Active-RIS-Aided Covert Communications in NOMA-Inspired ISAC Wireless Systems
Abstract
Non-orthogonal multiple access (NOMA)-inspired integrated sensing and communication (ISAC) facilitates spectrum sharing for radar sensing and NOMA communications, whereas facing privacy and security challenges due to open wireless propagation. In this paper, active reconfigurable intelligent surface (RIS) is employed to aid covert communications in NOMA-inspired ISAC wireless system with the aim of maximizing the covert rate. Specifically, a dual-function base-station (BS) transmits the superposition signal to sense multiple targets, while achieving covert and reliable communications for a pair of NOMA covert and public users, respectively, in the presence of a warden. To maximize the covert rate, the transmission beamforming at BS and reflection beamforming at active-RIS are jointly designed, subject to quality-of-service (QoS) requirements of NOMA public user, constraint of Cramér-Rao bound for multi-target estimations, and covertness level against warden. Two superposition transmission schemes, namely, the transmissions with dedicated sensing signal (w-DSS) and without dedicated sensing signal (w/o-DSS), are respectively considered in the formulations of the joint transmission and reflection beamforming optimization problems. To this end, we develop the efficient methods involving several penalized Dinkelbach transformation to convert the non-concave covert rate maximization problems into feasible ones and propose an alternating optimization algorithm to obtain stationary solutions for the original problems. Numerical results demonstrate that active-RIS-aided NOMA-ISAC system outperforms the passive-RIS-aided and without-RIS counterparts in terms of covert rate and trade-off between covert communication and sensing performance metrics. Finally, the w/o-DSS scheme, which omits the dedicated sensing signal, achieves a higher covert rate than the w-DSS scheme by allocating more transmit power for the covert transmissions, while preserving a comparable multi-target sensing performance.
Index Terms:
Reconfigurable intelligent surface, non-orthogonal multiple access, covert beamforming, integrated sensing and communicationI Introduction
Next generation wireless systems are envisioned with sensing functionalities that will allow them to achieve high-precision positioning of massive devices and real-time reconstructions of the physical world, which are key enablers for anytime, anywhere, internet of everything (IoE), as well as vehicles networking [1, 2]. With the advancements of massive multiple-input multiple-output (MIMO) schemes, ultra-wide spectral usage, and ultra-high frequency transmission, such as millimeter and terahertz waves, wireless communication systems naturally possess sensing functions with exceptional accuracy and resolution [3]. By co-designing communication and sensing systems together in order to use the same hardware and signal processing platforms, same wireless resources, and unified control modules, collaboration efficiencies can be significantly improved [1]. In this direction, novel concepts of integrated sensing and communication (ISAC) have recently sparked heated discussions, particularly on co-designing of dual-function waveforms [4, 5].
As a promising spectral efficiency (SE)-enhancement technique, non-orthogonal multiple access (NOMA) has been applied to enable ubiquitous high-quality communication and high-resolution sensing in NOMA-inspired ISAC wireless systems [6, 7], which were frequently constrained by limited wireless resources. Through superposition coding at the transmitter and successive interference cancellation (SIC) at the receiver, NOMA-ISAC addressed inter-user interference (IUI) effectively, while additional degrees of freedom (DoF) were introduced by adequate dual-functional beamforming [6]. To simultaneously deliver multicast and unicast messages, common beamforming and transmit power allocation were jointly optimized in NOMA-ISAC wireless systems with the aim of enhancing radar sensing accuracy and achieving extra DoF for communications [7]. Inspired by interference management of NOMA, the dedicated sensing signal (DSS) was partially treated as virtual communication signal and eliminated by SIC at communication receivers [8]. In uplink ISAC systems, a pure-NOMA-based scheme was reported to guarantee the sensing-prior system performance with a fixed communication-to-sensing decoding order [9]. As a step further, a semi-NOMA-based scheme was introduced to provide flexible resource allocation strategies between sensing and communication, which effectively satisfied different objectives of sensing and communication [10].
Due to open and broadcasting natures of wireless propagation, sensitive and privacy information embedded in NOMA-ISAC waveforms was susceptible to interception and eavesdropping [11, 12]. Considering radar target as potential eavesdropper, the authors of [11] exploited artificial jamming and NOMA signal for target detection and eavesdropping prevention. In [12], confidential information of NOMA users was concealed in radar beamforming, in which strong interference was conveyed to damage eavesdropping channels. By using SIC, artificial jamming and sensing interference were eliminated by NOMA users to enhance communication performance [11, 12]. Nevertheless, exposing existences of legitimate transmissions to malicious users brought potential security risks to ISAC systems [13, 14], e.g., exposing only network traffic pattern can lead to sensitive information leakage. Without additional spectrum investments, it is paramount importance to enhance security performance of ISAC systems by resorting to new technologies.
Fortunately, reconfigurable intelligent surface (RIS) provided a promising approach to simultaneously facilitate radar sensing and covert communications [15]. Since RIS possesses ability to manipulate propagation environments intelligently and efficiently, virtual line-of-sight (LoS) links can be created for radar sensing and communication resulting in new DoFs for ISAC optimizations [16, 17, 18]. By controlling reflection amplitude and phase-shift of each element of RIS, the reflected wireless signals can be tuned constructively or destructively, such that signal power in desired directions can be strengthened or weakened [19]. Recently, RIS was utilized to facilitate covert communications in ISAC systems [15] and NOMA systems [20, 21], which provided a higher level of security than conventional physical layer security (PLS) by concealing legitimate transmissions against wardens. Compared to conventional covert communications in NOMA systems, where only the signal of a NOMA public user was utilized as a shield for covert transmissions [22], RIS-aided superposition transmissions hide communication behaviors cost-effectively by leveraging RIS’s phase-shift uncertainties and superposition transmissions of NOMA public and covert users.
Due to “multiplicative fading” effects, reflection link qualities of passive-RIS-aided communications were limited and corresponding capacity gains were negligible. To overcome this limitation, active-RIS was introduced in [23] and [24], which integrated amplifiers into meta-elements to amplify and reflect signals, compensating for substantial path-loss of reflection links and obviating need for complex and power-hungry radio frequency (RF) chains [23]. Owning to the aforementioned benefits, PLS [25] and covert communication performances [26] were improved by optimizing active-RIS reflection beamforming and collaborating with base-station (BS) precoding optimization. In active-RIS-aided multiple-input single-output (MISO) NOMA systems [27], covert rate was maximized subject to the QoS requirements of NOMA public users and the maximum reflection amplitude and power budget of active-RIS.
Recently, active-RIS has been applied to enhance communication quality and sensing capability for ISAC systems in which direct links from BS to potential targets have been blocked [28, 29, 30, 31]. To enhance sensing capability for MIMO-ISAC systems, active-RIS was deployed to shape reflection beampattern towards a point-like target [28]. Different from [28], in which only communication signal was used to achieve dual-function ISAC, DSS was applied in [29] where transmit beamforming and reflection beamfomring were joint optimized to maximize the radar signal-to-noise ratio (SNR). Furthermore, to enhance the non-line-of-sight (NLoS) sensing capability, active-RIS was deployed to assist remote radio heads in cloud radio access networks (C-RANs) to conduct dual-function ISAC [30]. Taking into account target location estimation errors, a hybrid active-passive-RIS was deployed to maximize the minimum sensing beampattern gain while maintaining a pre-defined signal-to-interference-plus-noise ratio (SINR) for each user [31]. The high path-loss was intensively tackled by using active-RIS for ISAC systems, with the aim of not only improving the communication and sensing performances [32, 33, 34], but also enhancing the PLS capabilities [35]. Note that the above active-RIS-aided ISAC contributions, except for [28], have exploited DSS to achieve dual-function ISAC.
Despite the vast research effort that was put on analyzing and optimizing active-RIS empowered wireless systems, how to deploy active-RIS to make the most out of the covert communication for NOMA-ISAC wireless systems is still unknown. Additionally, works in [28, 29, 32, 33, 35, 34] investigated dual-function beamforming with respect to a single target, which was not a typical scenario in practice. Despite multiple targets being considered in [31, 30], the exploited sensing metric, i.e., beampattern gain, was too rough for estimating target parameters. From the perspective of dual-function waveforms, although the usage of DSS and the absence of DSS can improve both the communication and sensing performances, a comprehensive comparison of the impact of the usage of DSS and the absence of DSS on the system performance of active-RIS-aided ISAC systems is missing. In particular, the effects of exploiting DSS in active-RIS-aided NOMA-ISAC systems need to be quantified, especially when DSS is regarded as a part of the NOMA superposition signal. Another question that we need to answer is the following: when active-RIS is deployed to aid covert communications in practical NOMA-ISAC systems, should we apply DSS or not to achieve the enhanced covert communication performance in the presence of multiple targets?
As an attempt to answer the above open questions, we deploy an active-RIS to aid covert communications in a NOMA-ISAC system, where a dual-function BS serves two NOMA users while sensing multiple moving targets. In more detail, one of the NOMA users is a security-required user (covert user) with a high level of covertness and the other is a QoS-required user (public user) with low or no confidentiality requirements. We examine the use of DSS for multi-target sensing and apply the NOMA public user’s signal as the covert medium to hide covert transmissions against warden. Taking into account the realistic assumption of multiple moving targets, we derive Cramér-Rao bound (CRB) to characterize the sensing performance for the considered NOMA-ISAC wireless system. The trade-off between covert communication and multi-target sensing is investigated and the impact of the use of DSS is extrapolated. With the aim of maximizing the covert rate, transmission beamforming and reflection beamforming are jointly optimized, while satisfying the CRB constraint on multi-target estimation and ensuring the covertness level against warden. By involving user scheduling and pairing schemes, the considered NOMA-ISAC system is scalable to accommodate multiple NOMA users.
To the best of our knowledge, this is the first paper investigating covert communications for active-RIS-aided NOMA-ISAC wireless systems in the presence of a warden and multiple moving targets and the first attempt to reveal the impacts of DSS on the covert communication and sensing performances systematically. The key contributions of this paper are summarized as follows:
-
•
We deploy active-RIS to aid covert communications in a NOMA-ISAC system taking into account two superposition transmission schemes. The first scheme only transmits a NOMA signal without DSS (w/o-DSS scheme), whereas the second scheme transmits NOMA signal with DSS (w-DSS scheme). To precisely measure the sensing performance with respect to multiple moving targets, we exploit CRB as the target sensing metric for both the w/o-DSS and w-DSS schemes. In the w-DSS scheme, both the sensing and communication signals are utilized to not only estimate the parameters of multiple moving targets, but also hide the covert transmission behaviors from the dual-function BS to the NOMA covert user. In the w/o-DSS scheme, although only the signal of the NOMA public user is treated as a shield to achieve low-probability-of-detection covert communications for the NOMA covert user, more transmit power can be allocated to enhance covert communication performance.
-
•
For both the aforementioned superposition transmission schemes, we formulate the covert rate maximization problems subject to the QoS requirements of the NOMA public user, CRB constraint, power budget constraints at BS and active-RIS, and covertness constraint. We decouple the original non-concave optimization problem into two sub-problems of transmission beamforming optimization at BS and reflection beamforming optimization at active-RIS, respectively, to tackle the optimization variables coupled in the objective and constraints. The resulted rank-one constrained problem of transmission beamforming optimization is solved with the aid of a penalty-term, while the rank-one constrained fractional programming problem of reflection beamforming optimization is solved by exploiting a penalized Dinkelbach transform. Then, we introduce an alternating optimization (AO) algorithm to optimize the transmission and reflection beamforming in an alternating manner.
-
•
Extensive numerical results clarify the effectiveness of the derived solutions and AO algorithm. It is demonstrated that the active-RIS-aided NOMA-ISAC system outperforms the passive-RIS-aided and without-RIS counterparts in terms of the covert rate and trade-off between communication and sensing performances because active-RIS amplifies the incident signal to obtain additional covert rate gain and allows BS to allocate more transmit power for target sensing. The impacts of DSS on the ISAC system performance are also revealed by the numerical results. Compared to the w-DSS scheme, the w/o-DSS scheme achieves a higher covert rate because more transmit power is available for covert transmissions by omitting DSS, while exploiting only the NOMA signal ensures the required multi-target sensing performance in the considered NOMA-ISAC system.
The remainder of the paper is organized as follows: Section II presents the system model. The covert beamforming design is specified in Section III. Numerical results are illustrated in Section IV. Finally, Section V concludes the paper.
Notations: Throughout the paper, scalars are represented by italic letters, and vectors and matrices are represented by boldfaced lowercase and uppercase letters, respectively. denotes probability, denotes the expectation, and denotes the Euclidean norm of a complex vector. Superscript , and denote vector/matrix transpose, conjugate and Hermitian transpose, respectively. The Hadamard and Kronecker products are denoted by and , respectively. and denote the spaces of complex-valued matrices and real-valued matrices, respectively. represents the set of all complex Hermitian matrixes. indicates that is a positive semi-definite matrix. The symbols and denote the rank and trace of matrix , respectively. and denote the -dimensional all-zero and all-ones vectors, respectively. denote the identity matrix. The notation denotes a circular symmetric complex Gaussian (CSCG) random distribution with mean and variance .
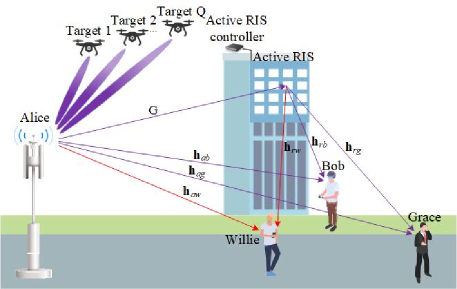
II System Model
We consider an active-RIS-aided NOMA-ISAC system consisting of a dual-function BS (Alice), an active-RIS, a warden (Willie), a NOMA public user (Grace), a NOMA covert user (Bob), and multiple moving targets indexed by , as shown in Fig. 1. We assume that Bob has a high-level of confidentiality and Grace only has reliability requirements, which is a realistic assumption in IoE applications. For example, military departments require covert communications in specific scenarios, while weather forecasts have low or no confidential requirements. In the NOMA-ISAC system, Alice is equipped with a uniform linear array (ULA) consisting of transmit antennas and receive antennas with half-wavelength spacing. For simplicity, we assume Alice works in full-duplex mode with perfect self-interference cancellation and . Each one of Grace, Bob, and Willie is equipped with a single antenna. The active-RIS consists of active reflecting elements and is deployed close to the users to assist information communications. We assume that targets fly at low altitudes, which results in strong LoS links from Alice to targets and vice versa, while active-RIS is deployed far away from targets resulting in weak RIS reflection links. Thus, we only consider direct links for target sensing [17, 34, 16]. In addition, Willie keeps monitoring the downlink transmission from Alice to the NOMA users and determining whether Alice is transmitting covert information to Bob. The channel between Alice and node is denoted by with , , and standing for Grace, Bob, and Willie, respectively. The Alice-RIS channel and RIS- channel are denoted by and , respectively. All of the communication channels are assumed to experience Rician fading with the distance-dependent path-loss, e.g., the Alice-RIS channel can be obtained as
| (1) |
where is the distance-dependent path-loss, is the Rician factor, denotes the LoS component that is expressed as , and denotes the Rayleigh fading component with zero mean and unit variance. Vectors and are the array response vectors of Alice and active-RIS, respectively, which are mathematically given by and , respectively, with , , and being the carrier wavelength, adjacent antenna spacing of Alice, and adjacent element spacing of the active-RIS, respectively. The Alice- and RIS- channels are independent and identical. Following the works in [20, 21], we assume that Alice possesses statistical knowledge of the channel state information (CSI) of the links involving Willie, along with perfect CSI for the other communication channels. Willie, on the other hand, can attain perfect CSI for its monitoring channels. It is assumed that all channels experience quasi-static block fading, remaining constant within each block. In the rest of this section, two transmission schemes, namely, the w/o-DSS and w-DSS schemes, are respectively presented.
II-A w/o-DSS Scheme
1) Communication Model: In each transmission block, Alice transmits the superimposed NOMA signal to serve two users while sensing the moving targets. Consider blocks of transmission and radar pulses within one coherent processing interval (CPI) indexed by , the transmitted signal at time index can be expressed as
| (2) |
where denotes the NOMA communication symbols satisfying , and are the information signals for Bob and Grace, respectively, and is the communication beamforming matrix with denoting the beamforming vector for (). The covariance matrix of the transmitted signal can be calculated by
| (3) |
In each transmission block, Alice transmits signal to active-RIS. Then, the incident signal is reflected by active-RIS. Taking into account the additive white Gaussian noise (AWGN) at active-RIS, the reflected signal at time index can be written as
| (4) |
where is an diagonal matrix with its th diagonal entity denoting the reflection coefficient of the th element of active-RIS and denotes AWGN at the active-RIS. In particular, and respectively represent the reflecting amplitude and phase shift of the th element and is the allowed maximum reflecting amplitude. In this setup, the total power of the reflected signal is limited by
| (5) |
where is the maximum power budget at the active-RIS. Then, the received signal at node , , at time index , can be expressed as
| (6) |
where is the equivalent composite channel from Alice to node and is the AWGN at node . With the assumption that , i.e., Bob and Grace are the near and far users, respectively, Alice allocates more transmit power to transmit rather than , i.e., , to guarantee the successfully SIC. In this paper, we assume perfect SIC at Bob and Grace. According to NOMA principles, Bob detects and removes the corresponding interference by exploiting SIC followed by the detection of its own signal . Grace detects by treating the signal related to as noise. The achievable rates of Bob corresponding to the transmissions of and are given by and , respectively, with the received signal-to-interference-plus noise ratios (SINRs) being given by
| (7) |
and
| (8) |
Moreover, the achievable rate of Grace is given by
| (9) |
To make SIC feasible at the NOMA receivers, the achievable rate at Grace to detect its own message should be no more than the achievable rate at Bob to detect . Thus, we have
| (10) |
2) Sensing Model: Since the NOMA signals are completely known at Alice, Alice is able to process the echo waves reflected by potential targets for parameters estimation. Therefore, in the considered NOMA-ISAC system, the transmitted NOMA signal can be exploited for target sensing [7]. As typically performed in radar sensing, the Alice-targets links are assumed to be LoS. The echo signal received at Alice at time index is given by
| (11) |
where is the th moving target’s complex reflection factor determined by its radar cross-section (RCS), denotes Doppler frequency of the th moving target, denotes the symbol period, with being the transmit steer vector at Alice, and denotes the AWGN following . In particular, with being the velocity of the th moving target, and and standing for the speed of light and carrier frequency, respectively. Since the considered NOMA-ISAC system conducts target sensing in a monostatic manner, the direction of arrival (DoA) and the direction of departure (DoD) are the same. For notation simplicity, (11) is equivalently rewritten as
| (12) |
where , with , and . For the sensing, we are interested in estimating the multiple moving targets’s parameters by using CRB, which is the lower bound on the variance of unbiased estimators and equivalent to the inverse of the fisher information matrix (FIM) [5]. For target , we define the estimation parameters , , and the FIM matrix for estimating of multiple moving targets as . As a result, can be partitioned as
| (13) |
where
| (14) |
with , , , , and , . The detailed derivation is provided in Appendix.
3) Covertness Requirement: Based on the received signal, Willie aims to determine whether the information transmission from Alice to Bob is present. The monitoring of Willie involves two hypotheses: indicates the absence of the information transmission from Alice to Bob and indicates the presence of the information transmission from Alice to Bob. Under and , the received signals at Willie at time index can be respectively expressed as
| (15) |
and
| (16) |
In general, the detection error probability (DEP) is utilized to measure the performance of Willie’s hypothesis test, which is defined as
| (17) |
where denotes the probability of false alarm, i.e., the rejection of when it is true. denotes the probability of miss detection, i.e., the acceptance of when it is false. and denote Willie’s binary decisions endorsing and , respectively. To evaluate the DEP, we assume the apriori probabilities are equal in the statistical hypothesis test. Assuming Willie uses the Neyman-Pearson criterion to detect the covert transmission, the optimal decision rule for minimizing the DEP is the likelihood ratio test, i.e.,
| (18) |
where
| (19) |
and
| (20) |
denote the likelihood functions for Willie’s received signals under and , respectively, with and , respectively. With respect to Willie’s received signal power, the optimal decision rule for Willie can be rewritten as
| (21) |
where and denotes the optimal detection threshold. Under the optimal detection rule, we can derive the minimum DEP achieved by Willie corresponding to the two hypotheses, as in [36]:
| (22) | |||||
To facilitate the design of covert communications, we further introduce a lower bound on [36]
| (23) |
where refers to the Kullback-Leibler (KL) divergence, which can be calculated as:
| (24) |
To ensure covertness, the minimum DEP of Willie should satisfy , where is the desired level of covertness. In this work, we set a tighter constraint, i.e.,
| (25) |
to ensure covertness, taking into account the lower bound on in (23). According to (24), by applying the monotonicity of the function in the interval , the covertness constraint can be reformulated as:
| (26) |
where is the unique root of in the interval . The above covertness constraint indicates that the AWGN introduced by the active-RIS and NOMA public user’s signal can be utilized as the shield of covert transmission to enhance the covert performance of the active-RIS aided NOMA-ISAC system.
II-B w-DSS Scheme
In this section, we apply the w-DSS scheme in the considered active-RIS-aided NOMA-ISAC system, in which the BS has the DSS.
1) Communication Model: Alice transmits the superimposed communication and DSSs for information transmission and targets estimation, in which the transmission of the DSS is assumed to be a general multi-beam transmission. Then, the transmitted signal at time index from Alice is expressed as
| (27) |
where is the DSS satisfying and is the sensing beamforming matrix. In (27), is the overall beamforming matrix to be designed and . We assume that all the signals are independent and pairwise uncorrelated. Therefore, the covariance matrix of the transmitted signal can be calculated as
| (28) |
The reflected signal by the active-RIS at time index can be written as
| (29) |
Accordingly, the total power of the reflected signal at the active-RIS is limited by
| (30) |
Then, the received signal at node , at time index is given by
| (31) |
It is observed in (27) and (31) each NOMA user suffers interference induced by information signal of another NOMA user and DSS. We assume that is predetermined sequences and the communication users can know it prior [37]. Thus, we consider the receivers of the NOMA users have the capability of cancelling interference resulted by DSS before detecting its desirable information signal. Consequently, Bob detects , with the achievable rate as
| (32) |
After detecting and removing signal of Grace, Bob detects its own signal with the achievable rate that is given by
| (33) |
Grace decodes its own message by regarding the signal of Bob as interference. Thus, the achievable rate of Grace can be written as
| (34) |
Similarly, we have to make SIC feasible at the NOMA receiver.
2) Sensing Model: Based on the signal model that both the NOMA communication signal and the DSS are exploited for targets parameters estimation, the echo signal received at Alice at time index is defined as
| (35) |
To estimate of multiple moving targets, the expression for the FIM can be presented in the same structure as that in (13) containing the following entries:
| (36) |
3) Covertness Requirement: In the w-DSS scheme, the received signals at Willie under and can be respectively expressed as
| (37) |
and
| (38) |
Similar to the derivation of (26), the covertness constraint under this setup can be formulated as
| (39) | |||||
In addition to the AWGN and NOMA public user’s signal, the expression in (39) indicates that the DSS is also utilized as the covert medium to facilitate covert communication of the NOMA-ISAC system.
III Problem Formulation and Proposed Solutions
In this section, we focus on the joint optimization of the transmission beamforming and reflection beamforming in the active-RIS-aided NOMA-ISAC system. We firstly formulate the optimization problems when Alice performs the target sensing and communication simultaneously in the two transmission schemes. Then, we present solutions to the formulated optimization problems by designing an AO algorithm for optimizing the transmission beamforming at Alice and reflection beamforming at the active-RIS.
III-A Problem formulation
The diagonal elements of the CRB matrix represent the minimum variance of the multiple targets parameters estimated by the unbiased estimator [38]. Our objective is to maximize the covert rate at Bob while limiting CRB. To investigate the tradeoff of covert transmission and target estimation, we jointly optimize the transmission beamforming and the reflection beamforming subject to the power budget constraints of Alice and active-RIS, achievable rate constraint for NOMA, Grace’s QoS requirement, CRB constraint and pre-defined covertness level. Considering the additional constraints imposed by the active-RIS-aided NOMA-ISAC system, the optimization problem without the dedicated sensing sihgnal is formulated as follows:
| (40a) | ||||
| s.t. | (40b) | |||
| (40c) | ||||
| (40d) | ||||
| (40e) | ||||
| (40f) | ||||
| (40g) | ||||
where is the CRB threshold, is the maximum transmit power budget at Alice, and is the minimum target rate of Grace. In problem (P1), (40b) is Alice’s maximum transmit power constraint, (40c) guarantees successful SIC at Bob and Grace, (40d) ensures that the QoS requirements of Grace is satisfied, (40e) represents the CRB constraint, (40f) indicates the limitation of the maximum reflecting amplitude of th element of , and constraints in (40g) denote reflection power budget at the active-RIS and covertness level, respectively.
For the w-DSS scheme, the corresponding optimization problem is formulated as follows:
| (41a) | ||||
| s.t. | (41b) | |||
| (41c) | ||||
| (41d) | ||||
| (41e) | ||||
| (41f) | ||||
| (41g) | ||||
In problems (P1) and (P2), the optimization objectives (40a) and (41a) are non-concave and the majority of the constraints are non-convex, both problems (P1) and (P2) should be transformed into a concave one to be solved.
III-B Proposed Solution to Problem (P1)
The main challenge for solving problem (P1) is the coupling between the optimization variables and , which makes it infeasible to jointly optimize and . To address this challenge, we decouple problem (P1) into two sub-problems of optimizing the transmission beamforming and reflection beamforming , respectively. Furthermore, we design an AO algorithm to obtain the optimal solution of problem (P1). The details of our proposed solution are presented below.
1) Transmission Beamforming Optimization: For any given feasible , problem (P1) can be reduced to optimize only. To tackle the non-convex CRB constraint, we transform it into a trackable form by introducing an auxiliary variable , . Considering that the FIM is a positive semidefinite matrix and the function is matrix decreasing on the positive semidefinte matrix space [39, Example 3.46], the CRB constraint (40e) is equivalent to the following two constraints:
| (42a) | |||
| (42b) | |||
To facilitate solving the transmission beamforming optimization problem, we introduce the auxiliary variables , , , , , and with . One can obtain that , , and with . In addition, constraint is equivalent to , which is independent of the transmission beamforming . Since the function is monotonically increasing, maximizing is equivalent to maximizing . Therefore, the optimization problem with respect to can be formulated as:
| (43a) | ||||
| s.t. | (43b) | |||
| (43c) | ||||
| (43d) | ||||
| (43e) | ||||
| (43f) | ||||
| (43g) | ||||
| (43h) | ||||
| (43i) | ||||
In problem (P3), constraint (43c) represents the QoS requirements of Grace with . To address the rank-one constraint (43i), we introduce a penalty term into (43a), where is a penalty factor, denotes the nuclear norm, and is the convex upper bound of the non-convex term with standing for the spectral norm, i.e., . One can obtain the convex upper bound by leveraging the first-order Taylor expansion at the point , which is expressed as , where is the solution obtained in the th iteration and is the eigenvector corresponding to the largest eigenvalue of . With the added penalty term, the transmission beamforming optimization problem can be formulated as
| (44a) | ||||
| (44b) | ||||
Here, if , the exactly rank-one metrics can be guaranteed by maximizing the new objective due to the fact that is equivalent to . It is evident that problem (P3.1) is a concave optimization problem and can be readily solved using existing convex optimization solvers such as CVX.
2) Reflection Beamforming Optimization: For any given , problem (P1) can be reduced to optimize only. To handle the non-concavity of the objective function and constraints (40c), (40d), and (40f) with respect to and formulate a tractable covert rate maximization problem, we first introduce with , , being the th diagonal element in and and construct and with , which results in the expression . Then, by applying the change of variables , , and with , we obtain that , , and . Also, we introduce and to transform constraint into . After taking the ratio term out of the function, we can formulate the reflection beamforming optimization problem as
| (45a) | ||||
| s.t. | (45b) | |||
| (45c) | ||||
| (45d) | ||||
| (45e) | ||||
| (45f) | ||||
| (45g) | ||||
| (45h) | ||||
To recast the resulting non-concave fractional programming (FP) problem with rank-one constraint to a convex form, we propose a penalized Dinkelbach approach. Specifically, we add a penalty-term to the objection function’s denominator to address the non-convexity of rank-one constraint generated by variable change in (45h). Here, is a control factor and is the upper bound on with closed form , where represents the eigenvector corresponding to the largest eigenvalue of in the th solution. As a result, the new objective function can be expressed as
| (46) |
By maximizing this fractional objective function, we ensure that as becasue is equivalent to . Since the above concave-convex single-ratio objective in (46) still hinders a direct solution, we further utilize the Dinkelbach transformation [40] to convert it into a concave form. Specifically, let
| (47) |
and
| (48) |
the transformed optimization problem can be expressed as
| (49a) | ||||
| (49b) | ||||
| (49c) | ||||
where the auxiliary variable is updated by in the th iteration. Now, problem (P4.1) is concave and can be optimized via the existed CVX solver.
The proposed AO algorithm is summarized in Algorithm 1. To prevent the optimization falling into local optima caused by the zero penalty-term during initialization, we set in the proposed penalized Dinkelbach approach. The overall computational complexity of Algorithm 1 is characterized by , where and denote the iteration numbers of the AO loop and Dinkelbach loop, respectively, and and denote the iteration numbers of the penalty-terms in problems (P3.1) and (P4.1), respectively.
III-C Proposed Solution to Problem (P2)
To obtain the solution to the non-concave optimization problem (P2), we also transform problem (P2) into two sub-problems of optimizing the transmission beamforming and reflection beamforming , respectively. The resultant sub-problems are efficient solved by utilizing an AO Algorithm similar to Algorithm 1.
1) Transmission Beamforming Optimization: For any given feasible , problem (P2) can be reduced to optimize only. We introduce the auxiliary variable and obtain . Thus, the optimization problem with respect to can be formulated as
| (50a) | ||||
| s.t. | (50b) | |||
| (50c) | ||||
| (50d) | ||||
| (50e) | ||||
| (50f) | ||||
| (50g) | ||||
| (50h) | ||||
| (50i) | ||||
where . Then, we apply the penalty-term method same as in problem (P3.1) to cope with the non-convexity of rank-one constraint in problem (P5), yielding the following transformed optimization problem:
| (51a) | ||||
| (51b) | ||||
Now, the above transmission beamforming problem is a concave optimization problem.
2) Reflection Beamforming Optimization: For any given , problem (P2) can be reduced to optimize only. With the introduced auxiliary variables in the previous section, we separately define with bing the th, , column of the beamforming matrix and with , and construct , yielding the expressions and . As a result, the reflection beamforming optimization problem is formulated as
| (52a) | ||||
| s.t. | (52b) | |||
| (52c) | ||||
| (52d) | ||||
| (52e) | ||||
| (52f) | ||||
| (52g) | ||||
| (52h) | ||||
Similar to the approach adopted in problem (P4), we transform problem (P6) into a concave one by applying the penalized Dinkelbach approach, which is formulated as
| (53a) | ||||
| (53b) | ||||
where
| (54) |
| (55) |
with being a penalty factor, and is a auxiliary variable updated by in the th iteration. After the above transformation, problem (P6.1) can be efficiently solved by the existing convex solvers. Similar to Algorithm 1, problem (P2) can be efficiently solved by iteratively solving the decoupled sub-problems (P5.1) and (P6.1)) with an AO Algorithm. Since the algorithm structure for solving problem (P2) is the same as Algorithm 1, we omit the details of the algorithm for solving problem (P2). In addition, the overall computational complexity of the algorithm for solving problem (P2) can be characterized by , where and denote the iteration numbers of the penalty-terms in problems (P5.1) and (P6.1), respectively.

IV Numerical Results
In this section, numerical results are provided to validate the system performance of the active-RIS-aided NOMA-ISAC system. Unless otherwise specified, we set , , , dBm, dBm, dBm, bps/Hz, , , and , . In the simulations, Alice, Bob, Grace, Willie, and active-RIS are located at m, m, m, m, and m, respectively, in an x-y coordinate plane. There are moving targets located at , , and , respectively, related to x-axis, and have distances of m, m, and m from Alice, respectively. The velocities of the three targets are ms, ms, and ms, respectively, and their RCSs satisfy . For the channel fading, the path-loss is modeled by with dB and denoting the distance between the two terminals. Specifically, we set for the Alice- link, for Alice- link, and for the channels associated with the active-RIS [25]. The Rician factor for the active-RIS-associated links is set as dB, while for the Alice- link is set as . In the following discussions, we compare the covert communication performance of the proposed active-RIS-aided NOMA-ISAC scheme against the passive-RIS-aided and without-RIS counterparts. To simulate the results of passive-RIS-aided NOMA-ISAC scheme, the covert rate maximization problems using both the w/o-DSS and w-DSS schemes are formulated by modifying the corresponding objectives and constraints. Specifically, constraint (40f) is modified as , constraint (5) is omitted, and is set to be zero in the corresponding objectives and constraints. In the following figures, the performance curves achieved by the active-RIS-aided and passive-RIS-aided NOMA-ISAC schemes are denoted as “A” and “P”, respectively, while the performance curves by the benchmark scheme without-RIS scheme are denoted as “w/o-RIS” in the legends.
The optimaml transit beampatterns achieved by the w-DSS and w/o-DSS schemes under various CRB thresholds are plotted in Fig 2, where we set and . Specifically, the transmit beamforming matrices of the w/o-DDS and w-DSS schemes are the optimized solutions of problems (P3.1) and (P5.1), respectively. The results in Fig. 2 show that the three moving targets are accurately captured in the mainlobes of the transmit beampatterns by the w-DSS and w/o-DSS schemes. Besides, the results in Fig. 2 reveals the impacts of CRB threshold on the transmit beampattern, i.e., a smaller CRB threshold can achieve a better beampattern because a smaller CRB threshold requires more transmit power to be allocated towards the target directions. Furthermore, since the CRB threshold constraints are the same for the w-DSS and w/o-DSS schemes, the transmit beampatterns achieved by the two schemes are almost identical in the mainlobes. Therefore, both the w-DSS and w/o-DSS schemes satisfy the sensing performance requirements in the considered system.
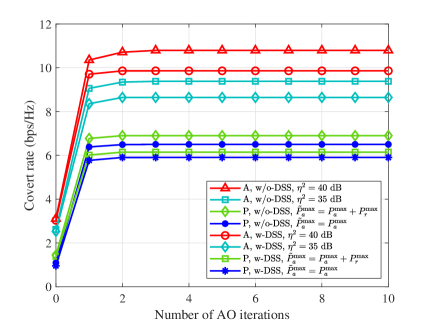
We show the convergence performance of the proposed AO algorithm in Fig. 3, where and . The covert rates versus the number of AO iterations under different settings of the active-RIS-aided and passive-RIS-aided systems are presented to verify the convergence of our proposed AO algorithm. Considering that the active-RIS introduces additional power supplies, the total system resource consumption is higher than the passive-RIS-aided system. For a relatively fair comparison with the passive-RIS-aided system, we consider two power budgets for the passive-RIS-aided system in which Alice has a power budget of either or . The curves of Fig. 3 show that the proposed AO algorithm converges within iterations for all the considered system settings. Furthermore, the covert rate almost no longer increases after iterations, which verifies the fast convergence and effectiveness of the proposed AO algorithm. Since the covert rate achieved in each iteration of transmission and reflection beamforming optimization consistently demonstrates a non-decreasing pattern, a limited number of iterations is sufficient for achieving convergence in the proposed AO algorithm.

In Fig. 4, we plot the curves of the covert rates achieved by the w/o-DSS and w-DSS schemes versus the CRB threshold to investigate the trade-off between covert communication performance and target parameter estimation performance. The without-RIS system is considered to have power budget for fair comparison. The curves in Fig. 4 clearly show the trade-off between the covert communication performance and target parameter estimation performance. As the CRB threshold relaxes, the priority is shifted to covert transmission, resulting in the increased covert rates for all the considered schemes. However, in the high CRB threshold regime, the covert rates achieved by all the schemes converge to be constant. Furthermore, both a higher and a looser covertness constraint lead to a higher covert rate, as verified by Fig. 4(a). When the w/o-DSS scheme is applied, the active-RIS-aided and passive-RIS-aided systems, as well as the w/o-RIS system achieve a better trade-off compared to the w-DSS scheme. The reason for this phenomenon is that the introduction of the DSS inevitably results in additional power consumption at Alice to realize sensing, thus leading to a degradation of the covert communication performance. The same phenomenon occurs at a stricter covertness level, i.e., decreases from to , and smaller reflection amplitude of active-RIS elements, i.e., dB, as shown in Fig. 4(a). In addition, the curves in Fig. 4 also reveal that the active-RIS-aided system has a significant advantage in the trade-off performance compared to the passive-RIS-aided system and w/o-RIS system. Furthermore, the passive-RIS provides negligible covert rate gain compared to w/o-RIS system. Due to the additional reflection gain loss and available covert transmission power loss, the passive-RIS-aided system using the w-DSS scheme with achieves the poorest trade-off performance.


In Fig. 5, to obtain more insights of the proposed schemes, we investigate the impacts of the moving target number on the trade-off between covert communication and sensing performances under the setting of and dB. When , Alice senses the target located at . When , we assume the targets located at and need to be detected, while all the three targets are considered for parameter estimation when . Analogous to the results in Fig. 4, the covert rates achieved by the cases of and increase with the increase of CRB threshold, i.e. the priority shifts to covert transmission. Furthermore, we observe that the w/o-DSS scheme also exhibits an explicit trade-off region gain over the w-DSS scheme when and . Attributing to the additional available transmit power for information transmission, the w/o-DSS scheme achieves a superior covert rate than the w-DSS scheme at the rightmost corner point for the considered three cases of target number. Besides, as the number of targets increases, the trade-off regions of both the w/o-DSS scheme and w-DSS scheme become worse due to the loss of the transmission beamforming power at each individual target.
In Fig. 6, we investigate the impacts of the transmit power budget on the covert rate for different schemes, where we set dBm and . From Fig. 6, we can see that the covert rates achieved by all the schemes increase with the increasing . Furthermore, the active-RIS-aided systems always outperform the passive-RIS-aided systems and w/o-RIS systems no matter when which transmission scheme is adopted. As expected, the improvement in covert performance is very little for the passive-RIS-aided systems compared to the w/o-RIS system due to the “multiplicative fading effect”. The curves in Fig. 6 confirm that a higher leads to a higher covert rate, which indicates that the constraints (5) and (30) are inactive, respectively. Thanks to the additional covert rate gain provided by the active-RIS and more available transmit power for covert transmission in the absence of the DSS, the active-RIS system using the w/o-DSS scheme achieves a considerably large covert rate in the high transmit power regime. The curves in Fig. 6 reveal that the passive-RIS-aided system with achieves a higher covert rate than the passive-RIS-aided system with in the low transmit power regime due to the additional transmit power budget, while the achieved covert rate of the consider two passive-RIS-aided systems tend to overlap with the increasing of . Thus, in the high regime, transmit power enhancement cannot achieve a higher covert rate in the passive-RIS-aided system.

Fig. 7 shows the covertness level versus the covert rate under the two transmission schemes, where we set . Both the passive-RIS-aided system with two considered power budgets and the w/o-RIS system are taken into consideration. As clearly shown by the curves in Fig. 7, the active-RIS-aided system exhibits an improved covertness performance with the increase of compared with the passive-RIS-aided system, which suffers the “multiplicative fading effect”, resulting in negligible covert rate gain compared to the without-RIS system. This result is consistent with the theoretical analysis, i.e., when becomes larger, the covertness constraint becomes loose, and the allocatable transmit power for and the reflection beamforming power towards Bob is larger, which leads to a larger covert rate for the active-RIS-aided system. Moreover, in the passive-RIS-aided system, as the covertness constraint is relaxed, the increase of the covert rate achieved by the w/o-DSS scheme is slower than that of the w-DSS scheme. This result is because the DSS can also be utilized as the covert medium to conceal the covert transmission from Alice to Bob, resulting in the covert rate growth achieved by the w-DSS scheme being larger than that of the w/o-DSS scheme as the covertness constraint loosing. Again, the active-RIS-aided system with the w/o-DSS scheme achieves a higher covert rate than with the w-DSS scheme, while the same thing occurs in the without-RIS system and passive-RIS-aided system, no matter which transmit power budget is applied.

In the next, the impacts of the number of the RIS reflecting elements, the number of the transmit antennas, and the horizontal position of the RIS on the covert performance are respectively investigated. Unless otherwise stated, we set , and in the simulations. The curves in Fig. 8 compare the covert rate performance versus the number of the RIS elements . For the active-RIS-aided system, it is obvious that more reflecting elements of the active-RIS provide more reflection beamforming gain and achieve a higher covert rate due to more DoFs exploited to manipulate the propagation environments. However, the additional reflection beamforming gain is negligible for passive-RIS-aided system, again due to the “multiplicative fading effect”. When the w/o-DSS scheme is applied, both the active-RIS-aided and passive-RIS-aided systems obtain a higher covert rate than the w-DSS scheme. Furthermore, the covert rate achieved by the active-RIS-aided system is significantly higher than that of the passive-RIS-aided system, no matter which transmit power budget is applied. The results also show that the passive-RIS-aided system with is better than the passive-RIS-aide system with due to more transmit power budget at Alice. By comparing the considered two transmission schemes, we see that additional reflecting elements provide more marked covert rate gains in the w/o-DSS scheme provides. To sum up, exploiting the NOMA signal only can achieve a better covert communication performance than utilizing the DSS in the considered RIS-aided NOMA-ISAC systems.
In Fig. 9, we investigate the impacts of the number of transmit antennas on the covert communication performance under different schemes. It can be seen that the covert rates achieved by all the considered schemes increase with the increasing owing to the enhanced array gain. The covert rate achieved in the active-RIS-aided system increases smoothly at first from to , and then increases more dramatically with the continued increasing . This result is due to the extra spatial DoFs introduced by the additional transmit antennas, thereby increasing the transmission beamforming resolution. Besides, the covert communication performance of the active-RIS-aided system hugely outperforms the passive-RIS-aided system and w/o-RIS system due to the additional covert rate gain provided by the larger reflecting amplitude of the active-RIS. From the perspective of covert communications, although the phase shift modulation of the passive-RIS can be employed to reduce the DEP at Willie, the passive-RIS reflection gain is negligible in the considered NOMA-ISAC system due to the severe ”multiplicative fading effect”. For the passive-RIS-aided system, the transmit power budget with scheme provides additional SNR for Bob compared to the transmit power budget with scheme, resulting in a higher covert rate, as indicated in Fig. 9. Fig. 9 also reveals that the presence of DSSs degrades the covert rate because the introduction of inevitably results in additional power consumption at Alice, thus leading to less transmit power for covert transmission.

Fig. 10 shows the covert rate versus the RIS’s horizontal position (x-coordinate) under different RIS schemes with the considered two transmission schemes, where the vertical position of RIS is fixed at m. It shows that the covert rates achieved by active-RIS-aided system increase with increasing horizontal position, until reaching about m and beginning to decrease, which indicates that when the active-RIS is properly deployed close to Bob and Willie, the highest covert rate gain of reflection beamforming can be obtained. On the contrary, the covert rates achieved by the passive-RIS-aided system change slightly with the increase of the horizontal position of the RIS, whereas the achieved covert rates are far less than those achieved by the active-RIS-aided system since the reflecting amplitude is limited at . Furthermore, the passive-RIS-aided system with transmit power budget scenario achieves a higher covert rate than the passive-RIS-aided system with transmit power budget scenario, which is expected due to the additional power gain. Fig. 10 also reveals that the covert performance of the w/o-DSS scheme outperforms that of the w-DSS scheme for both active-RIS-aided and passive-RIS-aided systems. Intuitively, when the DDSs are utilized as the shield to cover up the covert transmission for Bob, the covertness level should be better and the lower DEP at Willie may be achieved. Actually, for the considered NOAM-ISAC system, the shield of the NOMA public user’s signal is strong enough to achieve ideal covert performance at the same covertness level while allowing more transmit power budget to improve the covert rate at the NOMA covert user. In a nutshell, for the considered NOMA-ISAC system, the DSS is an obstruction to achieve the best covert performance and trade-off between communication and sensing.

V Conclusions
In this paper, two superposition transmission schemes, namely, the w-DSS and w/o-DSS schemes, were applied to enhance the covert communication and sensing performances for the active-RIS-aided NOMA-ISAC system. To tackle the non-concave covert rate maximization problem, in which the joint optimization of the transmission and reflection beamforming is needed, we decoupled the optimizations of the transmission and reflection beamforming and proposed an AO algorithm to maximize the covert rate. The rank-one constrained fractional programming sub-problems were efficiently solved by introducing the penalized Dinkelbach transformation. The numerical results verified the superiority of the active-RIS-aided NOMA-ISAC system in terms of covert rate and trade-off between communication and sensing performances over that of the passive-RIS-aided and without-RIS NOMA-ISAC system. It was shown that the w/o-DSS scheme achieves a better system performance than the w-DSS scheme. Specifically, it was clarified that exploiting only the NOMA signal achieves the same sensing performance as exploiting the superposition of NOMA signal and DSS, while the additional transmission power gain can be exploited by the w/o-DSS scheme to enhance the covert communication performance.
Appendix
derivation of the FIM in (13)
The matrix is related to four target parameters , . According to (11), the received free-noise signal at Alice is given by . The derivatives of with respect to each parameter can be calculated as
| (56) |
| (57) |
| (58) |
where , is the th column of , and denotes the partial derivatives of with respect to . We note that
| (59) |
Since , and and are diagonal matrices, (59) can be rewritten as
| (60) | |||||
where refer to the th row and th column element of the matrix. As a result, we obtain with specified in (14). Similarly, other terms of can be obtained in the same way by calculating the corresponding partial derivative, which results in the FIM in (13).
References
- [1] Y. Cui, F. Liu, X. Jing, and J. Mu, “Integrating sensing and communications for ubiquitous IoT: Applications, trends, and challenges,” IEEE Network, vol. 35, no. 5, pp. 158–167, Sep. 2021.
- [2] X. Cheng, D. Duan, S. Gao, and L. Yang, “Integrated sensing and communications (ISAC) for vehicular communication networks (VCN),” IEEE Internet Things J., vol. 9, no. 23, pp. 23 441–23 451, Dec. 2022.
- [3] F. Liu, L. Zhou, C. Masouros, A. Li, W. Luo, and A. Petropulu, “Toward dual-functional radar-communication systems: Optimal waveform design,” IEEE Trans. Signal Process., vol. 66, no. 16, pp. 4264–4279, Aug. 2018.
- [4] R. Liu, M. Li, Q. Liu, and A. L. Swindlehurst, “Dual-functional radar-communication waveform design: A symbol-level precoding approach,” IEEE J. Sel. Topics Signal Process., vol. 15, no. 6, pp. 1316–1331, Nov. 2021.
- [5] F. Liu, Y.-F. Liu, A. Li, C. Masouros, and Y. C. Eldar, “Cramér-rao bound optimization for joint radar-communication beamforming,” IEEE Trans. Signal Process., vol. 70, pp. 240–253, Dec. 2022.
- [6] Z. Wang, Y. Liu, X. Mu, Z. Ding, and O. A. Dobre, “NOMA empowered integrated sensing and communication,” IEEE Commun. Lett., vol. 26, no. 3, pp. 677–681, Mar. 2022.
- [7] X. Mu, Y. Liu, L. Guo, J. Lin, and L. Hanzo, “NOMA-aided joint radar and multicast-unicast communication systems,” IEEE J. Select. Areas Commun., vol. 40, no. 6, pp. 1978–1992, Jun. 2022.
- [8] Z. Wang, Y. Liu, X. Mu, and Z. Ding, “NOMA inspired interference cancellation for integrated sensing and communication,” in Proc. ICC 2022 - IEEE Inter. Conf. Commun., Seoul, Korea, Republic of, 16-20 May 2022, pp. 3154–3159.
- [9] X. Mu, Z. Wang, and Y. Liu, “NOMA for integrating sensing and communications towards 6G: A multiple access perspective,” IEEE Wireless Commun., pp. 1–8, Jan. 2023.
- [10] C. Zhang, W. Yi, and Y. Liu, “Semi-integrated-sensing-and-communication (Semi-ISaC) networks assisted by NOMA,” in Proc. IEEE Int. Conf. Commun. (ICC), Seoul, Korea, Republic of, 16-20 May 2022, pp. 3790–3795.
- [11] Z. Yang, D. Li, N. Zhao, Z. Wu, Y. Li, and D. Niyato, “Secure precoding optimization for NOMA-aided integrated sensing and communication,” IEEE Trans. Commun., vol. 70, no. 12, pp. 8370–8382, Dec. 2022.
- [12] D. Luo, Z. Ye, and J. Zhu, “Secure transmit beamforming for radar-communication systems using NOMA,” IEEE Commun. Lett., vol. 26, no. 11, pp. 2557–2561, Nov. 2022.
- [13] Z. Wei, F. Liu, C. Masouros, N. Su, and A. P. Petropulu, “Toward multi-functional 6G wireless networks: Integrating sensing, communication, and security,” IEEE Commun. Mag., vol. 60, no. 4, pp. 65–71, Apr. 2022.
- [14] S. Ma, H. Sheng, R. Yang, H. Li, Y. Wu, C. Shen, N. Al-Dhahir, and S. Li, “Covert beamforming design for integrated radar sensing and communication systems,” IEEE Trans. Wireless Commun., vol. 22, no. 1, pp. 718–731, Jan. 2023.
- [15] H. Du, J. Kang, D. Niyato, J. Zhang, and D. I. Kim, “Reconfigurable intelligent surface-aided joint radar and covert communications: Fundamentals, optimization, and challenges,” IEEE Veh. Technol. Mag., vol. 17, no. 3, pp. 54–64, Sep. 2022.
- [16] H. Luo, R. Liu, M. Li, Y. Liu, and Q. Liu, “Joint beamforming design for RIS-assisted integrated sensing and communication systems,” IEEE Trans. Veh. Technol., vol. 71, no. 12, pp. 13 393–13 397, Dec. 2022.
- [17] X. Wang, Z. Fei, Z. Zheng, and J. Guo, “Joint waveform design and passive beamforming for RIS-assisted dual-functional radar-communication system,” IEEE Trans. Veh. Technol., vol. 70, no. 5, pp. 5131–5136, May 2021.
- [18] J. Zuo, Y. Liu, C. Zhu, Y. Zou, D. Zhang, and N. Al-Dhahir, “Exploiting NOMA and RIS in integrated sensing and communication,” IEEE Trans. Veh. Technol., vol. 72, no. 10, pp. 12 941–12 955, Oct. 2023.
- [19] X. Tan, Z. Sun, J. M. Jornet, and D. Pados, “Increasing indoor spectrum sharing capacity using smart reflect-array,” in Proc. 2016 IEEE Int. Conf. Commun. (ICC), Kuala Lumpur, Malaysia, 22-27 May 2016, pp. 1–6.
- [20] L. Lv, Q. Wu, Z. Li, Z. Ding, N. Al-Dhahir, and J. Chen, “Covert communication in intelligent reflecting surface-assisted NOMA systems: Design, analysis, and optimization,” IEEE Trans. Wireless Commun., vol. 21, no. 3, pp. 1735–1750, Mar. 2022.
- [21] L. Yang, W. Zhang, P. S. Bithas, H. Liu, M. O. Hasna, T. A. Tsiftsis, and D. W. K. Ng, “Covert transmission and secrecy analysis of RS-RIS-NOMA-aided 6G wireless communication systems,” IEEE Trans. Veh. Technol., vol. 72, no. 8, pp. 10 659–10 670, Aug. 2023.
- [22] Y. Zhang, W. He, X. Li, H. Peng, K. Rabie, G. Nauryzbayev, B. M. ElHalawany, and M. Zhu, “Covert communication in downlink NOMA systems with channel uncertainty,” IEEE Sensors J., vol. 22, no. 19, pp. 19 101–19 112, Oct. 2022.
- [23] R. Long, Y.-C. Liang, Y. Pei, and E. G. Larsson, “Active reconfigurable intelligent surface-aided wireless communications,” IEEE Trans. Wireless Commun., vol. 20, no. 8, pp. 4962–4975, Aug. 2021.
- [24] K. Zhi, C. Pan, H. Ren, K. K. Chai, and M. Elkashlan, “Active RIS versus passive RIS: Which is superior with the same power budget?” IEEE Commun. Lett., vol. 26, no. 5, pp. 1150–1154, May 2022.
- [25] L. Dong, H.-M. Wang, and J. Bai, “Active reconfigurable intelligent surface aided secure transmission,” IEEE Trans. Veh. Technol., vol. 71, no. 2, pp. 2181–2186, Feb. 2022.
- [26] M. Wang, Z. Xu, B. Xia, and Y. Guo, “Active intelligent reflecting surface assisted covert communications,” IEEE Trans. Veh. Technol., vol. 72, no. 4, pp. 5401–5406, Apr. 2023.
- [27] M. Zhu, K. Guo, Y. Ye, L. Yang, T. A. Tsiftsis, and H. Liu, “Active RIS aided covert communications for MISO-NOMA systems,” IEEE Wireless Commun. Lett., vol. 12, no. 12, pp. 2203–2207, Dec. 2023.
- [28] J. Li, G. Zhou, T. Gong, and N. Liu, “Beamforming design for active IRS-aided MIMO integrated sensing and communication systems,” IEEE Wireless Commun. Lett., pp. 1786 – 1790, Oct. 2023.
- [29] Q. Zhu, M. Li, R. Liu, and Q. Liu, “Joint transceiver beamforming and reflecting design for active RIS-aided ISAC systems,” IEEE Trans. Veh. Technol., vol. 72, no. 7, pp. 9636–9640, Jul. 2023.
- [30] Y. Zhang, J. Chen, C. Zhong, H. Peng, and W. Lu, “Active IRS-assisted integrated sensing and communication in C-RAN,” IEEE Wireless Commun. Lett., vol. 12, no. 3, pp. 411–415, Mar. 2023.
- [31] C. Liao, F. Wang, G. Han, Y. Huang, and V. K. N. Lau, “Beamforming design for hybrid active-passive RIS assisted integrated sensing and communications,” IEEE Commun. Lett., pp. 2938–2942, Nov. 2023.
- [32] W. Hao, H. Shi, G. Sun, and C. Huang, “Joint beamforming design for active RIS-aided THz ISAC systems with delay alignment modulation,” IEEE Wireless Commun. Lett., pp. 1816–1820, Oct. 2023.
- [33] Z. Yu, H. Ren, C. Pan, G. Zhou, B. Wang, M. Dong, and J. Wang, “Active RIS aided ISAC systems: Beamforming design and performance analysis,” IEEE Trans. Commun., pp. 1–1, Nov. 2023.
- [34] Z. Chen, J. Ye, and L. Huang, “A two-stage beamforming design for active RIS aided dual functional radar and communication,” in Proc. 2023 IEEE Wireless Commun. Netw. Conf. (WCNC), Glasgow, United Kingdom, 26-29 Mar. 2023, pp. 1–6.
- [35] A. A. Salem, M. H. Ismail, and A. S. Ibrahim, “Active reconfigurable intelligent surface-assisted MISO integrated sensing and communication systems for secure operation,” IEEE Trans. Veh. Technol., vol. 72, no. 4, pp. 4919–4931, Dec. 2022.
- [36] B. A. Bash, D. Goeckel, and D. Towsley, “Limits of reliable communication with low probability of detection on AWGN channels,” IEEE J. Sel. Areas Commun., vol. 31, no. 9, pp. 1921–1930, Sep. 2013.
- [37] H. Hua, J. Xu, and T. X. Han, “Optimal transmit beamforming for integrated sensing and communication,” IEEE Trans. Veh. Technol., vol. 72, no. 8, pp. 10 588–10 603, Aug. 2023.
- [38] S. M. Kay, “Fundamentals of statistical signal processing: estimation theory,” Technometrics, vol. 37, p. 465, Mar. 1993.
- [39] S. Boyd and L. Vandenberghe, Convex Optimization. Cambridge, U.K.: Cambridge Univ. Press, Mar. 2004.
- [40] W. Dinkelbach, “On nonlinear fractional programming,” Management Science, vol. 13, no. 7, pp. 492–498, Mar. 1967.