A Geometric Approach to Resilient Distributed Consensus Accounting for State Imprecision and Adversarial Agents
Abstract
This paper presents a novel approach for resilient distributed consensus in multiagent networks when dealing with adversarial agents imprecision in states observed by normal agents. Traditional resilient distributed consensus algorithms often presume that agents have exact knowledge of their neighbors’ states, which is unrealistic in practical scenarios. We show that such existing methods are inadequate when agents only have access to imprecise states of their neighbors. To overcome this challenge, we adapt a geometric approach and model an agent’s state by an ‘imprecision region’ rather than a point in . From a given set of imprecision regions, we first present an efficient way to compute a region that is guaranteed to lie in the convex hull of true, albeit unknown, states of agents. We call this region the invariant hull of imprecision regions and provide its geometric characterization. Next, we use these invariant hulls to identify a safe point for each normal agent. The safe point of an agent lies within the convex hull of its normal neighbors’ states and hence is used by the agent to update it’s state. This leads to the aggregation of normal agents’ states to safe points inside the convex hull of their initial states, or an approximation of consensus. We also illustrate our results through simulations. Our contributions enhance the robustness of resilient distributed consensus algorithms by accommodating state imprecision without compromising resilience against adversarial agents.
I Introduction
In distributed multi-agent networks, agents work collaboratively to accomplish complex tasks by sharing information with each other. To make optimal decisions, they rely on this shared data. However, false or misleading information from a subset of agents–due to adversarial actions or other failures–can significantly compromise the network’s operations. Thus, to realize the full benefits of distributed decision-making, resilience to abnormal agents is crucial for the correct functioning of multi-agent systems. As such, there has been an increased interest in characterizing and imposing resilience in distributed systems.
Recent works on resilient distributed networks, particularly in resilient distributed consensus—a canonical problem in networked and distributed control systems–present a suite of algorithms and conditions on the network structure. If these conditions are satisfied, they guarantee the normal operations of the overall system [1, 2]. The main idea of such algorithms is to minimize the impact of information from adversarial or faulty agents, even without knowing their identities [3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18]. However, existing resilient consensus solutions often make the unrealistic assumption that agents can observe their neighbors’ exact, unperturbed states. In real-world applications, agents deal with imprecise data due to factors like sensor noise, environmental conditions, or hardware limitations [19, 20, 21, 22, 23]. As we demonstrate in this paper, applying current resilient algorithms in these ‘imprecise’ scenarios can lead to failures, even if the number of adversarial agents is below the theoretical threshold allowed by the solution. Therefore, new methods are needed, and this paper introduces strategies to handle both adversarial agents and imprecise states in multi-agent networks.
This paper introduces a new method to tackle the resilient distributed consensus problem, focusing on the commonly overlooked issue of state imprecision, that is, the observed states vary from the true state by a known bounded measure. There are existing studies that address a similar problem in a static scenario [24], however our formulation is developed independently and tailored towards the application of resilient consensus. Our approach ensures that all normal agents remain within the convex hull of their initial states and continuously converge towards a ball contained in the convex hull of the normal agents’ initial positions. The radius of the ball is dependent on the initial configuration, the actions of the attacker, and the stochastic discrepancy between true and observed states. However, the final state of each normal agent is guaranteed to be strictly contained in the initial convex hull of normal agents. We show that this approximation of “consensus” is achieved by the CPIH algorithm proposed in this paper, while existing distributed consensus algorithms fail to achieve even approximate consensus under imprecision. The crux of our method is ensuring that in each step of the state update process, a normal agent can find a point that is guaranteed to lie in the convex hull of its normal neighbors only. The agent then updates its state by moving towards that point, which is also referred to as the safe point [4, 3, 9, 25]. We show that existing methods fail to identify such safe points when faced with imprecision. In contrast, our approach successfully identifies these points and maintains the same level of resilience against adversarial agents as existing methods that do not account for state imprecision.
We summarize our key contributions as follows:
-
•
First, we show that current algorithms for resilient distributed consensus do not work well when agents have imprecise states (Section III). This is important because imprecise states are common in real-world applications.
-
•
Second, we introduce a new way to model these imprecise states. Instead of using points in , we use what we call ‘imprecision regions’ containing true states of agents. We then introduce the notion of invariant hull which is essentially the largest region that is contained in the convex hull of normal agents’ true states when only their imprecision regions are known. We also provide a geometric characterization of invariant hulls and an efficient algorithm to compute them (Section IV).
-
•
Third, we develop a method that leverages these invariant hulls to identify a ‘safe point’ in the neighborhood of a normal agent. This neighborhood may contain up to adversaries. Here, is the total number of nodes in the neighborhood of a normal agent and is the state dimension. This safe point allows the normal agent to update its state while ignoring any adversaries. We also illustrate our results through simulations (Section V).
The rest of the paper is organized as follows: Section II introduces preliminaries and notations. Section III reviews existing resilient consensus algorithms and show their inadequacy with imprecise states. Section IV introduces the invariant hull notion and discusses its computation and significance. Section V presents methods to compute safe point for resilient distributed consensus with imprecision, and present simulations. Finally, Section VI concludes the paper.
II Preliminaries
We consider a network of agents modeled by an undirected graph , where represents agents and denotes interactions among agents. An edge between agents and is denoted by an unordered pair . We use the terms agent and node interchangeably. Each agent has a -dimensional state vector whose value is updated over time. The state of agent at time is represented by a point . The neighborhood of is the set of nodes (node is included in its neighborhood). For a given set of points , we denote its convex hull by Conv. Also, we use terms points and states interchangeably.
Normal and Adversarial Agents – Agents in the network can either be normal or adversarial. Normal agents, denoted by , are the ones that interact with their neighbors synchronously and update their states according to a pre-defined state update rule, which is the consensus algorithm. Adversarial agents, denoted by , are the ones that can change their states arbitrarily. Moreover, an adversarial node can transmit different values to its different neighbors, which is referred to as the Byzantine model. The number of adversarial nodes in the neighborhood of a normal node is denoted by . For a normal node , all nodes in its neighborhood are indistinguishable, that is, cannot identify which of its neighbors are adversarial.
Agent Imprecision – We consider that each agent has an imprecise information of its neighbor’s state. In other words, an agent having agent as a neighbor, acquires/observes an imprecise value of agent ’s state, which could be due to perturbation as a result of improper calibration, hardware imprecision, or other measurement uncertainties. We denote this imprecise value of agents ’s state by , and associate a region of imprecision, such that the true value of agent ’s state, i.e., , can be anywhere inside this . An example of this imprecision model is a hypersphere with a center and radius . The true state value can be anywhere inside this hypersphere of radius (indicating the extent of imprecision). Another example of imprecision model is a hypercube, where imprecision in each coordinate is at most , as shown in Figure 1.

Resilient Consensus Problem – In a network with both normal and adversarial agents, the aim of resilient vector consensus is to design a mechanism that ensures all normal agents update their states to eventually converge on a common state. This common state must lie within the convex hull of their initial states, denoted as . The mechanism must satisfy the following conditions:
-
•
Safety: At any time step , the state of any normal node must lie within .
-
•
Agreement: For every , there exists a time , such that the states of any two normal agents and come within of each other for all .
Next, we discuss the resilient consensus solutions with and without imprecision.
III Effect of Imprecision
In this section, first, we review a resilient distributed consensus algorithm guarantees convergence of normal nodes despite adversarial agents without considering any imprecision in agents’ states. Then, we consider imprecision and show that the existing resilient algorithms fail to achieve consensus and perform poorly under states’ imprecision.
III-A Resilient Consensus with No Imprecision
Several resilient consensus schemes have been proposed in the literature for the scalar and higher dimensional cases, e.g., [3, 4, 5, 6, 7, 8, 9, 10, 1, 11, 12, 13, 14, 15, 2]. The main approach, especially in higher dimensions , relies on the principle that in each round/step of the consensus algorithm, each normal node computes a point that lies in the convex hull of its normal neighbors’ state, and then updates its state by moving towards that point, which is sometimes referred to as the ‘safe point’. The computation of this safe point is a challenging endeavour, and various methods are employed. A useful way that results in superior resilience (in terms of the number of adversarial agents that can be allowed) is to obtain a safe point by computing a centerpoint of the agents’ states. A centerpoint is a generalization of median in higher dimensions, and is defined below.
Definition 3.1.
(Centerpoint) Given a set of points in , a centerpoint is a point with the property that every closed halfspace of containing must also contain at least points of .
The set of all centerpoints is referred to as the centerpoint region. Figure 6 illustrates an example. There are six points in , and any line passing through a centerpoint divides these six points into two regions, each containing at least two points, as in Figures 6(a) and (b). Figure 6(c) illustrates the centerpoint region for the given example.


The notion of centerpoint provides a complete characterization of the safe point. It is shown in [4] that a safe point for an agent is essentially a centerpoint of its neighbors’ states as long as the number of adversaries in the neighborhood of is bounded by . Here, is the dimension of the state and is the number of neighbors of . Moreover, a safe point may not exist if the number of adversaries is more than . Thus, the centerpoint-based safe point computation is particularly useful.
Now, a resilient consensus algorithm based on centerpoints and considering no imprecision—agents observe their normal neighbors’ states exactly—can be designed as follows:
-
•
In each iteration , a normal agent gathers the state values of its neighbors in , and computes a safe point by computing a centerpoint agents’ states.
-
•
Agent updates its states as follows:
(1) where is a dynamically chosen parameter whose value depends on the application [3].
Analysis in [4] and [3] shows that the above scheme achieves resilient consensus as long as the number of adversaries in each normal agent is at most .
Next, we see how the above resilient consensus (and other safe point based) algorithms perform if we consider imprecise agents’ states.
III-B Resilient Solutions Do Not Work Under Imprecision
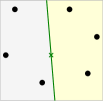
The fundamental premise of resilient consensus algorithms lies in computing safe points that are always inside the convex hull of normal agents’ true states. In the case of imprecision, however, the true states are unknown. Thus, computing a safe point is challenging, and the existing approaches prove inadequate. Note that, in general, true consensus is not possible when there is fixed imprecision in state values, however resilient consensus algorithms can fail to achieve approximate consensus as defined in Section I. For example, a centerpoint computed by a normal agent based on its neighbors’ observed states (due to imprecision) does not always lie in the convex hull of its normal neighbors’ true states and, therefore, is not a safe point. Figure 3 illustrates this situation.
In Figure 3(a), we have six agents that are in the neighborhood of a normal agent (including ). One of the agents, , is an adversary. Note that remains oblivious to the identity of the adversarial agent within its neighborhood. Each agent has a state in accompanied by a region of imprecision, which we assume to be a square. The centerpoint region based on the observed states (represented by ‘’) is highlighted in green, whereas the convex hull of normal agents’ true states (indicated by ‘’) is depicted as grey. Figure 3(b) reveals the challenge imprecision poses. The centerpoint region fails to remain entirely contained within the convex hull of the normal agents’ true states. Consequently, agent may select a centerpoint (indicated by ’’) that does not qualify as a safe point. As a result, may update its state by moving in a direction outside the convex hull of normal agents’ true states, thus violating the safety condition of the resilient consensus.

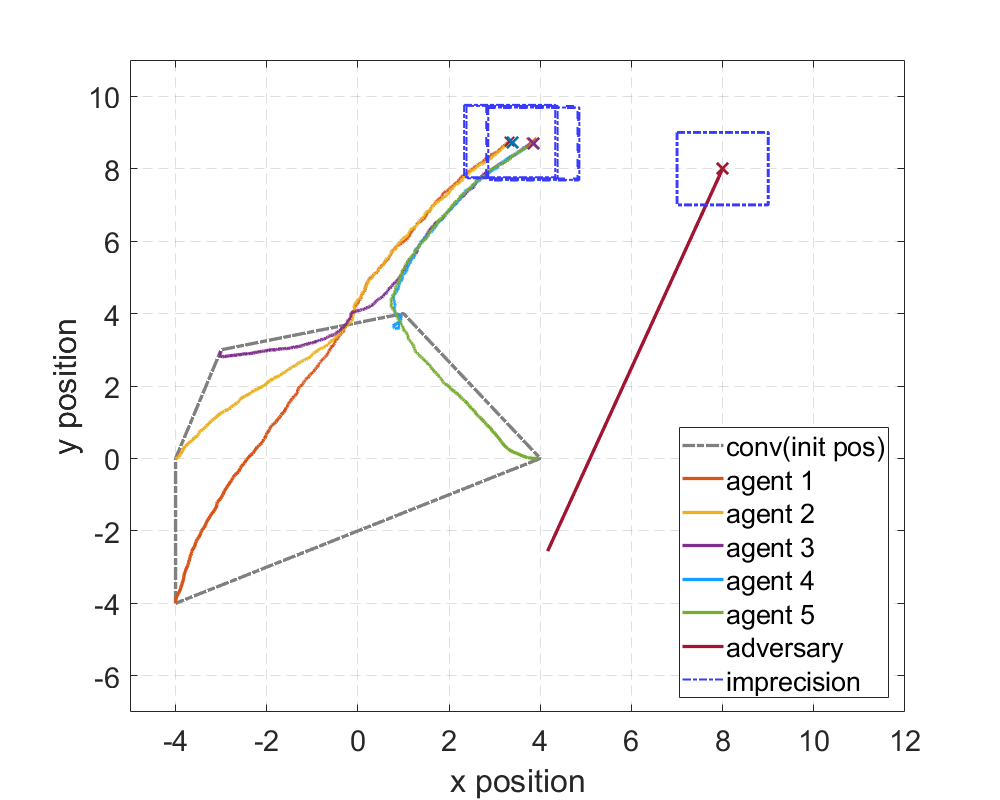
Figure 4 demonstrates examples of the run of the resilient consensus algorithm with and without the imprecision model. All six agents are pairwise adjacent, and there is one adversary. With no imprecision, all normal agents converge inside the convex hull of their initial states despite a single adversary, as shown by the state trajectories of agents in Figure 4(a). However, with imprecision (square regions), the resilient consensus algorithm fails as normal agents do not remain inside their initial states’ convex hull and continue moving farther away, as shown in Figure 4(b).
Thus, imprecision presents a significant obstacle to successfully operating resilient distributed algorithms. The primary hurdle arises from the difficulty in computing a safe point when dealing with imprecise observed states. Thus, it is imperative to explore new approaches to ensure the accurate computation of safe points, even in the presence of imprecision. We address this problem in the next section.

IV Resilience in the Presence of Imprecision
In this section, we address the challenge of dealing with imprecision in resilient consensus algorithms and present our approach to mitigate its impact. Our main objective is to enable normal agents to compute safe points even when they encounter imprecise state values from their neighbors.
When a normal agent observes an imprecise state of its neighbor , the agent essentially observes an imprecision region associated with . This imprecision region contains the true state value of , and is termed as a potential region (as any value in this region can potentially be a true value of the agent). Consequently, agent effectively observes a collection of potential regions linked to its neighbors. By selecting one value (a point) from each potential region, we construct a potential configuration for the given set of potential regions. It is worth noting that the true values of the agents represent just one potential configuration among an infinite set. Our focus lies in identifying the largest region contained within the convex hull of any potential configuration from a given set of potential regions. We refer to this set as an invariant hull. Importantly, an invariant hull, associated with a given set of potential regions is a subset of the convex hull of the true states of agents. At a high level, an invariant hull, pertaining to a specific set of potential regions, is akin to the convex hull of a given set of points. Figure 5 illustrates these concepts. Figure 5(a) shows a set of potential regions (blue boxes) and the associated invariant hull. Figure 5(b) shows one potential configuration (set of points in potential regions indicated by ‘’) and the associated convex hull of the potential configuration (grey shaded region). Note that the invariant hull is contained in the convex hull of the potential configuration shown. Similarly, if we choose any other potential configuration, the invariant hull will be contained in the convex hull of such a configuration.


Next, we introduce some notations and formally define invariant hull.
| Actual/true state of agent ; | |
| Observed state of agent ; | |
| potential region of agent ; | |
| Set of potential regions of agents in the set | |
| . |
Definition 4.1.
(Potential Configuration) For a given set of potential regions , a potential configuration is a set of points such that for each .
Now, we define the notion of invariant hull.
Definition 4.2.
(Invariant Hull) Consider a set of potential regions . Let be the set of all possible potential configurations, and Conv(P) denotes the convex hull of a potential configuration . Then, the invariant hull of is defined as,
| (2) |
In simpler terms, for the invariant hull, we find all possible potential configurations of , compute the convex hull of each such configuration, and finally compute the intersection of all such convex hulls. Consequently, the invariant hull is essentially a subset of the convex hull of any potential configuration of , as Figure 5 illustrates. Also, the invariant hull is a convex set.
Next, we provide a geometric characterization of the invariant hull. Then, in Section IV-B, we present an efficient method to compute the invariant hull of .
IV-A Characterization of Invariant Hull
First, we need to introduce notations to denote combinatorial families of sets.
-
•
Consider a set of potential regions , then denotes a family of all -member subsets of (i.e., subsets of consisting of potential regions). For example, consider , the corresponding , and , then
-
•
Similarly, for , the notation denotes the family of all -member subsets of . For example, in the above example, if , then
So, in general, a superscript on a set notation denotes the combinatorial family of the set.
The following lemma identifies the essential property for a point to be in the invariant hull of a set of potential regions.
Lemma 4.1.
Let be a -member subset of potential regions. If is non-empty, then a point if and only if has the following property:
-
fnum@PropertiesiProperty 1.Property 1.
For every hyperplane passing through , at least one potential region is contained in each of the associated halfspaces of .
Proof.
We prove the contrapositive. For a point , if , then by definition there exists a particular potential configuration such that and are disjoint. Then let denote a separating hyperplane, containing for which all points of are contained in , where is used to denote any halfspace of , with the opposite denoted . Since each of the points of are selected from the potential regions of , it follows that every potential region of extends into , and therefore no potential region is a subset of . Thus, if , then does not have Property 1.
Similarly, if a point does not possess Property 1, then there is a hyperplane passing through such that no potential region of is a subset of . Then it is possible to select such that . Since , and are disjoint, and thus .
Corollary 4.2.
For -region set , it follows from Lemma 4.1 that . Here we have used the set notation of “” to refer to the set of all elements of that are not elements of . This can be seen by observing that no point with Property 1 may exist in the convex hull of a -member subset of . Any hyperplane through and each of the members may only contain the remaining region of in one or the other of its halfspaces, leaving one halfspace with no potential region as a subset.
We now present an auxiliary lemma that will be used in proving Theorem 4.5 characterizing the invariant hulls.
Lemma 4.3.
If is a convex polytope, and if point is a vertex of , then for all -region subsets , , where refers to the interior of , or without its boundary points.
Proof.
Let denote in the following argument. Suppose is a set of potential regions of such that and is a vertex of . There are two possibilities: 1) , or 2) . In the first case, and therefore is not a vertex. In the second case, since is open, a -point configuration of can always be found that includes with such that . But since is invariant for any potential configuration by its definition, this is a contradiction, and therefore the assertion of Lemma 4.3 is true.
We now show that the the invariant convex hull of potential regions is the convex hull of the union of invariant hulls of each of the subsets of . First, we state a generalization of a theorem of Caratheodory to sets in , that will be used in our proof.
Theorem 4.4.
[26] For a family of sets , with , .
Note: Here and throughout the paper, if is a family of point sets, then .
In other words the convex hull of every point contained in the family of sets is equivalent to the union of the convex hulls of all of its -member subsets. Now, we state one of the main results of this section.Theorem 4.5.
Let be a collection of potential regions of and denote the family of -member subsets of . Then,
(3) Proof.
We will show that all vertices of are contained in . If is a vertex of , clearly . By Lemma 4.3, cannot be contained in the interior of the convex hull of any -member subset of . By Theorem 4.4, the convex hull of in is equal to the union of the convex hulls of its -member subsets. From Lemma 4.1 and Lemma 4.3, it follows that precisely contains all points that are in the interior of but not interior to the convex hull of any -member subset. This implies that . Furthermore for any , every point is trivially a point in , since and any point configuration of has a subset of points from the potential regions of . Since contains all vertices of and contributes no points exterior to , it follows that .
IV-B Computing the Invariant Hull
We now outline a procedure for computing the invariant hull of , given that . The procedure involves computing the equation of a tangent hyperplane equation to potential regions of . In the case that potential regions are polygons in , linear-time algorithms have been developed to find outer tangent lines, that is the tangent lines that have all participating polygons on one side [27].
Let . As stated in Corollary 4.2, is equivalent to . A simple approach is to compute the vertices of :-
1.
Select .
-
2.
For each , and each containing , compute hyperplane tangent to the members of such that and .
-
3.
Compute point of intersection:. Label as .
-
4.
Repeat steps 1-3 for all remaining .
-
5.
.
After repeating steps 1-5 for all , the invariant hull of is computed with any convex hull routine as:
according to Theorem IV-B.

(a) 
(b) 
(c) 
(d) 
(e) 
(f) 
(g) Figure 6: (a) Centerpoint region based on the intersection of the invariant hulls of subsets of potential regions. In each of (b)–(g), the green shaded region is contained entirely in the invariant hull of the five potential regions. V Resilient Consensus through Centerpoint using Invariant Hulls of Potential Regions
In this section, we present a way for a normal agent to compute a safe point despite access to only imprecise states of neighbors. Moreover, the proposed approach allows number of adversaries in the neighborhood of , where . The core of our method relies on the intersection of the invariant hulls of potential regions.
First, consider the case with no imprecision, i.e., normal agents observe true states of their neighbors (as discussed in [4, 25]). In this ideal situation, a safe point for a normal agent is effectively the centerpoint of its neighbors’ states, provided the number of adversarial agents in the neighborhood of is . This proposition is rooted in geometric principles. Specifically, a centerpoint of a given set of points in lies within the convex hull of any subset comprising more than of those points [28, 29, 30]. To put it practically, if we select an arbitrary subset of neighbors of —comprising more than neighbors—and compute the convex hull of their states, a centerpoint is guaranteed to lie within this hull. Since one such choice of more than neighbors of a normal agent consists of only normal neighbors of , a centerpoint of the states of agent ’s neighbors also lies within the convex hull of only the normal neighbors’ states.
In cases where the observed states are imprecise, the approach to determining a safe point for a normal agent must be modified. As elaborated in Section III-B, the inherent imprecision precludes the use of convex hulls calculated from observed states. Instead of knowing a true state of the neighbor, only knows the potential region of the neighbor (containing the true state). So, instead of computing convex hulls of subsets of neighbors’ observed states, a normal agent computes the invariant hulls of subsets of potential regions of neighbors. Assume that a normal agent has neighbors, of which at most are adversarial. For any subset of neighbors containing more than neighbors, agent computes the invariant hull of the potential regions of the corresponding neighbors, and then computes the intersection of all such invariant hulls. This resulting intersection serves as a modified ‘centerpoint region’, constructed from the invariant hulls of potential regions. Importantly, every point in this new centerpoint region is guaranteed to lie within the convex hull of the true states of agent ’s normal neighbors, and is thus a safe point (despite imprecise observed states). We illustrate this through an example below.
Example: Consider a set of six potential regions in a plane, each corresponding to an agent. Note that the true states of these agents are ‘hidden’ within these potential regions. Among these six, one potential region belongs to an adversarial agent, though we don’t know which one. The green-shaded region in Figure 6(a) is the centerpoint region constructed using the intersection of invariant hulls of subsets of potential regions. To see this, consider a subset of five potential regions—calculated as —and determine their invariant hull. As demonstrated in Figures 6(b)–6(g), the green centerpoint region is consistently enclosed within the invariant hull, regardless of which five potential regions are chosen. Notably, one of these choices in Figures 6(b)–6(g) includes the actual adversary. In this case, the computed invariant hull—by definition—remains a subset of the convex hull formed by the true states of normal agents. Therefore, the points in the green-shaded centerpoint region, which is contained entirely in the invariant hull, are assured to be safe points.
Next, we outline the steps of the state update for each normal agent. An essential step is the computation of a safe point using the idea of invariant hulls, as described previously. The steps of the algorithm, which we call centerpoint of invariant hulls (CPIH) method, are as follows:
For each node .
-
1.
At time compute .
-
2.
For , compute . ( Compute invariant hull of each -tuple of ).
-
3.
If , set . Otherwise, proceed to step 4. (Do nothing at time if safe region does not exist).
-
4.
Select safe point .
-
5.
.
The value of is a dynamic weight that may be chosen in range according to the application.
The CPIH algorithm identifies a region that is a generalization of the centerpoint region in that the property of a CPIH safe point has identical properties to that of of a centerpoint with compact sets replacing the role of points. Thus each halfspace of a hyperplane that intersects a CPIH safe point contains at least compact sets (potential regions of ). As such, every potential regions contain a CPIH safe point.
V-A Simulations and Discussion

(a) 
(b) 
(c) Figure 7: Implementation of CPIH algorithm. Normal agents remain inside the convex hull of their initial states and converge to a degree that depends on the level of state imprecision, as quantified by the parameter . In order to verify that the CPIH Algorithm succeeds where the ordinary centerpoint-based consensus algorithm fails (as illustrated in Figure 4), we executed a series of simulations using the above algorithm. For simplicity, potential regions were chosen to be a square of width centered around each node, and was chosen to be a complete graph. At each time step, agents received a uniformly random state estimate within the potential regions of each of its neighbors. For illustrative purposes, we chose a small range of values for . For each value of , a simulation was run for time steps. Figure 7 shows the results.
As may be inferred from Step 3 of the CPIH algorithm, this procedure will not, in general, result in uniform convergence of agents states. Instead, nodes will “cluster” into a region whose volume depends on the magnitude of . While this may appear to be an unsatisfactory result, it nonetheless assures that nodes will remain within their initial convex hull, whereas this is not the case for the resilient consensus algorithms that do not account for imprecision. As a result, CPIH algorithm presents a tradeoff between network safety and convergence precision, which is of significance on its own, especially when safety is of high priority in a setting with imprecision. In real world situations, imprecision typically decreases with proximity. Future developments of CPIH could achieve a convergent consensus under such an imprecision model.
VI Conclusion
In this paper, we have demonstrated that traditional resilient consensus algorithms can fail when they do not account for state imprecision. To address this, we proposed an uncertainty-aware geometric solution ensuring resilience against adversaries and state imprecision. Specifically, we extended the centerpoint-based resilient consensus algorithm by introducing the concept of an ’invariant hull,’ which we call the CPIH algorithm. Through illustrative simulations, we have showcased the effectiveness of our algorithm under varying levels of uncertainty. In the future, we aim to explore the resilience-accuracy trade-off further by determining the conditions under which the invariant hull of imprecise regions becomes empty.
References
- [1] H. Ishii, Y. Wang, and S. Feng, “An overview on multi-agent consensus under adversarial attacks,” Annual Reviews in Control, vol. 53, pp. 252–272, 2022.
- [2] M. Pirani, A. Mitra, and S. Sundaram, “Graph-theoretic approaches for analyzing the resilience of distributed control systems: A tutorial and survey,” Automatica, vol. 157, p. 111264, 2023.
- [3] H. Park and S. A. Hutchinson, “Fault-tolerant rendezvous of multirobot systems,” IEEE Transactions on Robotics, vol. 33, no. 3, pp. 565–582, 2017.
- [4] W. Abbas, M. Shabbir, J. Li, and X. Koutsoukos, “Resilient distributed vector consensus using centerpoint,” Automatica, vol. 136, p. 110046, 2022.
- [5] H. J. LeBlanc, H. Zhang, X. Koutsoukos, and S. Sundaram, “Resilient asymptotic consensus in robust networks,” IEEE Journal on Selected Areas in Communications, vol. 31, no. 4, pp. 766–781, 2013.
- [6] L. Su and N. Vaidya, “Multi-agent optimization in the presence of byzantine adversaries: Fundamental limits,” in American Control Conference (ACC), 2016, pp. 7183–7188.
- [7] H. Mendes, M. Herlihy, N. Vaidya, and V. K. Garg, “Multidimensional agreement in byzantine systems,” Distributed Computing, vol. 28, no. 6, pp. 423–441, 2015.
- [8] J. Yan, X. Li, Y. Mo, and C. Wen, “Resilient multi-dimensional consensus in adversarial environment,” Automatica, vol. 145, p. 110530, 2022.
- [9] J. Yan, Y. Mo, X. Li, and C. Wen, “A “safe kernel” approach for resilient multi-dimensional consensus,” IFAC-PapersOnLine, vol. 53, no. 2, pp. 2507–2512, 2020.
- [10] Y. Wang, H. Ishii, F. Bonnet, and X. Défago, “Resilient consensus for multi-agent systems under adversarial spreading processes,” IEEE Transactions on Network Science and Engineering, vol. 9, no. 5, pp. 3316–3331, 2022.
- [11] J. Li, W. Abbas, and X. Koutsoukos, “Resilient distributed diffusion in networks with adversaries,” IEEE Transactions on Signal and Information Processing over Networks, vol. 6, pp. 1–17, 2019.
- [12] Z. Yang and W. U. Bajwa, “Byrdie: Byzantine-resilient distributed coordinate descent for decentralized learning,” IEEE Transactions on Signal and Information Processing over Networks, vol. 5, no. 4, pp. 611–627, 2019.
- [13] L. Su and N. H. Vaidya, “Byzantine-resilient multiagent optimization,” IEEE Transactions on Automatic Control, vol. 66, no. 5, pp. 2227–2233, 2020.
- [14] J. Zhu, Y. Lin, A. Velasquez, and J. Liu, “Resilient distributed optimization,” in American Control Conference (ACC), 2023, pp. 1307–1312.
- [15] K. Kuwaranancharoen, L. Xin, and S. Sundaram, “Byzantine-resilient distributed optimization of multi-dimensional functions,” in American Control Conference (ACC), 2020, pp. 4399–4404.
- [16] J. Usevitch and D. Panagou, “Resilient leader-follower consensus to arbitrary reference values in time-varying graphs,” IEEE Transactions on Automatic Control, vol. 65, no. 4, pp. 1755–1762, 2019.
- [17] M. Safi, S. M. Dibaji, and M. Pirani, “Resilient coordinated movement of connected autonomous vehicles,” European Journal of Control, vol. 64, p. 100613, 2022.
- [18] S. M. Dibaji and H. Ishii, “Resilient consensus of second-order agent networks: Asynchronous update rules with delays,” Automatica, vol. 81, pp. 123–132, 2017.
- [19] D. Jayasimha, “Fault tolerance in a multisensor environment,” in Proceedings of IEEE Symposium on Reliable Distributed Systems, 1994, pp. 2–11.
- [20] E. F. Nakamura, A. A. Loureiro, and A. C. Frery, “Information fusion for wireless sensor networks: Methods, models, and classifications,” ACM Computing Surveys, vol. 39, no. 3, pp. 9–es, 2007.
- [21] M. Löffler, Data imprecision in computational geometry. Utrecht Univesity, 2009.
- [22] J. Park, R. Ivanov, J. Weimer, M. Pajic, S. H. Son, and I. Lee, “Security of cyber-physical systems in the presence of transient sensor faults,” ACM Transactions on Cyber-Physical Systems, vol. 1, no. 3, pp. 1–23, 2017.
- [23] G. Frehse, A. Hamann, S. Quinton, and M. Woehrle, “Formal analysis of timing effects on closed-loop properties of control software,” in IEEE Real-Time Systems Symposium, 2014, pp. 53–62.
- [24] T. Nagai, S. Yasutome, and N. Tokura, “Convex hull problem with imprecise input,” in Discrete and Computational Geometry. Berlin, Heidelberg: Springer Berlin Heidelberg, 2000, pp. 207–219.
- [25] J. Li, W. Abbas, M. Shabbir, and X. Koutsoukos, “Byzantine resilient distributed learning in multirobot systems,” IEEE Transactions on Robotics, vol. 38, no. 6, pp. 3550–3563, 2022.
- [26] I. Bárány, “A generalization of carathéodory’s theorem,” Discrete Mathematics, vol. 40, no. 2, pp. 141–152, 1982.
- [27] M. Abrahamsen and B. Walczak, “Common tangents of two disjoint polygons in linear time and constant workspace,” ACM Trans. Algorithms, vol. 15, no. 1, dec 2018.
- [28] J. Pach and P. K. Agarwal, Combinatorial Geometry. John Wiley & Sons, 2011.
- [29] J. Matousek, Lectures on Discrete Geometry. Springer Science & Business Media, 2013, vol. 212.
- [30] S. Ray and N. Mustafa, “An optimal generalization of the centerpoint theorem, and its extensions,” in Annual Symposium on Computational Geometry, 2007, pp. 138–141.
-
1.