Weinfurter, and A. Zeilinger, “Using quantum key distribution for cryptographic purposes: A survey,” Theoretical Computer Science, vol. 560, pp. 62–81, 2014, theoretical Aspects of Quantum Cryptography – celebrating 30 years of BB84. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0304397514006963
- [3] T. R. Beals and B. C. Sanders, “Distributed relay protocol for probabilistic information-theoretic security in a randomly-compromised network,” in Information Theoretic Security, R. Safavi-Naini, Ed. Berlin, Heidelberg: Springer Berlin Heidelberg, 2008, pp. 29–39.
- [4] ITU-T, “Overview on networks supporting quantum key distribution,” International Telecommunication Union, Geneva, Recommendation Y.3800, Oct. 2019.
- [5] N. Cai and R. Yeung, “Secure network coding,” in Proceedings IEEE International Symposium on Information Theory,, 2002, pp. 323–.
- [6] T. Cui, T. Ho, and J. Kliewer, “On secure network coding with unequal link capacities and restricted wiretapping sets,” in 2010 IEEE Information Theory Workshop, 2010, pp. 1–5.
- [7] N. Gisin, G. Ribordy, W. Tittel, and H. Zbinden, “Quantum cryptography,” Rev. Mod. Phys., vol. 74, pp. 145–195, Mar 2002. [Online]. Available: https://link.aps.org/doi/10.1103/RevModPhys.74.145
- [8] F. Xu, X. Ma, Q. Zhang, H.-K. Lo, and J.-W. Pan, “Secure quantum key distribution with realistic devices,” Rev. Mod. Phys., vol. 92, p. 025002, May 2020. [Online]. Available: https://link.aps.org/doi/10.1103/RevModPhys.92.025002
- [9] J. Katz and Y. Lindell, Introduction to Modern Cryptography, Third Edition, 3rd ed. Chapman & Hall/CRC, 2020.
- [10] M. N. Wegman and J. Carter, “New hash functions and their use in authentication and set equality,” Journal of Computer and System Sciences, vol. 22, no. 3, pp. 265 – 279, 1981. [Online]. Available: http://www.sciencedirect.com/science/article/pii/0022000081900337
- [11] M. Hayashi, M. Owari, G. Kato, and N. Cai, “Reduction theorem for secrecy over linear network code for active attacks,” entropy, vol. 22, p. 1053, 2020.
- [12] T. Ho and D. Lun, Network Coding: An Introduction. Cambridge University Press, 2008.
| Go Kato was born in Japan, in 1976. He received the M.S. and Ph.D. degrees in science from The University of Tokyo in 2001 and 2004, respectively. In 2004, he joined the NTT Communication Science Laboratories and has been engaged in the theoretical investigation of quantum information. He is especially interested in mathematical structures emerging in the field of quantum information. He is a member of the Physical Society of Japan. |
| Mikio Fujiwara received the B.S. and M.S. degrees in electrical engineering and the Ph.D. degree in physics from Nagoya University, Nagoya, Japan, in 1990, 1992, and 2002, respectively. He has been involved R&D activities at NICT (previous name CRL, Ministry of Posts and Telecommunications of Japan) since 1992. |
| Toyohiro Tsurumaru was born in Japan in 1973. He received the B.S. degree from the Faculty of Science, University of Tokyo, Japan in 1996, and M.S. and Ph.D. degrees in physics from the Graduate School of Science, University of Tokyo, Japan in 1998 and 2001, respectively. Then he joined Mitsubishi Electric Corporation in 2001. His research interests include theoretical aspects of quantum cryptography and of modern cryptography. |