A Survey on Adversarial Attacks
for Malware Analysis
Abstract
The last decade has experienced an exponential growth in research and adoption of Machine Learning (ML) and Artificial Intelligence (AI), and its application in different use-cases. Traditional machine learning algorithms have evolved into data intensive deep learning architectures, which have fostered cutting edge and unprecedented technological advancements revolutionizing today’s world. The capability of these ML algorithms to uncover knowledge and patterns from semi- or unstructured data to support automation in decision making has led to the revamping of domains such as medicine, e-commerce, autonomous cars, and cybersecurity. The growth and adoption of machine learning solutions have been lately slowed down with the advent of adversarial attacks. Adversaries are able to modify data at training and testing time, maximizing the classification error of the ML models. Minor intentional perturbations in test samples are crafted by the adversaries to exploit the discovered blind spots in trained models. The increased data dependency of these algorithms have offered a way for high incentives to disguise ML models. In order to survive against possible catastrophic implications, continuous research is required to find vulnerabilities in form of adversarial and design resilient autonomous systems.
Machine learning-based malware analysis approaches are widely researched and deployed in critical infrastructures for detecting and classifying evasive and growing malware threats. However, minor perturbations or few ineffectual bytes insertion can easily ’fool’ these trained ML classifiers, essentially making them ineffective against these crafted and smart malicious software. This survey aims at providing an encyclopedic introduction to adversarial evasion attacks that are carried out specifically against malware detection and classification systems. Since most of the research in the adversarial malware domain is new and has been performed in the last couple of years, our survey will cover the relevant literature published on the malware adversarial evasion attacks between the year 2013 to 2021. The paper will begin by introducing various machine learning techniques used to generate adversarial in malware analysis and explaining the structures of target files. The survey will model the threat posed by adversaries followed by brief descriptions of widely used adversarial algorithms. We will also provide a taxonomy of adversarial evasion attacks with respect to the attack domains and adversarial generation techniques that are widely used in malware detection and classification. Adversarial evasion attacks carried out against malware detectors will be discussed under each taxonomical headings and compared with related literature. The survey will conclude by highlighting the open problems, challenges and future research directions.
Index Terms:
Adversarial Evasion attack, Adversary Modeling, Data Poisoning, Malware Analysis, Machine Learning, Deep Learning, Security, Windows Malware, Android Malware, PDF Malware1 Introduction
Machine Learning has revolutionized the modern world due to its ubiquity and generalization power over the humongous volume of data. With Zettabytes of data hovering around the cloud [1], modern technology’s power resides in extracting knowledge from these unstructured raw data. Machine learning (ML) has provided the unprecedented power to automate the decision-making process, outperforming humans by far margin. ML has powered more robust and representative feature set in comparison to hand-crafted features. Transformation of ML approaches from classical algorithms to modern deep learning technologies are providing the major breakthroughs in state-of-art research problems. Further, deep learning (DL) has excelled in areas where traditional ML approaches were infeasible (or unsuccessful) to apply. The evolving deep learning techniques have furnished the fields of natural language processing [2, 3, 4], image classification [5, 6, 7, 8], autonomous driving [9, 10, 11, 12], neuro science [13, 14, 15, 16] and many other wide range of domains. Society is experiencing high-end amazing products like Apple Siri111https://www.apple.com/siri/, Amazon Alexa222https://alexa.amazon.com/ and Microsoft Cortana333https://www.microsoft.com/en-us/cortana due to recent advances in machine learning and artificial intelligence (AI). Needless to say that machine learning has started shaping our daily life habits; connecting to people on social media, ordering food and groceries from online stores, listening to music on Spotify444https://www.spotify.com/us/, watching movies on Netflix555https://www.netflix.com/, reading online news and books, are all examples of systems built around the recommendation engines powered by deep learning based models. Machine learning based solutions not only control our lifestyle but it has also revolutionized cyber security critical operations in different domains including malware analysis [17, 18, 19, 20, 21, 22], spam filtering [23, 24, 25, 26], fraud detection [27, 28, 29, 30], medical analysis [31, 32, 33, 34, 35], access control [36, 37, 38, 39], among others.
Malware analysis is one of the most critical fields where ML is being significantly employed. Traditional malware detection approaches [40, 41, 42, 43, 44] rely on signatures where unique identifiers of malware files are maintained in a database and are compared to extracted signatures from newly encountered suspicious files. However, several techniques are used to rapidly evolve the malware to avoid detection (more details in Section 4). With security researchers looking for detection techniques addressing such sophisticated zero-day and evasive malware, ML based approaches came to their rescue [45]. Most of the modern anti-malware engines, such as Windows Defender666https://www.microsoft.com/en-us/windows/comprehensive-security, Avast777https://www.avast.com/, Deep Instinct D-Client888https://www.deepinstinct.com/endpoint-security and Cylance Smart Antivirus999https://shop.cylance.com/us, are powered by machine learning[46], making them robust against emerging variants and polymorphic malware [47]. As per some estimates [48], around 12.3 billion devices are connected worldwide and spread of malware in this scale can result in catastrophic consequences. As such, it is evident that economies worth billions of dollars are directly or indirectly relying on machine learning’s performance and growth to be protect from this rapidly evolving menace of malware. Despite the existence of numerous malware detection approaches, including ones that leverage ML, recent ransomware attacks, like the Colonial Pipeline attack where operators had to pay around $5 million for recovering 5,500-mile long pipeline[49], the MediaMarkt attack worth around $50M bitcoin payment [50] and the computer giant Acer attack [51], highlight the vulnerabilities and limitations of current security approaches, and necessitates more robust, real-time, adaptable and autonomous defense mechanisms powered by AI and ML.

The performance of ML models relies on the basic assumption that training and testing are carried out under similar settings and that samples from training and testing datasets follow independent and identical distribution. This assumption is overly simplified and, in many cases, does not hold true for real world use-cases where adversaries deceive the ML models into performing wrong predictions (i.e. adversarial attacks). In addition to traditional threats like malware attack [52, 53, 54], phishing [55, 56, 57], man-in-the-middle attack [58, 59, 60], denial-of-service [61, 62, 63] and SQL injection [64, 65, 66], adversarial attacks has now emerged as a serious concern, threatening to dismantle and undermine all the progress made in the machine learning domain.
Adversarial attacks are carried out either by poisoning the training data or manipulating the test data (evasion attacks). Data poisoning attacks [67, 68, 69, 70] have been prevalent for some time but are less scrutinized as access to training data by the attackers is considered unlikely. In contrast, evasion attacks, first introduced by Szegedy et al. [71] against deep learning architectures, are carried out by carefully crafting imperceptible perturbation in test samples, forcing models to mis-classify as illustrated in Figure 1. Here, the attacker’s effort is to drag a test sample across the ML’s decision boundary through the addition of minimal perturbation to that sample. Considering the availability of research works and higher-risk in practicality, this survey will entirely focus on adversarial evasion attacks that are carried out against the malware detectors.
Adversarial evasion attacks were initially crafted on images as the only requirement for perturbation in an image is that it should be imperceptible to the human eye [72, 73]. A very common example for adversarial attack in images, shown in Figure 2, is performed by Goodfellow et al. [74] where GoogLeNet [75] trained on ImageNet[76] classifies panda as gibbon with addition of very small perturbations. This threat is not limited to experimental research labs but have already been successfully demonstrated in real world environments. For instance, Eykholt et al. performed sticker attacks to road signs forcing the image recognition system to detect ’STOP’ sign as a speed limit. Researchers from the Chinese technology company Tencent101010https://www.tencent.com/ tricked Tesla’s111111https://www.tesla.com/ Autopilot in Model S and forced it to switch lanes by adding few stickers on the road [77]. Such adversarial attacks on real world applications force us to rethink the increasing reliability over smart technologies like Tesla Autopilot121212https://www.tesla.com/autopilot.

| Paper | Year | Application Domain | Taxonomy |
Threat Modeling |
Adversarial Example |
|---|---|---|---|---|---|
| Barreno et al. [78] | 2008 | Security | Attack Nature | ||
| Gardiner et al. [79] | 2016 | Security | Attack Type/Algorithm | ||
| Kumar et al. [80] | 2017 | General | Attack Type | ||
| Yuan et al. [81] | 2017 | Image | Algorithm | ||
| Chakraborty et al. [82] | 2018 | Image/Intrusion | Attack Phase | ||
| Akhtar et al. [83] | 2018 | Image | Image domains | ||
| Duddu et al. [84] | 2018 | Security | Attack Type | ||
| Li et al. [85] | 2018 | General | Algorithm | ||
| Liu et al. [86] | 2018 | General | Target Phase | ||
| Biggio et al. [87] | 2018 | Image | Attack Type | ||
| Sun et al. [88] | 2018 | Image | Image Type | ||
| Pitropakis et al. [89] | 2019 | Image/Intrusion/Spam | Algorithm | ||
| Wang et al. [90] | 2019 | Image | Algorithm | ||
| Qiu et al. [91] | 2019 | Image | Knowledge | ||
| Xu et al. [92] | 2019 | Image/Graph/Text | Attack Type | ||
| Zhang et al. [93] | 2019 | Natural Language Processing | Knowledge/Algorithm | ||
| Martins et al. [94] | 2019 | Intrusion/Malware | Approach | ||
| Moisejevs [95] | 2019 | Malware Classification | Attack Phase | ||
| Ibitoye et al. [96] | 2020 | Network Security | Approach/Algorithm | ||
| Our Work | 2021 | Malware Analysis | Domain/Algorithm |
Year: Published Year, Application Domain: Dataset domain on which adversarial is crafted, Taxonomy: Basis on which attack taxonomy is made, Threat Modeling: Presence of threat modeling, Adversarial Example: Discuss actual adversarial attacks crafted in literature
However, adversarial generation is a completely different game in the malware domain, in comparison to computer vision, due to the increased number of constraints. Perturbations in malware files should be generated in a way that it should not affect both their functionality and executability. Adversarial evasion attacks on malware are carried out by manipulating or inserting few ineffectual bytes in the malware executables in a way that does not tamper with its original state, but change the classification decision by the ML model. For instance, one early demonstrated attack against anti-malware engine was carried out by Anderson et al. [97] using reinforcement learning. This black-box attack was able to bypass Random forest and gradient boosted decision trees (GBDT) detectors by modifying few bytes of Windows PE malware files. Kolosnjaji et al. [98] carried out evasion attack using gradient based approach against convolutional neural network (CNN) based malware detector. Since then, there has been numerous works trying to optimize the attacks, discovering better approaches to attack wide domains of malware detectors. Demetrio et al. [99] success in crafting adversarial from few header byte modification and Suciu et al. [100] experiment on inserting perturbations in different file locations, further magnified the interest towards improving the standard of attacks. The fear of evolving adversarial attack is growing among the cyber security research community and has provoked the everlasting war between adversarial attackers and defenders. To help researchers better understand the current situation of adversarial attacks in the malware domain and infer vulnerabilities on current approaches, this paper will provide a comprehensive survey of ongoing adversarial evasion attack researches against Windows, Android, PDF, Linux and Hardware-based malware.
1.1 Motivation and Contribution
1.1.1 Prior Surveys and Limitations
The surveys on adversarial attacks crafted in different domains have been summarized in Table I. Majority of surveys on adversarial attacks are focused on computer vision for images mis-classification. Yuan et al. [81] summarized major adversarial generation methods for images. Chakraborty et al. [82] surveyed adversarial in form of evasion and poisoning in image and anomaly detection. Akhtar et al.’s [83] work was restricted on the computer vision domain like most of the works. Biggio et al. [87] presented a historical timeline of evasion attacks along with works carried out on security of deep neural networks. Sun et al. [88] surveyed practical adversarial examples on graph data. Many of the surveys did not only focused on a single domain but covered generalized field across multiple domains including image, text, graph, intrusion, spam and malware. Kumar et al. [80] classified adversarial attacks into four overlapping classes. Li et al. [101] explains adversarial generation and defense mechanism through formal representation. Liu et al. [86] reviewed some general security threats and associated defensive techniques. Pitropakis et al. [89] surveyed adversarial in intrusion detection, spam filtering and image domain. Xu et al. [92] surveyed vulnerabilities, analysed reasons behind it and also proposed ways to detect adversarial examples. There have been a few works focusing on the security related domains like intrusion, malware, and network security. Barreno et al. [78] worked on one of the very first surveys done on security of machine learning where different categories of attacks and defenses against ML systems are discussed. Gardiner et al. [79] focused on reviewing call and control detection techniques. They identified vulnerabilities and also pointed limitations of malware detection systems. Duddu et al. [84] discussed the concern of privacy being leaked by information handled by machine learning algorithms. They also presented cyber-warfare testbed for the effectiveness of attack and defense strategies. Martins et al. [94] performed generalized survey on attacks focusing on cloud security, malware detection and intrusion detection. Ibitoye et al. [96] surveyed adversarial attacks in network domain using risk grid map.
With the discussed surveys, we can make certain conclusions reflecting the growing attention and concerns in the community as the world moves toward automation. First, the interest of people in adversarial domain has surged in last 3 or 4 years. Second, very few of the survey papers is solely focused on adversarial malware analysis, which is a growing menace. Majority of the surveys conducted on adversarial domain is built around computer vision attacks. Recent flux of works are spread in wide domains including network, natural language processing, security, and intrusion detection. There has been limited research on adversarial attacks in malware analysis, being a relatively new domain. The few existing surveys on malware domain are not focused on malware analysis but spread around multiple domains. The current surveys also does not cover entire attacks carried out on malware detection domain, but focuses on small subset of attacks. The outpouring interests in adversarial and lack of surveys justifying entire adversarial attacks on malware domain, motivates us to extensively survey adversarial evasion attack on malware.
| Acronym | Full Form |
|---|---|
| ACER | Actor Critic model with Experience Replay |
| AE | Adversarial Example |
| AI | Artificial Intelligence |
| AMAO | Adversarial Malware Alignment Obfuscation |
| API | Application Programming Interface |
| ATMPA | Adversarial Texture Malware Perturbation Attack |
| BFA | Benign Features Append |
| BRN | Benign Random Noise |
| CFG | Control Flow Graph |
| CNN | Convolutional Neural Network |
| CRT | Cross Reference Table |
| CW | Carlini-Wagner |
| DCGAN | Deep Convolutional GAN |
| DE | Differential Evolution |
| DL | Deep Learning |
| DNN | Deep Neural Network |
| DRL | Deep Reinforcement Learning |
| FGM | Fast Gradient Method |
| FGSM | Fast Gradient Sign Method |
| GADGET | Generative API Adversarial Generic Example by Transferability |
| GAN | Generative Adversarial Network |
| GAP | Global Average Pooling |
| GBDT | Gradient Boosted Decision Trees |
| GD-KDE | Gradient Descent and Kernel Density Estimation |
| GEA | Graph Embedding and Augmentation |
| GRU | Gated Recurrent Units |
| HDL | Hardware Description Language |
| HMD | Hardware Malware Detectors |
| IoT | Internet of Things |
| KNN | K-Nearest Neighbors |
| LLC | Logical Link Control |
| LR | Logistic Regression |
| LRP | Layer-wise Relevance Propagation |
| LSTM | Long Short Term Memory |
| MEV | Modification Evaluating Value |
| MIM | Momentum Iterative Method |
| ML | Machine Learning |
| MLP | Multi Layer Perceptron |
| MRV | Malware Recomposition Variation |
| OPA | One Pixel Attack |
| Portable Document Format | |
| PE | Portable Executable |
| PGD | Projected Gradient Descent |
| ReLU | Rectified Linear Unit |
| RF | Random Forest |
| RL | Reinforcement Learning |
| RNN | Recurrent Neural Network |
| RTLD | Resource Temporal Locale Dependency |
| SDG | System Dependency Graph |
| SHAP | SHapley Additive exPlanation |
| SR | Success Rate |
| SVM | Support Vector Machine |
| TCD | Trojan-net Concealment Degree |
| TLAMD | A Testing framework for Learning based Android Malware Detection systems for IoT Devices |
| TPR | True Positive Rate |
| VOTE | VOTing based Ensemble |
| ZOO | Zeroth Order Optimization |

1.1.2 Our Contributions
This work will contribute in understanding the arms race between attacker and defender by discussing adversarial evasion attacks in different folds of the malware domain. We aim to provide completely self-contained survey on adversarial attacks carried out against malware detection techniques. Based on our knowledge, this work is one among the first to solely focus on adversarial attacks on malware detection systems. In this work, our contributions cover the following dimensions:
-
•
As our goal is to make the survey as comprehensive as possible, we provide all the related information required to completely comprehend the contents of the survey. We discuss the machine learning approaches used, the adversarial generation algorithms used by attackers, the malware detection methods attacked and the structure of files that has been exploited to insert adversarial perturbations.
-
•
We provide the threat modeling to adversarial evasion attacks carried out in malware domain. The threat model helps in quantify and analyze the attack-specific risk associated to particular target of malware. The threat is modeled in terms of attack surface of the malware detector, attacker’s knowledge about the malware detector, attacker’s capabilities on malware, and adversarial goals that is to be achieved through the malware files. The proper threat modeling also helps to well understand the behaviors of malware, allowing the adversarial attacker to craft effective perturbations.
-
•
We systematically analyze different adversarial generation algorithms proposed in different domains, which have been attempted to be used in the malware domain. We then discuss the basics of standard adversarial algorithms and taxonomize adversarial evasion attacks in the malware domain with respect to various attack domains. As Windows malware are the most abundant and also the most exploited area, we further taxonomize attacks on Windows malware based on the attack algorithms used. We also discuss attacks carried out in the less frequent file structures like Android and PDF.
-
•
We discuss real evasion attacks carried out against anti-malware engines by the researchers, under each taxonomical headings. We also cover the attack strategies used by researchers to generate adversarial attacks, showing how the attacks evolved with time. Further, we compare the motivation and limitations of each research in tabular forms for each taxonomy-class.
-
•
We discuss the challenges and limitations on existing adversarial attacks while carrying out in real world environment. We also highlight the future research directions to carry out more practical, robust, efficient and generalized adversarial attacks on malware classifiers.
1.2 Survey Organization
In this paper, we structure our survey in a hierarchical manner as shown in Figure 3. Section 6 is placed before section 5 in the Figure 3 just to manage space but actual order in the paper is in incremental order of section number. We begin our survey, as discussed in Section 1, by introducing the field of adversarial machine learning along with motivation for the need to study adversarial attacks in the malware analysis domain. Note that Table II provides acronyms that are used frequently in the survey. Section 2 discusses different machine and deep learning algorithms that are used in state-of-art adversarial research. Understanding key concepts of machine learning prerequisites provides the readers the appropriate background to grasp adversarial generation techniques discussed later in the survey. Section 3 explains the structures of Windows, Android and PDF files. The structure of files plays a key role in apprehending adversarial attacks as perturbation depends on flow and robustness of files’ structure. Section 4 provides an introduction to malware detection approaches against which adversarial attacks are designed. Section 5 models the adversarial threat from different dimensions. This section briefly elaborates on attack surface, attacker’s knowledge, attacker’s capabilities and adversarial goals. Section 6 discusses various adversarial algorithms that are considered as standard techniques for perturbation generation across different domains. Section 6 taxonomizes existing real adversarial attacks based on the execution domains (Windows, PDF, Android, Hardware, Linux) and algorithms maneuvered to carry out attack. This section discusses real attacks carried out against malware detection approaches in detail and provides comparisons among related works. Section 8 highlights challenges of current adversarial generation approaches and sheds the light on open research areas and future directions for adversarial generation in malware analysis. Finally, Section 9 concludes our survey.
1.3 Literature Search Resources
To discover the relevant state-of-art works and publications in adversarial attacks on malware analysis, we relied on different digital libraries for computer science scholarly articles. Our major sources are IEEE Xplore131313https://www.ieee.org/, ACM digital library141414https://dl.acm.org/, DBLP151515https://dblp.uni-trier.de/, Semantic Scholar161616https://www.semanticscholar.org/ and arXiv171717https://arxiv.org/. Apart from these digital libraries, we also searched directly through Google181818https://www.google.com/ and Google Scholar191919https://scholar.google.com/ to get impactful papers in domain that were somehow missed in other libraries. Among numerous keywords used to fetch the papers from public libraries, ”Adversarial Malware” and ”Adversarial attacks in malware” gave us the most number of relevant papers. After listing all the published works in adversarial generation between year 2013 to 2021, we filtered out papers with good impact, relevance and prepared the final list to conduct our detailed survey.
2 Machine Learning Preliminaries
We are in the era of Big Data [102, 103, 104, 105, 106, 107], and an unprecedented amount of digital information is generated and flowing around us. With more than 2.5 Quintilian data bytes every day, around 200 million active web pages, 500 million tweets every day and a few million years of videos in YouTube, we can imagine the magnanimity of data around [108, 109, 110, 111]. Manual extraction of valuable information from raw data is a cumbersome, tedious, and infeasible task given the volume of data. Machine learning, due to its intrinsic capability to process this humongous amount of data which can learn from raw data, discover patterns and give decisions with least human interference. ML allows automatic detection of patterns in data and use the learned model to predict future data. Prediction on unseen data helps in probabilistic decision-making under uncertainty. Tom M. Mitchell, chair of Machine Learning at Carnegie Mellon University in his book Machine Learning (McGraw-Hill1997) [112] defines machine learning as ”A computer program is said to learn from experience E with respect to some class of tasks T and performance measure P, if its performance at tasks in T, as measured by P, improves with the experience E”. Simply stating, machine learning is a branch of artificial intelligence that enables learning from data used for training. Modern literature often confuses the term ’Artificial Intelligence’ with ’Machine Learning’ and they are used interchangeably. Machine learning are the subset of artificial intelligence as shown in Figure 5 that focuses on learning the patterns and improving the predictions as experience grows. Another term ’Deep Learning’ is the current hot-topic inside machine learning which we will discuss later in this section. A trained system should learn and improve with experience, being able to make predictions based on previous learning. The normal workflow of machine learning is shown in Figure 4, where training data is passed through learning algorithm and trained models are used to make predictions.

Interests in computational approaches to learning can be seen starting back in mid-1950s [113] and since then there has been continuous growth in the development of learning systems. It was only after the 1980s that ML was observed as real-world potential, and today it continues to foster its growth towards increased intelligence in the form of deep learning. The unprecedented power of making predictions, advancement of machine learning techniques and broadening of its application areas have increased exponentially. Originating from data analysis and statistics, it has already gained a pioneering position in fields of text recognition, Natural Language Processing (NLP), speech processing, computer vision application, computational biology, fraud detection, and many security-related critical applications. Classification[114, 115, 116], regression[117, 118, 119], clustering [120, 121, 122], dimensionality reduction [123, 124], and ranking [125, 126, 127] are some examples of the major machine learning tasks applied in different applications. Starting from search engines, online product recommendations to high-end self-driving cars and space missions, the growth of human civilization has already started to be driven by the progress of machine learning.
Classical machine learning is classified based on the way of interaction between the learner and the environment [128]. The most basic approaches include supervised [129, 130], unsupervised [131, 132], semi-supervised [133, 134] and reinforcement learning[135, 136]. Supervised learning deals with training from a set of labeled training data while unsupervised learning trains on unlabeled data to find any meaningful patterns. Having the capability of finding associations among data, machine learning was able to provide tailored product development based on customer demands. The normal workflow of traditional machine learning algorithms is shown in Figure 6. The raw data presented as image in the figure are first passed to feature extraction phase which outputs feature vectors in a form that is suitable to be fed to machine learning models. The feature vectors are then used for either training or testing machine learning algorithms. In this section, we will discuss the core machine learning terminologies that will be used frequently later in the survey. This section will not be covering traditional machine learning approaches as they are rarely used for generating adversarial these days in comparison to modern deep-learning based algorithms. The subsections of this section follows no particular hierarchical order, with each subsection being a stand-alone topic.

2.1 Deep Learning
Deep Learning (DL) is a sub-field of machine learning that uses supervised and unsupervised techniques to learn multiple level of representations and features in hierarchical architectures. The ability of conventional machine learning was very limited while processing a raw data. Deep learning has been able to make significant breakthroughs for challenges faced by ML practitioners by showcasing its ability to find patterns in very high dimensional data. Deep learning has enabled researchers to reach unparalleled success in fields of image recognition [137, 138, 139], speech recognition [140, 141, 142], neuro-science integration [143], malware detection [144, 145] and most of the ML powered research areas. Since the start, structuring conventional machine learning algorithm required careful feature engineering and high level domain expertise to extract meaningful features from raw data. The effectiveness of machine learning is largely dependent on the representation ability of feature vectors. Representation learning is an approach for ML which allows models to be fed with raw data and automatically learns the representation required to make decisions.


Deep-learning methods are representation learning approach with multiple level of representation, obtained by non-linear transformations from lower to higher abstraction level. By combining such simple, non-linear transformation, machine finally learns complex function. Taking representation to higher level in each step signifies amplifying aspects of input which are important for discrimination while suppressing irrelevant features. It can be observed in Figure 6 that all the feature extraction overhead of traditional learning is replaced by neural nets in deep learning. A standard neural network architecture are made up of connected neurons which are the processors and each neuron outputs a sequence of real-valued activation. Environmental input obtained by sensors activate the input neurons while deeper neurons get activated through weighted connections from previously active neurons. Deep learning operations are usually composed of weighted combination of a group of hidden units having a non-linear activation function, based on a model structure. The architecture of neural network resembles to the perception process of human brain, where a specific sets of unit get activated if it has a role in influencing the output of neural network model. Mathematically, the deep neural network architecture are usually differentiable, so that the optimal weights of the model are learned by minimizing a loss function using variants of stochastic gradient descent through back propagation. For the example mentioned in Figure 6, we can consider an image classification example where image input comes in the form of an array of pixel value [146]. During the first layer of representation, deep learning models learns the presence or absence of edges at particular orientation. Second layer tries to detect some arrangements in detected edges discarding the minute variations in the position of edges. These arrangement of edges are combined into larger combinations, corresponding to the sections of familiar objects and subsequent layer capable of giving the detection results.
2.2 Convolutional Neural Network
Convolutional Neural Network (CNN) is one of the most popular deep learning architecture inspired by natural visual perception of the living beings[147]. It takes its name from mathematical linear operation between the matrixes called convolution. One of the first multi layer artificial neural network (ANN), LeNet-5 [148, 149], as shown in Figure 7, is considered to have established the modern framework of CNN architecture. CNN has received ground breaking success in recent years in the field of image processing [150] which has been replicated to many other fields. One of the biggest aspects behind the success of CNN is its ability of reducing the parameters in ANN.
CNN is mainly composed of 3 layers as shown in Figure 7: convolutional layer, pooling layer and fully connected layer. Convolutional layer aims to learn feature representation from the input raw data. Feature maps are computed using convolutional kernels, with each neuron of a feature map connected to a region of neighbouring neurons in the previous layer. New feature map is received by convolving around the inputs with a learned kernel and applying element-wise nonlinear activation function on the convolved results. During feature map generation, kernels are shared by all the spatial locations of the input. The role of pooling layer is to reduce the number of connections among convolutional layers which in turn helps in reducing the complexity of computation. Pooling layer hovers over each activation map and scales the dimensionality using appropriate functions like max, average and so on. Stride and filter size of pooling defines the scaling. Fully connected layers in CNN have same role as that of standard ANN, producing class scores from the activation. Other common CNN architectures include AlexNet [150], VGG 16 [151], Inception ResNet [152], ResNeXt [153], DenseNet [154].
2.3 Reinforcement Learning
Reinforcement learning (RL) can be viewed as a learning problem and a sub-field of machine learning [155]. Basically, its about using past experience to enhance the future manipulation of a dynamic system and learning by maximizing some numerical value which helps to meet long term goals. A supervised learning model learns from data and its labels whereas a RL model completely relies on its experience. In RL, a model is trained to make sequence of decisions through the action of agent in a game-like environment. Diagrammatic representation of reinforcement learning is shown in Figure 8 where it is shown as the combination of four elements: an agent capable of learning, the current environment state, an action space from which an agent can choose an action and the reward value that an agent is provided in response to each action. Program is deployed to go through a trial and error process to reach the solution of a problem. Agent acting on an environment gets either a reward or penalties for an action it performs and the goal of learning is to maximize the total reward. The programmer sets up the action space, environment and reward policy required for learning and the model figures out the way of performing tasks and maximizing the reward. An agent learning starts with random trials and errors leading to highly sophisticated tactics and superhuman decision making. In a formal definition, a system governed by machine learning algorithm observes a state from its environment at time step . The agent performs action in state to make transition to a new state . The state is basically the information about environment which is sufficient for an agent to take best possible actions. The best sequence of actions are defined by the rewards provided by the environment while executing the actions. After completion of each action and transition of environment to new state, environment provides a scalar reward to the agent in form of feedback. Rewards could be positive to increase the strength and frequency of the action or negative to stop the occurrence of action. The goal of an agent is to learn a policy that maximizes the reward. Reinforcement learning faces the challenge of requiring extensive experience before reaching optimal policy.

Exploration and exploitation through all possible directions in high dimensional state spaces leads the learning process to an overwhelming number of states and negatively impact the performance. This had limited the previous success of reinforcement learning [156, 157, 158] to lower-dimensional problems. We have discussed the rise of deep learning in last decade by providing low dimensional representation in previous sections. In its way to solve the curse of dimensionality, deep learning also enabled reinforcement learning to scale to very high-dimensional states problem, which were previously considered impractical. Mnih et al. [136] work to play Atari game using deep reinforcement learning and beating human level experts, easily elevated the application of reinforcement learning in combination with deep learning. An actor-critic model with experience replay was used to reach such performance on the Atari game. In deep reinforcement learning framework, agent acting on end-to-end way, takes raw pixels as an input and outputs the associated rewards for each actions. The learned reward function is the basis for deep Q-learning which keeps refining over the experience. Deep reinforcement learning has already been very successful in fields such as robotics [159, 160, 161, 162] and game playing [163, 164, 165] where learning from experience is very effective, replacing hand-engineered low-dimensional states.
2.4 Recurrent Neural Network
Neural networks has already been established as a very powerful tool to perform in many supervised and unsupervised machine learning problems. Their ability to learn from underlying raw features which are not individually decipherable has been unparalleled. Despite their significant power to learn from hierarchical representations, they rely on assumption of independence among the training and test sets [166]. Despite of neural net’s ability to function perfectly with independent test cases, their assumption of independence fails while data points are correlated in time or space. Recurrent Neural Network (RNN) being a connectionist model, are able to pass information across the sequence steps and processes single sequential data at a time. We can relate this to understanding meaning of a word in text by understanding the previous contexts. RNN is a adaptation of the standard feed-forward neural network allowing it to model sequential data. The basic schema of RNN is shown in Figure 9 where hidden unit takes input of current unit as well as contextual units to provide output. Different from the feed-forward neural networks, the decision for current input depends on activation from previous time steps[167]. The activation values from previous state are stored inside the hidden layers of a network which provides all the temporal contextual information in place of fixed contextual Windows used for feed forward neural networks (FFNN). Hence, dynamically changing contextual window helps RNN better suited for sequence modeling tasks.

The gradients of the RNN are very easily computed using back-propagation through time [168], and gradient descent is a suitable option to train RNN. However, dynamics of RNN makes effectiveness of gradient highly unstable, resulting to exponential gradient decays or gradient blows up. To resolve this issue, enhanced RNN architecture, Long Short-Term Memory (LSTM) is designed [169]. The architecture of LSTM are made up of special units called memory blocks inside the hidden layer of RNN. Memory cells are made up of memory blocks storing the temporary state of network and gates controlling the information flow. A forget gate prevents LSTM models from processing continuous input streams by resetting the cell states. Today RNN are being extended towards deep RNNs, bidirectional RNNs and recursive neural nets. Among many application areas, language modeling [170, 171, 172], text generation [173, 174, 175], speech recognition [176, 177, 178], text summarization [179, 180, 181] are the major areas transformed by the use of RNN models.
2.5 Generative Adversarial Network

Generative Adversarial Network (GANs) are the generative modeling approach using deep learning methods. Goodfellow et al. [182] proposed GAN as a technique for unsupervised and semi-supervised learning. In a GAN model, two pairs of networks namely: Generator and Discriminator are trained in combination to reach the goal as presented in Figure 10. Creswell et al. [183] define the generator as an art forger and the discriminator as an art expert. The forger create forgeries, with the aim of making realistic images whereas discriminator tries to distinguish between forgeries and real image. The generator’s goal is to mimic a model distribution and the discriminator separates the model distribution from the target [184]. The concept here is to consecutively train the generator and the discriminator in turn, with goal of reducing difference between the model distribution and the target distribution. During the training of GANs, discriminator learns its parameters in such a way that its classification accuracy is maximized and generator learns its parameters is such a way that it maximally forges the discriminator. The generator and the discriminator must be differentiable, while not necessarily being invertible.
GAN’s ability to train a flexible generator functions, without absolutely computing likelihood has made GAN successful in image generation [185, 186] and image super resolution [187, 188]. The flexibility of the GAN models has allowed them to be extended to structured prediction [189, 190], training energy based models [191, 192], generating adversarial examples for malware [193, 194], and robust malware detection [45, 195]. GAN models suffers from issues of oscillation during training process [196], depriving them from converging to a fixed point. Approaches that has been taken to stabilize the learning process still rely on heuristics which are very sensitive to modifications [197]. Recent research work [198, 199] is being carried out to address the stability issues of GANs.

3 File Structure
Executable files are structured differently based on the target/host OS. In this survey, we briefly cover the adversarial attacks across Windows portable executable (PE) file, PDF file and Android files. Although detailed discussions on file structure is out-of-scope for survey, a good understanding of file structure is essential for successful generation of adversarial examples. Different sections of a file are classified into two groups, mutable and immutable. Mutable sections are those which can be modified for adversarial generation without altering the functionality of file whereas immutable sections either breaks the file or alters the functionality on modification. This section will provide brief overview of three kinds of file’s structure that are discussed in later parts of survey.
3.1 Windows PE File Structure
Windows PE file format is an executable file format based on the Common Object File Format (COFF) specification. The PE file is composed of linear streams of data. The structure of Windows PE file as shown in Figure 11 is derived and confirmed from [200, 201, 202]. The header section consists of MS-DOS MZ header, MS-DOS stub program, PE file signature, the COFF file header and an optional header. File headers are followed by body sections, before closing the file with debug information. First 64 bytes of PE file are occupied by MS-DOS header. This header is required to maintain the compatibility with files created on Windows version 3.1 or earlier. In absence of MZ header, the operating system will fail to load the incompatible file [201]. The Magic number used in the header determines if the file is of compatible type. Stub-program is run by MS-DOS after loading the executable and is responsible for giving output messages which include errors and warnings.
PE file header is searched by indexing the e_lfanew field to get the offset of file which is the actual memory-mapped address. This section of the PE file is one of the target areas to perform modification by using these locations as macros in order to create adversarial examples. The macro returns the offset of file signature location without any dependency on the type of executable file. At offset 0x3c, 4-byte signature is placed which helps to identify the file as a PE image. The next 224 bytes is taken by optional header. Even though it may be absent in few types of file, it is not an optional segment for PE files. It contains information like initial stack size, program entry point location, preferred base address, operating system version, section alignment information and few other [201]. Section headers are of 40 bytes without any padding in between. The number of entries in the section portion is given by the NumberofSections field in the file header [203]. Section header contains fields like Name, PhysicalAddress or VirtualSize, VirtualAddress, SizeOfRawData, PointerToRawData and few more pointers with characteristics.
Data is located in data directories inside data section. Information from both the section header as well as optional header are required to retrieve data directories. The .text section contains all the executable code sections along with the entry point. An uninitialized data for the applications are stored in the .bss section which includes all declared static variables and .rdata section represents all the read only data like constants, strings and debug directory information. The .rsrc section contains resorce information for the module and export data for an application are present in .edata section. Section data are the major area where perturbation takes place to make a file adversarial. Debug information is placed on .debug section but the actual debug directories resides in the .rdata section.
3.2 Android File Structure

Android APK file has been recently victimized as a tool for adversarial attacks [204, 205, 206, 207]. APK file is basically a ZIP files containing different entries as shown in Figure 12. Different sections of APK files are described below:
-
•
Androidmanifest.xml: AndroidManifest.xml contains the information to describe the application. It contains the information like application’s package name, components of application, permissions required and compatibility features [208]. Due to presence of large amount of information, AndroidManifest.xml is one of the majorly exploited section in APK file for adversarial attack.
-
•
classes.dex: As Android applications are written in Java, source code will be with extension .java. These source code are optimized and packed into this classes.dex file.
-
•
resources.arsc: This file is an archive of compiled resources. Resources include the design part of apps like layout, strings and images. This file form the optimized package of these resources.
-
•
res: Resources of app which is not compiled to store in resources.arsc stays in res folder. The XML files present inside this folder are compiled to binary XML to boost performance [209]. Each sub-folder inside res store different types of resources.
-
•
Meta-INF: This section is only present in signed APKs and has all the files in APK along with their signatures. Signature verification is done by comparing the signature with the uncompressed file in archive [210].
3.3 PDF File Structure

In this section we will look into the internal structure of PDF file format. PDF is a portable document with wide range of features, capable of representing documents which includes text, images, multimedia and many others. The basic structure of a PDF file is shown in Figure 13 and are discussed below:
-
•
PDF header: PDF header is the first line of PDF which specifies the version of a PDF file format.
-
•
PDF Body: The body of a PDF file consists of objects present in the document. The objects include image, data, fonts, annotations, text streams, etc. [211]. Interactive features like animation and graphics can also be embedded in the document. This section provides the possibility of injecting contents and files within it, which makes it the most favourable avenue for adversarial attackers.
-
•
Cross-reference table: The cross-reference table stores the links of all the objects or elements in a file. Table helps on navigating to other pages and contents of a document. Cross-reference table automatically gets updated on updating the PDF file.
-
•
The Trailer: The trailer denoted end of PDF file and contain a links to cross-reference table. The last line of trailer contains the end-of-file marker, %%EOF.
4 Malware Detection
In globally networked world, malware has posed a serious threat to data, devices and users on internet. From data theft to disrupting the computer operation, with increasing reliability over internet, malware is a growing menace. Malware is being used as a weapon on digital world carrying malicious intentions throughout the internet. Malware attacker tries to take advantage from legitimate users and accomplishing financial or other goals. Malware can be in any forms like viruses, trojan, ransomware, rootkits, spyware and so on. Global cybercrime cost is projected to be around $10.5 trillion in 2025 [212] which shows the required urgency to mitigate or limit the damage from these malicious software. Security researchers all around the world are working to combat with these malware files via antivirus software, firewalls and numerous other approaches. However, with big incentives driving malware production, millions of new malware202020https://www.av-test.org/en/statistics/malware/ are introduced to cyber world every year. These exponentially growing malware number comes with highly equipped tools and techniques, thus requiring continuous work on effective and efficient malware detection technologies.

Current malware detection techniques are broadly classified into signature based and behavioral based approaches as shown in Figure 14. Traditionally, signature based approaches were used to detect malware. However, due to inability of this approach to detect zero-day attacks, the much focused has been moved into behavioral based approaches (dynamic and online). In modern day anti-virus, hybrid approaches are considered by combining signature based approaches with behavioral based techniques. We will now discuss different types of malware detection approaches.
4.1 Signature Based Malware Detection
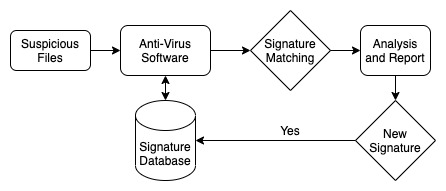
Signature is a short sequence of bytes unique to each malware and helps in identifying malware from rest of the files. Since this approach works by maintaining malware signature database, there are very low false positives rate. Signature based detection has been very effective and fast for malware detection but it is not able to capture the ‘unseen’ malware. Figure 15 shows the malware detection process using signature. As shown in figure, signature database is predefined list of all the possible malware signatures and is solely responsible for entire malware detection process. The anti-malware engine if detects the malicious objects, malware signature is updated in signature database for future detection. A good malware detector’s signature database has a huge number of signature that can detect malware [213]. Signature based malware detection are good at speed of detection, efficiency to run and broad accessibility [214]. However, the inability to detect zero-day malware whose signature is not available in database of anti-malware engine led to question the reliability of signature based approaches. Digital signature patterns can be extracted easily by attacker and implemented to confuse the signature of malware. Current malware comes with polymorphic and metamorphic properties [215, 216] which can easily change their behavior enough to change the signature of file. With complete dependence over known malware, signature based detection can neither detect zero day attacks nor the variations of existing attacks. In addition to it, signature database grows exponentially with malware family growing at a rapid pace [217].
4.2 Zero-day Malware Detection
To overcome the limitations posed by signature based approach, zero-day malware detection techniques are focused to capture the unseen malware. In modern zero-day detection approaches, suspicious objects are identified based on behavior or potential behavior of the file [22, 21]. An object’s potential behavior is first analyzed for suspicious activities before deploying in a real-time production environment. Those behavior which are anomalous to benign file actions, indicates the presence of malware. Most of the zero-day detection approaches are built around machine learning systems, with state-of-art works using modern deep learning architectures. The captured behavior of the file under inspection is generalized using machine learning models, which is later used to detect unseen malware family. Here, we discuss three different types of zero-day malware detection in this section below:

-
•
Static Approach: Static malware detection is the closest approach to signature based system as detection is carried out without running the file. Execution of unknown file may not be always possible in system due to security risks and this is where static detection comes into play. Anti-malware system captures static attributes like hashes, header information, file type, file size, presence of API calls, n-grams etc. from binary code of executable using reverse engineering tools. Once the features are extracted, they are pre-processed to keep only non-redundant and important features. Among numerous available features, n-Grams [218, 219] for byte sequence analysis and Opcode [220] used to analyze the frequency of ’Operation Code’ appearance are the most widely used ones. As shown in Figure 16, the extracted features are fed to different machine learning algorithms ranging from classical to deep learning architectures to train the detection model. The trained model is then used to carry out detection of malware from static features. However, static detection alone is not sufficient to detect more sophisticated attacks [221, 222, 223] as the static features can not reflect the exact behavior of malware on run time, which limits its applications [224] in real world.
-
•
Dynamic and Online Approach: Dynamic approaches [225, 226, 227] are constructed by executing a suspicious file inside the isolated virtual environments like a sandbox [228] and detecting malware based on a run-time behavior of a program. The use of closed environment is to prevent malware from escaping and attacking the system where analysis is being conducted. Malware on execution can change the registry key maliciously and obtain the privileged mode of operating system [229]. During the execution of malware, properties of operating system changes which is logged by agent in controlled environments. Dynamic analysis enables system to capture dynamic indicators like application programming interface (API) calls, registry keys, domain names, file locations and other system metrices. These features are pre-processed and fed to machine learning model to train malware detector in the flow as shown in Figure 17. Dynamic analysis are considered more powerful than static due to ability to capture more number of system features. Code obfuscation approaches and polymorphic malware are considered ineffective against dynamic malware detection [230] reflecting its resilience from such sophisticated malware.
Dynamic approach, though overcoming some limitations of the static detection, have its own challenges. Every suspicious file needs to be executed in an isolated environment for specific time frame which results in expense of significant time and resources [231]. The malware file does not guarantee to exhibit a same behavior both in a sandbox and live environment [232]. Modern smart malware comes with the ability of detecting the presence of sandbox and stay dormant till they reach live systems. In most of the current applications, both static and dynamic analysis are combined to detect the presence of malware in the file [233, 234, 235]. To combat the issue of polymorphic and metamorphic malware which are evasive to control malicious functionality only during some particular events, online malware detection approaches are performed [236, 237, 238, 20, 19]. Online malware analysis continuously monitors the system for the presence of maliciousness in any file [239]. Continuous monitoring helps to capture the malware at any time in live environment. However, online detection also demands for continuous monitoring overhead to the system. As most of the adversarial attacks performed so far in the literature are on static malware detection approaches, this survey will primarily focus on evasion attacks carried out against static malware detection.

5 Adversarial Threat Model
Security threats are defined in terms of their goals and capabilities. In this section, we defined the adversarial threat model, tailored to evasion attacks in malware, into four parts: adversarial knowledge, attack surface, adversarial capabilities and adversarial goals. This section aims to provide the readers with explanations to the major components of adversarial attacks.
5.1 Adversarial Knowledge
The adversary’s knowledge is the amount of information about a model under attack that the attacker has, or is assumed to have, to carry out adversarial attacks against the model. An adversarial attack can be classified into two groups based on the attacker’s knowledge:
-
•
White box attack: In a white box approach, an attacker has full knowledge about the underlying model. Such knowledge might include, but not limited to, the name of the algorithm, training data, tuned hyper-parameter, gradient information, among others. It is relatively easy to carry out attacks in white box model due to large amount of available knowledge. Current state-of-art works on white box environment have achieved near perfect adversarial attacks [100].
-
•
Black box attack: In a black box approach, an attacker only have access to inputs and outputs of the model. There is no information provided about the internal structure of the model. Generally in black box attack, surrogate model is created by making guess on internal structure of target model using input and output [240, 81]. In addition, in a gray box attack [241], a type of black box attacks, the attacker knows the output performance of the model in the form of accuracy, confusion matrix or some other performance metrics.
There is large variation on the amount of adversarial knowledge starting from complete access to actual source codes to receiving only output of models. In general, it is assumed that black box adversarial attacks are difficult to orchestrate compared to white box, primarily due to the information available regarding the underlying target model. However, black box attacks reflect more real world use-cases where, in practical sense, an attacker will not likely have any knowledge of models or other parameters.
5.2 Attack Surface
Attack surface includes different vulnerable points by which an attacker attacks the target model. Machine learning algorithms pass through a pipeline of different stages before deployment. The flow of data through this data pipeline introduces vulnerabilities in each stage [242]. Starting from collection of data, transformation and processing to output generation, an attackers have different attack entry points. Attack surface comprise all those points in machine learning models (malware defender models in our case), where adversaries can carry out their attacks. Based on different approaches to carry out attacks, attack surface has been classified into following broad categories [243]:
-
•
Poisoning Attack: This attack is carried out by contaminating training data during the training process of models [244, 245, 246]. Training data is poisoned with faulty data, making machine learning models learn on wrong dataset. As a result of poisoned training data, the entire training process is compromised.
- •
- •
5.3 Adversarial Capabilities
Adversarial capabilities denote the abilities of adversaries and are dependent on their knowledge of the target model. Some adversaries have access to training data, some have access to gradient information of the model, while others do not have any access to the model at all. The capabilities of attacker vary depending on the information and phase (i.e. training or testing phase) of the model they are attacking. The most straightforward attack approach is attacker having access to full or partial training data. For adversarial attacks carried out on malware files, adversarial capabilities can be classified into following categories:
-
•
Data Injection: Data injection is the ability of attackers to inject a new data. There are multiple types of data injection that might take place. One type of injection can be done on training data before training process. Another type of data injection is carried out by inserting a perturbations which forms a new section or replaces original section within an existing file. Injected data can corrupt the original model or cause the data injected file to evade detection.
-
•
Data Modification: Data modification can also be performed both for training data and evading file. If attacker has access to training data, data can be modified to cause model learn on modified data. Attacker can also modify input data to cause perturbation and leading to evasion.
-
•
Logic Corruption: Logic corruption is the most dangerous ability to be possessed by attacker and also the most improbable. Whenever an attacker has complete access over a model, they can modify the learning parameters and other hyper-parameters related to model. Logic corruption can go undetected which makes it hard to design any remedies.

5.4 Adversarial Goals
An attacker tries to fool the target model, causing it to produce misclassifications. Details of algorithms used to successfully attack and achieve the adversaries goals are discussed in section 6. Typically, the adversarial goals of attacker’s are categorized as follows:
-
•
Untargeted Misclassification: An attacker tries to change the output of model to a value different than original prediction. For a malware classification problem, if a ML model is predicting a malware file as family A, the goal is to force the model to misclassify it as a family other than A.
-
•
Targeted Misclassification: An attacker tries to change the output of the model to a target value. For example, if a ML model is predicting a malware file as family A, the goal is to force the model to misclassify it as a family B.
-
•
Confidence Reduction: An attacker’s goal is to reduce the confidence of a ML model’s prediction. It is not necessary to change the prediction value but a reduction of confidence is enough to meet the goal.
To summarize, Figure 18 gives an overview of the adversarial attack difficulty with respect to the attacker’s knowledge, capabilities and goals. While moving in the direction of increasing attack complexity from confidence reduction to targeted misclassification, attack difficulty also increases for the attacker. However, whitebox attacks with higher attacker’s capability has least attack difficulty.
6 Adversarial Algorithms
In this section, we will explore the most distinguished adversarial attack algorithms that have been discovered in different domains and are applied to generate adversarial malware samples. Different algorithms are developed in numerous time frames battling the trade off in terms of application domain, performance, computational efficiency and complexity [249]. We will discuss the architecture, implementation and challenges of each algorithm. Most of the attack algorithms are gradient based approaches where perturbations are obtained by optimizing some distance metrics between original and perturbed samples.
6.1 Limited-memory Broyden - Fletcher - Goldfarb - Shanno (L-BFGS)
Szegedy et al. [71] proposed one of the first gradient based approaches for adversarial example generation in the imaging domain using the box constrained Limited-Memory Broyden-Fletcher-Goldfarb-Shanno optimization technique. The authors studied counter-intuitive properties of deep neural networks which allow small perturbations in the images to fool deep learning models for misclassification. Adversarial examples trained for particular neural network are also able to evade other neural networks trained on completely different hyper-parameters. These results are attributed to non-intuitive characteristics and intrinsic blind spots of deep learning models learned by back propagation, with structure connected to data distribution in a non-obvious way. Traditionally, for small enough radius 0 around the given training sample , satisfying will be classified correctly by a model with very high probability. However, many underlying kernels are found not holding to this kind of smoothness. Simple optimization procedure is able to find adversarial sample using imperceptibly small perturbations, leading to incorrect classifications by classifier. While adding noise to an original image, the goal is to minimize perturbation added to the original image under distance. A classifier mapping pixel value vectors to a discrete label set is denoted as and the loss function associated is given by . For a given image with a target label , box-constrained optimization problem is defined as :
| (1) |
where x is the original image, r is the added perturbation, f is the loss function of the classifier and l is the label of incorrect prediction by the classifier. Perturbed is arbitrarily chosen using distance minimizer. The computation of distance is done by approximation using box-constrained L-BFGS. After this early proposal of L-BFGS for adversarial examples generation, plenty of research were triggered to dive into flaws of deep learning.
6.2 Fast Gradient Sign Method (FGSM)
Considering gradient-based optimization technique as a workhorse of modern AI, Goodfellow et al. [74] proposed an efficient approach for generation of adversarial perturbation in image domain. In contrast to earlier works which explained adversarial phenomena to non-linearity and overfitting, the authors argued the linear nature of neural networks leading to their vulnerability. Linear behaviour in high dimensional space are found sufficient to cause adversarial samples. Linearity is the result of trade off while designing models that are easy to train. LSTMs [169], ReLUs and maxout networks [250] are all found to be intentionally designed to behave linearly for ease of optimization. To define the approach formally, let’s consider as a parameter of model, as input to the model, as target associated with and be the cost function for training neural network. On linearizing the cost function around the current parameter values , perturbation can be obtained by
| (2) |
where required gradient can be computed using backpropagation and the approach is called as Fast Gradient Sign Method.
Conversion of features from problem space to feature space affects the precision. Commonly images are represented by 8 bits per pixel and all other information below 1/255 of continuous range are discarded. With limited precision, classifier may not be able to respond to all perturbations whose size is smaller precision of feature. Classifier having well-separated decision boundary for for classes are expected to assign same class for original sample and perturbed sample until where is small enough to be discarded. Taking the dot product and weight vector w and an adversarial example :
| (3) |
The adversarial perturbation increases the activation by . The amount of perturbation can be controlled by keeping max norm constraint on and assigning . Taking with dimensions and having average magnitude weight vector , the activation grows by . Even though does not grow with increasing dimensionality of the problem but for high-dimensional problems, the activation change caused by the adversarial perturbation can grow linearly. In presence of sufficient dimensions, even simple linear models are seen to have adversarial examples. Adversarial examples are found to occur in contiguous regions of 1-D subspace defined by the fast gradient sign method, where traditional belief was in fine pockets. This allows adversarial examples to be abundant and generalizable across different machine learning models. FGSM being one of the most efficient techniques for adversarial with fast generation of samples, is among the most used technique in this field.
6.3 Iterative Gradient Sign Method (IGSM)
Different from the one step perturbation approach where single large step in direction of increasing loss of classifier, Iterative Gradient Sign Method takes iterative small steps while adjusting the direction after each step [72]. Basic iterative method extends FGSM approach by applying it multiple times with small step size and clipping the pixel values after each iteration to ensure the perturbation within neighbourhood of original image.
| (4) |
where is the perturbed image at iteration and function performs pixel wise clipping on image in order to keep perturbation inside -neighbourhood of source image X. Kurakin et al. [72] extended basic iterative method to iteratively least likely class method to produce adversarial for targeted misclassification. Desired class for this version of iterative approach is chosen based on the prediction of the trained network, given as:
| (5) |
To make adversarial classified as is maximized taking iterative steps in direction given by . Now the adversarial generation cost function can be viewed as:
| (6) |
This iterative algorithm helps to add finer perturbations without damaging the original sample even with higher .
6.4 Jacobian Saliency Map Attack (JSMA)
Most of the adversarial generation techniques are based on observing output variations to generate input perturbations, while Papernot et al. [251] crafted adversarial samples by constructing a mapping of input perturbations with output variations. The approach is based on limiting the -norm of the perturbation which deals with minimal number of pixel modification. The proposed adversarial generation algorithm against feed forward DNN modifies small portion of input features by applying heuristic search approaches. Adversarial sample is constructed by adding perturbation to benign sample through following optimization problem:
| (7) |
where is the adversarial sample and is the desired adversarial output. Forward derivative is used to evaluate the changes on output due to corresponding modifications in input and these changes are presented on matrix form called as Jacobian of the function. Replacing gradient descent techniques with forward derivative allows attacker to generalize attack for both supervised and unsupervised architecture for broad families of adversaries. Forward derivative of Jacobian matrix of function F is learnt by neural network during training process. For a function with single dimensional output, Jacobian matrix is given as:
| (8) |
Forward derivative helps to distinguish the region which are unlikely to generate adversarial sample and focus on features with high forward derivative for efficient search and smaller distortions. JSMA is a black-box attack with only assumption of DNN architecture using differentiable activation function. Algorithms take a benign sample , a target output , a feedforward DNN F, a maximum distortion parameter , feature variation parameter and undergoes following steps to give adversarial sample such that .
-
•
Compute forward derivative
-
•
Construct a Saliency map S based on the derivative
-
•
Modify an input feature by
The forward derivative calculate gradients similar to those computed for back-propagation, taking derivative of network directly in place of its cost function and differentiating with respect to input features in place of the network parameters. Consequently, gradients are propagated forward which helps in determining input components leading to significant changes in network outputs. Authors extended application of saliency maps [252] to construct adversarial saliency maps which gives features having significant impact on output and thus is a very versatile tools to generate wide range of adversarial examples. Once saliency map gives the input feature that needs to be perturbed, benign samples are perturbed using distortions limited by parameter . The limiting parameter depends on human perception of adversarial sample. The experiment is carried out on LeNet architecture using MNIST dataset. Adversarial crafting is done by increasing or decreasing the pixel intensities of images. Before wrapping up JSMA, we discuss briefly about Saliency Vector. Saliency Vector contains the features in input blocks of data and their significance for machine learning model. Importance of input feature given by saliency vector can be thought of as a function of network’s sensitivity to changes in the input feature [253]. The regions of element in original files corresponds to the position of elements in the vector and value of that element gives the measure of importance of that feature region. Zhou et al. [254] proposed Class Activation Mapping to produce visual interpretation for CNN-based model. Authors used global average pooling to indicate discriminative image regions used by CNN to make the decision. Due to difficulty of modifying and retraining the original model to obtain CAM, Selvaraju et al. [255] proposed Grad-CAM method. Gradient-weighted CAM uses the gradient information flowing into the final convolutional layer to produce a localization map highlighting the important regions of image. Saliency vector allows to observe database bias and improve the models based on training data.
6.5 Carlini & Wagner attack (C&W)
Carlini & Wagner [256] proposed an adversarial generation approach to overcome the defensive distillation. Defensive distillation has been recent discovery to harden any feed-forward neural network against adversarial examples by performing only a single retraining. Proposed approach is able to perform three types of attacks: attack, attack and attack to evade defensively distilled and undistilled networks. These attacks are based on different distance metrics which are:
-
•
distance, measuring the number of pixels modified in an image
-
•
distance, measuring the standard Euclidean distance between original sample and perturbed sample
-
•
distance, measuring the highest change among any of the perturbed coordinates
The optimization problem for adversarial generation of input image is given as:
| (9) |
where input is fixed and goal is to reach that minimizes . could be any of distance metric among . Different approaches are taken to limit the modification and generate valid perturbations:
-
•
Projected gradient descent is allowed to perform only one standard gradient descent, clipping all other coordinates
-
•
Clipping gradient descent does not clips input perturbation on each iteration, but clips into objective function to be minimized
From their experiments [256], it is observed that attack has low distortion while and is not fully differentiable as well as bad suited for gradient descent.
6.6 DeepFool

Dezfooli et al. [257] proposed an untargeted white-box adversarial generation technique called as DeepFool. DeepFool works by minimizing the euclidean distance between perturbed sample and original samples. Attack begins by generating linear decision boundary to separate the given classes and accompanied by addition of perturbation perpendicular to the decision boundary that separates classes as demonstrated in Figure 19. Attacker projects the perturbation into a separating line called hyper-plane and tries to push it beyond for mis-classification. In high dimensional space, decision boundaries are usually non-linear, so the perturbation are added iteratively by performing multiple attacks till evasion. Attack for such multiclass finds the closest hyperplane and projects input towards that hyperplane and then proceeds to other. The minimal perturbation required to misclassifiy classifier is the orthogonal projection of onto and is given by closed loop formula in Equation 10.
| (10) |
where is perturbation, is classifier function. is gradient and the original sample.
6.7 Zeroth Order Optimization (ZOO)
All of the previously discussed adversarial generation algorithms are dependent on gradient of detector module which limits the adversarial attack space within white-box attack. Chen et al. [258] proposed a black-box adversarial generation approach by estimating the gradients of targeted DNN with only access to input and output of a target. Zeroth order methods are gradient-free optimization approach requiring only the zeroth order oracle for optimization process. The objective function is analyzed at every two close points and with a very small h, so that a gradient along the direction of vector can be estimated. Gradient estimation is followed by an optimization algorithms like gradient descent. While attacking black-box DNN with large input size, use of a single minute step of gradient descent can be very inefficient as large number of gradient needs to be estimated. To resolve this optimization issue, coordinate descent method is used by optimizing each coordinate iteratively.
Zeroth Order Optimization attack is inspired by formulation of the C&W attack. The loss function of C&W attack is modified in such a way that it is only dependent to output of DNN and desired class label. A new hinge like loss function based on the output of DNN is defined in Equation 11.
| (11) |
The proposed adversarial generation technique does not require gradient to be estimated accurately. To accelerate the zeroth order methods, attack-space dimension reduction approach is carried out which reduces the number of gradient to be estimated. Attack-space dimension reduction might lead to insufficient search space to find adversarial. So, hierarchical attack scheme is used where dimension is gradually increased during process of optimization. Using coordinate descent and importance sampling, attacker can also update pixels on a selective basis.
6.8 One Pixel Attack (OPA)
Another gradient free adversarial generation approach is proposed by Su et al. [259] by generating one pixel adversarial perturbations based on differential evolution (DE). Differential evolution is a population based optimization algorithm which has ability to find higher quality solutions than gradient based approaches [260]. Since gradient information is not required for DE, the need of differentiable objective functions is also omitted. One pixel attack perturbs single pixel using only probability labels. Single pixel modification allows attackers to hide the adversarial modifications making it imperceptible. To carry out the attack, each image is represented as a vector where each scalar element represents one pixel. With as the target function, representing n-dimensional inputs, being the original class, denoting the perturbation to be added to the input with maximum modification limited to , the optimized solution is given by Equation 12.
| (12) |
where d is a small number. This approach deals with determining two values: dimension to be perturbed and the required corresponding magnitude of modification for each dimension. Unlike other attack strategies, OPA focus modifications on only one pixel without limiting the strength of modification.
7 Adversarial Malware Evasion Attacks
Adversarial generation methods that originated in the image domain did not take long to migrate into the malware field. Among different adversarial threats, evasion attack has been the most worrisome approach that has already been exploited in different ways. Adversarial malware started with PDF and Windows files due to their abundance and then proliferated into other file formats. There have been significant work on adversarial generation for Android, PDF, Windows and Linux files. This section deals with adversarial examples generated to evade malware detection systems by making minor perturbations on input malware files. These subtle modifications on malware files during test time are able to sneak through blind-spots of machine learning models without breaking the functionality of malware. The following sections will briefly explain different adversarial generation works carried out by researcher on the malware domain. Adversarial work has been divided based on the attack domain which includes Windows, Android, PDF Hardware Based and Linux malware files. The following subsection discusses adversarial attacks in Windows files.
7.1 Windows Malware Adversarial
Microsoft Windows is a dominant operating system on PCs with more than 70% market share and 1.5 billion users worldwide [261]. Gartner research [262] predicts 30% of cyberattacks by 2022 will be carried out in form of adversarial. Abundant availability has placed Windows malware at the core of adversarial threats. Even the continuously evolving machine learning based malware detectors are not able to withstand adversarial attacks. In this section, we will cover different adversarial attacks carried out on Windows malware detectors.
Machine learning based models being data hungry, feature engineering is a critical task to feed important features as input. However, the advent of deep neural network has allowed models to learn features themselves from complex raw data. Deep neural networks have shown impressive performance in malware detection by providing whole binary file as a input without any hand crafted feature engineering effort. Different malware detectors have been previously discussed but we want to include Raff et al. work [263] in this section (referred as MalConv) which has been a industry standard in the field by making detection considering whole executable. Most of the attacks discussed in the survey are carried out against MalConv.

Detection using raw bytes comes with the sequence problem with millions of time steps and batch normalization hindering the learning process. Raff et al. tried to replicate the neural net’s success in learning features from raw inputs, successfully performed in image [75], speech [177] and text [264] domain. With bytes in malware having multiple modalities of information and contents exhibiting multiple spatial correlation, MalConv becomes the first ever architecture with ability to process a raw byte sequences of more than two million steps. MalConv addresses high amount of positional variation present in executable files. It’s architecture as shown in Figure 20, combines the convolutional activation with a global max-pooling before going to fully connected layers allowing the model to produce its activation regardless of the locations of the detected features. MalConv as one of the only robust static detector, has been considered a baseline for most of the static adversarial attacks.
| Paper/Year | Key Motivation | Target Model | Approach | Modification | Preserving Functionality |
| Kolosnjaji et al. 2018 [98] | Adversarial attack on malware detection using raw bytes | MalConv [263] | • Optimizing one byte at a time using gradient descent • Embedded layer to tackle non-differentiable MalConv architecture • Gradient calculation of objective function with respect to embedded representation | Bytes are padded only at the end of file | • Byte padding only at the end • Padding byte closest to embedded byte is chosen |
| Kreuk et al. 2018 [265] | Gradient based attack with better reconstruction | MalConv [263] | • Perturbation generation in embedded space • Calculation of weighted distance between generated adversarial embedding from actual embedding • Weighted gradient similar to iterative FGSM | Padding bytes at the end of file | • Loss function enforcing perturbation close to embedding matrix row • Payload bytes are inserted into marked and flagged region |
| Demetrio et al. 2019 [99] | Explainable technique for efficient adversarial generation | MalConv [263] | • Feature attribution to determine most influential feature • Perturbation generation using gradient of classification function with respect to embedding layer • Bytes modification in file header | Changing bytes of file header | • MZ magic number and offset at 0x3C are not modified |
| Suciu et al. 2018 [100] | Test existing methods on production-scale dataset and compare effectiveness of different strategies | MalConv [263] | • Random, gradient based and fast gradient perturbation • End of file append and slack region insertion • Transferability test across full, EMBER [266] and mini dataset | Padding bytes at the end and in the slack regions | • Slackindexes calculated before adversarial payload insertion • Updates only at the end or in slack regions |
| Chen et al. 2019 [267] | Enhancing effectiveness of gradient based approach through benign perturbation initialization | MalConv [263] | • Saliency vector generation using Grad-CAM method • Random benign block initialization and enhanced benign file append, followed by FGSM for white box attack • Experience based attack by summarizing the successful trajectories of random benign attacks for black box attack | Bytes are appended only at the end of file | • No alteration of existing section • Appending only at the end |
Key Motivation: The major motive behind the published work, Target Model: Target defense for adversarial attack, Approach: Key procedures to carry out adversarial attack, Modification: Changes on file to craft the adversarial perturbation, Preserving Functionality: Works towards safeguarding the functionality of a malware
7.1.1 Gradient Based Attack

Table III presents comparative study of adversarial attacks using gradient of cost function against Windows malware. Since Anderson et al.[97] proposed possibility of manipulating different sections of Windows PE malware to form adversarial, various researches have been conducted to bypass malware detector using malware PE files. Authors [97] used random actions from action space to modify PE files resulting in very low accuracy. To reduce the randomness of payloads, Kolosnjaji et al. [98] proposed appending optimized padding bytes using gradient descent, originally proposed by Biggio et al. [268]. Gradient based approaches are carried out using either append or insertion method for perturbation generated using gradient of cost function as shown in Figure 21. One-hot represented vector of malware is combined with gradient generated perturbation to bypass the malware detector. Making complex changes in architecture of file requires precise knowledge and could destroy file integrity as well. Kolosnjaji et al. [98] choose to append bytes only at the end of file by optimizing one padding byte at a time. In this case, attacker’s goal is to minimize the confidence of malicious class, limiting the maximum perturbation to . Appending bytes to input size should satisfy , where k is the number of informative bytes and d is fixed input size to detector. Due to non-differentiability issue of embedded layer in MalConv, negative gradient of loss function is calculated with respect to embedded representation. Embedding layer is a lookup table that contains mapping for each input to a 8-dimensional vector while optimizing one padding bytes at a time. Byte is replaced by optimal padding byte corresponding to embedded byte closest to line , defined parallel to negative gradient descent passing through embedded representation as shown in Figure 22. Authors were able to achieve evasion rate up to 60% by only modifying 1% of bytes in PE file.
Kreuk et al. [265, 269] proposed the enhanced attack method against MalConv [263] using iterative FGSM [74]. Authors focused this approach on enhancing reconstruction by introducing new surrogate loss function. Representation of binary files as a sequence of bytes are arbitrary and neural network is unable to work in this space. Generating adversarial examples deals with adding perturbations to original sample as given by increasing or decreasing gradient. However, this process is not that simple as perturbation in one-hot vector results to a vector that is no longer in one-hot vector space. This approach proceeds by generating perturbation in embedded space. In many cases, the perturbed embedding loses resemblance to embeddings in lookup table which contains mapping between bytes to embeddings. In absence of resemblance, reconstruction is not possible. Kreuk et al. introduced new term to loss function which causes perturbations to be close to embedding matrix. Introduced term is the weighted distance of generated adversarial embeddings from actual embeddings, with a goal of minimizing the distance. In order to preserve the functionality, payload bytes and flag is appended and only the flagged appended bytes is perturbed. The proposed white-box attack could obtain very high evasion rate of around 95%. The new loss function proposed by authors is given as:
| (13) |
where first part is the categorical loss called as the negative log-likelihood loss and second term gives the distance of generated adversarial embedding with the actual embedding in M. Second term is responsible to steer the direction towards reconstructible adversarial embeddings.
To interpret the blackbox decisions of malware detection model, Demetrio et al. [99] proposed a technique called integrated gradients initially proposed by Sundararajan et al. [270]. With input model , a point and baseline , the attribution of feature is computed as:
| (14) |
Equation (14) is the integral of the gradient computed on all points on line passing through and . Feature attribution is used to determine the most influential feature leading to meaningful explanations behind classifications of malware binaries. Feature attribution is extended in a way that information about relevant features are obtained from higher semantic level. Referencing the findings of research, authors are also able to generate adversarial malware samples by efficiently modifying few bytes in file header. Integrated gradient method satisfies both sensitivity and implementation invariance based on the concept of baseline. Findings of research showed that MalConv [263] learns to differentiate between malware and benign based on header bytes, ignoring the bytes present in other sections of file. Data sections and text sections being the major malicious section in file, considering only few header bytes for detection exposes serious concern in MalConv model. This approach is more efficient as it requires very few manipulations to bypass the detector. Authors were able to evade almost all malware by generating small perturbations on file header sections other than MZ magic number and value at offset 0x3C. Perturbation generation using gradient of classification function with respect to embedding layer is same as implemented by Kolosnjaji et al. [98]. Along with success in efficient adversarial attack from perturbations in file header, research also introduces to new challenges of perturbation being easily detected and patched. This study has directed further research towards hiding modifications from detection.

Suciu et al. [100] trained existing models to study their behaviour on a production-scale dataset. Author comparatively evaluated effectiveness of adversarial generation strategies at different scales and observed their transferability property. Full dataset with 16.3M PE files, EMBER dataset[266] with 1.1M PE files and mini dataset with 8598 files were used to train different attack strategies. Existing adversarial attacks are constrained on appending adversarial noise at the end of binary file. However, appended bytes are found to be less influential and offsetted by bytes in original malware. Inability of byte appending strategies while using size constrained detector like MalConv(Only first 2MB are considered for detection), led authors to use slack attacks. Slack attacks are performed by discovering the region in executable files that are not mapped to memory and will not affect the functionality on modification. These slack gaps formed due to mis-alignments between physical addresses in disk and virtual addresses are combined across all the slack regions and returned as slackindexes indicating modifiable regions. Research also pointed MalConv to take only 128 most discriminative features from 4195 possible features to make classification decision. Attacking most influential feature will amplify attack effectiveness and sufficiently appended bytes can replace legitimate features.
Random append adds values sampled from uniform distribution where gradient append uses gradient value of output with respect to input layer, giving the direction towards benign class. Random append and benign append fails to perform in all data size whereas Fast Gradient Method (FGM) append could reach 71% success rate in full dataset. Due to linearly increasing convergence time of gradient based approach with increase in number of appended bytes, FGM append attack is adapted as a one-shot gradient. Slack attacks are found to be more effective in both ember and full dataset with greater possibility for modifications in full dataset. FGM append achieved higher SR in comparison to slack attack but in expense of larger bytes modification. It is observed that models trained on larger data are more vulnerable as model encodes more sequential information allowing gradient evaluation be more meaningful. Need of appending bytes in each iteration for gradient append may lead to divergence from oscillating pattern. Single step gradient samples are found non-transferable against MalConv architecture. Authors were able to make comparative analysis over models in dataset of different scales and point out challenges of models.
| Paper/Year | Key Motivation | Target Model | Approach | Modification | Preserving Functionality |
|---|---|---|---|---|---|
| Park et al. 2019 [271] | Generative model by obfuscation in raw binaries | Inception V3 [272], MalConv [263] | • Dummy code insertion using Adversarial Malware Alignment Obfuscation • Semantic nops insertion to match original malware to standard adversarial • Optimization in closed loop till evasion | Semantic nops insertion | • Modification with executable adversarial • Dummy code insertion in form of semantic nops |
| Song et al. 2020 [273] | Practical adversarial generation and evaluation against real world anti-virus system | Signature based and machine learning based detectors | • Selection and application of macro actions from action space • Action sequence minimization, traversing through actions and removing unnecessary actions • Entangling macro actions to micro actions to evaluate feature essence | Through sequence of macro and micro action | • Functionality preserving actions • Cuckoo sandbox verification |
Key Motivation: The major motive behind the published work, Target Model: Target defense for adversarial attack, Approach: Key procedures to carry out adversarial attack, Modification: Changes on file to craft the adversarial perturbation, Preserving Functionality: Works towards safeguarding the functionality of a malware
All previous works based on gradient initialized perturbations with random noises and then iteratively updated using gradient of the model. Role of initializing perturbation in the success rate of adversarial generation can not be disregarded and Chen et al. [267] proposed use of saliency vector to select initializing perturbations from benign files. Researchers consider issue of accuracy and inefficiency in the work of Kreuk et al. [265] and Suciu et al. [100] as a result of random perturbation initialization before gradient driven iterative modification. Benign feature append method was carried out by debugging victim model once for generating saliency vectors whereas continuous debugging of model is required while incorporating FGSM algorithm. Saliency vector assigns values to benign and malicious regions of file with higher values linked to more significant features. In white box environment, BFA attack appends perturbation at the end of malicious files, selected using saliency vectors while enhanced-BFA attack uses most significant benign blocks for initialization. Avoiding random initialization helps model to obtain back propagation gradients and, gradient based algorithms can be implemented more effectively. Benign bytes form saliency vector also helps in mapping between adversarial from continuous space to discrete space avoiding random perturbations which can not be accurately mapped back to corresponding raw-byte perturbations. Authors also performed black box attack to malware detectors using random benign append and perturbations obtained by summarizing the successful trajectories of random attacks. This work was successful to increase the accuracy of gradient based adversarial generation techniques just by replacing random initialization.
7.1.2 Code Obfuscation Based Attack

Code obfuscation changes the pattern of program without any damage to program logic. Adversarial attacks using obfuscation deals with modifying code section without changing the functionality and flow of program, as shown in Figure 23. Table IV discusses the code obfuscation attacks done against Windows malware detectors. Park et al. [271] proposed a generative model for generating adversarial through obfuscation in raw binaries. The proposed approach minimally modifies malicious raw binaries using a dynamic programming based insertion algorithm, obfuscating the .txt section of a binary in executable byte sequence. Windows malware binaries are initially converted into grayscale images from byte code for obfuscation. Obfuscation technique called dummy code insertion is used to insert semantic nops (no operation) into a program. From the study, authors proposed Adversarial Malware Alignment Obfuscation (AMAO) algorithm which resembles string matching algorithm. Algorithm takes two inputs along with insertion points for semantic nops. One of the input is binary representation of non-executable adversarial example generated by standard adversarial generation algorithm (FGSM and C&W) with another input being binary representation of original malware. AMAO inserts semantic nops in original malware such that original malware matches to first input as closely as possible. At each iteration, algorithm chooses between inserting a semantic nop or not inserting anything based on distance metric between binary strings. Adding semantic nops is easier if the source code is given but without it, patching techniques are required [274, 275]. Algorithm outputs adversarial malware with original program’s logic after operating in a closed loop model until the classifier gets fooled. Authors tested AMAO algorithm against different classification models including simple CNN, LeNet5 [276], Inception V3 and MalConv [263] in a whitebox as well as blackbox environment. Proposed algorithm is found to be effective against classifiers employing both static and dynamic analysis with features such as API, system calls and n-grams.
Most of the attacks in adversarial domain are carried out in feature space and mapping features back to problem space is always not feasible. Attacks done in unrealistic scenarios are also not verified in terms of functionality. Song et al. [273] proposed a open-source systematic framework for adversarial malware attack using code randomization and binary manipulation to evaluate against real world antivirus systems. Authors collected large categories of features from open source malware detectors namely: hash-based signatures, rule-based signatures and data distribution based features. To carry modifications in these features, generic action set is prepared as micro and macro actions which are given in Table V. Micro actions are a relative concept, which only changes subset of actions inside macro-actions. Proposed workflow begins by selecting and applying macro-actions to original samples, till the original sample crosses decision boundary. Those macro-actions which do not have any roles are removed from action sequence to reach the most efficient evasive form. And finally, to get the detailed knowledge about the reason behind evasion, macro actions are broken into micro-action. From the modular point of view, binary rewriter module of framework generates different versions of original malware applying macro-actions randomly until the malware is able to evade static classifier. Action sequence minimization is carried out by traversing through actions and removing unnecessary actions. Cuckoo212121https://cuckoosandbox.org/ sandbox is used to verify the functionality of malware. To provide reasoning for evasion, every actions are entangled into several micro-actions and each macro-actions is replaced with one micro-actions at a time as shown in Figure 24. This process helps in evaluation of essential features change responsible for classification decision. Evasion rate of adversarial from framework is found to be highest in EMBER classifier while lowest in ClamAV222222https://www.clamav.net/. Signature based antivirus were evaded by only one byte of perturbation where machine learning based antivirus required more perturbations for evasion. This research directs future exploration towards generation of adversarial which can evade both static as well as dynamic detectors and also recommends antivirus systems to provide offline dynamic detection.
| Overlay Append | |
|---|---|
| Section Append | |
| Section Add | |
| Section Rename | |
| Remove Certificate | |
| Remove Debug | |
| Break Checksum | |
| Macro | Code Randomization |
| Overlay Append 1 Byte | |
| Section Append 1 Byte | |
| Section Add 1 Byte | |
| Section Rename 1 Byte | |
| Micro | Code Section Append 1 Byte |

7.1.3 Reinforcement Learning Based Attack
| Paper/Year | Target | Features | Action Space | Approach | Reward | SR |
| Anderson et al. 2018 [277] | Gradient Boosted Decision Trees (GBDT) | • 2350-Dimensional feature vector • Hashing trick to collapse into a vector of fixed size | 10 stochastic actions for simplicity | • ACER with DQN learns both a policy model and a Q-function • Boltzman exploration and exploitation where mutation are proportional to expected Q-value • Mutations till evasion or 10 rounds | Positive:10, Negative:0 | (12-24)% |
| Fang et al. 2019 [278] | GBDT | • Instability reduction using lower dimensional features • Feature vector of 513-D | 4 stochastic actions, choosen after assessing malware | • DQN with prioritized version of experience replay • Virtual address correction after modification • Integrity verification using Cuckoo Sandbox | TURN and discount factor based function | 75% |
| Chen et al. 2020 [279] | GBDT | • Features similar to Anderson et al.’s work [277] | 10 deterministic actions | • DQN and A2C based approach called as gym-malware-mini • Modification on original work of gym-malware | Positive:10, Negative:-1 | 83% |
| Fang et al. 2020 [280] | Neural network based DeepDetectNet with AUC score upto 0.989 | • Import function feature • General information feature • Byte entropy features • 2478-D feature vector | 200 deterministic actions | • Novel static feature extraction • RLAttackNet using DQN and optimized using double and dueling DQN • Different Q-network for choosing best action and Q-value | r= k*MAXTURN / TURN | 19.13% |
Target: Target defense for adversarial attack, Features: Properties of features considered for processing, Action Space: Nature of actions in action space Approach: Key procedures to carry out adversarial attack, Reward: Reward values used for learning, SR: Success Rate of evasion
To counter the need of differentiable model for gradient based approaches, reinforcement learning agent has been proposed to generate adversarial against malware detection. RL agent is provided with a set of operations to modify PE files while also preserving the functionality of malware. Goal of RL agent will be to perform sequence of operations on malware to evade detection. Reinforcement learning enables complete blackbox attacks to detector, creating real world attack scenario where attacker is completely unknown about detector. This reinforcement learning process is built around Markov decision process as shown in Figure 25. Table VI provides comparison of all RL approaches on adversarial evasion attack for Windows malware. Anderson et al. [97] proposed a whitepaper on evading malware detection by modifying Windows PE bytes for the first time. Anderson et al. [277] extended results of work done in [97] to perform generic black box attacks on static PE malware detection without assuming any knowledge of detector model’s structure and features, retrieving only malicious/benign label. Actor Critic Model with Experience Replay (ACER) is used to learn both policy model and a Q-function to estimate the state-action value. Reward of 0 is provided for malware samples which are detected by anti-malware engine and 10 for ones that can evade detection. Reward and state after each action are provided to an agent as a feedback. Feature vector is prepared such that it summarizes the state of the environment. 2350- dimensional feature vector is extracted from Windows PE malware consisting of features as:
-
•
Metadata of PE header
-
•
Section metadata: section name, size and characteristics
-
•
Metadata of Import and Export table
-
•
Counts of human readable strings
-
•
Byte histogram
-
•
2D byte-entropy histogram
Countably infinite features are collapsed into a vector of fixed size using hashing trick. The obtained feature vector provides the complete view of malware files.

Modifications to PE malware byte should not break file format and it’s functionality. So, functionality preserving actions used in action space includes following:
-
•
New functions are added to unused import address table
-
•
Existing section names can be manipulated
-
•
New sections can be created
-
•
Bytes can be appended to a space at the end of sections
-
•
A new entry point can be defined which can direct to an original entry point
-
•
A signer information can be removed
-
•
Debug info can be manipulated
-
•
Packing and unpacking operations can be carried out on file
-
•
Header checksum can be modified
-
•
Bytes can be appended in overlay
Functions in action space are stochastic in nature for simplicity. Appending bytes and compression level used by packer are chosen at random by the user to reduce the exponentially large number of mutations. During the construction of framework, authors considered feature representation used by agent to represent malware state, significantly overlaps with features of model under attack. Another important condition for success of reinforcement learning is that the agent’s actions need to be fully observable by state representation. Agent performs mutation using a Boltzman exploration/exploitation strategy where mutation are proportional to their expected value. The game of exploration and exploitation continues with mutation in each round till evasion or permitted mutation. Anderson et al. showed cross evasion attack by training models with different data sizes. Authors also successfully demonstrated model hardening by adversarial training using the evading samples during training process. Regardless of few shortcomings, [97] is able to direct the research towards adversarial world by just modifying binary bytes of Windows PE malware files in a blackbox environment.
To reduce the instability and increase the convergence speed of Gym-Malware [277], Fang et al. [278] proposed a Deep Q-network to Evade Antimalware engines (DQEAF) framework to evade anti-malware engines. DQEAF is able to reduce instability caused by higher dimensions, taking binary stream features of only 513 dimensions. It also takes only 4 functionality preserving actions in its action space to increase convergence and reports higher evasion rate. Action space is prepared only after assessing the malware to make actions more specific to the case. Actions proposed for deep Q-network training are as follows:
-
•
ARBE: Append random bytes at the end
-
•
ARI: Append random library with random function to import address table
-
•
ARS: Append a randomly named section to section table of PE data
-
•
RS: Remove Signature
An agent feeds the features and rewards to two different neural networks to determine action value and target action value, which undergoes global optimization during training process. At the end of training process, agent gives the optimal parameter values of neural networks. The deep Q-network in DQEAF is extended version of convolutional neural network, performed by adding new features with action value and target action value. Rewards are provided based on number of training ’TURN’ required to evade malware detection along with discount factor to consider future rewards, given in Equation 15.
| (15) |
where ’MAXTURN’ is defined to claim failure if the ’MAXTURN’ steps of modifications will still keep reward to 0. DQEAF also uses experience replay which allows reinforcement learning to remember and reuse experience from the past. Prioritized version of experience replay used, considers priority of transitions and important transitions are replayed more frequently. After number of transitions, action that leads to a maximum reward in state can be reached which is approximated in Equation 16.
| (16) |
where is the state at time , is action and is some weight to present the correctness of action selection. After maximization, best DQEAF agent is chosen which will carry out optimal actions to perform modifications on a malware file. Workflow of adversarial generation begins by reading original PE malware, followed by modifications using DQEAF and finally correcting the virtual address for sample with integrity ensurance using Cuckoo Sandbox. DQEAF was able to alleviate evasion rate to 70% in same dataset as used by Gym-Malware.
Chen et al. [279] proposed a reinforcement learning model based on Gym-Malware [97] using Deep Q-Network (DQN) and Advantage Actor Critic (A2C) deep reinforcement algorithm and named the environment as Gym-malware-mini. Even though authors claimed to have increased the evasion rate by 18% than that of Gym-Malware, it could be due to data leakage. Gym-malware-mini is trained and tested using the same data as that of gym-malware. Eleven actions in action space of Gym-Malware scales to uncountable number due to randomness in each action. Gym-malware-mini converts those random actions to 10 deterministic actions making actions space very small. 6 random actions that has been changed to deterministic are overlay append, imports append, section rename, section add, section append and upx pack. In addition, four actions are directly brought from gym malware including remove signature, remove debug, upx unpack and break optional header checksum. To balance the exploit and exploration, best action are chosen using epsilon-greedy method during the network training. Training workflow begins by initializing network parameters and hyper parameters. Once Gym-malware-mini gets the state of environment in form of feature vector, DQN network calculates action value followed by epsilon greedy algorithm choosing action to execute. The rewards are returned depending on the result of detector and state transitions are stored into replay buffer. Smaller action space aids in learning policy better. Gym-malware-mini also uses negative reward for punishment which helps to make agent learn faster.
Fang et al. [280] tried to address shortcomings of previous work by proposing own malware detection and adversarial generation method using DRL. MalConv [263], which has been a standard detector network for Windows PE malware by feeding whole binary bytes has been exploited by various researches. Its vulnerability to gradient based attacks for adversarial motivated authors to build their own malware detection system DeepDetectNet with AUC upto 0.989. For feature extraction, DeepDetecNet uses traditional approach which are based on feature engineering. Static feature extraction mainly includes three categories of features, which are:
-
•
Import Functions feature representing common import function
-
•
General information feature containing profile or overall attributes of a PE file
-
•
Bytes entropy feature is the feature extraction method
A total of 2478 features are extracted from PE files as Import Function features, General Information feature and Bytes Entropy feature. Same action in action space obtains different rewards based on the state of environment, which makes learning by agent confusing. Previous success on adversarial generation using reinforcement learning are found to be UPX packed which are not the actual modifications on PE files. In order to solve this problem, all random modification operations are expanded to 218 specific operations. To combat the problem of overestimation of reward as proposed by DeepMind [281], double and dueling DQN algorithm, RLAttackNet is proposed. The architecture is built using DQN and optimized with double DQN method and Dueling DQN method. One of the Q-network is responsible for choosing the most optimal action whereas another one for evaluating the Q-value. Dueling DQN divides Q-values into state values evaluating current environment state and action advantages which evaluates the goodness of actions. The reward is provided in each based on constants and which denotes maximum number of time a file can be modified. Authors could achieve the evasion rate of 19.13% and retrained DeepDetectNet using adversarial was able to reduce evasion rate to 3.1%.
7.1.4 GAN Based Attacks
| Paper/Year | Key-Motivation | Target Model | Byte/Feature | Approach | Feature Count |
| Hu. et al. 2017 [282] | Need of black-box flexible adversarial attack | ML based (RF, LR, DT, SVM, MLP, VOTE) detectors | Feature | • Feed Forward Neural Networks are used for both generator and substitute detector • Iterative approach, modifying one feature every iteration | 128 APIs |
| Kawai et al. 2019 [283] | Using single malware for realistic attacks | ML based (RF, LR, DT, SVM, MLP, VOTE) detectors | Feature | • Deep Convolutional GAN used for Substitutor() and Generator() • API list from multiple cleanware and single malware | All APIs |
| Castro et al. 2019 [284] | Automatic byte level modifications | GBDT Model | Byte Level | • Richer Feature representation • Generates random perturbation sequence with nine different options at each injection | 2350 Features |
| Yuan et al. 2020 [248] | End-to-End blackbox attacks at byte levels | MalConv [263] | Byte Level | • Dynamic thresholding to maintain the effectiveness of payload • Balance in attention of generator to payloads and adversarial samples are brought using automatic weight tuning | Raw Bytes |
Key Motivation: The major motive behind the published work, Target Model: Target defense for adversarial attack, Byte/Feature: Byte or Feature selected to modify, Approach: Key procedures to carry out adversarial attack, Feature Count: Number of features considered for processing
Most of existing adversarial generation deals with use of gradient information and hand-crafted rules. However, due to constrained representation ability of existing gradient based models, obtaining high true positive rate (TPR) has been the challenge. Generative Adversarial Networks (GAN) originally proposed by Goodfellow et al. [182] has inspired blackbox attack to malware detectors with very high TPR. The common GAN architecture that are used to perform adversarial malware attacks is shown in Figure 26. GAN uses discriminative model to distinguish between generated samples and real samples, and a generative model to fool the discriminative model between generated samples and real samples. Table VII summarizes adversarial attacks carried against Windows anti-malware engines.

Hu et al. [282] proposed an adversarial generation technique, MalGAN which is able to bypass black-box machine learning models. Like other GAN architecture, MalGAN is also made up of generator and a substitute detector with both being feed forward neural network. Binary features obtained by presence or absence of API are used as a input to model and number of input feature equals dimension of input. Generator is used to transform malware to its adversarial version by taking the probability distribution of adversarial far away from the detector. Concatenating malware feature vector with noise vector allows generator to produce numerous adversarial examples from a single malware feature vector. Substitute detector is used to fit the detector model and provide gradient information to train the generator.
MalGAN is trained with 160 system level Application Programming Interfaces (APIs) against different machine learning detector. Experiments were conducted separately with MalGAN and detector model sharing and splitting the training dataset. True positive rate of zero is obtained on most of machine learning models which shows the ability of substitute detector to fit with very high accuracy. MalGAN’s ability to perform complex transformation has resulted in zero TPR for both training and testing set.
Considering the use of multiple malware to train MalGAN affecting the performance of avoidance, Kawai et al. [283] proposed improved MalGAN with the use of only one malware for training. MalGAN imports malware detector for training and predicting which is not convenient for attackers. This improved MalGAN uses python’s sub process library to import only detection results to MalGAN. Authors also utilized all APIs used for malware to feature quantities instead of 128 APIs used by original MalGAN. Different dataset is used to prepare API list for training detector and MalGAN. API list are extracted by combining from multiple cleanware and single malware in order to avoid the malware detection process be driven by addition of cleanware’s features to malware file. Generator and Substitute model is also changed to Deep Convolutional GAN (DCGAN) originally proposed by Randford et al. [185] in image generation. For malware domain, activation is changed to Parametric Rectified Linear Unit (PReLU) function due to its ability to self-learn negative part of the Leaky ReLU function. Malware detectors are avoided by improved MalGAN through the addition of cleanware features to an initial malware file. Increase in feature quantities has improved the performance of both detectors and MalGAN.
Few assumptions made in designing MalGAN are less realistic and limited to bypass real malware classifier. One of such assumptions is that attackers are assumed to have full access to feature space in detector model. In addition, API features are considered too extended way to represent malware. To overcome these limitations, Castro et al. [284] published a poster to use GAN approach for generating adversarial examples by injecting byte-level perturbations. Proposed model works with real PE files instead of API feature representations. Automatic byte-level real perturbation is combined with feature representation to produce adversarial examples. Generator takes vector of 2350 features providing extensive overview of each malware and generates random perturbation sequence having 9 different possibilities at each injection. Use of richer feature representation and ability to return valid PE binaries makes system able to bypass not only GBDT detector but also cross-evade different classifiers.
Using API sequences or feature representation demands a lot of manual task to get the training data. Current state of art researches are directed towards end-to-end detection of malware without any feature engineering effort. Yuan et al. [248] proposed a GAPGAN framework which performs end-to-end black-box attacks against malware detectors using byte level features. Initial discrete malware binary features are mapped to continuous space before feeding to generator network of GAPGAN which generates adversarial perturbations to be appended at the end of original malware binaries. Dynamic thresholding preserves generated subtle perturbations while mapping back to discrete space from continuous space. The balance on the attention of the generator across payloads and adversarial samples is maintained using an automatic weight tuning strategy. Authors are able to achieve 100% evasion rate against MalConv [263] with the addition of only 2.5% perturbations data. Concurrently trained generator and discriminator keeps improving each other and transferability property of adversarial attack enables it to bypass detector. Variable input and output size gives great flexibility to GAPGAN model in contrast to prior research works.
7.1.5 Recurrent Neural Network Based Attack
Recent works have focused on use of Recurrent Neural Network (RNN) for malware detection and classification [21, 285, 286, 287]. Sequential malware API is used by RNN to predict whether the program is malware or benign. Papernot et al. [288] introduced adversarial sequence for RNN processing sequential data. The authors demonstrated the transferability property of adversarial examples generated from feed-forward neural networks against recurrent neural networks. Table VIII summarizes comparison among RNN, explainable ML and malware visualization based adversarial attacks. Hu et al. [240] proposed RNN based adversarial attack for RNN malware detector. The approximation of victim RNN model is done by training substitute RNN and generative RNN outputs sequential adversarial examples. Some irrelevant API sequence is generated and inserted in vulnerabilities of original sequence. API sequences, represented as a one-hot vector, are the input for generator network which generates adversarial API sequence. The generative part of RNN generates small API sequence pieces after each API which gets inserted after the API. Small sequence generation is done by sequence decoder where the hidden states are initialized with zero. A benign sequence and the Gumbel-Softmax [289] output is used to train the substitute network to fit the victim RNN based detector. Due to the use of bidirectional RNN equipped with an attention mechanism, substitute RNN can grasp the complex sequential pattern. Both forward and backward connections are present inside the bidirectional connection to represent the individual unidirectional connection. The attention mechanism helps by spreading the focus on different parts of the sequence. The output label provided by victim RNN for training data is used as training labels for substitute RNN. Gumbel-Softmax [289] exchanges gradient information across the generative RNN and the substitute RNN while also smoothing API symbols. Generative RNN function tries to minimize the probability of malicious prediction on which is given in Equation 17.
| (17) |
where is the regularization coefficient used for restricting the number of inserted APIs by maximing null API’s expectation probability, M is the index of the null API, denotes the expected value, is predicted malicious probability, is any parameter and is learned parameter. By separately tuning hyper-parameters of generative and substitute RNN, proposed architecture was successful in evading LSTM and BiLSTM based RNN malware detectors.
7.1.6 Explainable Machine Learning based attack
| Paper/Year | Key-Motivation | Target Model | Algorithms Used | Approach |
| Hu et al. 2017 [240] | Attack against RNN processing sequential data | LSTM and BiLSTM based detectors | Bidirectional RNN with attention mechanism | • Substitute RNN approximates victim RNN • Generative RNN gives sequential adversarial example • Irrelevant API sequence generated and inserted in vulnerabilities of original sequence |
| Rosenberg et al. 2020 [290] | Use of explainable machine learning for adversarial generation | GBDT Classifer | Integrated Gradient, LRP, DeepLIFT, SHAP | • Unearthing most impactful features using explainability algorithm • Manual selection of easily modifiable features • Feature by feature modification without harming functionality and interdependent features |
| Liu et al. 2019 [291] | Adversarial malware against visualization based detection | CNN, SVM and RF based malware detectors | ATMPA framework using GoogLeNet, FGSM and C&W | • Data transformation to convert code segments into grayscale images • Pre-training module to find function of malware detectors • Optimized FGSM and C&W attack is used to generate actual AE |
| Khormali et al. 2019 [292] | Targetted and Untargetted misclassification on windows and IoT malware dataset | Convolutional Neural Network | FGSM, C&W, DeepFool, MIM and PGD | • Adversarial generation using different algorithms • Conversion of adversarial dimension, same as of original image • Appending pixels at the end or injecting |
| Benkraouda et al. 2021 [293] | Attack against visualization based detection with ability to evade pre-processing filtering without losing functionality | Convolutional Neural Network | Modified version of CW attack[256], Euclidean distance | • Mask generator to flag the locations for perturbation • Modified version of CW attack to generate optimal perturbation • NOP generator to replace the perturbation from CW attack by semantic NOPs • AE optimizer to choose optimal viable NOPs |
Key-Motivation: The major motive behind the published work, Target Model: Target defense for adversarial attack, Algorithms Used: Algorithm used for crafting adversarial example, Approach: Key procedures to carry out adversarial attack
Malware detection is one of the most relevant domain for adversarial crafting as attackers are continuously attempting to evade detection networks. However, one of the biggest challenge of machine learning is the lack of explainability or reasoning behind such intelligent decisions. Recent researches have been able to bypass malware detectors using concept of explainable machine learning. Explainability approach involves finding the significance of each features and then conducting feature specific modification based on their importance.
Rosenberg et al. [290] proposed explainable ML approach to generate adversaries against multi-feature type malware classifiers. Authors not only performed feature addition like existing approaches but also modified feature-by-feature. Adversarial attackers first evaluate for the most effective list of features, and the features that are easy to modify are selected. Transferability of explainability allows the proposed attack achieve a very high impact on target classifier even in black-box attack. This approach assumes that the malware classifier and the substitute model possess similar feature importance, leading to modification in feature to impact the target malware classifier. Four different explainability algorithms on white-box [294, 295, 296] and black-box [297] are evaluated to make comparisons between substitute model and victim model. Brief introduction of each explainability algorithms is:
-
•
Integrated gradient [294] satisfies the completeness property by computing the average of the gradient on varying input while moving in a linear path.
-
•
Layer-wise Relevance Propagation (LRP) [295] works on backward pass by starting from the output layer. The relevance of each target neuron is given corresponding to the output of the neuron.
-
•
DeepLIFT [296] works in similar fashion to that of LRP but in backward order.
-
•
SHAP (SHapley Additive exPlanation) [297] attributes the classifier output to the totality of individual feature effects. SHAP can work without any knowledge about the architecture of the network to explain.
The proposed end-to-end PE adversarial examples performs feature modification without harming the malware functionality as well as interdependent features. Using naive and engineered features of EMBER dataset, explainable ML approach is successful in bypassing GBDT classifier. Rosenberg et al.’s work presents explainability as a duel edged sword that can be used by adversaries to make more explainable models as well as to carry out more robust adversarial attacks.
7.1.7 Malware Visualization based attack

Machine learning-based visualization detection has been popular due to its ability to prevent zero-day attacks and make detection without extracting pre-selected features [298, 299, 300]. These approaches convert binary code into image data and visualizes the features of sample, improving the detection speed for malicious program. Visualization based techniques are similar to adversarial generation in image domain where pixel perturbations are introduced as shown in Figure 27. Liu et al. [291] introduced Adversarial Texture Malware Perturbation Attack (ATMPA) against visualization based malware detection using rectifier in neural-network hidden layers. The framework allows an attacker to probe with the malware image while visualizing and also hiding them from malware detectors. The ATMPA framework is made up of three functional modules: data transformation, adversarial pre-training and malware detection. Code segments are converted into grayscale images during data transformation module. In the adversarial pre-training module, an attacker uses a machine learning approach to train an adversarial example generation model which produces a noise signal . The training process is divided into two modules: one to capture the normal malware behaviors and other to generate AEs. ATMPA framework uses GoogLeNet [75] for generating adversarial examples in the pre-training process where malware samples are represented using binary indicator vector without any structural properties or inter-dependencies. Adversarial example training uses a feedforward neural network having a rectifier as an activation function.
For generation of AEs, optimized FGSM and C&W attack is used. Using FGSM approach, perturbation with distortion = 0.35 was able to convert malware with 88.5% confidence into benign files with 99.8% confidence. ATMPA method also used -based C&W attack to generate adversarial, including and attack. Kaggle Microsoft Malware Classification Challenge232323https://www.kaggle.com/c/malware-classification/overview dataset is used against malware detection model built on commonly used CNN, SVM and RF-based detectors. Inception V3 architecture followed by FGSM and C&W attack methods generated pseudo-benign samples, successfully deceiving the detector. Authors also carried out transferability attack comparision on CNN, SVM and wavelet-combined algorithms with transfer rate as high as 88.7%.
COPYCAT approach proposed by Khormali et al. [292] produced both targeted and untargetted misclassification on Windows and IoT malware dataset. Author used two approaches: AE padding and sample injection to produce adversarial malware for visualization based detector. For padding method, COPYCAT generated adversarial using five different attack methods namely: FGSM [74], C&W [256], DeepFool [257], Momentum Iterative Method (MIM) [301] and Projection Gradient Descent (PGD) [302]. The generated adversarial needs to be converted to the dimensions same as that of original image before appending at the end of image. The binary samples from the targeted class are injected into an unreachable section of the target sample. The approach of this work is inspired by Cha et al. [303], where binaries of an application having different architecture are padded to alter the behavior based on the underlying system.
In order to provide adversarial attack that can evade visualization based detection system in presence of pre-processing filtering, Benkraouda et al.[293] proposed a binary rewriting based attack on malware files. A mask generator creates the space in the instruction boundary to insert the perturbations. Once the perturbation mask is created, the modified version of CW attack [256] is used to generated adversarial example in image space. The modified version is in the sense that, the perturbation mask is imposed while carrying out attack to restrict the positions of perturbations. NOP generator will replace the perturbation introduced by CW attack with the corresponding binaries, that preserve the malware functionality. And finally AE optimizer will use Euclidean distance metric to choose semantic NOPs that are closed to sequences in the allowed perturbation space. The approach is highly successfully in generating adversarial examples but are constrained by perturbation generation time as time is found to increase drastically with increase in size of malware.
7.2 Android Malware Adversarial
| Paper/Year | Target/Dataset | Approach | Modification | Limitations |
| Grosse et al. 2017 [304] | Feed forward neural network based detector / DREBIN | • Binary feature vector extraction using static evaluation • Jacobian matrix of neural network for adversarial generation • Direction for generated perturbation is given by gradient of the given function with respect to the input • Selection of perturbation with maximal positive gradient towards target class | • Feature addition to AndroidManifest.xml • Changing features leading to only one line of code | • Constrained on maximum feature space perturbation • Feature modifications confined inside AndroidManifest.xml |
| Yang et al. 2017 [305] | KNN, DT, SVM, RF/ DREBIN, VirusShare, Genome | • Malware Recomposition Variation conducting semantic analysis • Feature mutation analysis and phylogenetic analysis to perform automatic program transplantation • Malware evolution attack focusing on mimicking and automating the evolution of malware • Conufsion attack making features less differentiable to malware detection | • Resource, temporal, locale and dependency features used • Mutation following feature pattern of existing malware | • Significant alteration of semantic leading to higher failure rate of app |
| Rosenberg et al. 2018 [205] | RNN variaant and Feed forward neural networks/ VirusTotal | • Mimicry attacks against surrogate model • Surrogate model by querying black-box detectors with synthetic inputs selected by Jacobian based heuristics in prioritizing directions • Closest API call in direction indicated by Jacobian are selected | • No-op attack by adding API call with valid parameters • Functionality verification using sandbox after modification | • Detectable Residual artifacts during app transformation |
| Liu et al. 2019 [306] | Neural network, logistic regression, DT and RF based detectors/DREBIN | • Random forest to filter most significant features • Disturbance randomly generated and disturbance size calculated using genetic algorithm • Mutation using fitness function till fit and evading individual is produced | • Restricted permission modification on AndroidManifest file • Functionality changing modifications are deemed unfit | • Increased constraint on perturbation • Random perturbation affecting convergence |
| Shahpasand et al. 2019 [206] | SVM, Neural network, RF and LR / DREBIN | • GAN architecture with threshold on generated distortion • Different loss function to generate benign like adversarial and to produce high mis-classification | • Perturbation addition limited by threshold distortion amount | • Highly unstable learning of GAN architecture |
| Li et al. 2020 [307] | AdaBoost, CNN, SVM / Tencent Myapp, AndroZoo, VirusShare and Contagio | • Bi-objective GAN with two discriminator and one generator • First discriminator to distinguish malware and benign sample • Second discriminator to distinguish original and adversarial sample | • Iterative perturbation addition till evasion • Perturbation evading both malware and adversarial detection | • Very limited feature vectors ( Permission, action and API calls) are considered |
| Pierazzi et al. 2020 [207] | Linear SVM, Sec-SVM/DREBIN | • Formalization of adversarial evasion attacks in the problem feature space including transformations, semantics, robustness and plausibility • Automated software transplantation to extract benign slices from donor • Side effect features to find projections that maps perturbation to feasible problem-space regions • Gradient based strategy based on greedy algorithm to choose perturbation | • Perturbations appended at the end • Restricted addition of permissions • Cyclomatic Complexity to take heuristic approach maintaining existing homogeneity | • Heuristic based approaches are time and resource consuming |
| Bostani et al. 2021 [308] | DREBIN [309], Sec-SVM [310], MaMaDroid [311] / AndroZoo [312] | • Automated Software Transplantation Technique to prepare action set which includes gadgets extracted from benign Android apps • n-gram-based similarity method to identify benign APKs, closely similar to malware files • Applying extracted gadgets from benign samples into malicious files • Iterative and incremental manipulation | • Random Search(RS) for moving malware sample in problem space applying sequence of transformation in action set • New contents injected inside an IF statement | • In Random Search (RS) algorithm, actions from action space are random • Increase in adversarial size, increasing chances of adversarial detection |
Target/Dataset: Target defense for adversarial attack/Dataset used, Approach: Key procedures to carry out adversarial attack, Modification: Changes on file to craft the adversarial perturbation, Limitations: Shortcomings of proposed approach
Android has over 2.8 billion active users and owns 75% market share in mobile phone industry [313]. The wide usage of Android platform has attracted security threats in numerous forms and adversarial evasion attack is one of them. Table IX provides brief comparison among different adversarial attacks crafted against Android files. Grosse et al. [314] [304] generated adversarial examples for state-of-art Android malware detection trained on DREBIN dataset [309] with more than 63% accuracy. Authors migrated the method proposed by Papernot et al. [251] to handle binary features of Android malware while preserving the malicious functionality. Binary features are derived by statically evaluating code based on system call and usage of specific hardware. These derived features are also known as binary indicator vectors. The final goal of adversarial attack is to find perturbation/noise such that the prediction results of of is different from the original result, i.e, . gives target class while crafting adversarial. Authors adopted Jacobian matrix of neural network for adversarial generation. To get adversarial, the gradient of function with respect to is calculated to get the direction of perturbation such that output of classification function will change. Perturbation with highest positive gradient in direction of target is selected and is kept small enough to prevent negative change due to intermediary alterations of gradient. Functionality is preserved in this approach by changing features resulting in addition of only single line of code. Research also confine the modifications to manifest features related to AndroidManifest.xml file contained within Android application. With permissions, intents and activities being the most frequently modified features, authors successfully evaded DREBIN classifier[309] preserving the semantics of malware.
To overcome the white box attack issues, Rosenberg et al. [205] implemented GADGET framework to convert malware binary to an adversarial binary without access to malware source code. Proposed end-to-end black-box method is extended to bypass the multi-feature based malware classifiers relying on the transferability in RNN variants. For target RNN detector, malicious API call sequence is the adversarial example to be generated. Authors perform mimicry attacks where malicious code mimics the system calls of benign code to evade [315]. Adversaries train surrogate model having same decision boundaries as that of detector and then execute white-box attack on surrogate model. To build the surrogate model, black-box detector is queried with synthetic input values chosen by a Jacobian based heuristics in the prioritizing directions where model output varies. API calls which are nearest to the direction given by Jacobian are inserted to generate adversarial sequence. The label assigned to the input value by a black-box model gives the sign of the Jacobian matrix dimension. Jacobian matrix of the surrogate model is used for evaluation and after each iteration, synthetic example is added to each existing sample. However, finite set of legitimate API embeddings may not be enough for adversarial insertion, causing insertion of most impactful API call in direction indicated by Jacobian. Adversarial examples that are able to fool surrogate model has high likelihood of fooling original model as well [193]. Adversarial generation showed same success against the substitute and blackbox model with short API sequences, making adversarial generation faster. Framework also uses Cuckoo Sandbox to verify the malicious functionality of generated adversarial malware. GADGET framework wraps malware binary with proxy code and increases the risk even higher providing malware-as-a-service.
Adversarial attack on malware domain has not considered to manipulate the feature vector to see impact of mutation due to strict functionality preserving requirements of malware. Malware Recomposition Variation (MRV) based approach proposed by Yang et al. [305] performed an analysis of malware file semantically and construct a new variant of malware. Mutation strategies synthesized by conducting semantic-feature mutation analysis and phylogenetic analysis are used to perform automatic program transplantation [316]. Changing the traditional belief over mutation, authors followed feature patterns of existing malware to preserve the functionality. The proposed framework performs inter-component, inter-app, and inter-method transplantation. More comprehensive attack is performed on both the manifest file as well as dex code. Use of RTLD features allows substitute model to approximate targeted detector and also helps in separation of essential features and contextual features.
-
•
Resource features: These features provide the security-sensitive resources that are impacted by the malware. Resource features are extracted by forming call graphs and pinpointing call-graph nodes of those security-sensitive methods.
-
•
Temporal features: These features provide the environmental context at the trigger point of the malicious property and the context is inferred from the attributes at entry points.
-
•
Locale features: These features describe the location of programs where malicious activities are observed and can be either of the Android components of concurrency constructs.
-
•
Dependency features: These features are provided by constructing an inter-procedure control-flow graph, indicating the control dependencies when malicious activities are invoked.
The goal of malware evolution attack is to imitate and automate the evolution of malware using phylogenetic evolutionary tree [317]. A phylogenetic evolutionary tree shows the inferred relations between different samples based on the similarities and differences of feature representation. A pairwise distance between samples is fed to phylogenetic tree generation algorithm, Unweighted Pair Group Method Average (UPGMA), to generate phylogenetic tree which reflects the structure present in a similarity matrix. Another approach proposed by authors, confusion attack, tries to complement malware evolution attack against robust malware detectors [318]. The feature values modified by confusion attacks can be shared by both the malware sample and benign apps. This approach is more complete due to flexibility of mutation by different number of means but introduces challenges on keeping functionality intact due to higher volume of modification [207].
Several adversarial generation approaches have been conducted by making minor perturbations on existing attacks. Liu et al. [306] proposed a Testing framework for Learning-based Android Malware Detection systems (TLAMD). Framework uses genetic algorithm to perform black-box attack against Android malware detection system. Android files are modified by adding the request permission code to AndroidManifest.xml file which was originally proposed by Grosse et al. [304]. The restriction was imposed on the types and magnitude of permissions that can be added to AndroidManifest file. A random population is generated giving the characteristics of permission to add and followed by calculating the disturbance size for the sample malware. Using the evaluated perturbation size, adversarial is generated and tested against the detection model. Based on the result of detection either new disturbance size is calculated using genetic algorithms or perturbation is successfully added on Android application. Another important aspect of genetic algorithm is to model the fitness function which is this framework has been defined in Equation 18.
| (18) |
where and are the two weights, is the added disturbance, is number of permission features added and gives the probability of malicious sample being detected as malware. Fitness function searches for optimal solution to perform mutation leading to a new fit individual able to evade detection. Random forest approach is used to filter out insignificant features during feature extraction. Disturbance generated by genetic algorithm are able to bypass malware detectors trained on neural networks, logistic regression, decision trees and random forest.
Shahpasand et al. [206] implemented GAN to generate adversarial by keeping threshold on the distortion values of generated samples. The generated optimum perturbation is added to existing malware to produce adversarial. Like every other GAN architecture, generator can learn the distribution of benign samples, generating perturbations which are able to bypass learning based detector. The discriminator implicitly enhances the perturbation by escalating the loss of generator while the adversarial samples are identifiable with benign files. Loss function for GAN is similar to that of Goodfellow et al.’s [182] work given in Equation 19.
| (19) | |||
where gives probability of sample coming from benign software distribution, helps maximizing resemblance of adversarial malware with benign sample while limiting distortion less than c. Loss function of adversarial malware is given as:
| (20) |
where benign class is targeted for an adversarial sample against classifier trained on loss function. Finally, model loss is defined as:
| (21) |
In above equation, first loss forces the GAN to generate adversarial similar to benign samples while the second loss inclines adversarial samples to have higher miss-classification rate.
The goal of adversarial generation has been to bypass malware detector without losing functionality. However, due to growth in adversarial malware in recent time, defenders are employing firewalls to stop adversarial sample. Li et al. [307] extended the work of MalGAN [282] to make it robust against detection system equipped with firewall. Despite its high evasion rate against malware detectors, MalGAN is found to be less effective against detection systems using firewall. Bi-objective GAN with two discriminator having different objectives are used. One of the discriminator helps distinguish between malware and benign whereas another discriminator helps to find out whether the samples are adversarial or normal ones. Due to this feature, adversarial generated by generator can successfully bypass through the firewall as well as the malware detection. Authors used permissions, actions and application programming interface calls as a features to generate adversarial. In every round of training, gradient descent is used to update the parameters of discriminators and generator, represented by , and respectively. , and are considered functions implemented by generator, discriminator 1 and discriminator 2. First discriminator, used to separate benign and malicious class is trained to update , by minimizing its loss
| (22) |
where and denote the distributions of benign and malicious samples. Second discriminator used to separate between normal and adversarial samples is trained by updating by minimizing its loss
| (23) |
where is the distribution of normal samples and M is the distribution of generated samples detected as malicious. Generator is updated twice each round. After updating , is updated by minimizing
| (24) |
where is distribution of malicious samples fed to generator and is the distribution of noises fed to generator. After is updated, is updated by minimizing
| (25) |
| Paper/Year | Target | Approach | Modification | Limitations |
| Maiorca et al. 2013 [319] | PJScan, Malware Slayer and PDFRate | • Reverse mimicry attack by manipulating binary files to make it malicious • Malicious embedded EXE payload insertion • Malicious PDF file insertion inside a benign one • Encapsulating malicious JavaScript code | • Malicious EXE payload as a new version after trailer • Unrestrained embedded PDF structure insertion • JavaScript code without reference to any other object to minimize structure variation | • Less control on malicious goal |
| Biggio et al. 2014 [320, 321] | SVM and neural network based detectors | • Gradient based optimization inspired by Golland’s discriminative directions technique • Additional panalizing term to reshape objective function, biasing gradient descent towards region of negative class concentration | • Insertion of objects creating new PDF files | • Feature mapping issues • Non-differential discriminating functions can not be evaded |
| Srndic et al. 2014 [322] | PDFrate employed on Random Forest | • Taking advantage of discrepancy between operation of PDF reader and PDFrate • Mimicry attack to mimic 30 different benign files • GD-KDE attack to defeat classifier with differentiable decision function | • Insertion of dummy contents, ignored by PDF readers but affect detector • Trailer section moved away from cross reference table for file injection space | • Feature mappings are assumed to be perfect which is unrealistic |
| Carmony et al. 2016 [323] | PDFrate and PJScan | • Reference JavaScript extractor by directly tapping into a Adobe reader at locations identified by dynamic binary analysis • Parser confusion attack combined with reverse mimicry attack | • Obfuscation based on output of reference extractor | • Useful only for JavaScript based detector • Dependent on versions of Adobe Reader |
| Xu et al. 2016 [247] | PDFrate and Hidost | • Stochastic manipulations using genetic algorithm to generate population • Iterative population generation till evasion • Successful mutation traces reused for initialization efficiency • Fitness score based on maliciousness detected by oracle | • Inserting new, removing and modifying existing contents • Oracle confirming the maliciousness of file | • Stochastic approaches are resource intensive • No exact way to choose best fitness function |
Target: Target defense for adversarial attack, Approach: Key procedures to carry out adversarial attack, Modification: Changes on file to craft the adversarial perturbation, Limitations: Shortcomings of proposed approach
Pierazzi et al. [207] formalized the adversarial ML evasion attacks in the problem space and proposed a problem space attack on Android malware. The proposed approach formalizes the set of restriction in transformations available, semantics preserved, robustness of preprocessing approaches, and veracity. Research work is focused on evasion attacks at test time by modifying the objects in real input space corresponding to feature vector. With a goal of overcoming inverse feature-mapping problem from previous researches, author presents the idea of side-effect features. Side effect feature defines and proves the necessary as well as sufficient conditions behind the problem space attacks. An attack on a feature space is projected towards a feasibility region satisfying the problem space constraints to obtain the side effect features. To formally demonstrate the side-effect features, an object is initialized within a feasible region. A gradient-based attack takes an object in feature space to , with being the perturbation. The addition of perturbation misclassifies malware files as benign with high confidence. However, the new point with perturbed feature on feature vector may not be inside the feasibility region. Side effect features in perturbation help to map to the region of feasible problem-space.
Since side effect features contribute towards preserving validity of malware due to impact of original gradient based perturbation, side effect features alone can have both positive or negative influence on the classification score. Authors use automated software transplantation [316] to extract byte-codes from benign donor applications to inject into a malicious host, also known as organ harvesting. Insertion into a host is carried out between statements in non-system package to preserve the functionality and Cyclomatic Complexity is used to take a heuristic approach maintaining existing homogeneity and preventing violation of plausibility. Prior research works relied heavily on addition of permissions to the Android Manifest which is considered dangerous in Android documentation [324]. Authors bind the modifications to inject single permission to the host app. Gradient based strategy using greedy algorithm proposed in this approach overcomes previous limitations of preserving semantics and pre-processing robustness.
To overcome the challenges of limited access to target classifiers while circumventing black-box Android malware detectors, Bostani et al. [308] proposed a novel iterative and incremental manipulation strategy. The attack is carried out in two-step: preparation and manipulation. In preparation phase, automated software transplantation is employed to prepare action sets from Android apps. The n-gram-based similarity method is used to identify benign apps that closely matches to malware files. Insertion of extracted gadgets of closely matching benign files force malware sample towards the blind spots of the classifier. In the manipulation stage, perturbation on malware samples are applied incrementally, choosing from the collected action set. The search method randomly chooses suitable transformation and applies them to malware samples. This approach shows a high success rate in query efficient approach but increases the size of adversarial perturbation which in turn increases the risk of perturbation being easily detected.
7.3 PDF Malware Adversarial
Along with widespread applications and adoption, PDF documents have been one of the most exploited avenues for adversarial malware attacks. Initially, JavaScript based and structural properties detection were prominent for recognising malware in PDF. But freedom to distribute chunks of Javascript code and assemble together at run-time and high degree expressiveness in JavaScript language led to failure of Javascript based detection. Despite significant growth in PDF malware detection from JavaScript using deep learning techniques, the challenges posed by adversarial examples still exist. Early evasion attempts on PDF documents were crafted by Smutz et al. [325] and Šrndić et al. [326] using heuristic approaches. The authors proposed approach to build more robust PDF malware detection techniques, showcased the adversarial ability to mislead linear classification algorithm successfully.
Flexible logical structure of PDF has allowed to craft adversarial by carefully analyzing its structure. Maiorca et al. [319] demonstrated evasion technique called reverse mimicry attack against popular state-of-art malware detectors [327, 328, 325]. Traditionally, malicious PDF files are believed to be structurally different from benign PDF files. Taking advantage of this structural difference, most of malware detectors were able to discriminate PDF files with very high accuracy. However, malware files which can imitate the benign file structure or vice-versa can easily fool the detector. Reverse mimicry attacks can make benign files malicious with minimal changes in their structure. Malicious payloads poison the samples, initially classified as benign. Three kinds of malicious payloads introduced to benign files take the sample across the decision boundary of malware detector. First one is EXE payload with malicious embedding, which is introduced using Social Engineering Toolkit242424https://www.secmaniac.com/ as a new version after its trailer. On the addition of a new root object, the new trailer will point to a new object. In this payload, authors embedded malicious PDF files inside another benign PDF files using embedded function of PeePDF[329] tool. The embedded PDF file automatically opens without user interaction, allowing malicious PDF to be embed inside a benign one without any restriction on embedding file. PDF file injection enabled an attacker to have fine-grained control of structural features in the carrier file. A final kind of payload insertion is carried out by encapsulating a malicious JavaScript code without reference to other object. It helps to minimize variation in the benign-file structure by adding only one object to the tree. Such attacks based on structure are even capable of evading detectors using non-structural features. Table X provides overview of adversarial attacks carried out on PDF files.
Optimization based evasion attack against PDF malware detection was introduced by Biggio et al. [320, 321]. The attack was carried out using a gradient based optimization procedure inspired by Golland’s discriminative directions technique [330] to evade linear as well as non-linear classifiers. The proposed work was able to carry out complete knowledge and constrained knowledge attacks on non-linear models like Support Vector Machine(SVM) and neural networks. Work relied on easiness to insert new objects than to remove an embedded object to prevent from corrupting the PDF’s file structure. This approach used a gradient descent procedure with special consideration to avoid getting stuck on local optima. To increase the probability of successful evasion, an attacker needs to reach attack points that are legitimate, and to reach this, the additional penalizer term is introduced using a density estimator. The extra component helps imitate features of known legitimate samples, reshaping the objective function by biasing the gradient descent towards the negative class concentration region. This optimization-based approach dates before the realization of adversarial examples against deep learning architectures [331].

Srndic et al. [322] further enhanced optimization based attack against deployed system PDFrate [325] using mimicry attack, and Gradient Descent and Kennel Density Estimation (GD-KDE) attack. The attack takes advantage of discrepancy between functioning of PDF readers and PDFrate in terms of interpretation of semantic gaps as explained in [332]. The dummy contents to insert should be ignored by PDF readers but affect the feature computation in PDFrate. PDFrate evaluates sets of regular expressions from raw bytes, reading from beginning of PDF files while PDF readers parse PDF files using PDF format authorized by ISO 32000-1. PDF reader looks at the end of PDF for cross-reference table and goes to locate the object directly. Among 135 features of PDF rate, MIMICUS252525https://github.com/srndic/mimicus, 35 features are modified while incrementing values for 33 features with preserved functionality. Trailer section of PDF files were moved arbitrarily far away from cross-reference table, generating an empty space for file injection without affecting functionality of PDF document. A string pattern that is separated by whitespace is injected into the gap between CRT and the trailer of targeted PDF files as demonstrated in Figure 28. To match with specific PDFrate regular expression, patterns are also crafted. Two attack algorithms are implemented as explained:
-
•
Mimicry attack independent of underlying classifier, mimics a benign file by changing the modifiable features of malicious file. To increase effectiveness of the approach, each malware is trained to mimic 30 different benign files.
-
•
Gradient Descent and Kernel Density Estimation (GD-KDE) attack defeats classifier with a known and differentiable decision function [320]. GD-KDE algorithm follows the gradients of the classifier’s decision function and the estimated density function of benign samples.

PDF detection techniques are mostly reliant on PDF parser to extract features for classification [333, 334, 335]. These parser are unable to extract all JavaScript of PDF file. Carmony et al. [323] created a reference JavaScript extractor that measured the difference between the parser and Adobe Reader by tapping Adobe reader on locations given by binary analysis. Manual analysis refines the few candidate tap points provided by dynamic binary analysis. JavaScript extraction tap points are a function from which Adobe Reader extracts and executes JavaScript code from PDF documents. The memory accessed by Adobe Readers when reading PDF files using automatically executable JavaScript is analyzed to determine the raw JavaScript extraction tapping points. Proposed PDF parser confusion attack apply obfuscation on malicious PDF sample by analyzing the weaknesses of extractors in approach as shown in Figure 29. Reference extractor enables several new obfuscation in comparison to existing extractors and combination of these obfuscation were able to bypass all JavaScript extractor based detector. Metadata based detection systems require parser confusion attacks to be combined with reverse mimicry attack as core content of sample is not changed by confusion attacks.
In order to preserve maliciousness, most of research works take conservative approach by only inserting new contents and refraining from modification or removal of existing contents. Xu et al. [247] proposed a black-box generic method to evade the classifier as shown in Figure 30. As in figure, first the population is initialized by performing random modifications on malicious file. Then, each member of populations are passed through target classifier to measure maliciousness and through oracle to confirm the functionality. If no any samples are able to evade target classifier with functionality intact, subset of initialized population are chosen for next generation based on fitness score which indicates the progress towards evasive sample. Now, the population generation is repeated and this process is continued till the evasive sample is found or threshold iterations is met. Efficiency of search is enhanced by collecting traces of used mutation operation and reuse the effective operations. These effective traces are used for population initialization to generate variants for other malware. The author uses genetic programming (GP) to bring off stochastic modifications in an iterative manner till evasion. The oracle output and results of prediction from the target classifier need to be fed to the fitness function. Non malicious samples determined by oracle are assigned with low fitness score while malicious samples are provided with high score. Tools used as an oracle for maliciousness verification of adversarial samples, is an open computational challenge along with the selection of appropriate fitness function. The generic method is capable of automatically finding evasive variants irrespective of detection algorithms.

7.4 Hardware Based Malware Adversarial
| Paper/Year | Target Model | Data Collection | Feature Vectors | Approach |
| Khasawneh et al. 2017 [336] | Logistic Regression and neural network based detectors | • Running malware and cleanware files on a virtual machine operating on Windows 7 • Dynamic traces collected using Pin instrumentation tool • Dynamic traces providing run time behaviour of the programs | • Instructions Feature • Memory address patterns • Architectural Events | • Reverse engineering to create surrogate model of HMD • Dynamically instruction insertion into malware execution through Dynamic Control Flow Graph • Weighted injection strategy with insertion instruction selection proportional to negative weight |
| Dinakarrao et al. 2019 [337] | Logistic Regression and neural network based detectors | • Captured using Hardware Performance Counters (HPC) • Perf tool available under Linux used | • Low-level micro-architectural events • LLC load misses, branch instructions, branch misses and executed instructions | • Reverse engineering of Black-box HMD • HPC patterns perturbation mechanism determined using FGSM • Perturbation calculated using neural network • Adversarial generators running as separate thread to avoid interference with original source code |
| Nozawa et al. 2021 [338] | Neural network architecture | • Structural features analysis | • Gate level netlist | • Hardware circuits represented in graph structure and converted to feature space • During design step or after logic synthesis • Trojan-net concealment degree to prevent from detection • Modification evaluating value to limit the extent of modification |
Target Model: Defense model under adversarial attack, Data Collection: Feature value collection process, Feature Vectors: Types of features considered, Approach: Process of crafting adversarial

Hardware malware detectors use low-level information of features collected from hardware performance monitoring units available in CPUs. Hardware malware detectors are prone to reverse engineering [339], allowing mimicry attack [340] to reverse-engineered models. Adversarial against such detectors are carried out by generating perturbations in form of low-level hardware features, following the architecture shown in Figure 31. These adversarial generation approaches differ only on type of features used in comparison to previously discussed works. Table XI provides brief comparison of adversarial attacks against hardware malware detectors. Khasawneh et al. [336, 341] demonstrated evasion of Hardware Malware Detectors(HMD) after being reverse engineered, using low overhead evasion strategies. Data collected by running malware and cleanware programs on a virtual machine operating on Windows 7 are used to train a reverse-engineered model. Execution of malware requires disabling of Windows security services and firewall. Data required for training are dynamic traces while executing the program and are collected by using Pin instrumentation tool [342] by executing 500 system call or 15 millions of committed instructions. These dynamic traces are profiling of a run time behaviour of the programs. This dataset is comprised of three types of feature vectors:
-
•
Instructions feature giving the frequency of instructions.
-
•
Memory address patterns giving distribution of memory references.
-
•
Architectural events giving the occurrence of architectural events.
Reverse engineering allows to methodically create model similar to HMD, given the attacker has ability to query the target detector. Target detectors are considered to be based on logistic regression and neural networks to generalize most of the classification algorithms. Reverse engineering is carried out in all three types of feature vectors using both algorithms. Attackers have no information about size of instruction window, the specific features used by detector or the classification algorithm, detectors are trained on but have similar detectors to test their hypothesis. Authors[336] constructed a Dynamic Control Flow Graph (DCFG) of the malware to insert instructions into the executing malware dynamically. Injection of instruction feature increases the weight of the corresponding feature while memory feature injection alters the histogram of memory reference frequencies. Instructions are inserted using two approaches, block level and function level. Khasawneh et al. picked the instructions with negative weights to move the malware away from the decision boundary. Heuristic approach was taken to identify the candidate instructions for insertion. Weighted injection strategy where probability of selecting particular instruction is proportional to negative weight allowed to bypass HMD with around 10% dynamic overhead.
Dinakarrao et al. [337] also proposed an adversarial attack on low-level micro-architectural events captured through Hardware Performance Counters (HPC). Victim’s defense system (HMD) being black-box needs to be reverse engineered to mimic the behaviour. Number of HPC patterns required to bypass HMD is unknown which leads to need of adversarial sample predictor. The HPC patterns perturbing mechanism are implemented using a lower-complexity gradient approach, Fast Gradient Sign Method (FGSM).The adversarial perturbations needed to misclassify HPC trace is calculated using gradient based cost function of neural network. With being hyperparameters of neural network, being input HPC trace to the model and as output, cost function is defined as:
| (26) |
where is a scaling constant ranging between 0.0 to 1.0 and used to limit the perturbation to a very small value. The LLC load misses and branch misses are the most significant micro-architectural events of malicious application [343]. Linear models are built to find dependency of array sizes(n) and elements flushed(k) in route to determine LLC load misses generated. The adversarial perturbation generator is executed separately with a sample application to misclassify. The significance of running in a separated thread is to stop adversarial HPC generators from interfering with the application’s source code.
Micro-architectural events are useful when the malware program executes on a hardware device causing some changes in the performance of hardware. In addition to malware program execution, threat of injecting a malicious circuit during fabrication of hardware devices has grown [344]. Malicious circuits, also known as hardware Trojans, can be inserted into circuits producing logically equivalent results. Hardware circuits like processors include contribution of number of vendors before reaching to final product, and hence, carries high risk of adversarial circuit insertion anywhere between designing stage to manufacturing stage. Modifications in manufacturing stage are more tedious in comparison to design stage as few changes in hardware description language (HDL) are enough to embed hardware Trojans to the circuit. A trigger circuit allows the payload circuit to trigger malicious behavior such as information leakage and degrading performance after satisfying the trigger condition. A gate level netlist (the lists of nets and circuit elements) is used for malware detection by analyzing its structural features [345]. Several hardware Trojan detection have been recently adopted towards machine learning approaches including neural networks [346, 347, 348, 349].
Nozawa et al. [338] proposed an architecture to develop the adversarial hardware Trojan using Trojan-net Concealment Degree (TCD) and Modification Evaluating Value (MEV). Feature mapping issues like in all other adversarial attacks in Windows, Android and PDF are prevalent in hardware Trojan as well. Hardware circuits are represented in graphs structure and modifications in feature space does not guarantee the transfer back of modification to graph structure. Two stages in designing period are known for adversarial attack. First one being RTL (Register-transfer level) description design step and second one after logic synthesis. Authors take the assumption of Trojan detector using neural network architecture and the availability of raw output values from the detector to train adversarial model. Goal of adversarial is to maximize the loss function which is given as cross entropy(H) in Equation 27:
| (27) |
where K is the number of units in output layer, is the function to return label of and is function that returns the prediction result from classifier.
Summing up the loss function for each net and calculating the average gives Trojan-net concealment degree (TCD):
| (28) |
Larger TCD indicates the bigger difference in values of the prediction and answer, enabling to achieve the concealment of Trojan nets. However, to monitor the amount of modification authors used modification evaluating value (MEV).
| (29) | |||
where is one of the kinds of evaluation indicators and being the corresponding coefficient. The success of research work in evading Trojan nets from Trojan detectors reveal threat of adversarial at a whole new level.
7.5 Linux Malware Adversarial
Distributed edge computing has increased use of IoT devices. With large number of devices using Linux systems, robust malware detection is paramount. Both deep learning networks and Control Flow Graph (CFG) based malware detectors in IoT devices are found to be vulnerable against adversarial samples [350]. In off-the-shelf adversarial attack, authors examined different well known adversarial algorithms based on feature extraction. Generic adversarial algorithms are successful in adversarial generation with high evasion rate but limited on applicability of practical changes to feature space. In response to these challenges, adversarial based on control flow graph has been proposed[350]. Programs are structurally analyzed using vertices and edges with help of CFG. Graph embedding and augmentation (GEA) approach combines original graph with target graph, producing mis-classification while preserving the functionality of original program. GNU compiler collection command compiles in a way that only functionality related to original sample is executed. Linux based malware binaries easily evade IoT malware detection from different graph algorithmic constructs. In our search of literature, we found very limited works carried out as adversarial malware attacks in Linux domain.
8 Challenges and Future Directions
Following the introduction of adversarial attacks against deep learning by Szegedy et al. [71], machine learning research community have been concerned about its impact in different application domains. The research on adversarial attacks and its countermeasures is gaining momentum. To contribute towards the literature, we conducted a comprehensive research on various adversarial evasion attacks carried out against malware detection domain. Although, our survey highlights several successful adversarial attacks crafted against anti-malware engines, novel attacks are still evolving. In this section, we will discuss potential research open challenges and future direction as the adversarial approaches in malware analysis domain become more prevalent. Our intention is in no way to overlook or understate the contributions of existing adversarial attack researchers in malware domain.
8.1 Realistic (Practical) Attacks
Most of the existing adversarial attacks discussed in the survey are carried out using white-box approaches. In white-box approach, attackers are assumed to have full access to target model providing all required internal information to attackers. White-box approach is considered by most an unrealistic scenario in itself as it is unlikely that any ML based anti-malware engine will reveal information such as algorithms used, gradients of the model and hyper-parameters used to fine tune the model. Getting this information about a target model provides ‘superpower’ to attackers as they can camouflage the data in any way they want. In the future, research is expected to be more inclined towards complete black-box attacks. Few of the existing black-box attacks also depend on the performance of models provided in numeric form. Obtaining numerical performance is also not a realistic approach for attackers. So, we believe that further work should seek for completely black-box approaches for carrying out adversarial attacks.
In addition, the attacks discussed previously are primarily focused on static malware detection. The main reason behind it is the limited research carried out to test the robustness of dynamic detection. The modern industrial malware detection engines merge both static and dynamic detection techniques. Further, the attacker rarely gets the privilege to work with data at rest. There has been very few successful attempts to craft adversarial examples against data in motion [351, 352]. The malware domain can have data which is moving at a very high pace and may require to perform attack on data in motion. Data stored in a storage device or in transit may have enough time to let attackers generate adversarial examples for them while data moving at very high speed might allow smallest of time frames for attacker. Adversarial attacks are not always swift enough to work with data moving across network channels. So, more adversarial attacks are to be experimented for systems deployed with both static and dynamic detection as well as against data at motion.
8.2 Perturbation Insertion Space
Smart perturbation insertion plays a key role in determining the success of adversarial attacks. Initial adversarial evasion attacks on malware began by placing perturbations at the end of the malware file [265]. Most of the existing attack approaches are concentrated on additive adversarial perturbation. Demetrio et al. [99] later discovered that perturbations embedded at header sections of file resulted in effective adversarial attacks compared to perturbations appended at the end. However, header perturbation invited the risk of perturbation being detected and also increased the chances of breaking the malware file functionality. Suciu et al. [100] further investigated the possibility of inserting perturbations in slack regions of file which are left behind by the compilers. Experiments demonstrated that perturbations that are inserted in slack region are more effective than perturbations at other locations. These experiments provide inconclusive information about suitable insertion space for perturbation. Hence, further research is needed to determine optimal locations for perturbation that are more effective as well as undetected.
8.3 Enhancing Efficiency
Adversarial efficiency can be defined in terms of different parameters. The first and obvious efficiency criteria is the length of the payload to be generated as perturbation. Generating random noise is an inefficient approach while gradient based algorithms are developed to make an efficient adversarial attacks. The significance of the inserted payload determines the efficiency of perturbation. One way to insert efficient features is to first decipher the importance of each feature in the decision making of the machine learning model. Highly influential features can be modified to reach the adversarial goal with minimal perturbation volume. Despite the gradient helping attackers to generate perturbation in right direction, efficiency may be limited due to uncountable iterations to reach the adversarial goal. Applying small perturbations iteratively results in high quality adversarial evasion. However, these approaches will require immense amount of time, making it impossible for real time operation. To challenge this limitation, approaches like Fast Gradient Sign Method are proposed, which produce perturbations at very high pace but are less effective and have a high chance of being detected. Hence, research is needed to ensure that efficiency is looked both in terms of quantity and quality of noise generated to produce adversarial evasion. In addition, trade off between performance and computational complexity should be analysed to evaluate the worth of performing adversarial attacks [353].
8.4 Mapping Space Challenge
Mapping between problem space and feature space is performed by an embedding layer present in between them. The features in problem space can be of any form like n-grams, API names or other non-numeric parameters which can not be directly processed by machine learning models. This causes the problem space vectors to be converted into feature space which are some form of numeric values. The embedding layer however is an approximation mapping table between features in problem space and feature space. One of the biggest challenge of adversarial attacks is to map features in problem space and feature space precisely. Machine learning models require malware features to be converted to feature space from problem space so that adversarial examples can be crafted on them. However, there is no exact mapping between these spaces which results in approximate mapping, leading to slightly altered feature space than original problem space. After adversarial examples are crafted on malware files, mapping features back to problem space also lose few crafted perturbations due to lack of absolute mapping. Therefore, the challenge for defining adversarial space and efficiently searching elements approaching the best replacement has always been there in adversarial domain. Further research is needed to identify and map features in embedding space.
8.5 Automated Attacks
All of the discussed adversarial attacks require manual intervention at a few steps of the attack procedure. Human intervention makes the process time-consuming and impractical in many cases. In white-box attacks, the loss function of deep neural network can be used to determine most influential features and the corresponding features can be automatically modified [93]. Current literature relies on human efforts for feature extraction, mapping to adversarial generation and functionality verification. Minimizing human effort while moving towards automated adversarial generation could be the interesting arena to work on the future [354]. Novel research is needed to fully automate the adversarial attack ecosystem.
8.6 Explainable Adversarial
Adversarial vulnerabilities have been considered blind spots of machine learning models but current research work fails to assert concrete reasoning behind these blind spots. Having no consensus behind such reasoning leaves explaining the existence of adversarial example an open research domain. Goodfellow et al [74] first attributed vulnerability to the linear behavior of model in high dimensional space. However, there have been research that contradicts the accountability of adversarial behavior solely to linearity of model as highly non-linear models are also evaded successfully [355]. Explaining the adversarial phenomenon both in terms of models’ functionality and features’ contribution can pave a path for more robust adversarial attacks. Features can be assigned appropriate weights based on their contribution to alleviate the adversarial effect in the model. With the current state of the literature, explainable adversarial is still at an immature stage and requires concrete efforts from the community.
8.7 Transferable Attacks
Transferability refers to generalization property of the attack methods. A machine learning model with transferability property, trained on one particular dataset can generalize well for another different dataset as well. Transferability is a common property for evasion attack and is extensively exploited by black-box attacks. Untargeted attacks are found more transferable than targeted ones due to their generality [354]. Transferability can also take three different forms such as, same architecture with different data, different architecture with same application and different architecture with different data [81]. Although some studies have already been carried out on transferability, there is no any universally accepted postulation. The ability to use same data, model or algorithm to attack all available targets should be one of the goals of future research on adversarial attacks. Thus, attacker having transferability in their models should be able to attack defensive system irrespective of input and context in new targets.
8.8 Attacking Adversarial Defense
The influx of research on adversarial domain during last few years demonstrate the extent and importance of work in performing adversarial attack. The profound activity has not been limited to attack side but considering the threat posed to entire machine learning family, researchers have been equally active on defensive side as well. The cyber war between adversarial attackers and defenders are marching on an extremely high pace to overtake each other. Performing adversarial attacks are turning out to be harder than ever as many systems are designed robustly with adversarial defense in mind. Defensive approaches like adversarial training [356], defensive distillation [357] are proposed to stop adversarial attacks. Some recent techniques are hiding the gradients of target model [358], which if carried out successfully can completely nullify the threat of gradient based adversarial attacks. Hence, future adversarial attacks are required not only to bypass the machine learning detection but also overcome adversarial defenses. At the same time, novel defense mechanisms and approaches must be designed to make our models resilient against growing adversarial attack ecosystem.
8.9 Functionality Verification
Adversarial attacks on image domain carries a longer history than in malware domain. Image classifiers are attacked by modifying the image pixels to create adversarial. While modifying images, the pixels can be abundantly disrupted till it impacts the human perception. However, adversarial attacks is completely a different story in malware domain. The modifications carried out in a malware file should not alter the functionality of malware. The contents in executable file could be very sensitive and modification of a single byte can completely change the functionality of malware or even break the file, making it unexecutable. Most of the adversarial attacks have constrained themselves in perturbation type, volume and insertion techniques, just to preserve the functionality of executable. Malware functionality should not be compromised at the cost of any other adversarial constraints. Despite such gravity, most of the adversarial attacks are still not able to preserve the functionality of a modified files. Moreover, limited mechanisms exist to verify the functionality of malware after perturbing the file. One of the available approach is to run the malware file in an isolated environments like Cuckoo Sandbox [359]. But running every individual malware in a sandbox is inefficient and unrealistic. Therefore, further research should be directed to develop tools that can automatically and efficiently verify the functionality of malware post perturbations.
8.10 Attacking Federated Learning
Federated learning [360] is a hot topic as it allows individual nodes in a system to train a shared prediction model by confining all the data on individual devices [361]. This has gained a great popularity recently as it reduces the computational cost of centralized machine while preserving data privacy of each individual nodes. However, federated learning comes with greater risk of adversarial attacks as central system has no control over the training data. Learning system can easily be poisoned while training, leaving the backdoors in trained model [362]. The training model with backdoors can be easily evaded using targeted or untargeted attacks. As federated learning is coming into limelight recently, the adversarial risks are yet to be properly quantified before embracing the technology that could be the future.
8.11 Benign Files Attack
Adversarial attacks are performed in malware files by inserting some non-malicious contents which do not tamper with any functionality other than classification decision. Modifying malware files slowly has been a mainstream approach for adversarial. However, no limited or no existing research has studied the possibility of inserting malicious contents to a benign files. This approach works in a reverse way than the established adversarial approaches. Inserting and hiding malicious payload at different locations of file without affecting the classification decision is also a future research topics in adversarial and requires attention.
8.12 Targeting Unexplored Algorithms
Most of the machine learning algorithms have already been victimized by adversarial attackers, including sophisticated deep neural network architectures. However, there are some deep neural networks that haven’t yet been compromised by adversarial attackers such as Generative Adversarial Networks (GANs), Deep Reinforcement learning (DRL) and Variational Auto-Encoders (VAEs) [93]. These algorithms are itself in development stage, which has capped the adversarial attempt to them till date. Differentiable neural computer [363] are only attacked once [364]. These new sets of algorithms are yet to be explored by adversarial attackers.
8.13 Standardizing Testbed and Metrices
Adversarial attacks discussed in the survey are carried out in lab environments, taking numerous assumptions which may be unpragmatic for real world challenges. Most of the works have assumed unlimited access to machine learning model, favourable dataset and weak classifiers to bolster their results. The current literature lacks standardized dataset and detection mechanisms to measure the exact performance of adversarial attack. As vast number of research works are performed on different dataset and target model, it is not possible to compare the performance of attacks. Hence, the attack testbed should be standarized to bring the assessment uniformity across the research community and uplift the attack standard out from the lab environment.
The issue is not limited to test environment but also with evaluation metrices. More than often, the performance of adversarial attacker is reflected in terms of evasion accuracy inherited from machine learning models. However, accuracy only provides small fraction of attacker’s performance in adversarial domain. To provide the overall quality of attacks, metrics such as transferability, universality and imperceptability need to be studied [353]. The metrics should be descriptive, fair, and complete to evaluate the quality of attacks performed across different environments. Some metrics should also be developed to measure the degree of functionality preservation while manipulating the files. Incorporating attack’s meaning preservation capability as a quality metrics have shown the benefit in recent works [365]. Some distance metrics can be used to determine the differences between original file and adversarial modification. Metrics can also be designed to determine the sensitivity of file structure, helping attacker to determine the level of cautiousness required while modification. These complete and fair metrices will not only help to understand and compare the adversarial quality but also to enhance the performance of attacks.
8.14 Adversarial Defense
The growth in adversarial attacks and novel approaches will also require developing advanced defense mechanisms. Although, our survey is focused on adversarial evasion attacks, we believe it is important to briefly highlight future defense directions to present a comprehensive review paper. Among several defense techniques proposed, defensive distillation [366] and adversarial training [367, 368] are found to be the most effective. While talking about the effectiveness of existing works, we cannot undermine the challenges faced by them. Collection of adversarial samples in large amount to perform adversarial training is a tedious task as neural networks require massive volume of adversarial data [369]. An adversarial generation approach was proposed by Goodfellow et al. [182], however is still very far away from being efficient and accurate enough to perform the robust adversarial training. In addition, many defensive approaches that have been tested in an image domain [370, 371] are yet to be introduced for a defense in malware adversarial domains. Recent research using robust machine learning architectures like Generative Adversarial Networks (GANs) [372] for defending against adversarial attacks require more exploration to thwart or detect sophisticated evasion attacks. Overall, the future research works on adversarial malware should be directed to build more robust, efficient, generalized and reliable defense mechanisms that can protect malware detection models against the adversarial attacks.
9 Conclusion
Machine learning and AI solutions are increasingly playing an important role in cyber security domain. However, these data driven systems can be easily manipulated, misled and evaded which can have serious implications. Recent surge and research in adversarial attacks highlight the vulnerability of ML models making them ineffective against even minor perturbations. In this paper, we provide a comprehensive survey of recent work that focuses on adversarial evasion attacks in malware analysis domain. We have summarized the state-of-art adversarial attacks carried out against anti-malware engines in different file domains. The survey demonstrates the flaw of machine learning architectures against minute perturbations in form of adversarial attacks. We taxonomize the adversarial evasion world of malware based on attack domain and approach taken to realize adversarial evasion attacks. Survey briefly discusses approaches taken by researchers, comparing them with other concomitant works. We conclude the survey highlighting current challenges, open issues and future research directions in adversarial malware analysis. This work will provide a definitive guide to researchers and community, to understand the current scenarios of adversarial malware evasion attacks and prompting unexplored research territories in this highly dynamic and evolving domain.
References
- [1] Total data volume worldwide 2010-2025. https://www.statista.com/statistics/871513/worldwide-data-created/.
- [2] Daniel W. Otter, Julian R. Medina, and Jugal K. Kalita. A Survey of the Usages of Deep Learning for Natural Language Processing. IEEE Transactions on Neural Networks and Learning Systems, 32(2):604–624, 2021.
- [3] Tom Young, Devamanyu Hazarika, Soujanya Poria, and Erik Cambria. Recent Trends in Deep Learning Based Natural Language Processing [review article]. IEEE Computational Intelligence Magazine, 13(3):55–75, 2018.
- [4] Matt Gardner, Joel Grus, Mark Neumann, Oyvind Tafjord, Pradeep Dasigi, Nelson Liu, Matthew Peters, Michael Schmitz, and Luke Zettlemoyer. AllenNLP: A Deep Semantic Natural Language Processing Platform. arXiv preprint arXiv:1803.07640, 2018.
- [5] D Jude Hemanth and V Vieira Estrela. Deep Learning for Image Processing Applications, volume 31. IOS Press, 2017.
- [6] Muhammad Imran Razzak, Saeeda Naz, and Ahmad Zaib. Deep Learning for Medical Image Processing: Overview, Challenges and the Future. Classification in BioApps, pages 323–350, 2018.
- [7] Luis Perez and Jason Wang. The Effectiveness of Data Augmentation in Image Classification using Deep Learning. arXiv preprint arXiv:1712.04621, 2017.
- [8] Tsung-Han Chan, Kui Jia, Shenghua Gao, Jiwen Lu, Zinan Zeng, and Yi Ma. PCANet: A Simple Deep Learning Baseline for Image Classification? IEEE Transactions on Image Processing, 24(12):5017–5032, 2015.
- [9] Mohammed Al-Qizwini, Iman Barjasteh, Hothaifa Al-Qassab, and Hayder Radha. Deep learning algorithm for autonomous driving using GoogLeNet. In IEEE Intelligent Vehicles Symposium (IV), pages 89–96, 2017.
- [10] Hironobu Fujiyoshi, Tsubasa Hirakawa, and Takayoshi Yamashita. Deep learning-based image recognition for autonomous driving. IATSS research, 43(4):244–252, 2019.
- [11] Ahmad EL Sallab, Mohammed Abdou, Etienne Perot, and Senthil Yogamani. Deep Reinforcement Learning Framework for Autonomous Driving. Electronic Imaging, 2017(19):70–76, 2017.
- [12] Brody Huval, Tao Wang, Sameep Tandon, Jeff Kiske, Will Song, Joel Pazhayampallil, Mykhaylo Andriluka, Pranav Rajpurkar, Toki Migimatsu, Royce Cheng-Yue, et al. An Empirical Evaluation of Deep Learning on Highway Driving. arXiv preprint arXiv:1504.01716, 2015.
- [13] Adam H Marblestone, Greg Wayne, and Konrad P Kording. Toward an Integration of Deep Learning and Neuroscience. Frontiers in computational neuroscience, 10:94, 2016.
- [14] Blake A Richards, Timothy P Lillicrap, Philippe Beaudoin, Yoshua Bengio, Rafal Bogacz, Amelia Christensen, Claudia Clopath, Rui Ponte Costa, Archy de Berker, Surya Ganguli, et al. A Deep Learning Framework for Neuroscience. Nature neuroscience, 22(11):1761–1770, 2019.
- [15] Hidenori Tanaka, Aran Nayebi, Niru Maheswaranathan, Lane McIntosh, Stephen A Baccus, and Surya Ganguli. From Deep Learning to Mechanistic Understanding in Neuroscience: The Structure of Retinal Prediction. In Proceedings of the International Conference on Neural Information Processing Systems, 2019.
- [16] Mackenzie Weygandt Mathis and Alexander Mathis. Deep learning tools for the measurement of animal behavior in neuroscience. Current Opinion in Neurobiology, 60:1–11, 2020.
- [17] Mahmoud Abdelsalam, Ram Krishnan, Yufei Huang, and Ravi Sandhu. Malware Detection in Cloud Infrastructures Using Convolutional Neural Networks. In IEEE International Conference on Cloud Computing, pages 162–169, 2018.
- [18] Justin Sahs and Latifur Khan. A machine learning approach to android malware detection. In 2012 European Intelligence and Security Informatics Conference, pages 141–147. IEEE, 2012.
- [19] Andrew McDole, Maanak Gupta, Mahmoud Abdelsalam, Sudip Mittal, and Mamoun Alazab. Deep learning techniques for behavioral malware analysis in cloud IaaS. In Malware Analysis using Artificial Intelligence and Deep Learning, pages 269–285. Springer, 2021.
- [20] Andrew McDole, Mahmoud Abdelsalam, Maanak Gupta, and Sudip Mittal. Analyzing CNN based behavioural malware detection techniques on cloud IaaS. In International Conference on Cloud Computing, pages 64–79. Springer, 2020.
- [21] Jeffrey C Kimmel, Andrew D Mcdole, Mahmoud Abdelsalam, Maanak Gupta, and Ravi Sandhu. Recurrent Neural Networks Based Online Behavioural Malware Detection Techniques for Cloud Infrastructure. IEEE Access, 9:68066–68080, 2021.
- [22] Jeffrey C Kimmell, Mahmoud Abdelsalam, and Maanak Gupta. Analyzing Machine Learning Approaches for Online Malware Detection in Cloud. In IEEE Smartcomp, 2021.
- [23] Thiago S Guzella and Walmir M Caminhas. A review of machine learning approaches to Spam filtering. Expert Systems with Applications, 36(7):10206–10222, 2009.
- [24] Konstantin Tretyakov. Machine Learning Techniques in Spam Filtering. In Data Mining Problem-oriented Seminar, MTAT, volume 3, pages 60–79. Citeseer, 2004.
- [25] Chih-Chin Lai. An empirical study of three machine learning methods for spam filtering. Knowledge-Based Systems, 20(3):249–254, 2007.
- [26] Emmanuel Gbenga Dada, Joseph Stephen Bassi, Haruna Chiroma, Adebayo Olusola Adetunmbi, Opeyemi Emmanuel Ajibuwa, et al. Machine Learning for Email Spam Filtering: Review, Approaches and Open Research Problems. Heliyon, 5(6):e01802, 2019.
- [27] John O Awoyemi, Adebayo O Adetunmbi, and Samuel A Oluwadare. Credit card fraud detection using Machine Learning Techniques: A Comparative Analysis. In IEEE International Conference on Computing Networking and Informatics, 2017.
- [28] Dejan Varmedja, Mirjana Karanovic, Srdjan Sladojevic, Marko Arsenovic, and Andras Anderla. Credit Card Fraud Detection-Machine Learning methods. In International Symposium INFOTEH-JAHORINA (INFOTEH), pages 1–5. IEEE, 2019.
- [29] Aderemi O Adewumi and Andronicus A Akinyelu. A Survey of Machine-Learning and Nature-Inspired Based Credit Card Fraud Detection Techniques. International Journal of System Assurance Engineering and Management, 8(2):937–953, 2017.
- [30] Abhimanyu Roy, Jingyi Sun, Robert Mahoney, Loreto Alonzi, Stephen Adams, and Peter Beling. Deep Learning Detecting Fraud in Credit Card Transactions. In IEEE Systems and Information Engineering Design Symposium, pages 129–134, 2018.
- [31] Dinggang Shen, Guorong Wu, and Heung-Il Suk. Deep Learning in Medical Image Analysis. Annual Review of Biomedical Engineering, 19:221–248, 2017.
- [32] Miles N Wernick, Yongyi Yang, Jovan G Brankov, Grigori Yourganov, and Stephen C Strother. Machine Learning in Medical Imaging. IEEE Signal Processing Magazine, 27(4):25–38, 2010.
- [33] Igor Kononenko. Machine Learning for Medical Diagnosis: History, State of the Art and Perspective. Artificial Intelligence in Medicine, 23(1):89–109, 2001.
- [34] Bradley J Erickson, Panagiotis Korfiatis, Zeynettin Akkus, and Timothy L Kline. Machine Learning for Medical Imaging. Radiographics, 37(2):505–515, 2017.
- [35] Ashwin Dhakal, Cole McKay, John J Tanner, and Jianlin Cheng. Artificial intelligence in the prediction of protein-ligand interactions: recent advances and future directions. Briefings in Bioinformatics, page bbab476.
- [36] Evan Martin and Tao Xie. Inferring access-control policy properties via machine learning. In IEEE International Workshop on Policies for Distributed Systems and Networks, 2006.
- [37] Maanak Gupta, Farhan Patwa, and Ravi Sandhu. POSTER: Access control model for the Hadoop ecosystem. In Proceedings of the ACM on Symposium on Access Control Models and Technologies, 2017.
- [38] Leila Karimi and James Joshi. An Unsupervised Learning Based Approach for Mining Attribute Based Access Control Policies. In IEEE International Conference on Big Data (Big Data), 2018.
- [39] Maanak Gupta and Ravi Sandhu. Towards Activity-Centric Access Control for Smart Collaborative Ecosystems. In Proceedings of the ACM Symposium on Access Control Models and Technologies, 2021.
- [40] Zahra Bazrafshan, Hashem Hashemi, Seyed Mehdi Hazrati Fard, and Ali Hamzeh. A Survey on Heuristic Malware Detection Techniques. In IEEE Conference on Information and Knowledge Technology, pages 113–120, 2013.
- [41] Min Zheng, Mingshen Sun, and John CS Lui. DroidAnalytics: A Signature Based Analytic System to Collect, Extract, Analyze and Associate Android Malware. In IEEE Conference on Trust, Security and Privacy in Computing and Communications, 2013.
- [42] Deepak Venugopal and Guoning Hu. Efficient signature based malware detection on mobile devices. Mobile Information Systems, 4(1):33–49, 2008.
- [43] Abhaya Kumar Sahoo, Kshira Sagar Sahoo, and Mayank Tiwary. Signature based malware detection for unstructured data in Hadoop. In International Conference on Advances in Electronics Computers and Communications, pages 1–6. IEEE, 2014.
- [44] Muhamed Fauzi Bin Abbas and Thambipillai Srikanthan. Low-Complexity Signature-Based Malware Detection for IoT Devices. In International Conference on Applications and Techniques in Information Security, pages 181–189. Springer, 2017.
- [45] Jin-Young Kim, Seok-Jun Bu, and Sung-Bae Cho. Zero-day Malware Detection using Transferred Generative Adversarial Networks Based on Deep Autoencoders. Information Sciences, 460:83–102, 2018.
- [46] Gavin Phillips, Gavin Phillips (987 Articles Published) Gavin is the Junior Editor for Windows, and Technology Explained. These 4 Antivirus Tools Are Using AI to Protect Your System. https://www.makeuseof.com/tag/artificial-intelligence-antivirus-tools/, Aug 2018.
- [47] Konrad Rieck, Philipp Trinius, Carsten Willems, and Thorsten Holz. Automatic analysis of malware behavior using machine learning. Journal of Computer Security, 19(4):639–668, 2011.
- [48] State of IoT 2021: Number of connected IoT devices growing 9% to 12.3 billion globally, cellular IoT now surpassing 2 billion, Sep 2021.
- [49] Sara Morrison. How a major oil pipeline got held for ransom. https://www.vox.com/recode/22428774/ransomeware-pipeline-colonial-darkside-gas-prices, May 2021.
- [50] Electronics Retailer MediaMarkt Hit by Ransomware Demand for $50M Bitcoin Payment: Report. https://www.yahoo.com/lifestyle/electronics-retailer-mediamarkt-hit-ransomware-151038565.html.
- [51] Lawrence Abrams. Computer giant Acer hit by $50 million ransomware attack. https://www.bleepingcomputer.com/news/security/computer-giant-acer-hit-by-50-million-ransomware-attack/, Mar 2021.
- [52] MHR Khouzani, Saswati Sarkar, and Eitan Altman. Maximum Damage Malware Attack in Mobile Wireless Networks. IEEE/ACM Transactions on Networking, 20(5):1347–1360, 2012.
- [53] Hao Hu, Steven Myers, Vittoria Colizza, and Alessandro Vespignani. Wifi networks and malware epidemiology. Proceedings of the National Academy of Sciences, 106(5):1318–1323, 2009.
- [54] Michael Schwarz, Samuel Weiser, and Daniel Gruss. Practical enclave malware with Intel SGX. In International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, pages 177–196. Springer, 2019.
- [55] Surbhi Gupta, Abhishek Singhal, and Akanksha Kapoor. A Literature Survey on Social Engineering Attacks: Phishing Attack. In IEEE International conference on computing, communication and automation (ICCCA), pages 537–540, 2016.
- [56] Jason Hong. The State of Phishing Attacks. Communications of the ACM, 55(1):74–81, 2012.
- [57] Tzipora Halevi, Nasir Memon, and Oded Nov. Spear-Phishing in the Wild: A Real-World Study of Personality, Phishing Self-Efficacy and Vulnerability to Spear-Phishing Attacks. Phishing Self-Efficacy and Vulnerability to Spear-Phishing Attacks, 2015.
- [58] Ulrike Meyer and Susanne Wetzel. A man-in-the-middle attack on UMTS. In Proceedings of the 3rd ACM workshop on Wireless security, pages 90–97, 2004.
- [59] Franco Callegati, Walter Cerroni, and Marco Ramilli. Man-in-the-Middle Attack to the HTTPS Protocol. IEEE Security & Privacy, 7(1):78–81, 2009.
- [60] Simon Eberz, Martin Strohmeier, Matthias Wilhelm, and Ivan Martinovic. A Practical Man-In-The-Middle Attack on Signal-Based Key Generation Protocols. In European Symposium on Research in Computer Security, pages 235–252. Springer, 2012.
- [61] Jelena Mirkovic, Sven Dietrich, David Dittrich, and Peter Reiher. Internet Denial of Service: Attack and Defense Mechanisms (Radia Perlman Computer Networking and Security Book Series). 12 2004.
- [62] Christoph L Schuba, Ivan V Krsul, Markus G Kuhn, Eugene H Spafford, Aurobindo Sundaram, and Diego Zamboni. Analysis of a denial of service attack on TCP. In Proceedings IEEE Symposium on Security and Privacy, pages 208–223, 1997.
- [63] Tauseef Jamal, Zeeshan Haider, Shariq Aziz Butt, and Assim Chohan. Denial of Service Attack in Cooperative Networks. arXiv preprint arXiv:1810.11070, 2018.
- [64] William G Halfond, Jeremy Viegas, Alessandro Orso, et al. A Classification of SQL-Injection Attacks and Countermeasures. In Proceedings of the IEEE international symposium on secure software engineering, volume 1, pages 13–15. IEEE, 2006.
- [65] Adam Kieyzun, Philip J Guo, Karthick Jayaraman, and Michael D Ernst. Automatic creation of SQL injection and cross-site scripting attacks. In 2009 IEEE 31st international conference on software engineering, pages 199–209. IEEE, 2009.
- [66] Chris Anley. Advanced SQL injection in SQL server applications. 2002.
- [67] Ali Shafahi, W Ronny Huang, Mahyar Najibi, Octavian Suciu, Christoph Studer, Tudor Dumitras, and Tom Goldstein. Poison Frogs! Targeted Clean-Label Poisoning Attacks on Neural Networks. arXiv preprint arXiv:1804.00792, 2018.
- [68] Xuanqing Liu, Si Si, Xiaojin Zhu, Yang Li, and Cho-Jui Hsieh. A Unified Framework for Data Poisoning Attack to Graph-Based Semi-supervised Learning. arXiv preprint arXiv:1910.14147, 2019.
- [69] Di Cao, Shan Chang, Zhijian Lin, Guohua Liu, and Donghong Sun. Understanding Distributed Poisoning Attack in Federated Learning. In 2019 IEEE 25th International Conference on Parallel and Distributed Systems (ICPADS), pages 233–239. IEEE, 2019.
- [70] Juncheng Shen, Xiaolei Zhu, and De Ma. TensorClog: An Imperceptible Poisoning Attack on Deep Neural Network Applications. IEEE Access, 7:41498–41506, 2019.
- [71] Christian Szegedy, Wojciech Zaremba, Ilya Sutskever, Joan Bruna, Dumitru Erhan, Ian Goodfellow, and Rob Fergus. Intriguing properties of neural networks. arXiv preprint arXiv:1312.6199, 2013.
- [72] Alexey Kurakin, Ian J. Goodfellow, and Samy Bengio. Adversarial Examples in the Physical World. ArXiv, abs/1607.02533, 2017.
- [73] Ibrahim Yilmaz. Practical Fast Gradient Sign Attack Against Mammographic Image Classifier. arXiv preprint arXiv:2001.09610, 2020.
- [74] Ian J Goodfellow, Jonathon Shlens, and Christian Szegedy. Explaining and Harnessing Adversarial Examples. arXiv preprint arXiv:1412.6572, 2014.
- [75] Christian Szegedy, Wei Liu, Yangqing Jia, Pierre Sermanet, Scott Reed, Dragomir Anguelov, Dumitru Erhan, Vincent Vanhoucke, and Andrew Rabinovich. Going Deeper with Convolutions. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 1–9, 2015.
- [76] Jia Deng, Wei Dong, Richard Socher, Li-Jia Li, Kai Li, and Li Fei-Fei. ImageNet: A Large-scale Hierarchical Image Database. In 2009 IEEE Conference on Computer Vision and Pattern Recognition, pages 248–255. Ieee, 2009.
- [77] Tom Huddleston Jr. These Chinese hackers tricked Tesla’s Autopilot into suddenly switching lanes. https://www.cnbc.com/2019/04/03/chinese-hackers-tricked-teslas-autopilot-into-switching-lanes.html, Apr 2019.
- [78] Marco Barreno, Blaine Nelson, Anthony Joseph, and J. Tygar. The security of machine learning. Machine Learning, 81:121–148, 11 2010.
- [79] Joseph Gardiner and Shishir Nagaraja. On the Security of Machine Learning in Malware c&c Detection: A Survey. ACM Computing Surveys (CSUR), 49(3):1–39, 2016.
- [80] Atul Kumar and Sameep Mehta. A survey on resilient machine learning. arXiv preprint arXiv:1707.03184, 2017.
- [81] Xiaoyong Yuan, Pan He, Qile Zhu, and Xiaolin Li. Adversarial examples: Attacks and defenses for deep learning. IEEE transactions on neural networks and learning systems, 2019.
- [82] Anirban Chakraborty, Manaar Alam, Vishal Dey, Anupam Chattopadhyay, and Debdeep Mukhopadhyay. Adversarial attacks and defences: A survey. arXiv preprint arXiv:1810.00069, 2018.
- [83] Naveed Akhtar and Ajmal Mian. Threat of adversarial attacks on deep learning in computer vision: A survey. IEEE Access, 6:14410–14430, 2018.
- [84] Vasisht Duddu. A Survey of Adversarial Machine Learning in Cyber Warfare. Defence Science Journal, 68:356–366, 2018.
- [85] Guofu Li, Pengjia Zhu, Jin Li, Zhemin Yang, Ning Cao, and Zhiyi Chen. Security matters: A survey on adversarial machine learning. arXiv preprint arXiv:1810.07339, 2018.
- [86] Qiang Liu, Pan Li, Wentao Zhao, Wei Cai, Shui Yu, and Victor C. M. Leung. A Survey on Security Threats and Defensive Techniques of Machine Learning: A Data Driven View. IEEE Access, 6:12103–12117, 2018.
- [87] Battista Biggio and Fabio Roli. Wild Patterns: Ten Years After the Rise of Adversarial Machine Learning. Pattern Recognition, 84:317–331, Dec 2018.
- [88] Lu Sun, Mingtian Tan, and Zhe Zhou. A survey of practical adversarial example attacks. Cybersecurity, 1(1):1–9, 2018.
- [89] Nikolaos Pitropakis, Emmanouil A. Panaousis, Thanassis Giannetsos, Eleftherios Anastasiadis, and George Loukas. A taxonomy and survey of attacks against machine learning. Comput. Sci. Rev., 34, 2019.
- [90] Xianmin Wang, Jing Li, Xiaohui Kuang, Yu an Tan, and Jin Li. The security of machine learning in an adversarial setting: A survey. J. Parallel Distributed Comput., 130:12–23, 2019.
- [91] Shilin Qiu, Qihe Liu, Shijie Zhou, and Chunjiang Wu. Review of Artificial Intelligence Adversarial Attack and Defense Technologies. Applied Sciences, 2019.
- [92] Han Xu, Yao Ma, Hao-Chen Liu, Debayan Deb, Hui Liu, Ji-Liang Tang, and Anil K Jain. Adversarial attacks and defenses in images, graphs and text: A review. International Journal of Automation and Computing, 17(2):151–178, 2020.
- [93] Wei Emma Zhang, Quan Z Sheng, Ahoud Alhazmi, and Chenliang Li. Adversarial attacks on deep-learning models in natural language processing: A survey. ACM Transactions on Intelligent Systems and Technology (TIST), 11(3):1–41, 2020.
- [94] N. Martins, J. M. Cruz, T. Cruz, and P. Henriques Abreu. Adversarial Machine Learning Applied to Intrusion and Malware Scenarios: A Systematic Review. IEEE Access, 2020.
- [95] Ilja Moisejevs. Adversarial Attacks and Defenses in Malware Classification: A Survey. 2019.
- [96] Olakunle Ibitoye, Rana Abou-Khamis, Ashraf Matrawy, and M Omair Shafiq. The Threat of Adversarial Attacks on Machine Learning in Network Security–A Survey. arXiv preprint arXiv:1911.02621, 2019.
- [97] Hyrum S Anderson, Anant Kharkar, Bobby Filar, and Phil Roth. Evading Machine Learning Malware Detection. Black Hat, pages 1–6, 2017.
- [98] Bojan Kolosnjaji, Ambra Demontis, Battista Biggio, Davide Maiorca, Giorgio Giacinto, Claudia Eckert, and Fabio Roli. Adversarial Malware Binaries: Evading Deep Learning for Malware Detection in Executables. In 2018 26th European SIgnal Processing COnference (EUSIPCO), pages 533–537. IEEE, 2018.
- [99] Luca Demetrio, Battista Biggio, Giovanni Lagorio, Fabio Roli, and Alessandro Armando. Explaining Vulnerabilities of Deep Learning to Adversarial Malware Binaries. arXiv preprint arXiv:1901.03583, 2019.
- [100] Octavian Suciu, Scott E Coull, and Jeffrey Johns. Exploring Adversarial Examples in Malware Detection. In 2019 IEEE Security and Privacy Workshops (SPW), pages 8–14. IEEE, 2019.
- [101] Deqiang Li, Qianmu Li, Yanfang Ye, and Shouhuai Xu. Sok: Arms Race in Adversarial Malware Detection. arXiv preprint arXiv:2005.11671, 2020.
- [102] Judith S Hurwitz, Alan Nugent, Fern Halper, and Marcia Kaufman. Big Data for Dummies. John Wiley & Sons, 2013.
- [103] Seref Sagiroglu and Duygu Sinanc. Big Data: A Review. In IEEE International Conference on Collaboration Technologies and Systems (CTS), pages 42–47, 2013.
- [104] Gerard George, Martine R Haas, and Alex Pentland. Big Data and Management. Academy of Management Journal, 57(2):321–326, 2014.
- [105] Maanak Gupta, Farhan Patwa, and Ravi Sandhu. Object-tagged RBAC model for the Hadoop ecosystem. In IFIP Annual Conference on Data and Applications Security and Privacy. Springer, 2017.
- [106] Maanak Gupta, Farhan Patwa, James Benson, and Ravi Sandhu. Multi-layer authorization framework for a representative Hadoop ecosystem deployment. In Proceedings of the ACM on Symposium on Access Control Models and Technologies, 2017.
- [107] Maanak Gupta, Farhan Patwa, and Ravi Sandhu. An attribute-based access control model for secure big data processing in Hadoop ecosystem. In Proceedings of the Third ACM Workshop on Attribute-Based Access Control, 2018.
- [108] J Bulao. How Much Data Is Created Every Day in 2021?[You’ll be shocked!]. TechJury.[Online]. Available at https://techjury. net/blog/how-much-data-is-createdevery-day/.[Accessed: 20-Mar-2021], 2021.
- [109] Volume of data/information created, captured, copied, and consumed worldwide from 2010 to 2025. https://www.statista.com/statistics/871513/worldwide-data-created/.
- [110] Sean Fleming. This is how many websites exist globally. https://www.weforum.org/agenda/2019/09/chart-of-the-day-how-many-websites-are-there/, 2019.
- [111] Kit Smith. 60 Incredible and Interesting Twitter Stats and Statistics. https://www.brandwatch.com/blog/twitter-stats-and-statistics/, 2020.
- [112] Thomas M. Mitchell. Machine Learning. McGraw-Hill, Inc., USA, 1 edition, 1997.
- [113] Pat Langley. Elements of Machine Learning. Morgan Kaufmann, 1996.
- [114] Sotiris B Kotsiantis, I Zaharakis, P Pintelas, et al. Supervised Machine Learning: A Review of Classification Techniques. Emerging Artificial Intelligence Applications in Computer Engineering, 160(1):3–24, 2007.
- [115] Raphael Bost, Raluca Ada Popa, Stephen Tu, and Shafi Goldwasser. Machine Learning Classification over Encrypted Data. Cryptology ePrint Archive, 2014.
- [116] Marco Pennacchiotti and Ana-Maria Popescu. A machine learning approach to Twitter user classification. In Fifth International AAAI Conference on Weblogs and Social Media, 2011.
- [117] Shen Rong and Zhang Bao-wen. The research of regression model in machine learning field. In MATEC Web of Conferences, volume 176, page 01033. EDP Sciences, 2018.
- [118] Andrii Babii, Eric Ghysels, and Jonas Striaukas. Machine Learning Time Series Regressions With an Application to Nowcasting. Journal of Business & Economic Statistics, pages 1–23, 2021.
- [119] Ewout W Steyerberg, Tjeerd van der Ploeg, and Ben Van Calster. Risk prediction with machine learning and regression methods. Biometrical Journal, 56(4):601–606, 2014.
- [120] Anthony McGregor, Mark Hall, Perry Lorier, and James Brunskill. Flow Clustering Using Machine Learning Techniques. In International Workshop on Passive and Active Network Measurement, pages 205–214. Springer, 2004.
- [121] LV Bijuraj. Clustering and its Applications. In Proceedings of National Conference on New Horizons in IT-NCNHIT, volume 1, pages 169–172, 2013.
- [122] DT Pham and AA Afify. Clustering techniques and their applications in engineering. Proceedings of the Institution of Mechanical Engineers, Part C: Journal of Mechanical Engineering Science, 221(11):1445–1459, 2007.
- [123] G Thippa Reddy, M Praveen Kumar Reddy, Kuruva Lakshmanna, Rajesh Kaluri, Dharmendra Singh Rajput, Gautam Srivastava, and Thar Baker. Analysis of Dimensionality Reduction Techniques on Big data. IEEE Access, 8:54776–54788, 2020.
- [124] Dunja Mladenić. Feature Selection for Dimensionality Reduction. In International Statistical and Optimization Perspectives Workshop” Subspace, Latent Structure and Feature Selection”. Springer, 2005.
- [125] Matthew Richardson, Amit Prakash, and Eric Brill. Beyond PageRank: Machine Learning for Static Ranking. In Proceedings of the International Conference on World Wide Web, 2006.
- [126] David Cossock and Tong Zhang. Subset Ranking Using Regression. In International Conference on Computational Learning Theory, pages 605–619. Springer, 2006.
- [127] Shivani Agarwal, Deepak Dugar, and Shiladitya Sengupta. Ranking Chemical Structures for Drug Discovery: A New Machine Learning Approach. Journal of Chemical Information and Modeling, 50(5):716–731, 2010.
- [128] Shai Shalev-Shwartz and Shai Ben-David. Understanding Machine Learning: From Theory to Algorithms. Cambridge University Press, 2014.
- [129] Trevor Hastie, Robert Tibshirani, and Jerome Friedman. Overview of Supervised Learning. In The Elements of Statistical Learning, pages 9–41. Springer, 2009.
- [130] Michael Schuster. On supervised learning from sequential data with applications for speech recognition. Nara Institute of Science and Technology (PhD dissertation), 1999.
- [131] Horace B Barlow. Unsupervised Learning. Neural computation, 1(3):295–311, 1989.
- [132] Trevor Hastie, Robert Tibshirani, and Jerome Friedman. Unsupervised Learning. In The Elements of Statistical Learning, pages 485–585. Springer, 2009.
- [133] Xiaojin Zhu and Andrew B Goldberg. Introduction to Semi-Supervised Learning. Synthesis Lectures on Artificial Intelligence and Machine Learning, 3(1):1–130, 2009.
- [134] Diederik P Kingma, Shakir Mohamed, Danilo Jimenez Rezende, and Max Welling. Semi-Supervised Learning with Deep Generative Models. In Advances in Neural Information Processing Systems, pages 3581–3589, 2014.
- [135] Marco A Wiering and Martijn Van Otterlo. Reinforcement Learning. Adaptation, Learning, and Optimization, 12(3), 2012.
- [136] Volodymyr Mnih, Koray Kavukcuoglu, David Silver, Alex Graves, Ioannis Antonoglou, Daan Wierstra, and Martin Riedmiller. Playing Atari with Deep Reinforcement Learning. arXiv preprint arXiv:1312.5602, 2013.
- [137] Clement Farabet, Camille Couprie, Laurent Najman, and Yann LeCun. Learning Hierarchical Features for Scene Labeling. IEEE Transactions on Pattern Analysis and Machine Intelligence, 35(8):1915–1929, 2012.
- [138] Kaiming He, Xiangyu Zhang, Shaoqing Ren, and Jian Sun. Deep Residual Learning for Image Recognition. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 770–778, 2016.
- [139] Charles R Qi, Hao Su, Kaichun Mo, and Leonidas J Guibas. PointNet: Deep Learning on Point Sets for 3D Classification and Segmentation. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 652–660, 2017.
- [140] Li Deng, Geoffrey Hinton, and Brian Kingsbury. New Types of Deep Neural Network Learning for Speech Recognition and Related Applications: An Overview. In IEEE International Conference on Acoustics, Speech and Signal Processing, pages 8599–8603, 2013.
- [141] Dario Amodei, Sundaram Ananthanarayanan, Rishita Anubhai, Jingliang Bai, Eric Battenberg, Carl Case, Jared Casper, Bryan Catanzaro, Qiang Cheng, Guoliang Chen, et al. Deep Speech 2: End-to-End Speech Recognition in English and Mandarin. In International Conference on Machine Learning, pages 173–182. PMLR, 2016.
- [142] Awni Hannun, Carl Case, Jared Casper, Bryan Catanzaro, Greg Diamos, Erich Elsen, Ryan Prenger, Sanjeev Satheesh, Shubho Sengupta, Adam Coates, et al. Deep Speech: Scaling up end-to-end speech recognition. arXiv preprint arXiv:1412.5567, 2014.
- [143] Adam H Marblestone, Greg Wayne, and Konrad P Kording. Toward an Integration of Deep Learning and Neuroscience. Frontiers in Computational Neuroscience, 10:94, 2016.
- [144] Zhenlong Yuan, Yongqiang Lu, Zhaoguo Wang, and Yibo Xue. Droid-Sec: Deep Learning in Android Malware Detection. In Proceedings of the 2014 ACM Conference on SIGCOMM, pages 371–372, 2014.
- [145] Zhenlong Yuan, Yongqiang Lu, and Yibo Xue. DroidDetector: Android Malware Characterization and Detection Using Deep Learning. Tsinghua Science and Technology, 21(1):114–123, 2016.
- [146] Yann LeCun, Yoshua Bengio, and Geoffrey Hinton. Deep Learning. Nature, 521(7553):436–444, 2015.
- [147] Jiuxiang Gu, Zhenhua Wang, Jason Kuen, Lianyang Ma, Amir Shahroudy, Bing Shuai, Ting Liu, Xingxing Wang, Gang Wang, Jianfei Cai, et al. Recent Advances in Convolutional Neural Networks. Pattern Recognition, 77:354–377, 2018.
- [148] Yann LeCun, Bernhard Boser, John Denker, Donnie Henderson, Richard Howard, Wayne Hubbard, and Lawrence Jackel. Handwritten Digit Recognition with a Back-Propagation Network. Advances in Neural Information Processing Systems, 2, 1989.
- [149] Yann LeCun, Léon Bottou, Yoshua Bengio, and Patrick Haffner. Gradient-Based Learning Applied to Document Recognition. Proceedings of the IEEE, 86(11):2278–2324, 1998.
- [150] Alex Krizhevsky, Ilya Sutskever, and Geoffrey E Hinton. ImageNet Classification with Deep Convolutional Neural Networks. Advances in Neural Information Processing Systems, 25:1097–1105, 2012.
- [151] Karen Simonyan and Andrew Zisserman. Very Deep Convolutional Networks for Large-Scale Image Recognition. arXiv preprint arXiv:1409.1556, 2014.
- [152] Christian Szegedy, Sergey Ioffe, Vincent Vanhoucke, and Alexander A Alemi. Inception-v4, Inception-ResNet and the Impact of Residual Connections on Learning. In Thirty-first AAAI Conference on Artificial Intelligence, 2017.
- [153] Saining Xie, Ross Girshick, Piotr Dollár, Zhuowen Tu, and Kaiming He. Aggregated Residual Transformations for Deep Neural Networks. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 1492–1500, 2017.
- [154] Gao Huang, Zhuang Liu, Laurens Van Der Maaten, and Kilian Q Weinberger. Densely Connected Convolutional Networks. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 4700–4708, 2017.
- [155] Csaba Szepesvári. Algorithms for Reinforcement Learning. Synthesis Lectures on Artificial Intelligence and Machine Learning, 4(1):1–103, 2010.
- [156] Andrew Y Ng, Adam Coates, Mark Diel, Varun Ganapathi, Jamie Schulte, Ben Tse, Eric Berger, and Eric Liang. Autonomous Inverted Helicopter Flight via Reinforcement Learning. In Experimental Robotics IX, pages 363–372. Springer, 2006.
- [157] Nate Kohl and Peter Stone. Policy Gradient Reinforcement Learning for Fast Quadrupedal Locomotion. In IEEE International Conference on Robotics and Automation, volume 3, pages 2619–2624, 2004.
- [158] S. Singh, D. Litman, M. Kearns, and M. Walker. Optimizing Dialogue Management with Reinforcement Learning: Experiments with the NJFun System. Journal of Artificial Intelligence Research, 16:105–133, Feb 2002.
- [159] Shixiang Gu, Ethan Holly, Timothy Lillicrap, and Sergey Levine. Deep Reinforcement Learning for Robotic Manipulation with Asynchronous Off-Policy Updates. In IEEE International Conference on Robotics and Automation, pages 3389–3396. IEEE, 2017.
- [160] Timothy P Lillicrap, Jonathan J Hunt, Alexander Pritzel, Nicolas Heess, Tom Erez, Yuval Tassa, David Silver, and Daan Wierstra. Continuous Control with Deep Reinforcement Learning. arXiv preprint arXiv:1509.02971, 2015.
- [161] Lei Tai, Giuseppe Paolo, and Ming Liu. Virtual-to-real Deep Reinforcement Learning: Continuous Control of Mobile Robots for Mapless Navigation. In 2017 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), pages 31–36. IEEE, 2017.
- [162] Mel Vecerik, Todd Hester, Jonathan Scholz, Fumin Wang, Olivier Pietquin, Bilal Piot, Nicolas Heess, Thomas Rothörl, Thomas Lampe, and Martin Riedmiller. Leveraging Demonstrations for Deep Reinforcement Learning on Robotics Problems with Sparse Rewards. arXiv preprint arXiv:1707.08817, 2017.
- [163] Guillaume Lample and Devendra Singh Chaplot. Playing FPS Games with Deep Reinforcement Learning. In Thirty-First AAAI Conference on Artificial Intelligence, 2017.
- [164] Volodymyr Mnih, Koray Kavukcuoglu, David Silver, Andrei A Rusu, Joel Veness, Marc G Bellemare, Alex Graves, Martin Riedmiller, Andreas K Fidjeland, Georg Ostrovski, et al. Human-level control through Deep Reinforcement Learning. Nature, 518(7540):529–533, 2015.
- [165] Johannes Heinrich and David Silver. Deep Reinforcement Learning from Self-Play in Imperfect-Information Games. arXiv preprint arXiv:1603.01121, 2016.
- [166] Zachary C Lipton, John Berkowitz, and Charles Elkan. A Critical Review of Recurrent Neural Networks for Sequence Learning. arXiv preprint arXiv:1506.00019, 2015.
- [167] Haşim Sak, Andrew Senior, and Françoise Beaufays. Long Short-Term Memory Based Recurrent Neural Network Architectures for Large Vocabulary Speech Recognition. arXiv preprint arXiv:1402.1128, 2014.
- [168] David E Rumelhart, Geoffrey E Hinton, and Ronald J Williams. Learning Representations by Back-Propagating Errors. Nature, 323(6088):533–536, 1986.
- [169] Sepp Hochreiter and Jürgen Schmidhuber. Long Short-Term Memory. Neural Computation, 9(8):1735–1780, 1997.
- [170] Stefan Kombrink, Tomáš Mikolov, Martin Karafiát, and Lukáš Burget. Recurrent Neural Network Based Language Modeling in Meeting Recognition. In Twelfth Annual Conference of the International Speech Communication Association, 2011.
- [171] Jen-Tzung Chien and Yuan-Chu Ku. Bayesian Recurrent Neural Network for Language Modeling. IEEE Transactions on Neural Networks and Learning Systems, 27(2):361–374, 2015.
- [172] Martin Sundermeyer, Ralf Schlüter, and Hermann Ney. LSTM Neural Networks for Language Modeling. In Annual Conference of the International Speech Communication Association, 2012.
- [173] D Pawade, A Sakhapara, Mansi Jain, Neha Jain, and Krushi Gada. Story Scrambler-Automatic Text Generation Using Word Level RNN-LSTM. International Journal of Information Technology and Computer Science (IJITCS), 10(6):44–53, 2018.
- [174] Sidi Lu, Yaoming Zhu, Weinan Zhang, Jun Wang, and Yong Yu. Neural Text Generation: Past, Present and Beyond. arXiv preprint arXiv:1803.07133, 2018.
- [175] Lei Sha, Lili Mou, Tianyu Liu, Pascal Poupart, Sujian Li, Baobao Chang, and Zhifang Sui. Order-Planning Neural Text Generation From Structured Data. In Thirty-Second AAAI Conference on Artificial Intelligence, 2018.
- [176] Yajie Miao, Mohammad Gowayyed, and Florian Metze. EESEN: End-to-end speech recognition using deep RNN models and WFST-based decoding. In IEEE Workshop on Automatic Speech Recognition and Understanding, pages 167–174, 2015.
- [177] Alex Graves, Abdel-rahman Mohamed, and Geoffrey Hinton. Speech Recognition With Deep Recurrent Neural Networks. In 2013 IEEE International Conference on Acoustics, Speech and Signal Processing, pages 6645–6649. IEEE, 2013.
- [178] Jinyu Li, Rui Zhao, Hu Hu, and Yifan Gong. Improving RNN Transducer Modeling for End-to-End Speech Recognition. In 2019 IEEE Automatic Speech Recognition and Understanding Workshop (ASRU), pages 114–121. IEEE, 2019.
- [179] Ramesh Nallapati, Bing Xiang, and Bowen Zhou. Sequence-to-sequence RNNs for text summarization. CoRR abs/1602.06023 (2016). preprint arXiv:1602.06023, 2016.
- [180] Shuming Ma, Xu Sun, Jingjing Xu, Houfeng Wang, Wenjie Li, and Qi Su. Improving Semantic Relevance for Sequence-to-Sequence Learning of Chinese Social Media Text Summarization. arXiv preprint arXiv:1706.02459, 2017.
- [181] Ramesh Nallapati, Bowen Zhou, Caglar Gulcehre, Bing Xiang, et al. Abstractive Text Summarization Using Sequence-to-Sequence RNNs and Beyond. preprint arXiv:1602.06023, 2016.
- [182] Ian Goodfellow, Jean Pouget-Abadie, Mehdi Mirza, Bing Xu, David Warde-Farley, Sherjil Ozair, Aaron Courville, and Yoshua Bengio. Generative Adversarial Nets. Advances in Neural Information Processing Systems, 27, 2014.
- [183] Antonia Creswell, Tom White, Vincent Dumoulin, Kai Arulkumaran, Biswa Sengupta, and Anil A Bharath. Generative adversarial networks: An overview. IEEE Signal Processing Magazine, 35(1):53–65, 2018.
- [184] Takeru Miyato, Toshiki Kataoka, Masanori Koyama, and Yuichi Yoshida. Spectral Normalization for Generative Adversarial Networks. arXiv preprint arXiv:1802.05957, 2018.
- [185] Alec Radford, Luke Metz, and Soumith Chintala. Unsupervised Representation Learning With Deep Convolutional Generative Adversarial Networks. arXiv preprint arXiv:1511.06434, 2015.
- [186] Tim Salimans, Ian Goodfellow, Wojciech Zaremba, Vicki Cheung, Alec Radford, and Xi Chen. Improved Techniques for Training GANs. Advances in Neural Information Processing Systems, 29:2234–2242, 2016.
- [187] Adrian Bulat, Jing Yang, and Georgios Tzimiropoulos. To Learn Image Super-Resolution, Use a GAN To Learn How To Do Image Degradation First. In Proceedings of the European Conference on Computer Vision (ECCV), pages 185–200, 2018.
- [188] Pourya Shamsolmoali, Masoumeh Zareapoor, Ruili Wang, Deepak Kumar Jain, and Jie Yang. G-GANISR: Gradual Generative Adversarial Network for Image Super Resolution. Neurocomputing, 366:140–153, 2019.
- [189] Weixiang Hong, Zhenzhen Wang, Ming Yang, and Junsong Yuan. Conditional Generative Adversarial Network for Structured Domain Adaptation. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 1335–1344, 2018.
- [190] Edgar Simo-Serra, Satoshi Iizuka, and Hiroshi Ishikawa. Mastering Sketching: Adversarial Augmentation for Structured Prediction. ACM Transactions on Graphics (TOG), 37(1):1–13, 2018.
- [191] Junbo Zhao, Michael Mathieu, and Yann LeCun. Energy-Based Generative Adversarial Network. arXiv preprint arXiv:1609.03126, 2016.
- [192] Chelsea Finn, Paul Christiano, Pieter Abbeel, and Sergey Levine. A Connection Between Generative Adversarial Networks, Inverse Reinforcement Learning, and Energy-Based Models. arXiv preprint arXiv:1611.03852, 2016.
- [193] Nicolas Papernot, Patrick McDaniel, Ian Goodfellow, Somesh Jha, Z Berkay Celik, and Ananthram Swami. Practical Black-Box Attacks Against Machine Learning. In ACM Asia Conference on Computer and Communications Security, pages 506–519, 2017.
- [194] Yuanzhang Li, Yaxiao Wang, Ye Wang, Lishan Ke, and Yu-an Tan. A Feature-Vector Generative Adversarial Network for Evading PDF Malware Classifiers. Information Sciences, 523:38–48, 2020.
- [195] Jin-Young Kim, Seok-Jun Bu, and Sung-Bae Cho. Malware Detection using Deep Transferred Generative Adversarial Networks. In International Conference on Neural Information Processing, pages 556–564. Springer, 2017.
- [196] Kevin J Liang, Chunyuan Li, Guoyin Wang, and Lawrence Carin. Generative Adversarial Network Training is a Continual Learning Problem. arXiv preprint arXiv:1811.11083, 2018.
- [197] Martin Arjovsky and Léon Bottou. Towards Principled Methods for Training Generative Adversarial Networks. arXiv preprint arXiv:1701.04862, 2017.
- [198] Zhaoqing Pan, Weijie Yu, Xiaokai Yi, Asifullah Khan, Feng Yuan, and Yuhui Zheng. Recent Progress on Generative Adversarial Networks (GANs): A Survey. IEEE Access, 7:36322–36333, 2019.
- [199] Animesh Karnewar, Oliver Wang, and Raghu Sesha Iyengar. MSG-GAN: Multi-Scale Gradient GAN for Stable Image Synthesis. ArXiv, abs/1903.06048, 2019.
- [200] Kexugit. Inside Windows: Win32 Portable Executable File Format in Detail. https://docs.microsoft.com/en-us/archive/msdn-magazine/2002/february/inside-windows-win32-portable-executable-file-format-in-detail.
- [201] Portable Executable File Format. https://blog.kowalczyk.info/articles/pefileformat.html.
- [202] https://ivanlef0u.fr/repo/madchat/vxdevl/papers/winsys/pefile/pefile.html.
- [203] Karl-Bridge-Microsoft. PE Format - Win32 apps. https://docs.microsoft.com/en-us/windows/win32/debug/pe-format.
- [204] Heng Li, ShiYao Zhou, Wei Yuan, Jiahuan Li, and Henry Leung. Adversarial-Example Attacks Toward Android Malware Detection System. IEEE Systems Journal, 14(1):653–656, 2019.
- [205] Ishai Rosenberg, Asaf Shabtai, Lior Rokach, and Yuval Elovici. Generic Black-Box End-to-End Attack Against State of the Art API Call Based Malware Classifiers. In International Symposium on Research in Attacks, Intrusions, and Defenses, pages 490–510. Springer, 2018.
- [206] Maryam Shahpasand, Len Hamey, Dinusha Vatsalan, and Minhui Xue. Adversarial Attacks on Mobile Malware Detection. In 2019 IEEE 1st International Workshop on Artificial Intelligence for Mobile (AI4Mobile), pages 17–20. IEEE, 2019.
- [207] Fabio Pierazzi, Feargus Pendlebury, Jacopo Cortellazzi, and Lorenzo Cavallaro. Intriguing Properties of Adversarial ML Attacks in the Problem Space. In 2020 IEEE Symposium on Security and Privacy (SP), pages 1332–1349. IEEE, 2020.
- [208] App Manifest Overview : Android Developers. https://developer.android.com/guide/topics/manifest/manifest-intro.
- [209] Ajin Asokan. APK File Contents - In-Depth Explanation. https://ajinasokan.com/posts/apk-file-postmortem/, Sep 2016.
- [210] Wojtek Kaliciński. SmallerAPK, Part 1: Anatomy of an APK. https://medium.com/androiddevelopers/smallerapk-part-1-anatomy-of-an-apk-da83c25e7003, May 2016.
- [211] PDF File Structure - Four Main Parts: The Header, Body, Cross-Reference Table and Trailer. http://www.simpopdf.com/resource/pdf-file-structure.html.
- [212] Cybercrimemag. Cybercrime To Cost The World 10.5 Trillion Annually By 2025. https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/#:~:text=A2017reportfromCybersecurity,figureroseto\$11.5billion., Apr 2021.
- [213] Alireza Souri and Rahil Hosseini. A state-of-the-art survey of malware detection approaches using data mining techniques. Human-centric Computing and Information Sciences, 8(1):1–22, 2018.
- [214] Hao Sun, Xiaofeng Wang, Rajkumar Buyya, and Jinshu Su. CloudEyes: Cloud-based Malware Detection with Reversible Sketch for Resource-constrained Internet of Things (IoT) Devices. Software: Practice and Experience, 47(3):421–441, 2017.
- [215] Ping Wang and Yu-Shih Wang. Malware behavioural detection and vaccine development by using a support vector model classifier. Journal of Computer and System Sciences, 81(6), 2015.
- [216] James B Fraley and Marco Figueroa. Polymorphic Malware Detection Using Topological Feature Extraction with Data Mining. In SoutheastCon 2016, pages 1–7. IEEE, 2016.
- [217] Yong Tang, Bin Xiao, and Xicheng Lu. Signature Tree Generation for Polymorphic Worms. IEEE Transactions on Computers, 60(4):565–579, 2010.
- [218] J Zico Kolter and Marcus A Maloof. Learning to Detect and Classify Malicious Executables in the Wild. Journal of Machine Learning Research, 7(12), 2006.
- [219] Boyun Zhang, Jianping Yin, Jingbo Hao, Dingxing Zhang, and Shulin Wang. Malicious Codes Detection Based on Ensemble Learning. In International Conference on Autonomic and Trusted Computing, pages 468–477. Springer, 2007.
- [220] Daniel Bilar. Opcodes as Predictor for Malware. International Journal of Electronic Security and Digital Forensics, 1(2), 2007.
- [221] Weijie Han, Jingfeng Xue, Yong Wang, Lu Huang, Zixiao Kong, and Limin Mao. MalDAE: Detecting and Explaining Malware Based on Correlation and Fusion of Static and Dynamic Characteristics. Computers & Security, 83:208–233, 2019.
- [222] William Fleshman, Edward Raff, Richard Zak, Mark McLean, and Charles Nicholas. Static Malware Detection & Subterfuge: Quantifying the Robustness of Machine Learning and Current Anti-virus. In 2018 13th International Conference on Malicious and Unwanted Software (MALWARE), pages 1–10. IEEE, 2018.
- [223] Andreas Moser, Christopher Kruegel, and Engin Kirda. Limits of Static Analysis for Malware Detection. In Annual Computer Security Applications Conference, pages 421–430. IEEE, 2007.
- [224] Brad Miller, Alex Kantchelian, Michael Carl Tschantz, Sadia Afroz, Rekha Bachwani, Riyaz Faizullabhoy, Ling Huang, Vaishaal Shankar, Tony Wu, George Yiu, et al. Reviewer Integration and Performance Measurement for Malware Detection. In International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, pages 122–141. Springer, 2016.
- [225] Blake Anderson, Daniel Quist, Joshua Neil, Curtis Storlie, and Terran Lane. Graph-based Malware Detection Using Dynamic Analysis. Journal in Computer Virology, 7(4):247–258, 2011.
- [226] Wen-Chieh Wu and Shih-Hao Hung. DroidDolphin: a Dynamic Android Malware Detection Framework Using Big Data and Machine Learning. In Proceedings of the 2014 Conference on Research in Adaptive and Convergent Systems, pages 247–252, 2014.
- [227] Pengbin Feng, Jianfeng Ma, Cong Sun, Xinpeng Xu, and Yuwan Ma. A Novel Dynamic Android Malware Detection System With Ensemble Learning. IEEE Access, 6:30996–31011, 2018.
- [228] Carsten Willems, Thorsten Holz, and Felix Freiling. Toward Automated Dynamic Malware Analysis Using CWSandbox. IEEE Security & Privacy, 5(2):32–39, 2007.
- [229] Muhammad Ijaz, Muhammad Hanif Durad, and Maliha Ismail. Static and Dynamic Malware Analysis Using Machine Learning. In 2019 16th International Bhurban Conference on Applied Sciences and Technology (IBCAST), pages 687–691. IEEE, 2019.
- [230] Hengli Zhao, Ming Xu, Ning Zheng, Jingjing Yao, and Qiang Ho. Malicious Executables Classification Based on Behavioral Factor Analysis. In 2010 International Conference on e-Education, e-Business, e-Management and e-Learning, pages 502–506. IEEE, 2010.
- [231] Ronghua Tian, Rafiqul Islam, Lynn Batten, and Steve Versteeg. Differentiating Malware from Cleanware Using Behavioural Analysis. In 2010 5th International Conference on Malicious and Unwanted Software, pages 23–30. IEEE, 2010.
- [232] Martina Lindorfer, Clemens Kolbitsch, and Paolo Milani Comparetti. Detecting Environment-Sensitive Malware. In International Workshop on Recent Advances in Intrusion Detection, pages 338–357. Springer, 2011.
- [233] Zacharias Tzermias, Giorgos Sykiotakis, Michalis Polychronakis, and Evangelos P Markatos. Combining Static and Dynamic Analysis for the Detection of Malicious Documents. In Proceedings of the Fourth European Workshop on System Security, pages 1–6, 2011.
- [234] PV Shijo and AJPCS Salim. Integrated Static and Dynamic Analysis for Malware Detection. Procedia Computer Sci., 46, 2015.
- [235] Michael Spreitzenbarth, Thomas Schreck, Florian Echtler, Daniel Arp, and Johannes Hoffmann. Mobile-Sandbox: Combining Static and Dynamic Analysis with Machine-Learning Techniques. International Journal of Information Security, 14(2):141–153, 2015.
- [236] Sanjeev Das, Yang Liu, Wei Zhang, and Mahintham Chandramohan. Semantics-Based Online Malware Detection: Towards Efficient Real-Time Protection Against Malware. IEEE Transactions on Information Forensics and Security, 11(2):289–302, 2015.
- [237] Meltem Ozsoy, Caleb Donovick, Iakov Gorelik, Nael Abu-Ghazaleh, and Dmitry Ponomarev. Malware-Aware Processors: A Framework for Efficient Online Malware Detection. In 2015 IEEE 21st International Symposium on High Performance Computer Architecture (HPCA), pages 651–661. IEEE, 2015.
- [238] John Demme, Matthew Maycock, Jared Schmitz, Adrian Tang, Adam Waksman, Simha Sethumadhavan, and Salvatore Stolfo. On the Feasibility of Online Malware Detection with Performance Counters. ACM SIGARCH Computer Architecture News, 2013.
- [239] Mahmoud Abdelsalam, Ram Krishnan, and Ravi Sandhu. Online Malware Detection in Cloud Auto-scaling Systems Using Shallow Convolutional Neural Networks. In IFIP Annual Conference on Data and Applications Security and Privacy. Springer, 2019.
- [240] Weiwei Hu and Ying Tan. Black-Box Attacks against RNN based Malware Detection Algorithms. In Workshops at the Thirty-Second AAAI Conference on Artificial Intelligence, 2018.
- [241] BS Vivek, Konda Reddy Mopuri, and R Venkatesh Babu. Gray-box Adversarial Training. In Proceedings of the European Conference on Computer Vision (ECCV), pages 203–218, 2018.
- [242] Anirban Chakraborty, Manaar Alam, Vishal Dey, Anupam Chattopadhyay, and Debdeep Mukhopadhyay. Adversarial Attacks and Defences: A Survey. arXiv preprint arXiv:1810.00069, 2018.
- [243] Battista Biggio, Giorgio Fumera, and Fabio Roli. Security Evaluation of Pattern Classifiers under Attack. IEEE Transactions on Knowledge and Data Engineering, 26(4):984–996, Apr 2014.
- [244] Yizhen Wang and Kamalika Chaudhuri. Data Poisoning Attacks against Online Learning. arXiv preprint arXiv:1808.08994, 2018.
- [245] Xinyun Chen, Chang Liu, Bo Li, Kimberly Lu, and Dawn Song. Targeted Backdoor Attacks on Deep Learning Systems Using Data Poisoning. arXiv preprint arXiv:1712.05526, 2017.
- [246] Pang Wei Koh, Jacob Steinhardt, and Percy Liang. Stronger Data Poisoning Attacks Break Data Sanitization Defenses. arXiv preprint arXiv:1811.00741, 2018.
- [247] Weilin Xu, Yanjun Qi, and David Evans. Automatically Evading Classifiers: A Case Study on PDF Malware Classifiers. In Annual Network and Distributed System Security Symposium, 2016.
- [248] Junkun Yuan, Shaofang Zhou, Lanfen Lin, Feng Wang, and Jia Cui. Black-Box Adversarial Attacks Against Deep Learning Based Malware Binaries Detection with GAN. In ECAI 2020, pages 2536–2542. IOS Press, 2020.
- [249] Nuno Martins, José Magalhães Cruz, Tiago Cruz, and Pedro Henriques Abreu. Adversarial Machine Learning Applied to Intrusion and Malware Scenarios: A Systematic Review. IEEE Access, 8, 2020.
- [250] Ian Goodfellow, David Warde-Farley, Mehdi Mirza, Aaron Courville, and Yoshua Bengio. Maxout Networks. In International Conference on Machine Learning, pages 1319–1327. PMLR, 2013.
- [251] Nicolas Papernot, Patrick McDaniel, Somesh Jha, Matt Fredrikson, Z Berkay Celik, and Ananthram Swami. The Limitations of Deep Learning in Adversarial Settings. In IEEE European Symposium on Security and Privacy, pages 372–387, 2016.
- [252] Karen Simonyan, Andrea Vedaldi, and Andrew Zisserman. Deep Inside Convolutional Networks: Visualising Image Classification Models and Saliency Maps. arXiv preprint arXiv:1312.6034, 2013.
- [253] Jean M Steppe and Kenneth W Bauer Jr. Feature Saliency Measures. Computers & Mathematics with Applications, 33(8):109–126, 1997.
- [254] Bolei Zhou, Aditya Khosla, Agata Lapedriza, Aude Oliva, and Antonio Torralba. Learning Deep Features for Discriminative Localization. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 2921–2929, 2016.
- [255] Ramprasaath R. Selvaraju, Michael Cogswell, Abhishek Das, Ramakrishna Vedantam, Devi Parikh, and Dhruv Batra. Grad-CAM: Visual Explanations from Deep Networks via Gradient-Based Localization. International Journal of Computer Vision, 2019.
- [256] Nicholas Carlini and David Wagner. Towards Evaluating the Robustness of Neural Networks. In IEEE Symposium on Security and Privacy (SP), pages 39–57. IEEE, 2017.
- [257] Seyed-Mohsen Moosavi-Dezfooli, Alhussein Fawzi, and Pascal Frossard. DeepFool: A Simple and Accurate Method to Fool Deep Neural Networks. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 2574–2582, 2016.
- [258] Pin-Yu Chen, Huan Zhang, Yash Sharma, Jinfeng Yi, and Cho-Jui Hsieh. ZOO: Zeroth Order Optimization based Black-box Attacks to Deep Neural Networks without Training Substitute Models. In Proceedings of the 10th ACM Workshop on Artificial Intelligence and Security, pages 15–26, 2017.
- [259] Jiawei Su, Danilo Vasconcellos Vargas, and Kouichi Sakurai. One Pixel Attack for Fooling Deep Neural Networks. IEEE Transactions on Evolutionary Computation, 23(5):828–841, 2019.
- [260] Pinar Civicioglu and Erkan Besdok. A conceptual comparison of the Cuckoo-search, particle swarm optimization, differential evolution and artificial bee colony algorithms. Artificial Intelligence Review, 39(4):315–346, 2013.
- [261] Shanhong Liu. Desktop os market share. https://www.statista.com/statistics/218089/global-market-share-of-windows-7/, Jul 2021.
- [262] Gartner Inc. AI as a Target and Tool: An Attacker’s Perspective on ML. https://www.gartner.com/en/documents/3939991.
- [263] Edward Raff, Jon Barker, Jared Sylvester, Robert Brandon, Bryan Catanzaro, and Charles K Nicholas. Malware Detection by Eating a Whole EXE. In Workshops at the Thirty-Second AAAI Conference on Artificial Intelligence, 2018.
- [264] Xiang Zhang and Yann LeCun. Text Understanding from Scratch. arXiv preprint arXiv:1502.01710, 2015.
- [265] F. Kreuk, A. Barak, Shir Aviv-Reuven, Moran Baruch, Benny Pinkas, and Joseph Keshet. Adversarial Examples on Discrete Sequences for Beating Whole-Binary Malware Detection. ArXiv, abs/1802.04528, 2018.
- [266] Hyrum S Anderson and Phil Roth. Ember: An Open Dataset for Training Static PE Malware Machine Learning Models. arXiv preprint arXiv:1804.04637, 2018.
- [267] Bingcai Chen, Zhongru Ren, Chao Yu, Iftikhar Hussain, and Jintao Liu. Adversarial Examples for CNN-Based Malware Detectors. IEEE Access, 7:54360–54371, 2019.
- [268] Battista Biggio, Igino Corona, Davide Maiorca, Blaine Nelson, Nedim Šrndić, Pavel Laskov, Giorgio Giacinto, and Fabio Roli. Evasion Attacks against Machine Learning at Test Time. In Joint European Conference on Machine Learning and Knowledge Discovery in Databases, pages 387–402. Springer, 2013.
- [269] Felix Kreuk, Assi Barak, Shir Aviv-Reuven, Moran Baruch, Benny Pinkas, and Joseph Keshet. Deceiving End-to-End Deep Learning Malware Detectors using Adversarial Examples. arXiv preprint arXiv:1802.04528, 2018.
- [270] Mukund Sundararajan, Ankur Taly, and Qiqi Yan. Axiomatic Attribution for Deep Networks. In International Conference on Machine Learning, pages 3319–3328. PMLR, 2017.
- [271] Daniel Park, Haidar Khan, and Bülent Yener. Generation & Evaluation of Adversarial Examples for Malware Obfuscation. In 2019 18th IEEE International Conference On Machine Learning and Applications (ICMLA), pages 1283–1290. IEEE, 2019.
- [272] Christian Szegedy, Vincent Vanhoucke, Sergey Ioffe, Jon Shlens, and Zbigniew Wojna. Rethinking the Inception Architecture for Computer Vision. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 2818–2826, 2016.
- [273] Wei Song, Xuezixiang Li, Sadia Afroz, Deepali Garg, Dmitry Kuznetsov, and Heng Yin. Automatic Generation of Adversarial Examples for Interpreting Malware Classifiers. ArXiv, abs/2003.03100, 2020.
- [274] Pascal Junod, Julien Rinaldini, Johan Wehrli, and Julie Michielin. Obfuscator-LLVM–Software Protection for the Masses. In IEEE/ACM International Workshop on Software Protection, 2015.
- [275] Xiaozhu Meng and Barton P Miller. Binary Code is Not Easy. In Proceedings of the 25th International Symposium on Software Testing and Analysis, pages 24–35, 2016.
- [276] Christian Szegedy, Vincent Vanhoucke, Sergey Ioffe, Jon Shlens, and Zbigniew Wojna. Rethinking the Inception Architecture for Computer Vision. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 2818–2826, 2016.
- [277] Hyrum S Anderson, Anant Kharkar, Bobby Filar, David Evans, and Phil Roth. Learning to Evade Static PE Machine Learning Malware Models via Reinforcement Learning. arXiv preprint arXiv:1801.08917, 2018.
- [278] Zhiyang Fang, Junfeng Wang, Boya Li, Siqi Wu, Yingjie Zhou, and Haiying Huang. Evading Anti-Malware Engines With Deep Reinforcement Learning. IEEE Access, 7:48867–48879, 2019.
- [279] Jun Chen, Jingfei Jiang, Rongchun Li, and Yong Dou. Generating Adversarial Examples for Static PE Malware Detector Based on Deep Reinforcement Learning. In Journal of Physics: Conference Series, volume 1575, page 012011. IOP Publishing, 2020.
- [280] Yong Fang, Yuetian Zeng, Beibei Li, Liang Liu, and L. Zhang. DeepDetectNet vs RLAttackNet: An adversarial method to improve deep learning-based static malware detection model. PLoS ONE, 15, 2020.
- [281] DeepMind. https://deepmind.com.
- [282] Weiwei Hu and Ying Tan. Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN. ArXiv, abs/1702.05983, 2017.
- [283] Masataka Kawai, Kaoru Ota, and Mianxing Dong. Improved MalGAN: Avoiding Malware Detector by Leaning Cleanware Features. In IEEE International Conference on Artificial Intelligence in Information and Communication, pages 040–045, 2019.
- [284] Raphael Labaca Castro, Corinna Schmitt, and Gabi Dreo Rodosek. Poster: Training GANs to Generate Adversarial Examples Against Malware Classification. IEEE Secur. Priv, 2019.
- [285] Razvan Pascanu, Jack W. Stokes, Hermineh Sanossian, Mady Marinescu, and Anil Thomas. MALWARE CLASSIFICATION WITH RECURRENT NETWORKS. In 2015 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), pages 1916–1920, 2015.
- [286] Bojan Kolosnjaji, Apostolis Zarras, George Webster, and Claudia Eckert. Deep Learning for Classification of Malware System Call Sequences. In Australasian Joint Conference on Artificial Intelligence, pages 137–149. Springer, 2016.
- [287] Shun Tobiyama, Yukiko Yamaguchi, Hajime Shimada, Tomonori Ikuse, and Takeshi Yagi. Malware Detection with Deep Neural Network Using Process Behavior. In 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), volume 2, pages 577–582, 2016.
- [288] Nicolas Papernot, Patrick McDaniel, Ananthram Swami, and Richard Harang. Crafting Adversarial Input Sequences for Recurrent Neural Networks. In MILCOM 2016-2016 IEEE Military Communications Conference, pages 49–54. IEEE, 2016.
- [289] Eric Jang, Shixiang Gu, and Ben Poole. CATEGORICAL REPARAMETERIZATION WITH GUMBEL-SOFTMAX. arXiv preprint arXiv:1611.01144, 2016.
- [290] Ishai Rosenberg, Shai Meir, Jonathan Berrebi, Ilay Gordon, Guillaume Sicard, and Eli Omid David. Generating End-to-End Adversarial Examples for Malware Classifiers Using Explainability. In 2020 International Joint Conference on Neural Networks (IJCNN), pages 1–10. IEEE, 2020.
- [291] Xinbo Liu, Jiliang Zhang, Yaping Lin, and He Li. ATMPA: Attacking Machine Learning-based Malware Visualization Detection Methods via Adversarial Examples. In IEEE/ACM International Symposium on Quality of Service, pages 1–10, 2019.
- [292] Aminollah Khormali, Ahmed Abusnaina, Songqing Chen, DaeHun Nyang, and Aziz Mohaisen. COPYCAT: Practical Adversarial Attacks on Visualization-Based Malware Detection. arXiv preprint arXiv:1909.09735, 2019.
- [293] Hadjer Benkraouda, Jingyu Qian, Hung Quoc Tran, and Berkay Kaplan. Attacks on Visualization-Based Malware Detection: Balancing Effectiveness and Executability. In International Workshop on Deployable Machine Learning for Security Defense. Springer, 2021.
- [294] Mukund Sundararajan, Ankur Taly, and Qiqi Yan. Axiomatic Attribution for Deep Networks. In International Conference on Machine Learning, pages 3319–3328. PMLR, 2017.
- [295] Sebastian Bach, Alexander Binder, Grégoire Montavon, Frederick Klauschen, Klaus-Robert Müller, and Wojciech Samek. On Pixel-Wise Explanations for Non-Linear Classifier Decisions by Layer-Wise Relevance Propagation. PloS one, 10(7):e0130140, 2015.
- [296] Avanti Shrikumar, Peyton Greenside, and Anshul Kundaje. Learning Important Features Through Propagating Activation Differences. In International Conference on Machine Learning, pages 3145–3153. PMLR, 2017.
- [297] Scott M Lundberg and Su-In Lee. A Unified Approach to Interpreting Model Predictions. In International Conference on Neural Information Processing Systems, pages 4768–4777, 2017.
- [298] Kyoung Soo Han, Jae Hyun Lim, Boojoong Kang, and Eul Gyu Im. Malware analysis using visualized images and entropy graphs. Int. Journal of Information Security, 14(1):1–14, 2015.
- [299] Kesav Kancherla and Srinivas Mukkamala. Image Visualization based Malware Detection. In IEEE Symposium on Computational Intelligence in Cyber Security, pages 40–44, 2013.
- [300] Lakshmanan Nataraj, Sreejith Karthikeyan, Gregoire Jacob, and Bangalore S Manjunath. Malware Images: Visualization and Automatic Classification. In Proceedings of the 8th International Symposium on Visualization for Cyber Security, pages 1–7, 2011.
- [301] Yinpeng Dong, Fangzhou Liao, Tianyu Pang, Hang Su, Jun Zhu, Xiaolin Hu, and Jianguo Li. Boosting Adversarial Attacks with Momentum. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, pages 9185–9193, 2018.
- [302] Aleksander Madry, Aleksandar Makelov, Ludwig Schmidt, Dimitris Tsipras, and Adrian Vladu. Towards Deep Learning Models Resistant to Adversarial Attacks. preprint arXiv:1706.06083, 2017.
- [303] Sang Kil Cha, Brian Pak, David Brumley, and Richard Jay Lipton. Platform-Independent Programs. In Proceedings of the ACM Conference on Computer and Communications Security, 2010.
- [304] Kathrin Grosse, Nicolas Papernot, Praveen Manoharan, Michael Backes, and Patrick McDaniel. Adversarial Examples for Malware Detection. In European Symposium on Research in Computer Security, pages 62–79. Springer, 2017.
- [305] Wei Yang, Deguang Kong, Tao Xie, and Carl A Gunter. Malware detection in adversarial settings: Exploiting feature evolutions and confusions in android apps. In Proceedings of the 33rd Annual Computer Security Applications Conference, pages 288–302, 2017.
- [306] Xiaolei Liu, Xiaojiang Du, Xiaosong Zhang, Qingxin Zhu, Hao Wang, and Mohsen Guizani. Adversarial Samples on Android Malware Detection Systems for IoT Systems. Sensors, 2019.
- [307] Heng Li, ShiYao Zhou, Wei Yuan, Jiahuan Li, and Henry Leung. Adversarial-Example Attacks Toward Android Malware Detection System. IEEE Systems Journal, 14(1):653–656, 2019.
- [308] Hamid Bostani and Veelasha Moonsamy. EvadeDroid: A Practical Evasion Attack on Machine Learning for Black-box Android Malware Detection. arXiv preprint arXiv:2110.03301, 2021.
- [309] Dan Arp, Michael Spreitzenbarth, M. Hubner, Hugo Gascon, and K. Rieck. DREBIN: Effective and Explainable Detection of Android Malware in Your Pocket. In Proceedings of NDSS, 2014.
- [310] Ambra Demontis, Marco Melis, B. Biggio, Davide Maiorca, Dan Arp, K. Rieck, I. Corona, G. Giacinto, and F. Roli. Yes, Machine Learning Can Be More Secure! A Case Study on Android Malware Detection. IEEE Transactions on Dependable and Secure Computing, 16:711–724, 2019.
- [311] Enrico Mariconti, Lucky Onwuzurike, Panagiotis Andriotis, Emiliano De Cristofaro, Gordon Ross, and Gianluca Stringhini. Mamadroid: Detecting android malware by building markov chains of behavioral models. preprint arXiv:1612.04433, 2016.
- [312] Kevin Allix, Tegawendé F Bissyandé, Jacques Klein, and Yves Le Traon. Androzoo: Collecting Millions of Android Apps for the Research Community. In 2016 IEEE/ACM 13th Working Conference on Mining Software Repositories (MSR), pages 468–471. IEEE, 2016.
- [313] Android Statistics (2021). https://www.businessofapps.com/da-\\ta/android-statistics/, Jun 2021.
- [314] Kathrin Grosse, Nicolas Papernot, Praveen Manoharan, Michael Backes, and Patrick McDaniel. Adversarial Perturbations Against Deep Neural Networks for Malware Classification. arXiv preprint arXiv:1606.04435, 2016.
- [315] David Wagner and Paolo Soto. Mimicry Attacks on Host-Based Intrusion Detection Systems. In ACM Conference on Computer and Communications Security, pages 255–264, 2002.
- [316] Earl T Barr, Mark Harman, Yue Jia, Alexandru Marginean, and Justyna Petke. Automated Software Transplantation. In Proceedings of the 2015 International Symposium on Software Testing and Analysis, pages 257–269, 2015.
- [317] Carol J Bult. Bioinformatics: A Practical Guide to the Analysis of Genes and Proteins. Science, 282(5389):635–636, 1998.
- [318] Anshuman Singh, Andrew Walenstein, and Arun Lakhotia. Tracking Concept Drift in Malware Families. In ACM Workshop on Security and Artificial Intelligence, pages 81–92, 2012.
- [319] Davide Maiorca, Igino Corona, and Giorgio Giacinto. Looking at the Bag is Not Enough to Find the Bomb: An Evasion of Structural Methods for Malicious PDF Files Detection. In Proceedings of the 8th ACM SIGSAC Symposium on Information, Computer and Communications Security, pages 119–130, 2013.
- [320] Battista Biggio, Igino Corona, Davide Maiorca, Blaine Nelson, Nedim Šrndić, Pavel Laskov, Giorgio Giacinto, and Fabio Roli. Evasion Attacks against Machine Learning at Test Time. In Joint European Conference on Machine Learning and Knowledge Discovery in Databases, pages 387–402. Springer, 2013.
- [321] Battista Biggio, Igino Corona, Blaine Nelson, Benjamin IP Rubinstein, Davide Maiorca, Giorgio Fumera, Giorgio Giacinto, and Fabio Roli. Security Evaluation of Support Vector Machines in Adversarial Environments. In Support Vector Machines Applications, pages 105–153. Springer, 2014.
- [322] Pavel Laskov et al. Practical Evasion of a Learning-Based Classifier: A Case Study. In IEEE Symposium on Security and Privacy, pages 197–211. IEEE, 2014.
- [323] Curtis Carmony, Xunchao Hu, Heng Yin, Abhishek Vasisht Bhaskar, and Mu Zhang. Extract Me If You Can: Abusing PDF Parsers in Malware Detectors. In Proceedings of NDSS, 2016.
- [324] Permissions on Android : Android Developers. https://developer.android.com/guide/topics/permissions/.
- [325] Charles Smutz and Angelos Stavrou. Malicious PDF detection using metadata and structural features. In Proceedings of the Annual Computer Security Applications Conference, 2012.
- [326] Nedim Šrndic and Pavel Laskov. Detection of Malicious PDF Files Based on Hierarchical Document Structure. In Proceedings of the Annual Network & Distributed System Security Symposium, pages 1–16. Citeseer, 2013.
- [327] Pavel Laskov and Nedim Šrndić. Static Detection of Malicious JavaScript-Bearing PDF Documents. In Proceedings of the Annual Computer Security Applications Conference, pages 373–382, 2011.
- [328] Davide Maiorca, Giorgio Giacinto, and Igino Corona. A Pattern Recognition System for Malicious PDF Files Detection. In International Workshop on Machine Learning and Data Mining in Pattern Recognition, pages 510–524. Springer, 2012.
- [329] Jose Miguel Esparza. PEEPDF–PDF Analysis Tool, 2015.
- [330] Polina Golland. Discriminative Direction for Kernel Classifiers. Advances in Neural Information Processing Systems, 14, 2001.
- [331] Davide Maiorca, Battista Biggio, and Giorgio Giacinto. Towards Adversarial Malware Detection: Lessons Learned from PDF-based Attacks. ACM Computing Surveys (CSUR), 52(4):1–36, 2019.
- [332] Suman Jana and Vitaly Shmatikov. Abusing File Processing in Malware Detectors for Fun and Profit. In 2012 IEEE Symposium on Security and Privacy, pages 80–94. IEEE, 2012.
- [333] Pavel Laskov and Nedim Šrndić. Static Detection of Malicious JavaScript-Bearing PDF Documents. In Proceedings of the Annual Computer Security Applications Conference, pages 373–382, 2011.
- [334] Daiping Liu, Haining Wang, and Angelos Stavrou. Detecting Malicious Javascript in PDF through Document Instrumentation. In 2014 44th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, pages 100–111. IEEE, 2014.
- [335] Zacharias Tzermias, Giorgos Sykiotakis, Michalis Polychronakis, and Evangelos P Markatos. Combining Static and Dynamic Analysis for the Detection of Malicious Documents. In Proceedings of the Fourth European Workshop on System Security, pages 1–6, 2011.
- [336] Khaled N Khasawneh, Nael Abu-Ghazaleh, Dmitry Ponomarev, and Lei Yu. RHMD: Evasion-Resilient Hardware Malware Detectors. In Proceedings of the 50th Annual IEEE/ACM International Symposium on Microarchitecture, pages 315–327, 2017.
- [337] Sai Manoj Pudukotai Dinakarrao, Sairaj Amberkar, Sahil Bhat, Abhijitt Dhavlle, Hossein Sayadi, Avesta Sasan, Houman Homayoun, and Setareh Rafatirad. Adversarial Attack on Microarchitectural Events based Malware Detectors. In Proceedings of the Annual Design Automation Conference, pages 1–6, 2019.
- [338] Kohei Nozawa, Kento Hasegawa, Seira Hidano, Shinsaku Kiyomoto, Kazuo Hashimoto, and Nozomu Togawa. Generating Adversarial Examples for Hardware-Trojan Detection at Gate-Level Netlists. Journal of Information Processing, 29:236–246, 2021.
- [339] Yevgeniy Vorobeychik and Bo Li. Optimal Randomized Classification in Adversarial Settings. In Proceedings of the 2014 International Conference on Autonomous Agents and Multi-Agent Systems, pages 485–492, 2014.
- [340] Ke Wang, Janak J Parekh, and Salvatore J Stolfo. Anagram: A Content Anomaly Detector Resistant to Mimicry Attack. In International Workshop on Recent Advances in Intrusion Detection, pages 226–248. Springer, 2006.
- [341] Md Shohidul Islam, Khaled N Khasawneh, Nael Abu-Ghazaleh, Dmitry Ponomarev, and Lei Yu. Efficient Hardware Malware Detectors that are Resilient to Adversarial Evasion. IEEE Transactions on Computers, 2021.
- [342] Chi-Keung Luk, Robert Cohn, Robert Muth, Harish Patil, Artur Klauser, Geoff Lowney, Steven Wallace, Vijay Janapa Reddi, and Kim Hazelwood. Pin: Building Customized Program Analysis Tools with Dynamic Instrumentation. ACM SIGPLAN Notices, 40(6):190–200, 2005.
- [343] Nisarg Patel, Avesta Sasan, and Houman Homayoun. Analyzing hardware based malware detectors. In ACM/EDAC/IEEE Design Automation Conference (DAC), pages 1–6. IEEE, 2017.
- [344] Bao Liu and Gang Qu. VLSI Supply Chain Security Risks and Mitigation Techniques: A Survey. Integration, 55:438–448, 2016.
- [345] Masaru Oya, Youhua Shi, Masao Yanagisawa, and Nozomu Togawa. A Score-Based Classification Method for Identifying Hardware-Trojans at Gate-Level Netlists. In IEEE Design, Automation & Test in Europe Conference & Exhibition, 2015.
- [346] Kento Hasegawa, Masaru Oya, Masao Yanagisawa, and Nozomu Togawa. Hardware Trojans Classification for Gate-Level Netlists based on Machine Learning. In IEEE International Symposium on On-Line Testing and Robust System Design, pages 203–206, 2016.
- [347] Chen Dong, Guorong He, Ximeng Liu, Yang Yang, and Wenzhong Guo. A Multi-Layer Hardware Trojan Protection Framework for IoT Chips. IEEE Access, 7:23628–23639, 2019.
- [348] Tomotaka Inoue, Kento Hasegawa, Masao Yanagisawa, and Nozomu Togawa. Designing hardware trojans and their detection based on a SVM-based approach. In 2017 IEEE 12th International Conference on ASIC (ASICON), pages 811–814. IEEE, 2017.
- [349] Tomotaka Inoue, Kento Hasegawa, Yuki Kobayashi, Masao Yanagisawa, and Nozomu Togawa. Designing Subspecies of Hardware Trojans and Their Detection Using Neural Network Approach. In 2018 IEEE 8th International Conference on Consumer Electronics-Berlin (ICCE-Berlin), pages 1–4. IEEE, 2018.
- [350] Ahmed Abusnaina, Aminollah Khormali, Hisham Alasmary, Jeman Park, Afsah Anwar, and Aziz Mohaisen. Adversarial Learning Attacks on Graph-Based IoT Malware Detection Systems. In 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), pages 1296–1305. IEEE, 2019.
- [351] Yuan Gong, Boyang Li, Christian Poellabauer, and Yiyu Shi. Real-Time Adversarial Attacks. arXiv preprint arXiv:1905.13399, 2019.
- [352] Yi Xie, Cong Shi, Zhuohang Li, Jian Liu, Yingying Chen, and Bo Yuan. Real-time, Universal, and Robust Adversarial Attacks Against Speaker Recognition Systems. In IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), pages 1738–1742, 2020.
- [353] Izzat Alsmadi, Kashif Ahmad, Mahmoud Nazzal, Firoj Alam, Ala Al-Fuqaha, Abdallah Khreishah, and Abdulelah Algosaibi. Adversarial Attacks and Defenses for Social Network Text Processing Applications: Techniques, Challenges and Future Research Directions. arXiv preprint arXiv:2110.13980, 2021.
- [354] Bin Liang, Hongcheng Li, Miaoqiang Su, Pan Bian, Xirong Li, and Wenchang Shi. Deep Text Classification can be Fooled. arXiv preprint arXiv:1704.08006, 2017.
- [355] Honglin Li, Yifei Fan, Frieder Ganz, Anthony Yezzi, and Payam Barnaghi. Verifying the Causes of Adversarial Examples. In IEEE International Conference on Pattern Recognition, 2021.
- [356] Ali Shafahi, Mahyar Najibi, Amin Ghiasi, Zheng Xu, John Dickerson, Christoph Studer, Larry S Davis, Gavin Taylor, and Tom Goldstein. Adversarial Training for Free! arXiv preprint arXiv:1904.12843, 2019.
- [357] Nicolas Papernot and Patrick McDaniel. Extending Defensive Distillation. arXiv preprint arXiv:1705.05264, 2017.
- [358] Shilin Qiu, Qihe Liu, Shijie Zhou, and Chunjiang Wu. Review of Artificial Intelligence Adversarial Attack and Defense Technologies. Applied Sciences, 9(5):909, 2019.
- [359] Sainadh Jamalpur, Yamini Sai Navya, Perla Raja, Gampala Tagore, and G Rama Koteswara Rao. Dynamic Malware Analysis Using Cuckoo Sandbox. In IEEE International Conference on Inventive Communication and Computational Technologies, 2018.
- [360] Qiang Yang, Yang Liu, Yong Cheng, Yan Kang, Tianjian Chen, and Han Yu. Federated Learning. Synthesis Lectures on Artificial Intelligence and Machine Learning, 13(3):1–207, 2019.
- [361] Federated Learning: Collaborative Machine Learning without Centralized Training Data. https://ai.googleblog.com/2017/04/federated-learning-collaborative.html, Apr 2017.
- [362] Eugene Bagdasaryan, Andreas Veit, Yiqing Hua, Deborah Estrin, and Vitaly Shmatikov. How to Backdoor Federated Learning. In International Conference on Artificial Intelligence and Statistics, pages 2938–2948. PMLR, 2020.
- [363] Differentiable Neural Computers. https://deepmind.com/blog/article/differentiable-neural-computers.
- [364] Alvin Chan, Lei Ma, Felix Juefei-Xu, Xiaofei Xie, Yang Liu, and Yew Soon Ong. Metamorphic Relation Based Adversarial Attacks on Differentiable Neural Computer. arXiv preprint arXiv:1809.02444, 2018.
- [365] Paul Michel, Xian Li, Graham Neubig, and Juan Miguel Pino. On Evaluation of Adversarial Perturbations for Sequence-to-Sequence Models. arXiv preprint arXiv:1903.06620, 2019.
- [366] Nicolas Papernot, Patrick McDaniel, Xi Wu, Somesh Jha, and Ananthram Swami. Distillation as a Defense to Adversarial Perturbations against Deep Neural Networks. In IEEE Symposium on Security and Privacy (SP), pages 582–597, 2016.
- [367] Florian Tramèr, Alexey Kurakin, Nicolas Papernot, Dan Boneh, and Patrick McDaniel. Ensemble Adversarial Training: Attacks and Defenses. STAT, 1050:30, 2017.
- [368] Ali Shafahi, Mahyar Najibi, Zheng Xu, John Dickerson, Larry S Davis, and Tom Goldstein. Universal Adversarial Training. In Proceedings of the AAAI Conference on Artificial Intelligence, volume 34, pages 5636–5643, 2020.
- [369] Yunseok Jang, Tianchen Zhao, Seunghoon Hong, and Honglak Lee. Adversarial Defense via Learning to Generate Diverse Attacks. In Proceedings of the IEEE/CVF International Conference on Computer Vision, pages 2740–2749, 2019.
- [370] Fangzhou Liao, Ming Liang, Yinpeng Dong, Tianyu Pang, Xiaolin Hu, and Jun Zhu. Defense against Adversarial Attacks using High-Level Representation Guided Denoiser. In IEEE Conference on Computer Vision and Pattern Recognition, pages 1778–1787, 2018.
- [371] Dongyu Meng and Hao Chen. MagNet: a Two-Pronged Defense against Adversarial Examples. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, 2017.
- [372] Pouya Samangouei, Maya Kabkab, and Rama Chellappa. Defense-GAN: Protecting Classifiers against Adversarial Attacks using Generative Models. arXiv preprint arXiv:1805.06605, 2018.
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/aebc523c-2182-4763-b137-db1b661f0ad6/Kshitiz_photo.jpg) |
Kshitiz Aryal received the B.E. degree in Electronics and Communication Engineering from Paschimanchal Campus, Tribhuvan University, Nepal. He is currently pursuing the PhD degree with the Department of Computer Science, Tennessee Technological University, Cookeville, TN, USA. His current research interests include cybersecurity, adversarial attacks, machine learning, malware analysis, IoT, embedded system and data science. |
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/aebc523c-2182-4763-b137-db1b661f0ad6/Maanak_Gupta_journal.jpg) |
Maanak Gupta (Member, IEEE) is an Assistant Professor in Computer Science at Tennessee Technological University, Cookeville, USA. He received M.S. and Ph.D. in Computer Science from the University of Texas at San Antonio (UTSA) and has also worked as a postdoctoral fellow at the Institute for Cyber Security (ICS) at UTSA. His primary area of research includes security and privacy in cyber space focused in studying foundational aspects of access control, malware analysis, AI and machine learning assisted cyber security, and their applications in technologies including cyber physical systems, cloud computing, IoT and Big Data. He has worked in developing novel security mechanisms, models and architectures for next generation smart cars, intelligent transportation systems and smart farming. He was awarded the 2019 computer science outstanding doctoral dissertation research award from UT San Antonio. His research has been funded by the US National Science Foundation (NSF), NASA, and US Department of Defense (DoD) among others. He holds a B.Tech degree in Computer Science and Engineering, from India and an M.S. in Information Systems from Northeastern University, Boston, USA. |
![[Uncaptioned image]](https://cdn.awesomepapers.org/papers/aebc523c-2182-4763-b137-db1b661f0ad6/x9.png) |
Mahmoud Abdelsalam received the B.Sc. degree from the Arab Academy for Science and Technology and Maritime Transportation (AASTMT), in 2013, and the M.Sc. and Ph.D. degrees from the University of Texas at San Antonio (UTSA), in 2017 and 2018, respectively. He was working as a Postdoctoral Research Fellow with the Institute for Cyber Security (ICS), UTSA, and as an Assistant Professor with the Department of Computer Science, Manhattan College. He is currently working as an Assistant Professor with the Department of Computer Science, North Carolina A&T State University. His research interests include computer systems security, anomaly and malware detection, cloud computing security and monitoring, cyber physical systems security, and applied machine learning. |